Malicious MDM - Secure360
Download as pptx, pdf0 likes228 views
This document summarizes a presentation about malicious uses of Mobile Device Management (MDM) software. It describes how MDM can be used to manage devices but also exploited by attackers. It provides examples of techniques like using direct USB connections, websites, or email to deploy rogue MDM profiles that can steal credentials, intercept traffic, or install malicious apps. The presentation includes a demonstration of creating a fake wireless network and apps using an MDM profile. Defenses discussed include only adding devices to your legitimate MDM and not connecting devices to untrusted USB ports.
1 of 37
Download to read offline
























Ad
Recommended
Malicious MDM - AppSecCA
Malicious MDM - AppSecCAKarl Fosaaen
Ėý
The document discusses malicious Mobile Device Management (MDM) techniques, focusing on how attackers can exploit MDM systems to manage and control devices. It details various methods of deployment and post-deployment exploitation, including wireless attacks and application exploitation. Preventative measures are also suggested to safeguard against unauthorized device access.Lismar delgadoLismar Delgado
Ėý
El documento presenta un anÃĄlisis del pronÃģstico de ventas de la revista Hola Venezuela para los aÃąos 2014 y 2015. Incluye tablas con las ventas previstas y reales de 2014, factores que afectan los pronÃģsticos, mÃĐtodos cualitativos y cuantitativos de pronÃģstico, y el cÃĄlculo del pronÃģstico para 2015 usando anÃĄlisis de regresiÃģn. Se recomienda revisar trimestralmente el pronÃģstico y mercado para aplicar planes de contingencia.Hacking iOS with Proxies - dc612
Hacking iOS with Proxies - dc612Karl Fosaaen
Ėý
The document presents a comprehensive overview of hacking techniques related to iOS Game Center and Passbook using intercepting proxies to manipulate traffic. It discusses various tools, methods, and examples of attacks on Game Center scores and email hashes, as well as vulnerabilities within Passbook files. The author concludes with recommendations for improving security through better input validation and certificate pinning.Externally Testing Modern AD Domains - Arcticcon
Externally Testing Modern AD Domains - ArcticconKarl Fosaaen
Ėý
The document by Karl Fosaaen discusses various methods for externally testing modern Active Directory domains, including domain enumeration, credential brute forcing, and pivoting to internal networks. Key topics include the use of Graph API, ADFS, Office 365, and Skype for Business for exploiting weak logins and phishing vulnerabilities. It concludes with recommendations for attack mitigations such as enabling multi-factor authentication and limiting federation to trusted domains.Motivational week 1 disc. 2
Motivational week 1 disc. 2suesmith74
Ėý
This motivational presentation encourages the audience to never give up when facing challenges by making lemonade out of lemons and believing in themselves. It includes quotes about how the view is better when reaching the top rather than going down, that we get what we are rather than what we want, and that believing in oneself will lead others to believe in you as well. The overall message is to stay strong, keep a positive attitude, and believe in your own self-worth.GPU Cracking on the Cheap
GPU Cracking on the CheapKarl Fosaaen
Ėý
This document discusses how to set up an inexpensive GPU cracking rig to crack passwords. It recommends using graphics cards like the Radeon HD 7970 or 7950 for their high hash rates. An ASRock motherboard, Intel CPU, SSD, HDD, 1500W power supply, and open case design keep costs around $3,000. Linux is preferred over Windows for the operating system. OclHashcat is recommended cracking software that supports GPUs and many hash types. Dictionary, rule-based, and masking attacks are more effective than brute force. The document provides performance stats and concludes GPU cracking can be done affordably to test password security.Stampa 3D: La III Rivoluzione Industriale? - 3D Printing: The 3rd Industrial ...
Stampa 3D: La III Rivoluzione Industriale? - 3D Printing: The 3rd Industrial ...Marco Alici
Ėý
The document discusses the impact of 3D printing as a potential third industrial revolution, contrasting it with the earlier industrial revolutions. It outlines various 3D printing technologies and materials, highlighting their applications in prototyping, on-demand production, and innovative use cases. It also emphasizes the community-driven nature of 3D printing with open-source hardware and software, as well as notable advancements in 3D printing technology.Hacking iOS Applications with Proxies
Hacking iOS Applications with ProxiesKarl Fosaaen
Ėý
The document details a presentation by Karl Fosaaen on hacking iOS GameCenter and Passbook using proxies, focusing on intercepting iOS traffic and sharing tools and techniques for traffic tampering. It includes examples of attacks on GameCenter high scores and email hash extraction, as well as vulnerabilities in Passbook files. The presentation concludes with recommended fixes to enhance security through certificate pinning and better input validation.Flip book
Flip bookMichelle Saikali
Ėý
Social media allows people to communicate and share content online, but poses risks to young users. While the minimum age requirement for most sites is 13, over 7.5 million Facebook users are below this age. Young children may be exposed to predators online or experience depression from focusing on their social status. They also leave a permanent digital footprint of all content they post. However, social media does allow users to connect with others worldwide and stay informed, as 27% of Americans use social networks as a news source. But the large amounts of time spent on sites like Facebook, with 23% checking over five times daily and 700 billion minutes spent monthly, raises questions about internet addiction issues in future generations.Mobius lab Review
Mobius lab ReviewMuseum Planning, LLC
Ėý
The document provides a summary of Mark Walhimer's review of MobiusLab, a preview facility for the planned Mobius Science Center in Spokane, WA. Some key points:
1) Walhimer was impressed with MobiusLab's location in a suburban mall and felt it had a fun, welcoming atmosphere. However, he noted some visitors and mall staff were unaware of it.
