MQTT + DASH7 Integration
0 likes7,949 views
An introduction to integrating MQTT with DASH7. Deploying MQTT over DASH7 is not too difficult and we show examples for getting started.
1 of 7
Downloaded 16 times
![DASH7 with MQTT?
[Application Note]](https://image.slidesharecdn.com/mqttdash7intro-170511123047/85/MQTT-DASH7-Integration-1-320.jpg)

Recommended
Haystack + DASH7 Security



Haystack + DASH7 SecurityHaystack Technologies
?
An overview of Haystack's security features for low power IoT networks. Unlike most IoT stacks, when Haystack invented DASH7, security was an a priori principle and led to the most secure networking stack available in the low power, wide area networking (LPWAN) space today.More on Using Haystack + DASH7 with MQTT



More on Using Haystack + DASH7 with MQTTHaystack Technologies
?
More details on implementing broadcast/multicast messaging in IoT networking running Haystack + DASH7 networking software. Also implementing CBOR to enable queries over MQTT.Haystack Integration of NFC and DASH7



Haystack Integration of NFC and DASH7Haystack Technologies
?
Short overview on the evolution of NFC to accommodate broader IoT use cases including security, two-factor authentication and other applications of long range, low power wireless networking.How To Triple The Range of LoRa



How To Triple The Range of LoRaHaystack Technologies
?
Haystack is introducing a new mode called DASH7 XR Mode that can triple the range of LoRa networks. It utilizes advanced error correction techniques as well as automated receipt responses. Testing shows it can achieve 2-3x the range of LoRaWAN networks while preserving multi-year battery life. Private beta testing of XR Mode is now underway.Bringing Better Networking to LTE IoT



Bringing Better Networking to LTE IoTHaystack Technologies
?
The document discusses challenges with existing LTE IoT standards like LTE Cat M1 and NB-IoT in supporting real-time, low power networking. It proposes running the Haystack (DASH7) networking stack concurrently with TCP/IP on the same silicon to enable features like precision indoor location, peer-to-peer networking, and distributed applications while minimizing memory footprint impact. Using reference tags and RF fingerprinting, Haystack can provide indoor location precision of about 1 meter to complement wide area visibility from LTE. Overall Haystack aims to deliver a complete LPWAN-LAN connectivity solution for IoT use cases.How To Disrupt The Internet of Things With Unified Networking



How To Disrupt The Internet of Things With Unified NetworkingHaystack Technologies
?
Wireless IoT connections fall into two low-power camps: local area and wide area. Historically the two have not overlapped but advances in networking technologies make it possible for wide area technologies to perform the same functions as local area technologies with no additional cost or feature "sacrifice".Research and Experimentation of LoRa in Heavy Multipath



Research and Experimentation of LoRa in Heavy MultipathHaystack Technologies
?
- Research has shown that LoRa experiences significant degradation in environments with heavy multipath interference like dense urban or indoor settings due to Rayleigh flat fading.
- Experimentation in an airport parking lot exhibiting Rayleigh flat fading validated this, showing Haystack XR2 encoding provided roughly 30 dB gain to packet error rate over default LoRaWAN encoding.
- This gain allows LoRa networks using Haystack XR2 to achieve much higher quality of service, efficiency, and channel density in challenging multipath environments.Rpl2016



Rpl2016Pascal Thubert
?
The document discusses Internet of Things (IoT) networks and routing protocol RPL. It provides an agenda for covering open standards, IEEE and IETF work on low-power lossy networks (LLNs) and 6LoWPAN, concepts of RPL including DODAG, instances, objective functions and messages. It also discusses putting the pieces together including backbone routers and data packet flows. The goal is to reconsider basic Internet structures and expectations to support trillions of constrained devices connecting in IoT applications.Scaling the Web to Billions of Nodes: Towards the IPv6 ˇ°Internet of Thingsˇ± b...



Scaling the Web to Billions of Nodes: Towards the IPv6 ˇ°Internet of Thingsˇ± b...gogo6
?
gogo6 IPv6 Video Series. Event, presentation and speaker details below:
EVENT
gogoNET LIVE! 4: IPv6 & The Internet of Things. http://gogonetlive.com
November 12 ¨C 14, 201, Silicon Valley, California
Agenda: http://gogonetlive.com/gogonetlive4-agenda.asp
PRESENTATION
Scaling the Web to Billions of Nodes: Towards the IPv6 ˇ°Internet of Thingsˇ±
Abstract: http://www.gogo6.com/profiles/blogs/scaling-the-web-to-billions-of-nodes-towards-the-ipv6-internet-of
Presentation video: http://www.gogo6.com/video/scaling-the-web-to-billions-of-nodes-by-carsten-bormann-at-gogone
Interview video: http://www.gogo6.com/video/interview-with-carsten-bormann-at-gogonet-live-4-ipv6-iot-confere
SPEAKER
Carsten Bormann - Universit?t Bremen TZI & IETF WG Chair
Bio/Profile: http://www.gogo6.com/profile/CarstenBormann
MORE
Learn more about IPv6 on the gogoNET social network and our online training courses
http://www.gogo6.com/main
Get free IPv6 connectivity with Freenet6
http://www.gogo6.com/Freenet6
Subscribe to the gogo6 IPv6 Channel on YouTube
http://www.youtube.com/subscription_center?add_user=gogo6videos
Follow gogo6 on Twitter
http://twitter.com/gogo6inc
Like gogo6 on Facebook
http://www.facebook.com/pages/IPv6-products-community-and-services-gogo6/161626696777
DDoS Mitigation using BGP Flowspec 



