[Main Session] ??? ??? ?????? ?? ?? ? ??? ?? ?? ??
- 1. ?? ?????? ?? ?? ? ??? ?? ?? ??????? (? ??HP) ??? ???? CISA/CISSP/AWS SA, SysOps Admin/OCP/OCJP sanghyoun.kim@microfocus.com 2018/04/21 (?), ??180
- 2. Table of Contents 1. ?????? ?? ?? 2. ????? ?? ??? ?? - ??? ?? ? ?? ?? ??? ? ??? ?? ??, Mindset Deep Dive ? ?? ?? ?? ?? ?? ? ?? ??? ? ?? ?? ??? ?? ?? 3. ??? ?????? ?? ? ??? ?? ? ???? ???? ¨C RASP 4. ??? 2/120
- 3. ?????? ?? ??
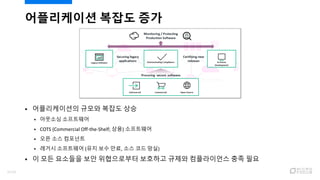
- 4. ? ??? ?? ??? 84%? ? ?????? ???? ?? ¨C ???, 2014 ? ?????? ?? (AppSec) ??? ?? ??? 23?? 1 ?????? ?? ?? 4/120
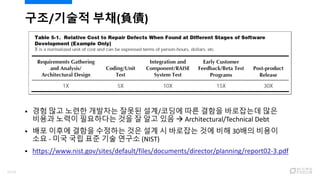
- 5. ?????? ??? ?? ? ??????? ??? ??? ?? ? ???? ????? ? COTS (Commercial Off-the-Shelf; ??) ????? ? ?? ?? ???? ? ??? ????? (?? ?? ??, ?? ?? ??) ? ? ?? ???? ?? ?????? ???? ??? ?????? ?? ?? 5/120
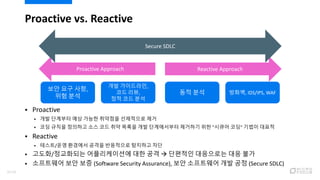
- 6. Proactive vs. Reactive ? Proactive ? ?? ???? ?? ??? ???? ????? ?? ? ?? ??? ???? ?? ?? ?? ??? ?? ?????? ???? ?? "??? ??" ??? ??? ? Reactive ? ???/?? ???? ??? ????? ???? ?? ? ???/????? ??????? ?? ?? ? ???? ????? ?? ?? ? ????? ?? ?? (Software Security Assurance), ?? ????? ?? ?? (Secure SDLC) Proactive Approach Reactive Approach Secure SDLC ?? ?? ??, ?? ?? ?? ?????, ?? ??, ?? ?? ?? ?? ?? ???, IDS/IPS, WAF 6/120
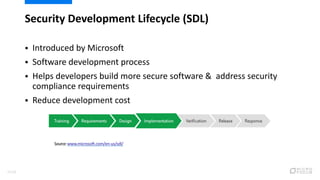
- 7. ? Introduced by Microsoft ? Software development process ? Helps developers build more secure software & address security compliance requirements ? Reduce development cost Source:www.microsoft.com/en-us/sdl/ Security Development Lifecycle (SDL) 7/120
- 8. ?????? ?? ??? ?? ¨C ??? ??
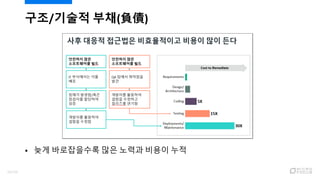
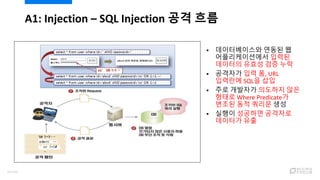
- 9. ??/??? ??(Ř“‚ů) ? ?? ?? ??? ???? ??? ??/??? ?? ??? ????? ?? ??? ??? ????? ?? ? ?? ?? ? Architectural/Technical Debt ? ?? ??? ??? ???? ?? ?? ? ???? ?? ?? 30?? ??? ?? - ?? ?? ?? ?? ??? (NIST) ? https://www.nist.gov/sites/default/files/documents/director/planning/report02-3.pdf 9/120
- 10. ? ?? ?????? ?? ??? ??? ?? ??/??? ??(Ř“‚ů) 10/120
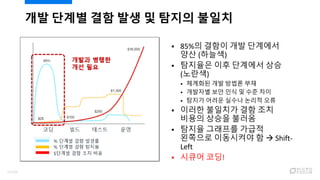
- 11. ? 85%? ??? ?? ???? ?? (???) ? ???? ?? ???? ?? (???) ? ???? ?? ??? ?? ? ???? ?? ?? ? ?? ?? ? ??? ??? ??? ??? ?? ? ??? ???? ?? ?? ??? ??? ??? ? ??? ???? ??? ???? ????? ? ? Shift- Left ? ??? ??! ?? ??? ?? ?? ? ??? ??? 11/120
- 12. ??? ?? ??? ? ??? ??? ?? ??? ?? ? ??? ??? ?? ?? SDL? ??? ? ????? ?? ?? ?? (SDL; Software Development Lifecycle)? ??? Metric ? ????? ??(Software Assurance) ?? (Metric) ? ???? ? ?? 12/120
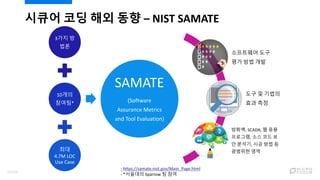
- 13. ????? ?? ?? ?? ?? ?? ? ??? ?? ?? ???, SCADA, ? ?? ????, ?? ?? ? ? ???, ?? ?? ? ???? ?? ??? ?? ?? ?? ¨C NIST SAMATE 3?? ? ?? 10?? ???* ?? 4.7M LOC Use Case SAMATE (Software Assurance Metrics and Tool Evaluation) - https://samate.nist.gov/Main_Page.html - *???? Sparrow ? ?? 13/120
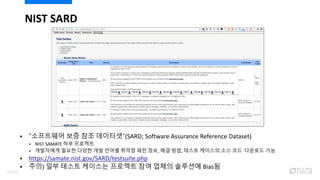
- 14. ? ˇ°????? ?? ?? ????ˇ±(SARD; Software Assurance Reference Dataset) ? NIST SAMATE ?? ???? ? ????? ??? ??? ?? ??? ??? ?? ??, ?? ??, ??? ???? ?? ?? ???? ?? ? https://samate.nist.gov/SARD/testsuite.php ? ??) ?? ??? ???? ???? ?? ??? ???? Bias? NIST SARD 14/120
- 15. ??? ?? ?? ?? ¨C ˇ°SW ????ˇ± ?? 2012.12 ?????? ˇ°SW ????" ??? ?? ??? ?? 40?? ?? 2014.01 ??? ?? 20?? ???? ?? 2015.01 ??? ?? ?? 2016.12 ?ˇ¸???? ? ???? ????? ????? ??ˇą(2016.12.26) ?? ?ˇ°SW ????ˇ± ????? ?????? ?? 2017.01 ?ˇ°????? ?? ?? ???ˇ± ?? 15/120
- 16. ? ????????(KISA) ? ?? ?? ?? ? ?? ? ?? ? ?? ??? ??? ?? ? ???? ?? ? http://www.kisa.or.kr/public/laws /laws3.jsp ? ?? ???? ?? ?? ?? ?? ??? ?? ??? ?? ?? ?? ¨C KISA 16/120
- 17. ? ??? ??? ?? ???? ??? ??? ? ?? ??? ?? ???? ?? ?? ???? ??? ?? ????? ???! ??? ?? ?? ? ??? ???? ?? 17/120
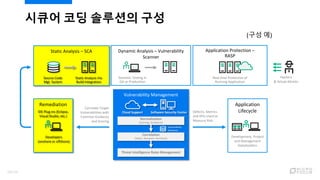
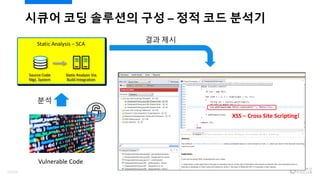
- 18. ??? ?? ???? ?? Static Analysis ¨C SCA Source Code Mgt. System Static Analysis Via Build Integration Dynamic Analysis ¨C Vulnerability Scanner Dynamic Testing in QA or Production Application Protection ¨C RASP Real-time Protection of Running Application Vulnerability Management Normalization (Scoring, Guidance) Vulnerability Database Remediation IDE Plug-ins (Eclipse, Visual Studio, etc.) Developers (onshore or offshore) Correlate Target Vulnerabilities with Common Guidance and Scoring Defects, Metrics and KPIs Used to Measure Risk Application Lifecycle Development, Project and Management Stakeholders Software Security CenterCloud Support Hackers & Actual Attacks Correlation (Static, Dynamic, Runtime) Threat Intelligence Rules Management (?? ?) 18/120
