Application Security Risk Rating
Download as PPTX, PDF2 likes2,466 views
The document discusses two problems related to application security risk rating: 1) limited resources to test a large number of applications, and 2) assigning risk levels to vulnerabilities found during manual assessments. For the first problem, the document proposes prioritizing applications by categorizing them into high, medium, and low risk based on a risk assessment analyzing business criticality and risk posture. For the second problem, the document outlines the OWASP risk rating methodology in six steps: identifying risks, estimating likelihood, estimating impact, determining severity, deciding what to fix, and customizing the risk rating model.
1 of 23
Downloaded 59 times




















Recommended
Pasta Threat Modeling



Pasta Threat ModelingEC-Council
?
PASTA allows organizations to understand an attackerĪ»s perspective on applications and infrastructure, thus developing threat management processes and policies. LetĪ»s learn more about PASTA threat modeling in this slideshare. To know more about threat modeling, click here: https://www.eccouncil.org/threat-modeling/ OWASP: Building Secure Web Apps



OWASP: Building Secure Web Appsmlogvinov
?
OWASP Bay Area Application Security Summit: Building Secure Web Applications in a Cloud Services EnvironmentDigital transformation continues to drive IT strategy, How is QA and testing ...



Digital transformation continues to drive IT strategy, How is QA and testing ...QA or the Highway
?
The 2016-2017 World Quality Report examines quality and testing across multiple industries and 33 countries for the eighth time. It addresses topics like digital transformation, IoT and security, Agile and DevOps, test environments, budgets, and provides recommendations. The report is produced by Capgemini, Sogeti, and HPE and is based on interviews with organizations worldwide.A quick guide to application security testing services



A quick guide to application security testing servicesAlisha Henderson
?
Application security testing of web applications should be included in the software development life-cycle (SDLC) with the standard QA testing. https://bit.ly/2Y4aDccThreat Simulation and Modeling Training



Threat Simulation and Modeling TrainingBryan Len
?
The document describes a 2-day threat simulation and modeling training course offered by Tonex for $1,699. The training covers topics such as the Process for Attack Simulation and Threat Analysis (PASTA), Common Attack Pattern Enumeration and Classification (CAPEC), and using threat modeling within the Software Development Life Cycle (SDLC). Attendees will learn how to identify threats, analyze vulnerabilities, simulate attacks, and manage residual risks. The course includes lectures, workshops, labs, and case studies.Web-based Security Analysis Tool for Android Applications



Web-based Security Analysis Tool for Android ApplicationsTandhy Simanjuntak
?
a web-based security analysis tool for android applications poster session at Advanced Cyber Security Center Annual Conference 2014, Boston, Nov 5th, 2014.How ThreatModeler Benefits Key Stakeholders



How ThreatModeler Benefits Key Stakeholdersreeftim
?
ThreatModeler allows key stakeholders to improve application security. Executives can ensure policy compliance and reduce risk. Directors can adopt scalable threat modeling and validate controls. Security teams can leverage automated modeling to assess controls and prioritize testing. Project managers can identify defects and enforce requirements. Developers can code securely and consistently through predefined controls.Cyber Threat Modeling



Cyber Threat ModelingEC-Council
?
Do you know what the steps of threat modeling and various models are? Take a look at these slides to learn.
To learn more about threat modeling, visit https://www.eccouncil.org/threat-modeling/ OAuth 2.0 & Security Considerations



OAuth 2.0 & Security ConsiderationsVaibhav Gupta
?
I gave this talk at OWASP/Null Delhi chapter meet. The session was around the OAuth 2.0 workflow and few security considerations that developers or security analyst needs to take care.
Meet details: https://null.co.in/events/210-delhi-null-delhi-meet-30-july-2016-null-owasp-combined-meetModel-Based Systems Engineering Tool How To Use Innoslate Pt. 2



Model-Based Systems Engineering Tool How To Use Innoslate Pt. 2Elizabeth Steiner
?
Daniel Hettema will show you the ins and outs of Innoslate and discuss in-depth systems engineering concepts. You will learn how to customize schema extensions to make Innoslate even more relevant to your organization. He will discuss and demonstrate best practices for the Monte Carlo Simulator and the Discrete Event Simulator. Minimizing Business Risk in IT Projects



Minimizing Business Risk in IT ProjectsITPSB Pty Ltd
?
Corporate profiling is a process that provides an in-depth blueprint of an organization's structure, technology, people, processes, and relationships with customers. It promotes visibility, collaboration, and accountability to improve decision making for IT projects. The document discusses how corporate profiling involves unbundling an organization into different layers and profiling core processes, the pre-implementation process, and external value chains to understand factors driving new IT investments.Reducing Application Risk: minimizing your web application's attack surface



Reducing Application Risk: minimizing your web application's attack surfaceSecurity Innovation
?
This webcast (now in PPT. format) demonstrates techniques to identify, reduce, and measure your applicationĪ»s attack surface.Simulazione di un Penetration Test



Simulazione di un Penetration TestSalvatore Lentini
?
In questo seminario ho simulato un Penetration Test completo partendo dalla fase di raccolta delle informazioni fino ad arrivare alla fase in cui l'attaccante penetra nel sistema e installa una backdoor per rafforzare la propria presenza nel sistema violato.
Durante ogni singola fase mi sono fermato a parlare di essa portando esempi sia teorici che demo pratiche.
Questo seminario nasce con lo scopo di appassionare i ragazzi e soprattutto far conoscere ad essi il mondo della sicurezza informatica rivolta ai test di penetrazione. Questo seminario nasce dall'invito che ho ricevuto da parte dell'istituto G.B. Vaccarini, essendo io stesso, un loro ex studente.Gilda's Club 2011 "Live! From South Florida...It's Saturday Night!" Virtual ...