DDoS Mitigation using BGP Flowspec APNIC
?
This document discusses using BGP Flowspec for DDoS mitigation. It provides an overview of legacy DDoS mitigation methods, describes how BGP Flowspec works by distributing flow specifications using BGP, and gives examples of how it can be used for inter-domain and intra-domain DDoS mitigation as well as with a scrubbing center. It also discusses vendor support, advantages over previous methods, potential issues, real world deployments, and the current state and future of BGP Flowspec.BGP Flowspec (RFC5575) Case study and Discussion



BGP Flowspec (RFC5575) Case study and DiscussionAPNIC
?
BGP Flowspec is a technique for distributing flow specification rules via BGP. It allows an ISP to dynamically distribute filtering and redirection rules to mitigate DDoS attacks. The document discusses several real-world use cases where BGP Flowspec was deployed to successfully block large DDoS attacks in a targeted manner without affecting legitimate traffic. However, interoperability between vendors and scalability challenges remain open issues requiring further work and testing.The Next Generation Internet Number Registry Services



The Next Generation Internet Number Registry ServicesMyNOG
?
This document provides an overview of registry services, including the Registration Data Access Protocol (RDAP) and the Resource Public Key Infrastructure (RPKI). RDAP is designed to replace the aging WHOIS protocol by providing structured query and response formats to enable automation. RDAP also supports access control, internationalization, redirection and extensibility. RPKI is a PKI framework that adds Internet number resource information to certificates to cryptographically validate resource ownership and authorization of routing announcements. It enables applications like route origin validation to secure the routing system. The document discusses how RDAP and RPKI work and provide benefits like improved security, automation and verification of registry data.LF_DPDK17_OpenNetVM: A high-performance NFV platforms to meet future communic...



LF_DPDK17_OpenNetVM: A high-performance NFV platforms to meet future communic...LF_DPDK
?
This document discusses software-based networking and network function virtualization (NFV). It introduces NetVM, an NFV platform developed by the author that provides high performance packet delivery across virtual machines using DPDK for zero-copy networking. NetVM enables complex network services to be distributed across multiple VMs while maintaining high throughput. The author also discusses OpenNetVM, an open source version of NetVM, and contributions like Flurries that enable unique network functions to run per flow for improved scalability. NFVnice, a userspace framework for scheduling NFV chains, is also introduced to improve throughput, fairness and CPU utilization.TRUST BASED ROUTING METRIC FOR RPL ROUTING PROTOCOL IN THE INTERNET OF THINGS



TRUST BASED ROUTING METRIC FOR RPL ROUTING PROTOCOL IN THE INTERNET OF THINGSpijans
?
While smart factories are becoming widely recognized as a fundamental concept of Industry 4.0, their implementation has posed several challenges insofar that they generate and process vast amounts of security critical and privacy sensitive data, in addition to the fact that they deploy IoT heterogeneous and constrained devices communicating with each other and being accessed ubiquitously through lossy networks. In this scenario, the routing of data is a specific area of concern especially with the inherent constraints and limiting properties of such devices like processing resources, memory capacity and battery life. To suit these constraints and to provide the required connectivity, the IETF has developed several standards, among them the RPL routing protocol for Low powerand Lossy Networks (LLNs). However, and even though RPL provides support for integrity and confidentiality of messages, its security may be compromised by several threats and attacks. We propose in this work TRM-RPL, a Trust based Routing Metric for the RPL protocol in an IIoT based environments. TRM-RPL uses a trust management mechanism to detect malicious behaviors and resist routing attacks while providing QoS guarantees. In addition, our model addresses both node and link trust and follows a multidimensional approach to enable
an accurate trust assessment for IoT entities. TRM-RPL is implemented, successfully tested and compared with the standard RPL protocol where its effectiveniness and resilience to attacks has been proved to be better.IoT Field Area Network Solutions & Integration of IPv6 Standards by Patrick G...



IoT Field Area Network Solutions & Integration of IPv6 Standards by Patrick G...gogo6
?
gogo6 IPv6 Video Series. Event, presentation and speaker details below:
EVENT
gogoNET LIVE! 4: IPv6 & The Internet of Things. http://gogonetlive.com
November 12 ¨C 14, 201, Silicon Valley, California
Agenda: http://gogonetlive.com/gogonetlive4-agenda.asp
PRESENTATION
IoT Field Area Network Solutions & Integration of IPv6 Standards
Abstract: http://www.gogo6.com/profiles/blogs/my-presentation-at-gogolive-integration-of-ipv4-and-non-ip
Presentation video: http://www.gogo6.com/video/iot-field-area-network-solutions-integration-of-ipv6-standards-by
Interview video: http://www.gogo6.com/video/interview-with-carsten-bormann-at-gogonet-live-4-ipv6-iot-confere
SPEAKER
Patrick Grossetete - Technical Marketing Engineer (IoT), Cisco
Bio/Profile: http://www.gogo6.com/profile/PatrickGrossetete
MORE
Learn more about IPv6 on the gogoNET social network and our online training courses
http://www.gogo6.com/main
Get free IPv6 connectivity with Freenet6
http://www.gogo6.com/Freenet6
Subscribe to the gogo6 IPv6 Channel on YouTube
http://www.youtube.com/subscription_center?add_user=gogo6videos
Follow gogo6 on Twitter
http://twitter.com/gogo6inc
Like gogo6 on Facebook
http://www.facebook.com/pages/IPv6-products-community-and-services-gogo6/161626696777
DASH7 Mode 2 Summary 



DASH7 Mode 2 Summary Haystack Technologies
?
This document discusses proposed revisions to ISO 18000-7 referred to as Mode 2. Key proposed changes include improvements to the physical layer to improve performance and reduce costs, improvements to the medium access control layer for better channel efficiency, and additions to allow for peer-to-peer communications and unsolicited packet transmissions. The revised standard would support features like decreased device size, external communication events, amorphous networks, and longer reading ranges.Is Internet getting old !!



