IS-IS Principles and Configurations.rpdf
- 1. Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. IS-IS Principles and Configurations
- 2. Page 1 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Foreword Ōܽ Intermediate System-to-Intermediate System (IS-IS) is a link-state based IGP. It uses the Shortest Path First (SPF) algorithm to calculate routes. IS-IS is a dynamic routing protocol initially designed by the International Organization for Standardization (ISO) for its Connectionless Network Protocol (CLNP). Ōܽ To support IP routing, the Internet Engineering Task Force (IETF) extends and modifies IS-IS in RFC 1195. This enables IS-IS to be applied to TCP/IP and OSI environments. This type of IS-IS is called Integrated IS-IS. IS-IS has been widely used in large ISP networks because of its simplicity and high scalability.
- 3. Page 2 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Objectives Ōܽ Upon completion of this section, you will be able to: ’ü░ Master IS-IS principles and configurations ’ü░ Be familiar with differences between IS-IS and OSPF
- 4. Page 3 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Contents 1. IS-IS Principles 2. Differences Between IS-IS and OSPF 3. IS-IS Configurations
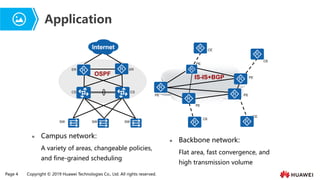
- 5. Page 4 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Ōܽ Backbone network: Flat area, fast convergence, and high transmission volume Ōܽ Campus network: A variety of areas, changeable policies, and fine-grained scheduling Application ER CS SW ER CS SW SW OSPF CE PE CE PE PE PE PE CE CE IS-IS+BGP
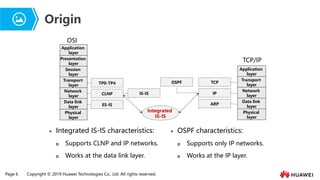
- 6. Page 6 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Origin Application layer Presentation layer Session layer Transport layer Network layer Data link layer Physical layer OSI Application layer Transport layer Network layer Data link layer Physical layer TCP/IP ARP TCP IP ES-IS TP0-TP4 CLNP IS-IS OSPF Integrated IS-IS Ōܽ Integrated IS-IS characteristics: ’ü░ Supports CLNP and IP networks. ’ü░ Works at the data link layer. Ōܽ OSPF characteristics: ’ü░ Supports only IP networks. ’ü░ Works at the IP layer.
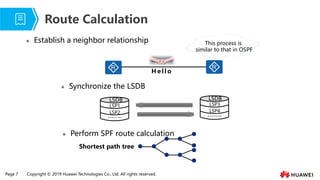
- 7. Page 7 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Ōܽ Establish a neighbor relationship Route Calculation Ōܽ Perform SPF route calculation Shortest path tree This process is similar to that in OSPF H e l l o Ōܽ Synchronize the LSDB LSDB LSP1 LSP2 ------- LSDB LSP3 LSP4 -------
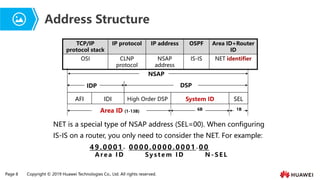
- 8. Page 8 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Address Structure High Order DSP System ID SEL IDI AFI Area ID (1-13B) 6B 1B NSAP IDP DSP 49.0 0 0 1 . 0000 . 0 0 0 0 . 0 0 0 1 . 0 0 A r e a I D Sy s t e m I D N - S E L NET is a special type of NSAP address (SEL=00). When configuring IS-IS on a router, you only need to consider the NET. For example: TCP/IP protocol stack IP protocol IP address OSPF Area ID+Router ID OSI CLNP protocol NSAP address IS-IS NET identifier
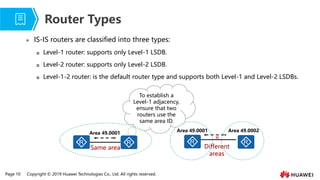
- 9. Page 10 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Ōܽ IS-IS routers are classified into three types: ’ü░ Level-1 router: supports only Level-1 LSDB. ’ü░ Level-2 router: supports only Level-2 LSDB. ’ü░ Level-1-2 router: is the default router type and supports both Level-1 and Level-2 LSDBs. Router Types To establish a Level-1 adjacency, ensure that two routers use the same area ID. Same area Area 49.0001 Different areas Area 49.0001 Area 49.0002 ├Ś
