Memory Handling and Garbage Collection in Python
Download as PPTX, PDF2 likes565 views
The document discusses memory handling and garbage collection in Python. It describes the three categories of memory for data storage: static, run-time stack, and heap. Problems can occur with heap storage in the form of memory leaks and dangling pointers. Garbage collection aims to solve these issues by identifying inaccessible blocks of storage and returning them to the free list. The three major approaches to automated garbage collection are reference counting, mark-sweep, and copy collection.
1 of 16
Downloaded 35 times











Recommended
Memory Management in Python



Memory Management in PythonVijay Kumar Bagavath Singh
╠²
The talk will cover the following topics: How Reference Counting Works, Issues with Reference Counting , Cycle Detection and GC, Useful Third Party Modules. Not many people really require to know how Python manages memory. But it is kind of nice to know how things work under the hood.Girls Go IT -- Day 6 Training 2 -- Bootstrap integration



Girls Go IT -- Day 6 Training 2 -- Bootstrap integrationMihai Iachimovschi
╠²
More bootstrap. Integrating to Python Flask.Girls Go IT -- Day 6 Training 3 -- Back to Python



Girls Go IT -- Day 6 Training 3 -- Back to PythonMihai Iachimovschi
╠²
A brief introduction to Object Oriented Programming using Python.Python GC



Python GCdelimitry
╠²
║▌║▌▀Żs for presentation about Python GC (Garbage Collector) and memory management in Python (CPython version 2.7)A History of Modern Garbage Collection Techniques



A History of Modern Garbage Collection TechniquesSasha Goldshtein
╠²
In this session we cover the variety of garbage collection algorithms, with a strong focus on tracing garbage collectors. We discuss concurrent and parallel GC, and novel approaches such as Azul's Completely Concurrent Compacting Collector (C4) and IBM's Metronome real-time GC.Django Interview Questions and Answers



Django Interview Questions and AnswersPython Devloper
╠²
Django is a open source framework written in Python, was designed to save Web developers time and money by promoting the idea of reusing code and avoiding replication. As with any language, programmers interviewing for a job involving Django are going to face a series of specialized questions.Ram & rom



Ram & romAhsan Rafiq
╠²
This document provides information about RAM and ROM, two types of computer memory. RAM (Random Access Memory) is volatile memory that allows reading and writing and is used to run applications, while ROM (Read Only Memory) is non-volatile and only allows reading to store programs for booting the computer. Key differences between RAM and ROM are outlined, such as RAM being faster but losing data when powered off, while ROM retains data when powered off but only allows writing once. Characteristics of each type of memory are also described.Memory Management In Python The Basics



Memory Management In Python The BasicsNina Zakharenko
╠²
This document summarizes the basics of memory management in Python. It discusses key concepts like variables, objects, references, and reference counting. It explains how Python uses reference counting with generational garbage collection to manage memory and clean up unused objects. The document also covers potential issues with reference counting like cyclic references and threads, and how the global interpreter lock impacts multi-threading in Python.No-no-no approach



No-no-no approachTimofey Golovin
╠²
The document outlines a startup idea focused on problem-solving that will conquer the world. It discusses different approaches to problem-solving, including through fun and beauty. However, the idea comes with challenges, as every problem-solving solution would need to be both fun and beautiful. By the end, the document expresses wanting to end the discussion.GALNT11 as a new molecular marker in chronic lymphocytic leukemia



GALNT11 as a new molecular marker in chronic lymphocytic leukemiaDiana Agudelo
╠²
This document summarizes a study on using GALNT11 as a new molecular marker for chronic lymphocytic leukemia (CLL). The study analyzed blood samples from CLL patients and healthy controls to examine GALNT11 expression levels. Results showed that GALNT11 was highly expressed in CLL cells and cancer markers TN antigen and sialyl-TN antigen. This suggests GALNT11 could serve as an effective diagnostic marker for CLL. The conclusions were that GALNT11 expression is specific to CLL cells and may help develop more targeted diagnostic tests and treatment approaches for this type of leukemia.Kossuth Palo Alto Economic Development Crop Jan-June Newsletter



Kossuth Palo Alto Economic Development Crop Jan-June NewsletterMid Iowa Growth Partnership
╠²
Walker Chiropractic & Wellness, a new chiropractic business, has opened two locations in Kossuth County. Owned and operated by husband and wife Dr. Jacob Walker and Dr. Rebecca Walker, the practice offers chiropractic treatment and wellness services. Woodford Equipment, an agricultural equipment dealer in Emmetsburg, has experienced rapid growth in its first two years, expanding its product offerings and developing an international customer base. Cozzini, formerly known as Algona Food Equipment Company, is a global manufacturer of food processing equipment headquartered in Algona.MUN U.K.



MUN U.K.anatfurber
╠²
The United Kingdom was formed through the union of England, Scotland, and Ireland over centuries. It is currently made up of England, Scotland, Wales, and Northern Ireland. The UK has a constitutional monarchy form of government and is a highly developed country with a strong economy focused on services, manufacturing, and trade. Its capital is London and it has strong cultural influence globally in areas like entertainment and scientific research.BACTERIAL INFECTION AND IMMUNE SYSTEM RESPONSE



BACTERIAL INFECTION AND IMMUNE SYSTEM RESPONSEDiana Agudelo
╠²
This document discusses bacterial infections and the immune system response. It begins with an introduction comparing prokaryotic and eukaryotic cells, noting that bacteria can be pathogenic or non-pathogenic to the human body. It then discusses typhoid fever caused by Salmonella bacteria, noting that immune cells try to contain the bacteria but some escape. The document also discusses Group A Streptococcus bacteria and the steps of how it causes necrotizing fasciitis, or flesh-eating disease. Specifically, it releases toxins that inhibit protein synthesis and the human cells increase asparagine production in response, which the bacteria uses to increase virulence. Finally, the student observes that asparaginase, which breaksGWC14: Toby Beresford - "Zoopla Gravity: Orbit strategy"



GWC14: Toby Beresford - "Zoopla Gravity: Orbit strategy"gamificationworldcongress
╠²
The document discusses how Zoopla uses gamification and an engagement platform called "Property Power 100" to keep customers engaged with their brand through weekly performance tracking and individual scores. This orbit strategy is said to attract and keep customers engaged with the brand beyond just purchases, making future purchases easier.GWC14: Carlos Guardiola - "Who gamifies the gamificators?



