Kosa - Theory for Privacy Measuring v2
1 like435 views
The document discusses the multifaceted nature of privacy across disciplines and the lack of standardized measurement methods. It highlights a theoretical framework that categorizes different states of privacy and emphasizes the importance of individual preferences and social structures. Additionally, it raises questions about decision-making in social contexts and explores technology's role in managing identifiable information.
1 of 37
Download to read offline



























Ad
Recommended
Resume harris 19
Resume harris 19NickHarris84
?
Nick Harris has experience working as a Congressional Fellow in the office of Rep. Michael McCaul, where he managed incoming communications and provided research and analysis. He has a COMPTIA Security+ certification demonstrating skills in areas like access control, cryptography, and cyber forensics. Harris earned an AS in Cybersecurity and Digital Forensics from Rose State College and a BA in International Security Studies from the University of Oklahoma. He also has skills in Python scripting, TCP/IP protocols, asymmetric cryptography, penetration testing, and vulnerability testing with tools like Nmap, Nessus, and Metasploit.Resume harris 19
Resume harris 19NickHarris84
?
Nick Harris has experience working as a Congressional Fellow in the office of Rep. Michael McCaul, where he managed communications, maintained public relations content, and handled sensitive data. He has a COMPTIA Security+ certification demonstrating skills in areas like cryptography, forensics, and risk management. Harris earned an AS in Cybersecurity from Rose State College and a BA in International Security Studies from the University of Oklahoma, and also speaks intermediate Russian and has experience studying abroad in Russia.Cybertech
CybertechChuck Brooks
?
Charles Brooks serves as Vice President and Client Executive for the Department of Homeland Security at Xerox. He has extensive experience in senior executive management, government relations, research and development, and business development. Previously, he served as the first Director of Legislative Affairs for the Science & Technology Directorate at DHS and was a Senior Advisor to Senator Arlen Specter, covering issues related to foreign affairs, business, and technology. Chuck also taught graduate courses on homeland security and Congress at Johns Hopkins University. He holds a Master's degree from the University of Chicago and a Bachelor's degree from DePauw University.Galway
GalwayColleen Krupski
?
Galway, New York is a quiet, rural town located north of Albany with rolling hills, farmland, and Galway Lake. As of 2000, the town had a population of 3,589 with an average income of $55,000. Most homes are well-maintained single family homes located on large plots of land. The village of Galway contains local businesses and services including a bank, post office, stores, and school. While the community and natural surroundings are well-kept, the town lacks many modern services and amenities, presenting challenges for residents.Galway ESC CH
Galway ESC CHColleen Krupski
?
Galway, New York is a rural town of 3,589 residents located north of Albany. It is characterized by rolling farmland and hills, private homes on large plots of land or acreage, and Sacandaga Lake. Residents enjoy the small town's natural beauty, strong school system, and safe, friendly atmosphere. However, the lack of modern services like public transportation, large employers, medical clinics, broadband internet, and gathering spaces for teens and seniors presents challenges for the community.Red Light Jam
Red Light JamAditya Arnoldi
?
This document proposes solutions to reduce boredom while waiting at traffic lights in Jakarta. It suggests providing shelters at intersections, having performers entertain people, and creating an app that notifies users when the light will change. The app would include a QR code on traffic lights that directs people to download it. It would then announce instructions to road users through speakers shaped like birds. The overall goal is to reduce boredom and encourage people to wait for lights safely at the proper stopping locations.trololo
trololotrollollo
?
This document provides tips for capturing an audience's attention through facial expressions and gestures. It recommends beginning with a friendly hello face, then making an appreciative "happy to meet you" face. Next, the document suggests breaking the ice by telling a joke and laughing at the punchline. It advises feeling gratitude for the audience's response before surprising them by changing tactics and adopting an authoritative expression. Finally, it recommends putting the audience at ease again and using the experience to teach them confidently walking.Ppt
Ppttomo14
?
The document provides tips for small business owners to better manage their money. It recommends setting aside money from each payment received to pay taxes quarterly instead of waiting until they are due. Tracking all expenditures personally and professionally is also advised so spending habits are known. Proper money management is an important skill that boosts confidence and success for business owners.§ĺ§é§Ö§Ň§ß§í§Ö §Ü§ĺ§â§ă§í §á§ŕ Microsoft?
§ĺ§é§Ö§Ň§ß§í§Ö §Ü§ĺ§â§ă§í §á§ŕ Microsoft?§°§Ý§î§Ô§Ń §©§Ń§Ó§î§ń§Ý§ŕ§Ó§Ń
?
§Ą§ŕ§Ü§ĺ§Ţ§Ö§ß§ä §á§â§Ö§Ő§ă§ä§Ń§Ó§Ý§ń§Ö§ä §ĺ§é§Ö§Ň§ß§í§Ű §Ü§ĺ§â§ă §á§ŕ §Ú§ă§á§ŕ§Ý§î§Ů§ŕ§Ó§Ń§ß§Ú§đ §ę§Ń§Ň§Ý§ŕ§ß§ŕ§Ó §Ó Microsoft Office Word 2007, §ŕ§Ň§ĺ§é§Ń§đ§ë§Ú§Ű §á§ŕ§Ý§î§Ů§ŕ§Ó§Ń§ä§Ö§Ý§Ö§Ű §ď§ć§ć§Ö§Ü§ä§Ú§Ó§ß§ŕ §ă§ŕ§Ů§Ő§Ń§Ó§Ń§ä§î §Ú §ß§Ń§ă§ä§â§Ń§Ú§Ó§Ń§ä§î §Ő§ŕ§Ü§ĺ§Ţ§Ö§ß§ä§í. §¬§ĺ§â§ă §Ó§Ü§Ý§đ§é§Ń§Ö§ä §á§â§Ń§Ü§ä§Ú§é§Ö§ă§Ü§Ú§Ö §Ů§Ń§Ő§Ń§ß§Ú§ń, §ä§Ö§ă§ä§í §Ú §á§ŕ§ę§Ń§Ô§ŕ§Ó§í§Ö §Ú§ß§ă§ä§â§ĺ§Ü§č§Ú§Ú §á§ŕ §á§ŕ§Ú§ă§Ü§ĺ, §ă§ŕ§Ů§Ő§Ń§ß§Ú§đ §Ú §â§Ö§Ő§Ń§Ü§ä§Ú§â§ŕ§Ó§Ń§ß§Ú§đ §ę§Ń§Ň§Ý§ŕ§ß§ŕ§Ó. §°§ă§ß§ŕ§Ó§ß§Ń§ń §č§Ö§Ý§î - §á§ŕ§Ţ§ŕ§é§î §á§ŕ§Ý§î§Ů§ŕ§Ó§Ń§ä§Ö§Ý§ń§Ţ §ď§Ü§ŕ§ß§ŕ§Ţ§Ú§ä§î §Ó§â§Ö§Ţ§ń §Ú §á§ŕ§Ó§í§ă§Ú§ä§î §á§â§ŕ§Ő§ĺ§Ü§ä§Ú§Ó§ß§ŕ§ă§ä§î §á§â§Ú §â§Ń§Ň§ŕ§ä§Ö §ă §Ő§ŕ§Ü§ĺ§Ţ§Ö§ß§ä§Ń§Ţ§Ú.§Ţ§ŕ§Ő§ĺ§Ý§î 3§Ń
§Ţ§ŕ§Ő§ĺ§Ý§î 3§Ń§°§Ý§î§Ô§Ń §©§Ń§Ó§î§ń§Ý§ŕ§Ó§Ń
?
