Mastering Network HackingFU - idsecconf2008
1 like708 views
Dokumen ini membahas tantangan keamanan pada protokol TCP/IP yang berusia 30 tahun dan berbagai teknik hacking seperti tunneling, spoofing, dan DDoS yang sering dieksploitasi. Selain itu, dijelaskan tentang alat dan teknik untuk melindungi jaringan, seperti ARP wall dan SSH tunneling, serta pentingnya enkripsi dan verifikasi. Meskipun ada rencana untuk beralih ke IPv6 untuk meningkatkan keamanan, adopsinya masih terbatas karena alasan politis dan bisnis.
1 of 18
Downloaded 79 times





![Bertahan dengan Unix
ŌĆó Paper Baca di
http://www.slideshare.net/y3dips/arpwall-protect-from-arp-spoofing/
ŌĆó ARPWatch ,Swatch, PyGTK (alert.py)
ARPWALL
ŌŚÅ Arp ŌĆōs [ip] [mac]
http://code.google.com/p/arpwall/ Wanna help ?
Mastering the Network HackingFU ŌĆō y3dips](https://image.slidesharecdn.com/net-idsecconf2008-100814111233-phpapp02/85/Mastering-Network-HackingFU-idsecconf2008-8-320.jpg)


![Perlengkapan
’ü¼ Python [kemampuan programming]
’ü¼ Scapy (pakcet Manipulating platform)
’ü¼ Spoofing
’ü¼ Sniffing (tcpdump only?)
’ü¼ Some l33t tools (THCAmapcrap)
Mastering the Network HackingFU ŌĆō y3dips](https://image.slidesharecdn.com/net-idsecconf2008-100814111233-phpapp02/85/Mastering-Network-HackingFU-idsecconf2008-12-320.jpg)




Recommended
Tugas pti
Tugas ptiagusriyanto1990
╠²
Dokumen tersebut membahas pentingnya keamanan jaringan komputer dan peran firewall dalam melindungi data dari pencurian. Firewall digunakan untuk menerapkan kebijakan keamanan dan mengurangi ancaman di internet sehingga pengguna dapat menjelajahi internet dengan lebih nyaman.Sistem deteksi intrusion berbasis jaringan
Sistem deteksi intrusion berbasis jaringanDuwinowo NT
╠²
Dokumen tersebut membahas tentang sistem deteksi intrusi berbasis jaringan yang digunakan untuk memantau jaringan berdasarkan gejala yang tidak normal dari serangan atau gangguan pada jaringan. Snort disebutkan sebagai contoh sistem deteksi intrusi jaringan yang ringan dan terbuka sumber.Powerpointku
PowerpointkuEuis Chealim
╠²
Dokumen ini membahas tentang pentingnya optimalisasi firewall pada jaringan besar untuk mengurangi ancaman dari internet, seperti virus dan serangan hacker. Penelitian ini menggunakan metode literatur untuk menyusun konfigurasi firewall yang efektif dan mencakup perangkat keras serta perangkat lunak yang dibutuhkan. Kesimpulan menunjukkan bahwa meskipun firewall tidak dapat memberikan perlindungan penuh, konfigurasi yang tepat dapat membantu mengamankan jaringan dan data dari ancaman.7 spread spectrum
7 spread spectrumUNTUNGSG
╠²
Dokumen ini membahas komunikasi spektrum tersebar, termasuk teknik DSSS dan FHSS, yang digunakan untuk meningkatkan transmisi sinyal dengan mengacak frekuensi dan menyebarkan informasi. DSSS mengandalkan kode sinyal untuk identifikasi pengguna dan memerlukan lebar pita yang lebih besar dari sinyal informasi, sementara FHSS melakukan loncatan frekuensi untuk menghindari gangguan, dengan Bluetooth sebagai salah satu contohnya. Teknologi ini meningkatkan keandalan komunikasi dan mendukung aplikasi seperti Wi-Fi dan perangkat mobile.Snort
SnortMunir Putra
╠²
Snort merupakan intrusion detection system (IDS) yang banyak digunakan untuk mendeteksi serangan jaringan. Snort memiliki tiga mode operasi yaitu sniffer, packet logger, dan intrusion detection. Laporan ini menjelaskan cara menginstal dan mengkonfigurasi Snort pada ketiga mode tersebut menggunakan MikroTik RouterBoard dan tiga interface jaringan.Keamanan jaringan
Keamanan jaringanShabrina Dewi
╠²
Dokumen tersebut membahas tentang konsep keamanan jaringan dan kejahatan internet. Secara singkat, dokumen tersebut menjelaskan tentang manfaat jaringan komputer, tantangan keamanan dalam jaringan, dan berbagai jenis serangan serta cara melindungi jaringan dari serangan tersebut seperti menggunakan enkripsi, firewall, dan kontrol akses. Dokumen tersebut juga membahas mengenai peningkatan kejahatan siber dan berbagai teknik kFirewall 2 nat
Firewall 2 natFajar Rohmawan
╠²
Dokumen ini membahas tentang konfigurasi firewall dengan menggunakan aturan NAT. Langkah-langkahnya adalah mengkonfigurasi host dan router Ubuntu sebagai firewall, lalu membuat aturan NAT menggunakan perintah iptables untuk menambahkan aturan MASQUERADE pada chain POSTROUTING. Kesimpulannya adalah chain POSTROUTING dan action MASQUERADE yang digunakan untuk membuat aturan NAT.backdooring workshop
backdooring workshopAmmar WK
╠²
Dokumen tersebut membahas tentang backdoor, yaitu metode untuk mem-bypass otentikasi dan keamanan akses secara remote ke suatu mesin tanpa batasan. Backdoor dapat berupa program yang diinstal, modifikasi program/file, berbasis aplikasi, atau program yang dijalankan seperti bindshell.Web Hacking (basic)
Web Hacking (basic)Ammar WK
╠²
Dokumen ini membahas berbagai jenis serangan terhadap aplikasi web, terutama cross site scripting (XSS) dan SQL injection. Penjelasan mencakup mekanisme serangan, contoh praktis, serta dampak potensial terhadap keamanan pengguna. Selain itu, dokumen juga menyarankan penggunaan aplikasi Damn Vulnerable Web Application (DVWA) untuk tujuan pembelajaran dan pengujian celah keamanan.password series
password seriesAmmar WK
╠²
Dokumen ini membahas berbagai metode untuk menyerang proses otentikasi sistem, dengan fokus pada penggunaan username dan password. Beberapa aplikasi yang disebutkan termasuk explore2fs, pwdump2, dan john the ripper. Selain itu, disinggung juga metode pasif untuk mendapatkan password tanpa melakukan tindakan langsung.Linux Exploit Research
