InsiderAttack_p3.ppt
- 1. Impact on Confidentiality due to Insider Attacks Project Part 3 Submitted by the Team: AVATAR (Jonathon Raclaw, Marek Jakubik, Rajesh Augustine, and Rao Pathangi)
- 2. ? Impact on Confidentiality due to Insider Attacks ? An insider is anyone with access to an organization's protected assets ? Insider attack is someone using that access to violate protocol or cause harm intentionally or unintentionally ? Protocol violations with good intentions are still considered threats ? We have already identified a variety of fields that have vulnerabilities due to Insider Attacks ? A Telecommunications Company and itˇŻs employees having default access to sensitive test data ? A Credit Card Company and itˇŻs employees having access to customer credit card numbers ? A Health Care Company and the diverse collection of people/employees that have access to user health data [2] Introduction and Background
- 3. ? There are four basic sources of insider security problems: ?Maliciousness ¨C that results in compromise or destruction of information, or disruption of services to other insiders ?Disdain of Security Practices ¨C that results in compromise or destruction of information, or disruption of services to other insiders. ?Carelessness ¨C in the use of an information system and/or the protection of company information ?Ignorance ¨C of security policy, security practices and information system use ? Current state of work: ?Basic User ID/ password validation ¨C missing role based access, department based access. If you know the User ID/ Password then you have pretty much every thing ?Policy and procedures ¨C Not strictly enforced [3]
- 4. ? Develop stronger authentication mechanisms ¨C Some apps do have generic User ID/ Password ? Implement role based access control ¨C Provide just what they are eligible to see ? Provide access to the information based on their departmentˇŻs business need ¨C Provide just what they need ? Enforce the security policy ¨C tie the violations to job performance [5]
- 5. ? Purchase Hitachi ID Identity Manager ¨C To better manage user access identities and privileges on a variety of IT systems ? Hitachi ID Identity Manager ¨C A complete user provisioning solution that also automates and simplifies the routine tasks of managing users across multiple systems ? Features provided by Hitachi ID Identity Manager ? Provides the Role Based Access Control (RBAC) ? Enables prompt and complete access deactivation across multiple systems ? Automatically deactivates access for terminated users ? Enforces authorization rules over security change requests ? Existing work ? No Role Based Access Control ¨C If you know User ID/ Password then you are good to go ? No centralized control of access control ? Each system has itˇŻs own way of authenticating users, some with no authentication!!!
- 6. Architectural view of Hitachi ID Integration [1]
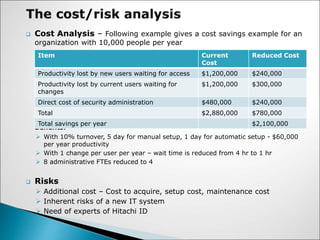
- 7. ? Cost Analysis ¨C Following example gives a cost savings example for an organization with 10,000 people per year Benefits: ? With 10% turnover, 5 day for manual setup, 1 day for automatic setup - $60,000 per year productivity ? With 1 change per user per year ¨C wait time is reduced from 4 hr to 1 hr ? 8 administrative FTEs reduced to 4 ? Risks ? Additional cost ¨C Cost to acquire, setup cost, maintenance cost ? Inherent risks of a new IT system ? Need of experts of Hitachi ID Item Current Cost Reduced Cost Productivity lost by new users waiting for access $1,200,000 $240,000 Productivity lost by current users waiting for changes $1,200,000 $300,000 Direct cost of security administration $480,000 $240,000 Total $2,880,000 $780,000 Total savings per year $2,100,000
- 8. ? Suited for large companies ¨C Large companies where we have many systems and large number of employees ? Build vs. Buy ¨C Building Custom solution would be more costly and may not produce an effective security solution, so go for a ready made solution ? Enterprise wide solution ¨C This strategy is to be adopted by the IT and other users of the companyˇŻs resources such as contractors, visitors, etc ? Incremental Deployment ¨C Is it incrementally deployable and would not require a require complete tear-down. ? Cost ¨C Cost is an obstacle but security needs to be implemented and enforced ? Lack of expertise ¨C Most of the companies lack expertise in building security solutions, so trust the leader in the field
- 9. ? Benefits of Hitachi ID versus Sun Identity Server ? More platform-neutral solution for their IDM products as opposed to Sun that is tied to Oracle ? Recognized by industry as more scalable and reliable ? Integrates equally well with all the major databases, operating systems, web servers and ERP applications ? User provisioning is open to allow easy integration ? Lower lifetime support costs for deployed systems since the customer has a stronger bargaining position at maintenance renewal time, since replacing one product is much easier than replacing many. [1]
- 10. A basic tenet of legal liability should compel a company to address security issues and to eliminate or mitigate hazardous conditions promptly. ? Business: ? No lost revenue due to malicious activities ? Reputation is maintained/ increased by reducing the information breaches and fraud ? Increased user productivity by automating and centralizing the access control ? Cost savings in a longer run ? Safeguard of the confidential information ? Legal: ? Regulatory Compliance such as Sarbanes-Oxley, HIPAA ? Avoid regulatory penalties for non compliance ? Avoid Lawsuits by customers for information leakage
- 11. ? With the Hitachi ID solution in place, we could more easily limit access to certain tools, such as make only development and test teams have access to test tools. Thus reducing the temptation of insider attacks by parties that are outside of the target environment. ? As the Hitachi implementation would work with the existing employee grade and position matrix, the Role Based Access Control (RBAC) could be targeted and changed easily if there is a restructure effort from management. ? Easy monitor of access to telecom systems, provisioning data, customer data, technical and product development data Fit of Proposed Solution for Telecom sector
- 12. ? Complex nature of business with several applications need a centralized control ? Cost savings by using Hitachi ID product does makes business sense ? Access for Customer Service Agents ?Role based, Example: regular agents, supervisors ?Based on their department, Example: marketing, collections, product sales ? Access to Intranet Applications ¨C Based on roles, Example: employee, manager, director ? Access to specific functionalities within a Application ¨C Based on roles, Example: in the time entry tool managers to see their staff information
- 13. ? Large number of applications for a educational setup ? Constant need of creating and removing the access for students ? Hitachi ID enables to propagate the password changes to multiple applications ? Access to Intranet Applications ¨C Based on roles, Example: student, professor ? Access to specific functionalities within a Application ¨C Based on roles Example: for teaching aid apps such as black board, professors to have more access than student
- 14. Risk Assessment Outcomes Threats Prioritized Risks Select Countermeasures System Design Policies Requirements Available Countermeasures Security Components Develop Security Architecture Security Architecture [4]
- 15. Source: ˇ°A Survey of Insider Attack Detection Researchˇ± by Malek Ben Salem, Shlomo Hershkop, and Salvatore J. Stolfo ? Modeling Unix shell commands: identify signature behavior of users based on the sequence of shell commands executed. ? Support Vector Machines ¨C Pattern Recognition: Model ˇ±insiderˇ± click behavior based on ˇ°clickˇ± data to monior ˇ°webˇ± traffic. ? Network Observable User Actions (ELICIT): Model data flow patterns relating to searching, browsing, downloading, printing, sensitive search terms, printer choice, anomalous browsing activity, and retrieving documents outside of oneˇŻs social network. ? Honeypots: Systems deliberately placed in the infrastructure to weed out malicious insiders. ? Future Research: ? Develop profile models that reveal ˇ°user intentˇ± as opposed to ˇ°user activity.ˇ± ? Develop integrated systems that follow the ELICIT model. ? Develop systems that preserve privacy in the event of a false positive ? Intelligent challenge/response model based on suspicion of anamalous activity ? ˇ°Trap the traitorˇ± solutions (IT + Psychology)
- 16. What How [4]
- 17. 1. http://hitachi-id.com/ 2. http://www.secretservice.gov/ntac/its_report_040820.pdf 3. http://www.itsecurity.com/ 4. ˇ°Security Attribute Evaluation Method: A Cost Benefit Analysisˇ±, Shawn A. Butler, Computer Science Department, Carnegie Mellon University 5. ITM Whitepaper, An Introduction to Insider Threat Management, Presented by infoLock Technologies 6. ˇ°A Survey of Insider Attack Detection Researchˇ± by Malek Ben Salem, Shlomo Hershkop, and Salvatore J. Stolfo

