Microcontroller mayhem - ECTF & USSS 2011
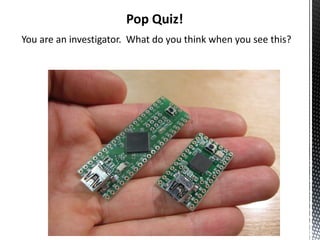
- 2. Pop Quiz! You are an investigator. What do you think when you see this?
- 4. USB Microcontrollers as an Attack Platform
- 5. Who am I • Information Security Operations Manager for Federal Reserve • Background - Threat Management, Forensics and Incident Response • Local Instructor for the SANS Institute – GCIA, GCFA, GCIH • Board Officer - Philadelphia Chapter of InfraGard • 2010 Excellence in Government Service award • Writer / Researcher – Corporate Espionage & Emerging Threats
- 6. Disclaimer • Everything presented here is based on personal research. • Statements and opinions are based on my personal perspective and does not reflect those of my employer. • I do not work for nor do I endorse any product or solution providers. • All testing was performed in a controlled isolated environment. • I do not condone the use of microcontrollers for malicious purposes. • Material presented here is for educational purposes.
- 7. Agenda • Microcontroller primer • Evolution of USB based attacks • New & Emerging USB Threats • Wired and wireless attacks • Real World examples • Challenges to Security Professionals • What the future holds • Q&A
- 8. Primer – What are Microcontrollers What classifies as a microcontroller?  Small programmable computer  Same fundamental components of a computer  Typically an “embedded device”  Self contained  Typically interact with other systems  Characteristics  Small  Low cost  Low power  Easily integrated  Highly adaptable & tolerant  Wired or Wireless
- 9. Primer – What are Microcontrollers Continued.. What’s the relationship to USB devices?  Virtually all USB devices have some form of microcontrollers in them  USB devices and microcontrollers have evolved together over the years  Consumer grade microcontrollers are often connected, programmed, controlled and interfaced via USB. “No electronic device interacts more with the physical world than Microcontrollers!”
- 10. Primer – What are Microcontrollers Continued.. Where are microcontrollers used?  Computer peripherals  Electronics (ipods, smart phones, tv, toasters, etc.)  Becoming more popular in appliances (washer, dryers, etc.)  Home water and gas meters  Sensors (heat, water, pressure, etc.)  SCADA Systems (Supervisory Control & Data Acquisition)  HVAC (Heating & AC)  Fire suppression Systems  Lighting Systems  USB connected electronics  So what’s the connection to USB devices?
- 11. In The Beginning Attacks Were Without Form  USB Antiquity Attacks & Malware  Since Inception USB keys and other connected devices have contained malicious code  Stand alone binaries  Relied on luck or social engineering  User initiated (Clicking the file)  More focused on destruction and propagation  Popularity grows Price Drops  USB as a malware transport increases (Slightly)  Many variations of drives become available  Drives become very small  Very cost effective data storage
- 12. Things Start Getting Interesting  Around 5-7 years ago USB drive popularity explodes  Highly reliable for storing large amounts of data  Cost effective way of storing data  Operating Systems on a stick  USB booting supported on most major operating systems  Self contained operating system  Bootable images become widely available  U3 drives – Hit the market!  Small microcontroller emulates Cdrom drive  Read-only ISO9660 volume  AutoRun Advantage  Ability to be reflash
- 13. Things Start Getting Interesting – Cont… New attack platform emerges! U3 drives USB Hacksaws (Switchblade) Utilized AutoRun features of Windows Many variations created Highly adaptable & effective* PsStart spinoff Non-U3 variations created Utilized autorun.inf & icons Somewhat effective
- 14. Security Industry Catches up… The Attack method Still works but…. The attack is well know in the Info. Sec. Community Only affective against Windows OS up to WinXP SP2. WinXP SP3 and Windows 7 disabled AutoRun. Not as effective on Mac, Linux, etc. AntiVirus, Malware, DLP & IDS detect most variants Forensically easy to detect on system  Application Logs  Network logs  System logs
- 15. The Bad Guys (Evolve) Alter their Tactics  What would the next evolution of USB attacks need?  Interacts, powered, developed, controlled via USB  Adapt to changes in motive  Looking to make money  Corporate Espionage / Data Theft  Botnets / System compromises  Fast and capable of surreptitiously executing code  Easy to develop and modify  Small (concealable)  Ample storage or ability to add additional storage  Forensically difficult to detect*  Easily integrated with both wired and wireless Networks  CHEAP!
