Lock based protocols
Download as PPTX, PDF0 likes3,071 views
This document discusses lock-based protocols for concurrency control. It describes that locks can be requested in exclusive or shared mode to control concurrent access to data items. A lock compatibility matrix is used to determine if a requested lock is compatible with existing locks held by other transactions. The Two Phase Locking protocol is introduced to ensure conflict serializable schedules by restricting transactions to an growing phase where they only acquire locks and a shrinking phase where they only release locks.
1 of 7
Download to read offline






Recommended
Deadlock in database



Deadlock in databaseTayyab Hussain
╠²
in this slides the topic of database management system of deadlock is covered that help the students of database relevant subjects to easy learn..2 phase locking protocol DBMS



2 phase locking protocol DBMSDhananjaysinh Jhala
╠²
1) The two-phase locking protocol requires transactions to acquire locks in two phases - the growing phase where locks can be acquired but not released, and the shrinking phase where locks can be released but not acquired.
2) The two-phase locking protocol ensures conflict serializability by ordering transactions based on their lock points.
3) However, it does not prevent deadlocks and can cause cascading rollbacks if transactions release locks before committing. Modifications like strict two-phase locking prevent this by requiring locks to be held until commit.Concurrency control



Concurrency controlJaved Khan
╠²
Concurrency control protocols control simultaneous transactions in a database. There are two main categories: lock-based and timestamp-based. Lock-based protocols use locks to control access to data, which can be in exclusive or shared mode. Timestamp-based protocols assign timestamps to transactions and data items to determine if operations can be executed or must be rejected. Optimistic concurrency control validates transactions in three phases: execution, validation, and commit, enforcing rules to ensure serializability.Concurrency control



Concurrency controlSoumyajit Dutta
╠²
Concurrency control mechanisms use various protocols like lock-based, timestamp-based, and validation-based to maintain database consistency when transactions execute concurrently. Lock-based protocols use locks on data items to control concurrent access, with two-phase locking being a common approach. Timestamp-based protocols order transactions based on timestamps to ensure serializability. Validation-based protocols validate that a transaction's writes do not violate serializability before committing its writes.Validation based protocol



Validation based protocolBBDITM LUCKNOW
╠²
This protocol is used in the concurrency control techniques in DBMS. This ppt will help you to know about the validation based protocol in DBMS.Concurrency Control in Distributed Database.



Concurrency Control in Distributed Database.Meghaj Mallick
╠²
The document discusses various techniques for concurrency control in distributed databases, including locking-based protocols and timestamp-based protocols. Locking-based protocols use exclusive and shared locks to control concurrent access to data items. They can be implemented using a single or distributed lock manager. Timestamp-based protocols assign each transaction a unique timestamp to determine serialization order and manage concurrent execution.VALIDATION BASED PROTOCOL AND MULTIPLE GRANULARITY.pptx



VALIDATION BASED PROTOCOL AND MULTIPLE GRANULARITY.pptxSamyakJain710491
╠²
This document discusses validation based protocol, an optimistic concurrency control technique used in database management systems. It has three phases - read, validation, and write. In the read phase, transactions read data into local variables without updating the database. In the validation phase, a test checks for serializability violations between transactions. If there are no violations, the transaction commits its writes to the database in the write phase. The protocol uses timestamps to order transactions and avoid conflicts. It can avoid cascading rollbacks but has a risk of starvation for long transactions. The document also discusses multiple granularity locking, which defines a hierarchy of data sizes from fine to coarse granularity to control concurrent access.16. Concurrency Control in DBMS



16. Concurrency Control in DBMSkoolkampus
╠²
The document discusses various concurrency control techniques for database systems, including lock-based protocols, timestamp-based protocols, and graph-based protocols. Lock-based protocols use locks to control concurrent access to data with different lock modes. Timestamp-based protocols assign timestamps to transactions and manage concurrency to ensure transactions execute in timestamp order. Graph-based protocols impose a partial ordering on data items modeled as a directed acyclic graph.Deadlock dbms



Deadlock dbmsVardhil Patel
╠²
In this presentation all concept of deadlock is included. and it explain in less slides so easy to explain.
It is also useful for study.Transaction states and properties



Transaction states and propertiesChetan Mahawar
╠²
Transaction is a unit of program execution that accesses and possibly updates various data items.
Usually, a transaction is initiated by a user program written in a high-level data-manipulation language or programming language (for example, SQL,COBOL, C, C++, or Java), where it is delimited by statements (or function calls) of the form begin transaction and end transaction.Concurrency control



Concurrency controlSubhasish Pati
╠²
This document summarizes a student's research project on improving the performance of real-time distributed databases. It proposes a "user control distributed database model" to help manage overload transactions at runtime. The abstract introduces the topic and outlines the contents. The introduction provides background on distributed databases and the motivation for the student's work in developing an approach to reduce runtime errors during periods of high load. It summarizes some existing research on concurrency control in centralized databases.Concurrency Control in Database Management System



