2013 - Mark story - Avoiding the Owasp
- 1. AVOIDING THE OWASP Top 10 security exploits Saturday, 5 October, 13
- 2. ME Illustrator turned developer PHP developer for 8 years Architect/Developer at FreshBooks Lead developer of CakePHP Saturday, 5 October, 13
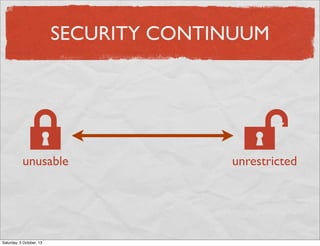
- 4. SECURITY CONTINUUM ( unusable Saturday, 5 October, 13 ) unrestricted
- 5. OWASP Open Web Application Security Project Saturday, 5 October, 13
- 6. OWASP TOP 10 Saturday, 5 October, 13
- 7. 1 INJECTION Saturday, 5 October, 13 ‘ OR 1=1 ‘--
- 8. RISKS Command - Permits arbitrary shell commands. SQL - Permits query manipulation, and arbitrary SQL. Bad guys can run arbitrary code/queries. Saturday, 5 October, 13
- 9. SQL INJECTION EXAMPLE $username = $_POST[‘username’]; $password = $_POST[‘password’]; $query = “SELECT * FROM user WHERE username = ‘$username’ AND password = ‘$password’”; $user = $db->query($query); Saturday, 5 October, 13
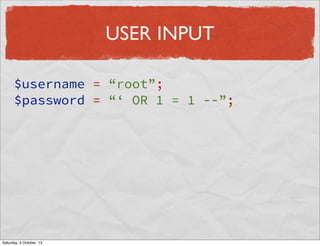
- 10. USER INPUT $username = “root”; $password = “‘ OR 1 = 1 --”; Saturday, 5 October, 13
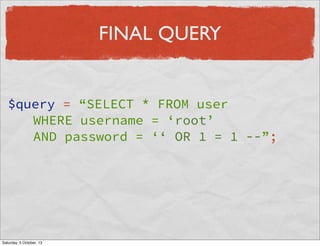
- 11. FINAL QUERY $query = “SELECT * FROM user WHERE username = ‘root’ AND password = ‘‘ OR 1 = 1 --”; Saturday, 5 October, 13
- 12. FINAL QUERY $query = “SELECT * FROM user WHERE username = ‘root’ AND password = ‘‘ OR 1 = 1 --”; Saturday, 5 October, 13
- 13. PREVENTION Use an ORM or Database abstraction layer that provides escaping. Doctrine, ZendTable, and CakePHP all do this. Use PDO and prepared statements. Never interpolate user data into a query. Never use regular expressions, magic quotes, or addslashes() Saturday, 5 October, 13
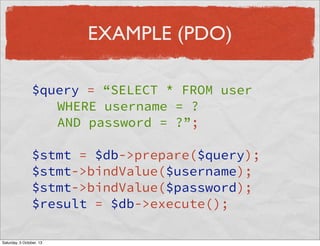
- 14. EXAMPLE (PDO) $query = “SELECT * FROM user WHERE username = ? AND password = ?”; $stmt = $db->prepare($query); $stmt->bindValue($username); $stmt->bindValue($password); $result = $db->execute(); Saturday, 5 October, 13
- 15. COMMAND INJECTION $file = $_POST[‘file’]; $res = file_get_contents($file); echo $res; Saturday, 5 October, 13
- 16. USER INPUT $f = “../../../../../../etc/passwd”; Saturday, 5 October, 13
- 17. PREVENTION Escape and validate input. Check for .. Check for ; Ensure the realpath resolves to a file that is allowed. Saturday, 5 October, 13
- 18. 2 BROKEN AUTHENTICATION & SESSION MANAGEMENT /index.php?PHPSESSID=pwned Saturday, 5 October, 13
- 19. RISKS Identity theft. Firesheep was an excellent example. Saturday, 5 October, 13
- 20. SESSION FIXATION EXAMPLE <?php session_start(); if (isset($_GET[‘sessionid’]) { session_id($_GET[‘sessionid’]); } Saturday, 5 October, 13
- 21. SESSION FIXATION EXAMPLE <?php session_start(); if (isset($_GET[‘sessionid’]) { session_id($_GET[‘sessionid’]); } Saturday, 5 October, 13
- 22. PREVENTION Rotate session identifiers upon login/logout Set the HttpOnly flag on session cookies. Use well tested / mature libraries for authentication. SSL is always a good idea. Saturday, 5 October, 13
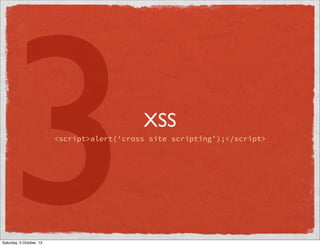
- 23. 3 XSS <script>alert(‘cross site scripting’);</script> Saturday, 5 October, 13
- 24. RISKS Allows bad guys to do things as the person viewing a page. Steal identities, passwords, credit cards, hijack pages and more. Saturday, 5 October, 13
- 25. XSS EXAMPLE <p> <?php echo $user[‘bio’]; ?> </p> Saturday, 5 October, 13
- 26. XSS EXAMPLE <p> <?php echo $user[‘bio’]; ?> </p> Saturday, 5 October, 13
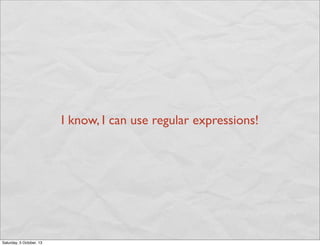
- 27. I know, I can use regular expressions! Saturday, 5 October, 13
- 28. NO Saturday, 5 October, 13
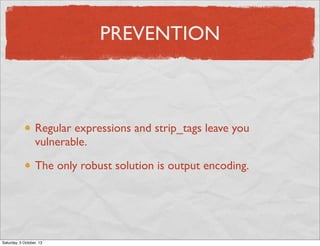
- 29. PREVENTION Regular expressions and strip_tags leave you vulnerable. The only robust solution is output encoding. Saturday, 5 October, 13
- 30. EXAMPLE <p> <?php echo htmlentities( $user[‘bio’], ENT_QUOTES, ‘UTF-8’ ); ?> </p> Saturday, 5 October, 13
- 31. DANGERS Manually encoding is error prone, and you will make a mistake. Using a template library like Twig that provides autoescaping reduces the chances of screwing up. Encoding is dependent on context. Saturday, 5 October, 13
