Image analysis for malicious advertisement detection
- 1. Image analysis for fraudulent advertisements Jithendranath J V
- 3. Image Analyzer for Creative Tester User Issue / Yahoo! Challenge Roadmap Theme & Goal âĒ Creative Tester gets approximately around a million creatives per day to be tested for malicious content. Of this 2 %â 5 % of adverts are of category windows mimic. These needs to be detected and banned at the earliest, with less human intervention. âĒ Need to validate brand safety and ensure quality impressions for advertisers. âĒ Trust and Safety team in collaboration with Sciences came up with a Image Analyzer module that can detect the malicious advertisements like windows mimic or fake brands with phony downloads and tag them appropriately to be banned. Value Proposition/Positioning â To reduce the manual effort in recognizing and banning of malicious advertisements that can be visually identified as fraudulent 3 12/4/2013
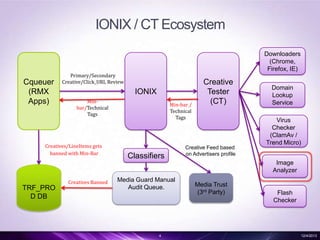
- 4. IONIX / CT Ecosystem Downloaders (Chrome, Firefox, IE) Cqueuer (RMX Apps) Primary/Secondary Creative/Click_URL Review IONIX Minbar/Technical Tags Creatives/LineItems gets banned with Min-Bar Min-bar / Technical Tags Classifiers Creative Tester (CT) Creative Feed based on Advertisers profile Domain Lookup Service Virus Checker (ClamAv / Trend Micro) Image Analyzer TRF_PRO D DB Creatives Banned Media Guard Manual Audit Queue. 4 Media Trust (3rd Party) Flash Checker 12/4/2013
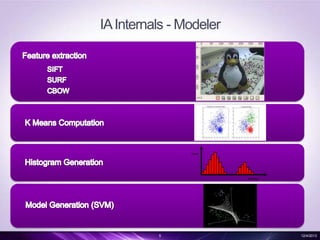
- 5. IA Internals - Modeler 5 12/4/2013
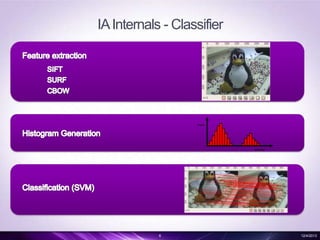
- 6. IA Internals - Classifier 6 12/4/2013
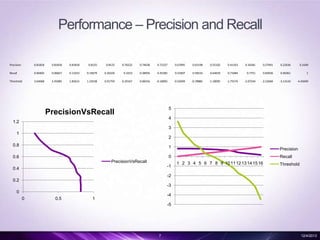
- 7. Performance â Precision and Recall Precision 0.81818 0.81818 0.81818 0.8125 0.8125 0.76522 0.74638 0.72327 0.67895 0.65198 0.55102 0.41163 0.34281 0.27941 0.22636 0.1649 Recall 0.00402 0.06827 0.13253 0.19679 0.26104 0.3253 0.38956 0.45382 0.51807 0.58233 0.64659 0.71084 0.7751 0.83936 0.90361 1 Threshold 3.64068 2.45085 1.85615 1.24538 0.91759 0.29167 0.06556 -0.18092 -0.52049 -0.78885 -1.18095 -1.75574 -2.07244 -2.52684 -3.13143 -4.45694 5 PrecisionVsRecall 4 1.2 3 1 2 0.8 1 0 0.6 Precision Recall PrecisionVsRecall -1 0.4 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 Threshold -2 0.2 -3 0 0 0.5 -4 1 -5 7 12/4/2013
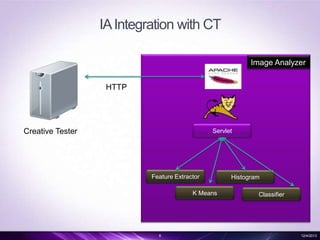
- 8. IA Integration with CT Image Analyzer HTTP Creative Tester Servlet Feature Extractor K Means 8 Histogram Classifier 12/4/2013
- 9. IA - API Example Response: Request: { { "responses":[ { "requests":[ { "imgid":"1", "imgurl":"http://ionix.zenfs.com/ct/dev2/screenshots/5d079 b5de50f6b30602e4a00b84a6e49e9443af7.jpg", "imgid":"1", "classifiers":[ { "classifier":"wnddlg", "statusâ:true, "result":true, "conf":0.40216639639794 }] } ] } "imgurl":"http://ionix.zenfs.com/ct/dev2/screenshots/5d0 79b5de50f6b30602e4a00b84a6e49e9443af7.jpg", "run_wnddlg":true } ] } 9 12/4/2013
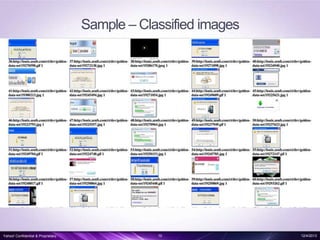
- 10. Sample â Classified images Yahoo! Confidential & Proprietary. 10 12/4/2013
- 11. What Does Success Look Like âĒ Who are the customers? â RMX and APT creative serving systems. â Moneyball (Going forward) âĒ Success metrics â Reducing the manual effort needed in identifying win mimic based advertisements â This would be measured by the confidence score generated by the system, that would eventually help us do everything automated â Reduction in customer complaints. âĒ Key business stakeholders who have/will validate success â Serving systems â Business teams â Manual review teams 11 12/4/2013