Gilda's Club 2011 "Live! From South Florida...It's Saturday Night!" Virtual ...Gilda's Club South Florida
?
This document provides information about the 16th Annual event for Gilda's Club South Florida including the mission statement, event details, sponsors, committee members, and more. The event will feature a national touring comic, Dean Napolitano, and be emceed by Drew Sattee. Gilda's Club South Florida thanks their many sponsors, volunteers, and partners who helped make the event possible.Beyondfreud



BeyondfreudTajana Klaric
?
This document provides an introduction to a book titled "Beyond Freud: A Study of Modern Psychoanalytic Theorists" edited by Joseph Reppen. The book contains chapters written by various authors on 14 modern psychoanalytic theorists who have expanded upon Freud's work. While the theorists presented have differing views and approaches, they are all informed by Freud's original ideas and continue to influence the field. The introduction provides background on the book's purpose and discusses some of the theorists that were not included. It aims to demonstrate how Freud's thinking has been built upon rather than disparage his work.Spark - Volume 3



Spark - Volume 3S.P. Jain center of Management
?
Spark is the student magazine from S.P.Jain Center of Management, Dubai / Singapore. This is third volume of the magazine.

GPP Final Draft for Scott Wells



GPP Final Draft for Scott WellsScott Wells
?
This document is Scott Wells' graduate project analyzing his process of preparing for and performing the role of Sheridan Whiteside in a 2013 production of The Man Who Came to Dinner at Florida Atlantic University. Wells identified early problems with overacting the caricatured role. Through research on the playwrights' vision and the "clown-farce" style, Wells worked to find emotional depth behind the sarcasm and develop Whiteside as a boor with a heart of gold.47035 0 mma



47035 0 mmaOperator Warnet Vast Raha
?
This document provides information about the Spring 2010 issue of the Marketing Management Journal, including the editors, production editor, publications council, and editorial review board. It also includes an index of article titles and authors in the issue. The high level information is that this document outlines the leadership and contents of the Spring 2010 issue of the Marketing Management Journal.Mercenaries Unleashed, 2016



Mercenaries Unleashed, 2016Russel Harland
?
This document discusses the growth of the private military and security company (PMSC) industry, with a focus on British companies. It notes that the UK is a major hub for PMSCs, with hundreds operating globally. Many British PMSCs are large corporations dominated by former military personnel. Iraq was a major incubator for the industry following the 2003 invasion, and British PMSCs continue to operate there providing security for governments and oil companies. The industry is also expanding into Africa to meet demand from extractive companies seeking security in unstable regions.Pre Internship Vaibhav Gupta Samtel



Pre Internship Vaibhav Gupta SamtelVaibhav Gupta
?
this is the pre internship project proposal that VAIBHAV GUPTA would be carrying out at Samtel delhi in may 2010.Master version draft final



Master version draft finalirbgcpartners
?
BGC Partners held an Investor & Analyst Day on May 29, 2014 to provide an overview and updates on the company. The presentation included:
- BGC has two business segments: Financial Services and Real Estate Services (Newmark Grubb Knight Frank)
- Financial Services revenues account for 62% of total revenues while Real Estate Services accounts for 36%
- BGC has a long track record of revenue growth and acquiring companies to expand its services
- Continuity of experienced executive and business management teamsForeign Educational Institutions In India Vaibhav Gupta



Foreign Educational Institutions In India Vaibhav GuptaVaibhav Gupta
?
THIS ARTICLE GIVES AN INITIAL GO TO MARKET STRATEGY FOR FOREIGN EDUCATION PROVIDERS WILLING TO START OPEARTIONS IN INDIA.Career Profile - Anshuman Jain



Career Profile - Anshuman JainAnshuman Jain
?
Anshuman Jain has over 8 years of experience in various roles including business development, project management, and administration. He is currently an executive at Syncom Formulations (India) Limited where he provides assistance to the CEO and handles various administrative tasks. The document outlines his professional experience, skills, education, and contact information while seeking new managerial opportunities.13 0716 session 1 & 2 webinars-final



13 0716 session 1 & 2 webinars-finalCleantechOpen
?
This document outlines an agenda for a webinar hosted by Cleantech Open on July 16, 2013 focusing on product/market fit and customer validation. The webinar will include a discussion of value creation through innovation, identifying customer segments for cleantech enterprises, defining value propositions, and conducting customer validation. It provides an overview of worksheets and judging criteria related to customer discovery, product/market fit, and interviewing customers in identified segments to validate value propositions.Publication listing



Publication listingKevin D. Brown, Ph.D.
?
This document provides a publication list for Dr. Kevin D. Brown including 36 peer-reviewed publications from 1990 to 2008. The publications focus on characterizing cytoskeletal proteins, identifying their roles in cell cycle regulation and DNA damage response pathways, and investigating epigenetic silencing of tumor suppressor genes in cancer development.Spartacus and the slave war



Spartacus and the slave wartastamal
?
The document provides background information on the slave revolt led by Spartacus from 73-71 BC in Rome. It discusses how Spartacus has become a symbol of rebellion against oppression. The passage then gives a brief overview of the origins and causes of the slave revolts in Rome in 135-132 BC and 104-100 BC that preceded Spartacus' revolt.Lessons from DevOps: Taking DevOps practices into your AppSec Life



Lessons from DevOps: Taking DevOps practices into your AppSec LifeMatt Tesauro
?
Bruce Lee once said Ī░DonĪ»t get set into one form, adapt it and build your own, and let it grow, be like waterĪ░.
AppSec needs to look beyond itself for answers to solving problems since we live in a world of every increasing numbers of apps. Technology and apps have invaded our lives, so how to you lead a security counter-insurgency? One way is to look at the key tenants of DevOps and apply those that make sense to your approach to AppSec. Something has to change as the application landscape is already changing around us.When to Implement a Vulnerability Assessment or Pen Test | IT Security & Risk...