Concurrency Control in Database Management SystemJanki Shah
╠²
Contents:
1.What is Concurrency Control?
2.Lock Based Protocol
3.Two Phase Locking Protocol
4.Deadlock
serializability in dbms



serializability in dbmsSaranya Natarajan
╠²
The document discusses different types of schedules for transactions in a database including serial, serializable, and equivalent schedules. A serial schedule requires transactions to execute consecutively without interleaving, while a serializable schedule allows interleaving as long as the schedule is equivalent to a serial schedule. Equivalence is determined based on conflicts, views, or results between the schedules. Conflict serializable schedules can be tested for cycles in a precedence graph to determine if interleaving introduces conflicts, while view serializable schedules must produce the same reads and writes as a serial schedule.Deadlock



DeadlockRajandeep Gill
╠²
The document discusses deadlocks in computer systems. It defines deadlock, presents examples, and describes four conditions required for deadlock to occur. Several methods for handling deadlocks are discussed, including prevention, avoidance, detection, and recovery. Prevention methods aim to ensure deadlocks never occur, while avoidance allows the system to dynamically prevent unsafe states. Detection identifies when the system is in a deadlocked state.Free space managment46



Free space managment46myrajendra
╠²
This document discusses free space management techniques in operating systems. It explains the need to track free disk space and reuse it from deleted files. Various free space list implementations are described, including bit vector, linked list, grouping, and counting. Bit vector uses a bitmap to track free blocks, linked list links free blocks, grouping stores addresses of free blocks in blocks, and counting tracks free block runs with an address and count.File organization 1



File organization 1Rupali Rana
╠²
This document discusses different methods for organizing and indexing data stored on disk in a database management system (DBMS). It covers unordered or heap files, ordered or sequential files, and hash files as methods for physically arranging records on disk. It also discusses various indexing techniques like primary indexes, secondary indexes, dense vs sparse indexes, and multi-level indexes like B-trees and B+-trees that provide efficient access to records. The goal of file organization and indexing in a DBMS is to optimize performance for operations like inserting, searching, updating and deleting records from disk files.Transaction management DBMS



Transaction management DBMSMegha Patel
╠²
This document discusses transaction processing and concurrency control in database systems. It defines a transaction as a unit of program execution that accesses and possibly modifies data. It describes the key properties of transactions as atomicity, consistency, isolation, and durability. It discusses how concurrency control techniques like locking and two-phase locking protocols are used to ensure serializable execution of concurrent transactions.15. Transactions in DBMS



15. Transactions in DBMSkoolkampus
╠²
Transactions are units of program execution that access and update database items. A transaction must preserve database consistency. Concurrent transactions are allowed for increased throughput but can result in inconsistent views. Serializability ensures transactions appear to execute serially in some order. Conflict serializability compares transaction instruction orderings while view serializability compares transaction views. Concurrency control protocols enforce serializability without examining schedules after execution.11. Storage and File Structure in DBMS



11. Storage and File Structure in DBMSkoolkampus
╠²
The document discusses various types of physical storage media used in databases, including their characteristics and performance measures. It covers volatile storage like cache and main memory, and non-volatile storage like magnetic disks, flash memory, optical disks, and tape. It describes how magnetic disks work and factors that influence disk performance like seek time, rotational latency, and transfer rate. Optimization techniques for disk block access like file organization and write buffering are also summarized.deadlock avoidance



deadlock avoidancewahab13
╠²
Deadlock occurs when a set of blocked processes form a circular chain where each process waits for a resource held by the next process. There are four necessary conditions for deadlock: mutual exclusion, hold and wait, no preemption, and circular wait. The banker's algorithm avoids deadlock by tracking available resources and process resource needs, and only allocating resources to a process if it will not cause the system to enter an unsafe state where deadlock could occur. It uses matrices to represent allocation states and evaluates requests to ensure allocating resources does not lead to deadlock.Introduction TO Finite Automata



Introduction TO Finite AutomataRatnakar Mikkili
╠²
This document provides an introduction to finite automata. It defines key concepts like alphabets, strings, languages, and finite state machines. It also describes the different types of automata, specifically deterministic finite automata (DFAs) and nondeterministic finite automata (NFAs). DFAs have a single transition between states for each input, while NFAs can have multiple transitions. NFAs are generally easier to construct than DFAs. The next class will focus on deterministic finite automata in more detail.Query optimization



Query optimizationPooja Dixit
╠²
Query Optimization, Importance, Query Processing, A Query-Evaluation Plan, Cost based Optimization (Physical), Heuristic Optimization (Logical), External sorting, External Merge sort, two-way merge sort
Transaction processing ppt