GWC14: Carlos Guardiola - "Who gamifies the gamificators?gamificationworldcongress
╠²
Medianet Software is an IT company that has been experimenting with gamification internally since 2012. They have run several gamification campaigns with their employees to learn how to best apply gamification principles and increase employee engagement. Some of their key lessons learned include not wasting time trying to engage everyone, respecting employee status and decision making, and ensuring objectives, metrics, and budgets are in place for any gamification initiative. Their internal gamification platform called Maiap allows employees to earn points, badges, and purchase items by participating in projects and skills endorsements.GWC14: Robert Figueras - "Panzer Chocolate: Play the film!"



GWC14: Robert Figueras - "Panzer Chocolate: Play the film!"gamificationworldcongress
╠²
The document describes an interactive transmedia horror film project called "Panzer Chocolate". It includes an interactive film that uses an app to provide additional content during and after the screening. It also includes additional transmedia elements like a comic, novel, and mobile series that expand upon the story. The goal is to create an immersive experience for audiences and explore new models of interactive storytelling across multiple platforms.Function points and elements



Function points and elementsBusi Sreedhaar Reddy
╠²
The document defines various elements of function point analysis including:
1. File Type References (FTRs), Internal Logical Files (ILFs), External Interface Files (EIFs), External Input (EI), External Output (EO), External Inquiry (EQ), and General System Characteristics (GSCs) which are the main components measured in a function point analysis.
2. It provides descriptions of each component - FTRs refer to files referenced by transactions, ILFs and EIFs are files stored internally or externally, EI involves data entering the system, EO is data exiting, and EQ retrieves data without updates.
3. GSCs consider other factors like architecture and performance thatGWC14: Isidro Rodrigo - "The boardgames that HR people [should] play"![GWC14: Isidro Rodrigo - "The boardgames that HR people [should] play"](https://cdn.slidesharecdn.com/ss_thumbnails/isidrorodrigogwc14-140703083354-phpapp01-thumbnail.jpg?width=560&fit=bounds)
![GWC14: Isidro Rodrigo - "The boardgames that HR people [should] play"](https://cdn.slidesharecdn.com/ss_thumbnails/isidrorodrigogwc14-140703083354-phpapp01-thumbnail.jpg?width=560&fit=bounds)
![GWC14: Isidro Rodrigo - "The boardgames that HR people [should] play"](https://cdn.slidesharecdn.com/ss_thumbnails/isidrorodrigogwc14-140703083354-phpapp01-thumbnail.jpg?width=560&fit=bounds)
![GWC14: Isidro Rodrigo - "The boardgames that HR people [should] play"](https://cdn.slidesharecdn.com/ss_thumbnails/isidrorodrigogwc14-140703083354-phpapp01-thumbnail.jpg?width=560&fit=bounds)
GWC14: Isidro Rodrigo - "The boardgames that HR people [should] play"gamificationworldcongress
╠²
This document discusses potential games that HR people could play. It mentions games like Pixel Dungeon which is a rogue-like game focused on exploration. It also discusses a potential "Learning Dungeon" game for developing skills through voluntary challenge within a guild structure. Finally, it proposes a "Quest" mechanic for a game that could focus on relatedness, meaning, competence and autonomy while tracking business metrics.Days remembered



Days rememberedThe Baltimore Sun
╠²
The panel discussion featured four individuals associated with The Baltimore Sun - two photographers, a director of photography, and a reporter - discussing iconic photographs from the newspaper's history. The photographers shared stories from their careers capturing memorable images for The Sun. The director of photography and reporter provided historical context for the impact of photographs published in the newspaper.Katharina reiss



Katharina reissnameless422
╠²
Katharina Reiss was a German linguist and translation scholar born in 1923. She is known for developing a text typology and defending the skopos theory of translation. Reiss's text typology categorizes texts as informative, expressive, operative, or audio medial based on their primary communicative purpose. The skopos theory, which Reiss supported, focuses on translation as an activity with an intended purpose and target audience in a given context.Fgd medan



Fgd medanArdi Novra
╠²
Dokumen membahas potensi integrasi usaha ternak sapi dengan perkebunan kelapa sawit BUMN. Terdapat peluang kerjasama antara BUMN perkebunan dengan pihak lain seperti BULOG maupun kelompok peternak lokal untuk meningkatkan produktivitas dan pemasaran daging sapi. Kerjasama dapat dilakukan melalui kemitraan baik di sektor input maupun output usaha ternak sapi.Elao integral presentation



Elao integral presentationElenaSoto75
╠²
The document discusses an integral computer-assisted language learning (ELAO Integral) program. It is taught by Alba Magdalena Sandoval Andrade and a team of teachers. The ELAO Integral program integrates all key aspects of technology into the process of studying a foreign language. For example, it describes the evolution of CALL from the 1970s focusing on grammar and drills, to the 1980s emphasizing communication, to the 21st century using multimedia and the internet for content-based and authentic discourse learning with a focus on accuracy, fluency and agency.Tugas agama



Tugas agamaSyarif Utsman
╠²
Ringkasan dokumen tersebut adalah:
1. Dokumen tersebut membahas tentang kerangka dasar ajaran Islam yang mencakup tiga bagian pokok yaitu aqidah, syariat, dan akhlak.
2. Bagian pertama membahas tentang pengertian dan dalil-dalil aqidah sebagai bagian pokok iman yang harus dianut.
3. Bagian selanjutnya membahas tentang pengertian dan dalil syariat sebagai aturan-aturan yang2011 Fort Dodge & Webster County Iowa Laborshed Summary



2011 Fort Dodge & Webster County Iowa Laborshed SummaryMid Iowa Growth Partnership
╠²
This laborshed summary covers Webster County Iowa and its largest city, Fort Dodge. It was completed in 2011.Data Validation for Business Continuity Planning