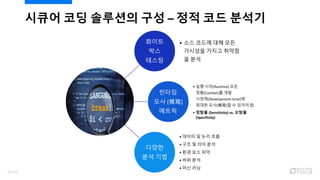
- 19. ??? ?? ???? ?? ¨C ?? ?? ??? Vulnerable Code ?? ?? ?? XSS ¨C Cross Site Scripting! 19/120
- 20. ??? ?? ???? ?? ¨C ?? ?? ??? ??? ?? ??? ? ?? ??? ?? ?? ???? ??? ??? ? ?? ??? ?? (ÄŁŚ‘) ??? ? ?? ??(Runtime) ?? ??(Context)? ?? ???(Development-time)? ??? ??(ÄŁŚ‘)? ? ??? ? ? ??? (Sensitivity) vs. ??? (Specificity) ??? ?? ?? ? ??? ? ?? ?? ? ?? ? ?? ?? ? ?? ?? ?? ? ?? ?? ? ?? ?? 20/120
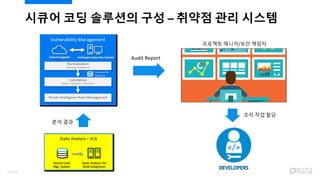
- 21. ??? ?? ???? ?? ¨C ??? ?? ??? ?? ?? Audit Report ???? ???/?? ??? ?? ?? ?? 21/120
- 22. ??? ?? ???? ?? ¨C ??? ?? ??? ?? ??? ? ?? ??????? ??? ?? ??? ????? ?? ?? ?? ? ???? ?? ??? ?? ?? ?? ? ???? ?? ?? ? ??? - ??? ?? ? ??PM - ??? ?? ? ?? ??? ?? ? CISO/CIO - ??? ??? ?? ? ?????? ?? ?? ?? DevOps/DevSecOps ?? ? CI/CD ?(Jenkins), ??? ?? ???(JIRA, BugZilla ?) ?? ?? ?? ? ??? ??? DevOps ??(DevSecOps)? ?????? ?? 22/120
- 23. ??? ?? ???? ?? ¨C ??? ?? ??? ?? ?? ???? ?? ??? ?? 23/120
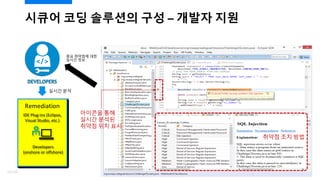
- 24. ??? ?? ???? ?? ¨C ??? ?? Security Automation ???? ?? ??? ?? ???? ??? ??? ?? ???? ?? ??? ? ??? ?? Eclipse, IntelliJ, Microsoft Visual Studio ? ??? ?? ?? ???? ?? ?? ??? ??? ? ??? ???? ????? Ant, Maven ?? ?? ???? ??? ? ?? ?? Tool Fatigue, Process Friction ??? 24/120
- 25. ?? ?? ???
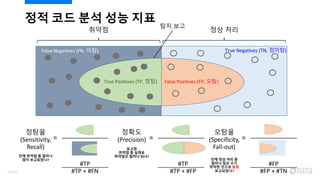
- 26. ?? ?? ?? ?? ?? ??? (Sensitivity, Recall) ?? ??? ? ??? ?? ?????? = ??? (Specificity, Fall-out) ?? ?? ?? ? ??? ?? ?? ??? ??? ?? ?????? = ??? (Precision) ??? ??? ? ??? ???? ??? ??? = #TP #TP + #FN #TP #TP + #FP #FP #FP + #TN ??? ?? ?? True Positives (TP, ??) False Positives (FP, ??) ?? ?? False Negatives (FN, ??) True Negatives (TN, ???) 27/120
- 27. ?? ?? ?? ?? ?? ? ??? (Precision) = #TP / (#TP + #FP) ? ??? ?? ??? ? ?? ??? ??, ?? ?? ?? ? Sensitivity (Recall?) = #TP / (#TP + #FN) ? ?? ?? ??? ? ??? ??? ??, ?? ?? ?? ? Specificity (Fall-out) = #FP / (#FP + #TN) ? ?? ?? ? ??? (?? ??) ? ???? ?? ??? ??, ?? ?? ?? ? ???? ?? ????? 80% ?? ?? ? Recall?? ???? ?? ?? ?? 50%? ??? ?? ? ???: 1? ??, ?? ??, ?????? ? ? ???: 2? ??, ?? ??, ?????? ?? ?? (Reported) ??? (Non-Reported) ?? ??? ??? (True Positive; TP) ??? (False Negative; FN) ??? ?? ??? (False Positive; FP) ??? (True Negative; TN) 28/120
- 28. ?? ?? ??? ??? ??? ?? ?? ??? 29/120
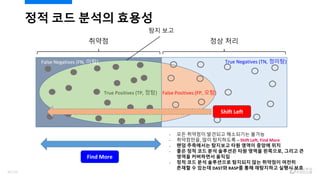
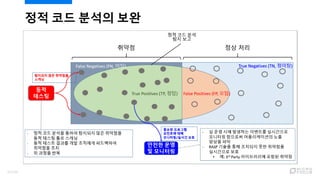
- 29. ?? ?? ??? ??? ??? ?? ?? True Positives (TP, ??) False Positives (FP, ??) ?? ?? False Negatives (FN, ??) True Negatives (TN, ???) Shift Left Find More - ?? ???? ???? ????? ??? - ?????, ?? ????? ¨C Shift Left, Find More - ?? ????? ???? ?? ??? ??? ?? - ?? ?? ?? ?? ???? ?? ??? ????, ??? ? ??? ????? ??? - ?? ?? ?? ????? ???? ?? ???? ??? ??? ? ??? DAST? RASP? ?? ????? ??? ?? 30/120
- 30. ?? ?? ??? ?? 31/120
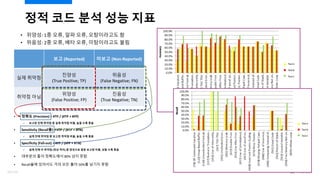
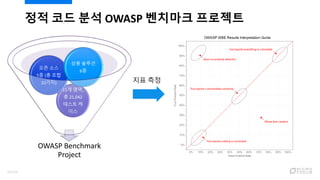
- 31. ?? ?? ?? OWASP ???? ???? OWASP Benchmark Project 11? ??, ? 21,042 ??? ? ?? ?? ?? 5? (? ?? 10??) ?? ??? 6? ?? ?? 32/120
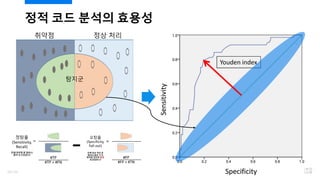
- 32. ?? ?? ?? OWASP ???? ???? ?? ? Youden Index (??? (TPR) - ??? (FPR))? ???(Score)? ?? ? ?? ???? ?? ?? ???? ?? ???? ??? ??? ?? (26% vs. 22%) ? ?? ???? ??? ??? ???? ?? ?? ???? ?? 8? ?? (21041 vs. 2704) ? ?? ?? ??? ?? ???? ?? ??? ??? ? (????: ???? 0.1418 vs. ?? 0.0650) ? ?? ?? ???? ?? ?? ?? ??? ?? ¨C ?? ??? ??? 33/120
- 33. ?? ?? ?? OWASP ???? ???? ?? (ContˇŻd) ? ?? ????? ???? ????? ???? ?? ???? ?? ? ?? ?? ??? ? ?? ?? ??? ?? FBwFindSecBugs v1.4.6 ? ?? ???? ?? ?? ??? ??? (57.74%) ? ??? ???? ??? ??? ?????? ???? ?? ???? ?? ??? ????, ???? ???? ???? ? ?? 34/120
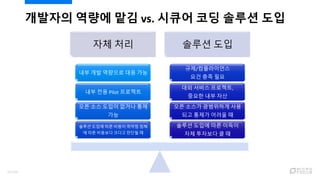
- 34. ???? ??? ?? vs. ??? ?? ??? ?? ?? ?? ??? ?? ??? ??? ?? ??? ?? ???? ? ? ?? ??? ????? ?? ?? ??? ??? ? ?? ??? ????, ??? ?? ?? ??/?????? ?? ?? ?? ??? ??? ?? ??? ??? ?? ? ?? ???? ??? ??? ? ?? ?? ??? ??? ?? ?? ?? ?? Pilot ???? ?? ?? ???? ?? ?? 35/120
- 35. ??? ?? ?? ??