2) Surveys of visitors found they enjoyed the interactive exhibits but few used the PassPort to Discovery digital learning system. Walhimer provided suggestions to better integrate it with the exhibits.
3) Walhimer recommended keeping MobiusLab open longer term and expanding it as Phase 1 of a multi-phasenew media
new mediajp500595
Ėý
This document appears to be a student's notes on various terms related to truth, respect, support, and concern for others. The notes include definitions for terms like "persuade", "truth", "respect", "friendly", "support", "allegiance", "bravery", "anywhere", "aspiration", and "unkind".Mohammad cv 16.5.2013
Mohammad cv 16.5.2013mohammadalbdour
Ėý
This document contains a summary of Mohammad R. Al-Bdour's career objective, personal information, professional experience, education, target job, skills, languages, and availability of references. Al-Bdour is seeking a challenging marketing or sales position in real estate, manufacturing, construction, or management. He has over 10 years of experience in sales and currently works as a sales executive for a UPVC windows and doors manufacturer in Abu Dhabi, UAE. Al-Bdour holds a Bachelor's degree in Marketing from Yarmouk University in Jordan.šÝšÝßĢ kombis
šÝšÝßĢ kombisNining Rn
Ėý
Dokumen tersebut membahas tentang perencanaan pesan-pesan persuasif dalam komunikasi bisnis. Terdapat empat komponen utama dalam membuat pesan persuasif yaitu menetapkan kredibilitas, membuat kerangka argumentasi, menghubungkan audiens dengan daya tarik logika dan emosi, serta memperkuat posisi dengan bahasa yang tepat. Dokumen ini juga menjelaskan berbagai jenis surat bisnis dan bagian-bagiannya.Conception avec pic nawzat
Ėý
Ce document est un support de cours sur la conception et la simulation de systÃĻmes à microcontrÃīleurs PIC, utilisant le compilateur Mikroc Pro et le simulateur Proteus ISIS. Il couvre divers aspects du langage C, y compris la dÃĐclaration des variables, les fonctions, et l'affichage des donnÃĐes, ainsi que des applications pratiques avec des capteurs et des systÃĻmes d'entrÃĐe. Le support vise à enseigner aux ÃĐtudiants des concepts fondamentaux pour dÃĐvelopper des projets avec les microcontrÃīleurs PIC.Attacking ADFS Endpoints - DerbyCon
Attacking ADFS Endpoints - DerbyConKarl Fosaaen
Ėý
The document presents a detailed examination of attacks on Active Directory Federation Services (ADFS) using PowerShell, covering user enumeration, phishing, and dictionary attacks. It provides a comprehensive guide on setting up a test environment, identifying federated endpoints, and mitigation strategies to enhance security. Key insights include the importance of dual-factor authentication and monitoring of federated services to protect against common vulnerabilities.Automating Attacks Against Office365 - BsidesPDX 2016
Automating Attacks Against Office365 - BsidesPDX 2016Karl Fosaaen
Ėý
The document discusses methods for automating attacks on Office 365, including techniques for domain enumeration, user enumeration, credential brute forcing, and internal network pivoting. It also highlights various PowerShell scripts and tools that facilitate these attacks and outlines mitigations such as enabling dual-factor authentication and limiting federation to trusted domains. The presentation emphasizes the importance of monitoring endpoints and enforcing strong password requirements to reduce vulnerabilities.FreeCAD il cad 3D libero
FreeCAD il cad 3D liberoMarco Alici
Ėý
FreeCAD is an open-source 3D CAD application that is free, modular, and multiplatform. It uses Open CASCADE for modeling geometry and Coin3D + Qt + Python for visualization. FreeCAD's modular architecture allows it to be highly customizable and its multiplatform support means it can run on Linux, Windows, and Mac.iOS enterprise
iOS enterprisedominion
Ėý
This document provides an overview of using iOS devices in the enterprise. It discusses why IT needs to be engaged with mobile device management as employees increasingly use iOS devices. It covers using IBM Lotus Traveler with iOS, iOS enterprise capabilities including configuration profiles, and over-the-air deployment and mobile device management (MDM) to securely manage iOS devices. The presentation includes demos of an MDM solution to illustrate how devices can be enrolled and managed remotely.UKLUG 2011 - iOS devices in the enterprise
UKLUG 2011 - iOS devices in the enterpriseRenÃĐ Winkelmeyer
Ėý
The presentation by RenÃĐ Winkelmeyer discusses the integration of iOS devices in enterprise environments, focusing on their management via IBM Lotus Traveler and mobile device management (MDM). It emphasizes the need for proper configuration, security measures, and over-the-air deployment to ensure effective usage of iOS devices in businesses. The conclusion highlights that while iOS devices are capable for enterprise use, robust device management is essential for a secure and productive experience.WSO2Con Asia 2014 - Embracing BYOD Trend Without Compromising Security, Emplo...
