IBM Christmas card attach: CS571
- 1. IBM Christmas Card Gauri Pulekar CS 528 Spring 2015
- 2. Season Of Joy And Gifts
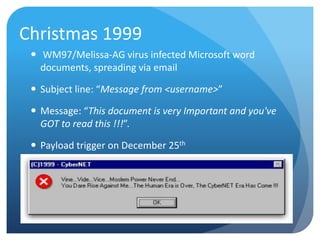
- 4. Christmas 1999 ’éŚ WM97/Melissa-AG virus infected Microsoft word documents, spreading via email ’éŚ Subject line: ŌĆ£Message from <username>ŌĆØ ’éŚ Message: ŌĆ£This document is very Important and you've GOT to read this !!!ŌĆØ. ’éŚ Payload trigger on December 25th
- 5. ŌĆó Attempt to format the C: drive on the next reboot. ŌĆó Insert randomly colored blocks in the current Word document
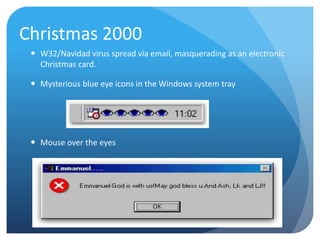
- 6. Christmas 2000 ’éŚ W32/Navidad virus spread via email, masquerading as an electronic Christmas card. ’éŚ Mysterious blue eye icons in the Windows system tray ’éŚ Mouse over the eyes
- 7. Christmas 2000 ’éŚ W32/Music email-aware worm ’éŚ Message: "Hi, just testing email using Merry Christmas music file, you'll like it.ŌĆØ ’éŚ Worm attached as a file called music.com, music.exe or music.zip.
- 8. ’éŚ Plays the first few bars of the song ’éŚ "We wish you a Merry ChristmasŌĆØ ’éŚ Displays a cartoon of Santa Claus with the caption ’éŚ "Music is playing, turn on your speaker if you have one" ’éŚ or "There is error in your sound system, music can't be heard."
- 9. Christmas 2001 ’éŚ Maldal virus spread via email using a seasonal electronic greeting card called Christmas.exe. ’éŚ Picture: Santa Claus on skis accompanied by a prancing reindeer ’éŚ Message: "From the heart, Happy new year!".
- 11. IBM Christmas Card: Facts ’éŚ When: 09th December 1987 ’éŚ Name: Christmas Tree Exec ’éŚ Place of Origin: Germany ’éŚ Significance: Worms were first noticed as a potential computer security threat ’éŚ Effect: It brought down both the world-wide IBM network and BITNET ’éŚ Source Language: REXX
- 12. Behavior ’éŚ E-mail Christmas card ’éŚ Subject line "Let this exec run and enjoy yourself!ŌĆØ. ’éŚ Included executable code. ’éŚ Claimed to draw a Christmas tree on the display. ’éŚ The user had to execute the program by typing christma or christmas.
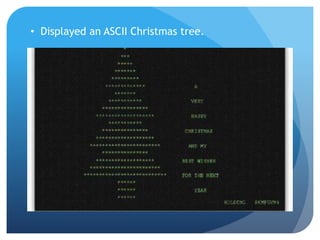
- 13. ŌĆó Displayed an ASCII Christmas tree.
- 14. ’éŚ A comment inside the source code: browsing this file is no fun at all just type CHRISTMAS from cms ’éŚ Sent a copy to everyone on the user's address lists.
- 15. Working ’éŚ Read the files: ’éŚ NAMES: Collection of information about other users with whom you communicate ’éŚ NETLOG: File transfer log ’éŚ Mailed itself to every email address ’éŚ Approximate number exceeded 1,000 ’éŚ People trusted it, because it was coming from a regular correspondent
- 16. The Name: CHRISTMA EXEC ’éŚ IBM VM systems originally required file names to be formatted as 8 characters + space + 8 characters ’éŚ IBM required REXX script files to have a file type of "EXECŌĆØ
- 17. Source of the Christmas card ’éŚ A student at the University of Clausthal in West Germany ’éŚ REXX scripting language: a shell script-like language for IBMŌĆÖs VM/CMS system ’éŚ Found by December 21 ’éŚ Barred from using his/her system. ’éŚ ŌĆ£The damage was unintentional and that the program was written to send Christmas greetings to my friends.ŌĆØ
- 18. Damage Done ’éŚ Worm itself wasnŌĆÖt malicious ’éŚ Exponential growth patterns ’éŚ Clogged servers, communication paths, spool directories ’éŚ Unintentional denial of service attack
- 19. Damage Done ’éŚ EARNet: ’éŚ The European Research and Education Networking Association (TERENA) ’éŚ BITNET: ’éŚ BITNET was an university computer network founded in 1981s at the City University of New York (CUNY) and Yale University ’éŚ Destroyed by December 14th
- 20. Damage Done ’éŚ IBM's VNet electronic mail network ’éŚ International computer networking system deployed in the mid-1970s. ’éŚ Developed inside IBM ’éŚ Provided the main email and file-transfer backbone for the company ’éŚ December 15th ’éŚ Paralyzed on 17th December ’éŚ Brought to a standstill two days later, only getting rid of the worm by shutting down the network. ’éŚ In 1990, Christmas Tree resurfaced after being posted to Usenet. IBM was forced to shut down its 350,000-terminal network
- 21. Countermeasures Taken ’éŚ Programmer at Cornell University had written a simple program ’éŚ Examined the network queues every five minutes and delete any files called Christma Exec; ’éŚ Purged about 300 copies in four and a half hours. ’éŚ Other operators did the same, writing and passing around ad- hoc program to eliminate copies of the worm.
- 22. Countermeasures Taken ’éŚ Such simple tools could only sample the queues every few seconds and purge what they found ’éŚ Worm could still sneak through to a limited degree. ’éŚ In Israel, one programmer wrote a program ŌĆ£anti-Christma Christma,ŌĆØ ’éŚ Examined usersŌĆÖ netlog to determine whether they had been victimized ’éŚ If yes, the new Christma would retrieve any copies of the original that had not yet been read by the addressee and then send itself onward to the same set of targets used by the original Christma.
- 23. Debate: Trojan or Worm ’éŚ Trojan: ’éŚ Appear to be useful, but will do damage once installed ’éŚ Required the user to download and run the attachment to make it replicate ’éŚ Worm: ’éŚ Virus Encyclopedia refers to it as a worm. ’éŚ Worms move from one computer to another regardless of any human action
- 24. References ’éŚ Burger, Ralf (1988). Computer viruses - a high tech disease. Abacus/Data Becker GmbH. p. 276. ISBN 1-55755-043-3. ’éŚ Capek, P.G.; Chess, D.M.; White, S.R.; Fedeli, A. (2003). "Merry Christma: An Early Network Worm". Security & Privacy 1 (5): 26ŌĆō 34. doi:10.1109/MSECP.2003.1236232. ’éŚ Martin, Will (March 4, 1988). "Re: BITNET Security". Security Digest (Mailing list). Archived from the original on September 25, 2006. Retrieved October 30, 2008. ’éŚ Patterson, Ross (December 21, 1987). "Re: IBM Christmas Virus". RISKS Digest (Mailing list). Retrieved October 30, 2008. ’éŚ "Viruses for the "Exotic" Platforms". VX Heaven. Archived from the original on August 6, 2013. Retrieved October 30, 2008. ’éŚ Otto Stolz. VIRUS-L Digest, Volume 5, Issue 178, "Re: CHRISTMA: The "Card"! (CVP)". 1992.11.12
- 25. Time to Discuss! Trojan ? ? Worm
- 26. Thank You