Data Validation for Business Continuity PlanningPOOJA MEHTA
╠²
This document proposes a metadata-driven and rule-based system for validating data across multiple data sources for business continuity planning purposes. The system has three main components - a rules handler to manage validation rules, a communication handler to distribute rules and collect results, and a data sources handler where validation is performed. The conceptual architecture is distributed with rules objects sent to each data source and results returned to a central dispatcher. The system was tested on real data sets and proved to be adaptable, faster than centralized validation, scalable, and protects sensitive data.Otp authentication scheme based on ECC



Otp authentication scheme based on ECCPOOJA MEHTA
╠²
This document proposes a one-time password (OTP) authentication scheme based on elliptic curves for Internet of Things (IoT) devices. It uses identity-based elliptic curve cryptography to design an OTP generation scheme based on Lamport's OTP algorithm. This proposed scheme requires fewer resources than existing schemes due to using a smaller key size and less infrastructure. Future work could explore using different prime numbers for encryption in satellite communications up to 128 bits. The document provides background on elliptic curves, Diffie-Hellman key exchange, and references for further reading.Fault tolerance in Big Data



Fault tolerance in Big DataPOOJA MEHTA
╠²
This document summarizes a research paper about fault tolerance techniques in big data tools. The paper discusses strategies for fault tolerance that include data duplication, checkpoints, and automatic recovery. It examines fault tolerance in Hadoop and MongoDB. The document reviews several other papers on enhancing fault tolerance in Hadoop clusters and the architecture and fault tolerance of geographically distributed Hadoop clusters. A proposed solution discusses providing fault tolerance using commercial off-the-shelf technology. The conclusion notes that critical components may become unavailable and their states impossible to reproduce due to environmental constraints and special operating systems.More Related Content
Viewers also liked (19)
No-no-no approach



No-no-no approachTimofey Golovin
╠²
The document outlines a startup idea focused on problem-solving that will conquer the world. It discusses different approaches to problem-solving, including through fun and beauty. However, the idea comes with challenges, as every problem-solving solution would need to be both fun and beautiful. By the end, the document expresses wanting to end the discussion.GALNT11 as a new molecular marker in chronic lymphocytic leukemia



GALNT11 as a new molecular marker in chronic lymphocytic leukemiaDiana Agudelo
╠²
This document summarizes a study on using GALNT11 as a new molecular marker for chronic lymphocytic leukemia (CLL). The study analyzed blood samples from CLL patients and healthy controls to examine GALNT11 expression levels. Results showed that GALNT11 was highly expressed in CLL cells and cancer markers TN antigen and sialyl-TN antigen. This suggests GALNT11 could serve as an effective diagnostic marker for CLL. The conclusions were that GALNT11 expression is specific to CLL cells and may help develop more targeted diagnostic tests and treatment approaches for this type of leukemia.Kossuth Palo Alto Economic Development Crop Jan-June Newsletter



Kossuth Palo Alto Economic Development Crop Jan-June NewsletterMid Iowa Growth Partnership
╠²
Walker Chiropractic & Wellness, a new chiropractic business, has opened two locations in Kossuth County. Owned and operated by husband and wife Dr. Jacob Walker and Dr. Rebecca Walker, the practice offers chiropractic treatment and wellness services. Woodford Equipment, an agricultural equipment dealer in Emmetsburg, has experienced rapid growth in its first two years, expanding its product offerings and developing an international customer base. Cozzini, formerly known as Algona Food Equipment Company, is a global manufacturer of food processing equipment headquartered in Algona.MUN U.K.



MUN U.K.anatfurber
╠²
The United Kingdom was formed through the union of England, Scotland, and Ireland over centuries. It is currently made up of England, Scotland, Wales, and Northern Ireland. The UK has a constitutional monarchy form of government and is a highly developed country with a strong economy focused on services, manufacturing, and trade. Its capital is London and it has strong cultural influence globally in areas like entertainment and scientific research.BACTERIAL INFECTION AND IMMUNE SYSTEM RESPONSE



BACTERIAL INFECTION AND IMMUNE SYSTEM RESPONSEDiana Agudelo
╠²
This document discusses bacterial infections and the immune system response. It begins with an introduction comparing prokaryotic and eukaryotic cells, noting that bacteria can be pathogenic or non-pathogenic to the human body. It then discusses typhoid fever caused by Salmonella bacteria, noting that immune cells try to contain the bacteria but some escape. The document also discusses Group A Streptococcus bacteria and the steps of how it causes necrotizing fasciitis, or flesh-eating disease. Specifically, it releases toxins that inhibit protein synthesis and the human cells increase asparagine production in response, which the bacteria uses to increase virulence. Finally, the student observes that asparaginase, which breaksGWC14: Toby Beresford - "Zoopla Gravity: Orbit strategy"



GWC14: Toby Beresford - "Zoopla Gravity: Orbit strategy"gamificationworldcongress
╠²
The document discusses how Zoopla uses gamification and an engagement platform called "Property Power 100" to keep customers engaged with their brand through weekly performance tracking and individual scores. This orbit strategy is said to attract and keep customers engaged with the brand beyond just purchases, making future purchases easier.GWC14: Carlos Guardiola - "Who gamifies the gamificators?



GWC14: Carlos Guardiola - "Who gamifies the gamificators?gamificationworldcongress
╠²
Medianet Software is an IT company that has been experimenting with gamification internally since 2012. They have run several gamification campaigns with their employees to learn how to best apply gamification principles and increase employee engagement. Some of their key lessons learned include not wasting time trying to engage everyone, respecting employee status and decision making, and ensuring objectives, metrics, and budgets are in place for any gamification initiative. Their internal gamification platform called Maiap allows employees to earn points, badges, and purchase items by participating in projects and skills endorsements.GWC14: Robert Figueras - "Panzer Chocolate: Play the film!"



