Introduction of Opentitan security model
- 1. OpenTitan Security Model Chia-Wei Wang 2021.10.26
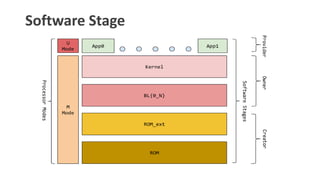
- 2. Outline ŌĆó Overview ŌĆó Logical Security Model ŌĆó Logical Entities ŌĆó Software Stage ŌĆó Memory layout ŌĆó Device Life Cycle ŌĆó Device Provisioning ŌĆó Ownership Transfer ŌĆó Identity and Root Key ŌĆó Device Attestation ŌĆó Secure Boot ŌĆó Boot Service
- 3. Overview ŌĆó Atrustworthy, vendor-agnostic opensourcesilicon RootofTrust (RoT)project ŌĆó Administrated bylowRISCCommunity Interest Company(C.I.C,non-profit) ŌĆó Based onRISC-VISA
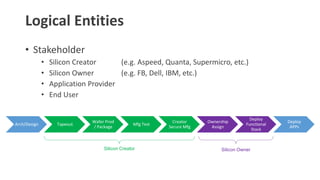
- 4. Logical Entities ŌĆó Stakeholder ŌĆó Silicon Creator (e.g. Aspeed, Quanta, Supermicro, etc.) ŌĆó Silicon Owner (e.g. FB, Dell, IBM, etc.) ŌĆó Application Provider ŌĆó End User Arch/Design Tapeout Wafer Prod / Package Mfg Test Creator Secure Mfg Ownership Assign Deploy Functional Stack Deploy APPs Silicon Creator Silicon Owner
- 7. OpenTitan Security Model Specification
- 8. Device Life Cycle ŌĆó Device operational states supported for ŌĆó Manufacturing ŌĆó Provisioning ŌĆó Regular operation ŌĆó RMA
- 9. Device Life Cycle Diagram Manufacturing State Manufacturing State ŌåÆ Identity Ownership State Identity & Ownership State ŌåÆ ŌĆó Unlock token is required for Conditional Transition ŌĆó Not require CPU intervention ŌĆó Sent via Test Access Port (TAP) interface Unlock Token Unlock Token ŌåÆ
- 10. Life Cycle State Capability Functions DFT_EN NVM_DEBUG_EN HW_DEBUG_EN CPU_EN RAW Y TEST_LOCKED TEST_UNLOCKED Y Y Y Y DEV Y Y PROD Y PROD_END Y RMA Y Y Y Y SCRAP INVALID DFT: Design For Test NVM: Non-Volatile Memory
- 11. Device Provisioning ŌĆó Device personalization ŌĆó Initialization of cryptographic secret for creator and device ŌĆó Occurs at manufacturing phase ŌĆó Device owner personalization ŌĆó Initialization of cryptographic secret for next owner
- 13. Device Owner Personalization ŌĆó ATE at manufacturing ŌĆó x86/AMD server at post-manufacturing (preferred)
- 14. Ownership Transfer ŌĆó Owner keys provisioned ŌĆó CODE_SIGN ŌĆó UNLOCK ŌĆó NEXT_OWNER ŌĆó CODE_SIGN ŌĆó Verify signed owner BL0 bootloader ŌĆó RSA-3072 public key with exponent 3 or F4 ŌĆó UNLOCK ŌĆó Verify signed command for UNLOCKED_OWNERSHIP state transition ŌĆó ECC NIST-P256 public key ŌĆó NEXT_OWNER ŌĆó Verify signed manifest with new owner keys included ŌĆó ECC NIST-P256 public key
- 15. Ownership Transfer Flow Kernel Signing Authority ROM_EXT 1. Request signature for OWNERSHIP_UNLOCK command 4. Request signature for next ownerŌĆÖs manifest 2. (OWNERSHIP_UNLOCK_CMD)UNLOCK 5. (NEXT_OWNER_MANIFEST)NEXT_OWNER 3. Request UNLOCKED_OWNERSHIP state transition with (OWNERSHIP_UNLOCK)UNLOCK 6. Request new manifest installation with (NEXT_OWNER_MANIFEST)NEXT_OWNER 7. New owner key provisioning K: Pre-provisioned Device Integrity Secret Kn = MAC(K, "OwnerSlot" | slot | id | prev_owner_digest) OpenTitan
- 16. Identities and Root Keys ŌĆó Terminology ŌĆó Device Identifier ŌĆó Non-cryptographic, per-device data ŌĆó Creator/Owner Public and Private Key ŌĆó Asymmetric key-pair authenticated by CA and verified through PKI chain ŌĆó Creator/Owner Identity ŌĆó Asymmetric key-pair derived for the attestation to the authenticity of the combination of HW and SW configuration ŌĆó xxxKey ŌĆó Symmetric key for key derivation and SW use ŌĆó KM_DERIVE ŌĆó Key Manager one-way function to derive a new symmetric key
