Keeping Your App's Email out of the SPAM Folder
- 1. Keeping Your App's Email out of the SPAM folder Elmer Thomas Hacker in Residence @thinkingserious
- 2. ŌĆ£If your emails donŌĆÖt make it to the Inbox, you are talking to yourself. Not cool.ŌĆØ - Email Sending Ninja, Elmer Thomas
- 3. I want you to stop talking to yourself.
- 4. De’¼ünitions & Assumptions How SPAM Filters Work The Key: Reputation Securing Your Identity Infrastructure Content & Relevancy Analytics The SPAM Game!
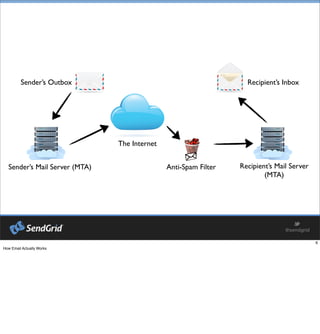
- 5. SenderŌĆÖs Outbox RecipientŌĆÖs Inbox
- 6. SenderŌĆÖs Outbox RecipientŌĆÖs Inbox SenderŌĆÖs Mail Server (MTA) The Internet RecipientŌĆÖs Mail Server (MTA) Anti-Spam Filter
- 7. TRANSACTIONAL Con’¼ürmations Alerts Noti’¼ücations Receipts Password Delivery Account Veri’¼ücations Statements Shipping Noti’¼ücations Reminders Cancellations Updates Announcements
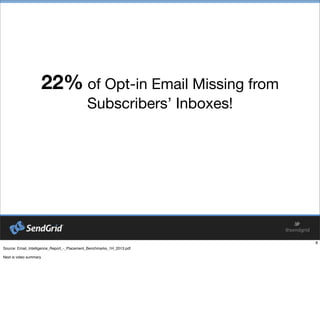
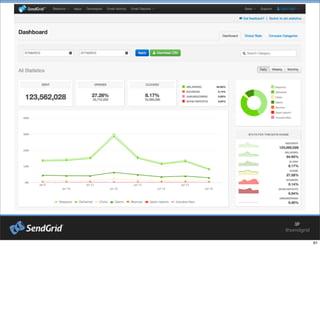
- 8. 22% of Opt-in Email Missing from SubscribersŌĆÖ Inboxes!
- 9. Email Deliverability = Getting to the Inbox
- 15. Heuristics, Statistics & Magic
- 17. Reputation
- 19. Discover the Keys to Building Your Reputation
- 20. Relevant, Properly Formatted Email
- 21. Send the right message to the right person at the right time with the right frequency
- 22. 0 15 30 45 60 M T W Th F S Su Emails Sent
- 23. Few Complaints
- 24. SPAM
- 25. Few Bounces
- 28. Transactional Emails are Exempt from CAN-SPAM
- 30. Learn How to Con’¼ürm Your Identity Through Email Authentication in 5 Steps
- 32. Sender Policy Framework (SPF) SenderID Domain Keys Identi’¼üed Mail (DKIM) Sender ID: http://www.microsoft.com/mscorp/safety/technologies/senderid/default.mspx SPF: http://docs.sendgrid.com/docs/email-deliverability/spf-records-voila-validation-verisimilitude DKIM: http://docs.sendgrid.com/documentation/apps/domain-keys
- 33. Update Your DNS Records
- 34. Sign Outbound Email with DKIM
- 35. Test Policy Record Tester: http://domainkeys.sourceforge.net/policycheck.html Selector Record Tester: http://domainkeys.sourceforge.net/selectorcheck.html Sender Policy Framework: http://www.openspf.org/Tools
- 36. How To Setup a Professional Infrastructure
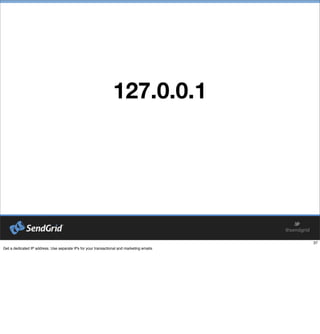
- 37. 127.0.0.1
- 40. Loops
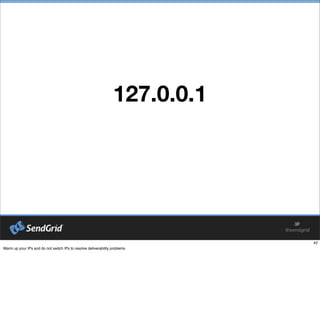
- 42. 127.0.0.1
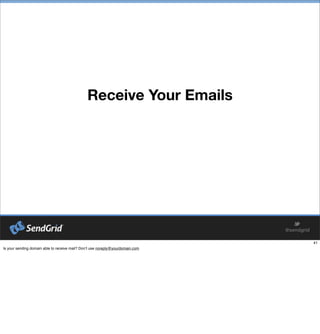
- 43. Learn About List Management
- 45. Keep Clean
- 46. Double Opt-In
- 47. Hard Bounce = Go Away Soft Bounce = Call Me Later
- 51. Segment Wisely
- 52. Avoid Trigger Words & Phishing Phrases 100 SPAM Trigger Words & Phrases to Avoid: http://blog.mannixmarketing.com/2009/08/spam-trigger-words/ Short List of Common Phishing Phrases: http://www.24hoursupport.com/index.php?option=com_content&task=view&id=192&Itemid=1
- 53. HTML + Text
- 55. Text : Image Ratio
- 56. Too BIG
- 57. HTML, CSS and Images validator.w3.org
- 58. Send the right message to the right person at the right time with the right frequency
- 59. Build and Maintain Your Reputation Check All of the Technical Checkboxes Be Relevant Monitor, Review and Improve
- 64. Now you can stop talking to yourself.