Is Internet getting old !!Bangladesh Network Operators Group
?
The document discusses the limitations of the current TCP/IP network architecture and proposes Recursive Internet Architecture (RINA) as a better alternative. RINA is based on the principle that networking is inter-process communication (IPC) that is recursed over different scopes. It was first presented in 2008 as a new architecture that supports capabilities like mobility, middleboxes, and layer violations without specific mechanisms. RINA structures the network in a way that aims to enhance its structure and economic efficiency compared to the TCP/IP model.L2 tp



L2 tpRamya Chowdary
?
Layer 2 Tunneling Protocol (L2TP) is a network layer VPN protocol that uses IP packets to encapsulate Layer 2 frames. L2TP extends the Point-to-Point Protocol (PPP) by allowing the Layer 2 and PPP endpoints to reside on different devices interconnected by a packet-switched network. L2TP establishes tunnels between an L2TP Access Concentrator (LAC) and an L2TP Network Server (LNS) to transport individual PPP frames across the network. Control connections and sessions are set up between the LAC and LNS to establish L2TP tunnels for transporting PPP data.07 (IDNOG02) SDN Research activity in Institut Teknologi Bandung by Affan Bas...



07 (IDNOG02) SDN Research activity in Institut Teknologi Bandung by Affan Bas...Indonesia Network Operators Group
?
This document summarizes an SDN and cloud computing presentation given by Affan Basalamah and Dr.-Ing. Eueung Mulyana from Institut Teknologi Bandung. It discusses SDN and cloud computing research activities at ITB, including implementing OpenFlow networks, developing SDN courses, and student projects involving OpenFlow, OpenStack, and IPsec VPNs. It also describes forming an SDN research group at ITB to facilitate collaboration between academia, network operators, and vendors on SDN topics.LF_DPDK17_DPDK with KNI ¨C Pushing the Performance of an SDWAN Gateway to High...



LF_DPDK17_DPDK with KNI ¨C Pushing the Performance of an SDWAN Gateway to High...LF_DPDK
?
The document outlines a presentation on using DPDK with KNI to improve the performance of an SD-WAN gateway. It discusses:
- Understanding typical SD-WAN ecosystems and gateway requirements
- How kernel-based forwarding has limitations that prevent meeting performance needs
- How DPDK can help by allowing dedicated resources and bypassing kernel processing
- The solution of using a dedicated DPDK application with KNI to leverage both DPDK and kernel functionality
- Details on the software architecture, component design, and how security and configuration are managedIntroduction To DASH7 Technology



Introduction To DASH7 Technologyjpnorair
?
DASH7 is an ultra-low power wireless technology standard based on ISO 18000-7 that operates at 433MHz. It was developed for the Department of Defense and allied militaries. DASH7 uses very little energy through an RF wakeup mechanism, allowing devices to last for months or years on battery power. It is well-suited for applications involving low latency, low power wireless communication through materials like water, earth, and concrete, such as sensor networks and networks where devices move. More information can be found on the DASH7 website.Applying IPv6 to LTE Networks



Applying IPv6 to LTE NetworksAPNIC
?
"Applying IPv6 to LTE Networks" by Deoknyong Ko.
A presentation given at the APNIC 40 Internet Mobility Nexus session on Tue 8 Sep 2015.Actual Condition Survey of Malware Download Sites for A Long Period



Actual Condition Survey of Malware Download Sites for A Long PeriodAPNIC
?
This document summarizes the results of observing over 60,000 malware download URLs over a period of 1.5 years. It finds that while reports have shown a decrease in the number of websites containing malware, malware download sites tend to be long-lived. Most exist on cloud services or hosting companies, and many relive multiple times by changing IP addresses or ASes. The document discusses implications for operators, including the need for long-term monitoring and information sharing between network organizations.IoT Communication Protocols



IoT Communication ProtocolsPradeep Kumar TS
?
This slide features the list of communication protocols that are suitable for Internet of things. It features from http to CoAPLF_DPDK17_Integrating and using DPDK with Open vSwitch



LF_DPDK17_Integrating and using DPDK with Open vSwitchLF_DPDK
?
The document discusses the challenges of integrating DPDK with Open vSwitch and the approaches taken to address them. Some key challenges included DPDK's preference for its own data structures, initialization requirements, threading model differences, and debugging difficulties. The integration addresses these by allowing Open vSwitch to maintain its own data structures and threading while initializing DPDK, and improving configuration, PMD support, and documentation for debugging. Upgrades remain challenging due to DPDK's API and ABI changes.DASH7 Alliance University Working Group Magazine - May 2012



DASH7 Alliance University Working Group Magazine - May 2012Haystack Technologies
?
Inaugural issue of the DASH7 Alliance University Working Group magazine, including articles on new indoor location technology, OpenTag, new DASH7 CoAP - Web Protocol for IoT



CoAP - Web Protocol for IoTAniruddha Chakrabarti
?
High level overview of CoAP or Constrained Application Protocol. CoAP is a HTTP like protocol suitable for constrained environment like IoT. CoAP uses HTTP like request response model, status code etc.Protocol and Integration Challenges for SDN



Protocol and Integration Challenges for SDNGerardo Pardo-Castellote
?
SDN programming and operations requires continuous monitoring of network and application state as well as consistent configuration and update of (forwarding) policies across heterogeneous devices. This is resulting in significant challenges.
Multiple open protocols such as OpenFlow, OF-CONFIG, OnePK , etc. are being adopted by different vendors causing an integration problem for developers.
Internet of Things applications are pushing the size and volume of data handled by SDN systems demanding more efficient and scalable protocols for information distribution and coordination of SDN devices.
This presentation will describe these and other SDN challenges and ways in which various open protocols, such as DDS, XMPP, AMQP, are being used to address them.
Protocols for internet of things