WSO2Con Asia 2014 - Embracing BYOD Trend Without Compromising Security, Emplo...WSO2
Ėý
WSO2 EMM is a mobile enterprise management solution that allows organizations to embrace BYOD trends while maintaining security, privacy, and user experience. It addresses challenges of mobility through features like mobile device management, a managed enterprise app store, and mobile app management. The presentation discusses different approaches to data security including MDM, separating personal and work environments, and MAM. MAM is highlighted as a best approach for controlling app behavior through SDKs or app wrapping while still providing a native user experience. WSO2 EMM provides all these capabilities in a unified solution to enable secure enterprise mobility.WSO2Con Asia 2014 - Embracing BYOD Trend Without Compromising Security, Emplo...
WSO2Con Asia 2014 - Embracing BYOD Trend Without Compromising Security, Emplo...WSO2
Ėý
WSO2 EMM is a mobile enterprise management solution that allows organizations to embrace BYOD trends while maintaining security, privacy, and user experience. It addresses challenges of mobility through features like mobile device management, a managed enterprise app store, and mobile app management. The presentation discusses different approaches to data security including MDM, separating personal and work environments, and MAM. MAM is highlighted as a best approach for controlling app behavior through SDKs or app wrapping while still providing a native user experience. WSO2 EMM provides all these capabilities in a unified solution to enable secure enterprise mobility.WSO2Con USA 2015: Connected Device Management for Enterprise Mobility and Beyond
WSO2Con USA 2015: Connected Device Management for Enterprise Mobility and BeyondWSO2
Ėý
The document outlines a framework for enterprise mobility and connected device management, emphasizing the need for robust data security measures in managing various mobile devices such as smartphones, tablets, and IoT. It details the challenges and risks associated with data security, including possible data leaks and device theft, and provides an overview of the functionalities and features of WSO2's enterprise mobility management platform. Additionally, it covers management capabilities for different operating systems like iOS, Android, and Windows, focusing on device management and application development.Wso2 con byod-shan-ppt
Wso2 con byod-shan-pptWSO2
Ėý
The document discusses embracing BYOD trends in enterprises while maintaining security, privacy and user experience. It outlines challenges like data security and different approaches like mobile device management (MDM), mobile application management (MAM) and separating enterprise and personal data. WSO2 Enterprise Mobility Manager is introduced as a solution that provides MDM, an enterprise app store, and mobile application management features to address BYOD challenges.DeepSec_2019_Chemerkin_Yury_-_Full_-_Final.pdf
DeepSec_2019_Chemerkin_Yury_-_Full_-_Final.pdfYury Chemerkin
Ėý
Yury Chemerkin is a seasoned multi-skilled security expert with over 10 years of experience in information security, focusing on areas such as privacy, compliance, and forensics. He highlights the significance of password management and the vulnerabilities associated with user credential storage systems, especially in mobile and cloud computing contexts. The document emphasizes various aspects of data leakage, forensics capabilities, and the management of interconnected accounts and their security risks.WSO2 Enterprise Mobility Manager - 2.0
WSO2 Enterprise Mobility Manager - 2.0Dilshan Edirisuriya
Ėý
WSO2 Enterprise Mobility Manager (EMM) allows organizations to securely manage mobile devices and apps. It addresses key challenges of data security, remote device management, and mobile application development. The EMM uses the Connected Device Management Framework (CDMF) for device, application, policy and other management functions. It supports features like device enrollment, policy enforcement, app distribution, and security controls on iOS, Android and Windows platforms to help organizations securely enable mobility.WSO2Con Asia 2014 - Embracing BYOD Trend Without Compromising Security, Emplo...
WSO2Con Asia 2014 - Embracing BYOD Trend Without Compromising Security, Emplo...WSO2
Ėý
This document discusses approaches to embracing bring your own device (BYOD) trends in enterprises without compromising security, employee privacy, or the mobile experience. It outlines challenges with enterprise mobility including data security, remote device management, and application development. Approaches to data security include mobile device management, separating enterprise apps and data from personal data, and mobile application management. Mobile application management provides a better user experience and privacy while controlling app behavior through SDKs, app wrapping, and policies. The document also summarizes features of the WSO2 Enterprise Mobility Manager for mobile device management, an enterprise app store, and mobile application management.WSO2Con Asia 2014 - ïŋž Embracing BYOD Trend Without Compromising Security, Emp...