Linux Exploit ResearchDan H
╠²
Dokumen ini adalah modul pelatihan tentang pengembangan kerentanan perangkat lunak, mencakup konsep dasar seperti buffer overflow, shellcode, dan teknik pengujian penetrasi menggunakan alat seperti Metasploit. Ini juga menjelaskan tentang register prosesor dan cara menulis kode untuk mengeksploitasi kerentanan. Tujuannya adalah untuk membantu peserta memahami cara eksploitasi bekerja dan meningkatkan keterampilan hacking mereka.Backtrack 5 - network pentest
Backtrack 5 - network pentestDan H
╠²
Dokumen ini merupakan panduan lengkap tentang pelatihan penggunaan Backtrack 5 untuk penetrasi keamanan jaringan. Berisi pengantar, instalasi, dasar penggunaan, metode pengumpulan informasi, penilaian kerentanan, dan teknik serangan. Selain itu, dokumen ini juga membahas tentang penggunaan berbagai alat keamanan yang tersedia dalam Backtrack.Backtrack 5 - web pentest
Backtrack 5 - web pentestDan H
╠²
Dokumen tersebut membahas tentang pelatihan penetrasi tes (penetration testing) menggunakan Backtrack 5. Pelatihan ini mencakup pengenalan Backtrack, instalasi dan konfigurasi Backtrack, teknik gathering informasi, penilaian kerentanan, eksploitasi web, serangan kata sandi, mempertahankan akses, dan eskalasi hak akses. Peserta diajak melakukan berbagai uji coba secara langsung di server target virtual dan membuat laporan hasil penetrasi mereka.Penetrasi Jaringan
Penetrasi JaringanDigital Echidna
╠²
The document outlines a presentation on network penetration testing, discussing both legal and illegal aspects. It details different types of penetration tests, methodologies, and tools used in the process, including information gathering, scanning, exploitation, and covering tracks. Additionally, it introduces the social engineering toolkit and its applications in client-side attacks.Ethical hacking
Ethical hackingKhairi Aiman
╠²
This document discusses ethical hacking and penetration testing. It provides an overview of the benefits of controlled penetration tests, the process involved, and some real-life case studies. It explains how penetration tests can identify vulnerabilities before they are exploited, help understand an organization's security environment, and serve as a preventative measure when vulnerabilities are remediated. The document outlines the general methodology for internal and external penetration tests, including reconnaissance, scanning, vulnerability analysis, and attempts to gain unauthorized access. Various tools used in the process are also described.Advanced Exploit Development (Updated on 28 January, 2016)
Advanced Exploit Development (Updated on 28 January, 2016)Dan H
╠²
Ringkasan dokumen tersebut adalah:
1. Dokumen tersebut merupakan modul pelatihan exploit development yang mencakup berbagai topik seperti stack overflow, bypassing structured exception handling, bypassing data exception prevention, dan lainnya.
2. Pelatihan akan membahas cara mencari celah keamanan, membuat, dan mengembangkan exploit.
3. Contoh kasus yang digunakan adalah celah stack overflow pada Free Float FTP server dan cara mengeksploitasi celah tersebut."Workshop 101 - Penetration testing & Vulnerability assessment system
Workshop 101 - Penetration testing & Vulnerability assessment systemDan H
╠²
Dokumen ini adalah panduan tentang pengujian penetrasi dan penilaian kerentanan dalam keamanan sistem, membahas metodologi yang harus diikuti, serta jenis-jenis kerentanan yang umum ditemukan. Terdapat juga penjelasan mengenai OWASP dan sepuluh celah teratas dalam keamanan aplikasi. Penekanan diberikan pada pentingnya persetujuan legal sebelum melakukan pengujian dan tanggung jawab etis dari para tester.Seminar Hacking & Security Analysis
Seminar Hacking & Security AnalysisDan H
╠²
The document discusses hacking and information security analysis. It covers various hacking techniques like cyber spying, fraud/forgery, and illegal access. It then discusses common vulnerabilities like buffer overflows, SQL injections, and cross-site scripting attacks. The document provides examples of stack-based buffer overflows and how they can be exploited to hijack a program's execution flow and potentially execute arbitrary code. It also discusses mitigation techniques used by modern operating systems and counter-techniques employed by hackers.Layer 7 denial of services attack mitigation
Layer 7 denial of services attack mitigationAmmar WK
╠²
This document discusses layer 7 denial of service attacks and mitigation techniques. It describes how layer 7 attacks target application layer protocols like HTTP and FTP to overwhelm servers. The document then provides an example of an HTTP flood attack against a website and the steps taken to analyze logs and implement mitigation like rate limiting, timeouts, and firewall rules. Effective mitigation requires identifying attacks, hardening servers, and contacting authorities.Pentesting with linux
Pentesting with linuxHammad Ahmed Khawaja
╠²
This document discusses penetration testing and the Metasploit framework. It defines penetration testing as evaluating a system's security using malicious techniques to identify vulnerabilities. Metasploit is an open-source framework for penetration testing that contains exploits, payloads, and modules. It can be used to test applications, operating systems, and web applications for vulnerabilities. The document provides examples of commands in msfconsole like 'use exploit' and 'set payload' to launch attacks using Metasploit.Debian Packaging tutorial