![? Impact on Confidentiality due to Insider Attacks
? An insider is anyone with access to an organization's protected
assets
? Insider attack is someone using that access to violate protocol
or cause harm intentionally or unintentionally
? Protocol violations with good intentions are still considered
threats
? We have already identified a variety of fields that have
vulnerabilities due to Insider Attacks
? A Telecommunications Company and itˇŻs employees having
default access to sensitive test data
? A Credit Card Company and itˇŻs employees having access to
customer credit card numbers
? A Health Care Company and the diverse collection of
people/employees that have access to user health data [2]
Introduction and Background](https://image.slidesharecdn.com/insiderattackp3-221114040951-2778544f/85/InsiderAttack_p3-ppt-2-320.jpg)
![? There are four basic sources of insider security
problems:
?Maliciousness ¨C that results in compromise or destruction of
information, or disruption of services to other insiders
?Disdain of Security Practices ¨C that results in compromise or
destruction of information, or disruption of services to other
insiders.
?Carelessness ¨C in the use of an information system and/or the
protection of company information
?Ignorance ¨C of security policy, security practices and
information system use
? Current state of work:
?Basic User ID/ password validation ¨C missing role based
access, department based access. If you know the User ID/
Password then you have pretty much every thing
?Policy and procedures ¨C Not strictly enforced [3]](https://image.slidesharecdn.com/insiderattackp3-221114040951-2778544f/85/InsiderAttack_p3-ppt-3-320.jpg)
![? Develop stronger authentication
mechanisms ¨C Some apps do have generic
User ID/ Password
? Implement role based access control ¨C
Provide just what they are eligible to see
? Provide access to the information based on
their departmentˇŻs business need ¨C Provide
just what they need
? Enforce the security policy ¨C tie the
violations to job performance
[5]](https://image.slidesharecdn.com/insiderattackp3-221114040951-2778544f/85/InsiderAttack_p3-ppt-4-320.jpg)

