LinkedIn - Disassembling Dalvik Bytecode
3 likes624 views
The document discusses disassembling Dalvik bytecode on Android. It begins by providing background on Android, Dalvik VM, APK files, DEX files, and JIT compilation. It then discusses ways to hack at different levels: using macros to automate games, intercepting REST traffic, analyzing APK/DEX files by decompiling them and modifying bytecode, analyzing and modifying shared object libraries, and disassembling machine code. The key steps outlined are decompiling DEX to Smali bytecode, applying changes, recompiling to an APK, installing on a device, and analyzing shared object libraries by disassembling to machine code.
1 of 27
Downloaded 12 times





















Recommended
Understanding the Dalvik bytecode with the Dedexer tool



Understanding the Dalvik bytecode with the Dedexer toolGabor Paller
?
This document discusses the Dalvik virtual machine used in Android and how to decompile Dalvik bytecode using the Dedexer tool. It provides background on Android's use of Java and the Dalvik VM. Key points include: Dalvik uses its own bytecode format rather than Java bytecode and executes applications; the Dedexer tool can be used to disassemble DEX files back into Dalvik bytecode; and differences in Dalvik like its register-based rather than stack-based design are explained. Examples of Dalvik bytecode instructions and register usage are also provided.Inc0gnito 2015 Android DEX Analysis Technique



Inc0gnito 2015 Android DEX Analysis Technique?? ?
?
- The document discusses analyzing Android DEX files, which contain Dalvik executable code.
- It explains how to parse different sections of a DEX file like the header, strings, types, protoypes, methods, and classes using a DEX parsing tool.
- It also discusses how to extract permission information from a DEX file by analyzing method calls to determine which permissions the app is actually using.Dancing with dalvik



Dancing with dalvikThomas Richards
?
So you've reversed you're first Android APK; now what? Java pseduocode is nice, but how do we modify the app? This is a crash course in reading and understanding Davlik opcodes. It will go through some basics then we will jump into a couple case studies to demonstrate some of the concepts. This talk should help testers who are interested in or do Android application assessments to better understand how to mess with the underlying code.The dedexer disassembler



The dedexer disassemblerGabor Paller
?
This slideset presents the motivation behind the Android bytecode disassembler called dedexer and sets the expectations with some examples.How to implement a simple dalvik virtual machine



How to implement a simple dalvik virtual machineChun-Yu Wang
?
This slide is an introduction to Android Dalvik Virtual Machine on a short course.
We use two hand-made JVM and DVM which called Simple JVM and Simple DVM respectively, to tell student how they work. A Foo Class was provided as a target for verifying the execution results of those VM. We hope it will help student to understand JVM and DVM quickly. NDK Primer (Wearable DevCon 2014)



NDK Primer (Wearable DevCon 2014)Ron Munitz
?
My session in Wearable DevCon 2014, Burlingame, CA
[Note: now the conference is called "Wearable Tech Con" ]
The session gives an introduction to using the Java Native Interface (JNI) in Java, and in particular in the Android Platform. The session then covers the use of the Native Development Kit (NDK) for developing Android applications.Java 7 - New Features - by Mihail Stoynov and Svetlin Nakov



Java 7 - New Features - by Mihail Stoynov and Svetlin NakovSvetlin Nakov
?
Java 7 - New Features
Introduction and Chronology
Compressed 64-bit Object Pointers
Garbage-First GC (G1)
Dynamic Languages in JVM
Java Modularity ©C Project Jigsaw
Language Enhancements (Project Coin)
Strings in Switch
Automatic Resource Management (ARM)
Improved Type Inference for Generic Instance Creation
Improved Type Inference for Generic Instance Creation
Simplified Varargs Method Invocation
Collection Literals
Indexing Access Syntax for Lists and Maps
Language Support for JSR 292
Underscores in Numbers
Binary Literals
Closures for Java
First-class Functions
Function Types
Lambda Expressions
Project Lambda
Extension Methods
Upgrade Class-Loader Architecture
Method to close a URLClassLoader
Unicode 5.1
JSR 203: NIO.2
SCTP (Stream Control Transmission Protocol)
SDP (Sockets Direct Protocol)
In Vogue Dynamic



In Vogue DynamicAlexander Shopov
?
JSR-292 - How and when to use invokedynamic.
Usage in Java 8 for lambdas.
Disassembling the code, bootstrap method glue and MethodHandlesDebugging Python with gdb



Debugging Python with gdbRoman Podoliaka
?
A PyConUA 2017 talk on debugging Python programs with gdb.
A blog post version: http://podoliaka.org/2016/04/10/debugging-cpython-gdb/Introduction to llvm



Introduction to llvmTao He
?
The document introduces LLVM and its intermediate representation (IR) for program analysis. It describes how LLVM IR uses static single assignment form and three-address code. It shows examples of common LLVM IR instructions like arithmetic operations, branches, function calls and definitions. It explains how to use the 'opt' command to run analysis passes and print outputs like call graphs. It provides guidance on writing custom analysis passes and installing LLVM to build and run them.I Know Kung Fu - Juggling Java Bytecode



I Know Kung Fu - Juggling Java BytecodeAlexander Shopov
?
The document discusses bytecode manipulation in Java using ASM. It begins with an introduction to bytecode and ASM. It then covers classfile structure, reading and transforming bytecode with ASM visitors, and provides examples of renaming a class, adding a field, changing a method, fixing constructors, and adding an interface. The overall document serves as a tutorial for how to manipulate Java bytecode programmatically using the ASM framework.Introduction to the LLVM Compiler System



Introduction to the LLVM Compiler Systemzionsaint
?
The LLVM project is a collection of compiler and toolchain technologies, including an optimizer, code generators, and front-ends like llvm-gcc and Clang. The project aims to provide modular, reusable compiler components to reduce the time and cost of building compilers. It also seeks to implement modern compiler techniques to generate fast, optimized code. LLVM has been used to build fast C/C++ compilers like LLVM-GCC that show improvements in compilation speed and generated code quality compared to GCC.???????, VM???: ?? ???? LLVM



???????, VM???: ?? ???? LLVMJung Kim
?
JCO ?????? ???? ?????. ??? ??? ???? LLVM ????? ? ??? ?????? ?????. Java? ?? ?? ?? ???? ??? ?? ? ?? LLVM ?? ???? ?????. LLVM? ?? ??? ??? ??? ? ????.LLVM



LLVMguest3e5046
?
The document discusses the LLVM compiler framework and infrastructure. It provides reusable components for building compilers to reduce the time and cost of building new compilers. The LLVM compiler framework uses the LLVM infrastructure to build static compilers, JITs, and trace-based optimizers. It emits C code or native code for x86, Sparc, and PowerPC architectures. The three primary LLVM components are the virtual instruction set (the common language- and target-independent intermediate representation), a collection of well-integrated libraries, and a collection of tools built from the libraries.LLVM Compiler - Link Time Optimization



LLVM Compiler - Link Time OptimizationVivek Pansara
?
LLVM is a compiler infrastructure that provides modular and reusable compiler components. It supports link-time optimization (LTO) which allows interprocedural optimizations by treating LLVM bitcode files like native object files during linking. LTO involves four phases: reading bitcode files, symbol resolution, optimizing bitcode, and final symbol resolution. It uses the libLTO shared object to handle LLVM bitcode, performing operations like creating and disposing modules, querying symbols, and compiling to a native object file.PHP Development Tools 2.0 - Success Story