Transaction processing pptJaved Khan
╠²
This document discusses transaction processing systems (TPS). It defines a transaction as a group of tasks that updates or retrieves data. A TPS collects, stores, modifies and retrieves enterprise data transactions. Transactions must follow the ACID properties - atomicity, consistency, isolation, and durability. There are two types of TPS - batch processing, which collects and stores data in batches, and real-time processing, which immediately processes data. Long duration transactions pose challenges as user interaction is required and partial data may be exposed if not committed. Nested transactions and alternatives to waits and aborts can help manage long-running transactions.concurrency-control



concurrency-controlSaranya Natarajan
╠²
- Concurrency control manages simultaneous database operations to prevent interference. This avoids issues like lost updates, dirty reads, and incorrect summaries.
- Lock-based protocols use locks to control concurrent access. Timestamp-based protocols assign timestamps to transactions to determine execution order.
- The two-phase locking protocol acquires all locks in a "growing" phase before releasing any locks in a "shrinking" phase, ensuring serializability. Variations include strict two-phase locking and rigorous two-phase locking.
- Timestamp-based protocols assign timestamps to transactions and check for conflicts between read/write operations and timestamps to ensure serial ordering. Thomas' write rule modifies checking for some write operations.Functional dependency



Functional dependencyTamajit Chakraborty
╠²
The document defines functional dependencies and describes how they constrain relationships between attributes in a database relation. A functional dependency X ŌåÆ Y means the Y attribute is functionally determined by the X attribute(s). The closure of a set of functional dependencies includes all dependencies that can be logically derived. Normalization aims to eliminate anomalies by decomposing relations based on their functional dependencies until a desired normal form is reached.13. Query Processing in DBMS



13. Query Processing in DBMSkoolkampus
╠²
The document discusses various steps and algorithms for processing database queries. It covers parsing and optimizing queries, estimating query costs, and algorithms for operations like selection, sorting, and joins. Selection algorithms include linear scans, binary searches, and using indexes. Sorting can use indexes or external merge sort. Join algorithms include nested loops, merge join, and hash join.Binary Search Tree



Binary Search Treesagar yadav
╠²
Binary search trees are binary trees where all left descendants of a node are less than the node's value and all right descendants are greater. This structure allows for efficient search, insertion, and deletion operations. The document provides definitions and examples of binary search tree properties and operations like creation, traversal, searching, insertion, deletion, and finding minimum and maximum values. Applications include dynamically maintaining a sorted dataset to enable efficient search, insertion, and deletion.Databases: Normalisation



Databases: NormalisationDamian T. Gordon
╠²
Normalisation is a process that structures data in a relational database to minimize duplication and redundancy while preserving information. It aims to ensure data is structured efficiently and consistently through multiple forms. The stages of normalization include first normal form (1NF), second normal form (2NF), third normal form (3NF), Boyce-Codd normal form (BCNF), fourth normal form (4NF) and fifth normal form (5NF). Higher normal forms eliminate more types of dependencies to optimize the database structure.concurrency control



concurrency controlrajshreemuthiah
╠²
This document provides an overview of concurrency control and two-phase locking protocol. It discusses lock-based concurrency control, two-phase locking protocol, deadlocks, and strategies for handling deadlocks such as deadlock prevention, avoidance, and detection and recovery. The key aspects covered are the lock compatibility matrix, differences between shared and exclusive locks, requirements for serializability under two-phase locking, and the four conditions required for a deadlock.Cs501 concurrency



Cs501 concurrencyKamal Singh Lodhi
╠²
This document discusses concurrency control and recovery techniques for databases. It covers various notions of serializability and recoverability. It describes lock-based protocols like two-phase locking and graph-based protocols like tree protocols. It discusses issues like deadlocks, cascading rollbacks, and starvation. It also covers deadlock handling techniques like prevention, detection and recovery.More Related Content
What's hot (20)
Deadlock dbms



Deadlock dbmsVardhil Patel
╠²
In this presentation all concept of deadlock is included. and it explain in less slides so easy to explain.
It is also useful for study.Transaction states and properties



Transaction states and propertiesChetan Mahawar
╠²
Transaction is a unit of program execution that accesses and possibly updates various data items.
Usually, a transaction is initiated by a user program written in a high-level data-manipulation language or programming language (for example, SQL,COBOL, C, C++, or Java), where it is delimited by statements (or function calls) of the form begin transaction and end transaction.Concurrency control



Concurrency controlSubhasish Pati
╠²
This document summarizes a student's research project on improving the performance of real-time distributed databases. It proposes a "user control distributed database model" to help manage overload transactions at runtime. The abstract introduces the topic and outlines the contents. The introduction provides background on distributed databases and the motivation for the student's work in developing an approach to reduce runtime errors during periods of high load. It summarizes some existing research on concurrency control in centralized databases.Concurrency Control in Database Management System



