MD5
Download as PPTX, PDF1 like631 views
The document discusses the MD5 algorithm used for generating message digests of arbitrary inputs. It describes the MD5 algorithm structure and implementation steps. The implementation involves padding the input message to a length congruent to 448 modulo 512 bits. A 64-bit representation of the original message length is then appended. The padded message is processed in 512-bit blocks, each divided into sixteen 32-bit words. Four initialization values are used to compute the message digest through four rounds of operations on each block.
1 of 16
Downloaded 36 times







![Append the original length before padding.
We use modulus 64 operation.
Get exact multiple of 512 after 64 bits adding.
Now create blocks according to bit length.
Before padding 1000bits.
Now apply mod64.
1000] length 264](https://image.slidesharecdn.com/presentation-190129142650/85/MD5-9-320.jpg)





![Implementation Steps
Round 1.
[abcd k s i] denote the operation a = b + ((a + F (b, c, d) + X [k] + T [i]) <<< s).
Do the following 16 operations.
[ABCD 0 7 1] [DABC 1 12 2] [CDAB 2 17 3] [BCDA 3 22 4]
[ABCD 4 7 5] [DABC 5 12 6] [CDAB 6 17 7] [BCDA 7 22 8]
[ABCD 8 7 9] [DABC 9 12 10] [CDAB 10 17 11] [BCDA 11 22 12]
[ABCD 12 7 13] [DABC 13 12 14] [CDAB 14 17 15] [BCDA 15 22 16]](https://image.slidesharecdn.com/presentation-190129142650/85/MD5-15-320.jpg)
![Single MD5 operation mathmeticaly defined like this:
a=b+((a+process,p(b,c,d)+M[i]+T[k]))<<shift
M[i]=message is i.
T[k]=constant is k.
<<shift=circular shift](https://image.slidesharecdn.com/presentation-190129142650/85/MD5-16-320.jpg)
Recommended
Cryptographic hash function md5



Cryptographic hash function md5Khulna University, Khulna, Bangladesh
Ėý
This document discusses the MD5 cryptographic hash function. It provides an introduction to hash functions and describes MD5, including its features, applications, algorithm, analysis, and drawbacks. MD5 produces a 128-bit hash value from a message of any size through a multi-step process involving padding, appending a length, initializing buffers, and processing in 16-word blocks. While once widely used, MD5 is now considered broken due to vulnerabilities found in its compression function and preimage resistance.Message digest 5



Message digest 5Tirthika Bandi
Ėý
MD5 is a cryptographic hash function that produces a 128-bit hash value for a message of any length. It was originally designed to provide authentication of digital signatures but is no longer considered reliable for cryptography due to techniques that can generate collisions. MD5 operates by padding the input, appending the length, dividing into blocks, initializing variables, processing blocks through 4 rounds of operations with different constants each round, and outputting the hash value. While it was intended to be difficult to find collisions or recover the input, MD5 is no longer considered cryptographically secure due to attacks demonstrating collisions.Sha



Shaha123
Ėý
Hash functions take a variable-length input and produce a fixed-length output. They are used to verify data integrity and ensure data has not been altered. Cryptographic hash functions have properties of being one-way and collision resistant. Secure Hash Algorithm 512 (SHA-512) is an iterative cryptographic hash function that produces a 512-bit hash value. It works by processing the input message in 1024-bit blocks through 80 rounds of compression functions using logical operations and round constants. SHA-512 and other cryptographic hash functions have applications in security protocols like TLS, PGP, and DNSSEC.MD-5 : Algorithm



MD-5 : AlgorithmSahil Kureel
Ėý
The document discusses the MD5 algorithm, which takes an input message of arbitrary length and produces a 128-bit fingerprint or message digest. It describes the technical process, including padding the message, appending the length, initializing buffers, processing the message in 16-word blocks using four auxiliary functions, and outputting the final message digest consisting of the values A, B, C, and D. The MD5 algorithm provides a secure way to compress a large file before encryption.SHA 1 Algorithm



SHA 1 AlgorithmShiva RamDam
Ėý
The document describes the SHA-1 hashing algorithm. SHA-1 produces a 160-bit hash value from an input of arbitrary length. It works by padding the input, appending the length, initializing hash buffers, processing the message through 80 rounds of compression, and outputting the final hash value. The compression function divides the padded message into 16-word blocks and schedules the words through the rounds using a message scheduling algorithm. It performs logical and bitwise operations on the words and chaining variables to generate a new hash.Blow fish final ppt



Blow fish final pptAjay AJ
Ėý
This document discusses the design and implementation of the Blowfish encryption algorithm using Verilog HDL. Blowfish is a symmetric block cipher that uses a variable-length key from 32 to 448 bits, making it suitable for securing data. The algorithm consists of two parts - key expansion and a round structure involving 16 rounds of operations. The authors implemented Blowfish using Verilog HDL on a Xilinx FPGA for applications requiring encryption like IoT devices. Their design achieved high-speed encryption of up to 4 bits per clock cycle and operated at a maximum frequency of 50MHz.The MD5 hashing algorithm



The MD5 hashing algorithmBob Landstrom
Ėý
An introduction to the MD5 Hashing Algorithm and its importance in the data center as an essential component of cryptography. http://boblandstrom.comSHA 1 Algorithm.ppt



SHA 1 Algorithm.pptRajapriya82
Ėý
The SHA-1 algorithm is a cryptographic hash function that takes an input and produces a 160-bit hash value. It works by padding the input message, appending the length, and then processing the message in 512-bit blocks through 80 processing steps using functions and constants to calculate new hash values. The final hash value after all blocks are processed represents the message digest.Hash function



Hash functionHarry Potter
Ėý
The document discusses hash functions and message authentication codes (MACs). It begins by defining hash functions and MACs, noting that hash functions generate a fingerprint for a message without a key while MACs use a keyed hash function. It then covers security requirements for hash functions like one-wayness and collision resistance. Popular hash functions are described like MD5, SHA-1, and the SHA-2 family. Constructions for hash functions based on block ciphers and iterated hash functions are also outlined. The document concludes by comparing hash functions and MACs and describing common MAC constructions.Hash Function