PHP Development Tools 2.0 - Success StoryMichael Spector
?
The document discusses the history and features of PHP Development Tools (PDT). PDT 1.0 was initially contributed by IBM and Zend in 2007, providing PHP capabilities like code assist, debugging, and navigation views. PDT 2.0 utilizes the Dynamic Languages Toolkit to be lighter and faster, with improved memory management and new features like build path configuration, mark occurrences, and type hierarchy. The document provides an example of extending PDT by creating a plugin to warn of potential cross-site scripting vulnerabilities.Open arkcompiler



Open arkcompileryiwei yang
?
- OpenArkCompiler supports multiple languages and aims to optimize cross-language calls and improve efficiency.
- It includes components for compiling, optimization passes on its intermediate representation Maple, and backend code generation.
- The founder Zhou Zhide has decades of experience in compiler design and led the development of several compilers including Open64.NDK Primer (AnDevCon Boston 2014)



NDK Primer (AnDevCon Boston 2014)Ron Munitz
?
The document discusses Ron Munitz's background and expertise, which includes distributed fault tolerant systems, highly distributed video routers, real-time embedded systems, Android, and enterprise mobility and security. It provides an agenda for a talk on the Java Native Interface (JNI) and native Android apps. The agenda includes an introduction to JNI theory and a "Hello World" tutorial, followed by a discussion of JNI in the Android Open Source Project (AOSP) and writing native Android apps.Lifting The Veil - Reading Java Bytecode



Lifting The Veil - Reading Java BytecodeAlexander Shopov
?
This document discusses reading Java bytecode and provides examples of how to interpret bytecode instructions and method signatures. It introduces key concepts of the Java Virtual Machine (JVM) like frames, stacks, local variables, and bytecode instructions. It also demonstrates how to decompile classes and interpret example bytecode snippets using the javap tool. The document is intended to help readers understand how Java code is executed at the bytecode level.Lifting The Veil - Reading Java Bytecode During Lunchtime



Lifting The Veil - Reading Java Bytecode During LunchtimeAlexander Shopov
?
This document discusses reading Java bytecode during lunchtime. It provides an overview of key concepts related to the Java Virtual Machine (JVM) like threads, frames, stacks, local variables, constant pools, and bytecode instructions. It then dives into examining specific bytecode instructions like load, store, math, object, and return operations. The document encourages learning to read bytecode as it allows understanding how Java functions at a lower level and can help with tasks like job interviews, debugging compiler issues, and tracking Java language vs platform evolution.Specialized Compiler for Hash Cracking



Specialized Compiler for Hash CrackingPositive Hack Days
?
This document describes john-devkit, an experiment to generate optimized C code for hash cracking algorithms in John the Ripper. It aims to separate algorithms, optimizations, and device-specific code to improve performance and scalability. Early results show speed improvements for some formats over John the Ripper's default implementation. The document discusses optimizations like interleaving, vectorization, and early reject that can be applied to any algorithm without effort. It also describes the intermediate language and optimizations specific to password cracking used by john-devkit to generate optimized output code.(COSCUP 2015) A Beginner's Journey to Mozilla SpiderMonkey JS Engine



(COSCUP 2015) A Beginner's Journey to Mozilla SpiderMonkey JS EngineZongXian Shen
?
This is my slides of COSCUP 2015 at Taipei, Taiwan.
The material is about the engine implementation overview from a 3 month experienced mentor bug contributor.C++ CoreHard Autumn 2018. ¦│¦Ó¦┘¦š¦č¦▀¦┌¦ų ¦ß¦č¦▄¦ų¦õ¦Ó¦ė ¦š¦▌¦± ¦Ó¦õ¦▄¦Ō¦Ē¦õ¦Ē¦ń ¦ę¦┌¦ę¦▌¦┌¦Ó¦õ¦ų¦▄ ¦ķ¦ų¦Ō¦ų¦┘ conan...



C++ CoreHard Autumn 2018. ¦│¦Ó¦┘¦š¦č¦▀¦┌¦ų ¦ß¦č¦▄¦ų¦õ¦Ó¦ė ¦š¦▌¦± ¦Ó¦õ¦▄¦Ō¦Ē¦õ¦Ē¦ń ¦ę¦┌¦ę¦▌¦┌¦Ó¦õ¦ų¦▄ ¦ķ¦ų¦Ō¦ų¦┘ conan...corehard_by
?
¦¬¦Ń¦ß¦Ó¦▌¦Ņ¦┘¦Ó¦ė¦č¦▀¦┌¦ų ¦Ń¦õ¦Ó¦Ō¦Ó¦▀¦▀¦┌¦ń ¦ę¦┌¦ę¦▌¦┌¦Ó¦õ¦ų¦▄ ¦ė ¦±¦┘¦Ē¦▄¦ų C++ ¦▀¦┌¦▄¦Ó¦į¦š¦č ¦▀¦ų ¦ę¦Ē¦▌¦Ó ¦ß¦Ō¦Ó¦Ń¦õ¦Ē¦▐ - ¦▀¦ų¦Ó¦ę¦ń¦Ó¦š¦┌¦▐¦Ó ¦ę¦Ē¦▌¦Ó ¦ß¦Ō¦č¦ė¦┌¦▌¦Ņ¦▀¦Ó ¦Ń¦Ó¦ę¦Ō¦č¦õ¦Ņ ¦┌¦ń, ¦┌¦▐¦ų¦± ¦š¦ų¦▌¦Ó ¦Ń ¦Ō¦č¦┘¦▌¦┌¦ķ¦▀¦Ē¦▐¦┌ ¦Ń¦┌¦Ń¦õ¦ų¦▐¦č¦▐¦┌ ¦Ń¦ę¦Ó¦Ō¦▄¦┌, ¦▀¦Ó ¦Ń ¦ß¦Ó¦±¦ė¦▌¦ų¦▀¦┌¦ų¦▐ ¦ß¦č¦▄¦ų¦õ¦▀¦Ó¦į¦Ó ¦▐¦ų¦▀¦ų¦š¦ž¦ų¦Ō¦č conan.io ¦ß¦Ō¦Ó¦Ķ¦ų¦Ń¦Ń ¦Ń¦õ¦č¦▌ ¦▀¦č¦▐¦▀¦Ó¦į¦Ó ¦ß¦Ō¦Ó¦ļ¦ų, ¦õ¦č¦▄ ¦ķ¦õ¦Ó ¦õ¦ų¦ß¦ų¦Ō¦Ņ ¦Ó¦Ń¦õ¦č¦▌¦Ó¦Ń¦Ņ ¦õ¦Ó¦▌¦Ņ¦▄¦Ó ¦Ń¦š¦ų¦▌¦č¦õ¦Ņ ¦ß¦č¦▄¦ų¦õ¦Ē ¦š¦▌¦± ¦▀¦Õ¦ž¦▀¦Ē¦▐ ¦ę¦┌¦ę¦▌¦┌¦Ó¦õ¦ų¦▄, ¦┌ ¦ė ¦’¦õ¦Ó¦▐ ¦ß¦Ó¦▐¦Ó¦ž¦ų¦õ ¦▄¦Ó¦▐¦č¦▀¦š¦č bincrafter-¦Ó¦ė.Toward dynamic analysis of obfuscated android malware



Toward dynamic analysis of obfuscated android malwareZongXian Shen
?
The document provides an overview of analyzing obfuscated Android malware. It begins with a quick review of the Android runtime and framework startup process. It then discusses dynamic analysis techniques for fighting encrypted DEX code and native protectors. For encrypted DEX code, it describes preparing an emulator, debugging tools, and tracing plugins to analyze a sample that uses encryption. It explores the sample's decryption and loading logic, class decryption through reflection, and an anti-tampering technique. For native protectors, it discusses unpacking the library through static and dynamic analysis, reviewing the library loading process, and preparing to trace library initialization for monitoring decryption.ProbeDroid - Crafting Your Own Dynamic Instrument Tool on Android for App Beh...