Concurrency Control in Database Management SystemJanki Shah
╠²
Contents:
1.What is Concurrency Control?
2.Lock Based Protocol
3.Two Phase Locking Protocol
4.Deadlock
serializability in dbms



serializability in dbmsSaranya Natarajan
╠²
The document discusses different types of schedules for transactions in a database including serial, serializable, and equivalent schedules. A serial schedule requires transactions to execute consecutively without interleaving, while a serializable schedule allows interleaving as long as the schedule is equivalent to a serial schedule. Equivalence is determined based on conflicts, views, or results between the schedules. Conflict serializable schedules can be tested for cycles in a precedence graph to determine if interleaving introduces conflicts, while view serializable schedules must produce the same reads and writes as a serial schedule.Deadlock



DeadlockRajandeep Gill
╠²
The document discusses deadlocks in computer systems. It defines deadlock, presents examples, and describes four conditions required for deadlock to occur. Several methods for handling deadlocks are discussed, including prevention, avoidance, detection, and recovery. Prevention methods aim to ensure deadlocks never occur, while avoidance allows the system to dynamically prevent unsafe states. Detection identifies when the system is in a deadlocked state.Free space managment46



Free space managment46myrajendra
╠²
This document discusses free space management techniques in operating systems. It explains the need to track free disk space and reuse it from deleted files. Various free space list implementations are described, including bit vector, linked list, grouping, and counting. Bit vector uses a bitmap to track free blocks, linked list links free blocks, grouping stores addresses of free blocks in blocks, and counting tracks free block runs with an address and count.File organization 1



File organization 1Rupali Rana
╠²
This document discusses different methods for organizing and indexing data stored on disk in a database management system (DBMS). It covers unordered or heap files, ordered or sequential files, and hash files as methods for physically arranging records on disk. It also discusses various indexing techniques like primary indexes, secondary indexes, dense vs sparse indexes, and multi-level indexes like B-trees and B+-trees that provide efficient access to records. The goal of file organization and indexing in a DBMS is to optimize performance for operations like inserting, searching, updating and deleting records from disk files.Transaction management DBMS



Transaction management DBMSMegha Patel
╠²
This document discusses transaction processing and concurrency control in database systems. It defines a transaction as a unit of program execution that accesses and possibly modifies data. It describes the key properties of transactions as atomicity, consistency, isolation, and durability. It discusses how concurrency control techniques like locking and two-phase locking protocols are used to ensure serializable execution of concurrent transactions.15. Transactions in DBMS



15. Transactions in DBMSkoolkampus
╠²
Transactions are units of program execution that access and update database items. A transaction must preserve database consistency. Concurrent transactions are allowed for increased throughput but can result in inconsistent views. Serializability ensures transactions appear to execute serially in some order. Conflict serializability compares transaction instruction orderings while view serializability compares transaction views. Concurrency control protocols enforce serializability without examining schedules after execution.11. Storage and File Structure in DBMS



11. Storage and File Structure in DBMSkoolkampus
╠²
The document discusses various types of physical storage media used in databases, including their characteristics and performance measures. It covers volatile storage like cache and main memory, and non-volatile storage like magnetic disks, flash memory, optical disks, and tape. It describes how magnetic disks work and factors that influence disk performance like seek time, rotational latency, and transfer rate. Optimization techniques for disk block access like file organization and write buffering are also summarized.deadlock avoidance



deadlock avoidancewahab13
╠²
Deadlock occurs when a set of blocked processes form a circular chain where each process waits for a resource held by the next process. There are four necessary conditions for deadlock: mutual exclusion, hold and wait, no preemption, and circular wait. The banker's algorithm avoids deadlock by tracking available resources and process resource needs, and only allocating resources to a process if it will not cause the system to enter an unsafe state where deadlock could occur. It uses matrices to represent allocation states and evaluates requests to ensure allocating resources does not lead to deadlock.Introduction TO Finite Automata



Introduction TO Finite AutomataRatnakar Mikkili
╠²
This document provides an introduction to finite automata. It defines key concepts like alphabets, strings, languages, and finite state machines. It also describes the different types of automata, specifically deterministic finite automata (DFAs) and nondeterministic finite automata (NFAs). DFAs have a single transition between states for each input, while NFAs can have multiple transitions. NFAs are generally easier to construct than DFAs. The next class will focus on deterministic finite automata in more detail.Query optimization



Query optimizationPooja Dixit
╠²
Query Optimization, Importance, Query Processing, A Query-Evaluation Plan, Cost based Optimization (Physical), Heuristic Optimization (Logical), External sorting, External Merge sort, two-way merge sort
Transaction processing ppt