Hash Functionstalin rijal
Ėý
A hash function maps data of arbitrary size to a fixed size value called a hash. Common hash functions include MD5 and SHA, with MD5 producing a 128-bit hash. While hashes were once used to securely store passwords, MD5 is now considered cryptographically broken due to collisions being found in its compression function. One-way signatures allow multiple users to generate linked signatures on the same message in a verifiable chain.Data encryption standard



Data encryption standardVasuki Ramasamy
Ėý
This document summarizes a chapter about the Data Encryption Standard (DES). It provides an overview of DES, describing it as a symmetric-key block cipher developed by IBM and adopted by the National Institute of Standards and Technology. The chapter then goes into details about the structure and design of DES, including its use of an initial and final permutation, 16 rounds of encryption using subkey values, and weaknesses like its short key length. It also discusses analyses of DES security, noting brute force, differential cryptanalysis, and linear cryptanalysis as potential attack methods.5. message authentication and hash function



5. message authentication and hash functionChirag Patel
Ėý
1) Message authentication can be achieved through message encryption, message authentication codes (MACs), or hash functions.
2) MACs provide authentication by appending a fixed-size block that depends on the message and a secret key. Receivers can verify messages by recomputing the MAC.
3) Hash functions map variable-length data to fixed-length outputs and are easy to compute but infeasible to reverse or find collisions. Common hash functions include MD5 and SHA-512.SHA- Secure hashing algorithm



SHA- Secure hashing algorithmRuchi Maurya
Ėý
Security Hash Algorithm (SHA) was developed in 1993 by the National Institute of Standards and Technology (NIST) and National Security Agency (NSA).
It was designed as the algorithm to be used for secure hashing in the US Digital Signature Standard.
âĒ Hashing function is one of the most commonly used encryption methods. A hash is a special mathematical function that performs one-way encryption.
âĒ SHA-l is a revised version of SHA designed by NIST and was published as a Federal Information Processing Standard (FIPS).
âĒ Like MD5, SHA-l processes input data in 512-bit blocks.
âĒ SHA-l generates a 160-bit message digest. Whereas MD5 generated message digest of 128 bits.
âĒ The procedure is used to send a non secret but signed message from sender to receiver. In such a case following steps are followed:
1. Sender feeds a plaintext message into SHA-l algorithm and obtains a 160-bit SHA-l hash.
2. Sender then signs the hash with his RSA private key and sends both the plaintext message and the signed hash to the receiver.
3. After receiving the message, the receiver computes the SHA-l hash himself and also applies the sender's public key to the signed hash to obtain the original hash H.
Encryption And Decryption Using AES Algorithm



Encryption And Decryption Using AES AlgorithmAhmed Raza Shaikh
Ėý
This is a Presentation On use of AES Algorithm To Encrypt Or Decrypt a Text File. This Algorithm is the latest and better than DES. It is a Networking Presentation. Thank You.Hash Function



Hash FunctionSiddharth Srivastava
Ėý
This document discusses message authentication techniques including message encryption, message authentication codes (MACs), and hash functions. It describes how each technique can be used to authenticate messages and protect against various security threats. It also covers how symmetric and asymmetric encryption can provide authentication when used with MACs or digital signatures. Specific MAC and hash functions are examined like HMAC, SHA-1, and SHA-2. X.509 is introduced as a standard for digital certificates.Trible data encryption standard (3DES)



Trible data encryption standard (3DES)Ahmed Mohamed Mahmoud
Ėý
This document provides an overview of the Triple Data Encryption Standard (3DES). It first briefly describes the original Data Encryption Standard (DES) and its key components including the initial and final permutations, substitution boxes, and key schedule. It then explains that 3DES applies DES three times with three different keys to strengthen security by effectively doubling the key size to 112 bits. Simulations are included showing encryption and decryption using 3DES with equal and different keys.PGP S/MIME



PGP S/MIMESou Jana
Ėý
1. PGP (Pretty Good Privacy) provides encryption and authentication for email. It uses public key cryptography and digital signatures to encrypt messages and verify sender identity.
2. PGP offers five main services - digital signatures for authentication, symmetric encryption for confidentiality, compression, encoding for email compatibility, and message segmentation.
3. The document describes how PGP provides both authentication and encryption of messages using a combination of public key and symmetric key cryptography. Digital signatures verify the identity of the sender and encrypted symmetric keys protect the confidentiality of messages.Message Authentication Code & HMAC



Message Authentication Code & HMACKrishna Gehlot
Ėý
This document discusses message authentication codes (MACs). It explains that MACs use a shared symmetric key to authenticate messages, ensuring integrity and validating the sender. The document outlines the MAC generation and verification process, and notes that MACs provide authentication but not encryption. It then describes HMAC specifically, which applies a cryptographic hash function to the message and key to generate the MAC. The key steps of the HMAC process are detailed.Symmetric encryption



Symmetric encryptionDR RICHMOND ADEBIAYE
Ėý
Modern block ciphers are widely used to provide encryption of quantities of information, and/or a cryptographic checksum to ensure the contents have not been altered. We continue to use block ciphers because they are comparatively fast, and because we know a fair amount about how to design them.
Hash function 



Hash function Salman Memon
Ėý
A hash function usually means a function that compresses, meaning the output is shorter than the input
A hash function takes a group of characters (called a key) and maps it to a value of a certain length (called a hash value or hash).
The hash value is representative of the original string of characters, but is normally smaller than the original.
This term is also known as a hashing algorithm or message digest function.
Hash functions also called message digests or one-way encryption or hashing algorithm.
http://phpexecutor.comRSA ALGORITHM