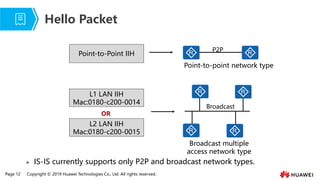
- 10. Page 12 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Ōܽ IS-IS currently supports only P2P and broadcast network types. Hello Packet Broadcast multiple access network type P2P Broadcast Point-to-Point IIH L1 LAN IIH Mac:0180-c200-0014 L2 LAN IIH Mac:0180-c200-0015 OR Point-to-point network type
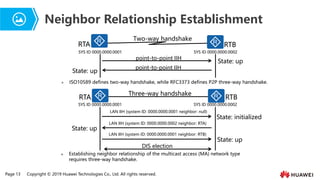
- 11. Page 13 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Neighbor Relationship Establishment Ōܽ ISO10589 defines two-way handshake, while RFC3373 defines P2P three-way handshake. point-to-point IIH RTA RTB SYS ID 0000.0000.0001 SYS ID 0000.0000.0002 point-to-point IIH State: up State: up Two-way handshake Ōܽ Establishing neighbor relationship of the multicast access (MA) network type requires three-way handshake. RTA RTB SYS ID 0000.0000.0001 SYS ID 0000.0000.0002 LAN IIH (system ID: 0000.0000.0001 neighbor: null) LAN IIH (system ID: 0000.0000.0002 neighbor: RTA) LAN IIH (system ID: 0000.0000.0001 neighbor: RTB) State: initialized State: up State: up Three-way handshake DIS election
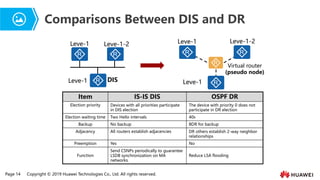
- 12. Page 14 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Comparisons Between DIS and DR Virtual router (pseudo node) Leve-1 Leve-1 Leve-1-2 DIS Item IS-IS DIS OSPF DR Election priority Devices with all priorities participate in DIS election The device with priority 0 does not participate in DR election Election waiting time Two Hello intervals 40s Backup No backup BDR for backup Adjacency All routers establish adjacencies DR others establish 2-way neighbor relationships Preemption Yes No Function Send CSNPs periodically to guarantee LSDB synchronization on MA networks. Reduce LSA flooding Leve-1 Leve-1-2 Leve-1
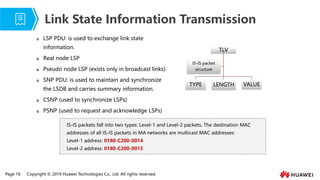
- 13. Page 16 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. TLV TYPE LENGTH VALUE IS-IS packet structure ’ü░ LSP PDU: is used to exchange link state information. ’ü░ Real node LSP ’ü░ Pseudo node LSP (exists only in broadcast links) ’ü░ SNP PDU: is used to maintain and synchronize the LSDB and carries summary information. ’ü░ CSNP (used to synchronize LSPs) ’ü░ PSNP (used to request and acknowledge LSPs) Link State Information Transmission IS-IS packets fall into two types: Level-1 and Level-2 packets. The destination MAC addresses of all IS-IS packets in MA networks are multicast MAC addresses: Level-1 address: 0180-C200-0014 Level-2 address: 0180-C200-0015
- 14. Page 18 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Link State Information Exchange CSNP A.00-00 ŌæĀ PSNP A.00-00 ŌæĪ LSP A.00-00 Ōæó ’ā╗ PSNP A.00-00 ŌæŻ Retransmission expires LSP A.00-00 Ōæż PSNP A.00-00 Retransmit PSNP Ōæź Ōܽ CSNPs are sent only once on a P2P network. That is, a CSNP is sent immediately after a neighbor relationship is established. Ōæó PSNP A.00-00 B.00-00 B.01-00 LSP C.00-00 C.00-01 ŌæĀ CSNP A.00-00 B.00-00 B.01-00 C.00-00 C.00-01 ŌæĪ LSP A.00-00 B.00-00 B.01-00 ŌæŻ Ōܽ CSNPs are multicast only by the DIS on an MA network at the default interval of 10s. Pseudo node LSP Fragment LSP RTA RTB P2P RTA RTC RTB DIS MA
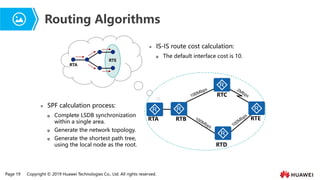
- 15. Page 19 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Routing Algorithms RTA RTE RTA RTB RTC RTD RTE Ōܽ IS-IS route cost calculation: ’ü░ The default interface cost is 10. Ōܽ SPF calculation process: ’ü░ Complete LSDB synchronization within a single area. ’ü░ Generate the network topology. ’ü░ Generate the shortest path tree, using the local node as the root.