- 32. 4 INSECURE DIRECT OBJECT REFERENCE Saturday, 5 October, 13
- 33. RISKS Bad guys can access information they shouldn’t Bad guys can modify data they shouldn’t. Saturday, 5 October, 13
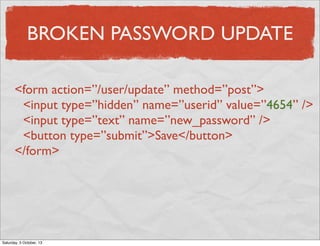
- 34. BROKEN PASSWORD UPDATE <form action=”/user/update” method=”post”> <input type=”hidden” name=”userid” value=”4654” /> <input type=”text” name=”new_password” /> <button type=”submit”>Save</button> </form> Saturday, 5 October, 13
- 35. PREVENTION Remember hidden inputs are not really hidden, and can be changed by users. Validate access to all things, don’t depend on things being hidden/invisible. If you need to refer to the current user, use session data not form inputs. Whitelist properties any form can update. Saturday, 5 October, 13
- 37. RISKS Default settings can be insecure, and intended for development not production. Attackers can use misconfigured software to gain knowledge and access. Saturday, 5 October, 13
- 38. PREVENTION Know the tools you use, and configure them correctly. Keep up to date on vulnerabilities in the tools you use. Remove/disable any services/features you aren’t using. Saturday, 5 October, 13
- 39. 6 SENSITIVE DATA EXPOSURE 4012 8888 8888 1881 Saturday, 5 October, 13
- 40. RISKS Bad guys get credit cards, personal identification, passwords or health records. Your company could be fined or worse. Saturday, 5 October, 13
- 41. ASSESSING RISK Do you have sensitive data? Is it in plaintext? Any old/bad crypto in use? Missing SSL? Who can access sensitive data? Saturday, 5 October, 13
- 42. 7 MISSING FUNCTION LEVEL ACCESS CONTROL Saturday, 5 October, 13
- 43. RISKS Anyone on the internet can request things. Missing access control could mean bad guys can do things they shouldn’t be able to. Saturday, 5 October, 13
- 44. PREVENTION No simple solutions sadly. Good automated tests help. Saturday, 5 October, 13
- 45. 8 CROSS SITE REQUEST FORGERY Saturday, 5 October, 13 (CSRF)
- 46. RISKS Evil websites can perform actions for users logged into your site. Side effects on GET can be performed via images or CSS files. Remember the Gmail contact hack. Saturday, 5 October, 13
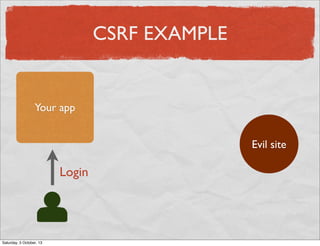
- 47. CSRF EXAMPLE Your app Evil site Saturday, 5 October, 13
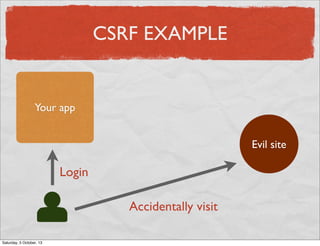
- 48. CSRF EXAMPLE Your app Evil site Login Saturday, 5 October, 13
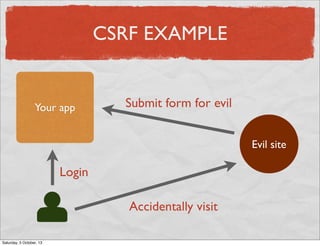
- 49. CSRF EXAMPLE Your app Evil site Login Accidentally visit Saturday, 5 October, 13
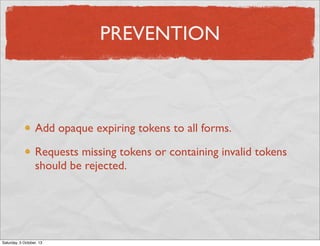
- 50. CSRF EXAMPLE Your app Submit form for evil Evil site Login Accidentally visit Saturday, 5 October, 13
- 51. PREVENTION Add opaque expiring tokens to all forms. Requests missing tokens or containing invalid tokens should be rejected. Saturday, 5 October, 13
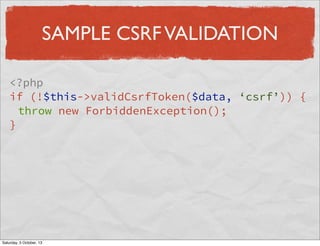
- 52. SAMPLE CSRF VALIDATION <?php if (!$this->validCsrfToken($data, ‘csrf’)) { throw new ForbiddenException(); } Saturday, 5 October, 13
- 53. 9 USING COMPONENTS WITH KNOWN VULNERABILITIES Saturday, 5 October, 13 CVE bingo
- 54. RISK Using old busted software can expose you to documented issues. CVE databases are filled with version numbers and matching exploits. Saturday, 5 October, 13
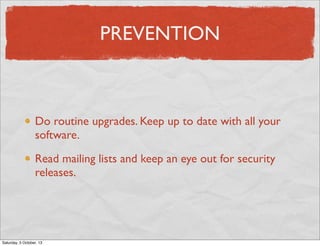
- 55. PREVENTION Do routine upgrades. Keep up to date with all your software. Read mailing lists and keep an eye out for security releases. Saturday, 5 October, 13
- 56. PREVENTION Several vulnerability databases around. https://cve.mitre.org/cve/ Saturday, 5 October, 13
- 57. 10 UNVALIDATED REDIRECTS & FORWARDS Saturday, 5 October, 13
- 58. RISKS Trusting user input for redirects opens phishing attacks. Breach of trust with your users. Saturday, 5 October, 13
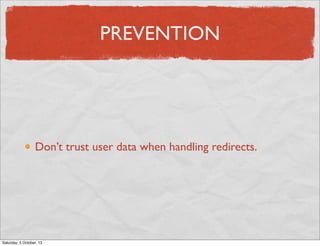
- 59. PREVENTION Don’t trust user data when handling redirects. Saturday, 5 October, 13
- 60. THANK YOU Saturday, 5 October, 13