RSA ALGORITHMDr. Shashank Shetty
Ėý
The document summarizes the RSA encryption algorithm. It begins by explaining that RSA was developed in 1977 by Rivest, Shamir and Adleman. It then provides an example to demonstrate how RSA works step-by-step, generating keys, encrypting a message and decrypting the ciphertext. Finally, it discusses some challenges with breaking RSA encryption, including brute force attacks and mathematical attacks based on factoring the encryption keys, as well as timing attacks that aim to deduce keys based on variations in processing time.DES



DESNaga Srimanyu Timmaraju
Ėý
DES was developed as a standard for communications and data protection by an IBM research team in response to a request from the National Bureau of Standards (now called NIST). DES uses the techniques of confusion and diffusion achieved through numerous permutations and the XOR operation. The basic DES process encrypts a 64-bit block using a 56-bit key over 16 complex rounds consisting of permutations and key-dependent calculations. Triple DES was developed as a more secure version of DES.Network security cryptographic hash function



Network security cryptographic hash functionMijanur Rahman Milon
Ėý
This document discusses cryptographic hash functions. It defines hashing as transforming a variable length string into a shorter, fixed length value. Cryptographic hash functions are designed to be one-way and resistant to tampering. They are important for security applications like digital signatures, message authentication and password verification. Commonly used hash functions include MD5 and SHA-1 which take arbitrary inputs and produce fixed-length outputs.Idea(international data encryption algorithm)



Idea(international data encryption algorithm)SAurabh PRajapati
Ėý
The document discusses the International Data Encryption Algorithm (IDEA). It was developed in 1990 as a replacement for the Data Encryption Standard. IDEA is a symmetric block cipher that uses a 128-bit key to encrypt 64-bit blocks of plaintext into ciphertext. The key is divided into 52 subkeys that are used in 8 rounds of encryption/decryption operations involving XOR, addition, and multiplication. IDEA was used in PGP v2.0 and can encrypt sensitive data for applications like financial services, broadcasting, and government use.Des



DesAnshul Sharma
Ėý
The document summarizes the Data Encryption Standard (DES) cryptosystem. It describes DES as a symmetric-key block cipher developed from a modified version of the Lucifer cipher and standardized by NIST in 1975. The core of DES is the DES function, which applies a 48-bit key to the rightmost 32 bits of the input block using substitution boxes and permutation tables to produce a 32-bit output in a Feistel network structure, with 16 rounds of processing to diffuse the plaintext over the block.Secure Hash Algorithm



Secure Hash AlgorithmVishakha Agarwal
Ėý
Secure Hash Algorithm (SHA) was developed by NIST and NSA to hash messages into fixed-length message digests. SHA has multiple versions including SHA-1, SHA-2, and SHA-3. SHA-1 produces a 160-bit message digest and works by padding the input message, appending the length, dividing into blocks, initializing variables, and processing blocks through 80 rounds of operations to output the digest. SHA-512 is closely modeled after SHA-1 but produces a 512-bit digest and uses 1024-bit blocks.DES (Data Encryption Standard) pressentation



DES (Data Encryption Standard) pressentationsarhadisoftengg
Ėý
This document discusses data encryption methods. It defines encryption as hiding information so it can only be accessed by those with the key. There are two main types: symmetric encryption uses one key, while asymmetric encryption uses two different but related keys. Encryption works by scrambling data using techniques like transposition, which rearranges the order, and substitution, which replaces parts with other values. The document specifically describes the Data Encryption Standard (DES) algorithm and the public key cryptosystem, which introduced the innovative approach of using different keys for encryption and decryption.Diffie hellman key exchange algorithm



Diffie hellman key exchange algorithmSunita Kharayat
Ėý
The presentation include:
-Diffie hellman key exchange algorithm
-Primitive roots
-Discrete logarithm and discrete logarithm problem
-Attacks on diffie hellman and their possible solution
-Key distribution center ENGG_CSE_III_YEAR_Message_Digest_MD_5.ppt



ENGG_CSE_III_YEAR_Message_Digest_MD_5.pptSakethBhargavaRallap
Ėý
ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_introduction to MD5 Massage Digest Algorithm.ppt



introduction to MD5 Massage Digest Algorithm.pptmadlord2
Ėý
This document summarizes the MD5 message digest algorithm. It was developed by Professor Ronald L. Rivest in 1991 to take an input of arbitrary length and produce a 128-bit fingerprint. The MD5 algorithm structure and implementation steps are described, including padding the input, appending the length, initializing buffers, and processing the message in 16-word blocks through four rounds of functions. Performance is provided showing MD5 is very fast on 32-bit machines. MD5 is compared to MD4, noting changes made and that it is widely used and considered efficient.More Related Content
What's hot (20)
Hash function



Hash functionHarry Potter
Ėý
The document discusses hash functions and message authentication codes (MACs). It begins by defining hash functions and MACs, noting that hash functions generate a fingerprint for a message without a key while MACs use a keyed hash function. It then covers security requirements for hash functions like one-wayness and collision resistance. Popular hash functions are described like MD5, SHA-1, and the SHA-2 family. Constructions for hash functions based on block ciphers and iterated hash functions are also outlined. The document concludes by comparing hash functions and MACs and describing common MAC constructions.Hash Function



Hash Functionstalin rijal
Ėý
A hash function maps data of arbitrary size to a fixed size value called a hash. Common hash functions include MD5 and SHA, with MD5 producing a 128-bit hash. While hashes were once used to securely store passwords, MD5 is now considered cryptographically broken due to collisions being found in its compression function. One-way signatures allow multiple users to generate linked signatures on the same message in a verifiable chain.Data encryption standard



Data encryption standardVasuki Ramasamy
Ėý
This document summarizes a chapter about the Data Encryption Standard (DES). It provides an overview of DES, describing it as a symmetric-key block cipher developed by IBM and adopted by the National Institute of Standards and Technology. The chapter then goes into details about the structure and design of DES, including its use of an initial and final permutation, 16 rounds of encryption using subkey values, and weaknesses like its short key length. It also discusses analyses of DES security, noting brute force, differential cryptanalysis, and linear cryptanalysis as potential attack methods.5. message authentication and hash function