GWC14: Robert Figueras - "Panzer Chocolate: Play the film!"gamificationworldcongress
╠²
The document describes an interactive transmedia horror film project called "Panzer Chocolate". It includes an interactive film that uses an app to provide additional content during and after the screening. It also includes additional transmedia elements like a comic, novel, and mobile series that expand upon the story. The goal is to create an immersive experience for audiences and explore new models of interactive storytelling across multiple platforms.Function points and elements



Function points and elementsBusi Sreedhaar Reddy
╠²
The document defines various elements of function point analysis including:
1. File Type References (FTRs), Internal Logical Files (ILFs), External Interface Files (EIFs), External Input (EI), External Output (EO), External Inquiry (EQ), and General System Characteristics (GSCs) which are the main components measured in a function point analysis.
2. It provides descriptions of each component - FTRs refer to files referenced by transactions, ILFs and EIFs are files stored internally or externally, EI involves data entering the system, EO is data exiting, and EQ retrieves data without updates.
3. GSCs consider other factors like architecture and performance thatGWC14: Isidro Rodrigo - "The boardgames that HR people [should] play"![GWC14: Isidro Rodrigo - "The boardgames that HR people [should] play"](https://cdn.slidesharecdn.com/ss_thumbnails/isidrorodrigogwc14-140703083354-phpapp01-thumbnail.jpg?width=560&fit=bounds)
![GWC14: Isidro Rodrigo - "The boardgames that HR people [should] play"](https://cdn.slidesharecdn.com/ss_thumbnails/isidrorodrigogwc14-140703083354-phpapp01-thumbnail.jpg?width=560&fit=bounds)
![GWC14: Isidro Rodrigo - "The boardgames that HR people [should] play"](https://cdn.slidesharecdn.com/ss_thumbnails/isidrorodrigogwc14-140703083354-phpapp01-thumbnail.jpg?width=560&fit=bounds)
![GWC14: Isidro Rodrigo - "The boardgames that HR people [should] play"](https://cdn.slidesharecdn.com/ss_thumbnails/isidrorodrigogwc14-140703083354-phpapp01-thumbnail.jpg?width=560&fit=bounds)
GWC14: Isidro Rodrigo - "The boardgames that HR people [should] play"gamificationworldcongress
╠²
This document discusses potential games that HR people could play. It mentions games like Pixel Dungeon which is a rogue-like game focused on exploration. It also discusses a potential "Learning Dungeon" game for developing skills through voluntary challenge within a guild structure. Finally, it proposes a "Quest" mechanic for a game that could focus on relatedness, meaning, competence and autonomy while tracking business metrics.Days remembered



Days rememberedThe Baltimore Sun
╠²
The panel discussion featured four individuals associated with The Baltimore Sun - two photographers, a director of photography, and a reporter - discussing iconic photographs from the newspaper's history. The photographers shared stories from their careers capturing memorable images for The Sun. The director of photography and reporter provided historical context for the impact of photographs published in the newspaper.Katharina reiss



Katharina reissnameless422
╠²
Katharina Reiss was a German linguist and translation scholar born in 1923. She is known for developing a text typology and defending the skopos theory of translation. Reiss's text typology categorizes texts as informative, expressive, operative, or audio medial based on their primary communicative purpose. The skopos theory, which Reiss supported, focuses on translation as an activity with an intended purpose and target audience in a given context.Fgd medan



Fgd medanArdi Novra
╠²
Dokumen membahas potensi integrasi usaha ternak sapi dengan perkebunan kelapa sawit BUMN. Terdapat peluang kerjasama antara BUMN perkebunan dengan pihak lain seperti BULOG maupun kelompok peternak lokal untuk meningkatkan produktivitas dan pemasaran daging sapi. Kerjasama dapat dilakukan melalui kemitraan baik di sektor input maupun output usaha ternak sapi.Elao integral presentation



Elao integral presentationElenaSoto75
╠²
The document discusses an integral computer-assisted language learning (ELAO Integral) program. It is taught by Alba Magdalena Sandoval Andrade and a team of teachers. The ELAO Integral program integrates all key aspects of technology into the process of studying a foreign language. For example, it describes the evolution of CALL from the 1970s focusing on grammar and drills, to the 1980s emphasizing communication, to the 21st century using multimedia and the internet for content-based and authentic discourse learning with a focus on accuracy, fluency and agency.Tugas agama



Tugas agamaSyarif Utsman
╠²
Ringkasan dokumen tersebut adalah:
1. Dokumen tersebut membahas tentang kerangka dasar ajaran Islam yang mencakup tiga bagian pokok yaitu aqidah, syariat, dan akhlak.
2. Bagian pertama membahas tentang pengertian dan dalil-dalil aqidah sebagai bagian pokok iman yang harus dianut.
3. Bagian selanjutnya membahas tentang pengertian dan dalil syariat sebagai aturan-aturan yang2011 Fort Dodge & Webster County Iowa Laborshed Summary



2011 Fort Dodge & Webster County Iowa Laborshed SummaryMid Iowa Growth Partnership
╠²
This laborshed summary covers Webster County Iowa and its largest city, Fort Dodge. It was completed in 2011.More from POOJA MEHTA (7)
Data Validation for Business Continuity Planning



Data Validation for Business Continuity PlanningPOOJA MEHTA
╠²
This document proposes a metadata-driven and rule-based system for validating data across multiple data sources for business continuity planning purposes. The system has three main components - a rules handler to manage validation rules, a communication handler to distribute rules and collect results, and a data sources handler where validation is performed. The conceptual architecture is distributed with rules objects sent to each data source and results returned to a central dispatcher. The system was tested on real data sets and proved to be adaptable, faster than centralized validation, scalable, and protects sensitive data.Otp authentication scheme based on ECC



Otp authentication scheme based on ECCPOOJA MEHTA
╠²
This document proposes a one-time password (OTP) authentication scheme based on elliptic curves for Internet of Things (IoT) devices. It uses identity-based elliptic curve cryptography to design an OTP generation scheme based on Lamport's OTP algorithm. This proposed scheme requires fewer resources than existing schemes due to using a smaller key size and less infrastructure. Future work could explore using different prime numbers for encryption in satellite communications up to 128 bits. The document provides background on elliptic curves, Diffie-Hellman key exchange, and references for further reading.Fault tolerance in Big Data