WSO2Con Asia 2014 - ïŋž Embracing BYOD Trend Without Compromising Security, Emp...WSO2
Ėý
This document discusses approaches to embracing bring your own device (BYOD) trends in enterprises without compromising security, employee privacy, or the mobile experience. It outlines challenges with enterprise mobility including data security, remote device management, and application development. Approaches to data security include mobile device management, separating enterprise apps and data from personal data, and mobile application management. Mobile application management provides a better user experience and privacy while controlling app behavior through SDKs, app wrapping, and policies. The document also summarizes features of the WSO2 Enterprise Mobility Manager for mobile device management, an enterprise app store, and mobile application management.OWASP Top 10 for Mobile
OWASP Top 10 for MobileAppvigil - Mobile App Security Scanner
Ėý
The document summarizes a recap of the OWASP Mobile App Security Meet, outlining key aspects of mobile app security, including its history, the essential top 10 security issues, and best practices. It emphasizes the importance of securing sensitive data, preventing data leakage, addressing client-side vulnerabilities, and enforcing robust server-side controls. Additionally, it highlights the need for developers to adhere to OWASP guidelines for ensuring mobile application security.Can You Steal From Me Now? Mobile and BYOD Security Risks
Can You Steal From Me Now? Mobile and BYOD Security RisksMichael Davis
Ėý
Mobile devices and BYOD policies introduce significant security risks to organizations. The proliferation of mobile devices has led to new threats like activity monitoring, unauthorized payments, and exfiltration of sensitive data. Many mobile applications also put users' private data at risk through unsafe data practices and potential impersonation attacks. To help address these issues, user education is important, and organizations need strong mobile privacy and document access controls.Smartphones
SmartphonesSaeed Slemy
Ėý
This document provides an overview of smart phones and how to configure internet access on different operating systems. It discusses the evolution of smart phones from early mobile phones used in World War II to today's advanced devices. It then explains how to set up internet access on Android, iOS, Windows Phone, and Symbian operating systems by accessing settings menus and configuring APN settings with the mobile network name "internet". The document aims to help users set up internet access on their smart phones.More Related Content
Viewers also liked (9)
Flip book
Flip bookMichelle Saikali
Ėý
Social media allows people to communicate and share content online, but poses risks to young users. While the minimum age requirement for most sites is 13, over 7.5 million Facebook users are below this age. Young children may be exposed to predators online or experience depression from focusing on their social status. They also leave a permanent digital footprint of all content they post. However, social media does allow users to connect with others worldwide and stay informed, as 27% of Americans use social networks as a news source. But the large amounts of time spent on sites like Facebook, with 23% checking over five times daily and 700 billion minutes spent monthly, raises questions about internet addiction issues in future generations.Mobius lab Review
Mobius lab ReviewMuseum Planning, LLC
Ėý
The document provides a summary of Mark Walhimer's review of MobiusLab, a preview facility for the planned Mobius Science Center in Spokane, WA. Some key points:
1) Walhimer was impressed with MobiusLab's location in a suburban mall and felt it had a fun, welcoming atmosphere. However, he noted some visitors and mall staff were unaware of it.
2) Surveys of visitors found they enjoyed the interactive exhibits but few used the PassPort to Discovery digital learning system. Walhimer provided suggestions to better integrate it with the exhibits.