- 36. ??? ?? ? ? ??? ???? ????? ??! 38/120
- 38. ? ?????? ?? ?? ?? ? http://riches2.mydemo.co.kr:580 82/riches/ ? ??) ??? ??? URL( ??)? ??? ?? ?? ? ????, ?? ??? ? ??? ???? ? ? ??? A1: Injection ¨C SQL Injection 40/120
- 39. ? Username: ˇ±eddieˇ±, Password: ˇ°eddieˇ± ???? ??? ? ???? ?? ˇ°Account Summaryˇ± ???? ?? A1: Injection ¨C SQL Injection (??) 41/120
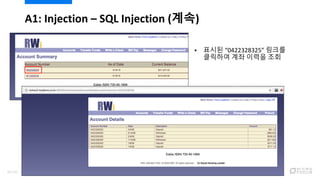
- 40. ? ??? ˇ°0422328325ˇ± ??? ???? ?? ??? ?? A1: Injection ¨C SQL Injection (??) 42/120
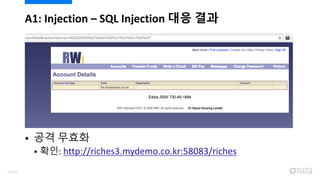
- 41. A1: Injection ¨C SQL Injection (??) ? ????? ???? [' or '1' = '1]? ???? ?? ? ˇ°???? ???? ???ˇ± ?? ??? ??? ??? 43/120
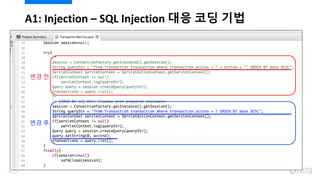
- 42. ? ??????? ??? ? ???????? ??? ???? ??? ?? ?? ? ???? ?? ?, URL ???? SQL? ?? ? ?? ???? ???? ?? ??? Where Predicate? ??? ?? ??? ?? ? ??? ???? ???? ???? ?? A1: Injection ¨C SQL Injection ?? ?? 44/120
- 43. ? PreparedStatement ???? ???? ???? ????? ??? ?? ???? executeQuery(), execute(), executeUpdate() ??? ?? ? PreparedStatement ???? ???? ???? ???? ?? Validation? ??? ? ?? ? Validation? SQL ?? ??, ?? ?? ??, ?? ?? ?? ????? ?? A1: Injection ¨C SQL Injection ?? ?? ?? 45/120
- 44. A1: Injection ¨C SQL Injection ?? ?? ?? ?? ? ?? ? 46/120
- 45. A1: Injection ¨C SQL Injection ?? ?? ? ?? ??? ? ??: http://riches3.mydemo.co.kr:58083/riches 47/120
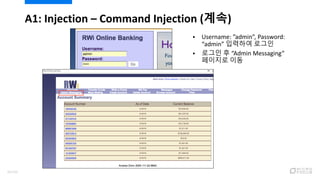
- 46. ? ?????? ?? ?? ?? ? http://riches2.mydemo.co.kr:580 82/riches/ A1: Injection ¨C Command Injection 48/120
- 47. A1: Injection ¨C Command Injection (??) ? Username: ˇ±adminˇ±, Password: ˇ°adminˇ± ???? ??? ? ??? ? ˇ°Admin Messagingˇ± ???? ?? 49/120
- 48. A1: Injection ¨C Command Injection (??) ? ??? ??? ["; cat /etc/passwd"] ?? ? ˇ°Send ?? ??ˇ± ? ???? ??? ??? ???? ?? 50/120
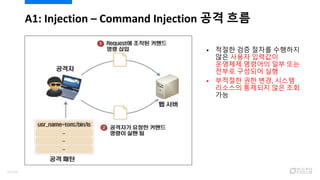
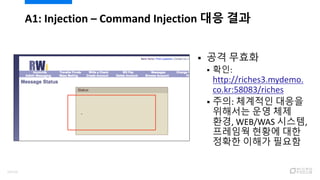
- 49. ? ??? ?? ??? ???? ?? ??? ???? ???? ???? ?? ?? ??? ???? ?? ? ???? ?? ??, ??? ???? ???? ?? ?? ?? A1: Injection ¨C Command Injection ?? ?? 51/120
- 50. ? ?????? ?? ???? ????? ??? ??? ???? ???? ??? ? ?? ??? ?? ??? ??? ??? ???? ????, ??? ??? ?? ??? ??? ??? ?? ?? ??? ?? ????? ?? A1: Injection ¨C Command Injection ?? ?? ?? 52/120
- 51. A1: Injection ¨C Command Injection ?? ?? ?? Validation ?? 53/120
- 52. A1: Injection ¨C Command Injection ?? ?? ? ?? ??? ? ??: http://riches3.mydemo. co.kr:58083/riches ? ??: ???? ??? ???? ?? ?? ??, WEB/WAS ???, ???? ??? ?? ??? ??? ??? 54/120
- 53. A7: Cross Site Scripting (XSS) ? ???? ?? ???? ?? ??? ????? ??? ??? ???? ?????? ??? ? ???, ?? ?? ??, ?? ?? ?? ????? ????? ?? ?? HTML? ??? ??? ???? ?? ??? ¨C ??? ??? ???? ??? ??? ?? ?? 55/120
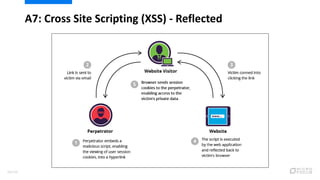
- 54. A7: Cross Site Scripting (XSS) - Reflected 56/120
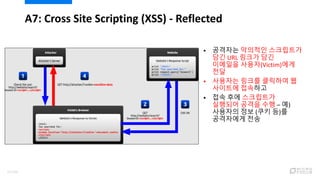
- 55. A7: Cross Site Scripting (XSS) - Reflected ? ???? ???? ????? ?? URL ??? ?? ???? ???(Victim)?? ?? ? ???? ??? ???? ? ???? ???? ? ?? ?? ????? ???? ??? ?? ¨C ?) ???? ?? (?? ?)? ????? ?? 57/120
- 56. ? ?????? ?? ?? ?? ? http://riches2.mydemo.co.kr:580 82/riches/ ? ??) ?? ????(?: ??, ???)??? XSS ???? ??? ?? ??? ???? ?? ???? ?? (??? ?????, ?????) A7: Cross Site Scripting (XSS) - Reflected 58/120
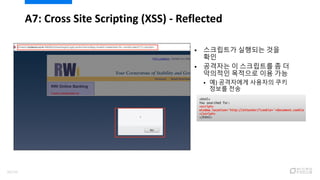
- 57. ? ???? Username? [<script>alert('1');</script>]? ???? ˇ°Goˇ± ?? ?? A7: Cross Site Scripting (XSS) - Reflected 59/120
- 58. ? ????? ???? ?? ?? ? ???? ? ????? ? ? ???? ???? ?? ?? ? ?) ????? ???? ?? ??? ?? A7: Cross Site Scripting (XSS) - Reflected 60/120
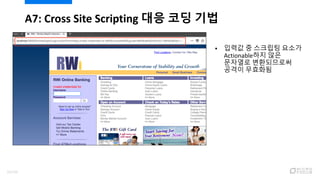
- 59. ? ? ??? ???? ?? ???? ?? Validation ? ??? ?? API? ?? ? OWASP ?? API ?ESAPI.encoder().encodeForHTMLAttrib ute(input); ? XSS Filter ?com.jesephoconnel.html.HTMLInputFilt er.filter(input); A7: Cross Site Scripting ?? ?? ?? From To < < > > ( ( ) ) # # & & 61/120
- 60. A7: Cross Site Scripting ?? ?? ?? 62/120
- 61. ? ??? ? ???? ??? Actionable?? ?? ???? ?????? ??? ???? A7: Cross Site Scripting ?? ?? ?? 63/120
- 62. ? ? ??? Cross Site Scripting ?? ?? 2?? ? ??? Reflected ??? ???????. ? ??? ?? ??? ?????? ??? ˇ°Pˇ±? ???? ????? ???? ?? ???. Quiz ¨C ?? ??? ??? ??? ???! 64/120
- 63. KISA ??? ?? ??? ? http://www.kisa.or.kr/public/ laws/laws3_View.jsp?cPage= 6&mode=view&p_No=259&b _No=259&d_No=55&ST=T&S V= 65/120
- 64. ??? ?? Mindset Deep Dive
- 65. ? ??? ? ?? ??? ????? ??????? ??? ???? ???? ???? ??? (?? ??) ? Injection ?? ? ???? ?? (Taint)? ???? ?? (Propagation) ??? ???? ??? ? ?? ???? ??? ?? ? Source ? ???? ?? (?, ???? ????) ?? ? Sink ? ????? ??? ?? ???? ?? Data Flow Analyzer 67/120
- 66. Understanding Data Flow 1 import java.sql.*; 2 3 public class SQLInjection { 4 public static void main (String args[]) { 5 Connection conn = null; 6 try { 7 String userName = args [0]; 8 String passwd = args [1]; 9 String query = "select uname, passwd from users where uname like "+userName+"%"; 10 conn = DriverManager.getConnection ("jdbc:odbc:logistics", "admin", "letmein"); 11 Statement stmnt = conn.createStatement (); 12 ResultSet rs = stmnt.executeQuery (query); 13 while ( rs.next() ) { 14 ... 15 } 16 rs.close (); 17 stmnt.close (); 18 conn.close (); 19 } 20 catch (SQLException err) { 21 err.printStackTrace (); 22 } 23 } 24 } 68/120
- 67. Understanding Data Flow import java.sql.*; public class SQLInjection { public static void main (String args[]) { Connection conn = null; try { String userName = args [0]; String passwd = args [1]; String query = "select uname, passwd from users where uname like "+userName+"%"; conn = DriverManager.getConnection ("jdbc:odbc:logistics", "admin", "letmein"); Statement stmnt = conn.createStatement (); ResultSet rs = stmnt.executeQuery (query); while ( rs.next() ) { ... } rs.close (); stmnt.close (); conn.close (); } catch (SQLException err) { err.printStackTrace (); } } } Source 69/120
- 68. Understanding Data Flow import java.sql.*; public class SQLInjection { public static void main (String args[]) { Connection conn = null; try { String userName = args [0]; String passwd = args [1]; String query = "select uname, passwd from users where uname like "+userName+"%"; conn = DriverManager.getConnection ("jdbc:odbc:logistics", "admin", "letmein"); Statement stmnt = conn.createStatement (); ResultSet rs = stmnt.executeQuery (query); while ( rs.next() ) { ... } rs.close (); stmnt.close (); conn.close (); } catch (SQLException err) { err.printStackTrace (); } } } args[] is tainted Source 70/120