Fault tolerance in Big DataPOOJA MEHTA
╠²
This document summarizes a research paper about fault tolerance techniques in big data tools. The paper discusses strategies for fault tolerance that include data duplication, checkpoints, and automatic recovery. It examines fault tolerance in Hadoop and MongoDB. The document reviews several other papers on enhancing fault tolerance in Hadoop clusters and the architecture and fault tolerance of geographically distributed Hadoop clusters. A proposed solution discusses providing fault tolerance using commercial off-the-shelf technology. The conclusion notes that critical components may become unavailable and their states impossible to reproduce due to environmental constraints and special operating systems.Computer organization and architecture



Computer organization and architecturePOOJA MEHTA
╠²
This document provides an introduction to computer architecture. It discusses how computer architecture defines a computer's capabilities and programming model. It also covers topics like instruction sets, microarchitecture, system design approaches like RISC and CISC, abstraction layers, applications of computer architecture in domains like desktop, server, and embedded computing, and conclusions. References are provided at the end.The optimization and implementation of iptables rules set



The optimization and implementation of iptables rules setPOOJA MEHTA
╠²
The document discusses optimizing iptables rules on Linux. It introduces iptables as a packet filter that operates on the TCP/IP stack. It covers the iptables framework and working, and describes iptables rule structure. The main topic is optimizing and realizing the rule set by eliminating duplication, improving filtration efficiency with algorithms, and enhancing system performance and network throughput.Deadlock Detection



Deadlock DetectionPOOJA MEHTA
╠²
The document evaluates and compares the performance of three deadlock detection algorithms: fully centralized, partially distributed, and fully distributed. The partially distributed algorithm provides the best performance. It uses fixed size messages and maintains allocation, local transaction, and resource tables to detect deadlocks. The evaluation found that the partially distributed algorithm uses less time and overhead for detection compared to the other algorithms. The centralized approach had the shortest deadlock lifetime but performed poorly with increased transaction sizes.Network Data Representation



Network Data RepresentationPOOJA MEHTA
╠²
This document evaluates different tools for efficiently encoding and decoding network data representations. It analyzes encoding and decoding techniques used by ASN.1 tools like SNACC, C ASN.1, and ISODE's POSY/PEPY. Benchmark results found that C ASN.1 encoders and decoders were the fastest. The conclusion recommends that efficient encoders and decoders must be carefully tuned and optimized to leverage advances in processor and memory speeds.Recently uploaded (20)
Data recovery and Digital evidence controls in digital frensics.pdf



Data recovery and Digital evidence controls in digital frensics.pdfAbhijit Bodhe
╠²
This topic contain information about Data recovery and Digital evidence controls in cyber and digital awarenessINVESTIGATION OF PUEA IN COGNITIVE RADIO NETWORKS USING ENERGY DETECTION IN D...



INVESTIGATION OF PUEA IN COGNITIVE RADIO NETWORKS USING ENERGY DETECTION IN D...csijjournal
╠²
Primary User Emulation Attack (PUEA) is one of the major threats to the spectrum sensing in cognitive
radio networks. This paper studies the PUEA using energy detection that is based on the energy of the
received signal. It discusses the impact of increasing the number of attackers on the performance of
secondary user. Moreover, studying how the malicious user can emulate the Primary User (PU) signal is
made. This is the first analytical method to study PUEA under a different number of attackers. The
detection of the PUEA increases with increasing the number of attackers and decreases when changing the
channel from lognormal to Rayleigh fading.Environmental Product Declaration - Uni Bell



Environmental Product Declaration - Uni BellManishPatel169454
╠²
The Uni-Bell PVC Pipe Association (PVCPA) has published the first North American industry-wide environmental product declaration (EPD) for water and sewer piping, and it has been verified by NSF Sustainability, a division of global public health organization NSF International.Air pollution is contamination of the indoor or outdoor environment by any ch...



Air pollution is contamination of the indoor or outdoor environment by any ch...dhanashree78
╠²
Air pollution is contamination of the indoor or outdoor environment by any chemical, physical or biological agent that modifies the natural characteristics of the atmosphere.
Household combustion devices, motor vehicles, industrial facilities and forest fires are common sources of air pollution. Pollutants of major public health concern include particulate matter, carbon monoxide, ozone, nitrogen dioxide and sulfur dioxide. Outdoor and indoor air pollution cause respiratory and other diseases and are important sources of morbidity and mortality.
WHO data show that almost all of the global population (99%) breathe air that exceeds WHO guideline limits and contains high levels of pollutants, with low- and middle-income countries suffering from the highest exposures.
Air quality is closely linked to the earthŌĆÖs climate and ecosystems globally. Many of the drivers of air pollution (i.e. combustion of fossil fuels) are also sources of greenhouse gas emissions. Policies to reduce air pollution, therefore, offer a win-win strategy for both climate and health, lowering the burden of disease attributable to air pollution, as well as contributing to the near- and long-term mitigation of climate change.
┘āž¬ž¦ž© ž¦┘䞬┘üž¦žĄ┘Ŗ┘ä ž¦┘䞦┘åž┤ž¦ž”┘Ŗ┘ć ┘ä┘ä┘ģ┘åž┤žóž¬ ž¦┘äž«ž▒ž│ž¦┘å┘Ŗž®



┘āž¬ž¦ž© ž¦┘䞬┘üž¦žĄ┘Ŗ┘ä ž¦┘䞦┘åž┤ž¦ž”┘Ŗ┘ć ┘ä┘ä┘ģ┘åž┤žóž¬ ž¦┘äž«ž▒ž│ž¦┘å┘Ŗž®o774656624
╠²
-Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait lets pas
il taille glacis Lieu daily qui les jeutaille pas bill Luc jean ├®cumait il taille Lacis just -Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait lets pas
il taille glacis Lieu daily qui les jeutaille pas bill Luc jean ├®cumait il taille Lacis just-Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait lets pas
il taille glacis Lieu daily qui les jeutaille pas bill Luc jean ├®cumait il taille Lacis just -Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait lets pas
il taille glacis Lieu daily qui les jeutaille pas bill Luc jean ├®cumait il taille Lacis just-Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait letsAI ppt on water jug problem by shivam sharma