- 16. Microcontrollers become the new attack Platform of Choice  Arduino Microcontrollers  Beginner friendly  Highly Adaptable / Capable  Low power consumption (powered via USB)  Come in all sizes and shapes  Easy to build and develop (C++ish language)  Large repositories of available code  Huge community following!  Large assortment of add-ons (shields)  CHEAP!  Other Microcontrollers (Parallax & Texas Instruments)  Basic Stamp I & II  MSP430 LaunchPad
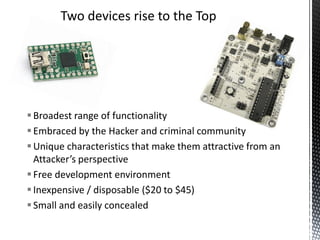
- 18. Two devices rise to the Top  Broadest range of functionality  Embraced by the Hacker and criminal community  Unique characteristics that make them attractive from an Attacker’s perspective  Free development environment  Inexpensive / disposable ($20 to $45)  Small and easily concealed
- 19. Teensy Microcontroller  Teensy  Created by Paul Stoffregen and Robin Coon http://www.pjrc.com  Originally designed to be a USB development board  Not Technically an “Arduino”  Very small – 1.2” by 0.7”  AVR processor, running up to 16mhz  ATMEGA32U4 Chip  32k flash memory  Teensyduino – allows the Teensy to use the Arduino IDE  Some disadvantages  Limited storage space (32k flash) fills up pretty quick with Libraries  Small number of I/O pins  Defaults to only 2mhz*  If running at 3.3v can’t go over 8mhz  Built in ability to emulate HID devices!
- 20. Teensy Microcontroller  What is a HID device?  Human Interface Device (HID)  Most commonly a Keyboard / Mouse  Many other interface devices that are used to enter data  HID devices are very special  HID devices initiate before at system startup  Load before operating system and other software  Use a special abstract layer that doesn’t require an OS  Have unique allocations of (ram) memory  Has for the most part been unchanged for many years  Well documented
- 21. Hacker community Develops Phuk’D Libraries  Hacker community discovers the HID capabilities  Programmable HID USB Keystroke Dongle  Free – Open source  Platform independent (Windows, Mac, etc.)  Easy to use and well documented  Emulates a person at the keyboard*  Complete control of a system before it boots  Can inject any combination of keystrokes  Provides special key combinations for Windows systems  Can execute commands, move files, delete files  Think about the possibilities!