§Ą§ŕ§Ü§ĺ§Ţ§Ö§ß§ä §ŕ§á§Ú§ă§í§Ó§Ń§Ö§ä §Ţ§Ö§ä§ŕ§Ő§í §â§Ń§Ů§â§Ń§Ň§ŕ§ä§Ü§Ú §Ú§ß§ć§ŕ§â§Ţ§Ń§č§Ú§ŕ§ß§ß§ŕ§Ô§ŕ §Ţ§Ń§ä§Ö§â§Ú§Ń§Ý§Ń §Ő§Ý§ń §Ő§Ú§ă§ä§Ń§ß§č§Ú§ŕ§ß§ß§ŕ§Ô§ŕ §Ü§ĺ§â§ă§Ń, §Ó§Ü§Ý§đ§é§Ń§ń §â§Ń§Ů§Ý§Ú§é§ß§í§Ö §ć§ŕ§â§Ţ§Ń§ä§í §á§â§Ö§Ő§ă§ä§Ń§Ó§Ý§Ö§ß§Ú§ń, §ä§Ń§Ü§Ú§Ö §Ü§Ń§Ü §Ó§Ú§Ő§Ö§ŕ§â§ŕ§Ý§Ú§Ü§Ú, §Ń§ĺ§Ő§Ú§ŕ§â§ŕ§Ý§Ú§Ü§Ú, §â§Ú§ă§ĺ§ß§Ü§Ú §Ú §ä§Ö§Ü§ă§ä. §˛§Ń§ă§ă§Ţ§Ń§ä§â§Ú§Ó§Ń§đ§ä§ă§ń §á§â§Ö§Ú§Ţ§ĺ§ë§Ö§ă§ä§Ó§Ń §Ô§â§Ń§ć§Ú§é§Ö§ă§Ü§ŕ§Ô§ŕ §ă§á§ŕ§ă§ŕ§Ň§Ń, §ä§Ń§Ü§Ú§Ö §Ü§Ń§Ü §ĺ§Ý§ĺ§é§ę§Ö§ß§Ú§Ö §Ó§ŕ§ă§á§â§Ú§ń§ä§Ú§ń §Ú §Ô§Ö§ß§Ö§â§Ń§č§Ú§ń §Ú§Ő§Ö§Ű, §Ń §ä§Ń§Ü§Ř§Ö §á§â§Ú§Ó§ŕ§Ő§ń§ä§ă§ń §á§â§Ú§Ţ§Ö§â§í §Ô§â§Ń§ć§Ú§é§Ö§ă§Ü§Ú§ç §ă§ç§Ö§Ţ, §ä§Ń§Ü§Ú§ç §Ü§Ń§Ü §Ő§Ú§Ń§Ô§â§Ń§Ţ§Ţ§í §Ó§Ö§ß§ß§Ń §Ú §Ţ§Ö§ß§ä§Ń§Ý§î§ß§í§Ö §Ü§Ń§â§ä§í. §Ł §Ü§ŕ§ß§č§Ö §Ő§ŕ§Ü§ĺ§Ţ§Ö§ß§ä§Ń §á§â§Ö§Ő§ă§ä§Ń§Ó§Ý§Ö§ß§ŕ §Ů§Ń§Ő§Ń§ß§Ú§Ö §ß§Ń §â§Ń§Ů§â§Ń§Ň§ŕ§ä§Ü§ĺ §ĺ§é§Ö§Ň§ß§ŕ§Ô§ŕ §ď§Ý§Ö§Ţ§Ö§ß§ä§Ń §ă §Ú§ă§á§ŕ§Ý§î§Ů§ŕ§Ó§Ń§ß§Ú§Ö§Ţ §Ô§â§Ń§ć§Ú§é§Ö§ă§Ü§Ú§ç §ă§ç§Ö§Ţ.BP presentation by Shih-Kai ou
BP presentation by Shih-Kai ouĘË„P ÖÜ
?
This document summarizes a presentation given by Shih-Kai Chou on an apparatus for continuous purification of household wastewater using solar power. The presentation discusses the business opportunity in wastewater treatment using solar energy. It describes the product, which uses various components like a shock absorber and reflective materials to distill wastewater into purified water using only solar power. Financial projections through 2016 show increasing sales and profits.mozzarella stuffed meatball
mozzarella stuffed meatballyakslope25
?
This document provides recipes for three types of meatballs:
1) Simple beef meatballs made from ground beef, tomato, onion, herbs and eggs that are simmered in a tomato sauce.
2) Swedish meatballs made from ground beef and/or pork, breadcrumbs, onions, white pepper and salt, and usually served with gravy, potatoes and lingonberry jam.
3) Stuffed meatballs made from ground meat filled with hard boiled egg pieces, and browned then simmered in tomato sauce.Love chloe 16013434_assignment2
Love chloe 16013434_assignment2chloelove1992
?
The document describes Mr. Rabbit's Counting Game, an educational game to help primary school children with number patterns involving 1s, 2s, 3s, 5s, and 10s. The game involves students answering questions about number sequences and patterns and earning carrots for correct answers. It concludes with contact information for technical support for any issues with the game.Normas ovos e derivadosThiago Portes
?
Este documento fornece diretrizes para estabelecimentos que processam ovos e derivados, cobrindo sua classifica??o, caracter¨Şsticas necess¨˘rias, localiza??o, instala??es e requisitos de higiene. Estabelece normas para granjas av¨Şcolas, entrepostos de ovos, f¨˘bricas de conservas de ovos e outros tipos de instala??es. Detalha requisitos para pisos, paredes, portas, ilumina??o, ventila??o e abastecimento de ¨˘gua desses estabelecimentos.Jobs plan - Bob Filner
Jobs plan - Bob FilnerBobFilnerforMayor
?
The document proposes a plan to create jobs in San Diego by growing what it calls the "Aqua Economy". The plan aims to create 6,000 jobs in the Aqua Economy by 2020 by bringing more public and private investment to the Port of San Diego and increasing the competitiveness of the region's maritime trade and cruise ship industries. The Aqua Economy combines "green" sectors like alternative energy with "blue" sectors including maritime trade, shipbuilding, and ocean research. The plan identifies 5 strategic areas to focus on, including taking advantage of the region's location on the Pacific Rim to increase international trade opportunities.Be cse
Be cseimamruta
?
The document provides details of the revised syllabus for 7th and 8th semesters of the B.E. Computer Science & Engineering program at Shivaji University, Kolhapur.
It lists the subjects to be taught in each semester along with their course codes, number of lecture hours, tutorials, practical sessions and marks distribution. Elective subjects are also specified for semesters 7 and 8. Guidelines for term work, project work, assignments and assessments are outlined. The syllabus for individual subjects like Advanced Computer Architecture, Distributed Systems and Advanced Database Systems are briefly described in terms of topics to be covered.Privacy and Surveillance
Privacy and SurveillanceIrem Gokce Aydin
?
