LiPari_MedicalDevices
Download as DOCX, PDF0 likes76 views
Increasing connectivity of medical devices to the internet is likely to increase vulnerabilities that can be exploited by cyber attackers through December 2015. Medical devices often use outdated and unsupported operating systems, making them vulnerable. Personal health information and device research data stored on networks are targets for sophisticated phishing attacks. Researchers demonstrated how easily medical devices could be hacked by exposing over 68,000 devices online and receiving bids for false vulnerabilities.
1 of 2
Download to read offline

Recommended
Enhancing Your Data Security: Closing the Gap on Unsecured Communications



Enhancing Your Data Security: Closing the Gap on Unsecured CommunicationsSpok
Ěý
This document discusses enhancing data security in healthcare by closing gaps in unsecured communications. It notes that healthcare is one of the most vulnerable industries to cyberattacks, with many recent breaches exposing patient data. While security is important, many healthcare companies are unprepared for attacks and share large amounts of data via unsecured methods. The document provides recommendations on keeping security plans updated through educated employees, tight processes, and the right technology like encryption, firewalls, and data loss prevention. It emphasizes defining a data strategy, implementing policies and layers of security tools, training end users, and developing business continuity plans to protect patient data.The Sick State of Healthcare Data Breaches



The Sick State of Healthcare Data BreachesLightCyber-Inc
Ěý
The healthcare industry has been a specific target for network attacks, spurred on by the high cost the data brings on the dark web. And statistic show that less than 5% of healthcare organizations have the ability to detect an active attacker on their network. This infographic gives some heart-stopping data about recent data breaches at healthcare organizations, along with information about how an active network attack progresses and then how to work to stop these attacks quickly. Medical device cybersecurity



Medical device cybersecuritywhitecryption
Ěý
According to the Identity Theft Resource Center, the first eight months of 2016 has seen 584 total breaches with more than 20,500,000 records exposed. Ransomware Attacks on Medical Devices on the Rise



Ransomware Attacks on Medical Devices on the RiseEMMAIntl
Ěý
In today’s modern era of the internet, it is a given that as medical device technology continues to develop, so will the number of devices that rely on network connectivity. The biggest market for these devices is healthcare clinics and hospitals as they allow the ability to monitor an increased array of patient information faster and more consistently...Healthcare and Cyber Security 2015 :Is India Ready? 



Healthcare and Cyber Security 2015 :Is India Ready? Apollo Hospitals Group and ATNF
Ěý
Explains about cyber security in Healthcare, Problem in Indian Scenario, Critical Infrastructure and Vulnerabilities. For more information visit: http://www.transformhealth-it.org/
Cyber physical system for healthcare



Cyber physical system for healthcareJUGAL GANDHI
Ěý
This document discusses the importance of security in healthcare systems and information. It notes that attackers can gain access to protected patient health information, insurance details, financial records, and more by exploiting vulnerabilities. The document outlines various security policies, techniques, and best practices that can be used, including encryption, access authorization, logging, firewalls, passwords, and more. It also provides examples of real-world healthcare cyberattacks and data breaches, such as the WannaCry ransomware attack and a human error that exposed millions of patient records. The document emphasizes that security is crucial in healthcare to protect private patient information and systems.Using Artificial Intelligenceto optimize PV workload



Using Artificial Intelligenceto optimize PV workloadOmar AIMER, Pharm.D, PhD
Ěý
My presentation at the World Drug Safety Congress Europe held on September 10th-11th, 2019 in AmsterdamHippa breaches



Hippa breachesViSolve, Inc.
Ěý
Security breaches have strong foot on healthcare industry this year. Nearly half of the organizations in healthcare were hit by security threats at least once this year and it is expected to increase in the forthcoming years.
The security breaches under HIPAA Violations could be classified as
• Stealth of Devices
• Process loopholes
• Employee Snooping
• Software defects
• HackingA Proposed Blueprint of a “privacy first” Pan Canadian Disease Contact Tracin...



A Proposed Blueprint of a “privacy first” Pan Canadian Disease Contact Tracin...Hisham Al Zanoon
Ěý
Disease Tracing is a vital tool but it needs to be designed following the key privacy by design principles.11 Most Common HIPAA Violations 



11 Most Common HIPAA Violations MariaClark32
Ěý
https://www.etacticsinc.com/
A HIPAA violation can cost a maximum of $1.5 million per year for violations of an identical provision and a lot of the time these are common HIPAA violations that can easily be adjusted.
When HIPAA was enacted on August 21, 1996, it turned the entire healthcare industry on its head. More than 20 years later, and many healthcare organizations constantly struggle when attempting to stay on top of everything this government regulation entails.
So what are some of the most common types of HIPAA violations?SeaCat: and SDN End-to-end Application Containment ArchitecTure



SeaCat: and SDN End-to-end Application Containment ArchitecTureUS-Ignite
Ěý
SeaCat: and SDN End-to-end Application Containment ArchitecTure a presentation by Jacobus Van der Merwe, U. Utah at US Ignite ONF GENI workshop on October 8, 2013Understanding Cybersecurity in Medical Devices and Applications



Understanding Cybersecurity in Medical Devices and ApplicationsEMMAIntl
Ěý
One of the major pillars of the current Industry 4.0 is Automation. Indeed, technology is intervening in almost every domain to “automate” the workforce and make human life easier and better. In the present age, machines are getting integrated with the Internet of Things, Cloud Computing, and Artificial Intelligence with the data flow being transferred and processed via the Internet. These changes indeed catalyze the overall productivity, but also expose data to the public
domains.
In cases of continuous data transfers and exposition, Cybersecurity becomes a pivotal element where it not only protects the data but also proactively provides mechanisms to defend against malicious attacks and malware. In the case of medical devices that include sensitive medical data flows and software-controlled hardware devices like heart implants or Continuous Glucose Monitoring (CGM) devices, Cybersecurity becomes an important factor for contributing towards system safety and quality...011918 espionage health_check_fact_sheet_rs



011918 espionage health_check_fact_sheet_rsRichard Smiraldi
Ěý
The document discusses an Espionage Health Check service that assesses organizations for cybersecurity vulnerabilities and potential breaches. The service includes on-site assessments of critical systems, network inspection, forensic analysis of disks and memory, and scanning systems for malware. Using intelligence from over 8,000 confirmed breaches, the experts can identify suspicious activity, malware, and areas of risk. The health check provides a report that summarizes any issues found and recommendations to strengthen defenses against cyber threats and espionage.INFOGRAPHIC: IS YOUR PATIENT DATA PROTECTED?