5. message authentication and hash functionChirag Patel
Ėý
1) Message authentication can be achieved through message encryption, message authentication codes (MACs), or hash functions.
2) MACs provide authentication by appending a fixed-size block that depends on the message and a secret key. Receivers can verify messages by recomputing the MAC.
3) Hash functions map variable-length data to fixed-length outputs and are easy to compute but infeasible to reverse or find collisions. Common hash functions include MD5 and SHA-512.SHA- Secure hashing algorithm



SHA- Secure hashing algorithmRuchi Maurya
Ėý
Security Hash Algorithm (SHA) was developed in 1993 by the National Institute of Standards and Technology (NIST) and National Security Agency (NSA).
It was designed as the algorithm to be used for secure hashing in the US Digital Signature Standard.
âĒ Hashing function is one of the most commonly used encryption methods. A hash is a special mathematical function that performs one-way encryption.
âĒ SHA-l is a revised version of SHA designed by NIST and was published as a Federal Information Processing Standard (FIPS).
âĒ Like MD5, SHA-l processes input data in 512-bit blocks.
âĒ SHA-l generates a 160-bit message digest. Whereas MD5 generated message digest of 128 bits.
âĒ The procedure is used to send a non secret but signed message from sender to receiver. In such a case following steps are followed:
1. Sender feeds a plaintext message into SHA-l algorithm and obtains a 160-bit SHA-l hash.
2. Sender then signs the hash with his RSA private key and sends both the plaintext message and the signed hash to the receiver.
3. After receiving the message, the receiver computes the SHA-l hash himself and also applies the sender's public key to the signed hash to obtain the original hash H.
Encryption And Decryption Using AES Algorithm



Encryption And Decryption Using AES AlgorithmAhmed Raza Shaikh
Ėý
This is a Presentation On use of AES Algorithm To Encrypt Or Decrypt a Text File. This Algorithm is the latest and better than DES. It is a Networking Presentation. Thank You.Hash Function



Hash FunctionSiddharth Srivastava
Ėý
This document discusses message authentication techniques including message encryption, message authentication codes (MACs), and hash functions. It describes how each technique can be used to authenticate messages and protect against various security threats. It also covers how symmetric and asymmetric encryption can provide authentication when used with MACs or digital signatures. Specific MAC and hash functions are examined like HMAC, SHA-1, and SHA-2. X.509 is introduced as a standard for digital certificates.Trible data encryption standard (3DES)



Trible data encryption standard (3DES)Ahmed Mohamed Mahmoud
Ėý
This document provides an overview of the Triple Data Encryption Standard (3DES). It first briefly describes the original Data Encryption Standard (DES) and its key components including the initial and final permutations, substitution boxes, and key schedule. It then explains that 3DES applies DES three times with three different keys to strengthen security by effectively doubling the key size to 112 bits. Simulations are included showing encryption and decryption using 3DES with equal and different keys.PGP S/MIME



PGP S/MIMESou Jana
Ėý
1. PGP (Pretty Good Privacy) provides encryption and authentication for email. It uses public key cryptography and digital signatures to encrypt messages and verify sender identity.
2. PGP offers five main services - digital signatures for authentication, symmetric encryption for confidentiality, compression, encoding for email compatibility, and message segmentation.
3. The document describes how PGP provides both authentication and encryption of messages using a combination of public key and symmetric key cryptography. Digital signatures verify the identity of the sender and encrypted symmetric keys protect the confidentiality of messages.Message Authentication Code & HMAC



Message Authentication Code & HMACKrishna Gehlot
Ėý
This document discusses message authentication codes (MACs). It explains that MACs use a shared symmetric key to authenticate messages, ensuring integrity and validating the sender. The document outlines the MAC generation and verification process, and notes that MACs provide authentication but not encryption. It then describes HMAC specifically, which applies a cryptographic hash function to the message and key to generate the MAC. The key steps of the HMAC process are detailed.Symmetric encryption



Symmetric encryptionDR RICHMOND ADEBIAYE
Ėý
Modern block ciphers are widely used to provide encryption of quantities of information, and/or a cryptographic checksum to ensure the contents have not been altered. We continue to use block ciphers because they are comparatively fast, and because we know a fair amount about how to design them.
Hash function 



Hash function Salman Memon
Ėý
A hash function usually means a function that compresses, meaning the output is shorter than the input
A hash function takes a group of characters (called a key) and maps it to a value of a certain length (called a hash value or hash).
The hash value is representative of the original string of characters, but is normally smaller than the original.
This term is also known as a hashing algorithm or message digest function.
Hash functions also called message digests or one-way encryption or hashing algorithm.
http://phpexecutor.comRSA ALGORITHM



RSA ALGORITHMDr. Shashank Shetty
Ėý
The document summarizes the RSA encryption algorithm. It begins by explaining that RSA was developed in 1977 by Rivest, Shamir and Adleman. It then provides an example to demonstrate how RSA works step-by-step, generating keys, encrypting a message and decrypting the ciphertext. Finally, it discusses some challenges with breaking RSA encryption, including brute force attacks and mathematical attacks based on factoring the encryption keys, as well as timing attacks that aim to deduce keys based on variations in processing time.DES



DESNaga Srimanyu Timmaraju
Ėý
DES was developed as a standard for communications and data protection by an IBM research team in response to a request from the National Bureau of Standards (now called NIST). DES uses the techniques of confusion and diffusion achieved through numerous permutations and the XOR operation. The basic DES process encrypts a 64-bit block using a 56-bit key over 16 complex rounds consisting of permutations and key-dependent calculations. Triple DES was developed as a more secure version of DES.Network security cryptographic hash function