ProbeDroid - Crafting Your Own Dynamic Instrument Tool on Android for App Beh...ZongXian Shen
?
The design memo and hack note of ProbeDroid
A dynamic binary instrumentation kit targeting Android(Lollipop) 5.0 and above
This is the first complete draft.
Improved version will be updated in a few days.Part II: LLVM Intermediate Representation



Part II: LLVM Intermediate RepresentationWei-Ren Chen
?
This document discusses the LLVM intermediate representation (IR) and the lowering process from LLVM IR to machine code. It covers:
1) The characteristics of LLVM IR including SSA form, infinite virtual registers, and phi nodes.
2) How the LLVM IRBuilder class is used to conveniently generate LLVM instructions.
3) The lowering flow from LLVM IR to selection DAGs to machine DAGs to machine instructions and finally machine code.
4) How assembler relaxation can optimize and correct instructions during assembly.▓╗╔Ņ▓╗£\Ż¼Ä¦─ŃšJūR LLVM (Found LLVM in your life)



▓╗╔Ņ▓╗£\Ż¼Ä¦─ŃšJūR LLVM (Found LLVM in your life)Douglas Chen
?
╚ń╣¹─Ńå¢╬ę╩▓³N╩ŪLLVMŻ¼╬ęĢ■Žļšf╦³╩Ū Compiler ĮńĄ─ iPhoneŻ¼«ö─ĻĢ■ū÷╩ųÖCĄ─╣½╦Š▀@³NČÓŻ¼Ų½Ų½ Apple ▀@éĆßßüĒš▀▓╗Ą½Šė╔ŽŻ¼▀Ćę²ŅI╩ųÖCĖ┼─ŅĄ─’L│▒ĪŻLLVM ę▓š²╩Ū▀@éĆĮŪ╔½Ż¼╬ęéāĄ─╔·╗Ņė·üĒė·ČÓ«aŲĘĄ─ķ_░lČ╝┼c LLVM ŽóŽóŽÓĻPĪŻ╦³▓╗ų╗ĪĖņ┼Ī╣▀Ć║▄ĪĖī┼Ī╣Ż¼▀@Äū─Ļ Apple, Google, Microsoft ę╗éĆéĆķ_╩╝Č╝ėą┤¾ą═īŻ░Ė╩╣ė├ĄĮ LLVMŻ¼į┌ŅIė“├µų╗ę¬┼cŠÄūgŲ„ėąŽÓĻPÅ─Machine Learning, RISC-V, JVM, Virtual Machine, Blockchain Č╝▀\ė├┴╦ LLVMŻ¼┐Ų╝╝▀M▓Į│╔▀@śė┴╦Ż¼─Ń▀Ć─▄▓╗ų¬Ą└╩▓³N╩Ū LLVM å߯ĪC++ programming



C++ programmingEmertxe Information Technologies Pvt Ltd
?
C++ is most often used programming language. This slide will help you to gain more knowledge on C++ programming. In this slide you will learn the fundamentals of C++ programming. The slide will also help you to fetch more details on Object Oriented Programming concepts. Each of the concept under Object Oriented Programming is explained in detail and in more smoother way as it will helpful for everyone to understand.Let's talk about jni



Let's talk about jniYongqiang Li
?
This document discusses the Java Native Interface (JNI) which allows Java code running in the Java Virtual Machine (JVM) to call and be called by native code such as C and C++. It provides an overview of JNI and walks through a sample implementation in 5 steps. It also discusses more details of JNI including JNI types, the JNIEnv interface, accessing fields and methods, and managing native memory.Android internals 05 - Dalvik VM (rev_1.1)



Android internals 05 - Dalvik VM (rev_1.1)Egor Elizarov
?
This document discusses the Dalvik virtual machine (VM) used in Android. It begins with an overview of VMs and describes Dalvik as a register-based VM that relies on the operating system for memory management, threading, and process isolation. It then covers Dalvik bytecode, the interpreter core, just-in-time compilation, application launching via the Zygote process, and porting Dalvik to new platforms.More Related Content
What's hot (20)
Debugging Python with gdb



Debugging Python with gdbRoman Podoliaka
?
A PyConUA 2017 talk on debugging Python programs with gdb.
A blog post version: http://podoliaka.org/2016/04/10/debugging-cpython-gdb/Introduction to llvm



Introduction to llvmTao He
?
The document introduces LLVM and its intermediate representation (IR) for program analysis. It describes how LLVM IR uses static single assignment form and three-address code. It shows examples of common LLVM IR instructions like arithmetic operations, branches, function calls and definitions. It explains how to use the 'opt' command to run analysis passes and print outputs like call graphs. It provides guidance on writing custom analysis passes and installing LLVM to build and run them.I Know Kung Fu - Juggling Java Bytecode



I Know Kung Fu - Juggling Java BytecodeAlexander Shopov
?
The document discusses bytecode manipulation in Java using ASM. It begins with an introduction to bytecode and ASM. It then covers classfile structure, reading and transforming bytecode with ASM visitors, and provides examples of renaming a class, adding a field, changing a method, fixing constructors, and adding an interface. The overall document serves as a tutorial for how to manipulate Java bytecode programmatically using the ASM framework.Introduction to the LLVM Compiler System



Introduction to the LLVM Compiler Systemzionsaint
?
The LLVM project is a collection of compiler and toolchain technologies, including an optimizer, code generators, and front-ends like llvm-gcc and Clang. The project aims to provide modular, reusable compiler components to reduce the time and cost of building compilers. It also seeks to implement modern compiler techniques to generate fast, optimized code. LLVM has been used to build fast C/C++ compilers like LLVM-GCC that show improvements in compilation speed and generated code quality compared to GCC.???????, VM???: ?? ???? LLVM



???????, VM???: ?? ???? LLVMJung Kim
?
JCO ?????? ???? ?????. ??? ??? ???? LLVM ????? ? ??? ?????? ?????. Java? ?? ?? ?? ???? ??? ?? ? ?? LLVM ?? ???? ?????. LLVM? ?? ??? ??? ??? ? ????.LLVM



LLVMguest3e5046
?
The document discusses the LLVM compiler framework and infrastructure. It provides reusable components for building compilers to reduce the time and cost of building new compilers. The LLVM compiler framework uses the LLVM infrastructure to build static compilers, JITs, and trace-based optimizers. It emits C code or native code for x86, Sparc, and PowerPC architectures. The three primary LLVM components are the virtual instruction set (the common language- and target-independent intermediate representation), a collection of well-integrated libraries, and a collection of tools built from the libraries.LLVM Compiler - Link Time Optimization



LLVM Compiler - Link Time OptimizationVivek Pansara
?
LLVM is a compiler infrastructure that provides modular and reusable compiler components. It supports link-time optimization (LTO) which allows interprocedural optimizations by treating LLVM bitcode files like native object files during linking. LTO involves four phases: reading bitcode files, symbol resolution, optimizing bitcode, and final symbol resolution. It uses the libLTO shared object to handle LLVM bitcode, performing operations like creating and disposing modules, querying symbols, and compiling to a native object file.PHP Development Tools 2.0 - Success Story