Protocols for internet of thingsCharles Gibbons
?
This document discusses various protocols that can be used for communication with devices in the Internet of Things. It describes several protocols including HTTP/HTTPS, WebSockets, MQTT, MQTT-SN, CoAP, and XMPP. For each protocol, it provides details on their appropriate uses, capabilities, and limitations when used with devices that have limited memory, power, or network connectivity. It recommends selecting the right protocol based on a device's capabilities and the specific communication needs of the application.Protocols for internet of things



Protocols for internet of thingsCharles Gibbons
?
This document discusses various protocols that can be used for communication with devices in the Internet of Things. It describes several protocols including HTTP/HTTPS, WebSockets, MQTT, MQTT-SN, CoAP, and XMPP. For each protocol, it provides details on their appropriate uses, capabilities, and limitations when used with devices that have limited memory, power, or network connectivity. It recommends selecting the right protocol based on a device's capabilities and the specific communication needs of the application.More Related Content
What's hot (20)
Scaling the Web to Billions of Nodes: Towards the IPv6 ˇ°Internet of Thingsˇ± b...



Scaling the Web to Billions of Nodes: Towards the IPv6 ˇ°Internet of Thingsˇ± b...gogo6
?
gogo6 IPv6 Video Series. Event, presentation and speaker details below:
EVENT
gogoNET LIVE! 4: IPv6 & The Internet of Things. http://gogonetlive.com
November 12 ¨C 14, 201, Silicon Valley, California
Agenda: http://gogonetlive.com/gogonetlive4-agenda.asp
PRESENTATION
Scaling the Web to Billions of Nodes: Towards the IPv6 ˇ°Internet of Thingsˇ±
Abstract: http://www.gogo6.com/profiles/blogs/scaling-the-web-to-billions-of-nodes-towards-the-ipv6-internet-of
Presentation video: http://www.gogo6.com/video/scaling-the-web-to-billions-of-nodes-by-carsten-bormann-at-gogone
Interview video: http://www.gogo6.com/video/interview-with-carsten-bormann-at-gogonet-live-4-ipv6-iot-confere
SPEAKER
Carsten Bormann - Universit?t Bremen TZI & IETF WG Chair
Bio/Profile: http://www.gogo6.com/profile/CarstenBormann
MORE
Learn more about IPv6 on the gogoNET social network and our online training courses
http://www.gogo6.com/main
Get free IPv6 connectivity with Freenet6
http://www.gogo6.com/Freenet6
Subscribe to the gogo6 IPv6 Channel on YouTube
http://www.youtube.com/subscription_center?add_user=gogo6videos
Follow gogo6 on Twitter
http://twitter.com/gogo6inc
Like gogo6 on Facebook
http://www.facebook.com/pages/IPv6-products-community-and-services-gogo6/161626696777
DDoS Mitigation using BGP Flowspec 



DDoS Mitigation using BGP Flowspec APNIC
?
This document discusses using BGP Flowspec for DDoS mitigation. It provides an overview of legacy DDoS mitigation methods, describes how BGP Flowspec works by distributing flow specifications using BGP, and gives examples of how it can be used for inter-domain and intra-domain DDoS mitigation as well as with a scrubbing center. It also discusses vendor support, advantages over previous methods, potential issues, real world deployments, and the current state and future of BGP Flowspec.BGP Flowspec (RFC5575) Case study and Discussion



BGP Flowspec (RFC5575) Case study and DiscussionAPNIC
?
BGP Flowspec is a technique for distributing flow specification rules via BGP. It allows an ISP to dynamically distribute filtering and redirection rules to mitigate DDoS attacks. The document discusses several real-world use cases where BGP Flowspec was deployed to successfully block large DDoS attacks in a targeted manner without affecting legitimate traffic. However, interoperability between vendors and scalability challenges remain open issues requiring further work and testing.The Next Generation Internet Number Registry Services



The Next Generation Internet Number Registry ServicesMyNOG
?
This document provides an overview of registry services, including the Registration Data Access Protocol (RDAP) and the Resource Public Key Infrastructure (RPKI). RDAP is designed to replace the aging WHOIS protocol by providing structured query and response formats to enable automation. RDAP also supports access control, internationalization, redirection and extensibility. RPKI is a PKI framework that adds Internet number resource information to certificates to cryptographically validate resource ownership and authorization of routing announcements. It enables applications like route origin validation to secure the routing system. The document discusses how RDAP and RPKI work and provide benefits like improved security, automation and verification of registry data.LF_DPDK17_OpenNetVM: A high-performance NFV platforms to meet future communic...



LF_DPDK17_OpenNetVM: A high-performance NFV platforms to meet future communic...LF_DPDK
?
This document discusses software-based networking and network function virtualization (NFV). It introduces NetVM, an NFV platform developed by the author that provides high performance packet delivery across virtual machines using DPDK for zero-copy networking. NetVM enables complex network services to be distributed across multiple VMs while maintaining high throughput. The author also discusses OpenNetVM, an open source version of NetVM, and contributions like Flurries that enable unique network functions to run per flow for improved scalability. NFVnice, a userspace framework for scheduling NFV chains, is also introduced to improve throughput, fairness and CPU utilization.TRUST BASED ROUTING METRIC FOR RPL ROUTING PROTOCOL IN THE INTERNET OF THINGS