Network security cryptographic hash functionMijanur Rahman Milon
Ėý
This document discusses cryptographic hash functions. It defines hashing as transforming a variable length string into a shorter, fixed length value. Cryptographic hash functions are designed to be one-way and resistant to tampering. They are important for security applications like digital signatures, message authentication and password verification. Commonly used hash functions include MD5 and SHA-1 which take arbitrary inputs and produce fixed-length outputs.Idea(international data encryption algorithm)



Idea(international data encryption algorithm)SAurabh PRajapati
Ėý
The document discusses the International Data Encryption Algorithm (IDEA). It was developed in 1990 as a replacement for the Data Encryption Standard. IDEA is a symmetric block cipher that uses a 128-bit key to encrypt 64-bit blocks of plaintext into ciphertext. The key is divided into 52 subkeys that are used in 8 rounds of encryption/decryption operations involving XOR, addition, and multiplication. IDEA was used in PGP v2.0 and can encrypt sensitive data for applications like financial services, broadcasting, and government use.Des



DesAnshul Sharma
Ėý
The document summarizes the Data Encryption Standard (DES) cryptosystem. It describes DES as a symmetric-key block cipher developed from a modified version of the Lucifer cipher and standardized by NIST in 1975. The core of DES is the DES function, which applies a 48-bit key to the rightmost 32 bits of the input block using substitution boxes and permutation tables to produce a 32-bit output in a Feistel network structure, with 16 rounds of processing to diffuse the plaintext over the block.Secure Hash Algorithm



Secure Hash AlgorithmVishakha Agarwal
Ėý
Secure Hash Algorithm (SHA) was developed by NIST and NSA to hash messages into fixed-length message digests. SHA has multiple versions including SHA-1, SHA-2, and SHA-3. SHA-1 produces a 160-bit message digest and works by padding the input message, appending the length, dividing into blocks, initializing variables, and processing blocks through 80 rounds of operations to output the digest. SHA-512 is closely modeled after SHA-1 but produces a 512-bit digest and uses 1024-bit blocks.DES (Data Encryption Standard) pressentation



DES (Data Encryption Standard) pressentationsarhadisoftengg
Ėý
This document discusses data encryption methods. It defines encryption as hiding information so it can only be accessed by those with the key. There are two main types: symmetric encryption uses one key, while asymmetric encryption uses two different but related keys. Encryption works by scrambling data using techniques like transposition, which rearranges the order, and substitution, which replaces parts with other values. The document specifically describes the Data Encryption Standard (DES) algorithm and the public key cryptosystem, which introduced the innovative approach of using different keys for encryption and decryption.Diffie hellman key exchange algorithm



Diffie hellman key exchange algorithmSunita Kharayat
Ėý
The presentation include:
-Diffie hellman key exchange algorithm
-Primitive roots
-Discrete logarithm and discrete logarithm problem
-Attacks on diffie hellman and their possible solution
-Key distribution center Similar to MD5 (20)
ENGG_CSE_III_YEAR_Message_Digest_MD_5.ppt



ENGG_CSE_III_YEAR_Message_Digest_MD_5.pptSakethBhargavaRallap
Ėý
ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_ENGG_CSE_III_YEAR_introduction to MD5 Massage Digest Algorithm.ppt



introduction to MD5 Massage Digest Algorithm.pptmadlord2
Ėý
This document summarizes the MD5 message digest algorithm. It was developed by Professor Ronald L. Rivest in 1991 to take an input of arbitrary length and produce a 128-bit fingerprint. The MD5 algorithm structure and implementation steps are described, including padding the input, appending the length, initializing buffers, and processing the message in 16-word blocks through four rounds of functions. Performance is provided showing MD5 is very fast on 32-bit machines. MD5 is compared to MD4, noting changes made and that it is widely used and considered efficient.Hash mac algorithms



Hash mac algorithmsFraboni Ec
Ėý
This document provides an overview of hash functions, secure hash algorithms (SHA), and HMAC.
It describes how hash functions work by taking a message and producing a fixed-size hash value. SHA algorithms like SHA-1, SHA-256, SHA-384, and SHA-512 are described as secure hash functions developed by NIST. The document outlines the 5 steps of the SHA-512 algorithm: 1) append padding bits, 2) append length, 3) initialize hash buffer, 4) process message in blocks, and 5) output hash value.
HMAC is then introduced as a way to incorporate a secret key into an existing hash algorithm like MD5 or SHA-1 to produce a message authentication codeHash& mac algorithms



Hash& mac algorithmsHarry Potter
Ėý
This document discusses hash and MAC algorithms. It provides details on hash functions, the Secure Hash Algorithm (SHA), and HMAC.
Hash functions take a message and produce a fixed-size hash value. SHA is a secure hash algorithm developed by NIST that produces 160-bit or longer hash values. It involves padding the message, initializing a buffer, processing the message in blocks through a compression function, and outputting the final hash.
HMAC is a MAC algorithm that incorporates a secret key into an existing hash function like MD5 or SHA. It pads and XORs the key, hashes the result with the message, then hashes again with a padded key to produce the MAC value.Hash mac algorithms



Hash mac algorithmsLuis Goldster
Ėý
This document discusses hash and MAC algorithms. It provides details on hash functions, the Secure Hash Algorithm (SHA), and HMAC.
Hash functions take a message and produce a fixed-size hash value. SHA is a secure hash algorithm developed by NIST that produces 160-bit or longer hash values. It works by padding the message, appending the length, initializing buffers, processing the message in blocks through compression functions, and outputting the hash value.
HMAC is a MAC algorithm that incorporates a secret key into an existing hash function like MD5 or SHA. It works by padding the key, XORing it with ipad or opad, appending the message or hash, and applying the hash function to produce theHash mac algorithms