INFOGRAPHIC: IS YOUR PATIENT DATA PROTECTED?Diaspark
Ěý
According to OCR, there were 253 breaches affecting 500 individuals or more w/ a combined loss of over 112M records. Healthcare Failing to secure their data
48% encountered a data breach or failed a compliance audit in the last 12 months
26% are protecting data because of a past data breach
138% jump in number of breached healthcare records since 2012
The estimated cost for HIPAA breaches since 2009 has reached over 31 billion dollars.
Healthcare IT Challenges
42% of 2014 data breaches were in healthcare
90% of healthcare organizations have had at least 1 data breach in past 2 years
40% report that they have had more than 5 incidents of the entire U.S population was impacted by cybercrime in 9 months
Healthcare Cost of Breach
29% Reputation and brand damage
21% lost productivity
19% Lost Revenue
12% Forensics
10% Technical Support
8% Compliance Regulatory
With Data breaches expected to reach $2.1 trillion globally by 2019, which is four times the expected cost for cybercrime in 2015, It's apparent that a new approach to data security is needed if organizations are to stay ahead of the attackers and more effectively protect their intellectual property, data, customer information, employees, and their bottom lines against data breaches in the future
Contact us to learn how to safeguard against such breaches and implement it security strategy.
Risk management in Healthcare on Cloud



Risk management in Healthcare on CloudSandeep Sharma IIMK Smart City,IoT,Bigdata,Cloud,BI,DW
Ěý
Quickly made presentation in two hours
Security Risk Management in Healthcare on Cloud using NIST guidelines
More details: (blog: http://sandyclassic.wordpress.com ,
linkedin: ie.linkedin.com/in/sandepsharma/)Cloud Computing: Scalable and Secure Sharing of Personal Health Records Using...



Cloud Computing: Scalable and Secure Sharing of Personal Health Records Using...dbpublications
Ěý
Personal health record (PHR) is an emerging patient-centric model of health information exchange, which is often outsourced to be stored at a third party, such as cloud providers. However, there have been wide privacy concerns as personal health information could be exposed to those third party servers and to unauthorized parties. To assure the patients’ control over access to their own PHRs, it is a promising method to encrypt the PHRs before outsourcing. Yet, issues such as risks of privacy exposure, scalability in key management, flexible access, and efficient user revocation, have remained the most important challenges toward achieving fine-grained, cryptographically enforced data access control. In this paper, we propose a novel patient-centric framework and a suite of mechanisms for data access control to PHRs stored in semi trusted servers. To achieve fine-grained and scalable data access control for PHRs, we leverage attribute-based encryption (ABE) techniques to encrypt each patient’s PHR file. Different fr previous works in secure data outsourcing, we focus on the multiple data owner scenario, and divide the users in the PHR system into
multiple security domains that greatly reduces the key management complexity for owners and users. A high degree of patient privacy is guaranteed simultaneously by exploiting multi authority ABE. Our scheme also enables dynamic modification of access policies or file attributes, supports efficient on-demand user/attribute revocation and break-glass access under emergency scenarios.Cyb 610 Enhance teaching / snaptutorial.com



Cyb 610 Enhance teaching / snaptutorial.comBaileyaby
Ěý
This document outlines the requirements for a project assessing operating system vulnerabilities in Windows and Linux. The student is tasked with conducting a security assessment report (SAR) on the state of operating systems used by an oil and gas company. In addition, the student must create a nontechnical narrated presentation summarizing the SAR for leadership. The project involves researching vulnerabilities in key operating systems, analyzing security incidents that occurred, and providing recommendations to address risks and strengthen security posture. CYB 610 Effective Communication/tutorialrank.com



CYB 610 Effective Communication/tutorialrank.comjonhson199
Ěý
For more course tutorials visit
www.tutorialrank.com
CYB 610 Project 1 Information Systems and Identity Management
CYB 610 Project 2 Operating Systems Vulnerabilities (Windows and Linux)
CYB 610 Project 3 Assessing Information System Vulnerabilities and Risk
Medical device security presentation - Frank Siepmann



Medical device security presentation - Frank SiepmannFrank Siepmann
Ěý
Since I am not presenting (due to personal reasons) at the Medical Device Security conference 25/26 July 2016 in Arlington, VA I thought I post my slides about the current problems with Medical Device security and what can be done on a tactical level and what is needed at a strategic level.CSEC 610 Education Specialist / snaptutorial.com



CSEC 610 Education Specialist / snaptutorial.comMcdonaldRyan78
Ěý
For more classes visit
www.snaptutorial.com
CSEC 610 Project 1 Information Systems and Identity Management
CSEC 610 Project 2 Operating Systems Vulnerabilities (Windows and Linux)
CST 610 Effective Communication/tutorialrank.com



CST 610 Effective Communication/tutorialrank.comjonhson198
Ěý
This document outlines 6 cybersecurity projects for a course. Project 2 tasks the student to assess operating system vulnerabilities in a company's Windows and Linux systems. The student is to conduct a security assessment report (SAR) on the state of the operating systems and create a non-technical presentation summarizing their findings for leadership. The student will need to understand both Windows and Linux technologies to complete vulnerability scanning.Csec 610 Enhance teaching / snaptutorial.com



