John locke-word camp-sacramento-2015
- 1. Plugins Part 1: iThemes Security JOHN LOCKE
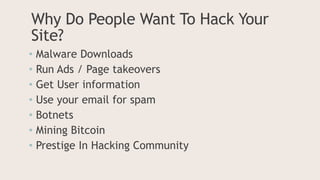
- 2. Why Do People Want To Hack Your Site? ŌĆó Malware Downloads ŌĆó Run Ads / Page takeovers ŌĆó Get User information ŌĆó Use your email for spam ŌĆó Botnets ŌĆó Mining Bitcoin ŌĆó Prestige In Hacking Community
- 3. WordPress Is A Lucrative Target ŌĆó One In Four Websites Run WordPress ŌĆó Find Vulnerabilities In WordPress ŌĆó Automate Attacks ŌĆó Profit!
- 56. John Locke LockedownDesign.com @Lockedown_ on Twitter
Editor's Notes
- #2: How many of you know someone whoŌĆÖs had a hacked site?
- #3: Your site doesnŌĆÖt need to be huge to be of value to hackers. They can use your blog or small business site for a variety of purposes. They can install malware on your site, which infect people who visit your site. Your site can house ads or even new pages for Viagra, Cialis, gambling, or other unsavory things. They can find information on other people registered to your site. They can use your email server to send spam to other victims. They can use your server resource as part of a botnet to attack other sites, mine Bitcoin, or just get recognition in the hacking community.
- #4: WordPress runs one in every four sites on Earth. If hackers can find vulnerabilities in WordPress, and automate attacks, they have the potential to take over hundreds of thousands of sites.
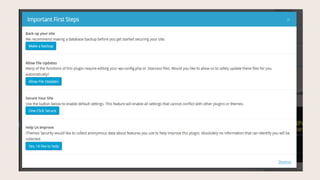
- #5: When you first install iThemes Security and go to the Dashboard, youŌĆÖll see four calls to action. First, a prompt to make a backup of your database. This is emailed to the administrator email. ItŌĆÖs always best to get backups that are not stored on the server. Because if your server is infected, the database backup on your server is also likely to be infected. Second, will you allow the plugin to update the wp-config and .htaccess files? The plugin uses these to help keep bad guys out. Third, a one-click button for default settings. There are about six settings here that go into effect. WeŌĆÖll look at those in a minute. Last, Can we observe how youŌĆÖre using this plugin so we can make improvements to the plugin?
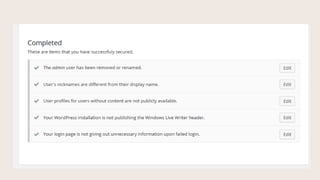
- #6: These are the settings we enabled with the one-click settings on the last page. WeŌĆÖve removed ŌĆ£adminŌĆØ as a username. When you do a fresh install of WordPress these days, you can choose any username you want. This wasnŌĆÖt always the case. In years past, it used to default to ŌĆ£adminŌĆØ as a username. Sites that were launched a few years ago may still have ŌĆ£adminŌĆØ as a main username. Now hackers only need to guess the password that goes with admin to break into your site. User nicknames are different from the display name. This prevents your username being displayed in plain sight by themes displaying author credits. User profiles with no published posts are also not displayed. This is so dormant accounts donŌĆÖt become an easy target for hackers. The login page is not giving out information on failed login, like ŌĆ£The username was incorrectŌĆØ or ŌĆ£The password was incorrectŌĆØ. We donŌĆÖt want to give hackers any clues to get into your site. The Windows Live Writer header is also removed.
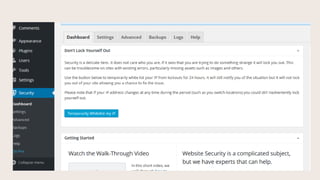
- #7: One of the first things you should always do is white-list your IP address for 24 hours. Since weŌĆÖre changing the site configuration, we can accidentally lock ourselves out. Whitelisting our IP helps prevent that. IŌĆÖd like to go over some of these tabs here: Dashboard and Settings help you keep track of what security measures are in place. Advanced are security settings you can use, but have a good backup of your site before you implement these. The Logs tab records details of activity and changes on your site.