PHP Development Tools 2.0 - Success StoryMichael Spector
?
The document discusses the history and features of PHP Development Tools (PDT). PDT 1.0 was initially contributed by IBM and Zend in 2007, providing PHP capabilities like code assist, debugging, and navigation views. PDT 2.0 utilizes the Dynamic Languages Toolkit to be lighter and faster, with improved memory management and new features like build path configuration, mark occurrences, and type hierarchy. The document provides an example of extending PDT by creating a plugin to warn of potential cross-site scripting vulnerabilities.Open arkcompiler



Open arkcompileryiwei yang
?
- OpenArkCompiler supports multiple languages and aims to optimize cross-language calls and improve efficiency.
- It includes components for compiling, optimization passes on its intermediate representation Maple, and backend code generation.
- The founder Zhou Zhide has decades of experience in compiler design and led the development of several compilers including Open64.NDK Primer (AnDevCon Boston 2014)



NDK Primer (AnDevCon Boston 2014)Ron Munitz
?
The document discusses Ron Munitz's background and expertise, which includes distributed fault tolerant systems, highly distributed video routers, real-time embedded systems, Android, and enterprise mobility and security. It provides an agenda for a talk on the Java Native Interface (JNI) and native Android apps. The agenda includes an introduction to JNI theory and a "Hello World" tutorial, followed by a discussion of JNI in the Android Open Source Project (AOSP) and writing native Android apps.Lifting The Veil - Reading Java Bytecode



Lifting The Veil - Reading Java BytecodeAlexander Shopov
?
This document discusses reading Java bytecode and provides examples of how to interpret bytecode instructions and method signatures. It introduces key concepts of the Java Virtual Machine (JVM) like frames, stacks, local variables, and bytecode instructions. It also demonstrates how to decompile classes and interpret example bytecode snippets using the javap tool. The document is intended to help readers understand how Java code is executed at the bytecode level.Lifting The Veil - Reading Java Bytecode During Lunchtime



Lifting The Veil - Reading Java Bytecode During LunchtimeAlexander Shopov
?
This document discusses reading Java bytecode during lunchtime. It provides an overview of key concepts related to the Java Virtual Machine (JVM) like threads, frames, stacks, local variables, constant pools, and bytecode instructions. It then dives into examining specific bytecode instructions like load, store, math, object, and return operations. The document encourages learning to read bytecode as it allows understanding how Java functions at a lower level and can help with tasks like job interviews, debugging compiler issues, and tracking Java language vs platform evolution.Specialized Compiler for Hash Cracking



Specialized Compiler for Hash CrackingPositive Hack Days
?
This document describes john-devkit, an experiment to generate optimized C code for hash cracking algorithms in John the Ripper. It aims to separate algorithms, optimizations, and device-specific code to improve performance and scalability. Early results show speed improvements for some formats over John the Ripper's default implementation. The document discusses optimizations like interleaving, vectorization, and early reject that can be applied to any algorithm without effort. It also describes the intermediate language and optimizations specific to password cracking used by john-devkit to generate optimized output code.(COSCUP 2015) A Beginner's Journey to Mozilla SpiderMonkey JS Engine



(COSCUP 2015) A Beginner's Journey to Mozilla SpiderMonkey JS EngineZongXian Shen
?
This is my slides of COSCUP 2015 at Taipei, Taiwan.
The material is about the engine implementation overview from a 3 month experienced mentor bug contributor.C++ CoreHard Autumn 2018. ¦│¦Ó¦┘¦š¦č¦▀¦┌¦ų ¦ß¦č¦▄¦ų¦õ¦Ó¦ė ¦š¦▌¦± ¦Ó¦õ¦▄¦Ō¦Ē¦õ¦Ē¦ń ¦ę¦┌¦ę¦▌¦┌¦Ó¦õ¦ų¦▄ ¦ķ¦ų¦Ō¦ų¦┘ conan...



C++ CoreHard Autumn 2018. ¦│¦Ó¦┘¦š¦č¦▀¦┌¦ų ¦ß¦č¦▄¦ų¦õ¦Ó¦ė ¦š¦▌¦± ¦Ó¦õ¦▄¦Ō¦Ē¦õ¦Ē¦ń ¦ę¦┌¦ę¦▌¦┌¦Ó¦õ¦ų¦▄ ¦ķ¦ų¦Ō¦ų¦┘ conan...corehard_by
?
¦¬¦Ń¦ß¦Ó¦▌¦Ņ¦┘¦Ó¦ė¦č¦▀¦┌¦ų ¦Ń¦õ¦Ó¦Ō¦Ó¦▀¦▀¦┌¦ń ¦ę¦┌¦ę¦▌¦┌¦Ó¦õ¦ų¦▄ ¦ė ¦±¦┘¦Ē¦▄¦ų C++ ¦▀¦┌¦▄¦Ó¦į¦š¦č ¦▀¦ų ¦ę¦Ē¦▌¦Ó ¦ß¦Ō¦Ó¦Ń¦õ¦Ē¦▐ - ¦▀¦ų¦Ó¦ę¦ń¦Ó¦š¦┌¦▐¦Ó ¦ę¦Ē¦▌¦Ó ¦ß¦Ō¦č¦ė¦┌¦▌¦Ņ¦▀¦Ó ¦Ń¦Ó¦ę¦Ō¦č¦õ¦Ņ ¦┌¦ń, ¦┌¦▐¦ų¦± ¦š¦ų¦▌¦Ó ¦Ń ¦Ō¦č¦┘¦▌¦┌¦ķ¦▀¦Ē¦▐¦┌ ¦Ń¦┌¦Ń¦õ¦ų¦▐¦č¦▐¦┌ ¦Ń¦ę¦Ó¦Ō¦▄¦┌, ¦▀¦Ó ¦Ń ¦ß¦Ó¦±¦ė¦▌¦ų¦▀¦┌¦ų¦▐ ¦ß¦č¦▄¦ų¦õ¦▀¦Ó¦į¦Ó ¦▐¦ų¦▀¦ų¦š¦ž¦ų¦Ō¦č conan.io ¦ß¦Ō¦Ó¦Ķ¦ų¦Ń¦Ń ¦Ń¦õ¦č¦▌ ¦▀¦č¦▐¦▀¦Ó¦į¦Ó ¦ß¦Ō¦Ó¦ļ¦ų, ¦õ¦č¦▄ ¦ķ¦õ¦Ó ¦õ¦ų¦ß¦ų¦Ō¦Ņ ¦Ó¦Ń¦õ¦č¦▌¦Ó¦Ń¦Ņ ¦õ¦Ó¦▌¦Ņ¦▄¦Ó ¦Ń¦š¦ų¦▌¦č¦õ¦Ņ ¦ß¦č¦▄¦ų¦õ¦Ē ¦š¦▌¦± ¦▀¦Õ¦ž¦▀¦Ē¦▐ ¦ę¦┌¦ę¦▌¦┌¦Ó¦õ¦ų¦▄, ¦┌ ¦ė ¦’¦õ¦Ó¦▐ ¦ß¦Ó¦▐¦Ó¦ž¦ų¦õ ¦▄¦Ó¦▐¦č¦▀¦š¦č bincrafter-¦Ó¦ė.Toward dynamic analysis of obfuscated android malware



Toward dynamic analysis of obfuscated android malwareZongXian Shen
?
The document provides an overview of analyzing obfuscated Android malware. It begins with a quick review of the Android runtime and framework startup process. It then discusses dynamic analysis techniques for fighting encrypted DEX code and native protectors. For encrypted DEX code, it describes preparing an emulator, debugging tools, and tracing plugins to analyze a sample that uses encryption. It explores the sample's decryption and loading logic, class decryption through reflection, and an anti-tampering technique. For native protectors, it discusses unpacking the library through static and dynamic analysis, reviewing the library loading process, and preparing to trace library initialization for monitoring decryption.ProbeDroid - Crafting Your Own Dynamic Instrument Tool on Android for App Beh...