- 69. Understanding Data Flow import java.sql.*; public class SQLInjection { public static void main (String args[]) { Connection conn = null; try { String userName = args [0]; String passwd = args [1]; String query = "select uname, passwd from users where uname like "+userName+"%"; conn = DriverManager.getConnection ("jdbc:odbc:logistics", "admin", "letmein"); Statement stmnt = conn.createStatement (); ResultSet rs = stmnt.executeQuery (query); while ( rs.next() ) { ... } rs.close (); stmnt.close (); conn.close (); } catch (SQLException err) { err.printStackTrace (); } } } Taint propagated to userName args[] is tainted Source 71/120
- 70. Understanding Data Flow import java.sql.*; public class SQLInjection { public static void main (String args[]) { Connection conn = null; try { String userName = args [0]; String passwd = args [1]; String query = "select uname, passwd from users where uname like "+userName+"%"; conn = DriverManager.getConnection ("jdbc:odbc:logistics", "admin", "letmein"); Statement stmnt = conn.createStatement (); ResultSet rs = stmnt.executeQuery (query); while ( rs.next() ) { ... } rs.close (); stmnt.close (); conn.close (); } catch (SQLException err) { err.printStackTrace (); } } } Tainted input userName used in assignment Taint propagated to userName args[] is tainted Source 72/120
- 71. Understanding Data Flow import java.sql.*; public class SQLInjection { public static void main (String args[]) { Connection conn = null; try { String userName = args [0]; String passwd = args [1]; String query = "select uname, passwd from users where uname like "+userName+"%"; conn = DriverManager.getConnection ("jdbc:odbc:logistics", "admin", "letmein"); Statement stmnt = conn.createStatement (); ResultSet rs = stmnt.executeQuery (query); while ( rs.next() ) { ... } rs.close (); stmnt.close (); conn.close (); } catch (SQLException err) { err.printStackTrace (); } } } Sink Tainted input userName used in assignment Taint propagated to userName args[] is tainted Source 73/120
- 72. Understanding Data Flow import java.sql.*; public class SQLInjection { public static void main (String args[]) { Connection conn = null; try { String userName = args [0]; String passwd = args [1]; String query = "select uname, passwd from users where uname like "+userName+"%"; conn = DriverManager.getConnection ("jdbc:odbc:logistics", "admin", "letmein"); Statement stmnt = conn.createStatement (); ResultSet rs = stmnt.executeQuery (query); while ( rs.next() ) { ... } rs.close (); stmnt.close (); conn.close (); } catch (SQLException err) { err.printStackTrace (); } } } Vulnerability Reported Sink Tainted input userName used in assignment Taint propagated to userName args[] is tainted Source 74/120
- 73. ? ??? ? ?? ??? ???? ?? ??? ?? ? ?? ??(State Machine) ??? ???? ??? ?? ??? ?? ? ? ?? ??? ???? ??? ? ?? ˇ°?? ??ˇ±? ?? ? ?? ? ???? ??? ?? ??? ??? ? ?? ???? ?? ??? ??? ? Control Flow Analyzer 75/120
- 74. Understanding Control Flow 1 private void cmdLogin_Click(object sender, System.EventArgs e){ 2 Label lblMsg = null; 3 try { 4 string txtUser = Request.Form["txtUsername"]; 5 string txtPassword = Request.Form["txtPassword"]; 6 string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;"; 7 SqlConnection cnx = new SqlConnection(strCnx); 8 cnx.Open(); 9 10 string strQry = "SELECT Count(*) FROM Users WHERE UserName='" + 11 txtUser + "' AND Password='" + txtPassword + "'"; 12 int intRecs; 13 14 SqlCommand cmd = new SqlCommand(strQry, cnx); 15 intRecs = (int)cmd.ExecuteScalar(); 16 17 if (intRecs > 0){ 18 FormsAuthentication.RedirectFromLoginPage(txtUser, false); 19 cnx.Close(); 20 } 21 else{ 22 lblMsg.Text = "Login attempt failed."; 23 } 24 } 25 catch (Exception err){ 26 Response.Write(err.StackTrace.ToString()); 27 } 28 } 76/120
- 75. private void cmdLogin_Click(object sender, System.EventArgs e){ Label lblMsg = null; try { string txtUser = Request.Form["txtUsername"]; string txtPassword = Request.Form["txtPassword"]; string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;"; SqlConnection cnx = new SqlConnection(strCnx); cnx.Open(); string strQry = "SELECT Count(*) FROM Users WHERE UserName='" + txtUser + "' AND Password='" + txtPassword + "'"; int intRecs; SqlCommand cmd = new SqlCommand(strQry, cnx); intRecs = (int)cmd.ExecuteScalar(); if (intRecs > 0){ FormsAuthentication.RedirectFromLoginPage(txtUser, false); cnx.Close(); } else{ lblMsg.Text = "Login attempt failed."; } } catch (Exception err){ Response.Write(err.StackTrace.ToString()); } } Understanding Control Flow Variable initialized & assigned 77/120
- 76. private void cmdLogin_Click(object sender, System.EventArgs e){ Label lblMsg = null; try { string txtUser = Request.Form["txtUsername"]; string txtPassword = Request.Form["txtPassword"]; string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;"; SqlConnection cnx = new SqlConnection(strCnx); cnx.Open(); string strQry = "SELECT Count(*) FROM Users WHERE UserName='" + txtUser + "' AND Password='" + txtPassword + "'"; int intRecs; SqlCommand cmd = new SqlCommand(strQry, cnx); intRecs = (int)cmd.ExecuteScalar(); if (intRecs > 0){ FormsAuthentication.RedirectFromLoginPage(txtUser, false); cnx.Close(); } else{ lblMsg.Text = "Login attempt failed."; } } catch (Exception err){ Response.Write(err.StackTrace.ToString()); } } Understanding Control Flow Connection closed Variable initialized & assigned 78/120
