Learning malware for fun and profit
- 1. Learning MALWARE ! for fun and profit SRINU sr1nu@ymail.com
- 2. What is malware? Types of malwares. How to create your own malware (Educational purpose only) Writing signatures to antiviruses. Evading antiviruses. (Educational purpose only)
- 3. What is a malware ? Malware short for malicious software . malware is a piece of software that is designed to disrupt operation , gather information , gain unauthorized access to system resources, and for exploitation purposes. The malware is a general term used by a computer professionals to mean a variety of forms of hostile , intrusive, or annoying software or programming code. In simply malware is a set of instructions that run on your computer and make your system do something that an attacker wants it to do.
- 4. Types of malware There are many types of malwares are there. most common are : Viruses Worms Rootkits Trojans Backdoors Spyware Keylogger Adware Crimeware Scareware This list goes on ŌĆ”ŌĆ”ŌĆ”ŌĆ”ŌĆ”ŌĆ”ŌĆ”
- 5. What is a Virus? A computer virus is a program that can replicate itself and spread from one computer to another. if a computer program is called as a virus it most have the capability to spread from one file to another file and one computer to another computer by means of Network or internet or carried it by a removable devices like CDŌĆÖs, DVDŌĆÖs, Floppy disks and USB devices. in simply virus is a program that can infect other programs by modifying them to include a, possibly evolved, version of itself.
- 6. Indications of Virus attack Hard drive is accessed even when not using the computer. Computer freezes frequently or encounters errors. Computer slows down when programs starts. Files and Folders are missing (god has to know what happened to files). Unable to load operating system files. Browser window freezes.
- 7. When computer get infected by Viruses DonŌĆÖt having proper antivirus application. Not updating antivirus and operating system and applications. Installing pirated software's and rouge applications. Opening an infected E-Mail attachments.
- 8. How to create your own Virus (Educational purpose only) DEMO
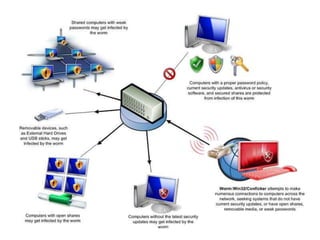
- 9. What is a Worm A computer worm is a self-replicating malware which uses a computer network to send copies of itself to another computer. However, a computer worm does not need to attach itself to a program in your system like a computer virus does in order to function. A computer worm generally localizes its damage to the computer network by causing increased bandwidth(only applicable to old worm types ’üŖ)
- 10. Indications of worm attacks ŌĆó Unusual network traffic in pc ŌĆó Not able to visit websites due to bandwidth is flooded by worm. ŌĆó Unusual files in network shares. ŌĆó Unable to update antiviruses.
- 11. How Worm spreads Peer 2 peer (p2p) Infected USB Network Emails networks like devices. shares. uTorrent.
- 13. How to create your own Worm (Educational purpose only) DEMO
- 14. Rootkit Rootkit is a stealthy type of malware designed to hide its existence from processes viewer and other monitor software's.
- 15. Types of rootkits ŌĆó There are two different types of rootkits. they are : ŌĆō User Mode rootkit User Mode ŌĆō Kernel Mode rootkit Supervisor / Kernel Mode
- 16. Backdoors ŌĆó A Backdoor is a way in to the system that allows an attacker to access the victim machine. ŌĆó after penetrating the victim machine the attacker installs the backdoor in it. ŌĆó it used to access the victim machine. ŌĆó Example: NetCat
- 17. Backdoor !!!! Hey got the backdoor. PWNED
- 18. Trojan ŌĆó Trojan is a piece of software which contains both legitimate code and malicious code. ŌĆó performs covert and overt actions. ŌĆó Frequently embedded in applets, games and email attachments. ŌĆó Examples ŌĆō Beast ŌĆō ProRat
- 19. Small story about Trojan
- 20. How to create your own Trojan (Educational purpose only) DEMO
- 21. Best Tips to Defend Against Malware Protect your computer with strong security software and keep updated. Enable Back up your automatic files regularly. Windows updates. Be careful Beware of when engaging spam-based in peer-to-peer phishing (P2P) file- schemes. sharing.
- 22. Writing signatures to antiviruses Mostly antivirus signature writers use three methods to create signatures They are: MD5 hashes Byte code Heuristic
- 23. Again DEMO
- 24. Evading Antiviruses Again An Awesome DEMO ’üŖ
- 25. Any Queries
- 26. Special Thanks to Imran Raghu chaitu