TRUST BASED ROUTING METRIC FOR RPL ROUTING PROTOCOL IN THE INTERNET OF THINGSpijans
?
While smart factories are becoming widely recognized as a fundamental concept of Industry 4.0, their implementation has posed several challenges insofar that they generate and process vast amounts of security critical and privacy sensitive data, in addition to the fact that they deploy IoT heterogeneous and constrained devices communicating with each other and being accessed ubiquitously through lossy networks. In this scenario, the routing of data is a specific area of concern especially with the inherent constraints and limiting properties of such devices like processing resources, memory capacity and battery life. To suit these constraints and to provide the required connectivity, the IETF has developed several standards, among them the RPL routing protocol for Low powerand Lossy Networks (LLNs). However, and even though RPL provides support for integrity and confidentiality of messages, its security may be compromised by several threats and attacks. We propose in this work TRM-RPL, a Trust based Routing Metric for the RPL protocol in an IIoT based environments. TRM-RPL uses a trust management mechanism to detect malicious behaviors and resist routing attacks while providing QoS guarantees. In addition, our model addresses both node and link trust and follows a multidimensional approach to enable
an accurate trust assessment for IoT entities. TRM-RPL is implemented, successfully tested and compared with the standard RPL protocol where its effectiveniness and resilience to attacks has been proved to be better.IoT Field Area Network Solutions & Integration of IPv6 Standards by Patrick G...



IoT Field Area Network Solutions & Integration of IPv6 Standards by Patrick G...gogo6
?
gogo6 IPv6 Video Series. Event, presentation and speaker details below:
EVENT
gogoNET LIVE! 4: IPv6 & The Internet of Things. http://gogonetlive.com
November 12 ¨C 14, 201, Silicon Valley, California
Agenda: http://gogonetlive.com/gogonetlive4-agenda.asp
PRESENTATION
IoT Field Area Network Solutions & Integration of IPv6 Standards
Abstract: http://www.gogo6.com/profiles/blogs/my-presentation-at-gogolive-integration-of-ipv4-and-non-ip
Presentation video: http://www.gogo6.com/video/iot-field-area-network-solutions-integration-of-ipv6-standards-by
Interview video: http://www.gogo6.com/video/interview-with-carsten-bormann-at-gogonet-live-4-ipv6-iot-confere
SPEAKER
Patrick Grossetete - Technical Marketing Engineer (IoT), Cisco
Bio/Profile: http://www.gogo6.com/profile/PatrickGrossetete
MORE
Learn more about IPv6 on the gogoNET social network and our online training courses
http://www.gogo6.com/main
Get free IPv6 connectivity with Freenet6
http://www.gogo6.com/Freenet6
Subscribe to the gogo6 IPv6 Channel on YouTube
http://www.youtube.com/subscription_center?add_user=gogo6videos
Follow gogo6 on Twitter
http://twitter.com/gogo6inc
Like gogo6 on Facebook
http://www.facebook.com/pages/IPv6-products-community-and-services-gogo6/161626696777
DASH7 Mode 2 Summary 



DASH7 Mode 2 Summary Haystack Technologies
?
This document discusses proposed revisions to ISO 18000-7 referred to as Mode 2. Key proposed changes include improvements to the physical layer to improve performance and reduce costs, improvements to the medium access control layer for better channel efficiency, and additions to allow for peer-to-peer communications and unsolicited packet transmissions. The revised standard would support features like decreased device size, external communication events, amorphous networks, and longer reading ranges.Is Internet getting old !!



Is Internet getting old !!Bangladesh Network Operators Group
?
The document discusses the limitations of the current TCP/IP network architecture and proposes Recursive Internet Architecture (RINA) as a better alternative. RINA is based on the principle that networking is inter-process communication (IPC) that is recursed over different scopes. It was first presented in 2008 as a new architecture that supports capabilities like mobility, middleboxes, and layer violations without specific mechanisms. RINA structures the network in a way that aims to enhance its structure and economic efficiency compared to the TCP/IP model.L2 tp



L2 tpRamya Chowdary
?
Layer 2 Tunneling Protocol (L2TP) is a network layer VPN protocol that uses IP packets to encapsulate Layer 2 frames. L2TP extends the Point-to-Point Protocol (PPP) by allowing the Layer 2 and PPP endpoints to reside on different devices interconnected by a packet-switched network. L2TP establishes tunnels between an L2TP Access Concentrator (LAC) and an L2TP Network Server (LNS) to transport individual PPP frames across the network. Control connections and sessions are set up between the LAC and LNS to establish L2TP tunnels for transporting PPP data.07 (IDNOG02) SDN Research activity in Institut Teknologi Bandung by Affan Bas...



07 (IDNOG02) SDN Research activity in Institut Teknologi Bandung by Affan Bas...Indonesia Network Operators Group
?
This document summarizes an SDN and cloud computing presentation given by Affan Basalamah and Dr.-Ing. Eueung Mulyana from Institut Teknologi Bandung. It discusses SDN and cloud computing research activities at ITB, including implementing OpenFlow networks, developing SDN courses, and student projects involving OpenFlow, OpenStack, and IPsec VPNs. It also describes forming an SDN research group at ITB to facilitate collaboration between academia, network operators, and vendors on SDN topics.LF_DPDK17_DPDK with KNI ¨C Pushing the Performance of an SDWAN Gateway to High...