Transaction processing pptJaved Khan
╠²
This document discusses transaction processing systems (TPS). It defines a transaction as a group of tasks that updates or retrieves data. A TPS collects, stores, modifies and retrieves enterprise data transactions. Transactions must follow the ACID properties - atomicity, consistency, isolation, and durability. There are two types of TPS - batch processing, which collects and stores data in batches, and real-time processing, which immediately processes data. Long duration transactions pose challenges as user interaction is required and partial data may be exposed if not committed. Nested transactions and alternatives to waits and aborts can help manage long-running transactions.concurrency-control



concurrency-controlSaranya Natarajan
╠²
- Concurrency control manages simultaneous database operations to prevent interference. This avoids issues like lost updates, dirty reads, and incorrect summaries.
- Lock-based protocols use locks to control concurrent access. Timestamp-based protocols assign timestamps to transactions to determine execution order.
- The two-phase locking protocol acquires all locks in a "growing" phase before releasing any locks in a "shrinking" phase, ensuring serializability. Variations include strict two-phase locking and rigorous two-phase locking.
- Timestamp-based protocols assign timestamps to transactions and check for conflicts between read/write operations and timestamps to ensure serial ordering. Thomas' write rule modifies checking for some write operations.Functional dependency



Functional dependencyTamajit Chakraborty
╠²
The document defines functional dependencies and describes how they constrain relationships between attributes in a database relation. A functional dependency X ŌåÆ Y means the Y attribute is functionally determined by the X attribute(s). The closure of a set of functional dependencies includes all dependencies that can be logically derived. Normalization aims to eliminate anomalies by decomposing relations based on their functional dependencies until a desired normal form is reached.13. Query Processing in DBMS



13. Query Processing in DBMSkoolkampus
╠²
The document discusses various steps and algorithms for processing database queries. It covers parsing and optimizing queries, estimating query costs, and algorithms for operations like selection, sorting, and joins. Selection algorithms include linear scans, binary searches, and using indexes. Sorting can use indexes or external merge sort. Join algorithms include nested loops, merge join, and hash join.Binary Search Tree



Binary Search Treesagar yadav
╠²
Binary search trees are binary trees where all left descendants of a node are less than the node's value and all right descendants are greater. This structure allows for efficient search, insertion, and deletion operations. The document provides definitions and examples of binary search tree properties and operations like creation, traversal, searching, insertion, deletion, and finding minimum and maximum values. Applications include dynamically maintaining a sorted dataset to enable efficient search, insertion, and deletion.Databases: Normalisation



Databases: NormalisationDamian T. Gordon
╠²
Normalisation is a process that structures data in a relational database to minimize duplication and redundancy while preserving information. It aims to ensure data is structured efficiently and consistently through multiple forms. The stages of normalization include first normal form (1NF), second normal form (2NF), third normal form (3NF), Boyce-Codd normal form (BCNF), fourth normal form (4NF) and fifth normal form (5NF). Higher normal forms eliminate more types of dependencies to optimize the database structure.Similar to Lock based protocols (20)
concurrency control



concurrency controlrajshreemuthiah
╠²
This document provides an overview of concurrency control and two-phase locking protocol. It discusses lock-based concurrency control, two-phase locking protocol, deadlocks, and strategies for handling deadlocks such as deadlock prevention, avoidance, and detection and recovery. The key aspects covered are the lock compatibility matrix, differences between shared and exclusive locks, requirements for serializability under two-phase locking, and the four conditions required for a deadlock.Cs501 concurrency



Cs501 concurrencyKamal Singh Lodhi
╠²
This document discusses concurrency control and recovery techniques for databases. It covers various notions of serializability and recoverability. It describes lock-based protocols like two-phase locking and graph-based protocols like tree protocols. It discusses issues like deadlocks, cascading rollbacks, and starvation. It also covers deadlock handling techniques like prevention, detection and recovery.Concurrency control!



Concurrency control!Ashish K
╠²
Concurrency control techniques ensure consistency and reliability of concurrent transactions in a database. They synchronize transaction operations to maintain consistency while allowing maximum concurrency. Three main techniques are locking-based protocols, timestamp ordering, and optimistic concurrency control. Locking-based protocols like two-phase locking use locks to control access to shared data and guarantee serializability. Timestamp ordering assigns timestamps to transactions and validates reads and writes based on timestamp order. Optimistic concurrency control allows transactions to read and write tentatively without locking, and validates at the end to commit only if no conflicts occurred.Dbms



Dbmskasthurimukila
╠²
Concurrency control protocols ensure transactions executed simultaneously in a database system uphold the ACID properties of atomicity, consistency, isolation, and durability. There are two main categories of concurrency control protocols: lock-based and timestamp-based. Lock-based protocols use shared and exclusive locks to control access to data, following a two-phase locking protocol where locks are acquired in a growing phase and released in a shrinking phase. Timestamp-based protocols order transactions based on assigned timestamps to determine a serializable execution schedule.Concurrency control PPT