When to Implement a Vulnerability Assessment or Pen Test | IT Security & Risk...Cam Fulton
?
Learn how to evaluate risk, what the differences are between vulnerability assessments and penetration tests, and when to implement both.
Presented by AWA International, a division of I.S. Partners, LLC https://www.ispartnersllc.com/awa-international-group/ Web Application Security Vulnerability Management Framework



Web Application Security Vulnerability Management Frameworkjpubal
?
Web Application Security Vulnerability Management Framework for building an application security programMore Related Content
Viewers also liked (20)
OAuth 2.0 & Security Considerations



OAuth 2.0 & Security ConsiderationsVaibhav Gupta
?
I gave this talk at OWASP/Null Delhi chapter meet. The session was around the OAuth 2.0 workflow and few security considerations that developers or security analyst needs to take care.
Meet details: https://null.co.in/events/210-delhi-null-delhi-meet-30-july-2016-null-owasp-combined-meetModel-Based Systems Engineering Tool How To Use Innoslate Pt. 2



Model-Based Systems Engineering Tool How To Use Innoslate Pt. 2Elizabeth Steiner
?
Daniel Hettema will show you the ins and outs of Innoslate and discuss in-depth systems engineering concepts. You will learn how to customize schema extensions to make Innoslate even more relevant to your organization. He will discuss and demonstrate best practices for the Monte Carlo Simulator and the Discrete Event Simulator. Minimizing Business Risk in IT Projects



Minimizing Business Risk in IT ProjectsITPSB Pty Ltd
?
Corporate profiling is a process that provides an in-depth blueprint of an organization's structure, technology, people, processes, and relationships with customers. It promotes visibility, collaboration, and accountability to improve decision making for IT projects. The document discusses how corporate profiling involves unbundling an organization into different layers and profiling core processes, the pre-implementation process, and external value chains to understand factors driving new IT investments.Reducing Application Risk: minimizing your web application's attack surface



Reducing Application Risk: minimizing your web application's attack surfaceSecurity Innovation
?
This webcast (now in PPT. format) demonstrates techniques to identify, reduce, and measure your applicationĪ»s attack surface.Simulazione di un Penetration Test



Simulazione di un Penetration TestSalvatore Lentini
?
In questo seminario ho simulato un Penetration Test completo partendo dalla fase di raccolta delle informazioni fino ad arrivare alla fase in cui l'attaccante penetra nel sistema e installa una backdoor per rafforzare la propria presenza nel sistema violato.
Durante ogni singola fase mi sono fermato a parlare di essa portando esempi sia teorici che demo pratiche.
Questo seminario nasce con lo scopo di appassionare i ragazzi e soprattutto far conoscere ad essi il mondo della sicurezza informatica rivolta ai test di penetrazione. Questo seminario nasce dall'invito che ho ricevuto da parte dell'istituto G.B. Vaccarini, essendo io stesso, un loro ex studente.Gilda's Club 2011 "Live! From South Florida...It's Saturday Night!" Virtual ...



Gilda's Club 2011 "Live! From South Florida...It's Saturday Night!" Virtual ...Gilda's Club South Florida
?
This document provides information about the 16th Annual event for Gilda's Club South Florida including the mission statement, event details, sponsors, committee members, and more. The event will feature a national touring comic, Dean Napolitano, and be emceed by Drew Sattee. Gilda's Club South Florida thanks their many sponsors, volunteers, and partners who helped make the event possible.Beyondfreud



BeyondfreudTajana Klaric
?
This document provides an introduction to a book titled "Beyond Freud: A Study of Modern Psychoanalytic Theorists" edited by Joseph Reppen. The book contains chapters written by various authors on 14 modern psychoanalytic theorists who have expanded upon Freud's work. While the theorists presented have differing views and approaches, they are all informed by Freud's original ideas and continue to influence the field. The introduction provides background on the book's purpose and discusses some of the theorists that were not included. It aims to demonstrate how Freud's thinking has been built upon rather than disparage his work.Spark - Volume 3



Spark - Volume 3S.P. Jain center of Management
?
Spark is the student magazine from S.P.Jain Center of Management, Dubai / Singapore. This is third volume of the magazine.

GPP Final Draft for Scott Wells



GPP Final Draft for Scott WellsScott Wells
?
This document is Scott Wells' graduate project analyzing his process of preparing for and performing the role of Sheridan Whiteside in a 2013 production of The Man Who Came to Dinner at Florida Atlantic University. Wells identified early problems with overacting the caricatured role. Through research on the playwrights' vision and the "clown-farce" style, Wells worked to find emotional depth behind the sarcasm and develop Whiteside as a boor with a heart of gold.47035 0 mma



47035 0 mmaOperator Warnet Vast Raha
?
This document provides information about the Spring 2010 issue of the Marketing Management Journal, including the editors, production editor, publications council, and editorial review board. It also includes an index of article titles and authors in the issue. The high level information is that this document outlines the leadership and contents of the Spring 2010 issue of the Marketing Management Journal.Mercenaries Unleashed, 2016



Mercenaries Unleashed, 2016Russel Harland
?
This document discusses the growth of the private military and security company (PMSC) industry, with a focus on British companies. It notes that the UK is a major hub for PMSCs, with hundreds operating globally. Many British PMSCs are large corporations dominated by former military personnel. Iraq was a major incubator for the industry following the 2003 invasion, and British PMSCs continue to operate there providing security for governments and oil companies. The industry is also expanding into Africa to meet demand from extractive companies seeking security in unstable regions.Pre Internship Vaibhav Gupta Samtel