LF_DPDK17_DPDK with KNI ¨C Pushing the Performance of an SDWAN Gateway to High...LF_DPDK
?
The document outlines a presentation on using DPDK with KNI to improve the performance of an SD-WAN gateway. It discusses:
- Understanding typical SD-WAN ecosystems and gateway requirements
- How kernel-based forwarding has limitations that prevent meeting performance needs
- How DPDK can help by allowing dedicated resources and bypassing kernel processing
- The solution of using a dedicated DPDK application with KNI to leverage both DPDK and kernel functionality
- Details on the software architecture, component design, and how security and configuration are managedIntroduction To DASH7 Technology



Introduction To DASH7 Technologyjpnorair
?
DASH7 is an ultra-low power wireless technology standard based on ISO 18000-7 that operates at 433MHz. It was developed for the Department of Defense and allied militaries. DASH7 uses very little energy through an RF wakeup mechanism, allowing devices to last for months or years on battery power. It is well-suited for applications involving low latency, low power wireless communication through materials like water, earth, and concrete, such as sensor networks and networks where devices move. More information can be found on the DASH7 website.Applying IPv6 to LTE Networks



Applying IPv6 to LTE NetworksAPNIC
?
"Applying IPv6 to LTE Networks" by Deoknyong Ko.
A presentation given at the APNIC 40 Internet Mobility Nexus session on Tue 8 Sep 2015.Actual Condition Survey of Malware Download Sites for A Long Period



Actual Condition Survey of Malware Download Sites for A Long PeriodAPNIC
?
This document summarizes the results of observing over 60,000 malware download URLs over a period of 1.5 years. It finds that while reports have shown a decrease in the number of websites containing malware, malware download sites tend to be long-lived. Most exist on cloud services or hosting companies, and many relive multiple times by changing IP addresses or ASes. The document discusses implications for operators, including the need for long-term monitoring and information sharing between network organizations.IoT Communication Protocols



IoT Communication ProtocolsPradeep Kumar TS
?
This slide features the list of communication protocols that are suitable for Internet of things. It features from http to CoAPLF_DPDK17_Integrating and using DPDK with Open vSwitch



LF_DPDK17_Integrating and using DPDK with Open vSwitchLF_DPDK
?
The document discusses the challenges of integrating DPDK with Open vSwitch and the approaches taken to address them. Some key challenges included DPDK's preference for its own data structures, initialization requirements, threading model differences, and debugging difficulties. The integration addresses these by allowing Open vSwitch to maintain its own data structures and threading while initializing DPDK, and improving configuration, PMD support, and documentation for debugging. Upgrades remain challenging due to DPDK's API and ABI changes.DASH7 Alliance University Working Group Magazine - May 2012



DASH7 Alliance University Working Group Magazine - May 2012Haystack Technologies
?
Inaugural issue of the DASH7 Alliance University Working Group magazine, including articles on new indoor location technology, OpenTag, new DASH7 CoAP - Web Protocol for IoT



CoAP - Web Protocol for IoTAniruddha Chakrabarti
?
High level overview of CoAP or Constrained Application Protocol. CoAP is a HTTP like protocol suitable for constrained environment like IoT. CoAP uses HTTP like request response model, status code etc.Protocol and Integration Challenges for SDN



Protocol and Integration Challenges for SDNGerardo Pardo-Castellote
?
SDN programming and operations requires continuous monitoring of network and application state as well as consistent configuration and update of (forwarding) policies across heterogeneous devices. This is resulting in significant challenges.
Multiple open protocols such as OpenFlow, OF-CONFIG, OnePK , etc. are being adopted by different vendors causing an integration problem for developers.
Internet of Things applications are pushing the size and volume of data handled by SDN systems demanding more efficient and scalable protocols for information distribution and coordination of SDN devices.
This presentation will describe these and other SDN challenges and ways in which various open protocols, such as DDS, XMPP, AMQP, are being used to address them.
07 (IDNOG02) SDN Research activity in Institut Teknologi Bandung by Affan Bas...



07 (IDNOG02) SDN Research activity in Institut Teknologi Bandung by Affan Bas...Indonesia Network Operators Group
?
Similar to MQTT + DASH7 Integration (20)
Protocols for internet of things



Protocols for internet of thingsCharles Gibbons
?
This document discusses various protocols that can be used for communication with devices in the Internet of Things. It describes several protocols including HTTP/HTTPS, WebSockets, MQTT, MQTT-SN, CoAP, and XMPP. For each protocol, it provides details on their appropriate uses, capabilities, and limitations when used with devices that have limited memory, power, or network connectivity. It recommends selecting the right protocol based on a device's capabilities and the specific communication needs of the application.Protocols for internet of things



Protocols for internet of thingsCharles Gibbons
?
This document discusses various protocols that can be used for communication with devices in the Internet of Things. It describes several protocols including HTTP/HTTPS, WebSockets, MQTT, MQTT-SN, CoAP, and XMPP. For each protocol, it provides details on their appropriate uses, capabilities, and limitations when used with devices that have limited memory, power, or network connectivity. It recommends selecting the right protocol based on a device's capabilities and the specific communication needs of the application.Internet of Things: Protocols for M2M



Internet of Things: Protocols for M2MCharles Gibbons
?
Internet of Things requires communication to devices that are either actuators or sensors. Each actuator and sensor has an identity. Each actuator and sensor may be either directly connected to the world wide web or indirectly connected via a type of gateway.
Communication to these devices needs to be reliable. Therefore each device may implement their most suitable communication protocol.
This deck describes the main common protocols and their usage for the Internet of Things
Charles Gibbons
apicrazy.comProtocols for internet of things



Protocols for internet of thingsCharles Gibbons
?
Internet of Things requires communication to devices that are either actuators or sensors. Each actuator and sensor has an identity. Each actuator and sensor may be either directly connected to the world wide web or indirectly connected via a type of gateway.
Communication to these devices needs to be reliable. Therefore each device may implement their most suitable communication protocol.
This deck describes the main common protocols and their usage for the Internet of Things
Charles Gibbons
apicrazy.comProtocols for internet of things