- 65. Thanks! To learn more, check out: http://go.sendgrid.com/DeliverabilityGuide.html or feel free to reach out: elmer.thomas@sendgrid.com @thinkingserious
Editor's Notes
- #2: ## Keep Your App's Email Out of the SPAM Folder Drawing from his experience at SendGrid, which has delivered over 114 billion emails on behalf of over 130,000 customers, Elmer will teach you the factors that determine whether your email will hit the inbox and the practical steps you can take today to avoid the SPAM folder and ensure that your customers receive the communications they expect. ## Bio: Elmer Thomas Elmer is formally trained as a Computer & Electrical Engineer with a B.S. in Computer Engineering and a Masters in Electrical Engineering (Focus was on Control Systems, specifically with GPS navigation systems) at the Univeristy of California, Riverside. Afterwards, he added a few mentors, then some sales and marketing skills to his repertoire and co-founded several companies, including AboveTheLimit.com , ThemBid.com and L ogoBids.com . He then began at SendGrid as a Web Development Manager (along with the many hats early SendGrid'ers wore), then moved to a Product Development role. Currently, Elmer is SendGrid's Hacker in Residence. His mission is to help SendGrid live up to its slogan: "Email Delivery. Simplified" by improving the lives of developers, both internally and externally. He is known in social media circles as ThinkingSerious.
- #5: Summary Treat this topics as a checklist to follow.
- #6: How Email Appears to Work
- #7: How Email Actually Works
- #8: What kind of emails are we talking about?
- #9: Source: Email_Intelligence_Report_-_Placement_Benchmarks_1H_2013.pdf Next is video summary
- #11: So what is email deliverability anyway? ItŌĆÖs getting to the inbox vs. junk/bulk/missing
- #12: Most Important fact: Delivery is never guaranteed
- #13: What happens when these emails donŌĆÖt get delivered? ItŌĆÖs pretty much the end of the world. - no purchase confirmations - no shipping information - no password resets - lost revenue - never get to meet that special someone at your favorite dating site Image Source: http://hubcityblues.wordpress.com
- #14: What happens when these emails get delivered? Unicorns and rainbows, of course. (and sometimes cupcakes and lollipops) :) - establish trust - better conversions Image Source: http://maxtheunicorn.blogspot.com
- #15: LetŌĆÖs talk about how SPAM filters work. Understanding what stands between you and the inbox is key. Image Source: http://sendgrid.com/blog/10-tips-to-keep-email-out-of-the-spam-folder
- #16: Some measure and track user interaction (messages that aren't read, or aren't opened and clicked on, are more likely to be sent to the Junk folder) Image Source: http://www.umnet.com
- #17: Some use heuristics (rules, often with regular expressions, to search for spammy content), message structure (does this look like a Newsletter we've seen before?), message fingerprinting (look up fingerprint to see if it matches know spam) and/or statistical methods (Bayesian filter: Does this message contain words similar to known spam or known clean messages?)