Pre Internship Vaibhav Gupta SamtelVaibhav Gupta
?
this is the pre internship project proposal that VAIBHAV GUPTA would be carrying out at Samtel delhi in may 2010.Master version draft final



Master version draft finalirbgcpartners
?
BGC Partners held an Investor & Analyst Day on May 29, 2014 to provide an overview and updates on the company. The presentation included:
- BGC has two business segments: Financial Services and Real Estate Services (Newmark Grubb Knight Frank)
- Financial Services revenues account for 62% of total revenues while Real Estate Services accounts for 36%
- BGC has a long track record of revenue growth and acquiring companies to expand its services
- Continuity of experienced executive and business management teamsForeign Educational Institutions In India Vaibhav Gupta



Foreign Educational Institutions In India Vaibhav GuptaVaibhav Gupta
?
THIS ARTICLE GIVES AN INITIAL GO TO MARKET STRATEGY FOR FOREIGN EDUCATION PROVIDERS WILLING TO START OPEARTIONS IN INDIA.Career Profile - Anshuman Jain



Career Profile - Anshuman JainAnshuman Jain
?
Anshuman Jain has over 8 years of experience in various roles including business development, project management, and administration. He is currently an executive at Syncom Formulations (India) Limited where he provides assistance to the CEO and handles various administrative tasks. The document outlines his professional experience, skills, education, and contact information while seeking new managerial opportunities.13 0716 session 1 & 2 webinars-final



13 0716 session 1 & 2 webinars-finalCleantechOpen
?
This document outlines an agenda for a webinar hosted by Cleantech Open on July 16, 2013 focusing on product/market fit and customer validation. The webinar will include a discussion of value creation through innovation, identifying customer segments for cleantech enterprises, defining value propositions, and conducting customer validation. It provides an overview of worksheets and judging criteria related to customer discovery, product/market fit, and interviewing customers in identified segments to validate value propositions.Publication listing



Publication listingKevin D. Brown, Ph.D.
?
This document provides a publication list for Dr. Kevin D. Brown including 36 peer-reviewed publications from 1990 to 2008. The publications focus on characterizing cytoskeletal proteins, identifying their roles in cell cycle regulation and DNA damage response pathways, and investigating epigenetic silencing of tumor suppressor genes in cancer development.Spartacus and the slave war



Spartacus and the slave wartastamal
?
The document provides background information on the slave revolt led by Spartacus from 73-71 BC in Rome. It discusses how Spartacus has become a symbol of rebellion against oppression. The passage then gives a brief overview of the origins and causes of the slave revolts in Rome in 135-132 BC and 104-100 BC that preceded Spartacus' revolt.Lessons from DevOps: Taking DevOps practices into your AppSec Life



Lessons from DevOps: Taking DevOps practices into your AppSec LifeMatt Tesauro
?
Bruce Lee once said Ī░DonĪ»t get set into one form, adapt it and build your own, and let it grow, be like waterĪ░.
AppSec needs to look beyond itself for answers to solving problems since we live in a world of every increasing numbers of apps. Technology and apps have invaded our lives, so how to you lead a security counter-insurgency? One way is to look at the key tenants of DevOps and apply those that make sense to your approach to AppSec. Something has to change as the application landscape is already changing around us.Gilda's Club 2011 "Live! From South Florida...It's Saturday Night!" Virtual ...



Gilda's Club 2011 "Live! From South Florida...It's Saturday Night!" Virtual ...Gilda's Club South Florida
?


Similar to Application Security Risk Rating (20)
When to Implement a Vulnerability Assessment or Pen Test | IT Security & Risk...



When to Implement a Vulnerability Assessment or Pen Test | IT Security & Risk...Cam Fulton
?
Learn how to evaluate risk, what the differences are between vulnerability assessments and penetration tests, and when to implement both.
Presented by AWA International, a division of I.S. Partners, LLC https://www.ispartnersllc.com/awa-international-group/ Web Application Security Vulnerability Management Framework



Web Application Security Vulnerability Management Frameworkjpubal
?
Web Application Security Vulnerability Management Framework for building an application security programBest Practices and ROI for Risk-based Vulnerability Management



Best Practices and ROI for Risk-based Vulnerability ManagementResolver Inc.
?
This document discusses best practices for risk-based vulnerability management. It begins with an introduction and agenda. It then covers common vulnerability management challenges such as debate over metrics, prioritizing remediation, and lack of governance. Recommendations for improving vulnerability management programs are provided, including implementing strong governance, classifying assets, enriching vulnerability data with threat and exploit data, calculating risk scores, automating processes, and reporting. A case study is presented on the return on investment of automation. The document concludes with introductions to the RiskVision vulnerability management solution and representatives.Outpost24 Webinar - Creating a sustainable application security program to dr...



Outpost24 Webinar - Creating a sustainable application security program to dr...Outpost24
?
In our next webinar, Simon Roe Product Manager at Outpost24 will discuss how you can create greater and more robust visibility of security within the application development lifecycle.Ownux global July 2023.pdf



Ownux global July 2023.pdfBella Nirvana Center
?
Ownux is an Information Security Consultation firm specializing in the field of Penetration Testing of every channel which classifies different security areas of interest within an organization. We are focused on Application Security, however, it is not limited to physical cyber security, reviewing the configurations of applications and security appliances. We have much more to offer.Iso 27001 2013 clause 6 - planning - by Software development company in india



Iso 27001 2013 clause 6 - planning - by Software development company in indiaiFour Consultancy
?
This video focuses on the management clauses of ISO 27001:2013 standards. The management clause 6 of ISMS framework relates to 'Planning'.
The 'General' and 'Risk Assessment' sections are explained in this presentation.- by Software development company in india
Ref:
http://www.ifour-consultancy.com
http://www.ifourtechnolab.com
** Custom software development companiesOWASP Risk Rating Methodology.pptx