Concurrency control PPTShushrutGupta
╠²
Powerpoint Presentaion on Concurrency Control Protocols,
is part of Btech 3rd year DBMS syllabus.
This slide is part of assignment provided during session 2018-2019Ch16



Ch16Welly Dian Astika
╠²
The document summarizes various concurrency control techniques used in database management systems to allow concurrent execution of transactions. It discusses lock-based protocols that use locking mechanisms and locking rules like two-phase locking to ensure serializability. It also covers timestamp-based protocols that order transactions based on timestamps to achieve serializability. Validation-based protocols allow optimistic execution of transactions by validating for serializability only at the end before committing. Graph-based protocols provide alternative locking approaches using data ordering graphs. The techniques aim to balance serializability with higher concurrency during parallel transaction execution.Concurrency Control Techniques



Concurrency Control TechniquesRaj vardhan
╠²
The document discusses various concurrency control techniques used in database management systems to ensure transaction isolation. It covers locking techniques like two-phase locking and timestamp ordering. Locking involves associating locks like read/write locks with data items. The two-phase locking protocol defines rules for acquiring and releasing locks in two distinct phases. Timestamp ordering assigns unique timestamps to transactions and ensures conflicting operations are executed based on timestamp order to guarantee serializability.Transaction management



Transaction managementjanani thirupathi
╠²
This document discusses transaction management and concurrency control. It summarizes two main categories of concurrency control protocols: lock-based protocols and timestamp-based protocols. For lock-based protocols, it describes four types: simplistic locking, pre-claiming, two-phase locking (2PL), and strict 2PL. For timestamp-based protocols, it explains how each transaction is assigned a timestamp and how read/write rules ensure serializability based on timestamp ordering.Concurrency Control database management system



Concurrency Control database management systemMahima788170
╠²
Study material for DBMS , concurrency controlConcurrency Control database management system



Concurrency Control database management systemMahima788170
╠²
Study material for DBMS , concurrency controlConcurrency Control.pptx



Concurrency Control.pptxVijaySourtha
╠²
This document discusses various concurrency control protocols used to manage concurrent access to databases. It describes lock-based protocols that use locking mechanisms to control access. It also covers timestamp-based protocols that order transactions based on timestamps to ensure serializability. Finally, it discusses validation-based or optimistic protocols that validate transactions have not violated consistency before committing writes.Concurrency Control in Databases.Database management systems



Concurrency Control in Databases.Database management systemsambikavenkatesh2
╠²
concurrency control pptDatabase management system chapter16



Database management system chapter16Md. Mahedi Mahfuj
╠²
The document discusses concurrency control techniques for databases, including lock-based protocols, timestamp-based protocols, and validation-based protocols. It focuses on lock-based protocols, describing how locks work, the two-phase locking protocol, deadlocks, and ways to handle them such as deadlock prevention and detection. It also discusses topics like multiple granularity locking, intention locks, and graph-based protocols.Chapter18



Chapter18gourab87
╠²
The document discusses various concurrency control techniques for databases including locking-based approaches like two-phase locking and multi-version concurrency control. It also covers non-locking approaches like timestamp ordering and validation (optimistic) concurrency control. Multiple granularity locking is described as a way to control concurrent access at different levels of data abstraction.deadlock and locking - dbms



deadlock and locking - dbmsSurya Swaroop
╠²
Concurrency Control
Lock-Based Protocols
Timestamp-Based Protocols
Validation-Based Protocols
Multiple Granularity
Multi-version Schemes
Insert and Delete Operations
Concurrency in Index Structures
database management system
------------------------------------------------------------------------------------Concurrency control



Concurrency controlvarsha singh
╠²
This document discusses various concurrency control techniques for database systems including lock-based protocols, timestamp-based protocols, validation-based protocols, and multiple granularity approaches. It focuses on lock-based protocols, describing how locks work in exclusive and shared modes. It also covers potential issues with lock-based protocols like deadlocks and starvation, and protocols to address these issues like two-phase locking.Vani dbms



Vani dbmsSangeethaSasi1
╠²
This document discusses concurrency control and its protocols. Concurrency control ensures correct results from concurrent operations while maximizing performance. It addresses issues that can arise from multiple transactions executing simultaneously on the same data. The ACID rules of atomicity, consistency, isolation, and durability are explained. Common concurrency control protocols include lock-based, two phase locking, and timestamp-based protocols. Lock-based protocols use shared and exclusive locks to control access to data. Two phase locking follows a growing and shrinking phase approach. Timestamp-based protocols serialize transactions based on timestamps.Concurrency note.pdf



Concurrency note.pdfBijayNag1
╠²
Concurrency control in database management systems allows multiple transactions to execute simultaneously without conflicts. It maintains consistency by coordinating access to shared data. Common techniques include locking, which reserves access to data for a transaction, and timestamp ordering, which sequences transactions based on their start time. Locking approaches include two-phase locking for serializable isolation and protocols that handle lock requests and conversions. Timestamp ordering rejects transactions that violate precedence relations between read and write timestamps of data items.Concurrency Control, Recovery, Case Studies