- 22. How it is being used  Numerous examples of their uses have been seen in the wild  Several example code snippets have been released  Embedded in common devices (mice, keyboards, toys, etc.)  Identify specific keystrokes or passwords from a device  Teensy as a Social Engineering Toolkit component (SET)  Disable Anti-virus or Firewall configuration  Open Browser to Malicious site to download code  Powershell to compile exploit code  Wscript HTTP GET MSF reverse shell
- 23. It’s potential uses  Used by an insider there are many potential attacks / applications  The Incriminator – A warning to Forensic Analysts  Inject false files and data on to a target system  Extremely difficult to repudiate*  Very effective for data theft or espionage  Leave posts on pages  Download files  Send emails  Snag documents  Upload documents to remote site  Execute tasks based on time /date  Drive by or done over long periods  Defense Lawyer’s dream
- 24. What Would a Security Analyst Do? Think about the forensic process…. Capture memory, running processes from live system etc. Make a bit-by-bit image Create a timeline Review activity and look for evidence Browser history, email vids, pics, etc. Files, docs, etc. Collect findings and generate report
- 25. Teensy - Incriminator  Existing Forensic Tools are not designed to effectively detect HID type of attacks  Executed commands run under the context of the logged in user  Application execution (Firefox, Internet Explorer, etc.)  File attributes will show time, date and file owner all point to target user  Directory structure will show folder owned by target user  Registry and typically reviewed files  Usbapi.log will show little to no evidence that anything malicious or abnormal transpired on the system  USBstor keys show no evidence and a keyboard is unlikely to raise suspicion  Device does not tag the registry with many of the keys since it is not a “mass storage device”  Logs  Application logs will not identify anyone but the logged in user as the source of the activity  Content filtering logs will confirm users activity  Browser history will not be a pretty site
- 26. Limitations of this type of attack  One size does not fit all  Needs to be highly specialized and target to an individual business or person  Requires physical access to the system*  Must be connected to target machine during the entire attack  Require some knowledge of environment and system configuration  Computer make, model, specs, etc.  Commonly used hardware (keyboards, mice, etc.)  Knowledge of habits and installed software  Attack has some timing requirements  Attack is limited to wired systems…. At least for now!*
- 27. Shifting gears - Let’s go wireless!  A spinoff to USB based attacks emerges  Niche wireless has become a focus  Zigbee (xbee) 802.15.4  2.4 Ghz range  FreakLab’s Chibi Arduino device  Low power, low cost, decent range  Simplicity of setup and design  Easily implemented (no wiring costs or labor)  Not a new protocol but has only recently been adopted  Not heavily used on consumer products (currently)  Very heavily used in industrial applications
- 28. Why Zigbee & Why should we care  The motives of attackers continues to shift  Cyber warfare, Terrorism, Extortion  Very little today in the way of detection & defense  Zigbee enabled Microcontrollers are widely used in Industry  Widely deployed in U.S. and Europe  Commonly found in  Refineries (mixture, flow control, pressure etc.)  Water treatment facilities (value control, pressure, leak detection)  Power plants  Manufacturing plants (system control belts, lighting, combustibles)  Medical Systems monitoring, reporting (BP & pulse oximeter devices)
- 29. Zigbee – Attack Types  Even low tech attacks can have significant consequences  DoS (Communication interruptions between devices)  Spoofing data being sent to a device  Intentional focused attacks could be devastating!  Takedown power grid  Chemical explosions, fires  Contamination (Water, Food, Materials, etc.)  Some of these attack vectors exist today  Very difficult to detect  No products exist today to monitoring or protect against attacks  Lack of awareness about the risks and threats
- 31. In Summary  USB microcontrollers are a new attack platform  Devices are inexpensive & easy to learn and use!  Criminals have found them and are learning – Fast!  Attack tools exist today to use these new technologies  These devices are designed for attacks against people and/or infrastructure. (Data theft, Espionage, Terrorism)  Wireless microcontrollers are used extensively in industry  Simple attacks can have a real impact  There is a lack of awareness and understanding about these types of attacks  It can be extremely difficult to detect USB microcontroller attacks with existing security tools and forensic practices  We are adapting to these new attacks slower than the bad guys!
- 32. Where are Things Going?  What does the future hold?  The use of blended attacks using hardware and software devices will continue to grow.  Microcontrollers as an attack platform will grow rapidly  More specialized USB microcontroller “attack tools” will be developed.  Attacks will be more focused on infrastructure & financial targets  Organizations will start focusing resources to monitor for “blended attacks”  I suspect we’ll start seeing the big vendors start selling products that play in this space.  Blended (hardware & software) security will become a new field or specialty in Information Security and/or Law Enforcement
- 34. THANK YOU!!! Contact information : Brad Bowers bbowers@digitalintercept.com