Debian Packaging tutorialnussbauml
╠²
This document is a comprehensive tutorial on Debian packaging, aiming to guide users in modifying existing packages and creating their own. It covers key topics like creating and maintaining source packages, tools required for packaging, and practical sessions for hands-on experience. The tutorial emphasizes the essential nature of Debian in free software distribution and outlines the workflow for building packages using .deb files.Had sec mikrotik administrator
Had sec mikrotik administratormuhammad pailus
╠²
Dokumen tersebut merupakan daftar bab dan objektif pelatihan HadSec Mikrotik Administrator yang meliputi pengenalan Mikrotik, konfigurasi dasar Mikrotik melalui Winbox, telnet, webfig, konfigurasi interface, firewall, web proxy, dan jaringan nirkabel beserta konfigurasinya. Pelatihan ini bertujuan membekali peserta dengan pengetahuan dan keterampilan dasar mengkonfigurasi dan memonitor jaringan Mikrotik skala kecil hingga menengah.Connect your Javascript web app to ownCloud over the WebDAV interface
Connect your Javascript web app to ownCloud over the WebDAV interface Ilian Sapundshiev
╠²
The document discusses the integration of a JavaScript web app, Tagspaces, with OwnCloud using the WebDAV interface. It covers the architecture of Tagspaces as a backendless offline application, the rationale for using OwnCloud, and outlines steps for creating an OwnCloud app for enhanced integration. The presentation highlights the need for features like search integration and user management in future development.bluetooth [in]security
bluetooth [in]securityAmmar WK
╠²
Bluetooth adalah teknologi pengganti kabel yang efisien dan murah digunakan untuk menghubungkan berbagai perangkat seperti headset, ponsel, dan komputer. Meskipun praktis, fitur keamanannya masih lemah, dengan potensi ancaman seperti pencurian data dan pemalsuan identitas. Kesadaran pengguna terhadap risiko keamanan ini juga masih rendah.webhacking
webhackingAmmar WK
╠²
Dokumen ini membahas mengenai simulasi ancaman peretasan web yang terjadi melalui protokol HTTP, serta cara memanfaatkan kelemahan aplikasi web dan browser. Juga dijelaskan tentang penggunaan berbagai metode HTTP untuk menyerang aplikasi web. Penelitian tersebut menyoroti perlunya langkah-langkah keamanan dalam aplikasi web untuk mencegah serangan tersebut.eMAPT
eMAPTAndrii Holovchenko
╠²
The document discusses a recommendation from Armandoromeo, the CEO and lead instructor at elearnsecurity, for 40 Continuing Professional Education (CPE) credits. It certifies the release of Emapt version 1.0 on November 25, 2015, and mentions Andrii Holovchenko in relation to the certification.Playin with Password
Playin with PasswordAmmar WK
╠²
The document discusses various methods for cracking passwords, including tools for cracking Windows and Linux passwords like John the Ripper. It also covers passive techniques for obtaining passwords like keyloggers, bugs in applications, and sniffing plaintext protocols. The document recommends ways to improve password security such as using strong passphrases, encryption, firewalls, and keeping systems updated.Exploit Development with Python
Exploit Development with PythonThomas Gregory
╠²
The document outlines various techniques for exploit development using Python, including stack buffer overflow, structured exception handling (SEH), and evasive shellcode techniques like egghunter. It details memory layout, how stack growth occurs, and protections against SEH exploitation, such as DEP and SafeSEH. Additionally, it provides skeleton code for different exploit scenarios demonstrating the exploitation process.Pertemuan 8
Pertemuan 8Agung Mzl
╠²
Dokumen ini membahas berbagai contoh eksploitasi lubang keamanan, termasuk teknik serangan seperti denial of service, sniffing, dan penggunaan trojan horse. Berbagai alat dan metode untuk mencari informasi serta melakukan serangan dijelaskan secara rinci, termasuk penggunaan tools seperti whois, dig, dan tcpdump. Selain itu, dokumen juga memberikan wawasan tentang cara melindungi jaringan dari potensi ancaman ini.Network security
Network securitymho3yank
╠²
Dokumen tersebut membahas tentang keamanan jaringan, meliputi pengenalan serangan tipikal dan tahapan terjadinya serangan, serta alat-alat untuk melakukan pencarian keamanan jaringan seperti scanning dan probing. Dokumen tersebut juga membahas mengenai etika dalam melakukan hacking untuk kepentingan keamanan jaringan.More Related Content
Viewers also liked (20)
Web Hacking (basic)
Web Hacking (basic)Ammar WK
╠²
Dokumen ini membahas berbagai jenis serangan terhadap aplikasi web, terutama cross site scripting (XSS) dan SQL injection. Penjelasan mencakup mekanisme serangan, contoh praktis, serta dampak potensial terhadap keamanan pengguna. Selain itu, dokumen juga menyarankan penggunaan aplikasi Damn Vulnerable Web Application (DVWA) untuk tujuan pembelajaran dan pengujian celah keamanan.password series
password seriesAmmar WK
╠²
Dokumen ini membahas berbagai metode untuk menyerang proses otentikasi sistem, dengan fokus pada penggunaan username dan password. Beberapa aplikasi yang disebutkan termasuk explore2fs, pwdump2, dan john the ripper. Selain itu, disinggung juga metode pasif untuk mendapatkan password tanpa melakukan tindakan langsung.Linux Exploit Research