AI ppt on water jug problem by shivam sharmaShivamSharma588604
╠²
this ppt is made on the topic of water jug problem.Biases, our brain and software development



Biases, our brain and software developmentMatias Iacono
╠²
Quick presentation about cognitive biases, classic psychological researches and quite new papers that displays how those biases might be impacting software developers.Von karman Equation full derivation .pdf



Von karman Equation full derivation .pdfEr. Gurmeet Singh
╠²
Von karman Equation full derivation
By Er. GURMEET SINGH
G.C.E.T JAMMU
Contact: gurmeet.b.tech@gmail.com
M.tech Transportation Engineering US Patented ReGenX Generator, ReGen-X Quatum Motor EV Regenerative Accelerati...



US Patented ReGenX Generator, ReGen-X Quatum Motor EV Regenerative Accelerati...Thane Heins NOBEL PRIZE WINNING ENERGY RESEARCHER
╠²
Preface: The ReGenX Generator innovation operates with a US Patented Frequency Dependent Load
Current Delay which delays the creation and storage of created Electromagnetic Field Energy around
the exterior of the generator coil. The result is the created and Time Delayed Electromagnetic Field
Energy performs any magnitude of Positive Electro-Mechanical Work at infinite efficiency on the
generator's Rotating Magnetic Field, increasing its Kinetic Energy and increasing the Kinetic Energy of
an EV or ICE Vehicle to any magnitude without requiring any Externally Supplied Input Energy. In
Electricity Generation applications the ReGenX Generator innovation now allows all electricity to be
generated at infinite efficiency requiring zero Input Energy, zero Input Energy Cost, while producing
zero Greenhouse Gas Emissions, zero Air Pollution and zero Nuclear Waste during the Electricity
Generation Phase. In Electric Motor operation the ReGen-X Quantum Motor now allows any
magnitude of Work to be performed with zero Electric Input Energy.
Demonstration Protocol: The demonstration protocol involves three prototypes;
1. Protytpe #1, demonstrates the ReGenX Generator's Load Current Time Delay when compared
to the instantaneous Load Current Sine Wave for a Conventional Generator Coil.
2. In the Conventional Faraday Generator operation the created Electromagnetic Field Energy
performs Negative Work at infinite efficiency and it reduces the Kinetic Energy of the system.
3. The Magnitude of the Negative Work / System Kinetic Energy Reduction (in Joules) is equal to
the Magnitude of the created Electromagnetic Field Energy (also in Joules).
4. When the Conventional Faraday Generator is placed On-Load, Negative Work is performed and
the speed of the system decreases according to Lenz's Law of Induction.
5. In order to maintain the System Speed and the Electric Power magnitude to the Loads,
additional Input Power must be supplied to the Prime Mover and additional Mechanical Input
Power must be supplied to the Generator's Drive Shaft.
6. For example, if 100 Watts of Electric Power is delivered to the Load by the Faraday Generator,
an additional >100 Watts of Mechanical Input Power must be supplied to the Generator's Drive
Shaft by the Prime Mover.
7. If 1 MW of Electric Power is delivered to the Load by the Faraday Generator, an additional >1
MW Watts of Mechanical Input Power must be supplied to the Generator's Drive Shaft by the
Prime Mover.
8. Generally speaking the ratio is 2 Watts of Mechanical Input Power to every 1 Watt of Electric
Output Power generated.
9. The increase in Drive Shaft Mechanical Input Power is provided by the Prime Mover and the
Input Energy Source which powers the Prime Mover.
10. In the Heins ReGenX Generator operation the created and Time Delayed Electromagnetic Field
Energy performs Positive Work at infinite efficiency and it increases the Kinetic Energy of the
system.
Sppu engineering artificial intelligence and data science semester 6th Artif...



Sppu engineering artificial intelligence and data science semester 6th Artif...pawaletrupti434
╠²
Sppu University Third year AI&DS Artificial Neural Network unit 1Helium Boosting & Decanting With Hydro Test Machine



Helium Boosting & Decanting With Hydro Test MachinePaskals Fluid Systems Pvt. Ltd.
╠²
About:
A helium boosting and decanting system is typically used in various industrial applications, particularly in the production and handling of gases, including helium including leak test of reciprocating cylinder. HereŌĆÖs a brief overview of its components and functions:
Components
1. Helium Storage Tanks: High-pressure tanks that store helium@ 150 bars.
2. Boosting Pumps: Designed to boost helium pressure up to 150 bar, ensuring efficient flow throughout the system.
3. Decanting Unit: Separates liquid helium from gas, facilitating decanting at pressures of up to 2 bars.
4. Pressure Regulators: Maintain and control the pressure of helium during transport.
5. Control Valves: automatic control valve is provided for the flow and direction of helium through the system.
6. Piping and Fittings: High-quality, corrosion-resistant materials for safe transport.
Functions
ŌĆó Boosting Pressure: The system boosts helium pressure up to 150 bar for various applications.
ŌĆó Decanting: Safely decants helium, separating liquid from gas at pressures of up to 2 bar.
ŌĆó Safety Measures: Equipped with relief valves and emergency shut-off systems to handle high pressures safely.
ŌĆó Monitoring and Control: Sensors and automated controls monitor pressure and flow rates.
Application:
ŌĆó Cryogenics: Cooling superconducting magnets in MRI machines and particle accelerators.
ŌĆó Welding: Used as a shielding gas in welding processes.
ŌĆó Research: Crucial for various scientific applications, including laboratories and space exploration.
Key Features:
ŌĆó Helium Storage & Boosting System
ŌĆó Decanting System
ŌĆó Pressure Regulation & Monitoring
ŌĆó Valves & Flow Control
ŌĆó Filtration & Safety Components
ŌĆó Structural & Material Specifications
ŌĆó Automation & Electrical Components
Design of cannal by Kennedy Theory full problem solved