ProbeDroid - Crafting Your Own Dynamic Instrument Tool on Android for App Beh...ZongXian Shen
?
The design memo and hack note of ProbeDroid
A dynamic binary instrumentation kit targeting Android(Lollipop) 5.0 and above
This is the first complete draft.
Improved version will be updated in a few days.Part II: LLVM Intermediate Representation



Part II: LLVM Intermediate RepresentationWei-Ren Chen
?
This document discusses the LLVM intermediate representation (IR) and the lowering process from LLVM IR to machine code. It covers:
1) The characteristics of LLVM IR including SSA form, infinite virtual registers, and phi nodes.
2) How the LLVM IRBuilder class is used to conveniently generate LLVM instructions.
3) The lowering flow from LLVM IR to selection DAGs to machine DAGs to machine instructions and finally machine code.
4) How assembler relaxation can optimize and correct instructions during assembly.▓╗╔Ņ▓╗£\Ż¼Ä¦─ŃšJūR LLVM (Found LLVM in your life)



▓╗╔Ņ▓╗£\Ż¼Ä¦─ŃšJūR LLVM (Found LLVM in your life)Douglas Chen
?
╚ń╣¹─Ńå¢╬ę╩▓³N╩ŪLLVMŻ¼╬ęĢ■Žļšf╦³╩Ū Compiler ĮńĄ─ iPhoneŻ¼«ö─ĻĢ■ū÷╩ųÖCĄ─╣½╦Š▀@³NČÓŻ¼Ų½Ų½ Apple ▀@éĆßßüĒš▀▓╗Ą½Šė╔ŽŻ¼▀Ćę²ŅI╩ųÖCĖ┼─ŅĄ─’L│▒ĪŻLLVM ę▓š²╩Ū▀@éĆĮŪ╔½Ż¼╬ęéāĄ─╔·╗Ņė·üĒė·ČÓ«aŲĘĄ─ķ_░lČ╝┼c LLVM ŽóŽóŽÓĻPĪŻ╦³▓╗ų╗ĪĖņ┼Ī╣▀Ć║▄ĪĖī┼Ī╣Ż¼▀@Äū─Ļ Apple, Google, Microsoft ę╗éĆéĆķ_╩╝Č╝ėą┤¾ą═īŻ░Ė╩╣ė├ĄĮ LLVMŻ¼į┌ŅIė“├µų╗ę¬┼cŠÄūgŲ„ėąŽÓĻPÅ─Machine Learning, RISC-V, JVM, Virtual Machine, Blockchain Č╝▀\ė├┴╦ LLVMŻ¼┐Ų╝╝▀M▓Į│╔▀@śė┴╦Ż¼─Ń▀Ć─▄▓╗ų¬Ą└╩▓³N╩Ū LLVM å߯ĪC++ programming



C++ programmingEmertxe Information Technologies Pvt Ltd
?
C++ is most often used programming language. This slide will help you to gain more knowledge on C++ programming. In this slide you will learn the fundamentals of C++ programming. The slide will also help you to fetch more details on Object Oriented Programming concepts. Each of the concept under Object Oriented Programming is explained in detail and in more smoother way as it will helpful for everyone to understand.C++ CoreHard Autumn 2018. ¦│¦Ó¦┘¦š¦č¦▀¦┌¦ų ¦ß¦č¦▄¦ų¦õ¦Ó¦ė ¦š¦▌¦± ¦Ó¦õ¦▄¦Ō¦Ē¦õ¦Ē¦ń ¦ę¦┌¦ę¦▌¦┌¦Ó¦õ¦ų¦▄ ¦ķ¦ų¦Ō¦ų¦┘ conan...



C++ CoreHard Autumn 2018. ¦│¦Ó¦┘¦š¦č¦▀¦┌¦ų ¦ß¦č¦▄¦ų¦õ¦Ó¦ė ¦š¦▌¦± ¦Ó¦õ¦▄¦Ō¦Ē¦õ¦Ē¦ń ¦ę¦┌¦ę¦▌¦┌¦Ó¦õ¦ų¦▄ ¦ķ¦ų¦Ō¦ų¦┘ conan...corehard_by
?
Viewers also liked (18)
Let's talk about jni



Let's talk about jniYongqiang Li
?
This document discusses the Java Native Interface (JNI) which allows Java code running in the Java Virtual Machine (JVM) to call and be called by native code such as C and C++. It provides an overview of JNI and walks through a sample implementation in 5 steps. It also discusses more details of JNI including JNI types, the JNIEnv interface, accessing fields and methods, and managing native memory.Android internals 05 - Dalvik VM (rev_1.1)



Android internals 05 - Dalvik VM (rev_1.1)Egor Elizarov
?
This document discusses the Dalvik virtual machine (VM) used in Android. It begins with an overview of VMs and describes Dalvik as a register-based VM that relies on the operating system for memory management, threading, and process isolation. It then covers Dalvik bytecode, the interpreter core, just-in-time compilation, application launching via the Zygote process, and porting Dalvik to new platforms.Understanding the Dalvik Virtual Machine



Understanding the Dalvik Virtual MachineNational Cheng Kung University
?
(1) Understand how a virtual machine works
(2) Analyze the Dalvik VM using existing tools
(3) VM hacking is really interesting!Hacking your Droid (Aditya Gupta)



Hacking your Droid (Aditya Gupta)ClubHack
?
This document provides an overview of malware on Android systems. It discusses the Android architecture and security model, how to analyze Android application packages (APKs), and techniques for reverse engineering and creating Android malware. Specific malware examples like Trojan-SMS.FakePlayer.a and Geinimi are described. The document also covers tools for mobile application penetration testing and discusses both legal and illegal ways that Android malware can generate money.│¦│Š▓╣▒¶Š▒ė’Ę©



│¦│Š▓╣▒¶Š▒ė’Ę©xiaoshan8743
?
1. Dalvik bytecode represents types as either primitive types represented by single letters (e.g. I for int) or reference types in the form of Lpackage/name/ObjectName;.
2. Methods are specified in a verbose form including the containing type, name, parameter types, and return type (e.g. Lpackage/name/ObjectName;->MethodName(III)Z).
3. Fields are also specified verbosely including the containing type, name, and field type (e.g. Lpackage/name/ObjectName;->FieldName:Ljava/lang/String;).Reverse engineering android apps



Reverse engineering android appsPranay Airan
?
With growth in app market it is essential to guard our android apps against possible threats, in this presentation we will walk through various tools and techniques which some one can use to reverse engineer an android app, we will see how some one can get access to APP DB, CODE, API, PREFERENCES.
We will also see different tools and techniques to guard our app against possible threats from code obfuscation with tools like dexgaurd to newer methods like verification of api calls using google play services.
This session was taken in Barcamp 13 bangalore http://barcampbangalore.org/bcb/bcb13/reverse-engineering-an-android-app-securing-your-android-apps-against-attacks
and bangalore android user group meetup Jan meetup http://www.meetup.com/blrdroid/events/100360682/Toward Reverse Engineering of VBA Based Excel Spreadsheets Applications