The document discusses the impact of technology on personal privacy and the role of policies in protecting individual information in the digital age. It examines key concepts such as digital rights, surveillance, and solutions for privacy concerns, highlighting the importance of privacy for democracy and freedom of expression. Additionally, it addresses challenges in regulation and the future of internet freedom, emphasizing the need for a coordinated global response to safeguard privacy.Chapter 3
Chapter 3Jennifer Polack
?
The document discusses several topics related to ethics and privacy when dealing with information technology:
1. It introduces four common ethical frameworks used to evaluate decisions: utilitarian, rights-based, fairness-based, and common good approaches.
2. It outlines some fundamental tenets of ethics like responsibility, accountability, and liability that are important in a corporate environment.
3. It identifies four general categories of ethical issues related to IT: privacy, accuracy, property, and accessibility. It provides examples of issues that fall under each category.
4. It focuses specifically on privacy issues, outlining concerns around electronic surveillance, personal information in databases, information shared online, and international differences in privacy laws and standards.Secure Software Design for Data Privacy
Secure Software Design for Data PrivacyNarudom Roongsiriwong, CISSP
?
The document discusses secure software design principles focused on data privacy, outlining the foundational principles of privacy by design and rules for data collection. It emphasizes concepts such as least privilege, separation of duties, and various cryptographic techniques for maintaining confidentiality and integrity of data. Additionally, it covers data anonymization and pseudonymization methods to protect personal information while allowing for necessary data processing.The role and value of making data inventories
The role and value of making data inventoriesOpen Knowledge Belgium
?
The document discusses the significance of data inventories in achieving mature data governance, emphasizing the need for transparency and effective data management in local governments. It outlines the challenges posed by privacy regulations like GDPR and the inefficiencies of current data security practices, advocating for an 'open by design' approach. Additionally, it highlights the importance of engaging various stakeholders in the data inventory process to foster better communication and improve policy outcomes.Matching Uses and Protections for Government Data Releases: Presentation at t...
Matching Uses and Protections for Government Data Releases: Presentation at t...Micah Altman
?
This document discusses the alignment of data protection methods with research uses, using the American Community Survey as a case study. It emphasizes the need for tiered access to government data to balance research needs with privacy concerns and outlines various methodologies for characterizing data analysis. The paper also suggests that existing privacy controls may not adequately address the risks associated with high-dimensional and high-frequency data.Cyber Summit 2016: Privacy Issues in Big Data Sharing and Reuse
Cyber Summit 2016: Privacy Issues in Big Data Sharing and ReuseCybera Inc.
?
This document summarizes a presentation on big data and data reuse given by Bart Custers. It discusses:
1) The Eudeco project which examines big data and data reuse from legal, societal, economic, and technological perspectives across multiple European countries.
2) Issues with data sharing and reuse, including potential privacy violations, discrimination, lack of transparency, and unintended consequences from new uses of data or placing it in new contexts.
3) Potential solutions discussed, including privacy impact assessments, privacy by design, and new approaches focusing more on transparency and responsibility than restricting data access and use.Privacy and data protection primer - City of Portland
Privacy and data protection primer - City of PortlandHector Dominguez
?
The document discusses the concept of privacy and data protection, highlighting the 'privacy paradox' where individuals both fear data misuse and willingly share their information. It outlines the definition of personally identifiable information (PII), the importance of data protection versus data privacy, and principles for building trust through informed consent and privacy by design. The document also addresses risks associated with data management and emphasizes the need for active engagement in achieving privacy in a networked environment.417_AI_Handbook_Class9-74-106 .pdf
417_AI_Handbook_Class9-74-106 .pdfpescbse9it1
?
detailed presentation based on the content provided with relevant explanation.PP Lec9n10 Sp2020.pptx
PP Lec9n10 Sp2020.pptxMuhammadAbdullah201796
?
This document discusses several key aspects of privacy and how they relate to computer technology. It begins by defining privacy and information privacy. It then examines how computer technologies like databases, cameras, social media, and location tracking have changed people's ability to access and use personal information. It outlines several privacy threats like intentional and unauthorized use of data, data theft, and inadvertent information leakage. The document also explores new risks from tools like surveillance, data analysis, cloud computing and vulnerabilities in data security. It discusses how personal information can now be gathered invisibly through things like cookies and device fingerprints. Key issues discussed include secondary use of data, data mining/matching/profiling and identity theft. The document concludes by examining principles of informedUN Global Pulse Privacy Framing
UN Global Pulse Privacy FramingMicah Altman
?
This document provides an overview of key concepts related to privacy, security, and big data. It discusses how easily private information can be leaked, different types of identifiability, how sensitive information can be if reidentified, and core concepts of privacy and security. It also covers security modeling, proposed privacy principles, challenges of big data, emerging approaches for big data, and the importance of lifecycle evaluation of data collection and use. The document aims to provide framing and guidance around privacy and security issues for big data.Attacking Decentralized Identity.pdf
Attacking Decentralized Identity.pdfssuser264cc11
?
Decentralized identity aims to give users control over their digital identities and data. However, decentralized identity systems also introduce new attack surfaces. Attackers could abuse protocols to access sensitive user data or present fake credentials. Successful attacks could undermine user trust and adoption of decentralized identity. Ongoing research and adoption of security best practices are needed to strengthen decentralized identity systems against current and future threats.More Related Content
Viewers also liked (11)
§ĺ§é§Ö§Ň§ß§í§Ö §Ü§ĺ§â§ă§í §á§ŕ Microsoft?
§ĺ§é§Ö§Ň§ß§í§Ö §Ü§ĺ§â§ă§í §á§ŕ Microsoft?§°§Ý§î§Ô§Ń §©§Ń§Ó§î§ń§Ý§ŕ§Ó§Ń
?
