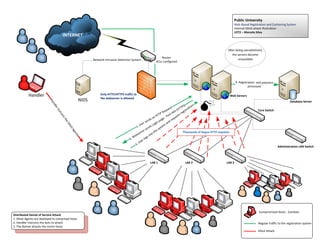
DDoS Attack illustration
- 1. Public University Web-Based Registration and Cashiering System Internal DDoS attack Illustration LOT2 ŌĆō Marcelo Silva INTERNET After being overwhelmed, the servers become Router unavailable Network Intrusion Detection System ACLs configured 4. Registration and payment processed Handler Only HTTP/HTTPS traffic to Web Servers the webserver is allowed NIDS Ha Database Server nd S) ion TP ler st t ue (HT istra Core Switch In eq 3 44 s reg PR str HT T ort est uc an -P ts ge u ds req th n pa r se in nd e se Log a DD 1. U ds tem oS sen sys ver he Ag ot Thousands of bogus HTTP requests ser en eb int ts 2. W gs r lo se 3 .U Administration LAN Switch LAB 1 LAB 2 LAB 3 Compromised Hosts - Zombies Distributed Denial of Service Attack 1. DDoS Agents are deployed to comprised hosts 2. Handler instructs the bots to attack Regular traffic to the registration system 3. The Botnet attacks the victim hosts DDoS Attack