- 77. private void cmdLogin_Click(object sender, System.EventArgs e){ Label lblMsg = null; try { string txtUser = Request.Form["txtUsername"]; string txtPassword = Request.Form["txtPassword"]; string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;"; SqlConnection cnx = new SqlConnection(strCnx); cnx.Open(); string strQry = "SELECT Count(*) FROM Users WHERE UserName='" + txtUser + "' AND Password='" + txtPassword + "'"; int intRecs; SqlCommand cmd = new SqlCommand(strQry, cnx); intRecs = (int)cmd.ExecuteScalar(); if (intRecs > 0){ FormsAuthentication.RedirectFromLoginPage(txtUser, false); cnx.Close(); } else{ lblMsg.Text = "Login attempt failed."; } } catch (Exception err){ Response.Write(err.StackTrace.ToString()); } } Understanding Control Flow Safe Sequence Connection closed Variable initialized & assigned 79/120
- 78. private void cmdLogin_Click(object sender, System.EventArgs e){ Label lblMsg = null; try { string txtUser = Request.Form["txtUsername"]; string txtPassword = Request.Form["txtPassword"]; string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;"; SqlConnection cnx = new SqlConnection(strCnx); cnx.Open(); string strQry = "SELECT Count(*) FROM Users WHERE UserName='" + txtUser + "' AND Password='" + txtPassword + "'"; int intRecs; SqlCommand cmd = new SqlCommand(strQry, cnx); intRecs = (int)cmd.ExecuteScalar(); if (intRecs > 0){ FormsAuthentication.RedirectFromLoginPage(txtUser, false); cnx.Close(); } else{ lblMsg.Text = "Login attempt failed."; } } catch (Exception err){ Response.Write(err.StackTrace.ToString()); } } Understanding Control Flow Variable initialized & assigned 80/120
- 79. private void cmdLogin_Click(object sender, System.EventArgs e){ Label lblMsg = null; try { string txtUser = Request.Form["txtUsername"]; string txtPassword = Request.Form["txtPassword"]; string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;"; SqlConnection cnx = new SqlConnection(strCnx); cnx.Open(); string strQry = "SELECT Count(*) FROM Users WHERE UserName='" + txtUser + "' AND Password='" + txtPassword + "'"; int intRecs; SqlCommand cmd = new SqlCommand(strQry, cnx); intRecs = (int)cmd.ExecuteScalar(); if (intRecs > 0){ FormsAuthentication.RedirectFromLoginPage(txtUser, false); cnx.Close(); } else{ lblMsg.Text = "Login attempt failed."; } } catch (Exception err){ Response.Write(err.StackTrace.ToString()); } } Understanding Control Flow Variable initialized & assigned Control Flow observes all possible paths 81/120
- 80. private void cmdLogin_Click(object sender, System.EventArgs e){ Label lblMsg = null; try { string txtUser = Request.Form["txtUsername"]; string txtPassword = Request.Form["txtPassword"]; string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;"; SqlConnection cnx = new SqlConnection(strCnx); cnx.Open(); string strQry = "SELECT Count(*) FROM Users WHERE UserName='" + txtUser + "' AND Password='" + txtPassword + "'"; int intRecs; SqlCommand cmd = new SqlCommand(strQry, cnx); intRecs = (int)cmd.ExecuteScalar(); if (intRecs > 0){ FormsAuthentication.RedirectFromLoginPage(txtUser, false); cnx.Close(); } else{ lblMsg.Text = "Login attempt failed."; } } catch (Exception err){ Response.Write(err.StackTrace.ToString()); } } Understanding Control Flow Analyze until cnx is out of scope Variable initialized & assigned Control Flow observes all possible paths 82/120
- 81. private void cmdLogin_Click(object sender, System.EventArgs e){ Label lblMsg = null; try { string txtUser = Request.Form["txtUsername"]; string txtPassword = Request.Form["txtPassword"]; string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;"; SqlConnection cnx = new SqlConnection(strCnx); cnx.Open(); string strQry = "SELECT Count(*) FROM Users WHERE UserName='" + txtUser + "' AND Password='" + txtPassword + "'"; int intRecs; SqlCommand cmd = new SqlCommand(strQry, cnx); intRecs = (int)cmd.ExecuteScalar(); if (intRecs > 0){ FormsAuthentication.RedirectFromLoginPage(txtUser, false); cnx.Close(); } else{ lblMsg.Text = "Login attempt failed."; } } catch (Exception err){ Response.Write(err.StackTrace.ToString()); } } Understanding Control Flow Analyze until cnx is out of scope Variable initialized & assigned Control Flow observes all possible paths Vulnerability Reported 83/120
- 82. private void cmdLogin_Click(object sender, System.EventArgs e){ Label lblMsg = null; try { string txtUser = Request.Form["txtUsername"]; string txtPassword = Request.Form["txtPassword"]; string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;"; SqlConnection cnx = new SqlConnection(strCnx); cnx.Open(); string strQry = "SELECT Count(*) FROM Users WHERE UserName='" + txtUser + "' AND Password='" + txtPassword + "'"; int intRecs; SqlCommand cmd = new SqlCommand(strQry, cnx); intRecs = (int)cmd.ExecuteScalar(); if (intRecs > 0){ FormsAuthentication.RedirectFromLoginPage(txtUser, false); cnx.Close(); } else{ lblMsg.Text = "Login attempt failed."; } } catch (Exception err){ Response.Write(err.StackTrace.ToString()); } } Understanding Control Flow Variable initialized & assigned Control Flow observes all possible paths 84/120
- 83. private void cmdLogin_Click(object sender, System.EventArgs e){ Label lblMsg = null; try { string txtUser = Request.Form["txtUsername"]; string txtPassword = Request.Form["txtPassword"]; string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;"; SqlConnection cnx = new SqlConnection(strCnx); cnx.Open(); string strQry = "SELECT Count(*) FROM Users WHERE UserName='" + txtUser + "' AND Password='" + txtPassword + "'"; int intRecs; SqlCommand cmd = new SqlCommand(strQry, cnx); intRecs = (int)cmd.ExecuteScalar(); if (intRecs > 0){ FormsAuthentication.RedirectFromLoginPage(txtUser, false); cnx.Close(); } else{ lblMsg.Text = "Login attempt failed."; } } catch (Exception err){ Response.Write(err.StackTrace.ToString()); } } Understanding Control Flow Analyze until cnx is out of scope Variable initialized & assigned Control Flow observes all possible paths 85/120
- 84. private void cmdLogin_Click(object sender, System.EventArgs e){ Label lblMsg = null; try { string txtUser = Request.Form["txtUsername"]; string txtPassword = Request.Form["txtPassword"]; string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;"; SqlConnection cnx = new SqlConnection(strCnx); cnx.Open(); string strQry = "SELECT Count(*) FROM Users WHERE UserName='" + txtUser + "' AND Password='" + txtPassword + "'"; int intRecs; SqlCommand cmd = new SqlCommand(strQry, cnx); intRecs = (int)cmd.ExecuteScalar(); if (intRecs > 0){ FormsAuthentication.RedirectFromLoginPage(txtUser, false); cnx.Close(); } else{ lblMsg.Text = "Login attempt failed."; } } catch (Exception err){ Response.Write(err.StackTrace.ToString()); } } Understanding Control Flow Vulnerability Reported Analyze until cnx is out of scope Variable initialized & assigned Control Flow observes all possible paths 86/120