3) Walhimer recommended keeping MobiusLab open longer term and expanding it as Phase 1 of a multi-phasenew media
new mediajp500595
Ėý
This document appears to be a student's notes on various terms related to truth, respect, support, and concern for others. The notes include definitions for terms like "persuade", "truth", "respect", "friendly", "support", "allegiance", "bravery", "anywhere", "aspiration", and "unkind".Mohammad cv 16.5.2013
Mohammad cv 16.5.2013mohammadalbdour
Ėý
This document contains a summary of Mohammad R. Al-Bdour's career objective, personal information, professional experience, education, target job, skills, languages, and availability of references. Al-Bdour is seeking a challenging marketing or sales position in real estate, manufacturing, construction, or management. He has over 10 years of experience in sales and currently works as a sales executive for a UPVC windows and doors manufacturer in Abu Dhabi, UAE. Al-Bdour holds a Bachelor's degree in Marketing from Yarmouk University in Jordan.šÝšÝßĢ kombis
šÝšÝßĢ kombisNining Rn
Ėý
Dokumen tersebut membahas tentang perencanaan pesan-pesan persuasif dalam komunikasi bisnis. Terdapat empat komponen utama dalam membuat pesan persuasif yaitu menetapkan kredibilitas, membuat kerangka argumentasi, menghubungkan audiens dengan daya tarik logika dan emosi, serta memperkuat posisi dengan bahasa yang tepat. Dokumen ini juga menjelaskan berbagai jenis surat bisnis dan bagian-bagiannya.Conception avec pic nawzat
Ėý
Ce document est un support de cours sur la conception et la simulation de systÃĻmes à microcontrÃīleurs PIC, utilisant le compilateur Mikroc Pro et le simulateur Proteus ISIS. Il couvre divers aspects du langage C, y compris la dÃĐclaration des variables, les fonctions, et l'affichage des donnÃĐes, ainsi que des applications pratiques avec des capteurs et des systÃĻmes d'entrÃĐe. Le support vise à enseigner aux ÃĐtudiants des concepts fondamentaux pour dÃĐvelopper des projets avec les microcontrÃīleurs PIC.Attacking ADFS Endpoints - DerbyCon
Attacking ADFS Endpoints - DerbyConKarl Fosaaen
Ėý
The document presents a detailed examination of attacks on Active Directory Federation Services (ADFS) using PowerShell, covering user enumeration, phishing, and dictionary attacks. It provides a comprehensive guide on setting up a test environment, identifying federated endpoints, and mitigation strategies to enhance security. Key insights include the importance of dual-factor authentication and monitoring of federated services to protect against common vulnerabilities.Automating Attacks Against Office365 - BsidesPDX 2016
Automating Attacks Against Office365 - BsidesPDX 2016Karl Fosaaen
Ėý
The document discusses methods for automating attacks on Office 365, including techniques for domain enumeration, user enumeration, credential brute forcing, and internal network pivoting. It also highlights various PowerShell scripts and tools that facilitate these attacks and outlines mitigations such as enabling dual-factor authentication and limiting federation to trusted domains. The presentation emphasizes the importance of monitoring endpoints and enforcing strong password requirements to reduce vulnerabilities.FreeCAD il cad 3D libero
FreeCAD il cad 3D liberoMarco Alici
Ėý
FreeCAD is an open-source 3D CAD application that is free, modular, and multiplatform. It uses Open CASCADE for modeling geometry and Coin3D + Qt + Python for visualization. FreeCAD's modular architecture allows it to be highly customizable and its multiplatform support means it can run on Linux, Windows, and Mac.Similar to Malicious MDM - Secure360 (20)
iOS enterprise
iOS enterprisedominion
Ėý
This document provides an overview of using iOS devices in the enterprise. It discusses why IT needs to be engaged with mobile device management as employees increasingly use iOS devices. It covers using IBM Lotus Traveler with iOS, iOS enterprise capabilities including configuration profiles, and over-the-air deployment and mobile device management (MDM) to securely manage iOS devices. The presentation includes demos of an MDM solution to illustrate how devices can be enrolled and managed remotely.UKLUG 2011 - iOS devices in the enterprise
UKLUG 2011 - iOS devices in the enterpriseRenÃĐ Winkelmeyer
Ėý
The presentation by RenÃĐ Winkelmeyer discusses the integration of iOS devices in enterprise environments, focusing on their management via IBM Lotus Traveler and mobile device management (MDM). It emphasizes the need for proper configuration, security measures, and over-the-air deployment to ensure effective usage of iOS devices in businesses. The conclusion highlights that while iOS devices are capable for enterprise use, robust device management is essential for a secure and productive experience.WSO2Con Asia 2014 - Embracing BYOD Trend Without Compromising Security, Emplo...
WSO2Con Asia 2014 - Embracing BYOD Trend Without Compromising Security, Emplo...WSO2
Ėý
WSO2 EMM is a mobile enterprise management solution that allows organizations to embrace BYOD trends while maintaining security, privacy, and user experience. It addresses challenges of mobility through features like mobile device management, a managed enterprise app store, and mobile app management. The presentation discusses different approaches to data security including MDM, separating personal and work environments, and MAM. MAM is highlighted as a best approach for controlling app behavior through SDKs or app wrapping while still providing a native user experience. WSO2 EMM provides all these capabilities in a unified solution to enable secure enterprise mobility.WSO2Con Asia 2014 - Embracing BYOD Trend Without Compromising Security, Emplo...