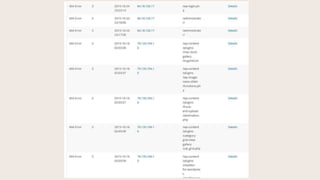
- #8: This is some of what you will find on your Logs page after a while. Here, it is recording 404 errors, where two different IPŌĆÖs were hitting 404ŌĆÖs while trying to find a login URL, and also looking for known plugin vulnerabilities for plugins that are not on this site. More on this in a few minutes.
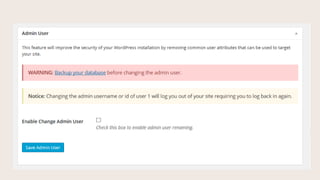
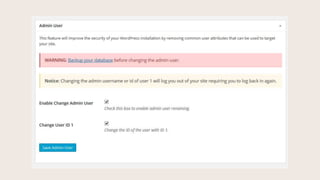
- #9: These are settings in the Advanced tab. This setting changes the admin user and changes user 1 to another number. When you install WordPress, who is the first user in the Users database table? That is the administrator. This deflects attacks aimed at the first user in the database.
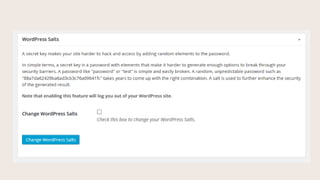
- #10: For those familiar with the wp-config file, the WordPress salts are those random characters attached to logins. When you change the salts, it logs everyone out everywhere. So if someone is logged into your site, they have to log back in.
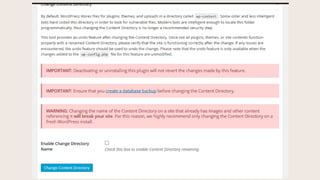
- #11: This setting changes the folder name of the wp-content folder. Many attacks are aimed at plugin and theme vulnerabilities. Where are those located? In the wp-content folder. IF we rename this folder, it prevents automated attacks against those files. Be careful with this one, as it will affect your whole site.
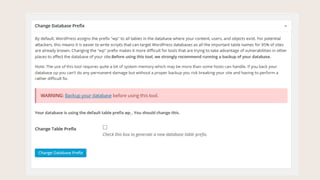
- #12: This setting changes the default database table prefix. When you install WordPress, the default prefix is ŌĆ£wp_ŌĆØ. This changes the prefix on those tables, so attacks looking for those specific database tables get derailed. Some managed WordPress hosts will do this automatically for you.
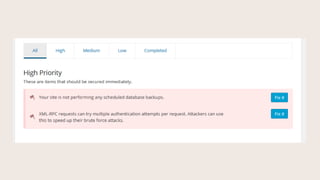
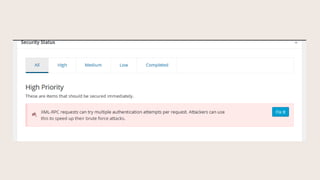
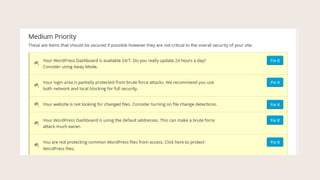
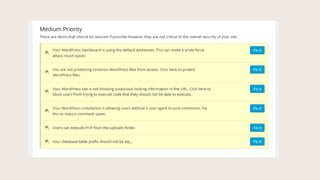
- #13: From here on in, weŌĆÖll look at the Dashboard, organized into suggested actions by High, Medium, Low, and Completed, and the corresponding places where the Fix It buttons link to in Settings. The first setting says we donŌĆÖt have regular backups scheduled.
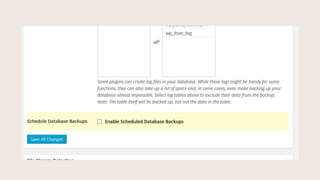
- #14: Whn we click the Fix It button, it takes us to scheduling database backups in Settings
- #15: You can choose how often you back up your database by how many days in between running backups.