- 85. ???? ?? ?? ?? ?? ??
- 86. 1. ???? ?? ?? ??? ˇ°richesˇ± ? ??????? ??? Reputation? ??? ???? ????? ???? ?? ?? ???? ??? ?? 2. DevSecOps ?????? ???? ?? ???? ?? ?? ???? ???? ???? ??? ??? ?? ?? ?? ???? 88/120
- 87. 1. ??? ??? ??? ?? ???? Renewal? ??? ?? ???? ??? ???? ??, ?????? ????? ???? ???? ?? 2. ˇ°Bi-Directional AppSec in CI/CD Pipelineˇ± ??? ????? ?? 1) ??? ???? Jenkins? Nightly Build ???? (?? 4?)? ?? ?? ?? ??? ?? 2) Ops/QA ?? ?? ?? ??? ??? ????? ??? Dev ??? ??? ???? ??? ?? ¨C Reverse AppSec 3) Ops ?? ??? ??? ?? ??? ?????? Renewal ?? ??? ????? ??? Production ??? Deploy, ?? ??????? ???? ??? ???? ????? ??? ?? ?? (RASP; Runtime Application Self Protection) ??? ??? ?? ¨C Forward AppSec ?? ???? 89/120
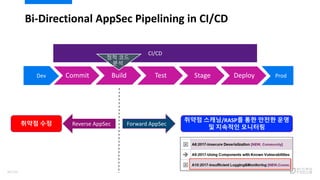
- 88. Bi-Directional AppSec Pipelining in CI/CD Commit Build Test Stage DeployDev Prod CI/CD ?? ?? ?? ??? ?? Reverse AppSec Forward AppSec ??? ???/RASP? ?? ??? ?? ? ???? ???? 90/120
- 89. ?? ? ?? ????? ?? ?? ?? ?? ???? ??? ???? ??? ?? ?? ?? ???? ???? ??? ?? ??? ??? ?? ???? ??? ???. ? ??? ???? ???? ???? ???, ?? ?? ?? ??? ???? ???? ?? ?? ??? ??? ?? ??? ??? ?? ??? ?? ?? ?? ?? ???? ???? ???? ??? ???? ?? ????. 91/120
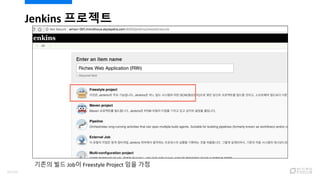
- 90. Jenkins ???? ??? ?? Job? Freestyle Project ?? ?? 92/120
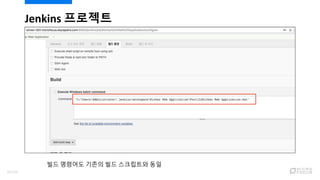
- 91. Jenkins ???? ?? ???? ??? ?? ????? ?? 93/120
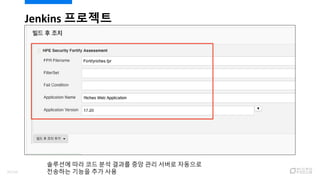
- 92. Jenkins ???? ?? ?? ?? ?? ??? ??? ????? ?? ?? ?? ???? ?? ??? ? ??94/120
- 93. Jenkins ???? ???? ?? ?? ?? ??? ?? ?? ??? ???? ???? ??? ?? ??95/120
- 94. Jenkins ???? ?? ?? - ?? ??? ?? (NVS): 387.2? ¨C ?? ???? ?? 96/120
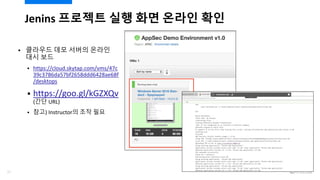
- 95. Jenins ???? ?? ?? ??? ?? ? ???? ?? ??? ??? ?? ?? ? https://cloud.skytap.com/vms/47c 39c3786da57bf2658ddd6428ae68f /desktops ? https://goo.gl/kGZXQv (?? URL) ? ??) Instructor? ?? ?? 97
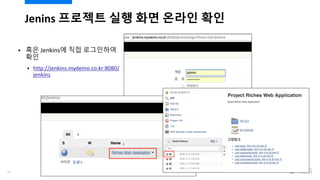
- 96. Jenins ???? ?? ?? ??? ?? ? ?? Jenkins? ?? ????? ?? ? http://jenkins.mydemo.co.kr:8080/ jenkins 98
- 97. Jenkins ???? ?? ?? - ?? ??? ?? (NVS): 387.2? ¨C ?? ???? ?? 99/120
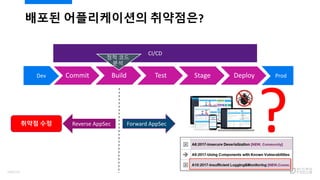
- 98. AppSec Myth ?? ??? ?? ?? ?? ???? ????? ? AppSec Myth ???! ?? ?? X Metric ˇ°???ˇ± ?? ?? ?? ???? ?? ??? ?? 100/120
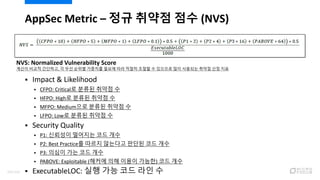
- 99. AppSec Metric ¨C ?? ??? ?? (NVS) ? Impact & Likelihood ? CFPO: Critical? ??? ??? ? ? HFPO: High? ??? ??? ? ? MFPO: Medium?? ??? ??? ? ? LFPO: Low? ??? ??? ? ? Security Quality ? P1: ???? ???? ?? ?? ? P2: Best Practice? ??? ???? ??? ?? ?? ? P3: ??? ?? ?? ?? ? PABOVE: Exploitable (??? ?? ??? ???) ?? ?? ? ExecutableLOC: ?? ?? ?? ?? ? NVS: Normalized Vulnerability Score ??? ??? ????, ? ?? ??? ???? ??? ?? ??? ??? ? ???? ?? ???? ??? ?? ?? 101/120
- 100. Bi-Directional AppSec Activity by NVS! ??? ?? (NVS 200 ??) ??? ?? (NVS 400 ??) NVS ?? 102/120
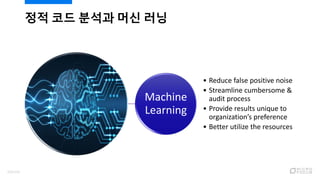
- 101. ?? ?? ??? ?? ?? Machine Learning ? Reduce false positive noise ? Streamline cumbersome & audit process ? Provide results unique to organizationˇŻs preference ? Better utilize the resources 103/120
- 102. ? Supervised Learning First - More data, better result ? Underlying ML algorithm can be extended to unsupervised clustering, data views and outlier detection ?? ?? ??? ?? ?? 104/120
- 103. ?? ?? Smart View 105/120
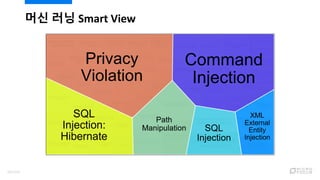
- 104. Prediction Confidence & Issue Graph 106/120
- 105. ? ?? ????? ?? ? Machine Learning ?? ?? ?? ? ???? ?? ???? ??? ?? ?? ?? Assign to Developer with Machine Learning Feedback 107/120
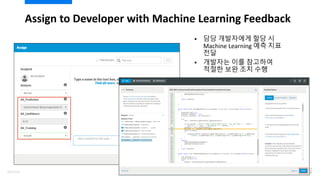
- 106. ??? ?????? ??
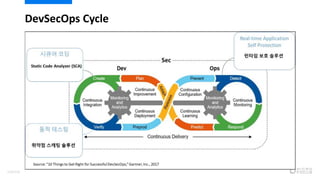
- 107. ??? ??????? ????? Commit Build Test Stage DeployDev Prod CI/CD ?? ?? ?? ??? ?? Reverse AppSec Forward AppSec ? 109/120
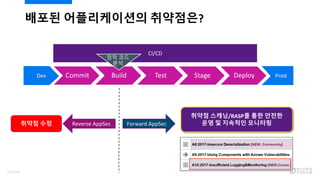
- 108. ??? ??????? ????? Commit Build Test Stage DeployDev Prod CI/CD ?? ?? ?? ??? ?? Reverse AppSec Forward AppSec ??? ???/RASP? ?? ??? ?? ? ???? ???? 110/120
- 109. ?? ?? ?? ???? 2014? APM ??? ?? ??: $2.72B 2019?? $4.98B?? (CAGR 12.86%) ? ??? ?????? ?? ?? (Runtime Application Self-Protection; RASP) ? RASP? ?? ????? ??? ??? ???? ?? ???? ??? ??? ????, ????? ??? ?? ? ???? ?? ?? ? 2017? 10? ?? ??? ¨C ??? ? ??? ??? ??? ?? ??? ??? ????? ?? ?? ? ??? ???: ?? ??? ??? ?? ? ????? ?? ??: ???? ???? ?? ? APM ??? ?? ??? ?? ?? ???ˇ 111/120
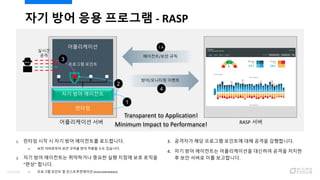
- 110. ?? ?? ?? ???? - RASP ?????? ?? RASP ?? ????/?? ?? ??/???? ??? ?????? ?? ?? ???? ???? ??? ??? ?? ??? 1. ??? ?? ? ?? ?? ????? ?????. A. ?? ????? ?? ??? ?? ??? ?? ????. 2. ?? ?? ????? ????? ??? ?? ??? ?? ??? ˇ°??ˇ± ???. ? ???? ??? ? ???????? (Instrumentation) 1 2 1.A 3 3. ???? ?? ???? ???? ?? ??? ?????. 4. ?? ?? ????? ??????? ???? ??? ??? ? ?? ??? ?? ?????. 4 Transparent to Application! Minimum Impact to Performance! 112/120
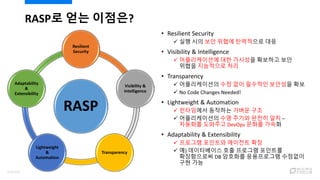
- 111. RASP? ?? ???? ? Resilient Security ? ?? ?? ?? ??? ????? ?? ? Visibility & Intelligence ? ??????? ?? ???? ???? ?? ??? ????? ?? ? Transparency ? ??????? ?? ?? ???? ???? ?? ? No Code Changes Needed! ? Lightweight & Automation ? ????? ???? ??? ?? ? ??????? ?? ??? ??? ?? ¨C ???? ???? DevOps ??? ??? ? Adaptability & Extensibility ? ???? ???? ???? ?? ? ?) ?????? ?? ???? ???? ?????? DB ???? ?????? ???? ?? ?? RASP Resilient Security Visibility & Intelligence Transparency Lightweight & Automation Adaptability & Extensibility 113/120
- 112. ? http://riches1.mydemo.co.kr:58081/riches/ ? Protection message configurable RASP ?? ¨C SQL Injection ?? ?? 114/120
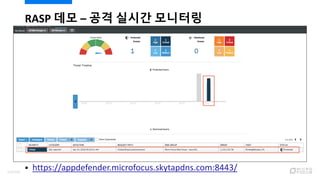
- 113. ? https://appdefender.microfocus.skytapdns.com:8443/ RASP ?? ¨C ?? ??? ???? 115/120
- 114. ???