OWASP Risk Rating Methodology.pptxChandan Singh Ghodela
?
Explain in Hindi: https://www.youtube.com/watch?v=6xqkDB3NHN0
Discovering vulnerabilities is important, but being able to estimate the associated risk to the business is just as important. Early in the life cycle, one may identify security concerns in the architecture or design by using threat modeling. Later, one may find security issues using code review or penetration testing. Or problems may not be discovered until the application is in production and is actually compromised.
Reference: https://owasp.org/www-community/OWASP_Risk_Rating_Methodology
https://www.owasp-risk-rating.com/Web Application Vulnerability Management



Web Application Vulnerability Managementjpubal
?
This document discusses building a web application vulnerability management program. It covers preparing by defining policies, inventorying applications, and choosing scanning tools. The core vulnerability management process involves enrolling applications, conducting dynamic application security testing, reporting vulnerabilities, and tracking remediation. It stresses the importance of defining metrics to measure the program's effectiveness over time. It also provides tips for conducting the process cost-effectively using open source and free tools.325838924-Splunk-Use-Case-Framework-Introduction-Session



325838924-Splunk-Use-Case-Framework-Introduction-SessionRyan Faircloth
?
This document provides an outline for developing security use cases and operationalizing them. It discusses motivators for developing use cases like compliance, visibility, and threat response. A framework is presented that involves problem scoping, data and event identification, and risk analysis. Goals should be set in a way that is measurable and accountable. Examples of use cases for malware detection and response are given at different levels from essential to mature. The document emphasizes goal setting, prioritization, and ensuring use cases demonstrate progress. It also provides guidance on working with Splunk experts to implement this approach through workshops and assessments.A Framework for Developing and Operationalizing Security Use Cases



A Framework for Developing and Operationalizing Security Use CasesRyan Faircloth
?
Build consensus, direction and enterprise mandate through strong use cases for your enterprise security team.What the New OWASP Top 10 2013 and Latest X-Force Report Mean for App Sec



What the New OWASP Top 10 2013 and Latest X-Force Report Mean for App SecIBM Security
?
Despite being on vulnerability Ī░Top 10Ī▒ lists for many years, application vulnerabilities such as SQL injection and Cross-Site scripting continue to be significant attack paradigms for organizational data breaches. In fact, the IBM X-Force 2013 Mid-Year Trend and Risk Report confirmed that SQL Injection (SQLi) remained the most common paradigm for attackers to breach organizational security controls. Meanwhile, Cross-Site Scripting continued to be the most common type of application vulnerability.
In this session, we review the latest trends in application and mobile security vulnerabilities, and how to combat them with improved security awareness, organizational controls and application security testing technologies. We also address how to improve application security on your organizationĪ»s mobile devices. The Four(ish) Appsec Metrics You CanĪ»t Ignore



The Four(ish) Appsec Metrics You CanĪ»t IgnoreVeracode
?
Which metrics should we use? You might expect an Ī░it dependsĪ▒ answer, but there are some metrics that are important for any application security program, regardless of audience or goals. WeĪ»ll take a look at a few of them in this post.Software Security Metrics



Software Security MetricsCigital
?
More often than not, company executives ask the wrong questions about software security. ?This session will discuss techniques for changing the conversation about software security in order to encourage executives to ask the right questions ©C and provide answers that show progress towards meaningful objectives. ?Caroline will discuss a progression of software security capabilities and the metrics that correspond to different levels of maturity. ?SheĪ»ll discuss an approach for developing key metrics for your unique software security program and walk through a detailed example.
project_risk_mgmt_final.ppt



project_risk_mgmt_final.pptAyidAlmgati
?
This document provides an overview of project risk management. It discusses the goals of risk management, including identifying and planning for risks to help projects succeed. The key aspects covered are identifying risks, analyzing their probability and impact, planning responses, and continuously monitoring risks. Qualitative and quantitative approaches to analysis are outlined. The overall process aims to move projects from reactive "firefighting" to proactive risk-based decision making.PMI project_risk_management_final_2022.ppt



PMI project_risk_management_final_2022.pptDorraLamouchi1
?
This document provides an overview of project risk management. It discusses what project risk is, the risk management process, and tools for risk identification, analysis, response planning, monitoring and control. The risk management process involves planning risk management, identifying risks, analyzing their probability and impact, developing response plans, monitoring risks throughout the project, and using tools like risk logs and templates. Managing risks proactively helps improve project success rates.project_risk_mgmt_final.ppt



project_risk_mgmt_final.pptavisha23
?
This document provides an overview of project risk management. It discusses the goals of risk management, including identifying and planning for risks to help projects succeed. The key aspects covered are identifying risks, analyzing their probability and impact, planning responses, and continuously monitoring risks. Qualitative and quantitative approaches to analysis are outlined. The overall process aims to move projects from reactive "firefighting" to proactive risk-based decision making.Enterprise Class Vulnerability Management Like A Boss



Enterprise Class Vulnerability Management Like A Bossrbrockway
?
A fluid and effective Vulnerability Management Framework, a core pillar in most Enterprise Security Architectures (ESA), remains a continual challenge to most organizations. Ask any of the major breach targets of the past several years. This talk takes the recent OWASP Application Security Verification Standard (ASVS) 2014 framework and applies it to Enterprise Vulnerability Management in an attempt to make a clearly complicated yet necessary part of your organization's ESA much more manageable, effective and efficient with feasible recommendations based on your business' needs.Ijetcas14 370