Protocols for internet of thingsCharles Gibbons
?
This document discusses various protocols that can be used for communication with devices in the Internet of Things. It describes several protocols including HTTP/HTTPS, WebSockets, MQTT, MQTT-SN, CoAP, and XMPP. For each protocol, it provides details on their appropriate uses, capabilities, and limitations when used with different types of devices and communication needs. It also compares MQTT and CoAP, noting that the best protocol depends on the specific application and devices used.Protocols for internet of things



Protocols for internet of thingsCharles Gibbons
?
Internet of Things, M2M, Protocols, Actuators, Sensors, XMPP, HTTP, MQPP, MQPP-SN, CoAP, Protocol Comparison, Machine to Machine, apicrazy, technologyMQTT with .NET Core



MQTT with .NET CoreMark Lechtermann
?
This document provides an overview of MQTT (Message Queuing Telemetry Transport), including topics, brokers, quality of service (QoS) levels, retained messages, last will and testament, and security. It then demonstrates how to use the MQTTnet library to connect to a broker, subscribe and publish messages with .NET Core.Modern Distributed Messaging and RPC



Modern Distributed Messaging and RPCMax Alexejev
?
This document provides an overview of lightweight messaging and remote procedure call (RPC) systems in distributed systems. It discusses messaging systems, typical peer-to-peer and broker-based messaging topologies, characteristics and features of messaging systems, main classes of messaging systems including enterprise service buses (ESBs), JMS implementations, AMQP implementations, and lightweight modern systems. It also covers RPC, serialization libraries, differences between messaging and RPC, examples of ZeroMQ for peer-to-peer messaging, Apache Kafka for broker-based messaging, and Twitter Finagle for scalable RPC.Deploy Secure and Scalable Services Across Kubernetes Clusters with NATS



Deploy Secure and Scalable Services Across Kubernetes Clusters with NATSNATS
?
Services and Streams are the cornerstones of any modern distributed architecture. Communications and observability of modern systems have become just as important as the deployment of the components themselves. In this talk maintainers of the NATS projectwill create a service using NATS as the communication technology. They will show how NATS allows a service application to utilize cutting edge security with the ability to scale up and down, across multiple Kubernetes clusters and cloud deployments. This will be completely observable, with no code changes from the demo code base to global deployment. NATS allows cutting edge modern systems to be built without the additional complexity of load balancers, proxies or sidecars. NATS allows radically easy yet secure deployments across multiple k8s clusters, in any cloud or on-premise environment.Redis v5 & Streams



Redis v5 & StreamsItamar Haber
?
What's new is Redis v5 and an overview of Streams - as presented at the Redis TLV Meetup on Oct 28th, 2018.Basics of the Highly Available Distributed Databases - teowaki - javier ramir...



Basics of the Highly Available Distributed Databases - teowaki - javier ramir...javier ramirez
?
Basic concepts of distributed systems, such as consensus, gossip and infection protocols, vector clocks, sharding storage, so you can create highly available distributed systemsEverything you always wanted to know about highly available distributed datab...



Everything you always wanted to know about highly available distributed datab...Codemotion
?
Can you imagine a database that stands as much traffic as you want, adding and removing nodes automatically, working interruption-free even if a volcano starts spitting lava over your data centres? That's the promise of distributed systems like Cassandra, Voldemort or Riak. But, how do they do it? In this talk I will tell you the basics of distributed databases. Come to my talk if you want to learn about CAP, BASE, incremental scalability, replication or consensus. I will also explain geeky things like gossip, vector clocks, hinted handoff, or entropy.03_MQTT_Introduction.pptx



03_MQTT_Introduction.pptxABHIsingh526544
?
MQTT is a publish-subscribe messaging protocol that is lightweight and designed for constrained devices and unreliable networks. It uses topics to allow publishers and subscribers to communicate asynchronously and decoupled in time and space. MQTT has a hierarchical topic namespace that allows for wildcard subscriptions. Clients connect to a broker that handles routing of messages between publishers and subscribers based on topic filters.Analysis of the LAN Sync Protocol



Analysis of the LAN Sync ProtocolSJSU
?
The objective of this project is to analyse in-depth the behaviour of the ˇ°LAN Sync protocolˇ± adapted by Dropbox which uses distributed cloud computing storage to enable users to store and share data. Dropbox allows the computers on the same subnet or broadcast to access the network and share files with each other. This project will also help us understand about a helper protocol to LAN sync called ˇ°LAN sync Discoveryˇ±. By capturing packets with Wireshark we will conduct a detailed research on the LAN sync protocol.Module 1 slides



Module 1 slidesAnaniaKapala
?
This document provides an overview of CCNA Module 1 on internetworking. It describes the purpose of routers, switches, hubs and other network devices. It also covers networking concepts like collision domains, broadcast domains, and the operation of Ethernet networks using CSMA/CD. The document explains the OSI model layers and compares it to the TCP/IP model. It also discusses common network applications and protocols like TCP, UDP, IP, ARP and ICMP.Introduction to socket programming nbv



Introduction to socket programming nbvNagasuri Bala Venkateswarlu
?
This presentation is used in many places including Vignan, AITAM, This contains both tutorials and hands on training. This presentation explains Unix Internals, Socket programming, both data gram based and IP based concepts are explained with live examples.Week10 transport



Week10 transportkapilpahwabnb
?
The transport layer provides end-to-end communication between processes on different machines. Two main transport protocols are TCP and UDP. TCP provides reliable, connection-oriented data transmission using acknowledgments and retransmissions. UDP provides simpler, connectionless transmission but without reliability. Both protocols use port numbers to identify processes and negotiate quality of service options during connection establishment.Wireshark