§Ą§ŕ§Ü§ĺ§Ţ§Ö§ß§ä §á§â§Ö§Ő§ă§ä§Ń§Ó§Ý§ń§Ö§ä §ĺ§é§Ö§Ň§ß§í§Ű §Ü§ĺ§â§ă §á§ŕ §Ú§ă§á§ŕ§Ý§î§Ů§ŕ§Ó§Ń§ß§Ú§đ §ę§Ń§Ň§Ý§ŕ§ß§ŕ§Ó §Ó Microsoft Office Word 2007, §ŕ§Ň§ĺ§é§Ń§đ§ë§Ú§Ű §á§ŕ§Ý§î§Ů§ŕ§Ó§Ń§ä§Ö§Ý§Ö§Ű §ď§ć§ć§Ö§Ü§ä§Ú§Ó§ß§ŕ §ă§ŕ§Ů§Ő§Ń§Ó§Ń§ä§î §Ú §ß§Ń§ă§ä§â§Ń§Ú§Ó§Ń§ä§î §Ő§ŕ§Ü§ĺ§Ţ§Ö§ß§ä§í. §¬§ĺ§â§ă §Ó§Ü§Ý§đ§é§Ń§Ö§ä §á§â§Ń§Ü§ä§Ú§é§Ö§ă§Ü§Ú§Ö §Ů§Ń§Ő§Ń§ß§Ú§ń, §ä§Ö§ă§ä§í §Ú §á§ŕ§ę§Ń§Ô§ŕ§Ó§í§Ö §Ú§ß§ă§ä§â§ĺ§Ü§č§Ú§Ú §á§ŕ §á§ŕ§Ú§ă§Ü§ĺ, §ă§ŕ§Ů§Ő§Ń§ß§Ú§đ §Ú §â§Ö§Ő§Ń§Ü§ä§Ú§â§ŕ§Ó§Ń§ß§Ú§đ §ę§Ń§Ň§Ý§ŕ§ß§ŕ§Ó. §°§ă§ß§ŕ§Ó§ß§Ń§ń §č§Ö§Ý§î - §á§ŕ§Ţ§ŕ§é§î §á§ŕ§Ý§î§Ů§ŕ§Ó§Ń§ä§Ö§Ý§ń§Ţ §ď§Ü§ŕ§ß§ŕ§Ţ§Ú§ä§î §Ó§â§Ö§Ţ§ń §Ú §á§ŕ§Ó§í§ă§Ú§ä§î §á§â§ŕ§Ő§ĺ§Ü§ä§Ú§Ó§ß§ŕ§ă§ä§î §á§â§Ú §â§Ń§Ň§ŕ§ä§Ö §ă §Ő§ŕ§Ü§ĺ§Ţ§Ö§ß§ä§Ń§Ţ§Ú.§Ţ§ŕ§Ő§ĺ§Ý§î 3§Ń
§Ţ§ŕ§Ő§ĺ§Ý§î 3§Ń§°§Ý§î§Ô§Ń §©§Ń§Ó§î§ń§Ý§ŕ§Ó§Ń
?
§Ą§ŕ§Ü§ĺ§Ţ§Ö§ß§ä §ŕ§á§Ú§ă§í§Ó§Ń§Ö§ä §Ţ§Ö§ä§ŕ§Ő§í §â§Ń§Ů§â§Ń§Ň§ŕ§ä§Ü§Ú §Ú§ß§ć§ŕ§â§Ţ§Ń§č§Ú§ŕ§ß§ß§ŕ§Ô§ŕ §Ţ§Ń§ä§Ö§â§Ú§Ń§Ý§Ń §Ő§Ý§ń §Ő§Ú§ă§ä§Ń§ß§č§Ú§ŕ§ß§ß§ŕ§Ô§ŕ §Ü§ĺ§â§ă§Ń, §Ó§Ü§Ý§đ§é§Ń§ń §â§Ń§Ů§Ý§Ú§é§ß§í§Ö §ć§ŕ§â§Ţ§Ń§ä§í §á§â§Ö§Ő§ă§ä§Ń§Ó§Ý§Ö§ß§Ú§ń, §ä§Ń§Ü§Ú§Ö §Ü§Ń§Ü §Ó§Ú§Ő§Ö§ŕ§â§ŕ§Ý§Ú§Ü§Ú, §Ń§ĺ§Ő§Ú§ŕ§â§ŕ§Ý§Ú§Ü§Ú, §â§Ú§ă§ĺ§ß§Ü§Ú §Ú §ä§Ö§Ü§ă§ä. §˛§Ń§ă§ă§Ţ§Ń§ä§â§Ú§Ó§Ń§đ§ä§ă§ń §á§â§Ö§Ú§Ţ§ĺ§ë§Ö§ă§ä§Ó§Ń §Ô§â§Ń§ć§Ú§é§Ö§ă§Ü§ŕ§Ô§ŕ §ă§á§ŕ§ă§ŕ§Ň§Ń, §ä§Ń§Ü§Ú§Ö §Ü§Ń§Ü §ĺ§Ý§ĺ§é§ę§Ö§ß§Ú§Ö §Ó§ŕ§ă§á§â§Ú§ń§ä§Ú§ń §Ú §Ô§Ö§ß§Ö§â§Ń§č§Ú§ń §Ú§Ő§Ö§Ű, §Ń §ä§Ń§Ü§Ř§Ö §á§â§Ú§Ó§ŕ§Ő§ń§ä§ă§ń §á§â§Ú§Ţ§Ö§â§í §Ô§â§Ń§ć§Ú§é§Ö§ă§Ü§Ú§ç §ă§ç§Ö§Ţ, §ä§Ń§Ü§Ú§ç §Ü§Ń§Ü §Ő§Ú§Ń§Ô§â§Ń§Ţ§Ţ§í §Ó§Ö§ß§ß§Ń §Ú §Ţ§Ö§ß§ä§Ń§Ý§î§ß§í§Ö §Ü§Ń§â§ä§í. §Ł §Ü§ŕ§ß§č§Ö §Ő§ŕ§Ü§ĺ§Ţ§Ö§ß§ä§Ń §á§â§Ö§Ő§ă§ä§Ń§Ó§Ý§Ö§ß§ŕ §Ů§Ń§Ő§Ń§ß§Ú§Ö §ß§Ń §â§Ń§Ů§â§Ń§Ň§ŕ§ä§Ü§ĺ §ĺ§é§Ö§Ň§ß§ŕ§Ô§ŕ §ď§Ý§Ö§Ţ§Ö§ß§ä§Ń §ă §Ú§ă§á§ŕ§Ý§î§Ů§ŕ§Ó§Ń§ß§Ú§Ö§Ţ §Ô§â§Ń§ć§Ú§é§Ö§ă§Ü§Ú§ç §ă§ç§Ö§Ţ.BP presentation by Shih-Kai ou
BP presentation by Shih-Kai ouĘË„P ÖÜ
?
This document summarizes a presentation given by Shih-Kai Chou on an apparatus for continuous purification of household wastewater using solar power. The presentation discusses the business opportunity in wastewater treatment using solar energy. It describes the product, which uses various components like a shock absorber and reflective materials to distill wastewater into purified water using only solar power. Financial projections through 2016 show increasing sales and profits.mozzarella stuffed meatball
mozzarella stuffed meatballyakslope25
?
This document provides recipes for three types of meatballs:
1) Simple beef meatballs made from ground beef, tomato, onion, herbs and eggs that are simmered in a tomato sauce.
2) Swedish meatballs made from ground beef and/or pork, breadcrumbs, onions, white pepper and salt, and usually served with gravy, potatoes and lingonberry jam.
3) Stuffed meatballs made from ground meat filled with hard boiled egg pieces, and browned then simmered in tomato sauce.Love chloe 16013434_assignment2
Love chloe 16013434_assignment2chloelove1992
?
The document describes Mr. Rabbit's Counting Game, an educational game to help primary school children with number patterns involving 1s, 2s, 3s, 5s, and 10s. The game involves students answering questions about number sequences and patterns and earning carrots for correct answers. It concludes with contact information for technical support for any issues with the game.Normas ovos e derivadosThiago Portes
?
Este documento fornece diretrizes para estabelecimentos que processam ovos e derivados, cobrindo sua classifica??o, caracter¨Şsticas necess¨˘rias, localiza??o, instala??es e requisitos de higiene. Estabelece normas para granjas av¨Şcolas, entrepostos de ovos, f¨˘bricas de conservas de ovos e outros tipos de instala??es. Detalha requisitos para pisos, paredes, portas, ilumina??o, ventila??o e abastecimento de ¨˘gua desses estabelecimentos.Jobs plan - Bob Filner
Jobs plan - Bob FilnerBobFilnerforMayor
?