Toward Reverse Engineering of VBA Based Excel Spreadsheets ApplicationsREvERSE University of Naples Federico II
?
These slides were presented at the 2nd Workshop on Software Engineering Methods in Spreadsheets co-located with ICSE Ī»15 in Florence.
We propose reverse engineering techniques aimed at supporting the comprehension of spreadsheet applications enhanced through the use of Visual Basic for Applications (VBA).Reverse Engineering Android Application



Reverse Engineering Android Applicationn|u - The Open Security Community
?
This document discusses reverse engineering of Android applications. It provides an overview of Android, noting that it is an open source platform based on Linux and uses Java and the Dalvik Virtual Machine. It lists the tools needed for reverse engineering like JRE, Apktools, SignApk, Dex2jar, and JD-GUI. It outlines two approaches - using Apktool to convert the DEX to SMALI or using Dex2jar to convert to a JAR and then Java. The document concludes by mentioning a live demo will be provided.Reverse Engineering .NET and Java



Reverse Engineering .NET and JavaJoe Kuemerle
?
Powerpoint from CodepaLOUsa 2011.
Learn the various techniques bad guys can use to extract information from your .NET or Java applications or at least how you can recover the source code that your predecessor deleted before he quit. A demo filled session on how easy it is to extract information from virtually any .NET or Java application (yes, including Silverlight). Android reverse engineering - Analyzing skype



Android reverse engineering - Analyzing skypeM©ório Almeida
?
During one of my personal projects I decided to study the internals of Android and the potential of altering the Dalvik VM (e.g. Xposed framework and Cydia) and application behaviour. Not going into detail about runtime hooking of constructors and classes like these two tools provide, I also explored the possibility of reverse engineering and modifying existing applications.
In the web you can find multiple tutorials on Android reverse engineering of applications but not many that do it with real applications that are often subject to obfuscation or with complex execution flows. So in order to learn I decided to pick a common application such as Skype and do the following:
decompile it
study contents and completely remove some functionality (e.g. ads)
change some resources (not described in presentation bellow)
recompile, sign and install.
Used tools include :
apktool ©C for (de)compiling android applications
jarsigner ©C for signing android applications
xposed ©C for intercepting runtime execution flow (will make public in future)
The following presentation describes the steps taken in order to completely remove the ads from skype. This includes any computation or data plan usage the ads consume. Please note the disclaimer of the presentation as this information is for educational purposes only.
Check my website : www.marioalmeida.euAndroid JNI



Android JNISiva Ramakrishna kv
?
Android JNI/NDK allows developers to use native code like C/C++ code in Android applications. It does this through the Java Native Interface (JNI) which provides a way to create Java objects and call Java methods from native code. The Native Development Kit (NDK) includes tools to compile C/C++ code for the Android platform. JNI allows accessing native methods and data types from Java code. It provides functions for loading native libraries, registering native methods, and manipulating objects, strings, classes and fields between the Java and native environments. Exceptions must be handled when using JNI to ensure stable applications.How to reverse engineer Android applicationsĪ¬using a popular word game as an ...



How to reverse engineer Android applicationsĪ¬using a popular word game as an ...Christoph Matthies
?
Short introduction to the basic methods and techniques used in reverse engineering Android applications. A popular word game is used as an example app.
The slides describe obtaining the application code, decompiling it, debugging Android applications, using a proxy server (Man-in-the-Middle) to extract communication protocols and automating Android applications.
Published under CC BY-NC-SA 3.0Garbage Collection of Java VM



Garbage Collection of Java VMYongqiang Li
?
The document discusses garbage collection in the Java Virtual Machine. It outlines the runtime data areas of JVM including heap, stacks, and method area. It describes different approaches to determining if an object is live or dead including reference counting and tracing GC roots. The document then explains common garbage collection algorithms like mark-sweep and copying and how different garbage collectors in Hotspot JVM like Serial, Parallel, and CMS work. It also discusses policies for object allocation and handling promotion of objects.Practice of Android Reverse Engineering



Practice of Android Reverse EngineeringNational Cheng Kung University
?
(Presentation at HITcon 2011) This talk introduces how to do Android application reverse engineering by real example. And, it covers the advanced topics like optimized DEX and JNI.Learning by hacking - android application hacking tutorial



Learning by hacking - android application hacking tutorialLandice Fu
?
It's just a tutorial to Android app hacking.
Wanna know more?
You can contact
FB: Landice Fu
email: rusty.flower@gmail.comInside Android's Dalvik VM - NEJUG Nov 2011



Inside Android's Dalvik VM - NEJUG Nov 2011Doug Hawkins
?
In this presentation, Doug Hawkins will discuss how the Dalvik VM is different from traditional Java VMs and the motivations behind those differences. Along the way, you'll learn about Android's service architecture, Dalvik's byte code format, and the surprising details of how Android installs, launches, and executes applications.Google ART (Android RunTime)



Google ART (Android RunTime)Niraj Solanke
?
The new runtime which Google is started implementing as developers view to implement or not which has advantages over the previous Dalvik runtime and more...IEEE Day 2013 - Reverse Engineering an Android Application



IEEE Day 2013 - Reverse Engineering an Android ApplicationRufatet Babakishiyev
?
Rufat Babakishiyev will give a presentation on reverse engineering an Android application. The presentation will include an overview of reverse engineering and forensic research, a review of the Android OS architecture, an analysis of the Yahoo email client application, decompiling the application files and database, examining application artifacts after installation and uninstallation, and security best practices. The goal is to understand how the application stores and manages data and identify artifacts left behind after uninstall.Toward Reverse Engineering of VBA Based Excel Spreadsheets Applications



Toward Reverse Engineering of VBA Based Excel Spreadsheets ApplicationsREvERSE University of Naples Federico II
?
How to reverse engineer Android applicationsĪ¬using a popular word game as an ...



How to reverse engineer Android applicationsĪ¬using a popular word game as an ...Christoph Matthies
?
Similar to LinkedIn - Disassembling Dalvik Bytecode (20)
Advance Android Application Development



Advance Android Application DevelopmentRamesh Prasad
?
The document discusses native application development for Android. It covers using the Native Development Kit (NDK) to write parts of Android apps in native code like C/C++ for performance benefits. The key points are:
- Native code can provide speed improvements for tasks like signal processing but also increases complexity.
- Google's Bionic C library is used instead of glibc for size, speed and licensing reasons and has some differences like lacking C++ exceptions.
- The NDK allows building native code libraries and combining them with Java code via the Java Native Interface (JNI).
- Native code interfaces with Android via JNI and system headers while the build system handles toolchains.lecture-2-android-dev.pdf



lecture-2-android-dev.pdfjakjak36
?
This document provides an introduction to Android development. It outlines the Android operating system architecture including the Linux kernel, native framework layer, and Android framework built using Java. It discusses Android versioning and accessing the source code. The document also covers the development tools including the Android SDK, NDK, and Android Studio IDE. It provides steps for setting up an Android development environment and deploying application packages. Finally, it demonstrates a step-by-step example of creating a basic "Hello World" Android application within the Android Studio IDE.Introduction to the Android NDK



Introduction to the Android NDKSebastian Mauer
?
This document provides an introduction to the Android NDK (Native Development Kit). It discusses that the NDK allows developing parts of Android apps using native code written in C/C++ for performance reasons or hardware access. Using native code adds complexity since it must be compiled for each hardware platform and interfaced with Java code. The document outlines NDK development, including compiling native libraries for different ABIs (CPU architectures), debugging native code, and considerations for standard C/C++ compatibility on Android.Mobile development in 2020 