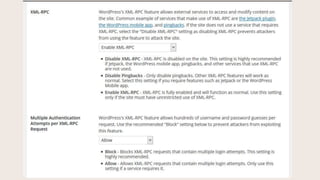
- #16: XML-RPC is something used by Jetpack, the mobile app, certain plugins, and Pingbacks.
- #17: This used to be one setting, in the last version this became two settings. At the top, you can allow all XML-RPC, disable only Pingbacks, or Disable XML-RPC completely. Pingbacks can also be used in a Ddos, or denial of service attack. The second setting lets you disable multiple username and password combos per authentication. This helps prevent brute force attacks.
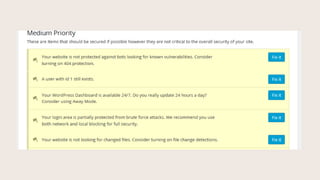
- #18: In Medium Priority, the first setting is turning on 404 protection.
- #19: Remember when I showed you the Logs a minute ago? When we turn on 404 protection, this locks out bad guys looking for things they shouldnŌĆÖt be looking for, if they hit too many 404ŌĆÖs in a certain time span.
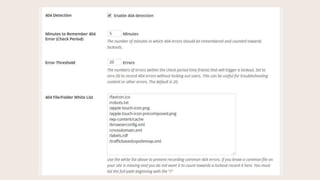
- #20: You can set how many 404s it takes to trigger a lockout in how long a time. Also has a white-list for file types, like jpgs, so accidental lockouts due to incorrect file paths.
- #21: User with id of 1 still exists, we just covered this on the Advanced tab.
- #22: This is what it looks like when we rename the admin user and change User ID 1.
- #23: Your WordPress Dashboard is available 24 hours a day. This on e is really interesting.
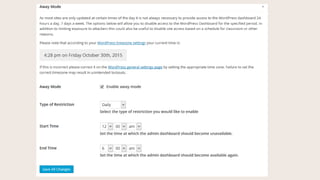
- #24: LetŌĆÖs say you only have one or two people working on your site. Should people be logging in when youŌĆÖre normally asleep?
- #25: Away Mode lets you designate what time access to the backend automatically shuts down. Between these hours, the login screen is completely inaccessible, and youŌĆÖll be logged out when that away time starts.
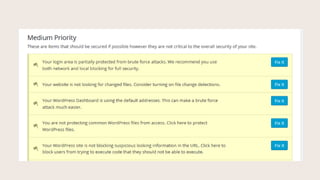
- #26: Your login area is partially protected from brute force attacks.
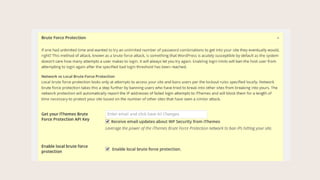
- #27: Network brute force protection keeps track not only of the IPŌĆÖs that try to break into your site, but also the IPŌĆÖs that have tried to break into other sites in a network. By entering your email here, IPŌĆÖs that have been identified as malicious by other sites will also be blocked from your site.
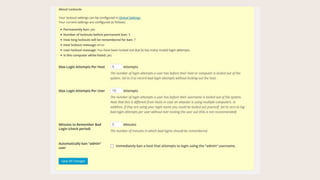
- #28: You can also control lockouts locally, for IPŌĆÖs that try to force your site open. These are settings for when those lockouts trigger, and how long to remember bad IP addresses. You can also automatically ban anyone that attempts to login with ŌĆ£adminŌĆØ username. This is commonly used, because many older, unmaintained WordPress sites have admin for a username, usually accompanied by a weak password.