Csec 610 Enhance teaching / snaptutorial.comBaileyabv
Ěý
For more classes visit
www.snaptutorial.com
CSEC 610 Project 1 Information Systems and Identity Management
CSEC 610 Project 2 Operating Systems Vulnerabilities (Windows and Linux)
CSEC 610 Project 3 Assessing Information System Vulnerabilities and Risk
CSEC 610 Project 4 Threat Analysis and Exploitation
Cyb 610Education Specialist / snaptutorial.com



Cyb 610Education Specialist / snaptutorial.comMcdonaldRyan80
Ěý
CYB 610 Project 1 Information Systems and Identity Management
CYB 610 Project 2 Operating Systems Vulnerabilities (Windows and Linux)
CYB 610 Project 3 Assessing Information System Vulnerabilities and Risk
CYB 610 Project 4 Threat Analysis and Exploitation
Cyb 610 Education Organization-snaptutorial.com



Cyb 610 Education Organization-snaptutorial.comrobertlesew8
Ěý
For more classes visit
www.snaptutorial.com
CYB 610 Project 1 Information Systems and Identity Management
CYB 610 Project 2 Operating Systems Vulnerabilities (Windows and Linux)
CYB 610 Project 3 Assessing Information System Vulnerabilities and Risk
CYB 610 Project 4 Threat Analysis and Exploitation
CYB 610 Project 5 Cryptography
CYB 610 Project 6 Digital Forensics Analysis
Cyb 610 Believe Possibilities / snaptutorial.com



Cyb 610 Believe Possibilities / snaptutorial.comDavis12a
Ěý
For more classes visit
www.snaptutorial.com
CYB 610 Project 1 Information Systems and Identity Management
CYB 610 Project 2 Operating CST 610 RANK Redefined Education--cst610rank.com



CST 610 RANK Redefined Education--cst610rank.comclaric240
Ěý
FOR MORE CLASSES VISIT
www.cst610rank.com
CST 610 Project 1 Information Systems and Identity Management CST 610 Project 2 Operating Systems Vulnerabilities (Windows and Linux) CST 610 Project 3 Assessing Information System Vulnerabilities and Risk CST 610 Project 4 Threat Analysis and Exploitation CST 610 Project 5 Cryptography CST 610 Project 6 Digital Forensics Analysis
Csec 610 Believe Possibilities / snaptutorial.com



Csec 610 Believe Possibilities / snaptutorial.comDavis10a
Ěý
For more classes visit
www.snaptutorial.com
CSEC 610 Project 1 Information Systems and Identity Management
CSEC 610 Project 2 Operating Medical Device Cybersecurity : A Regulatory Perspective



Medical Device Cybersecurity : A Regulatory PerspectiveJon Lendrum
Ěý
The document summarizes a presentation on cybersecurity regulations for medical devices. It discusses how the FDA regulates cybersecurity through guidance documents and interpretations of quality system regulations, despite no explicit authority. The presentation reviews FDA recommendations for documenting cybersecurity in premarket submissions and debunks common myths. Senator Blumenthal introduced legislation to further require cybersecurity testing and transparency.

La descentralizaciĂłnleonelcamacaro
Ěý
La descentralizaciĂłn es una polĂtica que busca transferir poder del gobierno central a las regiones y localidades para construir un paĂs más justo. Involucra la transferencia de competencias administrativas y decisiones polĂticas a los gobiernos locales. Tiene caracterĂsticas sociopolĂticas, econĂłmicas, administrativas e institucionales.More Related Content
What's hot (20)
A Proposed Blueprint of a “privacy first” Pan Canadian Disease Contact Tracin...



A Proposed Blueprint of a “privacy first” Pan Canadian Disease Contact Tracin...Hisham Al Zanoon
Ěý
Disease Tracing is a vital tool but it needs to be designed following the key privacy by design principles.11 Most Common HIPAA Violations 



11 Most Common HIPAA Violations MariaClark32
Ěý
https://www.etacticsinc.com/
A HIPAA violation can cost a maximum of $1.5 million per year for violations of an identical provision and a lot of the time these are common HIPAA violations that can easily be adjusted.
When HIPAA was enacted on August 21, 1996, it turned the entire healthcare industry on its head. More than 20 years later, and many healthcare organizations constantly struggle when attempting to stay on top of everything this government regulation entails.
So what are some of the most common types of HIPAA violations?SeaCat: and SDN End-to-end Application Containment ArchitecTure



SeaCat: and SDN End-to-end Application Containment ArchitecTureUS-Ignite
Ěý
SeaCat: and SDN End-to-end Application Containment ArchitecTure a presentation by Jacobus Van der Merwe, U. Utah at US Ignite ONF GENI workshop on October 8, 2013Understanding Cybersecurity in Medical Devices and Applications



Understanding Cybersecurity in Medical Devices and ApplicationsEMMAIntl
Ěý
One of the major pillars of the current Industry 4.0 is Automation. Indeed, technology is intervening in almost every domain to “automate” the workforce and make human life easier and better. In the present age, machines are getting integrated with the Internet of Things, Cloud Computing, and Artificial Intelligence with the data flow being transferred and processed via the Internet. These changes indeed catalyze the overall productivity, but also expose data to the public
domains.
In cases of continuous data transfers and exposition, Cybersecurity becomes a pivotal element where it not only protects the data but also proactively provides mechanisms to defend against malicious attacks and malware. In the case of medical devices that include sensitive medical data flows and software-controlled hardware devices like heart implants or Continuous Glucose Monitoring (CGM) devices, Cybersecurity becomes an important factor for contributing towards system safety and quality...011918 espionage health_check_fact_sheet_rs



011918 espionage health_check_fact_sheet_rsRichard Smiraldi
Ěý
The document discusses an Espionage Health Check service that assesses organizations for cybersecurity vulnerabilities and potential breaches. The service includes on-site assessments of critical systems, network inspection, forensic analysis of disks and memory, and scanning systems for malware. Using intelligence from over 8,000 confirmed breaches, the experts can identify suspicious activity, malware, and areas of risk. The health check provides a report that summarizes any issues found and recommendations to strengthen defenses against cyber threats and espionage.INFOGRAPHIC: IS YOUR PATIENT DATA PROTECTED?