![Architectural view of Hitachi ID Integration
[1]](https://image.slidesharecdn.com/insiderattackp3-221114040951-2778544f/85/InsiderAttack_p3-ppt-6-320.jpg)

![? Benefits of Hitachi ID versus Sun Identity Server
? More platform-neutral solution for their IDM products
as opposed to Sun that is tied to Oracle
? Recognized by industry as more scalable and reliable
? Integrates equally well with all the major databases,
operating systems, web servers and ERP applications
? User provisioning is open to allow easy integration
? Lower lifetime support costs for deployed systems
since the customer has a stronger bargaining position
at maintenance renewal time, since replacing one
product is much easier than replacing many. [1]](https://image.slidesharecdn.com/insiderattackp3-221114040951-2778544f/85/InsiderAttack_p3-ppt-9-320.jpg)




![Risk
Assessment
Outcomes
Threats
Prioritized
Risks Select
Countermeasures
System
Design
Policies Requirements
Available
Countermeasures
Security
Components Develop
Security
Architecture
Security Architecture
[4]](https://image.slidesharecdn.com/insiderattackp3-221114040951-2778544f/85/InsiderAttack_p3-ppt-14-320.jpg)

![What
How
[4]](https://image.slidesharecdn.com/insiderattackp3-221114040951-2778544f/85/InsiderAttack_p3-ppt-16-320.jpg)

















































![YTD Video Downloader Pro 7.6.2.1 Full Crack [Latest]](https://cdn.slidesharecdn.com/ss_thumbnails/chapter6socialmobilemarketing-250319033537-a777274a-250319222733-b19b89de-thumbnail.jpg?width=560&fit=bounds)

![Adguard Premium Crack + License Key [Latest Version]](https://cdn.slidesharecdn.com/ss_thumbnails/understandingblockchain-250316100234-eef745e9-thumbnail.jpg?width=560&fit=bounds)


