Lva I Brochure
- 1. Precise information for better recruitment LVA-i HR integrity assessment systems
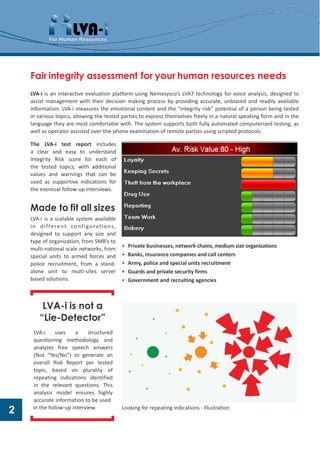
- 2. Fair integrity assessment for your human resources needs LVA-i is an interactive evaluation platform using Nemesyscoâs LVA7 technology for voice analysis, designed to assist management with their decision making process by providing accurate, unbiased and readily available information. LVA-i measures the emotional content and the âintegrity riskâ potential of a person being tested in various topics, allowing the tested parties to express themselves freely in a natural speaking form and in the language they are most comfortable with. The system supports both fully automated computerized testing, as well as operator assisted over-the-phone examination of remote parties using scripted protocols. The LVA-i test report includes a clear and easy to understand Integrity Risk score for each of the tested topics, with additional values and warnings that can be used as supportive indications for the eventual follow-up interviews. Made to fit all sizes LVA-i is a scalable system available in different conf igurations, designed to support any size and type of organization, from SMBâs to âĒ Private businesses, network chains, medium size organizations multi-national scale networks, from special units to armed forces and âĒ Banks, insurance companies and call centers police recruitment, from a stand- âĒ Army, police and special units recruitment alone unit to multi-sites server âĒ Guards and private security firms based solutions. âĒ Government and recruiting agencies LVA-i is not a âLie-Detectorâ LVA-i uses a structured questioning methodology and analyzes free speech answers (Not âYes/Noâ) to generate an overall Risk Report per tested topic, based on plurality of repeating indications identified in the relevant questions. This analysis model ensures highly accurate information to be used in the follow-up interview. Looking for repeating indications - Illustration 2
- 3. LVA-i tests modes & scripts LVA-i can perform a test in What is an Integrity two modes of operation: Test? âĒ In the Automated Test mode the candidate is seated in a quiet room Integrity tests attempt to measure in front of the LVA-i computer terminal. Using the screen and the LVA-i the potential and personal phone-like handset, the system will present the selected questionnaire, acceptance of undesired or automatically advancing to the next question once a proper voice unlawful behaviors. LVA-iâs Integrity response was recorded. Risk result reflects the probable âĒ In the Telephone Test mode an operator will assist the test procedure risk of the tested party acting in a manner that might expose your with a remote party, reading the scriptâs questions from his screen. organization to danger. Automated Test mode Telephone Test mode Use LVA-i for: âĒ Pre-employment screening âĒ Periodical veracity tests and âHonesty maintenanceâ âĒ Special event tests in the The LVA-i package contains several standard employment scripts for both organization (Theft, Confidential the phone and the automated modes. These scripts contain questions in information leakage, etcâĶ) the classical and most relevant topics (theft, drug abuse, etc.). Custom âĒ Security clearance made scripts can be created as needed. âĒ Employees satisfaction surveys The LVA-i test report is automatically generated using the analysis of the LVA-i integrates unique voice subjectâs responses to the scripted questions in the different topics. analysis technology with carefully designed sets of investigative LVA-i Automated Report Logic questions to identify repeating emotional indications surrounding Topic 1 relevant questions to produce Question 1 its assessment. The systemâs Question 2 standard questionnaires are Question 3 specifically designed to scan the candidatesâ personal history, test Topic 2 the consistency of their opinions at Question 1 present and determine the level of Question 2 their commitment to the future. Question 3 Topic 3 Question 1 Question 2 Question 3 3
- 4. The Automated Test Mode LVA-i automated questionnaires are based on Adobe FlashâĒ technology, Conducting an automated test - providing flexible, rich multi-media step by step presentation and advanced options Preparing the applicant for the test Before any test procedure, it is increationofuniquequestionnaires. Each questionnaire is divided into important the tested party receives full instructions about the test different topics, each containing procedures and objectives. Test candidates are provided with a âconsent a number of questions covering a formâ explaining the topics and nature of questions to be asked, and allow specific issue. The questions are the candidate to ask any clarification questions or even quit. presented to the candidates both textually and vocally one after the Step 1: The LVA-i operator ensures that the testing room is clean and other. quiet, and initiates the test from the management panel. The operator fills in the candidateâs details and selects the relevant test questionnaire. The standard tests contain the A click on the âStart Testâ button loads the testing interface and locks the following topics: management panel. âĒ Confidentiality and Secrecy âĒ Theft from Place of Employment âĒ Credibility and Criminal Tendencies âĒ Bribery and Kickbacks âĒ Fraud and Deceit âĒ Drug Usage âĒ Alcohol Usage âĒ Gambling Step 2: The candidate enters the examination room and sits in front of the LVA-i monitor. The operator explains the test procedure and leaves the room, allowing the candidate to complete the test in privacy. Step 3: The candidate selects the test language from the available set and confirm his personal details. As the test progresses, the candidate has to answer a series of questions, one after the other. Step 4: Once the test has been completed, the candidate leaves the room and the LVA-i returns to standby mode. At this time, the HR Manager can 4 log in and review the test report in preparation for a follow-up interview. No further operation or analysis is required from the manager.