INFOGRAPHIC: IS YOUR PATIENT DATA PROTECTED?Diaspark
Ěý
According to OCR, there were 253 breaches affecting 500 individuals or more w/ a combined loss of over 112M records. Healthcare Failing to secure their data
48% encountered a data breach or failed a compliance audit in the last 12 months
26% are protecting data because of a past data breach
138% jump in number of breached healthcare records since 2012
The estimated cost for HIPAA breaches since 2009 has reached over 31 billion dollars.
Healthcare IT Challenges
42% of 2014 data breaches were in healthcare
90% of healthcare organizations have had at least 1 data breach in past 2 years
40% report that they have had more than 5 incidents of the entire U.S population was impacted by cybercrime in 9 months
Healthcare Cost of Breach
29% Reputation and brand damage
21% lost productivity
19% Lost Revenue
12% Forensics
10% Technical Support
8% Compliance Regulatory
With Data breaches expected to reach $2.1 trillion globally by 2019, which is four times the expected cost for cybercrime in 2015, It's apparent that a new approach to data security is needed if organizations are to stay ahead of the attackers and more effectively protect their intellectual property, data, customer information, employees, and their bottom lines against data breaches in the future
Contact us to learn how to safeguard against such breaches and implement it security strategy.
Risk management in Healthcare on Cloud



Risk management in Healthcare on CloudSandeep Sharma IIMK Smart City,IoT,Bigdata,Cloud,BI,DW
Ěý
Quickly made presentation in two hours
Security Risk Management in Healthcare on Cloud using NIST guidelines
More details: (blog: http://sandyclassic.wordpress.com ,
linkedin: ie.linkedin.com/in/sandepsharma/)Cloud Computing: Scalable and Secure Sharing of Personal Health Records Using...



Cloud Computing: Scalable and Secure Sharing of Personal Health Records Using...dbpublications
Ěý
Personal health record (PHR) is an emerging patient-centric model of health information exchange, which is often outsourced to be stored at a third party, such as cloud providers. However, there have been wide privacy concerns as personal health information could be exposed to those third party servers and to unauthorized parties. To assure the patients’ control over access to their own PHRs, it is a promising method to encrypt the PHRs before outsourcing. Yet, issues such as risks of privacy exposure, scalability in key management, flexible access, and efficient user revocation, have remained the most important challenges toward achieving fine-grained, cryptographically enforced data access control. In this paper, we propose a novel patient-centric framework and a suite of mechanisms for data access control to PHRs stored in semi trusted servers. To achieve fine-grained and scalable data access control for PHRs, we leverage attribute-based encryption (ABE) techniques to encrypt each patient’s PHR file. Different fr previous works in secure data outsourcing, we focus on the multiple data owner scenario, and divide the users in the PHR system into
multiple security domains that greatly reduces the key management complexity for owners and users. A high degree of patient privacy is guaranteed simultaneously by exploiting multi authority ABE. Our scheme also enables dynamic modification of access policies or file attributes, supports efficient on-demand user/attribute revocation and break-glass access under emergency scenarios.Cyb 610 Enhance teaching / snaptutorial.com



Cyb 610 Enhance teaching / snaptutorial.comBaileyaby
Ěý
This document outlines the requirements for a project assessing operating system vulnerabilities in Windows and Linux. The student is tasked with conducting a security assessment report (SAR) on the state of operating systems used by an oil and gas company. In addition, the student must create a nontechnical narrated presentation summarizing the SAR for leadership. The project involves researching vulnerabilities in key operating systems, analyzing security incidents that occurred, and providing recommendations to address risks and strengthen security posture. CYB 610 Effective Communication/tutorialrank.com



CYB 610 Effective Communication/tutorialrank.comjonhson199
Ěý
For more course tutorials visit
www.tutorialrank.com
CYB 610 Project 1 Information Systems and Identity Management
CYB 610 Project 2 Operating Systems Vulnerabilities (Windows and Linux)
CYB 610 Project 3 Assessing Information System Vulnerabilities and Risk
Medical device security presentation - Frank Siepmann



Medical device security presentation - Frank SiepmannFrank Siepmann
Ěý
Since I am not presenting (due to personal reasons) at the Medical Device Security conference 25/26 July 2016 in Arlington, VA I thought I post my slides about the current problems with Medical Device security and what can be done on a tactical level and what is needed at a strategic level.CSEC 610 Education Specialist / snaptutorial.com



CSEC 610 Education Specialist / snaptutorial.comMcdonaldRyan78
Ěý
For more classes visit
www.snaptutorial.com
CSEC 610 Project 1 Information Systems and Identity Management
CSEC 610 Project 2 Operating Systems Vulnerabilities (Windows and Linux)
CST 610 Effective Communication/tutorialrank.com



CST 610 Effective Communication/tutorialrank.comjonhson198
Ěý
This document outlines 6 cybersecurity projects for a course. Project 2 tasks the student to assess operating system vulnerabilities in a company's Windows and Linux systems. The student is to conduct a security assessment report (SAR) on the state of the operating systems and create a non-technical presentation summarizing their findings for leadership. The student will need to understand both Windows and Linux technologies to complete vulnerability scanning.Csec 610 Enhance teaching / snaptutorial.com