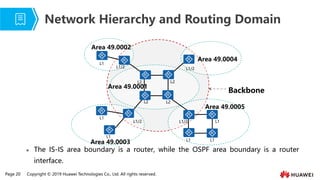
- 16. Page 20 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Ōܽ The IS-IS area boundary is a router, while the OSPF area boundary is a router interface. Network Hierarchy and Routing Domain L2 L2 L2 L1/2 L2 L1/2 L1 L1/2 L1 L1 L1 L1/2 L1 L1 Area 49.0001 Area 49.0002 Area 49.0003 Area 49.0004 Area 49.0005 Backbone
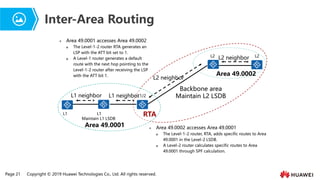
- 17. Page 21 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. L1 L1 Maintain L1 LSDB L1/2 L1 neighbor Area 49.0001 L1 neighbor Backbone area Maintain L2 LSDB L2 Area 49.0002 L2 neighbor L2 neighbor L2 Ōܽ Area 49.0001 accesses Area 49.0002 ’ü░ The Level-1-2 router RTA generates an LSP with the ATT bit set to 1. ’ü░ A Level-1 router generates a default route with the next hop pointing to the Level-1-2 router after receiving the LSP with the ATT bit 1. Ōܽ Area 49.0002 accesses Area 49.0001 ’ü░ The Level-1-2 router, RTA, adds specific routes to Area 49.0001 in the Level-2 LSDB. ’ü░ A Level-2 router calculates specific routes to Area 49.0001 through SPF calculation. RTA Inter-Area Routing
- 18. Page 22 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Contents 1. IS-IS Principles 2. Differences Between IS-IS and OSPF 3. IS-IS Configurations
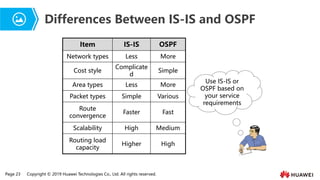
- 19. Page 23 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Differences Between IS-IS and OSPF Use IS-IS or OSPF based on your service requirements Item IS-IS OSPF Network types Less More Cost style Complicate d Simple Area types Less More Packet types Simple Various Route convergence Faster Fast Scalability High Medium Routing load capacity Higher High
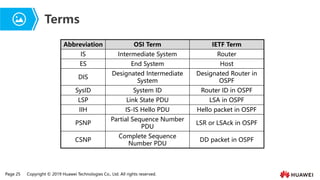
- 20. Page 25 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Terms Abbreviation OSI Term IETF Term IS Intermediate System Router ES End System Host DIS Designated Intermediate System Designated Router in OSPF SysID System ID Router ID in OSPF LSP Link State PDU LSA in OSPF IIH IS-IS Hello PDU Hello packet in OSPF PSNP Partial Sequence Number PDU LSR or LSAck in OSPF CSNP Complete Sequence Number PDU DD packet in OSPF
- 21. Page 26 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Contents 1. IS-IS Principles 2. Differences Between IS-IS and OSPF 3. IS-IS Configurations
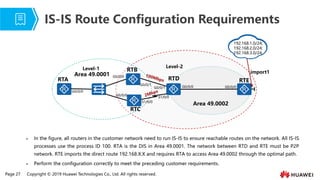