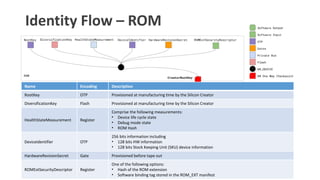
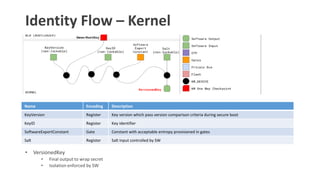
- 17. Identity Flow
- 18. Identity Flow ŌĆō ROM Name Encoding Description RootKey OTP Provisioned at manufacturing time by the Silicon Creator DiversificationKey Flash Provisioned at manufacturing time by the Silicon Creator HealthStateMeasurement Register Comprise the following measurements: ŌĆó Device life cycle state ŌĆó Debug mode state ŌĆó ROM Hash DeviceIdentifier OTP 256 bits information including ŌĆó 128 bits HW information ŌĆó 128 bits Stock Keeping Unit (SKU) device information HardwareRevisionSecret Gate Provisioned before tape out ROMExtSecurityDescriptor Register One of the following options: ŌĆó Hash of the ROM extension ŌĆó Software binding tag stored in the ROM_EXT manifest
- 19. Identity Flow ŌĆō ROM Extension Name Encoding Description SoftwareBinding Register Software binding value configured during secure boot. OwnerRootSecret Flash Provisioned at ownership transfer. Hidden from SW (ROM/ROM_EXT optional) IdentityDiversifactionConstant Gate Constant with acceptable entropy provisioned in gates
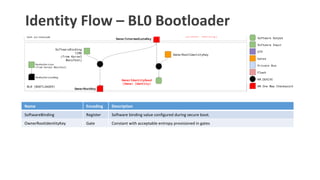
- 20. Identity Flow ŌĆō BL0 Bootloader Name Encoding Description SoftwareBinding Register Software binding value configured during secure boot. OwnerRootIdentityKey Gate Constant with acceptable entropy provisioned in gates
- 21. Identity Flow ŌĆō Kernel Name Encoding Description KeyVersion Register Key version which pass version comparison criteria during secure boot KeyID Register Key identifier SoftwareExportConstant Gate Constant with acceptable entropy provisioned in gates Salt Register Salt input controlled by SW ŌĆó VersionedKey ŌĆó Final output to wrap secret ŌĆó Isolation enforced by SW
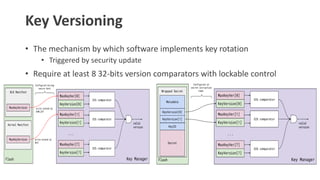
- 22. Key Versioning ŌĆó The mechanism by which software implements key rotation ŌĆó Triggered by security update ŌĆó Require at least 8 32-bits version comparators with lockable control
- 23. Device Attestation ŌĆó Provide signed evidence about the device state ŌĆó Is it secure booted? ŌĆó Is it debug enabled? ŌĆó Rooted in two asymmetric keys ŌĆó Creator Identity ŌĆó Owner Identity ŌĆó Two attestation mechanisms supported ŌĆó Creator Based Attestation ŌĆó Owned Device Attestation
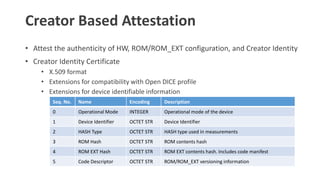
- 24. Creator Based Attestation ŌĆó Attest the authenticity of HW, ROM/ROM_EXT configuration, and Creator Identity ŌĆó Creator Identity Certificate ŌĆó X.509 format ŌĆó Extensions for compatibility with Open DICE profile ŌĆó Extensions for device identifiable information Seq. No. Name Encoding Description 0 Operational Mode INTEGER Operational mode of the device 1 Device Identifier OCTET STR Device Identifier 2 HASH Type OCTET STR HASH type used in measurements 3 ROM Hash OCTET STR ROM contents hash 4 ROM EXT Hash OCTET STR ROM EXT contents hash. Includes code manifest 5 Code Descriptor OCTET STR ROM/ROM_EXT versioning information
- 25. Owned Device Attestation ŌĆó Attest ownership of the device, BL0 configuration, and Owner Identity ŌĆó Owner Identity Certificate ŌĆó X.509 format ŌĆó Extensions for compatibility with Open DICE profile ŌĆó Extensions for BL0 information Seq. No. Name Encoding Description 0 Code Descriptor OCTET STR BL0 version and key manager software binding tag information