Csec 610 Enhance teaching / snaptutorial.comBaileyabv
Ěý
For more classes visit
www.snaptutorial.com
CSEC 610 Project 1 Information Systems and Identity Management
CSEC 610 Project 2 Operating Systems Vulnerabilities (Windows and Linux)
CSEC 610 Project 3 Assessing Information System Vulnerabilities and Risk
CSEC 610 Project 4 Threat Analysis and Exploitation
Cyb 610Education Specialist / snaptutorial.com



Cyb 610Education Specialist / snaptutorial.comMcdonaldRyan80
Ěý
CYB 610 Project 1 Information Systems and Identity Management
CYB 610 Project 2 Operating Systems Vulnerabilities (Windows and Linux)
CYB 610 Project 3 Assessing Information System Vulnerabilities and Risk
CYB 610 Project 4 Threat Analysis and Exploitation
Cyb 610 Education Organization-snaptutorial.com



Cyb 610 Education Organization-snaptutorial.comrobertlesew8
Ěý
For more classes visit
www.snaptutorial.com
CYB 610 Project 1 Information Systems and Identity Management
CYB 610 Project 2 Operating Systems Vulnerabilities (Windows and Linux)
CYB 610 Project 3 Assessing Information System Vulnerabilities and Risk
CYB 610 Project 4 Threat Analysis and Exploitation
CYB 610 Project 5 Cryptography
CYB 610 Project 6 Digital Forensics Analysis
Cyb 610 Believe Possibilities / snaptutorial.com



Cyb 610 Believe Possibilities / snaptutorial.comDavis12a
Ěý
For more classes visit
www.snaptutorial.com
CYB 610 Project 1 Information Systems and Identity Management
CYB 610 Project 2 Operating CST 610 RANK Redefined Education--cst610rank.com



CST 610 RANK Redefined Education--cst610rank.comclaric240
Ěý
FOR MORE CLASSES VISIT
www.cst610rank.com
CST 610 Project 1 Information Systems and Identity Management CST 610 Project 2 Operating Systems Vulnerabilities (Windows and Linux) CST 610 Project 3 Assessing Information System Vulnerabilities and Risk CST 610 Project 4 Threat Analysis and Exploitation CST 610 Project 5 Cryptography CST 610 Project 6 Digital Forensics Analysis
Csec 610 Believe Possibilities / snaptutorial.com



Csec 610 Believe Possibilities / snaptutorial.comDavis10a
Ěý
For more classes visit
www.snaptutorial.com
CSEC 610 Project 1 Information Systems and Identity Management
CSEC 610 Project 2 Operating Medical Device Cybersecurity : A Regulatory Perspective



Medical Device Cybersecurity : A Regulatory PerspectiveJon Lendrum
Ěý
The document summarizes a presentation on cybersecurity regulations for medical devices. It discusses how the FDA regulates cybersecurity through guidance documents and interpretations of quality system regulations, despite no explicit authority. The presentation reviews FDA recommendations for documenting cybersecurity in premarket submissions and debunks common myths. Senator Blumenthal introduced legislation to further require cybersecurity testing and transparency.A Proposed Blueprint of a “privacy first” Pan Canadian Disease Contact Tracin...



A Proposed Blueprint of a “privacy first” Pan Canadian Disease Contact Tracin...Hisham Al Zanoon
Ěý
Viewers also liked (13)


La descentralizaciĂłnleonelcamacaro
Ěý
La descentralizaciĂłn es una polĂtica que busca transferir poder del gobierno central a las regiones y localidades para construir un paĂs más justo. Involucra la transferencia de competencias administrativas y decisiones polĂticas a los gobiernos locales. Tiene caracterĂsticas sociopolĂticas, econĂłmicas, administrativas e institucionales.Quanta voglia hai di correre?



Quanta voglia hai di correre?Chiesa Cristiana Evangelica della Vera Vite
Ěý
Inizia un nuovo anno: quanta voglia hai di correre con Cristo durante il 2017?



Boletim 27 05-2016Thiago Tavares
Ěý
O dĂłlar fechou em alta de 0,38% no Brasil, influenciado pela possibilidade de aumento de juros nos EUA. Investidores continuaram cautelosos com o noticiário polĂtico no Brasil envolvendo gravações que derrubaram ministros. Os preços internacionais de commodities agrĂcolas tiveram pouca variação na semana.Final



FinalAnne-Stuart Teter
Ěý
This document provides contact information for Carol L. Amernick, a certified public accountant and business consultant. Ms. Amernick is the president of her firm, Carol L. Amernick, CPAs & Business Consultants, located at 2505 Waco Street in Henrico, Virginia. The document lists her office phone number, toll-free number, fax number, email address, and website.Sisense and Simba MongoDB Analytics Webinar



Sisense and Simba MongoDB Analytics WebinarSimba Technologies
Ěý
In this joint webinar between Sisense and Simba you will learn how to access, prepare and analyze data in MongoDB using Sisense BI. Sisense Product Manager Evan Castle goes over a sample automated analytics workflow for MongoDB leveraging Simba ODBC connectivity, schema auto-discovery and customization. You can watch the video recording at http://www.simba.com/webinar/operations-insights-mongodb-sisense-simba-odbc/Mali ulke raporu_2013



Mali ulke raporu_2013UlkeRaporlari2013
Ěý
Direkt indirmek için tıklayınız: --> http://bit.ly/1Bayg08ALFA ROMEO ALFETTA: AN INCREDIBLE ADVENTURE IN 1973!