The document proposes a plan to create jobs in San Diego by growing what it calls the "Aqua Economy". The plan aims to create 6,000 jobs in the Aqua Economy by 2020 by bringing more public and private investment to the Port of San Diego and increasing the competitiveness of the region's maritime trade and cruise ship industries. The Aqua Economy combines "green" sectors like alternative energy with "blue" sectors including maritime trade, shipbuilding, and ocean research. The plan identifies 5 strategic areas to focus on, including taking advantage of the region's location on the Pacific Rim to increase international trade opportunities.Be cse
Be cseimamruta
?
The document provides details of the revised syllabus for 7th and 8th semesters of the B.E. Computer Science & Engineering program at Shivaji University, Kolhapur.
It lists the subjects to be taught in each semester along with their course codes, number of lecture hours, tutorials, practical sessions and marks distribution. Elective subjects are also specified for semesters 7 and 8. Guidelines for term work, project work, assignments and assessments are outlined. The syllabus for individual subjects like Advanced Computer Architecture, Distributed Systems and Advanced Database Systems are briefly described in terms of topics to be covered.Similar to Kosa - Theory for Privacy Measuring v2 (20)
Privacy and Surveillance
Privacy and SurveillanceIrem Gokce Aydin
?
The document discusses the impact of technology on personal privacy and the role of policies in protecting individual information in the digital age. It examines key concepts such as digital rights, surveillance, and solutions for privacy concerns, highlighting the importance of privacy for democracy and freedom of expression. Additionally, it addresses challenges in regulation and the future of internet freedom, emphasizing the need for a coordinated global response to safeguard privacy.Chapter 3
Chapter 3Jennifer Polack
?
The document discusses several topics related to ethics and privacy when dealing with information technology:
1. It introduces four common ethical frameworks used to evaluate decisions: utilitarian, rights-based, fairness-based, and common good approaches.
2. It outlines some fundamental tenets of ethics like responsibility, accountability, and liability that are important in a corporate environment.
3. It identifies four general categories of ethical issues related to IT: privacy, accuracy, property, and accessibility. It provides examples of issues that fall under each category.
4. It focuses specifically on privacy issues, outlining concerns around electronic surveillance, personal information in databases, information shared online, and international differences in privacy laws and standards.Secure Software Design for Data Privacy
Secure Software Design for Data PrivacyNarudom Roongsiriwong, CISSP
?
The document discusses secure software design principles focused on data privacy, outlining the foundational principles of privacy by design and rules for data collection. It emphasizes concepts such as least privilege, separation of duties, and various cryptographic techniques for maintaining confidentiality and integrity of data. Additionally, it covers data anonymization and pseudonymization methods to protect personal information while allowing for necessary data processing.The role and value of making data inventories
The role and value of making data inventoriesOpen Knowledge Belgium
?
The document discusses the significance of data inventories in achieving mature data governance, emphasizing the need for transparency and effective data management in local governments. It outlines the challenges posed by privacy regulations like GDPR and the inefficiencies of current data security practices, advocating for an 'open by design' approach. Additionally, it highlights the importance of engaging various stakeholders in the data inventory process to foster better communication and improve policy outcomes.Matching Uses and Protections for Government Data Releases: Presentation at t...
Matching Uses and Protections for Government Data Releases: Presentation at t...Micah Altman
?
This document discusses the alignment of data protection methods with research uses, using the American Community Survey as a case study. It emphasizes the need for tiered access to government data to balance research needs with privacy concerns and outlines various methodologies for characterizing data analysis. The paper also suggests that existing privacy controls may not adequately address the risks associated with high-dimensional and high-frequency data.Cyber Summit 2016: Privacy Issues in Big Data Sharing and Reuse
Cyber Summit 2016: Privacy Issues in Big Data Sharing and ReuseCybera Inc.
?
This document summarizes a presentation on big data and data reuse given by Bart Custers. It discusses:
1) The Eudeco project which examines big data and data reuse from legal, societal, economic, and technological perspectives across multiple European countries.
2) Issues with data sharing and reuse, including potential privacy violations, discrimination, lack of transparency, and unintended consequences from new uses of data or placing it in new contexts.
3) Potential solutions discussed, including privacy impact assessments, privacy by design, and new approaches focusing more on transparency and responsibility than restricting data access and use.Privacy and data protection primer - City of Portland
Privacy and data protection primer - City of PortlandHector Dominguez
?
The document discusses the concept of privacy and data protection, highlighting the 'privacy paradox' where individuals both fear data misuse and willingly share their information. It outlines the definition of personally identifiable information (PII), the importance of data protection versus data privacy, and principles for building trust through informed consent and privacy by design. The document also addresses risks associated with data management and emphasizes the need for active engagement in achieving privacy in a networked environment.417_AI_Handbook_Class9-74-106 .pdf
417_AI_Handbook_Class9-74-106 .pdfpescbse9it1
?
detailed presentation based on the content provided with relevant explanation.PP Lec9n10 Sp2020.pptx
PP Lec9n10 Sp2020.pptxMuhammadAbdullah201796
?
This document discusses several key aspects of privacy and how they relate to computer technology. It begins by defining privacy and information privacy. It then examines how computer technologies like databases, cameras, social media, and location tracking have changed people's ability to access and use personal information. It outlines several privacy threats like intentional and unauthorized use of data, data theft, and inadvertent information leakage. The document also explores new risks from tools like surveillance, data analysis, cloud computing and vulnerabilities in data security. It discusses how personal information can now be gathered invisibly through things like cookies and device fingerprints. Key issues discussed include secondary use of data, data mining/matching/profiling and identity theft. The document concludes by examining principles of informedUN Global Pulse Privacy Framing
UN Global Pulse Privacy FramingMicah Altman
?
This document provides an overview of key concepts related to privacy, security, and big data. It discusses how easily private information can be leaked, different types of identifiability, how sensitive information can be if reidentified, and core concepts of privacy and security. It also covers security modeling, proposed privacy principles, challenges of big data, emerging approaches for big data, and the importance of lifecycle evaluation of data collection and use. The document aims to provide framing and guidance around privacy and security issues for big data.Attacking Decentralized Identity.pdf
Attacking Decentralized Identity.pdfssuser264cc11
?
Decentralized identity aims to give users control over their digital identities and data. However, decentralized identity systems also introduce new attack surfaces. Attackers could abuse protocols to access sensitive user data or present fake credentials. Successful attacks could undermine user trust and adoption of decentralized identity. Ongoing research and adoption of security best practices are needed to strengthen decentralized identity systems against current and future threats.Geographic data uncertainty
Geographic data uncertaintyJayanthaSamarasinghe1
?
The document discusses geographic data uncertainty and its impact on decision-making processes, detailing various facets of uncertainty that arise from data quality and interpretation. It presents a model of decision-making that encompasses documentation, analysis, taking, implementation, and evaluation phases, highlighting the continuous presence of uncertainty throughout these steps. Additionally, it emphasizes the ethical responsibilities associated with data quality, advocating for the use of safeguards and adherence to professional codes of ethics to mitigate risks.Mobile Devices: Systemisation of Knowledge about Privacy Invasion Tactics and...