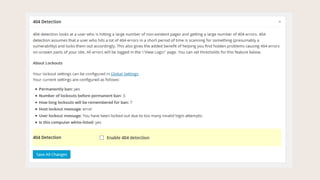
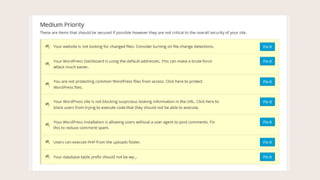
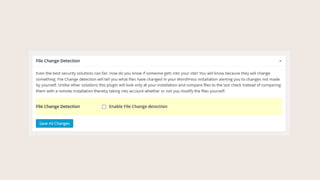
- #29: You website is not looking for changed files.
- #30: iThemes Security will observe if files get changed on your site, and send you an email alerting you to exactly what got changed.
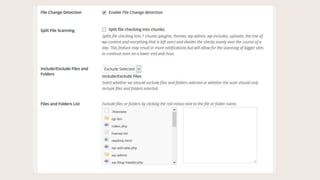
- #31: You can split file checking into chunks, or exclude certain files from being checked (though I would not enable this).
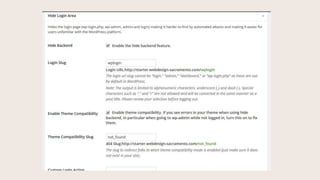
- #32: Your WordPress Dashboard is using the default web address. This feature allows you to change the default logins URLs.
- #33: Instead of default /wp-login.php or /wp-admin/ login screens, you can make the login URL whatever you want. Hackers send automated attacks to the default addresses, and when they donŌĆÖt find those, that results in a 404, which we are protecting against. This is security by obscurity. Sophisticated hackers can still find your login URL, but this will eliminate many automated attacks. DonŌĆÖt use wplogin or anything obvious for a URL. Use a secret phrase, word or random string of characters that is difficult to guess.
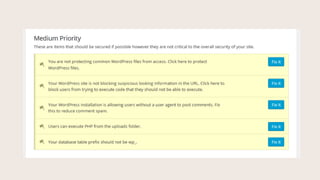
- #34: You are not protecting common WordPress files from access.
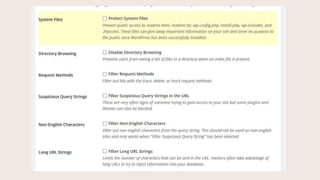
- #35: These settings protect people from browsing the wp-config file, .htaccess, wp-includes folder, and install.php files. You can also prevent people from browsing empty directories, filter out suspicious request methods in URLs, disallow non-English characters in the URL, and limit unusually long URLs. These can all be means people are trying to use to gain access to your site.
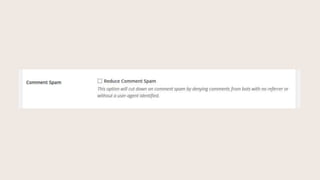
- #36: The reduce comment spam option denies comments without a user agent. Browsers have user-agent headers. Search engine crawlers even have user-agent headers. Generally, only comment spam bots are missing a referrer or identifiable user-agent.
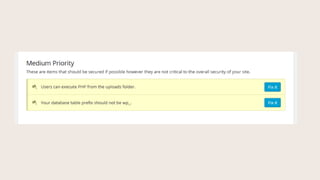
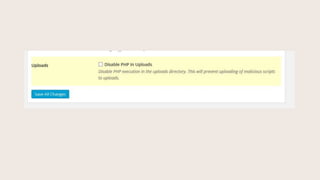
- #37: Users can execute PHP from the uploads folder.
- #38: This setting prevents people form uploading PHP files to execute in your uploads folder.
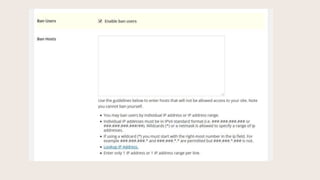
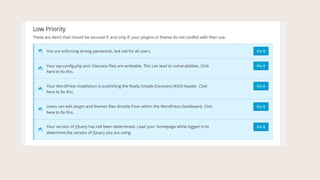
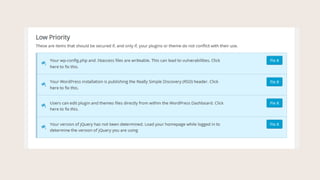
- #39: HereŌĆÖs the Low Priority Items. Enable Ban Users.