ALFA ROMEO ALFETTA: AN INCREDIBLE ADVENTURE IN 1973!Maurizio Sala
Ěý
This article has been extracted from the magazine “Il Quadrifoglio”, the house organ of Alfa Romeo printed from 1966 to 1973. This is the #28, issued in november 1973. A present for all the Alfa enthusiastic. A great raid of 26,000 km, in 29 days. Great Alfetta! Ingiltere ulke raporu_2013



Ingiltere ulke raporu_2013UlkeRaporlari2013
Ěý
Direkt indirmek için bu linki kullanın.
http://bit.ly/1CvguluPakistan ulke raporu_2013



Pakistan ulke raporu_2013UlkeRaporlari2013
Ěý
Direkt indirmek için tıklayınız: --> http://bit.ly/1sG3ppcSimilar to LiPari_MedicalDevices (20)
Privacy and Security by Design



Privacy and Security by DesignUnisys Corporation
Ěý
Privacy and Security by Design Spotlight Presentation at HIMMS Privacy and Security Forum, December 5th 2016. Presented by Jeff R. Livingstone, PhD, Vice President and Global Lead, Life Sciences & Healthcare, Unisys Corporation.Threatsploit Adversary Report January 2019



Threatsploit Adversary Report January 2019Briskinfosec Technology and Consulting Pvt Ltd
Ěý
“Many organizations security defences have been smacked Their earned reputation within a flash have been jacked Heartless jokes on them by others also have been cracked How come they’re sure that their firms haven’t been hacked?" THE FDA and Medical Device Cybersecurity Guidance



THE FDA and Medical Device Cybersecurity GuidancePam Gilmore
Ěý
The document discusses the FDA's guidance on medical device cybersecurity. It outlines that the FDA's scope goes beyond HIPAA and includes risk analysis for devices and networks. Researchers identified vulnerabilities in 300 medical devices in 2013. The FDA issued a safety communication in 2013 calling for cybersecurity safeguards for devices and networks. A risk analysis model for devices includes privacy, availability, authentication, integrity, non-repudiation and safety factors. Manufacturers must now include cybersecurity risk analyses and protections in device design submissions to the FDA and disclose security features through an industry standard form. Intrusion detection aims to identify unauthorized access attempts and advanced persistent threats can be detected through Splunk monitoring of foreign access attempts.Hot Topics in Privacy and Security



Hot Topics in Privacy and SecurityPYA, P.C.
Ěý
PYA Principal Barry Mathis presented “Hot Topics in Privacy and Security,” at the Florida Hospital Association's 14th Annual Health Care Corporate Compliance Education Retreat.
The presentation explored:
• Changes in the privacy and security ecosystem.
• Emerging technology risks and hot topics.
• What happens to hacked data.
• How to best protect data.Cybersecurity



CybersecurityChristopher Daza
Ěý
ybersecurity is an increasing
concern for many in the
medical cybersecurity and
information technology
professions. As computerized
devices in medical facilities
become increasingly networked
within their own walls and
with external facilities, the risk
of cyberattacks also increases,
threatening confidentiality,
safety, and well-being. This
article describes what health
care organizations and
imaging professionals should
do to minimize the risks.IoT tietoturva terveydenhuollossa, 2017-03-21, gko



IoT tietoturva terveydenhuollossa, 2017-03-21, gkoGlen Koskela
Ěý
Finnish Information Security Cluster meeting on March 21st in Helsinki. IoT in healthcare and the various current and emerging cyber security risks IoT brings into healthcare environment, especially hospitals, and their security requirements and frameworks; includes some examples of dark web activity.
Healthcare Attorneys Feel the Healthcare Industry Is More Vulnerable to Cyber...



Healthcare Attorneys Feel the Healthcare Industry Is More Vulnerable to Cyber...mosmedicalreview
Ěý
Electronic medical records have many advantages, but a growing concern with this system is their vulnerability to cyberattacks.The FDA - Mobile, and Fixed Medical Devices Cybersecurity Guidance



The FDA - Mobile, and Fixed Medical Devices Cybersecurity GuidanceValdez Ladd MBA, CISSP, CISA,
Ěý
This presentation is intended for the customer facing risk managers, sales staff, and IT staff of a medical device manufacturer and their medical doctors and IT hospital and clinical counterparts.
It is intended to give an overview and highlight process considerations for incident management and reporting of cybersecurity issues.
It is based on the technical paper published by Pam Gilmore and Valdez Ladd in the ISSA Journal in 2014.Safety of protected health information (phi)



Safety of protected health information (phi)Josette Pribilla
Ěý
Protected health information (PHI) refers to any identifiable patient information disclosed for healthcare services. The Healthcare Insurance Portability and Accountability Act (HIPAA) protects PHI and requires healthcare providers to notify patients of any breaches. Common types of breaches involve hacking, malware attacks, and accidental sharing of electronic health records. Healthcare organizations implement encryption, passwords, audit trails, and firewalls to safeguard PHI and comply with HIPAA security rules.INCIDENT RESPONSE PLAN FOR A SMALL TO MEDIUM SIZED HOSPITAL



INCIDENT RESPONSE PLAN FOR A SMALL TO MEDIUM SIZED HOSPITALIJNSA Journal
Ěý
Most small to medium health care organizations do not have the capability to address cyber incidents within the organization. Those that do are poorly trained and ill equipped. These health care organizations are subject to various laws that address privacy concerns, proper handling of financial information, and Personally Identifiable Information. Currently an IT staff handles responses to these incidents in an Ad Hoc manner. A properly trained, staffed, and equipped Cyber Incident Response Team is needed to quickly respond to these incidents to minimize data loss, and provide forensic data for the purpose of notification, disciplinary action, legal action, and to remove the risk vector. This paper1 will use the proven Incident Command System model used in emergency services to show any sized agency can have an adequate CIRT.Running head Information security threats 1Information secur.docx