Hash mac algorithmsJames Wong
Ėý
This document discusses hash and MAC algorithms. It provides details on hash functions, the Secure Hash Algorithm (SHA), and HMAC.
Hash functions take a message and produce a fixed-size hash value. SHA is a secure hash algorithm developed by NIST that produces 160-bit or longer hash values. It works by padding and processing the message in blocks, using a compression function and initialization vector.
HMAC is a MAC algorithm that incorporates a secret key into an existing hash function like MD5 or SHA. It works by XORing the key with ipad and opad pads, hashing the padded message, and outputting the result. HMAC executes with similar speed to the underlying hash function.Hash mac algorithms



Hash mac algorithmsDavid Hoen
Ėý
This document discusses hash and MAC algorithms. It provides details on hash functions, the Secure Hash Algorithm (SHA), and HMAC.
Hash functions take a message and produce a fixed-size hash value. SHA is a secure hash algorithm developed by NIST that produces 160-bit or longer hash values. It works by padding and processing the message in blocks, using a compression function and initialization vector.
HMAC is a MAC algorithm that incorporates a secret key into the hashing process. It works by XORing the key with ipad and opad pads, hashing the padded message, and outputting the result. HMAC allows existing hash functions to be used for message authentication in a way that relies on the secretHash mac algorithms



Hash mac algorithmsTony Nguyen
Ėý
This document discusses hash and MAC algorithms. It provides details on hash functions, the Secure Hash Algorithm (SHA), and HMAC.
Hash functions take a message and produce a fixed-size hash value. SHA is a secure hash algorithm developed by NIST that produces 160-bit or longer hash values. It works by padding the message, appending the length, initializing buffers, processing the message in blocks through compression functions, and outputting the hash value.
HMAC is a MAC algorithm that incorporates a secret key into an existing hash function like MD5 or SHA. It works by padding the key, XORing it with ipad or opad, appending the message or hash, and applying the hash function to produce theBasic explanation to md5 implementation in C



Basic explanation to md5 implementation in CSourav Punoriyar
Ėý
MD5 is a hashing algorithm that takes an input of arbitrary length and produces a 128-bit hash value. It works by processing the input message in 512-bit blocks, padding the last block as needed, and performing transformations using auxiliary functions to update the hash value after each block. The implementation in C uses a state buffer to store the running hash value, along with functions for initialization, updating the hash with new data blocks, finalization including padding, and transforming blocks.MD5.pptx.pdf



MD5.pptx.pdfPrateekKarkera1
Ėý
This document provides an overview of MD5, a message digest algorithm. It discusses how MD5 works by taking a message of any length and producing a 128-bit hash value. The MD5 process involves padding the message to a length of a multiple of 512 bits, dividing it into blocks, initializing chaining variables, and then performing four rounds of processing on each block that includes applying a non-linear process, adding message sub-blocks and constants, and shifting values. The output of MD5 is a hash that uniquely identifies the original message and is useful for authentication and detecting message tampering.Unit-3.pdf



Unit-3.pdfHarishChaudhary21
Ėý
The document discusses message authentication and hash functions. It defines message authentication as a way to ensure data integrity and describes how message authentication codes (MACs) work using symmetric keys. It also explains how hash functions take an input of any length and produce a fixed-length output digest. Specific hash functions discussed include MD4, MD5, SHA-1, and how they work by padding the input, initializing buffers, processing the input in blocks, and outputting the digest.Data streaming algorithms



Data streaming algorithmsHridyesh Bisht
Ėý
This presentation has information about what do you mean by an algorithm, what is hashing and various hashing algorithms and their applications. Approximate counting Algorithm and their applications, Counting Distinct Elements Algorithm and their applications and Frequency estimation algorithm and their applications . Also, the research papers we referenced.
A Comparative Analysis between SHA and MD5 algorithms 



A Comparative Analysis between SHA and MD5 algorithms Er Piyush Gupta IN ââïĢŋ
Ėý
this paper belongs to deep analysis of secure hash algorithm and message digest version 5 algorithm....MD5 ALGORITHM.pptx



MD5 ALGORITHM.pptxRajapriya82
Ėý
The MD5 algorithm is a cryptographic hash function that generates a 128-bit digest from a message of any length. It works by first padding the message to a length that is a multiple of 512 bits, then appending the message length. It initializes buffers and processes the message in 512-bit blocks using four rounds of 16 operations each, applying different functions to update the buffers. The final buffer values become the MD5 digest. It is commonly used to verify file integrity but is now considered insecure due to possible hash collisions.Cryptographic Hash Functions in Security.pptx



Cryptographic Hash Functions in Security.pptxVivekanandaGN1
Ėý
Cryptographic Hash Functions in SecurityMessage Digest Algorithm 4 cryptography.pptx



Message Digest Algorithm 4 cryptography.pptxmchod4461
Ėý
Message digest 4 is the topic related to cryptography Secure hashing algorithm



Secure hashing algorithmKarteek Paruchuri
Ėý
This document discusses secure hashing algorithms used for authentication rather than encryption. It provides an overview of the requirements for authentication including preventing masquerading, content modification, sequence modification, and timing modification. It then describes the basic theory behind hashing including producing a message digest, ensuring it is computationally infeasible to find two messages with the same digest, and being unable to recreate a message from its digest. Finally, it details the framework of the SHA-1 hashing algorithm including preprocessing the message, initializing buffers, processing the message in blocks, and outputting the final digest.SHA



SHASubashiniRathinavel
Ėý
The Secure Hash Algorithm (SHA) was developed by NIST and NSA to generate a 160-bit message digest from inputs of less than 264 bits. SHA-1 works by padding the input message, appending the length, dividing into 512-bit blocks, initializing chain variables, and processing each block through 80 iterations involving logical, shift, and addition operations to update the variables. Each iteration uses a constant and the previous output to calculate the next output in order to make it difficult to determine the input from the digest or find colliding messages. Later versions such as SHA-256 increased security by lengthening the digest and number of steps.MD5 - Hash Functions & RIPEMD160