- 22. Page 27 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Ōܽ In the figure, all routers in the customer network need to run IS-IS to ensure reachable routes on the network. All IS-IS processes use the process ID 100. RTA is the DIS in Area 49.0001. The network between RTD and RTE must be P2P network. RTE imports the direct route 192.168.X.X and requires RTA to access Area 49.0002 through the optimal path. Ōܽ Perform the configuration correctly to meet the preceding customer requirements. IS-IS Route Configuration Requirements import1 RTB RTC RTD Area 49.0001 Area 49.0002 Level-1 Level-2 RTA 192.168.1.0/24; 192.168.2.0/24; 192.168.3.0/24; G0/0/0 G0/0/0 G0/0/1 G0/0/1 G0/0/0 G0/0/0 G0/0/0 S1/0/0 S1/0/0 RTE
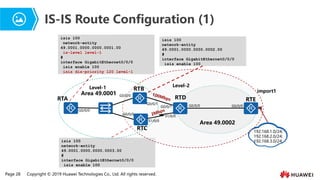
- 23. Page 28 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. IS-IS Route Configuration (1) isis 100 network-entity 49.0001.0000.0000.0001.00 is-level level-1 # interface GigabitEthernet0/0/0 isis enable 100 isis dis-priority 120 level-1 isis 100 network-entity 49.0001.0000.0000.0002.00 # interface GigabitEthernet0/0/0 isis enable 100 isis 100 network-entity 49.0001.0000.0000.0003.00 # interface GigabitEthernet0/0/0 isis enable 100 import1 RTB RTC RTD Area 49.0001 Area 49.0002 Level-1 Level-2 RTA 192.168.1.0/24; 192.168.2.0/24; 192.168.3.0/24; G0/0/0 G0/0/0 G0/0/1 G0/0/1 G0/0/0 G0/0/0 G0/0/0 S1/0/0 S1/0/0 RTE
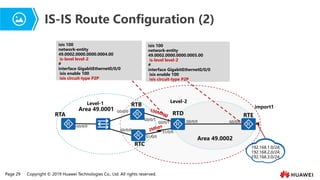
- 24. Page 29 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. IS-IS Route Configuration (2) import1 RTB RTC RTD Area 49.0001 Area 49.0002 Level-1 Level-2 RTA 192.168.1.0/24; 192.168.2.0/24; 192.168.3.0/24; G0/0/0 G0/0/0 G0/0/1 G0/0/1 G0/0/0 G0/0/0 G0/0/0 S1/0/0 S1/0/0 RTE isis 100 network-entity 49.0002.0000.0000.0005.00 is-level level-2 # interface GigabitEthernet0/0/0 isis enable 100 isis circuit-type P2P isis 100 network-entity 49.0002.0000.0000.0004.00 is-level level-2 # interface GigabitEthernet0/0/0 isis enable 100 isis circuit-type P2P
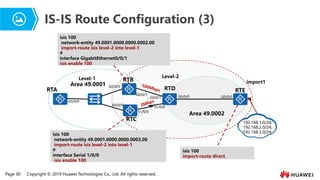
- 25. Page 30 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. IS-IS Route Configuration (3) import1 RTB RTC RTD Area 49.0001 Area 49.0002 Level-1 Level-2 RTA 192.168.1.0/24; 192.168.2.0/24; 192.168.3.0/24; G0/0/0 G0/0/0 G0/0/1 G0/0/1 G0/0/0 G0/0/0 G0/0/0 S1/0/0 S1/0/0 RTE isis 100 network-entity 49.0001.0000.0000.0002.00 import-route isis level-2 into level-1 # interface GigabitEthernet0/0/1 isis enable 100 isis 100 network-entity 49.0001.0000.0000.0003.00 import-route isis level-2 into level-1 # interface Serial 1/0/0 isis enable 100 isis 100 import-route direct
- 26. Page 31 Copyright ┬® 2019 Huawei Technologies Co., Ltd. All rights reserved. Quiz 1. How many IS-IS router types exist? 2. What is the function of PSNPs in neighbor interaction? 3. What are the advantages of IS-IS compared with OSPF?