Running head Information security threats 1Information secur.docxwlynn1
Ěý
Running head: Information security threats 1
Information security threats 7
Information security threats
Khaleem Pasha Mohammad
Campbellsville University
Introduction
The development of technology has been greatly embraced in hospitals, saved innumerable lives, and improved the quality of care provision. Not exclusively has technology changed patients knowledgeable and of their families but further consideration has had a significant impact on the strategy and practices of practitioners. One in every five of the areas that have greatly embraced technology is care data. Technology has helped inside the treatment of care records through the introduction of electronic health records, that's exchange paper records. With the availability of electronic care record (EHR) systems, a nurse can merely check for patients’ allergies, case history, weight, age, and prescription through the press of a button. However, the most quantity as institutions are clasp technology to stay up their health records, there are series of risks associated with these technologies. Since the start of technology inside the upkeep of care records, the care trade has been a primary target for cyber crimes. The motives behind cyber-attacks on care are clear as insurance firms, hospitals, care clinics, and totally different care suppliers keep health records that contain valuable information. The use of America Department of Health and Human Services for Civil Rights has acknowledged that over 100 million people square measure suffering from care data security breach. Gregorian calendar month 2015 was a foul month for electronic data jointly of the most important hacks on health care records on Anthem Blue Cross resulting in over seventy-eight million patients’ health data was taken. The cyber-attack scarf sensitive data that contained social securities, names, and residential addresses of people. Constant year, Premera Blue Cross reported that a cyber-attack has exposed medical information of over eleven million customers. Back in 2011, over 4.9 million health records were taken electronically from Science Application International Corporation. These are few cases of a care data breach with sensitive data falling into the hands of third parties. In guaranteeing that there are privacy and security in care records, bureau insurance mobility and responsibility (HIPPA) is providing legislation that hospital and totally different institutions that handle patient’s data to adopt in guaranteeing that varied security measures are enforced in protecting data.
HIPPA and Security Compliance
As much as institutions are clasp technology in storing care data, it is vital for institutions like HIPPA to regulate these bodies to substantiate that shopper rights are protected. The HIPAA Security Rule provides that electronic records of patients got to be protected in any respect times from any unauthorized access nonetheless the information being at rest or in transit.Data Breach: It Can Happen To You



Data Breach: It Can Happen To YouCooperative of American Physicians, Inc.
Ěý
Health care providers have become prime targets of cyber criminals, since they hold a treasure trove of irresistible data, including Social Security numbers and medical records (think access to prescription painkillers). As cyber criminals become more sophisticated, medical practices are more vulnerable than ever.
In this webinar "Data Breach: It Can Happen To You," hosted by the Cooperative of American Physicians, Inc. (CAP), viewers will learn:
+ What a data breach is
+ Its economic impact
+ Why the threat is growing
+ Steps to take to protect yourself
+ The must-dos in the event of a breach
Watch the webinar here —> https://youtu.be/mqdMA-UZNy0
About Our Presenters:
Melvin Osswald, Vice President Program Underwriting, NAS Insurance — Ms. Osswald joined NAS in 2002 and specializes in health care, cyber liability, employment practice, directors and officers coverage. Ms. Osswald currently supports NAS’ reinsurance programs and oversees the underwriting and product development of Billing Errors and Omissions, Cyber Liability, Employment Practices Liability, and Directors and Officers programs created to address the new exposures facing health care providers. She has been featured as a guest speaker at various industry conferences addressing the evolving professional liability risks in health care, and served on the Steering Committee of the Southern California Chapter of the Professional Liability Underwriting Society.
Chris Reese, Vice President, Director of Underwriting, NAS Insurance — As part of NAS’ key management team, Ms. Reese provides insurance solutions for clients in the health care industry. She has held leadership positions on both the underwriting and retail broker sides of the business, and has worked in the London market for a reinsurance intermediary. Ms. Reese has been involved with cyber risk insurance for the health care industry since 2004, providing coverage to physicians, medical groups, and integrated delivery systems.
MORE SLIDESHARE PRESENTATIONS
http://www.slideshare.net/capphysicians/presentations
VISIT OUR WEBSITE
http://www.cappphysicians.com
LET'S CONNECT
Twitter: http://www.twitter.com/CAPphysicians
LinkedIn: https://www.linkedin.com/company/cooperative-of-american-physicians-inc-
Facebook: http://www.facebook.com/CooperativeofAmericanPhysiciansInc
Youtube: http://youtube.com/CAPphysicians
Google+: http://www.google.com/+CapphysiciansCybersécurité des dispositifs médicaux



Cybersécurité des dispositifs médicauxMarket iT
Ěý
Cybersecurity risks to medical devices and healthcare systems have increased due to greater connectivity of devices, software use, and data sharing. Recent incidents highlight vulnerabilities that could disrupt care, compromise data, or directly endanger patients if devices are attacked. Regulators and industry stakeholders must collaborate to address both security and safety issues through coordinated risk management and standards application over medical device lifecycles.Ivanti threat thursday deck october v2



Ivanti threat thursday deck october v2Ivanti
Ěý
The document summarizes discussions from a webinar on prioritizing risk. It describes several recent healthcare and retail cyber attacks, including a ransomware attack on a large hospital system that affected over 80 sites, a ransomware attack disrupting clinical trial data, and a ransomware group stealing unencrypted patient data from a hospital and demanding ransom. It then discusses challenges with vulnerability management and the need for improved communication between security and operations teams. The document promotes a product for prioritizing patch risk and compliance through features like risk-based prioritization and tracking out-of-compliance systems. It ends with a reminder to stay vigilant of cyber threats during the US election period.Digital Health Data



Digital Health DataShahidul Islam Khan Nayeem
Ěý
1) The document discusses privacy and security risks associated with digital health data. It provides statistics showing that attacks on healthcare organizations' data have increased by 1.25 times in the last five years compared to previously.
2) On average, each data breach incident in healthcare organizations results in the compromise of over 18,000 patient records. The cost of each breached record is also highest for healthcare at $363.
3) Criminal attacks are now the leading cause of data breaches in healthcare, surpassing unintentional leaks and insider breaches. The document recommends measures to reduce privacy and security risks when integrating digital health data.Systems Thinking on a National Level, Part 2Drew David.docx