Concurrency Control, Recovery, Case StudiesPrabu U
╠²
This document provides an overview of concurrency control and recovery techniques in database management systems. It discusses lock-based protocols, timestamp-based protocols, validation-based protocols, deadlock handling, and recovery methods. The key points covered are locking mechanisms, two-phase locking protocol, timestamp ordering protocol, Thomas' write rule, validation-based protocols, deadlock detection using wait-for graphs, and recovery from failures. Case studies on IBM DB2 and MySQL databases are also mentioned.ch15.ppt



ch15.pptmukul narayana
╠²
This document discusses concurrency control techniques for database systems. It covers lock-based protocols using locking to control concurrent access. Key aspects covered include lock compatibility, two-phase locking protocol, deadlocks, and lock implementation. It also discusses timestamp-based protocols that use timestamps to determine serialization order and validation-based protocols. Multiple granularity locking and intention lock modes are explained.Recently uploaded (20)
Unit-03 Cams and Followers in Mechanisms of Machines.pptx



Unit-03 Cams and Followers in Mechanisms of Machines.pptxKirankumar Jagtap
╠²
Unit-03 Cams and Followers.pptxCecille Seminario Marra - Specializes In Medical Technology



Cecille Seminario Marra - Specializes In Medical TechnologyCecille Seminario Marra
╠²
Cecille Seminario Marra, a dedicated bioengineer, graduated from Florida Gulf Coast University with a BS in Bioengineering. She has two years of experience in bioengineering and biotechnology, focusing on medical technology advancements. Cecille excels in managing projects and analyzing data using MATLAB, Python, and R.Artificial intelligence and Machine learning in remote sensing and GIS



Artificial intelligence and Machine learning in remote sensing and GISamirthamm2083
╠²
Artificial intelligence and Machine learning in remote sensing and GIS Floating Offshore Wind in the Celtic Sea



Floating Offshore Wind in the Celtic Seapermagoveu
╠²
Floating offshore wind (FLOW) governance arrangements in the Celtic Sea case are changing and innovating in response to different drivers including domestic political priorities (e.g. net-zero, decarbonization, economic growth) and external shocks that emphasize the need for energy security (e.g. the war in Ukraine).
To date, the rules of the game that guide floating wind in the UK have evolved organically rather than being designed with intent, which has created policy incoherence and fragmented governance arrangements. Despite this fragmentation, the UK has a well-established offshore wind sector and is positioning itself to become a global leader in floating wind.
Marine governance arrangements are in a state of flux as new actors, resources, and rules of the game are being introduced to deliver on this aspiration. However, the absence of a clear roadmap to deliver on ambitious floating wind targets by 2030 creates uncertainty for investors, reduces the likelihood that a new floating wind sector will deliver economic and social value to the UK, and risks further misalignment between climate and nature goals.FIRST Tech Challenge/Robotics: Scouting out the competition



FIRST Tech Challenge/Robotics: Scouting out the competitionFTC Team 23014
╠²
Learn how to effectively scout teams in preparation for your next competitionAnalysis of Daylighting in Interior Spaces using the Daylight Factor - A Manu...



Analysis of Daylighting in Interior Spaces using the Daylight Factor - A Manu...Ignacio J. J. Palma Carazo
╠²
Daylighting manual method based on Daylight Factor for indoor spaces, previous to any computational simulation method.Telehealth technology ŌĆō A new horizon in health care



Telehealth technology ŌĆō A new horizon in health careDr INBAMALAR T M
╠²
Telehealth technology ŌĆō A new horizon in health care, Telemedicine, E-healthSoftware security: Security a Software Issue



Software security: Security a Software IssueDr Sarika Jadhav
╠²
Software is often designed with security as an afterthought, leading to vulnerabilities that can be exploited by attackers. This has become a critical issue as our reliance on software continues to grow.
Increasing number and sophistication of attacks (CERT vulnerability reports rising).
Software security is the practice of protecting applications from unauthorized access, modification, and destruction.
Secure software development practices.
Executives (E)
Project Managers (M)
Technical Leaders (L)
Chapter1-Introduction ╬Ģ╬╣Žā╬▒╬│Žē╬│╬╣╬║╬ŁŽé ╬Ł╬Į╬Į╬┐╬╣╬ĄŽé



Chapter1-Introduction ╬Ģ╬╣Žā╬▒╬│Žē╬│╬╣╬║╬ŁŽé ╬Ł╬Į╬Į╬┐╬╣╬ĄŽéssuserb91a20
╠²
╬Ģ╬╣Žā╬▒╬│Žē╬│╬╣╬║Žī ╬║╬ĄŽå╬¼╬╗╬▒╬╣╬┐Caddlance PortfolioMixed Projects 2024.pdf