Linux Exploit ResearchDan H
╠²
Dokumen ini adalah modul pelatihan tentang pengembangan kerentanan perangkat lunak, mencakup konsep dasar seperti buffer overflow, shellcode, dan teknik pengujian penetrasi menggunakan alat seperti Metasploit. Ini juga menjelaskan tentang register prosesor dan cara menulis kode untuk mengeksploitasi kerentanan. Tujuannya adalah untuk membantu peserta memahami cara eksploitasi bekerja dan meningkatkan keterampilan hacking mereka.Backtrack 5 - network pentest
Backtrack 5 - network pentestDan H
╠²
Dokumen ini merupakan panduan lengkap tentang pelatihan penggunaan Backtrack 5 untuk penetrasi keamanan jaringan. Berisi pengantar, instalasi, dasar penggunaan, metode pengumpulan informasi, penilaian kerentanan, dan teknik serangan. Selain itu, dokumen ini juga membahas tentang penggunaan berbagai alat keamanan yang tersedia dalam Backtrack.Backtrack 5 - web pentest
Backtrack 5 - web pentestDan H
╠²
Dokumen tersebut membahas tentang pelatihan penetrasi tes (penetration testing) menggunakan Backtrack 5. Pelatihan ini mencakup pengenalan Backtrack, instalasi dan konfigurasi Backtrack, teknik gathering informasi, penilaian kerentanan, eksploitasi web, serangan kata sandi, mempertahankan akses, dan eskalasi hak akses. Peserta diajak melakukan berbagai uji coba secara langsung di server target virtual dan membuat laporan hasil penetrasi mereka.Penetrasi Jaringan
Penetrasi JaringanDigital Echidna
╠²
The document outlines a presentation on network penetration testing, discussing both legal and illegal aspects. It details different types of penetration tests, methodologies, and tools used in the process, including information gathering, scanning, exploitation, and covering tracks. Additionally, it introduces the social engineering toolkit and its applications in client-side attacks.Ethical hacking
Ethical hackingKhairi Aiman
╠²
This document discusses ethical hacking and penetration testing. It provides an overview of the benefits of controlled penetration tests, the process involved, and some real-life case studies. It explains how penetration tests can identify vulnerabilities before they are exploited, help understand an organization's security environment, and serve as a preventative measure when vulnerabilities are remediated. The document outlines the general methodology for internal and external penetration tests, including reconnaissance, scanning, vulnerability analysis, and attempts to gain unauthorized access. Various tools used in the process are also described.Advanced Exploit Development (Updated on 28 January, 2016)
Advanced Exploit Development (Updated on 28 January, 2016)Dan H
╠²
Ringkasan dokumen tersebut adalah:
1. Dokumen tersebut merupakan modul pelatihan exploit development yang mencakup berbagai topik seperti stack overflow, bypassing structured exception handling, bypassing data exception prevention, dan lainnya.
2. Pelatihan akan membahas cara mencari celah keamanan, membuat, dan mengembangkan exploit.
3. Contoh kasus yang digunakan adalah celah stack overflow pada Free Float FTP server dan cara mengeksploitasi celah tersebut."Workshop 101 - Penetration testing & Vulnerability assessment system
Workshop 101 - Penetration testing & Vulnerability assessment systemDan H
╠²
Dokumen ini adalah panduan tentang pengujian penetrasi dan penilaian kerentanan dalam keamanan sistem, membahas metodologi yang harus diikuti, serta jenis-jenis kerentanan yang umum ditemukan. Terdapat juga penjelasan mengenai OWASP dan sepuluh celah teratas dalam keamanan aplikasi. Penekanan diberikan pada pentingnya persetujuan legal sebelum melakukan pengujian dan tanggung jawab etis dari para tester.Seminar Hacking & Security Analysis
Seminar Hacking & Security AnalysisDan H
╠²
The document discusses hacking and information security analysis. It covers various hacking techniques like cyber spying, fraud/forgery, and illegal access. It then discusses common vulnerabilities like buffer overflows, SQL injections, and cross-site scripting attacks. The document provides examples of stack-based buffer overflows and how they can be exploited to hijack a program's execution flow and potentially execute arbitrary code. It also discusses mitigation techniques used by modern operating systems and counter-techniques employed by hackers.Layer 7 denial of services attack mitigation
Layer 7 denial of services attack mitigationAmmar WK
╠²
This document discusses layer 7 denial of service attacks and mitigation techniques. It describes how layer 7 attacks target application layer protocols like HTTP and FTP to overwhelm servers. The document then provides an example of an HTTP flood attack against a website and the steps taken to analyze logs and implement mitigation like rate limiting, timeouts, and firewall rules. Effective mitigation requires identifying attacks, hardening servers, and contacting authorities.Pentesting with linux
Pentesting with linuxHammad Ahmed Khawaja
╠²
This document discusses penetration testing and the Metasploit framework. It defines penetration testing as evaluating a system's security using malicious techniques to identify vulnerabilities. Metasploit is an open-source framework for penetration testing that contains exploits, payloads, and modules. It can be used to test applications, operating systems, and web applications for vulnerabilities. The document provides examples of commands in msfconsole like 'use exploit' and 'set payload' to launch attacks using Metasploit.Debian Packaging tutorial
