Intro to White Chapel
- 1. White Chapel Password Auditing Framework
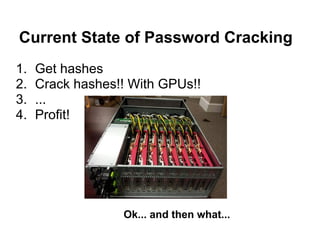
- 2. Current State of Password Cracking 1. Get hashes 2. Crack hashes!! With GPUs!! 3. ... 4. Profit! Ok... and then what...
- 4. The 'dark side' to Password Cracking â—Ź Dump/Cracked are either deleted or left scattered around the cracking box â—Ź Clear-text passwords never make it to password cracking box for addition to dictionaries (don't need to be cracked) â—Ź Each team member uses their own methods, tools, and dictionaries
- 5. The 'dark side' to Password Cracking - cont'd â—Ź Running the same dictionary over and over is a waste of computer time â—Ź Cross-hash knowledge is that golden nugget that gets forgotten â—‹ Password "P#$$w0rd1259_%" cracked because LM stored, isn't checked against MySQL hash and goes uncracked because hash type is unrealistic to brute to 14 characters
- 6. But why not use one of the online hash databases? â—Ź No way I'm going on unemployment for divulging internal passwords to a 3rd party. â—Ź For the most part they don't allow upload of files ( pwdump / shadow / dictionary ) to do mass lookups/adds â—Ź Not open source. I don't know what or where the things I'm looking up go
- 7. What about #{hash_cracking_tool} â—Ź WhiteChapel doesn't try to replace or do cracking better, John The Ripper and Hashcat have teams and community support. â—‹ Not to mention WAY better at math than me â—Ź WhiteChapel should just be your first (check for any known passwords instantly) and last (import all of your known passwords) stop on the password cracking train
- 8. Enter White Chapel my solution to those issues
- 10. White Chapel 1.0
- 11. Problem 1: No centralized storage â—Ź WhiteChapel uses ElasticSearch as a backend "database" of passwords and hashes
- 12. Problem 2: Clear-Text Passwords â—Ź WhiteChapel allows you to input either dictionaries or single passwords through an easy to use web interface
- 13. Problem 3: No team collaboration â—Ź WhiteChapel utilizes a centralized, yet easily clustered Elastic Search backend. â—Ź Joe imports their dictionary â—Ź Alice adds the 20 character password they found in a text file â—Ź Joe finds a MySQL hash that matches that 20 character password â—Ź Alice finds 20 extra passwords using WhiteChapel's mass-lookup due to Joe's dictionary contribution
- 14. Problem 4: Re-running same dictionary â—Ź WhiteChapel enables upload of pwdump and hashlist files, this allows for near instant searching of hashes stored in whitechapel, no matter the hash type's cracking speed â—Ź Since ElasticSearch can easily handle billions of what it calls "documents", this can out-pace standard cracking tools
- 15. Problem 5: Cross-hash knowledge â—Ź Since WhiteChapel generates all of the supported hash types for all of the passwords inputted, finding where users have re-used passwords can result in new findings â—Ź This is mostly useful beyond the threshold of standard brute-force lengths (passwords over 10 characters) and saves you time processing a "found pass" dictionary.
- 17. Installation Steps (Dependencies) 1. Ruby 2. ElasticSearch a. Download then run ./bin/elasticsearch -f b. Requires Java or OpenJDK c. http://www.elasticsearch.org/download/ 3. Redis Server a. Download then run ./redis-server --foreground b. http://redis.io/download Both of those options are foreground running, works in screen, but each OS has service based options
- 18. Installation Steps 1. git clone repo a. edit elastic.conf for elasticsearch ip/port if different b. edit Rakefile for redis ip/port if different 2. bundle install (to pull ruby gems)
- 19. Start the app, queue system and one worker 1. foreman start
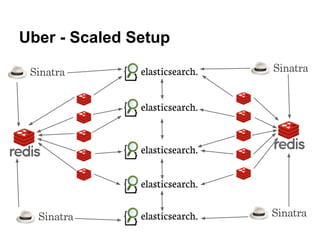
- 20. Expanding... â—Ź Start more elasticsearch servers â—‹ elasticsearch/bin/elasticsearch -f â—Ź Start more redis servers â—‹ redis/redis-server --foreground â—Ź Start more redis-resque workers â—‹ ./scripts/start_worker.sh â—Ź Start another Sinatra front-end â—‹ ruby app.rb
- 21. Infrastructure
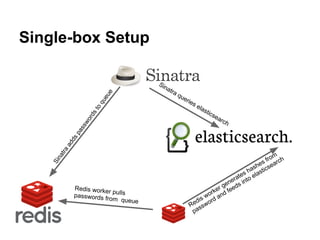
- 22. Single-box Setup Sin atr aq e eu ue qu ries ela o sti st cs e rd arc wo h ss pa ds ad tra m na fro rch Si es a sh ticse ha s es ela rat o ne s int ge d Redis worke rp rk er fee passwords fr ulls wo and om queue is d ed wor R ss pa
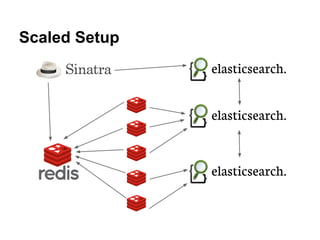
- 23. Scaled Setup
- 24. Uber - Scaled Setup