Mobile development in 2020 Bogusz Jelinski
?
a short manual how to begin developing software with mobile frameworks - flutter, ionic and reactnative (draft, will be extended)Getting started with the NDK



Getting started with the NDKKirill Kounik
?
The document discusses native development for Android using the Native Development Kit (NDK). The NDK allows writing code in C/C++ and compiling it to create native libraries that can be called from Java code using JNI. It requires compiling libraries for each CPU architecture and may increase APK size. The NDK includes tools for setting up a project, configuring ABIs, debugging crashes using tombstone files, ndk-stack, and addr2line.Android Development



Android DevelopmentJohn Mark źĖźńź¾ź▐®`ź»
?
This document provides an overview of Android development. It outlines the Android platforms, Google Play, system architecture, installation requirements, and IDE. It discusses creating a "Hello World" project using Model-View-Controller. It also covers the Android Debug Bridge, activities, fragments, and differences between native, web and hybrid apps. Key topics include Android versions, top 5 phones, publishing apps, and using emulators and the Android Virtual Device Manager.Alternatives to Java for Android development



Alternatives to Java for Android developmentttogrul
?
The document discusses alternatives to Java for Android development, including the Android NDK which allows building activities and handling user input in C/C++. It describes tools in the NDK for building, compiling, and packaging native code libraries. Instructions are provided for installing C/C++ support in Eclipse and Cygwin. The document also mentions using C# for Android development with Mono and Visual Studio, and lists other programming languages like Python, Scala, Clojure, Ruby, and their respective frameworks for Android. Useful Android development links are included at the end.To?rul Ta??yev - M©╣xt?lif dill?rd? Android proqramla?d?rma



To?rul Ta??yev - M©╣xt?lif dill?rd? Android proqramla?d?rmaFarhad
?
The document discusses alternatives to Java for Android development, including the Android NDK which allows building activities and handling user input in C/C++. It describes tools in the NDK for building, compiling, and packaging native code libraries. Instructions are provided for installing C/C++ support in Eclipse and Cygwin. The document also mentions using C# for Android development with Mono and Visual Studio, and lists other programming languages like Python, Scala, Clojure, Ruby, and their respective frameworks for Android. Useful Android development links are included at the end.To?rul Ta??yev - M©╣xt?lif dill?rd? Android proqramla?d?rma



To?rul Ta??yev - M©╣xt?lif dill?rd? Android proqramla?d?rmaFarhad
?
The document discusses alternatives to Java for Android development, including the Android NDK which allows building activities and handling user input in C/C++. It describes tools in the NDK for building, compiling, and packaging native code libraries. Instructions are provided for installing C/C++ support in Eclipse and Cygwin. The document also mentions using C# for Android development with Mono and Visual Studio, and lists other programming languages like Python, Scala, Clojure, Ruby, and their respective frameworks for Android. Useful Android development links are included at the end.Beginners guide-to-reverse-engineering-android-apps-pau-oliva-fora-viaforensi...



Beginners guide-to-reverse-engineering-android-apps-pau-oliva-fora-viaforensi...viaForensics
?
This document provides an overview of reverse engineering Android apps. It discusses the anatomy of Android apps, obtaining target apps from a device or Google Play, and tools for disassembling and decompiling apps like Apktool, Dex2jar, and Android decompilers. It also promotes the use of Santoku Linux, an operating system distribution containing tools for mobile forensics and malware analysis.Alternatives to Java for Android development



Alternatives to Java for Android developmentttogrul
?
The Android NDK allows building performance-critical parts of apps in native code like C/C++. It provides headers and libraries for activities, input handling, sensors, resources, and more. It includes tools to build, compile code for device architectures, and package libraries into APKs for distribution.Getting Native with NDK



Getting Native with NDKź╩źÓ-Nam Nguy?n
?
The document provides information about using the Native Development Kit (NDK) to build native code for Android applications. It discusses what the NDK is, why developers may want to use native code, and how to set up a sample project to call native code from Java using the Java Native Interface (JNI). The sample project implements Fibonacci functions recursively and iteratively in both Java and C++ to demonstrate how to define and call native functions from an Android app.Using the android ndk - DroidCon Paris 2014



Using the android ndk - DroidCon Paris 2014Paris Android User Group
?
http://fr.droidcon.com/2014/agenda/
http://fr.droidcon.com/2014/agenda/detail?title=The+Android+Native+Development+Kit
The Android NDK is used to integrate C/C++ code into Android applications and libraries.
Learn how you can use the NDK and NDK-based libraries with Eclipse and Android Studio, and how you can debug and optimize your code.
Discover what changes from the new Android Runtime may break your integration, and how you can target new 64-bit architectures with the upcoming android L-release.
Speaker : Alexander Weggerle, IntelManish Chasta - Securing Android Applications



Manish Chasta - Securing Android ApplicationsPositive Hack Days
?
Mansih Chasta is a principal consultant at Indusface with over 6 years of experience in information and application security. The document discusses an upcoming training on analyzing and reverse engineering Android applications. It will cover topics like the Android SDK, setting up a GoatDroid application, memory analysis, intercepting layer 7 traffic, reverse engineering Android apps, SQLite database analysis, and demonstrating exploits on an ExploitMe application. Statistics are provided on growth in mobile app downloads from 2010 to 2014.Droidcon uk2012 androvm



Droidcon uk2012 androvmdfages
?
This document provides an overview of AndroVM, an alternative to the Android SDK emulator. It summarizes the Android Open Source Project (AOSP) and how it was ported to run in VirtualBox virtual machines. Key points include that AOSP includes a VirtualBox target but many functions were missing, so the AndroVM project worked to develop functions like mouse, ethernet, WiFi emulation, OpenGL ES 2.0 hardware support, and a configuration tool to improve the AOSP VirtualBox port.Calc app



Calc appAsad Ullah YousufZai
?
This document discusses the process of creating and running an Android application from source code. It involves writing Java source code, compiling it to Java bytecode, then to Dalvik bytecode optimized for Android. The Dalvik bytecode and other app files are combined into an .apk file. An IDE like Android Studio is used to compile the code, start an emulator, and run the app. The app undergoes multiple translations from human-readable code to processor-understandable instructions before being executed on Android devices.OWF12/PAUG Conf Days Alternative to google's android emulator, daniel fages, ...



OWF12/PAUG Conf Days Alternative to google's android emulator, daniel fages, ...Paris Open Source Summit
?
This document provides an overview of the AndroVM project, which aims to provide functional and robust Android virtual machine images as an alternative to the Android SDK emulator. It summarizes the project's goals of porting the Android Open Source Project (AOSP) to run on VirtualBox, including developing support for mouse, network, audio, OpenGL ES 2.0, USB, WiFi emulation, and ARM application support. The document also discusses AndroVM's usage by over 15,000 developers as a performance alternative to the SDK emulator and provides an agenda for a demo and future work on the project.Android porting for dummies @droidconin 2011



Android porting for dummies @droidconin 2011pundiramit
?
This document provides an overview of porting Android to new hardware:
1. It describes the Android software stack and the structure of the Android Open Source Project code.
2. It discusses requirements for building and accessing the AOSP code, including using the 'repo' tool to download the source.
3. It summarizes the AOSP code structure and highlights key components like the Linux kernel, HAL, and build system.
4. It provides an overview of the Android boot process and offers tips for debugging, including increasing log levels and using tools like logcat, adb, and dumpsys.Introduction to the Android NDK



Introduction to the Android NDKBeMyApp
?
This document provides an introduction to the Android Native Development Kit (NDK). It discusses that the NDK allows compiling C/C++ code into native libraries that can be used in Android apps. Native code can provide benefits like performance improvements for complex algorithms, but also introduces more complexity. The document outlines the basic process of creating and integrating native libraries into an Android project using the NDK, including compiling for different CPU architectures and interfacing between native and Java code through the Java Native Interface (JNI). It also discusses some potential pitfalls of using native code like reduced portability and difficulties with debugging.Android_Studio_Structure.docx



Android_Studio_Structure.docxKNANTHINIMCA
?
Java is used for Android application development because it was chosen as the primary development language for the Android platform. Developers write Java code that interacts with the Android API and compiles into DEX code to run on the Dalvik Virtual Machine. The key components of an Android application are activities, services, broadcast receivers, and content providers which are declared in the AndroidManifest.xml file. The application code, resources, and manifest are bundled into an APK file that can be installed and run on Android devices.OWF12/PAUG Conf Days Alternative to google's android emulator, daniel fages, ...