Debian Packaging tutorialnussbauml
╠²
This document is a comprehensive tutorial on Debian packaging, aiming to guide users in modifying existing packages and creating their own. It covers key topics like creating and maintaining source packages, tools required for packaging, and practical sessions for hands-on experience. The tutorial emphasizes the essential nature of Debian in free software distribution and outlines the workflow for building packages using .deb files.Had sec mikrotik administrator
Had sec mikrotik administratormuhammad pailus
╠²
Dokumen tersebut merupakan daftar bab dan objektif pelatihan HadSec Mikrotik Administrator yang meliputi pengenalan Mikrotik, konfigurasi dasar Mikrotik melalui Winbox, telnet, webfig, konfigurasi interface, firewall, web proxy, dan jaringan nirkabel beserta konfigurasinya. Pelatihan ini bertujuan membekali peserta dengan pengetahuan dan keterampilan dasar mengkonfigurasi dan memonitor jaringan Mikrotik skala kecil hingga menengah.Connect your Javascript web app to ownCloud over the WebDAV interface
Connect your Javascript web app to ownCloud over the WebDAV interface Ilian Sapundshiev
╠²
The document discusses the integration of a JavaScript web app, Tagspaces, with OwnCloud using the WebDAV interface. It covers the architecture of Tagspaces as a backendless offline application, the rationale for using OwnCloud, and outlines steps for creating an OwnCloud app for enhanced integration. The presentation highlights the need for features like search integration and user management in future development.bluetooth [in]security
bluetooth [in]securityAmmar WK
╠²
Bluetooth adalah teknologi pengganti kabel yang efisien dan murah digunakan untuk menghubungkan berbagai perangkat seperti headset, ponsel, dan komputer. Meskipun praktis, fitur keamanannya masih lemah, dengan potensi ancaman seperti pencurian data dan pemalsuan identitas. Kesadaran pengguna terhadap risiko keamanan ini juga masih rendah.webhacking
webhackingAmmar WK
╠²
Dokumen ini membahas mengenai simulasi ancaman peretasan web yang terjadi melalui protokol HTTP, serta cara memanfaatkan kelemahan aplikasi web dan browser. Juga dijelaskan tentang penggunaan berbagai metode HTTP untuk menyerang aplikasi web. Penelitian tersebut menyoroti perlunya langkah-langkah keamanan dalam aplikasi web untuk mencegah serangan tersebut.eMAPT
eMAPTAndrii Holovchenko
╠²
The document discusses a recommendation from Armandoromeo, the CEO and lead instructor at elearnsecurity, for 40 Continuing Professional Education (CPE) credits. It certifies the release of Emapt version 1.0 on November 25, 2015, and mentions Andrii Holovchenko in relation to the certification.Playin with Password
Playin with PasswordAmmar WK
╠²
The document discusses various methods for cracking passwords, including tools for cracking Windows and Linux passwords like John the Ripper. It also covers passive techniques for obtaining passwords like keyloggers, bugs in applications, and sniffing plaintext protocols. The document recommends ways to improve password security such as using strong passphrases, encryption, firewalls, and keeping systems updated.Exploit Development with Python
Exploit Development with PythonThomas Gregory
╠²
The document outlines various techniques for exploit development using Python, including stack buffer overflow, structured exception handling (SEH), and evasive shellcode techniques like egghunter. It details memory layout, how stack growth occurs, and protections against SEH exploitation, such as DEP and SafeSEH. Additionally, it provides skeleton code for different exploit scenarios demonstrating the exploitation process.Similar to Mastering Network HackingFU - idsecconf2008 (7)
Pertemuan 8
Pertemuan 8Agung Mzl
╠²
Dokumen ini membahas berbagai contoh eksploitasi lubang keamanan, termasuk teknik serangan seperti denial of service, sniffing, dan penggunaan trojan horse. Berbagai alat dan metode untuk mencari informasi serta melakukan serangan dijelaskan secara rinci, termasuk penggunaan tools seperti whois, dig, dan tcpdump. Selain itu, dokumen juga memberikan wawasan tentang cara melindungi jaringan dari potensi ancaman ini.Network security
Network securitymho3yank
╠²
Dokumen tersebut membahas tentang keamanan jaringan, meliputi pengenalan serangan tipikal dan tahapan terjadinya serangan, serta alat-alat untuk melakukan pencarian keamanan jaringan seperti scanning dan probing. Dokumen tersebut juga membahas mengenai etika dalam melakukan hacking untuk kepentingan keamanan jaringan.Attacking The Lan
Attacking The Lanphanleson
╠²
Dokumen tersebut membahas serangan-serangan yang sering dilakukan dari jaringan lokal seperti spoofing, sniffing, Man in The Middle, remote code execution, dan denial of service. Metode spoofing dijelaskan dengan contoh IP spoofing untuk melakukan TCP SYN flooding. Metode Man in The Middle menggunakan ARP cache poisoning untuk menempatkan diri di tengah-tengah komunikasi. Proses sniffing dijelaskan dengan menangkap username dan password FTP. Remote code execution dijelaskan dengan contohBab i dasar dasar jaringan
Bab i dasar dasar jaringanCandra Adi Putra
╠²
Bab pertama mendiskusikan konsep dasar jaringan komputer termasuk topologi LAN, perangkat jaringan seperti switch, file server, billing server, dan router. Juga membahas konsep TCP/IP seperti alamat IP, subnet mask, gateway, dan DNS. Terakhir membahas perintah dasar jaringan seperti ipconfig, ping, tracert, nslookup, dan netstat.Tipe serangan pada website&webserver