- 115. ??? ?? ?? ¨C AppSec Journey Cycle SCA ???? ?? ???? ???? ??? ¨C Shift Left, Find More! ?? ??? ?? Scan Surface? ??? SCA? ???? ?? ???? ??? ??? ?? ?? ? ?? ???? ??? ?? RASP ??? ?? ?? ??? ???? ????, ??? ???? ?? ???? ?? 117/120
- 116. ???... ? ??????? ???? ???? ???? ???? ??? ? ??? ??? ??? ? ?? ??? ??? ????. ? ???? ????? ?? ???? ?? (Viral) ?? ?? ?? ??? ???? ?? ˇ°DevOpsˇ±? ˇ°CI/CDˇ±? ????. ? ??? ??? ??? ?? ??? ?? ?? ???? CI/CD ?? Jenkins? ???? ?? ??? ?? ?????. ? ??? ??? ???? ????? ??? ? ?? ??? ??????? ??? ???? ????? ? ?? RASP? ???? ???????. ? ?? ??? ???? ????? ??? ? ??? ???? ???? ???? AppSec ??? ?? ???? ????! 118/120
- 118. ?????!
















![A1: Injection ¨C SQL Injection (??)
? ????? ???? [' or '1' =
'1]? ???? ??
? ˇ°???? ???? ???ˇ±
?? ??? ??? ???
43/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-41-320.jpg)


![A1: Injection ¨C Command Injection (??)
? ??? ??? ["; cat
/etc/passwd"] ?? ? ˇ°Send
?? ??ˇ±
? ???? ??? ???
???? ??
50/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-48-320.jpg)




![? ???? Username?
[<script>alert('1');</script>]?
???? ˇ°Goˇ± ?? ??
A7: Cross Site Scripting (XSS) - Reflected
59/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-57-320.jpg)





![Understanding Data Flow
1 import java.sql.*;
2
3 public class SQLInjection {
4 public static void main (String args[]) {
5 Connection conn = null;
6 try {
7 String userName = args [0];
8 String passwd = args [1];
9 String query = "select uname, passwd from users where uname like "+userName+"%";
10 conn = DriverManager.getConnection ("jdbc:odbc:logistics", "admin", "letmein");
11 Statement stmnt = conn.createStatement ();
12 ResultSet rs = stmnt.executeQuery (query);
13 while ( rs.next() ) {
14 ...
15 }
16 rs.close ();
17 stmnt.close ();
18 conn.close ();
19 }
20 catch (SQLException err) {
21 err.printStackTrace ();
22 }
23 }
24 }
68/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-66-320.jpg)
![Understanding Data Flow
import java.sql.*;
public class SQLInjection {
public static void main (String args[]) {
Connection conn = null;
try {
String userName = args [0];
String passwd = args [1];
String query = "select uname, passwd from users where uname like "+userName+"%";
conn = DriverManager.getConnection ("jdbc:odbc:logistics", "admin", "letmein");
Statement stmnt = conn.createStatement ();
ResultSet rs = stmnt.executeQuery (query);
while ( rs.next() ) {
...
}
rs.close ();
stmnt.close ();
conn.close ();
}
catch (SQLException err) {
err.printStackTrace ();
}
}
}
Source
69/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-67-320.jpg)
![Understanding Data Flow
import java.sql.*;
public class SQLInjection {
public static void main (String args[]) {
Connection conn = null;
try {
String userName = args [0];
String passwd = args [1];
String query = "select uname, passwd from users where uname like "+userName+"%";
conn = DriverManager.getConnection ("jdbc:odbc:logistics", "admin", "letmein");
Statement stmnt = conn.createStatement ();
ResultSet rs = stmnt.executeQuery (query);
while ( rs.next() ) {
...
}
rs.close ();
stmnt.close ();
conn.close ();
}
catch (SQLException err) {
err.printStackTrace ();
}
}
}
args[] is tainted
Source
70/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-68-320.jpg)
![Understanding Data Flow
import java.sql.*;
public class SQLInjection {
public static void main (String args[]) {
Connection conn = null;
try {
String userName = args [0];
String passwd = args [1];
String query = "select uname, passwd from users where uname like "+userName+"%";
conn = DriverManager.getConnection ("jdbc:odbc:logistics", "admin", "letmein");
Statement stmnt = conn.createStatement ();
ResultSet rs = stmnt.executeQuery (query);
while ( rs.next() ) {
...
}
rs.close ();
stmnt.close ();
conn.close ();
}
catch (SQLException err) {
err.printStackTrace ();
}
}
}
Taint propagated to userName
args[] is tainted
Source
71/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-69-320.jpg)
![Understanding Data Flow
import java.sql.*;
public class SQLInjection {
public static void main (String args[]) {
Connection conn = null;
try {
String userName = args [0];
String passwd = args [1];
String query = "select uname, passwd from users where uname like "+userName+"%";
conn = DriverManager.getConnection ("jdbc:odbc:logistics", "admin", "letmein");
Statement stmnt = conn.createStatement ();
ResultSet rs = stmnt.executeQuery (query);
while ( rs.next() ) {
...
}
rs.close ();
stmnt.close ();
conn.close ();
}
catch (SQLException err) {
err.printStackTrace ();
}
}
}
Tainted input
userName used
in assignment
Taint propagated to userName
args[] is tainted
Source
72/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-70-320.jpg)
![Understanding Data Flow
import java.sql.*;
public class SQLInjection {
public static void main (String args[]) {
Connection conn = null;
try {
String userName = args [0];
String passwd = args [1];
String query = "select uname, passwd from users where uname like "+userName+"%";
conn = DriverManager.getConnection ("jdbc:odbc:logistics", "admin", "letmein");
Statement stmnt = conn.createStatement ();
ResultSet rs = stmnt.executeQuery (query);
while ( rs.next() ) {
...
}
rs.close ();
stmnt.close ();
conn.close ();
}
catch (SQLException err) {
err.printStackTrace ();
}
}
}
Sink
Tainted input
userName used
in assignment
Taint propagated to userName
args[] is tainted
Source
73/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-71-320.jpg)
![Understanding Data Flow
import java.sql.*;
public class SQLInjection {
public static void main (String args[]) {
Connection conn = null;
try {
String userName = args [0];
String passwd = args [1];
String query = "select uname, passwd from users where uname like "+userName+"%";
conn = DriverManager.getConnection ("jdbc:odbc:logistics", "admin", "letmein");
Statement stmnt = conn.createStatement ();
ResultSet rs = stmnt.executeQuery (query);
while ( rs.next() ) {
...