Mobile Devices: Systemisation of Knowledge about Privacy Invasion Tactics and...CREST
?
The document discusses the privacy risks associated with mobile devices, emphasizing the extensive data that can be tracked or misused, including personal mobility traces and device-specific information. It highlights systematic reviews as a methodology for synthesizing research on privacy invasion tactics and countermeasures, while also presenting various privacy preservation strategies, such as anonymization and data encryption. The concluding remarks stress the necessity for user empowerment, training in privacy engineering, and the development of automated technologies for protecting data.Luciano uvi hackfest.28.10.2020
Luciano uvi hackfest.28.10.2020Joanne Luciano
?
The document provides an overview of an event on emerging trends in data science given by Dr. Joanne Luciano. It discusses the data science workflow and various processes involved. Some key trends highlighted include increased use of AI and machine learning in data management and reporting, growth of natural language processing, advances in deep learning, emphasis on data privacy and ethics. The document also promotes the new minor in data science offered at University of the Virgin Islands, covering required courses and examples of course sequences for different disciplines.Privacy Secrets Your Systems May Be Telling
Privacy Secrets Your Systems May Be TellingSecurity Innovation
?
This document summarizes a webinar on privacy secrets and how systems can reveal personal information. It discusses defining privacy, the seven types of privacy, and the differences between privacy and security. It also covers threats to privacy like big data, location tracking, and metadata analysis. The webinar examines data types like PII, PHI, and anonymous/pseudonymous data. It provides examples of data lifecycles and analyzing how data flows through systems and to third parties. The goal is to help organizations understand privacy risks and comply with regulations like GDPR.Privacy Secrets Your Systems May Be Telling
Privacy Secrets Your Systems May Be TellingRebecca Leitch
?
The webinar presented by Kevin Poniatowski focuses on the significance of privacy in the context of data security, outlining the various types of privacy and illustrating the importance of user control over personal data. It discusses the key drivers for investing in privacy, the threats posed by modern data practices, and the regulatory frameworks that govern data privacy. The session also emphasizes the need for organizations to understand data flows and privacy risks to ensure compliance and maintain consumer trust.Digital Forensic: Brief Intro & Research Challenge
Digital Forensic: Brief Intro & Research ChallengeAung Thu Rha Hein
?
This document provides an overview of digital forensics. It discusses what digital forensics is, examples of cases, branches of digital forensics like disk, network, and mobile forensics. It also outlines the methodology, challenges, and tools used in digital forensics. Some challenges discussed include increasing device types and file formats, data volume, and limitations of current tools to keep up with evolving technology. The document concludes that digital forensics research faces many challenges and needs a clear research agenda to address issues like investigation time, cloud computing, and encryption.Data Science at Intersection of Security and Privacy
Data Science at Intersection of Security and PrivacyTarun Chopra
?
This document discusses balancing security and privacy through data science. It provides context on security and privacy, describing them as similar but different concepts. It also describes facets of privacy like anonymity and pseudonymity. The document examines how data science techniques like statistical analysis, machine learning, and predictive analytics can impact both privacy and security. It provides examples of how these techniques can help or harm privacy and security goals. Finally, it recommends that organizations understand their data and capabilities, follow guidance like NIST 800-53, and continuously monitor developments to balance privacy and security appropriately.Lecture 4,5, 6 comp forensics 19 9-2018 basic security
Lecture 4,5, 6 comp forensics 19 9-2018 basic securityAlchemist095
?
This document provides an overview of computer forensics. It discusses what computer forensics involves, including the collection, preservation, analysis and presentation of digital evidence. Typical computer forensic investigations include theft of company data, employee sabotage, financial crimes, and child pornography cases. The document outlines who uses computer forensics, such as law enforcement, private organizations, the military, and IT professionals. It also discusses computer forensic tools and techniques, such as recovering deleted files, and the importance of accuracy in investigations.Polina Zvyagina - Airbnb - Privacy & GDPR Compliance - Stanford Engineering -...
Polina Zvyagina - Airbnb - Privacy & GDPR Compliance - Stanford Engineering -...Burton Lee
?
The document outlines key privacy concerns faced by big tech companies, emphasizing the importance of privacy laws, data protection, and regulatory compliance. It discusses various legal frameworks and case studies highlighting costly breaches and the necessity for proactive privacy measures, such as privacy by design. Furthermore, it highlights consumer rights and the need for transparency in how companies handle personal data to maintain trust.Ad
Recently uploaded (20)
Agentic AI for Developers and Data Scientists Build an AI Agent in 10 Lines o...
Agentic AI for Developers and Data Scientists Build an AI Agent in 10 Lines o...All Things Open
?
Presented at All Things Open RTP Meetup
Presented by William Hill - Developer Advocate, NVIDIA
Title: Agentic AI for Developers and Data Scientists
Build an AI Agent in 10 Lines of Code and the Concepts Behind the Code
Abstract: In this talk we will demonstrate building a working data science AI agent in 10 lines of basic Python code in a Colab notebook. Our AI Agent will perform LLM prompt-driven visual analysis using open-source libraries. In this session we will show how to develop an AI Agent using GPUs through NVIDIAˇŻs developer program and Google Colab notebooks. After coding our AI Agent, we will break down the 10 lines of code. We will show the key components and open source library integrations that enable the agent's functionality, focusing on practical implementation details and then the theoretical concepts. The presentation concludes with a survey of current LLM technologies and the latest trends in developing AI applications for enthusiasts and enterprisesTechniques for Automatic Device Identification and Network Assignment.pdf
Techniques for Automatic Device Identification and Network Assignment.pdfPriyanka Aash
?
Techniques for Automatic Device Identification and Network AssignmentCracking the Code - Unveiling Synergies Between Open Source Security and AI.pdf
Cracking the Code - Unveiling Synergies Between Open Source Security and AI.pdfPriyanka Aash
?
Cracking the Code - Unveiling Synergies Between Open Source Security and AISmarter Aviation Data Management: Lessons from Swedavia Airports and Sweco
Smarter Aviation Data Management: Lessons from Swedavia Airports and SwecoSafe Software
?
Managing airport and airspace data is no small task, especially when youˇŻre expected to deliver it in AIXM format without spending a fortune on specialized tools. But what if there was a smarter, more affordable way?
Join us for a behind-the-scenes look at how Sweco partnered with Swedavia, the Swedish airport operator, to solve this challenge using FME and Esri.
Learn how they built automated workflows to manage periodic updates, merge airspace data, and support data extracts ¨C all while meeting strict government reporting requirements to the Civil Aviation Administration of Sweden.
Even better? Swedavia built custom services and applications that use the FME Flow REST API to trigger jobs and retrieve results ¨C streamlining tasks like securing the quality of new surveyor data, creating permdelta and baseline representations in the AIS schema, and generating AIXM extracts from their AIS data.
To conclude, FME expert Dean Hintz will walk through a GeoBorders reading workflow and highlight recent enhancements to FMEˇŻs AIXM (Aeronautical Information Exchange Model) processing and interpretation capabilities.