Tipe serangan pada website&webserverMaya Ayunanda
╠²
Dokumen ini membahas berbagai tipe serangan pada website dan webserver, termasuk metode serangan DOS dan DDoS, serta memberikan informasi mengenai kerentanan dan solusi yang dapat diterapkan oleh webmaster. Serangan ini meliputi berbagai teknik seperti FTP bounce, syn flooding, dan DNS cache poisoning, yang semuanya dapat menyebabkan dampak serius pada operasional situs web. Penting bagi webmaster untuk secara proaktif mengidentifikasi celah keamanan dan menerapkan langkah perlindungan untuk mencegah serangan tersebut.02 teknik penyerangan
02 teknik penyeranganSetia Juli Irzal Ismail
╠²
Dokumen ini membahas teknik penyerangan dan keamanan jaringan yang mencakup berbagai tipe serangan seperti sniffing, spoofing, dan denial of service, serta tahapan hacking dari pengumpulan informasi hingga menghapus jejak penyerang. Selain itu, juga dijelaskan tentang tools untuk footprinting dan scanning jaringan, serta pentingnya vulnerability scanning untuk mengidentifikasi celah keamanan. Materi ini ditujukan untuk memberikan pemahaman mendalam tentang keamanan dalam dunia teknologi komputer.04 sniffing
04 sniffingSetia Juli Irzal Ismail
╠²
Dokumen ini membahas teknik keamanan jaringan, khususnya mengenai sniffing, metode penyadapan paket data dalam jaringan, serta cara-cara untuk mendeteksi dan mencegahnya. Selain itu, dijelaskan tentang exploitasi celah keamanan menggunakan Metasploit, dan berbagai jenis serangan denial of service (DoS) yang dapat mengganggu sumber daya jaringan. Referensi buku juga disertakan untuk bacaan lebih lanjut tentang hacking dan pengujian penetrasi.More from Ammar WK (20)
Vvdp-fgd-bssn
Vvdp-fgd-bssnAmmar WK
╠²
Dokumen ini membahas uji publik peraturan BSSN tentang Penyelenggaraan Program Pengungkapan Kerentanan Secara Sukarela (VVDP) serta aktivitas bug hunting di Indonesia. Ahmad Muammar, seorang direktur keamanan siber, menyoroti kendala yang dihadapi oleh bug bounty hunter, termasuk kurangnya pemahaman hukum terkait aktivitas bug hunting. Selain itu, terdapat agenda diskusi mengenai idealnya aktivitas bug hunting dan model komunikasi yang perlu ditingkatkan dalam proses pelaporan celah keamanan.Pen-testing is Dead?
Pen-testing is Dead?Ammar WK
╠²
Ahmad Muammar discusses the misconceptions surrounding penetration testing, arguing that it is not dead but evolves alongside practices like bug bounty programs and red team assessments. He emphasizes that while these methods serve distinct purposes, they should complement each other to ensure thorough security evaluations. The presentation highlights the importance of adapting penetration testing to modern development practices, such as Agile methodologies and Industry 4.0 technologies.How To [relatively] Secure your Web Applications
How To [relatively] Secure your Web ApplicationsAmmar WK
╠²
The document outlines the importance of securing web applications, highlighting various risks including financial, brand, customer, and technology risks. It emphasizes that security is a continuous process involving defensive and offensive strategies, such as secure coding, regular assessments, and penetration testing. Key methodologies like the ISSAF penetration testing framework are discussed to aid in identifying and addressing vulnerabilities.A Journey Into Pen-tester land: Myths or Facts!
A Journey Into Pen-tester land: Myths or Facts!Ammar WK
╠²
The document discusses penetration testing, differentiating it from vulnerability assessments and security audits, emphasizing the importance of validating security measures in IT infrastructure. It covers the skillsets required for penetration testers, including formal education and self-taught experiences, and debunks common myths surrounding the profession. The content emphasizes that effective pen-testing is crucial for organizations to identify vulnerabilities before malicious attackers do.Cybercrime: A threat to Financial industry
Cybercrime: A threat to Financial industryAmmar WK
╠²
The document discusses the threats posed by cybercrime to the financial industry, categorizing different types of cyber crimes targeting individuals, property, organizations, and society. It highlights the significant costs associated with cybercrime in financial services and identifies prevalent threats like credit card fraud, social engineering, and malware. Additionally, it suggests controls and mitigations to protect against these threats, emphasizing the importance of continuous education and security measures in financial institutions.Bugbounty vs-0day
Bugbounty vs-0dayAmmar WK
╠²
The document discusses bug bounty programs, which offer compensation for reporting software vulnerabilities, potentially mitigating zero-day attacks. It presents examples of high bounties from major companies like Microsoft, Apple, and Google, and outlines the nature of zero-day exploits as vulnerabilities unknown to vendors. The conclusion questions whether bug bounty programs effectively reduce zero-day attacks and provide proactive defenses against advanced persistent threats.Advanced Persistent Threat
Advanced Persistent ThreatAmmar WK
╠²