Ijetcas14 370Iasir Journals
?
- The document discusses the relationship between requirement engineering processes and risk management in software development projects.
- It notes that many software projects fail or go over budget due to poor requirement engineering, including a lack of understanding of client requirements and frequent changes.
- The author conducted a survey of 23 software professionals from 9 companies to assess how requirement engineering processes impact risk management.
- The survey found that the vast majority of respondents believed that requirement engineering is important or very important for improving risk management and that it enables better management of requirements and assessment of changing requirements.ASIS - Training #4 - Social innovation risk management



ASIS - Training #4 - Social innovation risk managementarmelleguillermet
?
This document provides an introduction to risk management and social innovation. It defines key risk management terms and describes the basic 5-step risk management process of identification, analysis, evaluation, treatment, and monitoring. For social innovation projects, opportunities include addressing social issues, though risks include weaknesses in the process that can lead to wasted resources or failure to achieve goals. Structured risk management applied to the procurement process can help promote social innovations by creating a fair and transparent framework to identify deficiencies and potential savings. The document concludes by thanking participants and directing them to a quiz to test their new knowledge.OWASP Chicago Meetup Presentation - Threat Modeling-Process Maturity



OWASP Chicago Meetup Presentation - Threat Modeling-Process MaturitySynopsys Software Integrity Group
?
Vinay Vishwanatha, associate managing consultant, Synopsys presented at a recent OWASP Chicago Meetup Presentation. For more information, please visit us at https://www.synopsys.com/blogs/software-security/pattern-based-threat-model/OWASP Chicago Meetup Presentation - Threat Modeling-Process Maturity



OWASP Chicago Meetup Presentation - Threat Modeling-Process MaturitySynopsys Software Integrity Group
?
Recently uploaded (20)
Brave Browser Crack 1.45.133 Activated 2025



Brave Browser Crack 1.45.133 Activated 2025kherorpacca00126
?
https://ncracked.com/7961-2/
Note: >> Please copy the link and paste it into Google New Tab now Download link
Brave is a free Chromium browser developed for Win Downloads, macOS and Linux systems that allows users to browse the internet in a safer, faster and more secure way than its competition. Designed with security in mind, Brave automatically blocks ads and trackers which also makes it faster,
As Brave naturally blocks unwanted content from appearing in your browser, it prevents these trackers and pop-ups from slowing Download your user experience. It's also designed in a way that strips Downloaden which data is being loaded each time you use it. Without these components
Understanding Traditional AI with Custom Vision & MuleSoft.pptx



Understanding Traditional AI with Custom Vision & MuleSoft.pptxshyamraj55
?
Understanding Traditional AI with Custom Vision & MuleSoft.pptx | ### ║▌║▌▀Ż Deck Description:
This presentation features Atul, a Senior Solution Architect at NTT DATA, sharing his journey into traditional AI using Azure's Custom Vision tool. He discusses how AI mimics human thinking and reasoning, differentiates between predictive and generative AI, and demonstrates a real-world use case. The session covers the step-by-step process of creating and training an AI model for image classification and object detectionĪ¬specifically, an ad display that adapts based on the viewer's gender. Atulavan highlights the ease of implementation without deep software or programming expertise. The presentation concludes with a Q&A session addressing technical and privacy concerns.Early Adopter's Guide to AI Moderation (Preview)



Early Adopter's Guide to AI Moderation (Preview)nick896721
?
Early Adopter's Guide to AI Moderation preview by User Interviews.L01 Introduction to Nanoindentation - What is hardness



L01 Introduction to Nanoindentation - What is hardnessRostislavDaniel
?
Introduction to NanoindentationReplacing RocksDB with ScyllaDB in Kafka Streams by Almog Gavra



Replacing RocksDB with ScyllaDB in Kafka Streams by Almog GavraScyllaDB
?
Learn how Responsive replaced embedded RocksDB with ScyllaDB in Kafka Streams, simplifying the architecture and unlocking massive availability and scale. The talk covers unbundling stream processors, key ScyllaDB features tested, and lessons learned from the transition.Transform Your Future with Front-End Development Training



Transform Your Future with Front-End Development TrainingVtechlabs
?
Kickstart your career in web development with our front-end web development course in Vadodara. Learn HTML, CSS, JavaScript, React, and more through hands-on projects and expert mentorship. Our front-end development course with placement includes real-world training, mock interviews, and job assistance to help you secure top roles like Front-End Developer, UI/UX Developer, and Web Designer.
Join VtechLabs today and build a successful career in the booming IT industry!DealBook of Ukraine: 2025 edition | AVentures Capital



DealBook of Ukraine: 2025 edition | AVentures CapitalYevgen Sysoyev
?
The DealBook is our annual overview of the Ukrainian tech investment industry. This edition comprehensively covers the full year 2024 and the first deals of 2025. Computational Photography: How Technology is Changing Way We Capture the World



Computational Photography: How Technology is Changing Way We Capture the WorldHusseinMalikMammadli
?
? Computational Photography (Computer Vision/Image): How Technology is Changing the Way We Capture the World
He? d©╣?©╣nm©╣s©╣n©╣zm©╣, m©╣asir smartfonlar v? kameralar nec? bu q?d?r g?z?l g?r©╣nt©╣l?r yarad?r? Bunun sirri Computational Fotoqrafiyas?nda(Computer Vision/Imaging) gizlidirĪ¬??kill?ri ??km? v? emal etm? ©╣sulumuzu t?kmill??dir?n, komp©╣ter elmi il? fotoqrafiyan?n inqilabi birl??m?si.SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOT



SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOTTanmaiArni
?
SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOTThe Future of Repair: Transparent and Incremental by Botond De?nes



The Future of Repair: Transparent and Incremental by Botond De?nesScyllaDB
?
Regularly run repairs are essential to keep clusters healthy, yet having a good repair schedule is more challenging than it should be. Repairs often take a long time, preventing running them often. This has an impact on data consistency and also limits the usefulness of the new repair based tombstone garbage collection. We want to address these challenges by making repairs incremental and allowing for automatic repair scheduling, without relying on external tools.FinTech - US Annual Funding Report - 2024.pptx