- #18: Some use human user feedback and community voting ("This is spam" button in mail client or webmail app.)
- #19: Some look at sender reputation (based on sending IP or domain) Image Source: http://myfirstfarce.blogspot.com
- #20: ...but there's no silver bullet. Spammers adapt. Filters adapt. Some innocent messages get caught in the crossfire (false positives). Image Source: http://sbrownehr.com
- #21: Building Your Reputation Why? Because it's a key factor that determines if you hit the Inbox Image Source: http://herocomplex.latimes.com
- #22: The formula Send Relevant, Properly Formatted Email. If they asked to be alerted, send an alert. I will go into detail during the Content & Relevancy portion
- #23: Most of the time, when someone marks your message as spam, It wasn't the right message (relevance) Or it wasn't sent to the right person (confirmed opt-in list or purchased list or stale list?) Or it wasn't sent at the right time (obtained the email address years ago while working for a different company selling a different product) Or it wasn't sent with the right frequency (recipients get "email fatigue" if you send too often (use a preference center), or may forget about you if you don't send often enough.)
- #24: Consistent Volume Predictable
- #25: Very Few Complaints Re-iterate the relevancy formula Image Source: http://www.goodfinancialcents.com
- #26: Avoid SPAM Traps Image Source: http://instanttrap.com /
- #27: Low Bounce Rates Image Source: http://www.cybersalt.org/
- #28: Professionally Configured Infrastructure Source: http://www.motifake.com
- #29: No Blacklist Appearance See List Management section for help keeping off of black lists Blacklist checking resources: https://www.senderscore.org/blacklistlookup http://www.mxtoolbox.com/blacklists.aspx h ttp://www.dnsstuff.com/docs/ip4r/ Image Source: http://www.deliverability.com
- #30: Comply with CAN-SPAM or face penalties up to $16,000 Reference: www.ftc.govŌĆöbus61.shtm Note: If your email contains only transactional emails or relationship content, then you are exempt from these rules; however, you must still not include false or misleading routing information.
- #31: Check your Sender Score here: https://www.senderscore.org Email Deliverability Checker: https://chrome.google.com/w ebstore/detail/mbfenkanhbafpdmlmhiicehikmfccebb
- #33: Step 1: Identify all machines that send mail for your company and determine the IPs and sending domains used. Source Image: http://www.limonwhitaker.com
- #34: Step 2: Create your authentication records Sender ID: http://www.microsoft.com/mscorp/safety/technologies/senderid/default.mspx SPF: http://docs.sendgrid.com/docs/email-deliverability/spf-records-voila-vali dation-verisimilitude DKIM: http://docs.sendgrid.com/documentation/apps/domain-keys
- #35: Step 3: Publish your authentication records via your DNS records
- #36: Step 4: Setup your mail server to sign outbound email with DKIM Reference: http://www.sendmail.com/sm/wp/dkim
- #37: Step 5: Test by publishing in "test" mode. Policy Record Tester: http://domainkeys.sourceforge.net/policycheck.html Selector Record Tester: http://domainkeys.sourceforge.net/selectorcheck.ht ml Sender Policy Framework: http://www.openspf.org/T ools Keep an eye on DMARC: http://sendgrid.com/blog/what-is-dmarc-and-why-sh ould-you-care/ Image Source : http://www.geeky-gadgets.com
- #38: Make sure your Infrastructure is Sound
- #39: Get a dedicated IP address. Use separate IPs for your transactional and marketing emails.