MD5 - Hash Functions & RIPEMD160chuxuantinh
Ėý
MD5 and RIPEMD-160 are cryptographic hash functions used to verify data integrity.
MD5 takes an input of arbitrary length and produces a 128-bit hash value. It operates by padding the input, appending the length, initializing buffers, and processing the message in 512-bit blocks through four rounds of compression.
RIPEMD-160 produces a 160-bit hash value. Like MD5, it pads and appends the length before initializing buffers and processing the message in 512-bit blocks. However, it uses two parallel lines of five rounds each consisting of 10 steps to compress the input. Both functions aim to make collisions difficult by using shifting and logical operations in their compression functions.Recently uploaded (20)
The Asia- Pacific Islands Rural Advisory Services



The Asia- Pacific Islands Rural Advisory ServicesFrancois Stepman
Ėý
Presentation by Dr. Rasheed Sulaiman V, Director, Centre for Research on Innovation and Science Policy (CRISP),
on The Asia- Pacific Islands Rural Advisory Services.
10 March 2025. Brussels. In person meeting of the Collective Action Agroecology. This is a pre-event before the DeSIRA-Lift conference: Boosting agrifood research and innovation cooperation for impact at scale (11-13 March 2025 in Brussels).Brazil: promoting participatory plant breeding through the establishment of a...



Brazil: promoting participatory plant breeding through the establishment of a...Francois Stepman
Ėý
14 March 2025. Investing in innovative solutions for nutrition-sensitive agriculture"
Rikke Olivera Grand and Cynthia Torres de Toledo Machado presented the nutrition-climate-biodiversity nexus through the innovative approaches emerging from the Global Programme for Small-scale Agroecology Producers and Sustainable Food Systems Transformation (GP-SAEP) showcasing the experience from Brazil promoting participatory plant breeding through the establishment of agroecological corridors fostering the development of new corn varieties.Causes and prevention of perinatal mortality rate.pptx



Causes and prevention of perinatal mortality rate.pptxBenTennyson31
Ėý
causes and prevention of perinatal mortalityThe Global NARS Consortium (GNC) supported by: Transforming the Agri-Food Sys...



The Global NARS Consortium (GNC) supported by: Transforming the Agri-Food Sys...Francois Stepman
Ėý
11-13 March 2025. Brussels. Conference on ÂīBoosting agrifood research and innovation cooperation for impact at scale
Day 3: GFAiR, innovating and operationalising agile impact partnership at scale
Global Forum on Agricultural Research and Innovation (GFAiR) and AgriCord presented and discussed the Global NARS Consortium (GNC) with (funding) partners. With the participation of EC DG INTPA, APAARI, EFARD, FARA, sub-regional R&I Organisations and NARS in Africa, and CGIAR.
Ravi Khetarpal, Executive Secretary of APAARIAgroecology based research & innovation for food system transitions



Agroecology based research & innovation for food system transitionsFrancois Stepman
Ėý
11-13 March 2025. Brussels. Conference on ÂīBoosting agrifood research and innovation cooperation for impact at scale
SESSION 6 Agroecology based research & innovation for food system transitions
Presentation by Oliver Oliveros, Agroecology Coalition ScreenHunter pro crack with serial free Download 2025



ScreenHunter pro crack with serial free Download 2025nidah52605
Ėý
ScreenHunter is a popular screen capture software that enables users to take screenshots, record screen activity, and save them in various formats. Itâs widely used for creating tutorials, capturing website content, taking snapshots of documents, or simply grabbing content from your screen for personal or professional use. ScreenHunter offers several versions with varying levels of functionality, from basic screenshot-taking features to more advanced tools for recording and editing images.
Please Copy This Direct Download Link Belowð
https://profreecracks.com/download-setup/
âââââNote: >> Please copy the link and paste it into Google New Tab now Download link
Key Features of ScreenHunter:
Capture Screenshots:
Full Screen Capture: Capture the entire screen, including all active windows.
Active Window Capture: Capture a specific application window while excluding the rest of the screen.Warman Robot Challenge Project Plan.pptx



Warman Robot Challenge Project Plan.pptxAvikBhattacharya25
Ėý
Its a plan for Warman Robot Challenge, giving a brief overview of the planning processEU R&I landscape and its instruments (relevance, success, limits)



EU R&I landscape and its instruments (relevance, success, limits)Francois Stepman
Ėý
11-13 March 2025. Brussels. Conference on ÂīBoosting agrifood research and innovation cooperation for impact at scale
SESSION 3: Frame the EU R&I landscape and its instruments (relevance, success, limits)
This session illustrated the EU capacities to collaborate with partners and to evolve to better address the challenges, with key lessons learnt and recommendations for the future. The panel focused on Europe and Africa partnerships.
by Bernard Mallet: CIRAD, CEA-FIRSTUpdated treatment of hypothyroidism ,diagnosis



Updated treatment of hypothyroidism ,diagnosisMohammed Ahmed Bamashmos
Ėý
Updated treatment of hypothyroidism Ciwara Capital: Innovative fund owned and managed by Africans living in Europ...



Ciwara Capital: Innovative fund owned and managed by Africans living in Europ...Francois Stepman
Ėý
14 March 2025. Investing in innovative solutions for nutrition-sensitive agriculture"
Alima Keita, Co-founder Ciwara Capital: She shared the experience of an innovative fund owned and managed by Africans living in Europe to support small and medium enterprises in their origin country.Biography of Bradley Liebe



Biography of Bradley LiebeBradley Liebe
Ėý
Bradley Liebe has established himself as a leader with over twenty years of extensive experience in non-profit and faith-based sectors. Originally from Wisconsin, his journey has led him from serving as a Student Ministries Director in Fort Myers, Florida, to holding influential positions such as Executive Pastor and COO in Fresno, California. His broad expertise encompasses team leadership, project management, and financial planning, and he is also a captivating public speaker and coach known for his ability to engage and inspire audiences worldwide.Research Survey Practical research seinor highschool



Research Survey Practical research seinor highschoolgamershadow621
Ėý
Senior HIghschool Research surveyPMO šÝšÝßĢs for Process Improvement in all environments



PMO šÝšÝßĢs for Process Improvement in all environmentsAnnamalai Ramanathan
Ėý
Speaks to good practices for Program Management Supporting innovations at scale through relevant funding mechanisms and markets



Supporting innovations at scale through relevant funding mechanisms and marketsFrancois Stepman
Ėý
11-13 March 2025. Brussels. Conference on ÂīBoosting agrifood research and innovation cooperation for impact at scale
Extract of Day 2
How to support innovation at scale for productive, inclusive and sustainable food system transformation and potential contribution of research
Session 2: Supporting innovations at scale through relevant funding mechanisms and markets: Elise Juguet, Horus Development Finance History, diversity, and social class mmm



History, diversity, and social class mmmMarhamahRazak1
Ėý
2. History, diversity, and social class (1).pptxExploring Agroecological Principles in Practice: Preliminary Survey Results f...