Discover how airports like Swedavia are harnessing the power of FME to simplify aviation data management, and how you can too.Quantum AI: Where Impossible Becomes Probable
Quantum AI: Where Impossible Becomes ProbableSaikat Basu
?
Imagine combining the "brains" of Artificial Intelligence (AI) with the "super muscles" of Quantum Computing. That's Quantum AI!
It's a new field that uses the mind-bending rules of quantum physics to make AI even more powerful.9-1-1 Addressing: End-to-End Automation Using FME
9-1-1 Addressing: End-to-End Automation Using FMESafe Software
?
This session will cover a common use case for local and state/provincial governments who create and/or maintain their 9-1-1 addressing data, particularly address points and road centerlines. In this session, you'll learn how FME has helped Shelby County 9-1-1 (TN) automate the 9-1-1 addressing process; including automatically assigning attributes from disparate sources, on-the-fly QAQC of said data, and reporting. The FME logic that this presentation will cover includes: Table joins using attributes and geometry, Looping in custom transformers, Working with lists and Change detection.From Manual to Auto Searching- FME in the Driver's Seat
From Manual to Auto Searching- FME in the Driver's SeatSafe Software
?
Finding a specific car online can be a time-consuming task, especially when checking multiple dealer websites. A few years ago, I faced this exact problem while searching for a particular vehicle in New Zealand. The local classified platform, Trade Me (similar to eBay), wasnˇŻt yielding any results, so I expanded my search to second-hand dealer sitesˇŞonly to realise that periodically checking each one was going to be tedious. ThatˇŻs when I noticed something interesting: many of these websites used the same platform to manage their inventories. Recognising this, I reverse-engineered the platformˇŻs structure and built an FME workspace that automated the search process for me. By integrating API calls and setting up periodic checks, I received real-time email alerts when matching cars were listed. In this presentation, IˇŻll walk through how I used FME to save hours of manual searching by creating a custom car-finding automation system. While FME canˇŻt buy a car for youˇŞyetˇŞit can certainly help you find the one youˇŻre after!Security Tips for Enterprise Azure Solutions
Security Tips for Enterprise Azure SolutionsMichele Leroux Bustamante
?
Delivering solutions to Azure may involve a variety of architecture patterns involving your applications, APIs data and associated Azure resources that comprise the solution. This session will use reference architectures to illustrate the security considerations to protect your Azure resources and data, how to achieve Zero Trust, and why it matters. Topics covered will include specific security recommendations for types Azure resources and related network security practices. The goal is to give you a breadth of understanding as to typical security requirements to meet compliance and security controls in an enterprise solution.OpenACC and Open Hackathons Monthly Highlights June 2025
OpenACC and Open Hackathons Monthly Highlights June 2025OpenACC
?
The OpenACC organization focuses on enhancing parallel computing skills and advancing interoperability in scientific applications through hackathons and training. The upcoming 2025 Open Accelerated Computing Summit (OACS) aims to explore the convergence of AI and HPC in scientific computing and foster knowledge sharing. This year's OACS welcomes talk submissions from a variety of topics, from Using Standard Language Parallelism to Computer Vision Applications. The document also highlights several open hackathons, a call to apply for NVIDIA Academic Grant Program and resources for optimizing scientific applications using OpenACC directives.Raman Bhaumik - Passionate Tech Enthusiast
Raman Bhaumik - Passionate Tech EnthusiastRaman Bhaumik
?
A Junior Software Developer with a flair for innovation, Raman Bhaumik excels in delivering scalable web solutions. With three years of experience and a solid foundation in Java, Python, JavaScript, and SQL, she has streamlined task tracking by 20% and improved application stability.Oh, the Possibilities - Balancing Innovation and Risk with Generative AI.pdf
Oh, the Possibilities - Balancing Innovation and Risk with Generative AI.pdfPriyanka Aash
?
Oh, the Possibilities - Balancing Innovation and Risk with Generative AIConnecting Data and Intelligence: The Role of FME in Machine Learning
Connecting Data and Intelligence: The Role of FME in Machine LearningSafe Software
?
In this presentation, we want to explore powerful data integration and preparation for Machine Learning. FME is known for its ability to manipulate and transform geospatial data, connecting diverse data sources into efficient and automated workflows. By integrating FME with Machine Learning techniques, it is possible to transform raw data into valuable insights faster and more accurately, enabling intelligent analysis and data-driven decision making.EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdf
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdfEarley Information Science
?
As AI reshapes expectations in retail and B2B commerce, organizations are recognizing a critical reality: meaningful AI outcomes depend on well-structured, adaptable infrastructure. In this session, Seth Earley is joined by Phil Ryan - AI strategist, search technologist, and founder of Glass Leopard Technologies - for a candid conversation on what it truly means to engineer systems for scale, agility, and intelligence.
Phil draws on more than two decades of experience leading search and AI initiatives for enterprise organizations. Together, he and Seth explore the challenges businesses face when legacy architectures limit personalization, agility, and real-time decisioning - and what needs to change to support agentic technologies and next-best-action capabilities.
Key themes from the webinar include:
Composability as a prerequisite for AI?- Why modular, loosely coupled systems are essential for adapting to rapid innovation and evolving business needs
Search and relevance as foundational to AI?- How techniques honed-in enterprise search have laid the groundwork for more responsive and intelligent customer experiences
From MDM and CDP to agentic systems?- How data platforms are evolving to support richer customer context and dynamic orchestration
Engineering for business alignment?- Why successful AI programs require architectural decisions grounded in measurable outcomes
The conversation is practical and forward-looking, connecting deep technical understanding with real-world business needs. Whether youˇŻre modernizing your commerce stack or exploring how AI can enhance product discovery, personalization, or customer journeys, this session provides a clear-eyed view of the capabilities, constraints, and priorities that matter most.Hyderabad MuleSoft In-Person Meetup (June 21, 2025) şÝşÝߣs
Hyderabad MuleSoft In-Person Meetup (June 21, 2025) şÝşÝߣsRavi Tamada
?
Hyderabad MuleSoft In-Person Meetup (June 21, 2025) şÝşÝߣsThe Growing Value and Application of FME & GenAI
The Growing Value and Application of FME & GenAISafe Software
?
With the cost of using Generative AI services dropping exponentially and the array of available models continually expanding, integrating AI into FME workflows has become inexpensive, accessible and effective. This presentation explores how GenAI within FME can cost-effectively transform data workflows by automating data extraction, validation, classification and augmentation tasks. WeˇŻll discuss how FMEˇŻs no-code flexibility enables users to combine Generative AI and Computer Vision tools that create efficient workflows tailored to specific challenges. Using recent practical examples, weˇŻll demonstrate how these integrations can simplify complex tasks, save time and enhance data quality.Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical Universes
Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical UniversesSaikat Basu
?
Embark on a cosmic journey exploring the intersection of quantum
computing, consciousness, and ancient wisdom. Together we'll uncover the
recursive patterns that bind our reality.You are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
?
We live in an ever evolving landscape for cyber threats creating security risk for your production systems. Mitigating these risks requires participation throughout all stages from development through production delivery - and by every role including architects, developers QA and DevOps engineers, product owners and leadership. No one is excused! This session will cover examples of common mistakes or missed opportunities that can lead to vulnerabilities in production - and ways to do better throughout the development lifecycle.AI vs Human Writing: Can You Tell the Difference?