Design of cannal by Kennedy Theory full problem solvedEr. Gurmeet Singh
╠²
Design of cannal by Kennedy Theory
By Er Gurmeet Singh
G.C.E.T JAMMU
CONTACT: Gurmeet.b.tech@gmail.com
Soil Properties and Methods of Determination



Soil Properties and Methods of DeterminationRajani Vyawahare
╠²
This PPT covers the index and engineering properties of soil. It includes details on index properties, along with their methods of determination. Various important terms related to soil behavior are explained in detail. The presentation also outlines the experimental procedures for determining soil properties such as water content, specific gravity, plastic limit, and liquid limit, along with the necessary calculations and graph plotting. Additionally, it provides insights to understand the importance of these properties in geotechnical engineering applications.Designing Flex and Rigid-Flex PCBs to Prevent Failure



Designing Flex and Rigid-Flex PCBs to Prevent FailureEpec Engineered Technologies
╠²
Flex and rigid-flex printed circuit boards (PCBs) can be considered at the basic level some of the most complex PCBs in the industry. With that in mind, itŌĆÖs incredibly easy to make a mistake, to leave something out, or to create a design that was doomed from the start.
Such design failures can end up leading to an eventual failure by delamination, short circuits, damage to the flex portions, and many other things. The easiest way to circumvent these is to start at the beginning, to design with preventing failure in mind rather than trying to fix existing designs to accommodate for problems.
In this webinar, we cover how to design flex and rigid-flex PCBs with failure prevention in mind to save time, money, and headaches, and what failure can look like.
For more information on our flex and rigid-flex PCB solutions, visit https://www.epectec.com/flex.Common Network Architecture:X.25 Networks, Ethernet (Standard and Fast): fram...



Common Network Architecture:X.25 Networks, Ethernet (Standard and Fast): fram...SnehPrasad2
╠²
X.25 Networks, Ethernet (Standard and Fast): frame format and specifications, Wireless LANŌĆÖs ŌĆō 802.11x, 802.3 Bluetooth etc.
Design and Analysis of Algorithms Unit 5



Design and Analysis of Algorithms Unit 5sureshkumara29
╠²
Algorithm design techniques include:
Brute Force
Greedy Algorithms
Divide-and-Conquer
Dynamic Programming
Reduction / Transform-and-Conquer
Backtracking and Branch-and-Bound
Randomization
Approximation
Recursive Approach
What is an algorithm?
An Algorithm is a procedure to solve a particular problem in a finite number of steps for a finite-sized input.
The algorithms can be classified in various ways. They are:
Implementation Method
Design Method
Design Approaches
Other Classifications
In this article, the different algorithms in each classification method are discussed.
The classification of algorithms is important for several reasons:
Organization: Algorithms can be very complex and by classifying them, it becomes easier to organize, understand, and compare different algorithms.
Problem Solving: Different problems require different algorithms, and by having a classification, it can help identify the best algorithm for a particular problem.
Performance Comparison: By classifying algorithms, it is possible to compare their performance in terms of time and space complexity, making it easier to choose the best algorithm for a particular use case.
Reusability: By classifying algorithms, it becomes easier to re-use existing algorithms for similar problems, thereby reducing development time and improving efficiency.
Research: Classifying algorithms is essential for research and development in computer science, as it helps to identify new algorithms and improve existing ones.
Overall, the classification of algorithms plays a crucial role in computer science and helps to improve the efficiency and effectiveness of solving problems.
Classification by Implementation Method: There are primarily three main categories into which an algorithm can be named in this type of classification. They are:
Recursion or Iteration: A recursive algorithm is an algorithm which calls itself again and again until a base condition is achieved whereas iterative algorithms use loops and/or data structures like stacks, queues to solve any problem. Every recursive solution can be implemented as an iterative solution and vice versa.
Example: The Tower of Hanoi is implemented in a recursive fashion while Stock Span problem is implemented iteratively.
Exact or Approximate: Algorithms that are capable of finding an optimal solution for any problem are known as the exact algorithm. For all those problems, where it is not possible to find the most optimized solution, an approximation algorithm is used. Approximate algorithms are the type of algorithms that find the result as an average outcome of sub outcomes to a problem.
Example: For NP-Hard Problems, approximation algorithms are used. Sorting algorithms are the exact algorithms.
Serial or Parallel or Distributed Algorithms: In serial algorithms, one instruction is executed at a time while parallel algorithms are those in which we divide the problem into subproblems and execute them on different processors. ESIT135 Problem Solving Using Python Notes of Unit-2 and Unit-3



ESIT135 Problem Solving Using Python Notes of Unit-2 and Unit-3prasadmutkule1
╠²
ESIT135 Problem Solving Using Python Notes of Unit-2 and Unit-3US Patented ReGenX Generator, ReGen-X Quatum Motor EV Regenerative Accelerati...