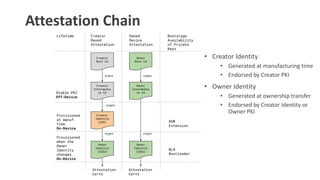
- 26. Attestation Chain ŌĆó Creator Identity ŌĆó Generated at manufacturing time ŌĆó Endorsed by Creator PKI ŌĆó Owner Identity ŌĆó Generated at ownership transfer ŌĆó Endorsed by Creator Identity or Owner PKI
- 27. Secure Boot Isolated Verify with Silicon Creator CA Public Key Verify with Silicon Owner CA Public Key
- 28. Boot Service Kernel ROM_EXT Scratch Reg Retention SRAM 1. Write BOOT_SERVICE_REQUEST 2. Enqueue boot_request structure 3. Trigger system reset 4. Check reset cause 5. Parse boot_request and serve Command Description Recall UNLOCK_OWNERSHIP Relinquish ownership of the device pg. 15 TRANSFER_OWNERSHIP Initiate processing of an ownership transfer blob pg. 15 REFRESH_ATTESTATION Causes the ROM_EXT to regenerate the attestation chain pg. 16 UPDATE_FIRMWARE Instructs the active ROM_EXT to begin the firmware update process
- 29. Discussion ŌĆó Can ROM_EXT stay alive after its boot stage ŌĆó No, ROM_EXT serves only at AC-on and reset with BOOT_SERVICE_REQUEST ŌĆó Difference between Creator/Owner CA keys and identity keys ŌĆó CA keys: used for identity keys endorsement and secure boot ŌĆó Identity keys: used only for attestation ŌĆó Key versioning use case ŌĆó No idea now
- 30. Thank You
- 31. Manufacturing State 1/3 Name Encoding Description RAW OTP This is the default state of the OTP. During this state, no functions other than transition to TEST_UNLOCKED0 are available. The token authorizing the transition from RAW to TEST_UNLOCKED0 is a value that is secret global to all devices. This is known as the RAW_UNLOCK token. TEST_LOCKED{N} OTP TEST_LOCKED{N} states have identical functionality to RAW state and serve as a way for the Silicon Creator to protect devices in transit. It is not possible to provision OTP root secrets during this state. This is enforced by hardware and is implementation defined. To progress from a TEST_LOCKED state to another TEST_UNLOCKED state, a TEST_UNLOCK token is required. TEST_UNLOCKED{N} OTP Transition from RAW state using OTP write. This state is used for manufacturing and production testing. During this state: ŌĆó CPU execution is enabled ŌĆó NVM backdoor functions are enabled ŌĆó Debug functions are enabled ŌĆó DFT functions are enabled Note: during this state it is not possible to provision specific OTP root secrets. This will be enforced by hardware. It is expected that during TEST_UNLOCKED0 the TEST_UNLOCK and TEST_EXIT tokens will be provisioned into OTP. Once provisioned, these tokens are no longer readable by software. Back Back
- 32. Manufacturing State 2/3 Name Encoding Description PROD OTP Transition from TEST_UNLOCKED state via OTP write. This is a mutually exclusive state to DEV and PROD_END. To enter this state, a TEST_EXIT token is required. This state is used both for provisioning and mission mode. During this state: ŌĆó CPU execution is enabled ŌĆó NVM backdoor functions are disabled ŌĆó Debug functions are disabled ŌĆó DFT functions are disabled PROD_END OTP This state is identical in functionality to PROD, except the device is never allowed to transition to RMA state. To enter this state, a TEST_EXIT token is required. DEV OTP Transition from TEST_UNLOCKED state via OTP write. This is a mutually exclusive state to PROD and PROD_END. To enter this state, a TEST_EXIT token is required. This state is used for developing provisioning and mission mode software. During this state ŌĆó CPU execution is enabled ŌĆó NVM backdoor functions are disabled ŌĆó Debug functions are enabled ŌĆó DFT functions are disabled Back Back