AI vs Human Writing: Can You Tell the Difference?Shashi Sathyanarayana, Ph.D
?
This slide illustrates a side-by-side comparison between human-written, AI-written, and ambiguous content. It highlights subtle cues that help readers assess authenticity, raising essential questions about the future of communication, trust, and thought leadership in the age of generative AI.cnc-processing-centers-centateq-p-110-en.pdf
cnc-processing-centers-centateq-p-110-en.pdfAmirStern2
?
???? ??????? ??????? ??? 3/4/5 ?????, ?? 22 ?????? ???? ?? ?? ???????? ?????? ???????.???? ??? ????? ???? ????? ??? ??? ?????? ???? ??????/?????/??????/??????/????? ????..
????? ???? ?????? ????? ????? ???????? ?????? ?????: ????? ????, ?????, ?????, ?????? ????.2025_06_18 - OpenMetadata Community Meeting.pdf
2025_06_18 - OpenMetadata Community Meeting.pdfOpenMetadata
?
The community meetup was held Wednesday June 18, 2025 @ 9:00 AM PST.
Catch the next OpenMetadata Community Meetup @ https://www.meetup.com/openmetadata-meetup-group/
In this month's OpenMetadata Community Meetup, "Enforcing Quality & SLAs with OpenMetadata Data Contracts," we covered data contracts, why they matter, and how to implement them in OpenMetadata to increase the quality of your data assets!
Agenda Highlights:
? Introducing Data Contracts: An agreement between data producers and consumers
? Data Contracts key components: Understanding a contract and its purpose
??? Writing your first contract: How to create your own contracts in OpenMetadata
? An OpenMetadata MCP Server update!
? And More!You are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
?
Ad
Kosa - Theory for Privacy Measuring v2
- 12. Why Privacy?
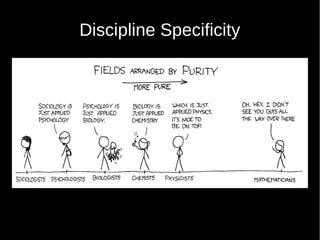
- 17. Problem ˇń Research across disciplines suffers because there is no unifed mechanism for measurement ˇń Computer science has focussed on policy enforcement, ontologies and taxonomies ˇń Nobody looks at individual privacy preferences in a given environment, which is the basis for legislation ¨C And also how requirements must be derived
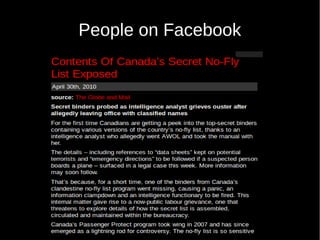
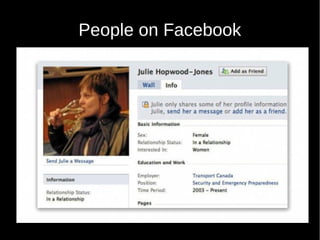
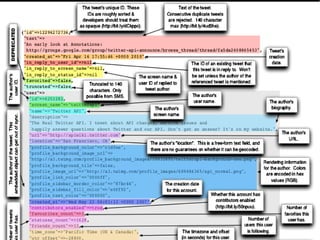
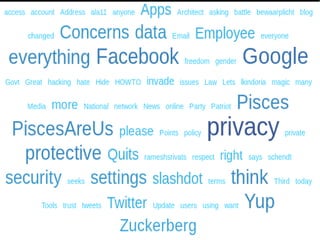
- 18. 2 Examples ˇń Facebook ˇń Twitter
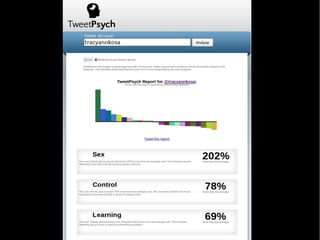
- 23. Versus
- 26. Hypothesis ˇń Disregarding the value-based approach to privacy, it's possible to dervie a finite representation based on discrete factors ˇń The representation can be used to understand privacy betteracross disciplines ¨C Standardization ¨C Measurement ¨C Management
- 27. Theoretical Framework ˇń Scientific / mathematical determinism ˇń Plus.
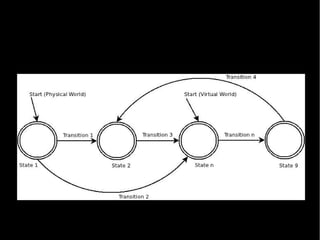
- 28. The States 1)Private: existence is unknown 2)Unidentified: presence is known 3)Anonymous: information known but no identity 4)Masked: identity linkage is concealed 5)De-identified: identity is not directly linked 6)Pseudonymous: identity is falsefied 7)Confidential: identity is known for a specific purpose 8)Identified: capable of being distinguised 9)Public: everything is known and assigned
- 30. Factors ˇń Human: considerations when privacy decisions are made ˇń Technology: services that computers perform related to information management ˇń Data Types: types of identifiable information ˇń Recepient: machine v. human ˇń Architecture: characteristics of the physical environment
- 31. Human ˇń Human privacy rules are specific to the establishment; they are reflected in the physical structure and properties of society ˇń Each individual has a social contact threshold which determines how they exercise their privacy rights ˇń Examples: ˇń Subject matter of the object ˇń Control of disclosure, information, audience ˇń Social structure and condition ˇń Visibility ˇń Expectations
- 32. Data Types ˇń Notion of privacy as information protection is well represented in legislaiton and regulation across the world ˇń Less widely used is the notion of identifiability: that data exists that may or may not include the traditional identifiers, e.g. Name, but may still uniquely identify a person ˇń What is more private: a phone number or a prescription?
- 33. Technology ˇń Computers are generally accepted to be an effective tool for information management; used to acquire, organize, retrieve, search and maintain information ˇń This happens increasingly without human intervention ˇń When it comes to managing information about an identifiable person, there are a discrete number of functions that computers can provide ˇń Examples: ˇń Network, hosting, registration, mail, website/portal, software, backup
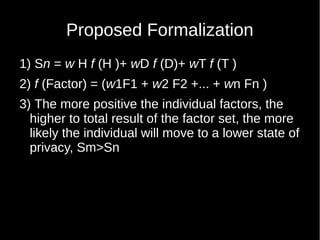
- 34. Proposed Formalization 1) Sn = w H f (H )+ wD f (D)+ wT f (T ) 2) f (Factor) = (w1F1 + w2 F2 +... + wn Fn ) 3) The more positive the individual factors, the higher to total result of the factor set, the more likely the individual will move to a lower state of privacy, Sm>Sn
- 35. Transitions ˇń Forward ˇń I disclose about me, my objects ˇń You disclose about me, my objects ˇń Backward ˇń information redaction ˇń information protection
- 36. Questions For You ˇń How do people make decisions? ˇń Specifically in social situations? ˇń How does space change behaviour? ˇń Any suggestions for testing? ˇń What are the other disciplines that talk about space, privacy, representation of self? ˇń Suggestions on theoretical frameworks?
- 37. An Offer