WSO2Con Asia 2014 - Embracing BYOD Trend Without Compromising Security, Emplo...WSO2
Ėý
WSO2 EMM is a mobile enterprise management solution that allows organizations to embrace BYOD trends while maintaining security, privacy, and user experience. It addresses challenges of mobility through features like mobile device management, a managed enterprise app store, and mobile app management. The presentation discusses different approaches to data security including MDM, separating personal and work environments, and MAM. MAM is highlighted as a best approach for controlling app behavior through SDKs or app wrapping while still providing a native user experience. WSO2 EMM provides all these capabilities in a unified solution to enable secure enterprise mobility.WSO2Con USA 2015: Connected Device Management for Enterprise Mobility and Beyond
WSO2Con USA 2015: Connected Device Management for Enterprise Mobility and BeyondWSO2
Ėý
The document outlines a framework for enterprise mobility and connected device management, emphasizing the need for robust data security measures in managing various mobile devices such as smartphones, tablets, and IoT. It details the challenges and risks associated with data security, including possible data leaks and device theft, and provides an overview of the functionalities and features of WSO2's enterprise mobility management platform. Additionally, it covers management capabilities for different operating systems like iOS, Android, and Windows, focusing on device management and application development.Wso2 con byod-shan-ppt
Wso2 con byod-shan-pptWSO2
Ėý
The document discusses embracing BYOD trends in enterprises while maintaining security, privacy and user experience. It outlines challenges like data security and different approaches like mobile device management (MDM), mobile application management (MAM) and separating enterprise and personal data. WSO2 Enterprise Mobility Manager is introduced as a solution that provides MDM, an enterprise app store, and mobile application management features to address BYOD challenges.DeepSec_2019_Chemerkin_Yury_-_Full_-_Final.pdf
DeepSec_2019_Chemerkin_Yury_-_Full_-_Final.pdfYury Chemerkin
Ėý
Yury Chemerkin is a seasoned multi-skilled security expert with over 10 years of experience in information security, focusing on areas such as privacy, compliance, and forensics. He highlights the significance of password management and the vulnerabilities associated with user credential storage systems, especially in mobile and cloud computing contexts. The document emphasizes various aspects of data leakage, forensics capabilities, and the management of interconnected accounts and their security risks.WSO2 Enterprise Mobility Manager - 2.0
WSO2 Enterprise Mobility Manager - 2.0Dilshan Edirisuriya
Ėý
WSO2 Enterprise Mobility Manager (EMM) allows organizations to securely manage mobile devices and apps. It addresses key challenges of data security, remote device management, and mobile application development. The EMM uses the Connected Device Management Framework (CDMF) for device, application, policy and other management functions. It supports features like device enrollment, policy enforcement, app distribution, and security controls on iOS, Android and Windows platforms to help organizations securely enable mobility.WSO2Con Asia 2014 - Embracing BYOD Trend Without Compromising Security, Emplo...
WSO2Con Asia 2014 - Embracing BYOD Trend Without Compromising Security, Emplo...WSO2
Ėý
This document discusses approaches to embracing bring your own device (BYOD) trends in enterprises without compromising security, employee privacy, or the mobile experience. It outlines challenges with enterprise mobility including data security, remote device management, and application development. Approaches to data security include mobile device management, separating enterprise apps and data from personal data, and mobile application management. Mobile application management provides a better user experience and privacy while controlling app behavior through SDKs, app wrapping, and policies. The document also summarizes features of the WSO2 Enterprise Mobility Manager for mobile device management, an enterprise app store, and mobile application management.WSO2Con Asia 2014 - ïŋž Embracing BYOD Trend Without Compromising Security, Emp...
WSO2Con Asia 2014 - ïŋž Embracing BYOD Trend Without Compromising Security, Emp...WSO2
Ėý
This document discusses approaches to embracing bring your own device (BYOD) trends in enterprises without compromising security, employee privacy, or the mobile experience. It outlines challenges with enterprise mobility including data security, remote device management, and application development. Approaches to data security include mobile device management, separating enterprise apps and data from personal data, and mobile application management. Mobile application management provides a better user experience and privacy while controlling app behavior through SDKs, app wrapping, and policies. The document also summarizes features of the WSO2 Enterprise Mobility Manager for mobile device management, an enterprise app store, and mobile application management.OWASP Top 10 for Mobile
OWASP Top 10 for MobileAppvigil - Mobile App Security Scanner
Ėý
The document summarizes a recap of the OWASP Mobile App Security Meet, outlining key aspects of mobile app security, including its history, the essential top 10 security issues, and best practices. It emphasizes the importance of securing sensitive data, preventing data leakage, addressing client-side vulnerabilities, and enforcing robust server-side controls. Additionally, it highlights the need for developers to adhere to OWASP guidelines for ensuring mobile application security.Can You Steal From Me Now? Mobile and BYOD Security Risks
Can You Steal From Me Now? Mobile and BYOD Security RisksMichael Davis
Ėý
Mobile devices and BYOD policies introduce significant security risks to organizations. The proliferation of mobile devices has led to new threats like activity monitoring, unauthorized payments, and exfiltration of sensitive data. Many mobile applications also put users' private data at risk through unsafe data practices and potential impersonation attacks. To help address these issues, user education is important, and organizations need strong mobile privacy and document access controls.Smartphones
SmartphonesSaeed Slemy
Ėý
This document provides an overview of smart phones and how to configure internet access on different operating systems. It discusses the evolution of smart phones from early mobile phones used in World War II to today's advanced devices. It then explains how to set up internet access on Android, iOS, Windows Phone, and Symbian operating systems by accessing settings menus and configuring APN settings with the mobile network name "internet". The document aims to help users set up internet access on their smart phones.Tablets, Apps and Cybersecurity
Tablets, Apps and CybersecurityOpen University and others
Ėý
The document outlines tablet familiarization and essential applications, covering setup, cybersecurity, photography, communication, and potential productivity tools. It emphasizes the importance of cyber security, social media usage, and privacy concerns, while also providing practical guidance on using social networking effectively both at work and in personal life. Additionally, it offers insights into various apps for photography, communication, and productivity for users to enhance their tablet experience.Harbin clinic iot-mobile-no-vid
Harbin clinic iot-mobile-no-vidErnest Staats
Ėý
The document provides tips for securing your digital footprint and privacy online. It discusses securing social media accounts, using strong and unique passwords, deleting personal information from search engines, enabling two-factor authentication, using secure browsers and VPNs, being wary of sharing personal information publicly, and understanding the risks of a large digital shadow and footprint online. It also covers tips for securing mobile devices, IoT devices, and protecting privacy when traveling across borders.WSO2Con US 2013 - Achieving Safe BYOD and Productive Apps with WSO2 Mobile De...