- 5. LVA-i Phone Test mode Specially designed questionnaires for telephone interviews are also included with the LVA-i software. Unlike the automatic questionnaire, this questionnaire is designed in a form of conversation script where the operator reads through the pre-scripted questions one after the other, leading the candidate throughout the entire test procedure. Step 1: The operator ensures the candidate on the other end of the line is in a quiet location and understands the nature of the test. Step 2: The operator fills in the candidateâs details and selects the test to be performed. Step 3: LVA-i opens the âConversation Managementâ screen and loads the selected script. The operator reads through the script as it appears on his screen, one question after the other. The system monitors the conversation and analyzes the candidateâs answers. Step 4: Once the test has been completed, the LVA-i report is created and added to the database. No further 5 operation or analysis is required from the manager.
- 6. LVA-i Reports and Management System Selecting a case file from the different database views opens the relevant LVA-i report. The analyses records use a risk scoring and color codes for easy review of the results: Test results LVA-i report screen is made of several tabs, providing different levels of information. The General Info tab displays the candidatesâ details and a clear color coded reading of the topicsâ risk analysis results. In addition, the main tab displays the operatorâs assessment (if applicable) and a highlighted âWarnings Logâ. The risk analysis results are based on the specific script topics, summarizing the analysis indications from all the specific topicâs questions. The 5 risk level indications range from low (a single green block) to high risk (5 red blocks). The Details tab This screen provides the user with a deeper analysis of the test results, divided into the topics and questions. Use this screen to further examine âHigh Riskâ answers, and cross references in topics that may reveal additional information. Final reports tab Following review, managers can add their comments and observations to be included in the test file and printed reports. Playback (optional) Where applicable by law, LVA-i allows you to record the whole test. When selecting a specific answer or segment the player will play the relevant section, and will show the selected portion location on the bar below the slider. Who can operate LVA-i? The LVA-i analysis process is fully automated. It was designed to operate with minimal training and requires no specific technical or theoretical 6 expertise for standard operation.
- 7. Periodical clearance and Automated posts pre-employment screening for security organizations LVA-i tests offer a very flexible, highly accurate and cost-effective solution for veracity and psychological evaluation of operational forces and sensitive positionsâ recruitment. Used for threat estimation in selected topics of interest with current employees and employment candidates, LVA-i is an essential recruiting tool for any security organizations/agencies and for in-house security departments conducting periodical clearances. Phone posts âĒ Highly cost-effective solution for integrity assessment âĒ Completely automated assessment process âĒ Customized questionnaires designed for various specific needs âĒ Can detect unsuitable emotional profiles for sensitive tasks and positions (when using specially designed questionnaires) âĒ Intuitive and easy to understand reports âĒ Enhance security and safety of the employees and the organizationâs Manager seat environment âĒ Promote fair hiring practices by providing unbiased assessments âĒ Language-independent: analyzes responses in any language âĒ Easily operated by everyone - Full training of the LVA-i platform operation takes less than a single day! Professional seats WEB Suitable for all sizes of organizations From a single post service provider to multi-sites international installations Remote centers Legal note Risk detection using LVA technology has been found to be effective in reducing organizationâs exposure to unlawful acts and deter fraudsters; however, this kind of testing should only be performed in accordance with the pertinent local laws and regulations. Please consult with your legal advisor for the applicable regulations in your region. 7
- 8. About Nemesysco Nemesysco Ltd. is the leading provider of voice analysis and emotion detection technologies, for defense and civilian markets. Nemesyscoâs LVA (Layered Voice Analysis) technology detects the emotional content of a conversation, in real-time or from recorded materials, enabling analysis of different types of stress, cognitive processes and various emotional reactions. Nemesyscoâs products are implemented in a wide variety of applications for law enforcement, homeland security, insurance and banks fraud prevention, employee screening, call center quality monitoring, healthcare and entertainment. Nemesysco is a privately held company, founded in 2000 and is headquartered in Netanya, Israel. Nemesysco Service Centre Africa (Pty) Ltd. ïĻ: +27 21 851 5859 | ïĐ: +27 82 698 1369 |ïŊ: jkvd@nemesysco.co.za PO Box 3932 Somerset West 7129, South Africa ÂĐ Copyright 2011 Nemesysco Ltd. All rights reserved.