FinTech - US Annual Funding Report - 2024.pptxTracxn
?
US FinTech 2024, offering a comprehensive analysis of key trends, funding activities, and top-performing sectors that shaped the FinTech ecosystem in the US 2024. The report delivers detailed data and insights into the region's funding landscape and other developments. We believe this report will provide you with valuable insights to understand the evolving market dynamics.DAO UTokyo 2025 DLT mass adoption case studies IBM Tsuyoshi Hirayama (ŲĮ╔ĮęŃ)



DAO UTokyo 2025 DLT mass adoption case studies IBM Tsuyoshi Hirayama (ŲĮ╔ĮęŃ)Tsuyoshi Hirayama
?
DAO UTokyo 2025
¢|Š®┤¾č¦Ūķł¾č¦Łh źųźĒź├ź»ź┴ź¦®`ź¾čąŠ┐źżź╦źĘźóźŲźŻźų
https://utbciii.com/2024/12/12/announcing-dao-utokyo-2025-conference/
Session 1 :DLT mass adoption
IBM Tsuyoshi Hirayama (ŲĮ╔ĮęŃ)Inside Freshworks' Migration from Cassandra to ScyllaDB by Premkumar Patturaj



Inside Freshworks' Migration from Cassandra to ScyllaDB by Premkumar PatturajScyllaDB
?
Freshworks migrated from Cassandra to ScyllaDB to handle growing audit log data efficiently. Cassandra required frequent scaling, complex repairs, and had non-linear scaling. ScyllaDB reduced costs with fewer machines and improved operations. Using Zero Downtime Migration (ZDM), they bulk-migrated data, performed dual writes, and validated consistency.Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]Jonathan Bowen
?
Alan Turing arguably wrote the first paper on formal methods 75 years ago. Since then, there have been claims and counterclaims about formal methods. Tool development has been slow but aided by MooreĪ»s Law with the increasing power of computers. Although formal methods are not widespread in practical usage at a heavyweight level, their influence as crept into software engineering practice to the extent that they are no longer necessarily called formal methods in their use. In addition, in areas where safety and security are important, with the increasing use of computers in such applications, formal methods are a viable way to improve the reliability of such software-based systems. Their use in hardware where a mistake can be very costly is also important. This talk explores the journey of formal methods to the present day and speculates on future directions.
BoxLang JVM Language : The Future is Dynamic



BoxLang JVM Language : The Future is DynamicOrtus Solutions, Corp
?
Just like life, our code must evolve to meet the demands of an ever-changing world. Adaptability is key in developing for the web, tablets, APIs, or serverless applications. Multi-runtime development is the future, and that future is dynamic. Enter BoxLang: Dynamic. Modular. Productive. (www.boxlang.io)
BoxLang transforms development with its dynamic design, enabling developers to write expressive, functional code effortlessly. Its modular architecture ensures flexibility, allowing easy integration into your existing ecosystems.
Interoperability at Its Core
BoxLang boasts 100% interoperability with Java, seamlessly blending traditional and modern development practices. This opens up new possibilities for innovation and collaboration.
Multi-Runtime Versatility
From a compact 6MB OS binary to running on our pure Java web server, CommandBox, Jakarta EE, AWS Lambda, Microsoft Functions, WebAssembly, Android, and more, BoxLang is designed to adapt to any runtime environment. BoxLang combines modern features from CFML, Node, Ruby, Kotlin, Java, and Clojure with the familiarity of Java bytecode compilation. This makes it the go-to language for developers looking to the future while building a solid foundation.
Empowering Creativity with IDE Tools
Unlock your creative potential with powerful IDE tools designed for BoxLang, offering an intuitive development experience that streamlines your workflow. Join us as we redefine JVM development and step into the era of BoxLang. Welcome to the future.
Revolutionizing-Government-Communication-The-OSWAN-Success-Story



Revolutionizing-Government-Communication-The-OSWAN-Success-Storyssuser52ad5e
?
? ????? ??????? ????? ?
???????? ??????????? is proud to be a part of the ?????? ????? ???? ???? ??????? (?????) success story! By delivering seamless, secure, and high-speed connectivity, OSWAN has revolutionized e-?????????? ?? ??????, enabling efficient communication between government departments and enhancing citizen services.
Through our innovative solutions, ???????? ?????????? has contributed to making governance smarter, faster, and more transparent. This milestone reflects our commitment to driving digital transformation and empowering communities.
? ?????????? ??????, ?????????? ??????????!
UiPath Automation Developer Associate Training Series 2025 - Session 2