}
rs.close ();
stmnt.close ();
conn.close ();
}
catch (SQLException err) {
err.printStackTrace ();
}
}
}
Vulnerability
Reported
Sink
Tainted input
userName used
in assignment
Taint propagated to userName
args[] is tainted
Source
74/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-72-320.jpg)

![Understanding Control Flow
1 private void cmdLogin_Click(object sender, System.EventArgs e){
2 Label lblMsg = null;
3 try {
4 string txtUser = Request.Form["txtUsername"];
5 string txtPassword = Request.Form["txtPassword"];
6 string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;";
7 SqlConnection cnx = new SqlConnection(strCnx);
8 cnx.Open();
9
10 string strQry = "SELECT Count(*) FROM Users WHERE UserName='" +
11 txtUser + "' AND Password='" + txtPassword + "'";
12 int intRecs;
13
14 SqlCommand cmd = new SqlCommand(strQry, cnx);
15 intRecs = (int)cmd.ExecuteScalar();
16
17 if (intRecs > 0){
18 FormsAuthentication.RedirectFromLoginPage(txtUser, false);
19 cnx.Close();
20 }
21 else{
22 lblMsg.Text = "Login attempt failed.";
23 }
24 }
25 catch (Exception err){
26 Response.Write(err.StackTrace.ToString());
27 }
28 }
76/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-74-320.jpg)
![private void cmdLogin_Click(object sender, System.EventArgs e){
Label lblMsg = null;
try {
string txtUser = Request.Form["txtUsername"];
string txtPassword = Request.Form["txtPassword"];
string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;";
SqlConnection cnx = new SqlConnection(strCnx);
cnx.Open();
string strQry = "SELECT Count(*) FROM Users WHERE UserName='" +
txtUser + "' AND Password='" + txtPassword + "'";
int intRecs;
SqlCommand cmd = new SqlCommand(strQry, cnx);
intRecs = (int)cmd.ExecuteScalar();
if (intRecs > 0){
FormsAuthentication.RedirectFromLoginPage(txtUser, false);
cnx.Close();
}
else{
lblMsg.Text = "Login attempt failed.";
}
}
catch (Exception err){
Response.Write(err.StackTrace.ToString());
}
}
Understanding Control Flow
Variable
initialized &
assigned
77/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-75-320.jpg)
![private void cmdLogin_Click(object sender, System.EventArgs e){
Label lblMsg = null;
try {
string txtUser = Request.Form["txtUsername"];
string txtPassword = Request.Form["txtPassword"];
string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;";
SqlConnection cnx = new SqlConnection(strCnx);
cnx.Open();
string strQry = "SELECT Count(*) FROM Users WHERE UserName='" +
txtUser + "' AND Password='" + txtPassword + "'";
int intRecs;
SqlCommand cmd = new SqlCommand(strQry, cnx);
intRecs = (int)cmd.ExecuteScalar();
if (intRecs > 0){
FormsAuthentication.RedirectFromLoginPage(txtUser, false);
cnx.Close();
}
else{
lblMsg.Text = "Login attempt failed.";
}
}
catch (Exception err){
Response.Write(err.StackTrace.ToString());
}
}
Understanding Control Flow
Connection
closed
Variable
initialized &
assigned
78/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-76-320.jpg)
![private void cmdLogin_Click(object sender, System.EventArgs e){
Label lblMsg = null;
try {
string txtUser = Request.Form["txtUsername"];
string txtPassword = Request.Form["txtPassword"];
string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;";
SqlConnection cnx = new SqlConnection(strCnx);
cnx.Open();
string strQry = "SELECT Count(*) FROM Users WHERE UserName='" +
txtUser + "' AND Password='" + txtPassword + "'";
int intRecs;
SqlCommand cmd = new SqlCommand(strQry, cnx);
intRecs = (int)cmd.ExecuteScalar();
if (intRecs > 0){
FormsAuthentication.RedirectFromLoginPage(txtUser, false);
cnx.Close();
}
else{
lblMsg.Text = "Login attempt failed.";
}
}
catch (Exception err){
Response.Write(err.StackTrace.ToString());
}
}
Understanding Control Flow
Safe
Sequence
Connection
closed
Variable
initialized &
assigned
79/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-77-320.jpg)
![private void cmdLogin_Click(object sender, System.EventArgs e){
Label lblMsg = null;
try {
string txtUser = Request.Form["txtUsername"];
string txtPassword = Request.Form["txtPassword"];
string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;";
SqlConnection cnx = new SqlConnection(strCnx);
cnx.Open();
string strQry = "SELECT Count(*) FROM Users WHERE UserName='" +
txtUser + "' AND Password='" + txtPassword + "'";
int intRecs;
SqlCommand cmd = new SqlCommand(strQry, cnx);
intRecs = (int)cmd.ExecuteScalar();
if (intRecs > 0){
FormsAuthentication.RedirectFromLoginPage(txtUser, false);
cnx.Close();
}
else{
lblMsg.Text = "Login attempt failed.";
}
}
catch (Exception err){
Response.Write(err.StackTrace.ToString());
}
}
Understanding Control Flow
Variable
initialized &
assigned
80/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-78-320.jpg)
![private void cmdLogin_Click(object sender, System.EventArgs e){
Label lblMsg = null;
try {
string txtUser = Request.Form["txtUsername"];
string txtPassword = Request.Form["txtPassword"];
string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;";
SqlConnection cnx = new SqlConnection(strCnx);
cnx.Open();
string strQry = "SELECT Count(*) FROM Users WHERE UserName='" +
txtUser + "' AND Password='" + txtPassword + "'";
int intRecs;
SqlCommand cmd = new SqlCommand(strQry, cnx);
intRecs = (int)cmd.ExecuteScalar();
if (intRecs > 0){
FormsAuthentication.RedirectFromLoginPage(txtUser, false);
cnx.Close();
}
else{
lblMsg.Text = "Login attempt failed.";
}
}
catch (Exception err){
Response.Write(err.StackTrace.ToString());
}
}
Understanding Control Flow
Variable
initialized &
assigned
Control Flow observes all
possible paths
81/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-79-320.jpg)
![private void cmdLogin_Click(object sender, System.EventArgs e){
Label lblMsg = null;
try {
string txtUser = Request.Form["txtUsername"];
string txtPassword = Request.Form["txtPassword"];
string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;";
SqlConnection cnx = new SqlConnection(strCnx);
cnx.Open();
string strQry = "SELECT Count(*) FROM Users WHERE UserName='" +
txtUser + "' AND Password='" + txtPassword + "'";
int intRecs;
SqlCommand cmd = new SqlCommand(strQry, cnx);
intRecs = (int)cmd.ExecuteScalar();
if (intRecs > 0){
FormsAuthentication.RedirectFromLoginPage(txtUser, false);
cnx.Close();
}
else{
lblMsg.Text = "Login attempt failed.";
}
}
catch (Exception err){
Response.Write(err.StackTrace.ToString());
}
}
Understanding Control Flow
Analyze until cnx is out
of scope
Variable
initialized &
assigned
Control Flow observes all
possible paths
82/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-80-320.jpg)
![private void cmdLogin_Click(object sender, System.EventArgs e){
Label lblMsg = null;
try {
string txtUser = Request.Form["txtUsername"];
string txtPassword = Request.Form["txtPassword"];
string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;";
SqlConnection cnx = new SqlConnection(strCnx);
cnx.Open();
string strQry = "SELECT Count(*) FROM Users WHERE UserName='" +
txtUser + "' AND Password='" + txtPassword + "'";
int intRecs;
SqlCommand cmd = new SqlCommand(strQry, cnx);
intRecs = (int)cmd.ExecuteScalar();
if (intRecs > 0){
FormsAuthentication.RedirectFromLoginPage(txtUser, false);
cnx.Close();
}
else{
lblMsg.Text = "Login attempt failed.";
}
}
catch (Exception err){
Response.Write(err.StackTrace.ToString());
}
}
Understanding Control Flow
Analyze until cnx is out
of scope
Variable
initialized &
assigned
Control Flow observes all
possible paths
Vulnerability
Reported
83/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-81-320.jpg)
![private void cmdLogin_Click(object sender, System.EventArgs e){
Label lblMsg = null;
try {
string txtUser = Request.Form["txtUsername"];
string txtPassword = Request.Form["txtPassword"];
string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;";
SqlConnection cnx = new SqlConnection(strCnx);
cnx.Open();
string strQry = "SELECT Count(*) FROM Users WHERE UserName='" +
txtUser + "' AND Password='" + txtPassword + "'";
int intRecs;
SqlCommand cmd = new SqlCommand(strQry, cnx);
intRecs = (int)cmd.ExecuteScalar();
if (intRecs > 0){
FormsAuthentication.RedirectFromLoginPage(txtUser, false);
cnx.Close();
}
else{
lblMsg.Text = "Login attempt failed.";
}
}
catch (Exception err){
Response.Write(err.StackTrace.ToString());
}
}
Understanding Control Flow
Variable
initialized &
assigned
Control Flow observes all
possible paths
84/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-82-320.jpg)
![private void cmdLogin_Click(object sender, System.EventArgs e){
Label lblMsg = null;
try {
string txtUser = Request.Form["txtUsername"];
string txtPassword = Request.Form["txtPassword"];
string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;";
SqlConnection cnx = new SqlConnection(strCnx);
cnx.Open();
string strQry = "SELECT Count(*) FROM Users WHERE UserName='" +
txtUser + "' AND Password='" + txtPassword + "'";
int intRecs;
SqlCommand cmd = new SqlCommand(strQry, cnx);
intRecs = (int)cmd.ExecuteScalar();
if (intRecs > 0){
FormsAuthentication.RedirectFromLoginPage(txtUser, false);
cnx.Close();
}
else{
lblMsg.Text = "Login attempt failed.";
}
}
catch (Exception err){
Response.Write(err.StackTrace.ToString());
}
}
Understanding Control Flow
Analyze until cnx is out
of scope
Variable
initialized &
assigned
Control Flow observes all
possible paths
85/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-83-320.jpg)
![private void cmdLogin_Click(object sender, System.EventArgs e){
Label lblMsg = null;
try {
string txtUser = Request.Form["txtUsername"];
string txtPassword = Request.Form["txtPassword"];
string strCnx = "server=localhost;database=northwind;uid=sa;pwd=;";
SqlConnection cnx = new SqlConnection(strCnx);
cnx.Open();
string strQry = "SELECT Count(*) FROM Users WHERE UserName='" +
txtUser + "' AND Password='" + txtPassword + "'";
int intRecs;
SqlCommand cmd = new SqlCommand(strQry, cnx);
intRecs = (int)cmd.ExecuteScalar();
if (intRecs > 0){
FormsAuthentication.RedirectFromLoginPage(txtUser, false);
cnx.Close();
}
else{
lblMsg.Text = "Login attempt failed.";
}
}
catch (Exception err){
Response.Write(err.StackTrace.ToString());
}
}
Understanding Control Flow
Vulnerability
Reported
Analyze until cnx is out
of scope
Variable
initialized &
assigned
Control Flow observes all
possible paths
86/120](https://image.slidesharecdn.com/s-sdlcsecurecoding2018-04-21-180423031934/85/Main-Session-84-320.jpg)