The document discusses Advanced Persistent Threats (APTs). It begins by defining APTs and noting some common misconceptions about them. It then discusses notable APT attacks from 2003 to 2017. Finally, it outlines the typical lifecycle of an APT attack, including preparation such as researching targets, acquiring tools, and testing for detection, as well as the intrusion deployment phase.Mobile hacking, pentest, and malware
Mobile hacking, pentest, and malwareAmmar WK
╠²
The document discusses mobile hacking techniques, focusing on targeted attacks like the Pegasus malware which exploits vulnerabilities in iOS and Android systems. It highlights key vulnerabilities such as memory corruption and insufficient security controls that can lead to device compromise. The document also outlines best practices for mobile penetration testing and emphasizes the importance of including security audits in the software development life cycle.Hacker? : it's not about Black or White
Hacker? : it's not about Black or WhiteAmmar WK
╠²
Dokumen ini adalah pengantar buku yang membahas tentang hacking dan keamanan internet, ditulis oleh penulis yang berbagi pengalaman dan pandangannya terkait tema tersebut. Penulis berusaha menyajikan cerita yang menarik melalui karakter remaja yang berhubungan dengan dunia komputer, dan menyampaikan pentingnya generasi muda untuk memahami teknologi secara profesional. Buku ini berisi berbagai tema terkait cybersecurity dan diharapkan dapat memberikan wawasan baru kepada pembaca, sekaligus mendorong diskusi tentang isu-isu ini.Introduction to IOS Application Penetration Testing
Introduction to IOS Application Penetration TestingAmmar WK
╠²
The document provides an overview of iOS mobile application penetration testing, outlining key concepts such as attack vectors, methodologies, and essential tools used in the analysis and exploitation of vulnerabilities. It discusses factors like information disclosure, insecure file permissions, and session management. Additionally, it includes references to various resources, cheat sheets, and techniques for conducting security assessments on iOS applications.Burp suite
Burp suiteAmmar WK
╠²
Burp Suite adalah perangkat keamanan gratis yang berguna untuk melakukan pengujian penetrasi web. Terdiri dari beberapa alat seperti proxy, spider, intruder, repeater, sequencer, dan decoder yang memungkinkan penangkapan dan modifikasi lalu lintas jaringan serta otomatisasi uji coba serangan."Network Packet Analysis
Network Packet AnalysisAmmar WK
╠²
The document outlines an agenda for a technical workshop on network packet analysis using Wireshark. The agenda includes playing with captured network files, examining Wireshark features, conducting packet analysis case studies, reviewing other packet analysis tools, and creating Wireshark dissectors. The workshop also demonstrates Wireshark statistics, protocol hierarchy, conversations, and IO graphs as useful features for analysis. It presents four case studies analyzing network packet captures and provides a summary of an attack called "Operation Aurora". Finally, it briefly introduces other packet analysis tools like Xplico and Network Miner.Packet analysis (Basic)
Packet analysis (Basic)Ammar WK
╠²
This document summarizes a technical workshop on network packet analysis presented by Ahmad Muammar W.K. OSCP. The workshop covers capturing and analyzing network traffic at different levels, from examining protocol fields to reconstructing files. Challenges like encrypted traffic and incorrect protocol dissection are also discussed. Various Wireshark features are demonstrated including capture and display filters, protocol decoding, and reconstructing files transmitted over non-standard ports.Network security
Network securityAmmar WK
╠²
The document discusses various topics related to network security including network layers, internet protocols like IPv4 and IPv6, network packet inspection, common attacks like spoofing, man-in-the-middle attacks, and denial of service attacks. It provides information on these topics and examples of hands-on exercises using tools like Wireshark to inspect network packets and demonstrate attacks. The document emphasizes the importance of network security defenses like IPsec, firewalls, intrusion detection systems, and security best practices.Penetration testing
Penetration testingAmmar WK
╠²
The document discusses penetration testing and related security concepts. It covers topics like vulnerability assessment, security audits, the differences between penetration testing and other assessments, common penetration testing methodologies, and the standard phases of information gathering, network mapping, vulnerability identification, exploitation, privilege escalation, maintaining access and covering tracks.Information Security Professional
Information Security ProfessionalAmmar WK
╠²
This document discusses information security professionals. It describes how some gain their knowledge through hacking as "natural born hackers" while others get formal education. It outlines the different types of hackers and professionals that work in information security like security officers, analysts, auditors, and engineers. Requirements for these roles include skills, experience, certification, and the ability to work independently or as part of a team. Maintaining the right attitude and continuing improvement are also important to avoid failure in these types of positions.Handout infosec defense-mechanism-y3dips
Handout infosec defense-mechanism-y3dipsAmmar WK
╠²