- 33. Manufacturing State 3/3 Name Encoding Description RMA OTP Transition from TEST_UNLOCKED / PROD / DEV via OTP write. It is not possible to reach this state from PROD_END. When transitioning from PROD or DEV, an RMA_UNLOCK token is required. When transitioning from TEST_UNLOCKED, no RMA_UNLOCK token is required. A hardware-backed mechanism will erase all owner flash content before RMA transition is allowed. This includes the isolation owner flash partitions as well as any owner code. Once erasure is confirmed and verified, RMA transition will proceed. During this state ŌĆó CPU execution is enabled ŌĆó NVM backdoor is enabled ŌĆó Debug functions are enabled ŌĆó DFT functions are enabled SCRAP OTP Transition from any manufacturing state via OTP write. During SCRAP state the device is completely dead. All functions, including CPU execution are disabled. No owner consent is required to transition to SCRAP. Note also, SCRAP is meant as an EOL manufacturing state. Transition to this state is always purposeful and persistent, it is NOT part of the deviceŌĆÖs native security countermeasure to transition to this state. INVALID OTP Invalid is any combination of OTP values that do not fall in the categories above. It is the ŌĆ£defaultŌĆØ state of life cycle when no other conditions match. Functionally, INVALID is identical to SCRAP in that no functions are allowed and no transitions are allowed. A user is not able to explicitly transition into INVALID (unlike SCRAP), instead, INVALID is meant to cover in-field corruptions, failures or active attacks. Back Back
- 34. Identity & Ownership State Name Encoding Description BLANK OTP Initial identity and ownership state. There is no hardware identity or ownership provisioned CREATOR PERSONALIZED OTP The hardware relevant information has been provisioned. This includes: ŌĆó RMA_UNLOCK Token ŌĆó Creator Root Key ŌĆó Creator Diversification Key Once the identity state advances to CREATOR_PERSONALIZED, creator provisioned secrets (see Identity flow) are no longer accessible to software and are directly consumed by hardware. UNLOCKED_OWNERSHIP Isolated Flash This state represents a device which contains a Creator Identity but does not yet have a Silicon Owner provisioned. Since this state is software managed, software is free to define a different state. LOCKED_OWNERSHIP Isolated Flash This state represents a device which contains both a Creator Identity and a Silicon Owner. A device in the LOCKED_OWNERSHIP state can transition back to UNLOCKED_OWNERSHIP when it is explicitly unbound. The unbinding process is described separately. Since this state is software managed, software is free to define a different state. EOL Isolated Flash This state represents a device that has reached its identity EOL. Since this state is software managed, software is free to define a different state. Back Back
- 35. Unlock Token Token Storage Device Unique? Usage RAW_UNLOCK RTL No From RAW->TEST_UNLOCKED0 TEST_UNLOCK OTP Silicon creator choice From TEST_LOCKED{N} to TEST_UNLOCKED{N} TEST_EXIT OTP Silicon creator choice From any TEST_UNLOCKED state to DEV, PROD_END or PROD RMA_UNLOCK OTP Yes From PROD/DEV to RMA Back Back