- 12. Competitive Landscape âĒ 3rd party ad verification companies. etc., âĒ What differentiates our product/Solution? â â â â Avoiding the need to expose and send out demand inventory. Flexibility to keep improvising the algorithms for higher precision/recall. Quick turn around time for validation. Building highly targeted models ( for ex: fake facebook, or fake adobe) 12 12/4/2013
Editor's Notes
- #5: Cequer -> Ionix -> Can send to DLSor to CT -> set of tests like downloader, virus checker, flash checker etc.,classifier for landing page detection and also 3rd party validations.The results are tagged and sent back.Business logic on what action to take will be done by cequer.
- #6: Feature Extraction:In pattern recognition and in image processing, feature extraction is a special form of dimensionality reduction.When the input data to an algorithm is too large to be processed and it is suspected to be notoriously redundant (e.g. the same measurement in both feet and meters) then the input data will be transformed into a reduced representation set of features (also named features vector). Result of application of local neighborhood operation on the image. Neighborhood operation means, going to every point and then applying a function on that point, based on its neighbor. Visit each point p in the image data and do { N = a neighborhood or region of the image data around the point p result(p) = f(N)} Edge detection:Edge detection is the name for a set of mathematical methods which aim at identifying points in a digital image at which the image brightness changes sharply or, more formally, has discontinuities. Corner detection:Interest point detection or corner can be defined as the intersection of two edges. A corner can also be defined as a point for which there are two dominant and different edge directions in a local neighborhood of the point. Blob detection:Informally, a blob is a region of a digital image in which some properties are constant or vary within a prescribed range of values; all the points in a blob can be considered in some sense to be similar to each other.Sift - Scale invariant feature transform:Sift algorithm will calculate features that are scale invariant. Which means the image can still be recognized, when it is rotated or scaled or when viewed from a different view point.CBOW - Contextual Bag of WordsIn computer vision, the bag-of-words model (BoW model) can be applied to image classification, by treating image features as words. In document classification, a bag of words is a sparse vector of occurrence counts of words; that is, a sparse histogram over the vocabulary. In computer vision, a bag of visual words is a sparse vector of occurrence counts of a vocabulary of local image features.SVM:a support vector machine constructs a hyperplane or set of hyperplanes in a high- or infinite-dimensional space, which can be used for classification, regression, or other tasks.



![IA - API Example
Response:
Request:
{
{
"responses":[
{
"requests":[
{
"imgid":"1",
"imgurl":"http://ionix.zenfs.com/ct/dev2/screenshots/5d079
b5de50f6b30602e4a00b84a6e49e9443af7.jpg",
"imgid":"1",
"classifiers":[
{
"classifier":"wnddlg",
"statusâ:true,
"result":true,
"conf":0.40216639639794
}]
}
]
}
"imgurl":"http://ionix.zenfs.com/ct/dev2/screenshots/5d0
79b5de50f6b30602e4a00b84a6e49e9443af7.jpg",
"run_wnddlg":true
}
]
}
9
12/4/2013](https://image.slidesharecdn.com/imageanalyzerad-blr-ic4ic5techtalk-131204224110-phpapp01/85/Image-analysis-for-malicious-advertisement-detection-9-320.jpg)