Systems Thinking on a National Level, Part 2Drew David.docxperryk1
Ěý
This document discusses various cybersecurity threats faced by the healthcare industry, including phishing emails, SQL injection attacks, eavesdropping, and viruses. Phishing emails are a major issue, accounting for 93% of breached healthcare data. Hackers use phishing emails that appear legitimate to trick staff into revealing sensitive information. The document also examines ways to better protect against these threats, such as password protection, data loss prevention, access controls, and staff training. Overall, the document analyzes the cybersecurity risks healthcare organizations face and ways to decrease breaches through education and prevention methods.Top 5 Challenges in Healthcare Data Security & Their Solutions



Top 5 Challenges in Healthcare Data Security & Their SolutionsSaad Sarwar
Ěý
Explore the top 5 data security challenges facing the healthcare industry today and discover practical solutions to protect sensitive patient information.Cybercrime and the Healthcare Industry



Cybercrime and the Healthcare IndustryEMC
Ěý
This white paper discusses the various cyber threats targeting healthcare organizations and the challenges security professionals face in securing access to protected health information.
TIPPSS for Enabling & Securing our Increasingly Connected World – Trust, Iden...



TIPPSS for Enabling & Securing our Increasingly Connected World – Trust, Iden...PacificResearchPlatform
Ěý
Securing Research Data: A Workshop on Emerging Practices in Computation and
Storage for Sensitive Data - August 22, 2019
Florence Hudson, Founder and CEO, FDHint LLC
NSF Cybersecurity Center of Excellence, Indiana University - Special Advisor
Northeast Big Data Innovation Hub, Columbia University – Special Advisor
IEEE Engineering in Medicine and Biology Society – Standards Committee
Cybersecurity Challenges in Healthcare



Cybersecurity Challenges in HealthcareDoug Copley
Ěý
This document discusses cybersecurity challenges in healthcare. It begins with an agenda covering healthcare cybersecurity headlines, trends, unique issues, practical remedies, where to begin, and building security collaboratively. It then covers each agenda item in more detail. The document emphasizes that healthcare data is highly valuable to hackers and outlines trends like increasing ransomware attacks and data breaches. It describes unique challenges for healthcare like medical devices and real-time access needs. Practical steps are outlined like risk assessments, policies, access controls, and partnering with groups like state agencies and information sharing organizations.TIPPSS for Enabling & Securing our Increasingly Connected World – Trust, Iden...



TIPPSS for Enabling & Securing our Increasingly Connected World – Trust, Iden...PacificResearchPlatform
Ěý
LiPari_MedicalDevices
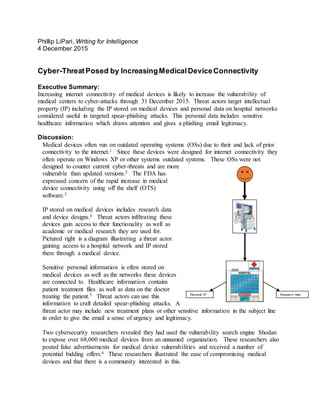
- 1. Phillip LiPari, Writing for Intelligence 4 December 2015 Cyber-ThreatPosed by IncreasingMedicalDeviceConnectivity Executive Summary: Increasing internet connectivity of medical devices is likely to increase the vulnerability of medical centers to cyber-attacks through 31 December 2015. Threat actors target intellectual property (IP) including the IP stored on medical devices and personal data on hospital networks considered useful in targeted spear-phishing attacks. This personal data includes sensitive healthcare information which draws attention and gives a phishing email legitimacy. Discussion: Medical devices often run on outdated operating systems (OSs) due to their and lack of prior connectivity to the internet.1 Since these devices were designed for internet connectivity they often operate on Windows XP or other systems outdated systems. These OSs were not designed to counter current cyber-threats and are more vulnerable than updated versions.2 The FDA has expressed concern of the rapid increase in medical device connectivity using off the shelf (OTS) software.3 IP stored on medical devices includes research data and device designs.4 Threat actors infiltrating these devices gain access to their functionality as well as academic or medical research they are used for. Pictured right is a diagram illustrating a threat actor gaining access to a hospital network and IP stored there through a medical device. Sensitive personal information is often stored on medical devices as well as the networks these devices are connected to. Healthcare information contains patient treatment files as well as data on the doctor treating the patient.5 Threat actors can use this information to craft detailed spear-phishing attacks. A threat actor may include new treatment plans or other sensitive information in the subject line in order to give the email a sense of urgency and legitimacy. Two cybersecurity researchers revealed they had used the vulnerability search engine Shodan to expose over 68,000 medical devices from an unnamed organization. These researchers also posted false advertisements for medical device vulnerabilities and received a number of potential bidding offers.6 These researchers illustrated the ease of compromising medical devices and that there is a community interested in this. Personal IP Research data
- 2. Source Reliability: High Analytic Confidence: Medium Analytic Confidence: The analyst worked with a small group to compile this information. The deadline was reasonable and the information was simple to find. The analyst did not use structured analytic methods. With questions and comments, please contact the author: Phillip LiPari 1 http://gizmodo.com/thousands-of-medical-devices-are-open-to-hacking-over-t-1733961503 (M) 2 https://blogs.microsoft.com/cybertrust/2013/08/15/the-risk-of-running-windows-xp-after-support-ends-april- 2014/ (L) 3 http://www.fda.gov/RegulatoryInformation/Guidances/ucm077812.htm (H) 4 http://www.pabstpatent.com/medical-devices (H) 5 http://www.forbes.com/sites/bernardmarr/2015/04/21/how-big-data-is-changing-healthcare/ (M) 6 http://www.bbc.com/news/technology-34390165 (M)