Exploring Agroecological Principles in Practice: Preliminary Survey Results f...Francois Stepman
Ėý
Exploring Agroecological Principles in Practice: Preliminary Survey Results from the FO-RI Program - Stockholm Environment Institute (SEI), Swedish University of Agricultural Sciences (SLU) & AgriCord - Presentation by
by Aziliz LE ROUZO of SEI
10 March 2025. Brussels. In person meeting of the Collective Action Agroecology. This is a pre-event before the DeSIRA-Lift conference: Boosting agrifood research and innovation cooperation for impact at scale (11-13 March 2025 in Brussels).MD5
- 1. MD5 Message Digest Algorithm KHAWAJA ROKHAM TARIQ C O M P U T E R S C I E N C E D E P A R T M E N T U N V E R S I T Y O F K O T L I A Z A D A N D J A M M U K A S H M I R
- 2. Content Introduction Hashing knowledge MD5 Algorithm Structure Implementation Steps Performance MD5 vs. SHA
- 3. Hashing knowledge It is a mathematical function that convert a numerical values into another compressed numerical values. Output will always of fixed length. Same message have same particular same output.
- 4. Introduction MD5 algorithm was developed by Professor Ronald L. Rivest in 1991. MD5 message-digest algorithm takes as input a message of arbitrary length and produces as output a 128-bit "fingerprint" or "message digest" of the input. The MD5 algorithm is intended for digital signature applications, where a large file must be "compressed" in a secure manner before being encrypted with a private (secret) key under a public-key cryptosystem such as RSA.
- 6. Original message Add padding Original message Add padding Add length 512 bits blocks 512 bits blocks
- 7. Implementation Steps Step1 Append padding bits The input message is "padded" (extended) so that its length (in bits) equals to 448 mod 512. Padding is always performed, even if the length of the message is already 448 mod 512. Padding is performed as follows: a single "1" bit is appended to the message, and then "0" bits are appended so that the length in bits of the padded message becomes congruent to 448 mod 512. At least one bit and at most 512 bits are appended.
- 8. Padding is done such that the total length is 64bit < exact multiple of 512. Suppose original message is 1000bit. Now check exact multiple of 512 Total 1000bits 512*2=1024 which is not good. 512*3=1536 Now sub 64 from 1536 1536-64=1472 We need to add 472 bits more for calculation. Also 1472 is 64bit less than exact multiple of 512.
- 9. Append the original length before padding. We use modulus 64 operation. Get exact multiple of 512 after 64 bits adding. Now create blocks according to bit length. Before padding 1000bits. Now apply mod64. 1000] length 264
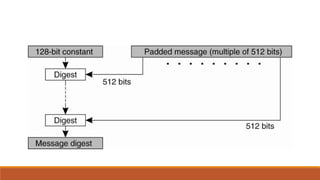
- 10. Implementation Steps Step2. Append length A 64-bit representation of the length of the message is appended to the result of step1. If the length of the message is greater than 2^64, only the low-order 64 bits will be used. The resulting message (after padding with bits and with b) has a length that is an exact multiple of 512 bits. The input message will have a length that is an exact multiple of 16 (32-bit) words.
- 11. Processing blocks Copy 4-chaining blocks into small corresponding variables. Dividing 512 bit block into 16(32bits blocks) Apply four rounds. 16 sub blocks Constant (t) One round a b c d
- 12. Implementation Steps Step3. Initialize MD buffer A four-word buffer (A, B, C, D) is used to compute the message digest. Each of A, B, C, D is a 32-bit register. These registers are initialized to the following values in hexadecimal, low-order bytes first): word A: 01 23 45 67 word B: 89 ab cd ef word C: fe dc ba 98 word D: 76 54 32 10
- 13. Intinliaze 4-Chaining varbles 32 bits Name A,B,C,D. Values in hexadecimal.
- 14. Implementation Steps Step4. Process message in 16-word blocks Four functions will be defined such that each function takes an input of three 32-bit words and produces a 32-bit word output. F (X, Y, Z) = XY or not (X) Z G (X, Y, Z) = XZ or Y not (Z) H (X, Y, Z) = X xor Y xor Z I (X, Y, Z) = Y xor (X or not (Z))
- 15. Implementation Steps Round 1. [abcd k s i] denote the operation a = b + ((a + F (b, c, d) + X [k] + T [i]) <<< s). Do the following 16 operations. [ABCD 0 7 1] [DABC 1 12 2] [CDAB 2 17 3] [BCDA 3 22 4] [ABCD 4 7 5] [DABC 5 12 6] [CDAB 6 17 7] [BCDA 7 22 8] [ABCD 8 7 9] [DABC 9 12 10] [CDAB 10 17 11] [BCDA 11 22 12] [ABCD 12 7 13] [DABC 13 12 14] [CDAB 14 17 15] [BCDA 15 22 16]
- 16. Single MD5 operation mathmeticaly defined like this: a=b+((a+process,p(b,c,d)+M[i]+T[k]))<<shift M[i]=message is i. T[k]=constant is k. <<shift=circular shift