WSO2Con US 2013 - Achieving Safe BYOD and Productive Apps with WSO2 Mobile De...WSO2
Ėý
1) The document discusses how organizations can achieve safe BYOD (Bring Your Own Device) programs and productive mobile apps using WSO2Mobile MDM and MAM.
2) It explains that WSO2Mobile MDM allows enforcing policies like device restrictions, authentication, blocking compromised devices, and BYOD policies to ensure security.
3) It also discusses how WSO2Mobile MAM provides an enterprise app store, publisher, and management console to easily provision apps to employees' devices and apply policies.Cyber Security Seminar
Cyber Security SeminarJeremy Quadri
Ėý
The document outlines a cybersecurity conference organized by Quadri Consulting Ltd, with key topics including the rise of cyberattacks and the importance of data protection. It provides statistics on data breaches, highlights common misconceptions about cybersecurity, and offers practical tips for protecting personal and business data. Additionally, it emphasizes the need for continuous education, vigilance against social engineering, and the implementation of robust security measures.CIS13: Managing Mobility with Identity Standards
CIS13: Managing Mobility with Identity StandardsCloudIDSummit
Ėý
The document discusses various device management strategies (BYOD, CYOD) and their implications on data security and employee privacy, emphasizing the importance of context in applying controls. It explains the distinctions between Mobile Device Management (MDM), Mobile Application Management (MAM), and Mobile Information Management (MIM), focusing on how they interact with user identities and data policies. Additionally, it underscores the significance of identity standards in enabling a dual persona approach to balance security and personal usage effectively.CIS14: Mobilize Your Workforce with Secure Identity Services
CIS14: Mobilize Your Workforce with Secure Identity ServicesCloudIDSummit
Ėý
The document discusses the challenges and solutions for secure identity services in mobile and cloud applications, emphasizing the importance of a single sign-on (SSO) for enterprise users. It highlights issues related to bring your own device (BYOD) policies, such as password fatigue and the risks of data exposure, while proposing solutions like federated identity and application containerization to enhance security. Best practices for mobile enterprise SSO are also outlined, advocating for simplified user experiences and improved authentication processes.Mobile Device Mismanagement
Mobile Device Mismanagementbreenmachine
Ėý
This document discusses vulnerabilities found in mobile device management (MDM) solutions. It begins with background on the growing MDM market and how the research started from vulnerabilities discovered during a penetration test. The research found issues in how MDM solutions implemented the iOS MDM API, including lack of encryption, token issues, and flaws in signature validation. This could allow impersonation of users, denial of service attacks, intercepting sensitive data, and more. The document warns that MDM solutions can increase security risks if not implemented carefully, and that vendors and users must prioritize security practices like penetration testing, secure development, and monitoring.Ad
Malicious MDM - Secure360
- 1. iOS users - Scan to Connect to the Secure360 Wireless Network* (Open the URL in Safari) *Not Really
- 2. Malicious MDM: Fun with iOS MobileConfigs Karl Fosaaen
- 3. Introductions âĒ Who am I? âKarl Fosaaen âĒ What do I do? âPen Testing âPassword Cracking âSocial Engineering âBlogging âPinball Repair
- 4. Malicious MDM âĒ Overview âIntro âWhat is MDM? âTry This at Home! âMalicious Techniques âDemo âConclusion
- 5. Malicious MDM âĒ What is MDM? Mobile Device Management Any platform that can be used to manage mobile devices
- 6. Malicious MDM âĒ What can it do? âSet Password/lock requirements âAutomate email account setup âVPN settings âApplication Push âRemote Wipe âGeotracking ÂŊ_(ã)_/ÂŊ
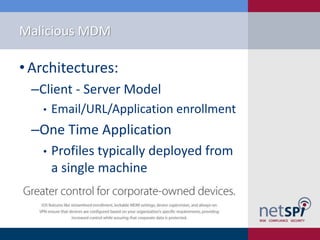
- 7. Malicious MDM âĒ Architectures: âClient - Server Model âĒ Email/URL/Application enrollment âOne Time Application âĒ Profiles typically deployed from a single machine
- 9. Malicious MDM Try This at Home!