- #40: Secured servers
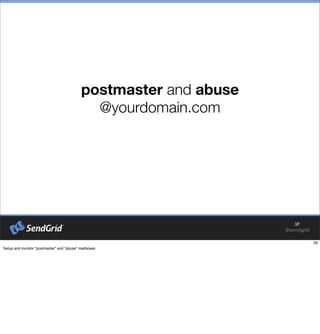
- #41: Setup and monitor "postmaster" and "abuse" mailboxes
- #42: Signed up for ISP Feedback Loops Resource: http://blog.whitesites.com/ISP-Feedback-Loop-list__634207841076562500_blog.htm Image Source: http://microadvert.net
- #43: Is your sending domain able to receive mail? DonŌĆÖt use [email_address]
- #44: Warm up your IPs and do not switch IPs to resolve deliverability problems
- #45: List Management
- #46: Don't rent or buy email lists, ever!
- #47: Keep your lists clean Image Source: http://en.wikipedia.org
- #48: Use an industry standard opt-in process. The best is confirmed opt-in (aka double opt-in) where you send the subscriber a verification email that requires confirmation (click link) before you add them to your list.╠² Senders should store proof of their subscribers' confirmed opt-in status. (New Canadian anti-spam law requires senders to show proof of subscriber opt-in if a case comes to court.)
- #49: Soft vs. Hard Bounce Tracking Remove hard bounces immediately and closely monitor soft bounces.
- #50: Engage! What kind of data are ISPs using to determine engagement? Beyond opens and clicks to your specific message, ISPs are use TiNS data (ŌĆ£This is not spam), panel data, trusted reporter data and inactive accounts as measures of engagement. TiNs data is gathered from users actively clicking a button that says ŌĆ£This is Not Spam.ŌĆØ This shows that users really want your email and will help improve your reputation metrics over time. Panel data is a panel of users that determine whether email messages have been correctly marked as spam based on specific criteria specified by the email providers. Trusted reporter data is culled from accounts that have proven to be real users who display normal behavior when interacting with their email messages. To avoid issues overall, employ strong permissioning practices. Inactive accounts are mailboxes that do not have regularly activity. To avoid mailing to inactive accounts, segment out inactives every six months and alter your email strategy in consideration of their lack of response. As a sender, you are not privy to these metrics, but knowing that some ISPs are using this data to determine inbox placement helps you prioritize your goals when it comes to list hygiene, messaging and your overall email strategy. Use SendGrid's Event API to gather real-time engagement metrics so they can segment their list better
- #51: Soft vs. Hard Bounce Tracking Remove hard bounces immediately and closely monitor soft bounces.
- #52: Make it easy to unsubscribe so they don't hit the "This is SPAM" button Image Source: http://www.damiansaunders.net
- #53: Segment by demographics, interests and purchase behavior to increase relevancy and value Image Source: http://www.huffingtonpost.com
- #54: 100 SPAM Trigger Words & Phrases to Avoid: http://blog.mannixmarketing.com/2009/08/spam-trigger-words/ Short List of Common Phishing Phrases: http://www.24hoursupport.com/index.php?option=com_content&t ask=view&id=192&Itemid=1
- #55: Include a text version if sending HTML Emails
- #57: Maintain a good text to image ratio. Don't send any image-only emails. For every graphic include 2 lines of text. Optimize your images.
- #59: Use the ALT tag & store images on a web server. Don't use CSS. Double check your message's HTML content code: validator.w3.org
- #60: Most of the time, when someone marks your message as spam, It wasn't the right message (relevance) Or it wasn't sent to the right person (confirmed opt-in list or purchased list or stale list?) Or it wasn't sent at the right time (obtained the email address years ago while working for a different company selling a different product) Or it wasn't sent with the right frequency (recipients get "email fatigue" if you send too often (use a preference center), or may forget about you if you don't send often enough.)
- #61: Key Takeaways
- #62: http://blog.sendgrid.com/email-deliverability-metrics-7-metrics-watch-prevent-delivery-failures/
- #64: Please remember though, sometimes other forms of communications can be superior to email ;)
- #65: Either play the name that SPAM game, or the create the worlds worst SPAM message game, depending on the audience.