Caddlance PortfolioMixed Projects 2024.pdfsonam254547
╠²
A glimpse into the world of Caddlance! Explore our portfolio featuring captivating 3D renderings, detailed BIM models, and inspiring architectural designs. Let's build the future, together. #Architecture #3D #BIM #CaddlanceUsing 3D CAD in FIRST Tech Challenge - Fusion 360



Using 3D CAD in FIRST Tech Challenge - Fusion 360FTC Team 23014
╠²
Choose a 3D CAD software and understand its usagesEnergy Transition Factbook Bloomberg.pdf



Energy Transition Factbook Bloomberg.pdfCarlosdelaFuenteMnde
╠²
This factbook, using research from BloombergNEF and other sources, provides public and private sector leaders the critical information they need to accelerate the
transition to clean energy, along with all the health and economic benefits it will bring.module-4.1-Class notes_R and DD_basket-IV -.pdf



module-4.1-Class notes_R and DD_basket-IV -.pdfritikkumarchaudhury7
╠²
About Quick, merge and Binary search.UHV UNIT-5 IMPLICATIONS OF THE ABOVE HOLISTIC UNDERSTANDING OF HARMONY ON ...



UHV UNIT-5 IMPLICATIONS OF THE ABOVE HOLISTIC UNDERSTANDING OF HARMONY ON ...ariomthermal2031
╠²
IMPLICATIONS OF THE ABOVE HOLISTIC UNDERSTANDING OF HARMONY ON PROFESSIONAL ETHICS NBA Criteria TIER I and TIER II Comparison



NBA Criteria TIER I and TIER II ComparisonDr INBAMALAR T M
╠²
Document Preparation for NBA
Self Assessment Report (SAR) Tier I Formats
Analysis of Daylighting in Interior Spaces using the Daylight Factor - A Manu...



Analysis of Daylighting in Interior Spaces using the Daylight Factor - A Manu...Ignacio J. J. Palma Carazo
╠²
Lock based protocols
- 2. LOCK BASED PROTOCOLS ’üĄ A lock is a mechanism to control concurrent access to a data item ’üĄ Data items can be locked in two modes : 1. exclusive (X) mode. Data item can be both read as well as written. X-lock is requested using lock-X instruction. 2. shared (S) mode. Data item can only be read. S-lock is requested using lock-S instruction. ’üĄ Lock requests are made to the concurrency-control manager by the programmer. Transaction can proceed only after request is granted.
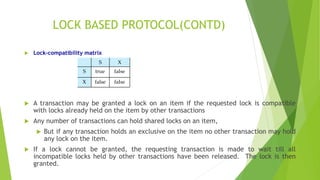
- 3. LOCK BASED PROTOCOL(CONTD) ’üĄ Lock-compatibility matrix ’üĄ A transaction may be granted a lock on an item if the requested lock is compatible with locks already held on the item by other transactions ’üĄ Any number of transactions can hold shared locks on an item, ’üĄ But if any transaction holds an exclusive on the item no other transaction may hold any lock on the item. ’üĄ If a lock cannot be granted, the requesting transaction is made to wait till all incompatible locks held by other transactions have been released. The lock is then granted.
- 4. LOCK BASED PROTOCOL(CONTD) ’üĄ Example of a transaction performing locking: T2: lock-S(A); read (A); unlock(A); lock-S(B); read (B); unlock(B); display(A+B) ’üĄ Locking as above is not sufficient to guarantee serializability ŌĆö if A and B get updated in- between the read of A and B, the displayed sum would be wrong. ’üĄ A locking protocol is a set of rules followed by all transactions while requesting and releasing locks. Locking protocols restrict the set of possible schedules.
- 5. TWO PHASE LOCKING PROTOCOL ’üĄ This protocol ensures conflict-serializable schedules. ’üĄ Phase 1: Growing Phase ’üĄ Transaction may obtain locks ’üĄ Transaction may not release locks ’üĄ Phase 2: Shrinking Phase ’üĄ Transaction may release locks ’üĄ Transaction may not obtain locks ’üĄ The protocol assures serializability. It can be proved that the transactions can be serialized in the order of their lock points (i.e., the point where a transaction acquired its final lock).
- 6. TWO PHASE LOCKING PROTOCOL(CONTD) ’üĄ There can be conflict serializable schedules that cannot be obtained if two- phase locking is used. ’üĄ However, in the absence of extra information (e.g., ordering of access to data), two-phase locking is needed for conflict serializability in the following sense: ’üĄ Given a transaction Ti that does not follow two-phase locking, we can find a transaction Tj that uses two-phase locking, and a schedule for Ti and Tj that is not conflict serializable.
- 7. THANK YOU