UiPath Automation Developer Associate Training Series 2025 - Session 2DianaGray10
?
In session 2, we will introduce you to Data manipulation in UiPath Studio.
Topics covered:
Data Manipulation
What is Data Manipulation
Strings
Lists
Dictionaries
RegEx Builder
Date and Time
Required Self-Paced Learning for this session:
Data Manipulation with Strings in UiPath Studio (v2022.10) 2 modules - 1h 30m - https://academy.uipath.com/courses/data-manipulation-with-strings-in-studio
Data Manipulation with Lists and Dictionaries in UiPath Studio (v2022.10) 2 modules - 1h - https:/academy.uipath.com/courses/data-manipulation-with-lists-and-dictionaries-in-studio
Data Manipulation with Data Tables in UiPath Studio (v2022.10) 2 modules - 1h 30m - https:/academy.uipath.com/courses/data-manipulation-with-data-tables-in-studio
?? For any questions you may have, please use the dedicated Forum thread. You can tag the hosts and mentors directly and they will reply as soon as possible. Application Security Risk Rating
- 1. Application Security Risk Rating Vaibhav Gupta Security Researcher ©C Adobe in.linkedin.com/in/vaibhav0 @VaibhavGupta_1
- 2. $ whoami 2 ? Current ? Security Researcher - Adobe ? Previous ? Sr. Information Security Engg. ©C Fortune 500 company ? Before that.. ? InfoSec consultant at various companies
- 3. Problem Statement 1. Limited resources to security test large threat landscape of web applications within enterprise 2. Assigning risk levels to vulnerabilities found in manual assessments 3 in.linkedin.com/in/vaibhav0
- 4. Lets first deal with Ī░1Ī▒ 4 1. Limited resources to security test large threat landscape of web applications within enterprise ? Increasing threat landscape ? Slow pace of organizations to adopt secure coding practices ? Does not make sense to address all issues simultaneously in.linkedin.com/in/vaibhav0
- 5. Solution ? 5 ? Prioritization ? Focus on categorizing into high, medium and low risk applications in.linkedin.com/in/vaibhav0
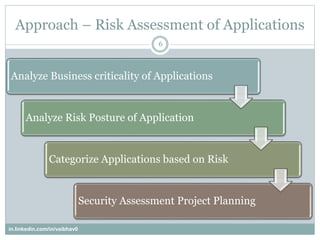
- 6. Approach ©C Risk Assessment of Applications 6 Analyze Business criticality of Applications Analyze Risk Posture of Application Categorize Applications based on Risk Security Assessment Project Planning in.linkedin.com/in/vaibhav0
- 7. Analyze Business criticality of Application 7 Critical Important Strategic Internal in.linkedin.com/in/vaibhav0
- 8. Sr. # Questions Response (Yes/No) 1 Is the application facing the internet? 2 Is this application dealing with credit card data? 3 Is this application dealing with SSN or any other PII data? 4 Does application host any classified or patented data? 5 If the application goes down, can it create threat to human life? 6 Will this application be subject to any compliance audits? 7 Is this application designed to aid Top Management or Board Members in decision making? 8 Does application implement any kind of authentication? If yes, please give additional details 9 Does application implement any kind of authorization? If yes, provide additional details 10 Is this application developed as a plug-in or extension for other application? If yes, please provide additional details on what all applications it will be working with Analyze Risk Posture of Application 8
- 9. Categorize Applications based on Risk 9 Inventory Business Criticality Risk Posture Categorized Inventory Low Medium High in.linkedin.com/in/vaibhav0
- 10. Test Case - Categorize Applications based on Risk 10 in.linkedin.com/in/vaibhav0 ? Payroll application
- 11. Lets deal with next problem statement: Ī░2Ī▒ 11 2. Assigning risk levels to vulnerabilities found in manual assessments ???? Why are we even considering this problem statement in.linkedin.com/in/vaibhav0
- 12. OWASP: Risk Rating Methodology 12 ? There are many different approaches to risk analysis. The OWASP approach is based on standard methodologies and is customized for application security. ? Standard risk model : Risk = Likelihood * Impact in.linkedin.com/in/vaibhav0
- 13. OWASP: Risk Rating Methodology - Steps 13 Step 1 ? Identifying a Risk Step 2 ? Estimating Likelihood Step 3 ? Estimating Impact Step 4 ? Determining Severity of the Risk Step 5 ? Deciding What to Fix Step 6 ? Customizing Your Risk Rating Model in.linkedin.com/in/vaibhav0
- 14. Step 1: Identifying a Risk 14 ? What needs to be rated? ? XSS ? ? SQLi ? ? Threat agents ? ? Impact ? in.linkedin.com/in/vaibhav0
- 15. Step 2: Estimating Likelihood 15 ? Threat Agent Factors ? Skill level ? Motive ? Opportunity ? Size ? Vulnerability Factors ? Ease of discovery ? Ease of exploit ? Awareness ? Intrusion detection in.linkedin.com/in/vaibhav0
- 16. Step 3: Estimating Impact 16 ? Technical Impact Factors ? Loss of confidentiality ? Loss of integrity ? Loss of availability ? Loss of accountability ? Business Impact Factors ? Financial damage ? Reputation damage ? Non-compliance ? Privacy violation in.linkedin.com/in/vaibhav0
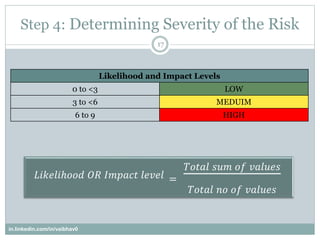
- 17. Step 4: Determining Severity of the Risk 17 Likelihood and Impact Levels 0 to <3 LOW 3 to <6 MEDUIM 6 to 9 HIGH in.linkedin.com/in/vaibhav0 ?????????? ?? ?????? ????? = ????? ??? ?? ?????? ????? ?? ?? ??????
- 18. Step 4: Determining Severity of the Risk (Cont..) 18
- 19. Test Case - OWASP Risk Rating 19 in.linkedin.com/in/vaibhav0
- 20. Step 5: Deciding What to Fix 20 in.linkedin.com/in/vaibhav0 PRIORITIZE Critical High Medium Low Note Note: As a general rule, you should fix the most severe risks first
- 21. Step 6: Customizing Your Risk Rating Model 21 Ī░A tailored model is much more likely to produce results that match people's perceptions about what is a serious riskĪ▒ - OWASP ? Adding factors ? Customizing options ? Weighting factors in.linkedin.com/in/vaibhav0
- 22. ?? Questions ?? Vaibhav Gupta Security Researcher ©C Adobe in.linkedin.com/in/vaibhav0 @VaibhavGupta_1
Editor's Notes
- #8: Critical - > paypal.com for paypal Important -> Strategic - > companyĪ»s main website Internal -> payroll app/AMS