The document outlines the key elements of information security defense mechanisms and highlights the importance of understanding potential enemies, their motives, and attack vectors. It emphasizes the necessity of security measures such as education, security updates, hardening strategies, and security policies to mitigate risks. Additionally, it discusses the roles of different types of adversaries, including hackers, cyberespies, and cyberterrorists, as well as various security tools and assessment techniques.y3dips - Who Own Your Sensitive Information?
y3dips - Who Own Your Sensitive Information?Ammar WK
╠²
This document discusses who owns sensitive information, how it is taken, and how to protect it. It notes that hackers, cyber mafia, cyber terrorists, movies, cyber armies, and Wikileaks can own sensitive information. Information is often taken through password theft, insecure infrastructure, insecure data protection, lack of security policies/procedures, intrusion/hacking, and social engineering. The document provides examples of how Bradley Manning leaked classified US airstrike videos and diplomatic cables to Wikileaks by copying them to a Lady Gaga CD. It recommends upgrading security awareness, following security manuals, using strong authentication/encryption, antivirus software, and realizing that no system is completely secure and security requires human diligenceidsecconf2010-hacking priv8 network
idsecconf2010-hacking priv8 networkAmmar WK
╠²
This document discusses hacking into IPSec VPNs used by banks. It describes how banks historically used private networks but now rely on VPNs to connect over public infrastructure in a cost-effective way. However, VPNs are only relatively secure. The document outlines vulnerabilities in the IKE aggressive mode handshake when using pre-shared keys to authenticate, allowing tools to crack keys. It recommends ways to improve VPN security, such as disabling aggressive mode, not using dynamic IPs, and filtering connections.Mastering Network HackingFU - idsecconf2008
- 1. Mastering the Network HackingFU y3dips {y3dips/at/echo/or/id}
- 2. Ada apa dengan TCP/IP ’ü¼ Sudah Tua, kurang lebih 30 tahun. ’ü¼ Dibuat tanpa memperhatikan keamanan ŌłÆ Contoh : Telnet, FTP, SMTP ’ü¼ Celah sesungguhnya pada layer IP (v4) ŌłÆ Tidak ada metode verifikasi & enkripsi ŌłÆ Rentan terhadap IP spoofing dan MITM Mastering the Network HackingFU ŌĆō y3dips
- 3. Terkenal ’ü¼ Tunneling ’ü¼ Spoofing ’ü¼ Sniffing ’ü¼ ddos/botnet Mastering the Network HackingFU ŌĆō y3dips
- 4. Tunneling ŌŚÅ TOR╠²(the╠²Onion╠²Router) ŌĆō ŌĆ£Emerge╠²tor╠²privoxyŌĆØ ŌĆō Konfigurasikan╠²untuk╠²jalan╠²berbarengan ŌŚÅ Forward┬Łsocks4a╠²╠²╠²/╠²╠²╠²╠²╠²╠²╠²╠²╠²╠²╠²╠²╠²╠²╠²127.0.0.1:9050╠². ŌŚÅ Node╠²TOR╠²bisa╠²dibuat╠²siapa╠²saja ŌĆō Gov,╠²Mil,╠²Mafia,╠²dan╠²siapa╠²saja ŌŚÅ Gunakan╠²enkripsi,╠²atau╠²prinsip╠²dual╠²tunnel ŌŚÅ https://www.torproject.org/
- 5. Tunneling ŌŚÅ SSH╠²Tunneling ŌĆ£ssh╠²user@server╠²┬ŁD╠²port╠² ŌŚÅ Stunnel╠²┬Ł╠²stunnel.org ŌŚÅ Mengamankan╠²transaksi╠²melalui╠²protokol2╠² tanpa╠²enkripsi ŌĆō Tunneling╠²http,╠²smb╠²melalui╠²ssh/stunnel
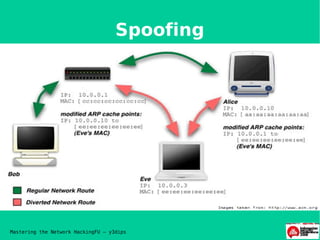
- 6. Spoofing Mastering the Network HackingFU ŌĆō y3dips
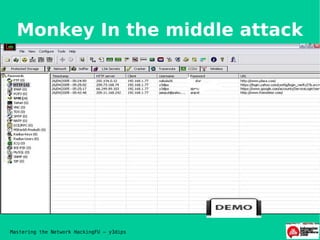
- 7. Monkey In the middle attack Mastering the Network HackingFU ŌĆō y3dips
- 8. Bertahan dengan Unix ŌĆó Paper Baca di http://www.slideshare.net/y3dips/arpwall-protect-from-arp-spoofing/ ŌĆó ARPWatch ,Swatch, PyGTK (alert.py) ARPWALL ŌŚÅ Arp ŌĆōs [ip] [mac] http://code.google.com/p/arpwall/ Wanna help ? Mastering the Network HackingFU ŌĆō y3dips
- 9. dDOS ŌĆó Untuk Dos, lihat http://www.slideshare.net/y3dips/denial-of-services/ ŌĆó Deteksi Botnet via SNMP ŌĆō 6666 ŌĆō 7000 open ŌĆó Syn attack v.s Syn Cookies ŌĆó Teknik baru (sebenarnya lama) ŌĆō http://it.slashdot.org/article.pl?sid=08/10/01/0127245 Mastering the Network HackingFU ŌĆō y3dips
- 10. Dunia Liar ’ü¼ Tidak Standar (proprietary) ’ü¼ Tertutup (closed source) ’ü¼ Selamat tinggal anak-anak (kiddo) ’ü¼ Kuat? Mastering the Network HackingFU ŌĆō y3dips
- 11. Dunia Liar ’ü¼ Aplikasi scanner umumnya tak berdaya NMAP, Nessus, superscan ’ü¼ Bekerja berdasarkan data yang di input ’ü¼ Metode handshake berbeda Mastering the Network HackingFU ŌĆō y3dips
- 12. Perlengkapan ’ü¼ Python [kemampuan programming] ’ü¼ Scapy (pakcet Manipulating platform) ’ü¼ Spoofing ’ü¼ Sniffing (tcpdump only?) ’ü¼ Some l33t tools (THCAmapcrap) Mastering the Network HackingFU ŌĆō y3dips
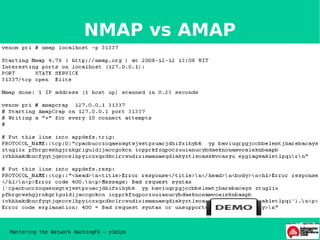
- 13. NMAP vs AMAP Mastering the Network HackingFU ŌĆō y3dips
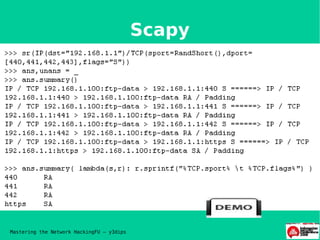
- 14. Scapy Mastering the Network HackingFU ŌĆō y3dips
- 15. Aplikasi Pribadi ŌĆó Tidak kuat, bahkan ŌĆ£ŌĆÖrelatifŌĆÖ lebih lemah Hanya telnet secara multiple dan mereka mati ŌĆó Tcp/ip memang bercelah, Aplikasi yang berjalan diatasnya membawa dosa yang sama ŌĆó Tanpa metode verifikasi + enkripsi ŌĆó Tidak ada akses kontrol, otentikasi, session timeout, limitasi koneksi Mastering the Network HackingFU ŌĆō y3dips
- 16. Tips Info di Jaringan ’ü¼ Snmp (default community strings) ’ü¼ Smtp ( vrfy dan expn verbs ; enumerate user) ’ü¼ Ftp (user enum) ’ü¼ Pop3 (user enum) Mastering the Network HackingFU ŌĆō y3dips
- 17. Bertahan? ŌĆó IPV6 ŌĆó Medukung Autentikasi , IP proteksi dan Trafik Kontrol ŌĆó Alasan politis dan bisnis maka belum populer. Mastering the Network HackingFU ŌĆō y3dips
- 18. Santai Tanya & Jawab Terima Kasih - Komite - himatif UPN - Kamu!, ya kamu yang mendukung acara ini. Mastering the Network HackingFU ŌĆō y3dips