![SQL INJECTION EXAMPLE
$username = $_POST[‘username’];
$password = $_POST[‘password’];
$query = “SELECT * FROM user
WHERE username = ‘$username’
AND password = ‘$password’”;
$user = $db->query($query);
Saturday, 5 October, 13](https://image.slidesharecdn.com/markstory-avoidingtheowasp-140129054743-phpapp01/85/2013-Mark-story-Avoiding-the-Owasp-9-320.jpg)

![COMMAND INJECTION
$file = $_POST[‘file’];
$res = file_get_contents($file);
echo $res;
Saturday, 5 October, 13](https://image.slidesharecdn.com/markstory-avoidingtheowasp-140129054743-phpapp01/85/2013-Mark-story-Avoiding-the-Owasp-15-320.jpg)




![SESSION FIXATION EXAMPLE
<?php
session_start();
if (isset($_GET[‘sessionid’]) {
session_id($_GET[‘sessionid’]);
}
Saturday, 5 October, 13](https://image.slidesharecdn.com/markstory-avoidingtheowasp-140129054743-phpapp01/85/2013-Mark-story-Avoiding-the-Owasp-20-320.jpg)
![SESSION FIXATION EXAMPLE
<?php
session_start();
if (isset($_GET[‘sessionid’]) {
session_id($_GET[‘sessionid’]);
}
Saturday, 5 October, 13](https://image.slidesharecdn.com/markstory-avoidingtheowasp-140129054743-phpapp01/85/2013-Mark-story-Avoiding-the-Owasp-21-320.jpg)


![XSS EXAMPLE
<p>
<?php echo $user[‘bio’]; ?>
</p>
Saturday, 5 October, 13](https://image.slidesharecdn.com/markstory-avoidingtheowasp-140129054743-phpapp01/85/2013-Mark-story-Avoiding-the-Owasp-25-320.jpg)
![XSS EXAMPLE
<p>
<?php echo $user[‘bio’]; ?>
</p>
Saturday, 5 October, 13](https://image.slidesharecdn.com/markstory-avoidingtheowasp-140129054743-phpapp01/85/2013-Mark-story-Avoiding-the-Owasp-26-320.jpg)

![EXAMPLE
<p>
<?php echo htmlentities(
$user[‘bio’],
ENT_QUOTES,
‘UTF-8’
); ?>
</p>
Saturday, 5 October, 13](https://image.slidesharecdn.com/markstory-avoidingtheowasp-140129054743-phpapp01/85/2013-Mark-story-Avoiding-the-Owasp-30-320.jpg)