US Patented ReGenX Generator, ReGen-X Quatum Motor EV Regenerative Accelerati...Thane Heins NOBEL PRIZE WINNING ENERGY RESEARCHER
╠²
Memory Handling and Garbage Collection in Python
- 1. Memory Handling & Garbage Collection in Python Prepared by: Ms. Pooja Mehta ITSNS Branch, GTU-CDAC-BISAG ME Program, Gandhinagar 1
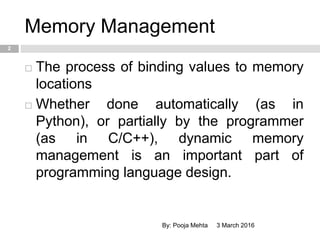
- 2. Memory Management 3 March 2016By: Pooja Mehta 2 ’é© The process of binding values to memory locations ’é© Whether done automatically (as in Python), or partially by the programmer (as in C/C++), dynamic memory management is an important part of programming language design.
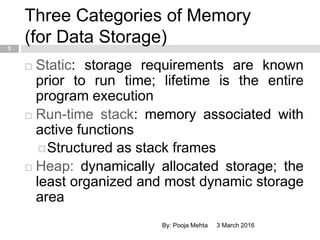
- 3. Three Categories of Memory (for Data Storage) 3 March 2016By: Pooja Mehta 3 ’é© Static: storage requirements are known prior to run time; lifetime is the entire program execution ’é© Run-time stack: memory associated with active functions ’éżStructured as stack frames ’é© Heap: dynamically allocated storage; the least organized and most dynamic storage area
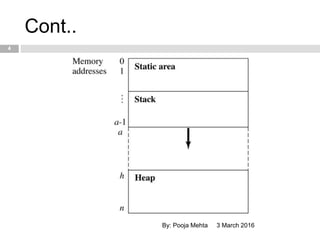
- 4. Cont.. 3 March 2016By: Pooja Mehta 4
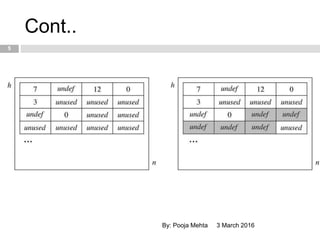
- 5. Cont.. 3 March 2016By: Pooja Mehta 5
- 6. Memory Leaks and Garbage Collection 3 March 2016By: Pooja Mehta 6 ’é© Three types of storage ’éż Static ’éż Stack ’éż Heap ’é© Problems with heap storage: ’éż Memory leaks (garbage): failure to free storage when pointers (references) are reassigned ’éż Dangling pointers: when storage is freed, but references to the storage still exist.
- 7. Garbage 3 March 2016By: Pooja Mehta 7 ’é© Any block of heap memory that cannot be accessed by the program; i.e., there is no stack pointer to the block; but which the runtime system thinks is in use. ’é© Garbage is created in several ways: ’éż A function ends without returning the space allocated to a local array or other dynamic variable. ’éż A node is deleted from a linked data structure, but isnŌĆÖt freed
- 8. Garbage Collection 3 March 2016By: Pooja Mehta 8 ’é© All inaccessible blocks of storage are identified and returned to the free list. ’é© The heap may also be compacted at this time: allocated space is compressed into one end of the heap, leaving all free space in a large block at the other end.
- 9. Implementing Automated Garbage Collection 3 March 2016By: Pooja Mehta 9 ’é© If programmers were perfect, garbage collection wouldnŌĆÖt be needed. ’é© There are three major approaches to automating the process: ’éż Reference counting ’éż Mark-sweep ’éż Copy collection
- 10. Reference Counting 10 ’é© Prior to Python version 2.0, the Python interpreter only used reference counting for memory management. ’é© Reference counting works by counting the number of times an object is referenced by other objects in the system. ’é© When references to an object are removed, the reference count for an object is decremented. ’é© When the reference count becomes zero the object is de allocated. 3 March 2016By: Pooja Mehta
- 11. Mark and Sweep 3 March 2016By: Pooja Mehta 11 ’é© Reference counting tries to find unreachable objects by finding objects with no incoming references. ’é© Imprecise because we forget which references those are.
- 12. Cont.. 3 March 2016By: Pooja Mehta 12 ’é© The root set is the set of memory locations in the program that are known to be reachable. ’é© Any objects reachable from the root set are reachable. ’é© Any objects not reachable from the root set are not reachable.
- 13. Cont.. 3 March 2016By: Pooja Mehta 13 Marking phase: Find reachable objects. ’é© Add the root set to a worklist. ’é© While the worklist isn't empty: ’éż Remove an object from the worklist. ’éż If it is not marked, mark it and add to the worklist all objects reachable from that object. Sweeping phase: Reclaim free memory. ’é© For each allocated object: ’éż If that object isn't marked, reclaim its memory. ’éż If the object is marked, unmark it (so on the next mark-and sweep iteration we have to mark it again).
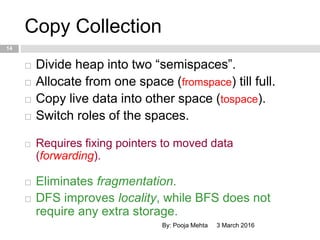
- 14. Copy Collection 3 March 2016By: Pooja Mehta 14 ’é© Divide heap into two ŌĆ£semispacesŌĆØ. ’é© Allocate from one space (fromspace) till full. ’é© Copy live data into other space (tospace). ’é© Switch roles of the spaces. ’é© Requires fixing pointers to moved data (forwarding). ’é© Eliminates fragmentation. ’é© DFS improves locality, while BFS does not require any extra storage.
- 15. References 15 ’é© https://docs.python.org/2/c-api/memory.html ’é© http://foobarnbaz.com/2012/07/08/understanding- python-variables/ ’é© https://www.digi.com/wiki/developer/index.php/Pyt hon_Garbage_Collection 3 March 2016By: Pooja Mehta
- 16. 16 Thank you...!
Editor's Notes
- #11: The user does not have to preallocate or deallocate memory by hand as one has to when using dynamic memory allocation in languages such as C or C++.
- #12: The easiest way to create a reference cycle is to create an object which refers to itself as in the example below: def make_cycle(): l = [ ] l.append(l) make_cycle() Reference counting is extremely efficient but it does have some caveats. One such caveat is that it cannot handle reference cycles. A reference cycle is when there is no way to reach an object but its reference count is still greater than zero.
- #14: Problems Memory Fragmentation Work proportional to size of heap Potential lack of locality of reference for newly allocated objects (fragmentation) Solution Compaction Contiguous live objects, contiguous free space
- #15: Automatic Garbage Collection of Cycles Because reference cycles are take computational work to discover, garbage collection must be a scheduled activity. Python schedules garbage collection based upon a threshold of object allocations and object deallocations. When the number of allocations minus the number of deallocations are greater than the threshold number, the garbage collector is run. One can inspect the threshold for new objects (objects in Python known as generation 0 objects) by loading the gc module and asking for garbage collection thresholds. Because make_cycle() creates an object l which refers to itself, the object l will not automatically be freed when the function returns. This will cause the memory that l is using to be held onto until the Python garbage collector is invoked