- #40: You can ban IP addresses. You can also ban user-agents (certain crawler bots you want to restrict from your site).
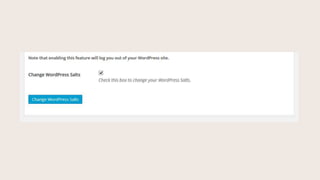
- #41: Changing Salts.
- #42: Changing salts in the wp-config file logs everyone out, everywhere.
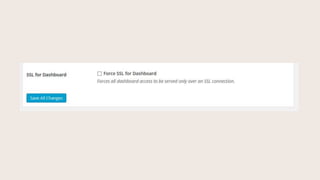
- #43: Require secure connection = Forcing SSL / HTTPS for login.
- #44: You can lock everyone out of the site. Get help with this one.
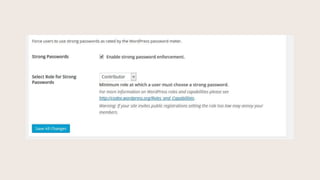
- #45: Enforce Strong Passwords
- #46: New WordPress installs now prompt admins for strong passwords. But what about Editors or other people with advanced roles and privileges? Someone can hack an Edotr account and still do damage to your site. With this, you can select which role level strong passwords are enforced at.
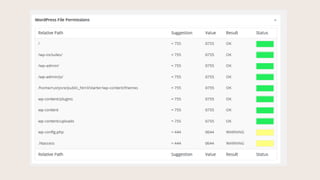
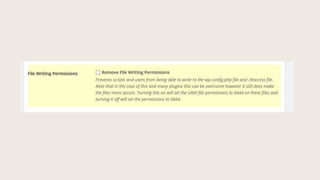
- #47: Wp-Config and .htacces files are writeable by default. This is a vulnerability.
- #48: This screenshot is at bottom of the Dashboard screen. You can see file permissions and what the recommendations are.
- #49: Change permissions on these sensitive files here.
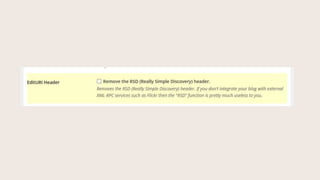
- #50: Really Simple Discovery header is information used by certain services like Flickr, but itŌĆÖs likely you donŌĆÖt need it displaying in your source code.
- #51: RSD header can give away information we donŌĆÖt want bad guys to have,
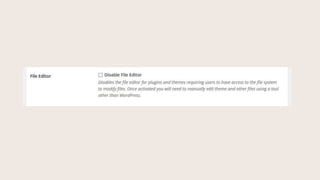
- #52: Disabling the file editor
- #53: This means you wonŌĆÖt be able to edit theme or plugin files in the backend of the site. This also prevents someone from cracking your site and altering those files from the backend, if they hack into your site.
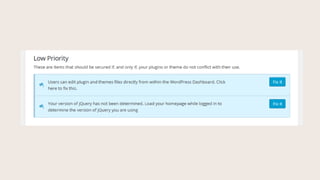
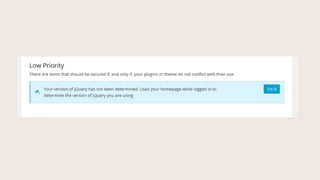
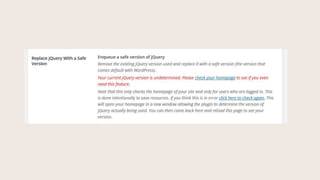
- #54: Check to see if your theme is loading a safe version of jQuery.
- #55: To test, click ŌĆ£Check your homepageŌĆØ. This is important because if a theme bundles an old version of jQuery in the actual theme files, that theme can be hacked and that file can be malformed to become malicious. Same thing if you link to an unmaintained code repo for jQuery.
- #56: Once your home page is checked, refresh the screen. You should see the okay message here.