OWF12/PAUG Conf Days Alternative to google's android emulator, daniel fages, ...Paris Open Source Summit
?
LinkedIn - Disassembling Dalvik Bytecode
- 2. Background
- 3. What is Android? Android is an operating system by Google that uses a Linux kernel and runs its applications on a VM, formerly known as Dalvik The programs that run on Android are packaged and distributed as APK files Inside each APK file, there is an executable DEX file which is what actually gets run when the program starts Android has the largest installed base of all operating systems of any kind
- 4. What is Dalvik? ItĪ»s a VM but itĪ»s not the Java VM Register-based VM made more efficient when running on battery-powered, relatively low CPU/RAM smartphones You write Java source that compiles to Java bytecode which then gets translated to Dalvik bytecode Successor is Android Runtime (ART), introduced in KitKat (4.4+), completely replaced Dalvik in Lollipop (5.0+), which compiles-on-install rather than JIT
- 5. What is an APK? Android Package This is what you download and install from the Google Play store ItĪ»s really just a zip file containing an app Holds the appĪ»s assets and Dalvik bytecode (in .dex or .odex format)
- 6. What is bytecode? Not machine code DEX = Dalvik Executable Intermediate found in Java .class files and Dalvik .dex files Translated between .dex and .class using the dx tool Machine code is only created at runtime by the Just-In-Time (JIT) compiler
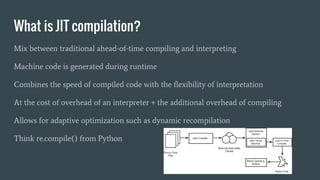
- 7. What is JIT compilation? Mix between traditional ahead-of-time compiling and interpreting Machine code is generated during runtime Combines the speed of compiled code with the flexibility of interpretation At the cost of overhead of an interpreter + the additional overhead of compiling Allows for adaptive optimization such as dynamic recompilation Think re.compile() from Python
- 8. What is the Android NDK? Android Native Development Kit A set of tools that allow you to leverage C and C++ code in your Android apps Uses the Java Native Interface (JNI) to expose Java calls to underlying system Used by Cocos2d-x, game development tools written in C++ Cocos is compiled as a shared library and shipped inside the APK
- 9. Hacking at the Surface Level
- 10. Use a Macro to Ī░BotĪ▒ the Game Was the goal of my last talk Use macros or scripts to automate some repeatable circuit to gain in-game currencies all day every day Prone to errors Slow, human level gain Too Bad ItĪ»s Not Really That Cool
- 11. Hacking at the REST Level
- 12. Wireshark Sniff the traffic to and from an Android emulator Make a malicious imposter client Replay the get/put/posts using curl or python Fail: Google Play Services uses OAuth 2.0 Sends ephemeral Base64-URL-encoded token
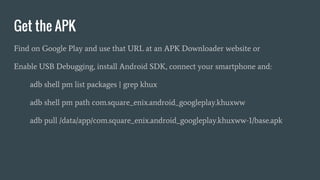
- 14. Hacking at the APK/DEX level
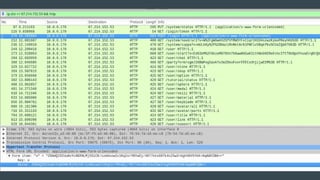
- 15. Get the APK Find on Google Play and use that URL at an APK Downloader website or Enable USB Debugging, install Android SDK, connect your smartphone and: adb shell pm list packages | grep khux adb shell pm path com.square_enix.android_googleplay.khuxww adb pull /data/app/com.square_enix.android_googleplay.khuxww-1/base.apk
- 16. DEX Bytecode Disassembling (Baksmaling) Two ways, recommend doing both: Directly: Convert to bytecode to a readable format (Baksmali, Jasmine, etc.) apktool d -f Ī░khux.apkĪ▒ -o smali Indirectly: Convert to Java first, then use JavaĪ»s decompiling tools dex2jar -> Java Decompiler (JD-Core, JD-GUI, etc.)
- 17. Smali Dalvik Bytecode Representation
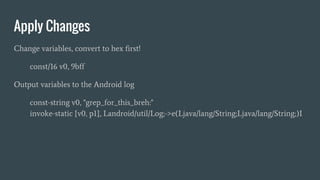
- 18. Apply Changes Change variables, convert to hex first! const/16 v0, 9bff Output variables to the Android log const-string v0, "grep_for_this_breh:" invoke-static {v0, p1}, Landroid/util/Log;->e(Ljava/lang/String;Ljava/lang/String;)I
- 19. APK Reassembling apktool b -f smali/ -o khux_rekt.apk jarsigner (Android SDK) - sign the apk with your own keystore or.. https://github.com/appium/sign java -jar sign.jar modded.apk zipalign (Android SDK) - (optional) ensures that all uncompressed data starts with a particular alignment relative to the start of the file, reducing appĪ»s RAM footprint zipalign 4 modded.s.apk aligned.apk
- 20. Reinstall the APK Uninstall the original APK if itĪ»s still on the device Install the modded APK adb install aligned.apk Disable or uninstall Facebook if youĪ»re having problems with Facebook login Watch the logs adb logcat | grep grep_for_this_breh
- 21. Hacking at the Shared Object Level
- 22. Shared Object Analysis libcocos2dcpp.so was the only meaningful difference When diff tells you Ī░Binary files differĪ▒, you can convert to hex and try again. xxd hacked.so > hacked.hex vimdiff hacked.hex unhacked.hex You can also try a byte-for-byte comparison cmp -l file1.so file2.so This prints out the line number of the changes and their differences in octal
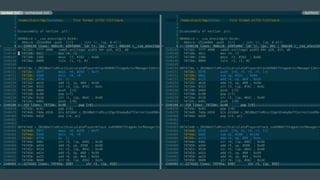
- 24. Machine Code Disassembly Get the Android NDK Find the right objdump for your architecture For Android smartphones, itĪ»s usually ARM little endian, arm-linux-androideabi /path/to/arch/objdump -d haxt.so > haxt.asm You can also use Hex-Keys IDA Pro (Interactive Disassembler) for multiarch disassembly
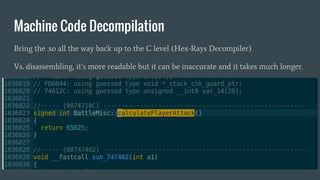
- 26. Machine Code Decompilation Bring the .so all the way back up to the C level (Hex-Rays Decompiler) Vs. disassembling, itĪ»s more readable but it can be inaccurate and it takes much longer.
- 27. The End