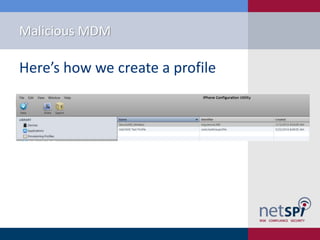
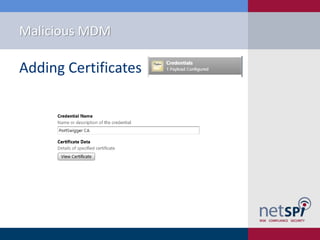
- 10. Malicious MDM Hereâs how we create a profile
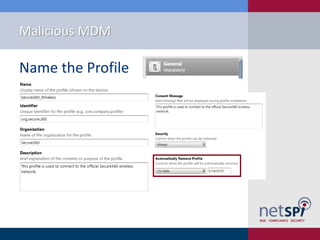
- 11. Malicious MDM Name the Profile
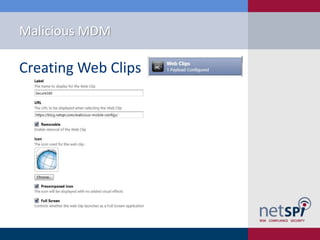
- 14. Malicious MDM Creating Web Clips
- 18. Malicious MDM âĒ Malicious Techniques âDirect USB Connection âiPhone Configuration Utility âRequires Unlocked Device
- 19. Malicious MDM âĒ Malicious Techniques ââJuice Jackingâ
- 20. Malicious MDM âĒ Malicious Techniques âWebsite deployment âĒ Direct .mobileconfig link âĒ XSS targeting iOS users âĒ Malicious Ad Servers
- 21. Malicious MDM âĒ Malicious Techniques âWebsite deployment âĒ QR code links
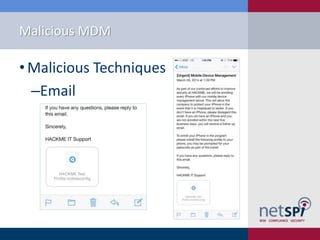
- 22. Malicious MDM âĒ Malicious Techniques âEmail
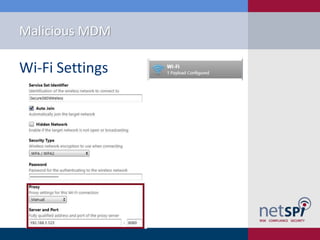
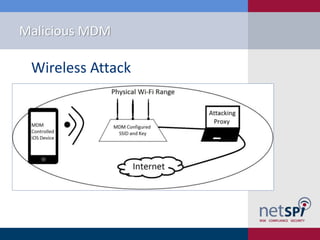
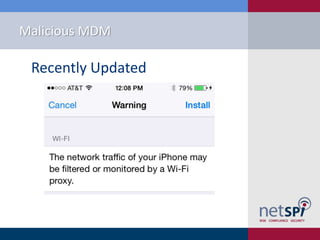
- 24. Malicious MDM âĒ Post Deployment Exploitation âWireless Attack âĒ Set Default SSID âĒ Set SSL Root Certificates âĒ Set Default Proxy âĒ Capture Creds âVPN Attack
- 28. Malicious MDM âĒ Post Deployment Exploitation âApplication Attacks âĒ Custom Applications âĒ Web Clips âMore Credential Grabbing
- 29. Malicious MDM âĒ Installed âAąčąčąôūąģĶēđģŲūąīĮēÔâ
- 30. Malicious MDM âĒ Post Deployment Exploitation âSo you have credentialsâĶ âĒ Single Factor VPN (PPTP) âĒ Internet facing authentication
- 31. Malicious MDM âĒ Installed âAąčąčąôūąģĶēđģŲūąīĮēÔâ âInvisible Applications âPush with MDM ââVOIPâ application âĒ Access to the microphone âĒ Always runningâĶ
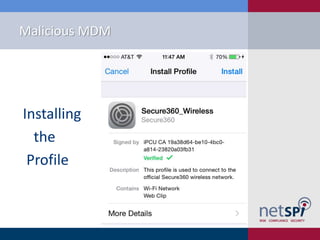
- 33. Malicious MDM Scan to Connect to the Secure360 Wireless Network* *Not Really
- 34. Malicious MDM
- 35. Malicious MDM
- 36. Malicious MDM âĒ Preventions âStart with clean phones, then add to the MDM âPrevent users from installing other MDM profiles âAdd devices to the MDM before an attacker does it for you âDonât plug into USB ports that you donât own
