Illustration of ssl uses both asymmetric and symmetric encryption
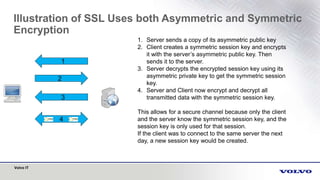
- 1. Volvo IT 4 Illustration of SSL Uses both Asymmetric and Symmetric Encryption 1 2 3 1. Server sends a copy of its asymmetric public key 2. Client creates a symmetric session key and encrypts it with the server’s asymmetric public key. Then sends it to the server. 3. Server decrypts the encrypted session key using its asymmetric private key to get the symmetric session key. 4. Server and Client now encrypt and decrypt all transmitted data with the symmetric session key. This allows for a secure channel because only the client and the server know the symmetric session key, and the session key is only used for that session. If the client was to connect to the same server the next day, a new session key would be created.
- 2. Volvo IT Steps Detail of SSL Handshake (Key Establishment) SSL Client e.g. LeaseVision SSL Server e.g. IIB (MQ) 1. Client Hello 2. Server Responds with Certificate 4. Client Encrypts Session Key with Server Certificate and Sends to Server 3. Client Creates Session Key 5. Server Decrypts Session Key 6. Session Key Used for Remainder of SSL Session • Server requires a digital certificate, which includes the server’s subject name, its public key, and a signature. • When a client establishes a connection to the server, the server authenticated to the client by submitting its certificate, the client then validates the certificate by referring to the signature.