Wiresharklakshya dubey
?
Wireshark is the graphical network protocol analyzer tool.
The ppt covers all the basics which will help you to kick start with wireshark.Highly available distributed databases, how they work, javier ramirez at teowaki



Highly available distributed databases, how they work, javier ramirez at teowakijavier ramirez
?
This document summarizes key aspects of distributed databases. It discusses master-slave and multi-master replication approaches. It then covers the challenges of achieving availability, partition tolerance and consistency as defined by Brewer's CAP theorem. The rest of the document dives deeper into data distribution, replication, conflict resolution, membership protocols, and allowing the system to operate during network partitions or node failures. It provides examples of gossip protocols, vector clocks, hinted handoff, and anti-entropy processes used in distributed databases. Finally, it notes that building these systems requires clients to be aware of some internal workings and allows for extra credit in building your own distributed database.Recently uploaded (20)
Next.js Development: The Ultimate Solution for High-Performance Web Apps



Next.js Development: The Ultimate Solution for High-Performance Web Appsrwinfotech31
?
The key benefits of Next.js development, including blazing-fast performance, enhanced SEO, seamless API and database integration, scalability, and expert support. It showcases how Next.js leverages Server-Side Rendering (SSR), Static Site Generation (SSG), and other advanced technologies to optimize web applications. RW Infotech offers custom solutions, migration services, and 24/7 expert support for seamless Next.js operations. Explore more :- https://www.rwit.io/technologies/next-js
2025-04-05 - Block71 Event - The Landscape of GenAI and Ecosystem.pdf



2025-04-05 - Block71 Event - The Landscape of GenAI and Ecosystem.pdfIvan Tang
?
The different layers of GenAI stack.The effectiveness of ai powered educational tools in enhancing academic perfo...



The effectiveness of ai powered educational tools in enhancing academic perfo...aebhpmqaocxhydmajf
?
The effectiveness of ai powered educational tools in enhancing academic performance and student engagement in higherHow Telemedicine App Development is Revolutionizing Virtual Care.pptx



How Telemedicine App Development is Revolutionizing Virtual Care.pptxDash Technologies Inc
?
Telemedicine app development builds software for remote doctor consultations and patient check-ups. These apps bridge healthcare professionals with patients via video calls, secure messages, and interactive interfaces. That helps practitioners to provide care without immediate face-to-face interactions; hence, simplifying access to medical care. Telemedicine applications also manage appointment scheduling, e-prescribing, and sending reminders.
Telemedicine apps do not only conduct remote consultations. They also integrate with entire healthcare platforms, such as patient forums, insurance claims processing, and providing medical information libraries. Remote patient monitoring enables providers to keep track of patients' vital signs. This helps them intervene and provide care whenever necessary. Telehealth app development eliminates geographical boundaries and facilitates easier communication.
In this blog, we will explore its market growth, essential features, and benefits for both patients and providers. Building High-Impact Teams Beyond the Product Triad.pdf



Building High-Impact Teams Beyond the Product Triad.pdfRafael Burity
?
The product triad is broken.
Not because of flawed frameworks, but because it rarely works as it should in practice.
When it becomes a battle of roles, it collapses.
It only works with clarity, maturity, and shared responsibility.GDG Cloud Southlake #41: Shay Levi: Beyond the Hype:How Enterprises Are Using AI



GDG Cloud Southlake #41: Shay Levi: Beyond the Hype:How Enterprises Are Using AIJames Anderson
?
Beyond the Hype: How Enterprises Are Actually Using AI
Webinar Abstract:
AI promises to revolutionize enterprises - but whatˇŻs actually working in the real world? In this session, we cut through the noise and share practical, real-world AI implementations that deliver results. Learn how leading enterprises are solving their most complex AI challenges in hours, not months, while keeping full control over security, compliance, and integrations. WeˇŻll break down key lessons, highlight recent use cases, and show how UnframeˇŻs Turnkey Enterprise AI Platform is making AI adoption fast, scalable, and risk-free.
Join the session to get actionable insights on enterprise AI - without the fluff.
Bio:
Shay Levi is the Co-Founder and CEO of Unframe, a company redefining enterprise AI with scalable, secure solutions. Previously, he co-founded Noname Security and led the company to its $500M acquisition by Akamai in just four years. A proven innovator in cybersecurity and technology, he specializes in building transformative solutions.Leadership Spectrum by Sonam Sherpa at GDG Kathmandu March Monthly Meetup



Leadership Spectrum by Sonam Sherpa at GDG Kathmandu March Monthly MeetupGDG Kathmandu
?
Leadership by Sonam SherpaBenefits of Moving Ellucian Banner to Oracle Cloud



Benefits of Moving Ellucian Banner to Oracle CloudAstuteBusiness
?
Discover the advantages of migrating Ellucian Banner to Oracle Cloud Infrastructure, including scalability, security, and cost efficiency for educational institutions.
HHUG-04-2025-Close-more-deals-from-your-existing-pipeline-FOR SLIDESHARE.pptx



HHUG-04-2025-Close-more-deals-from-your-existing-pipeline-FOR SLIDESHARE.pptxHampshireHUG
?
Struggling to get real value from HubSpot Sales Hub? Learn 5 mighty methods to close more deals without more leads or headcount (even on Starter subscriptions)!
These slides accompanied a webinar run by Hampshire's HubSpot User Group (HUG) on 2nd April, 2025.
HubSpot subscribers can watch the recording here: https://events.hubspot.com/events/details/hubspot-hampshire-presents-5-ways-to-close-more-deals-from-your-existing-sales-pipeline/
ABOUT THE EVENT:
Unlock hidden revenue in your CRM with our practical HubSpot tactics
Are you struggling to get real value from your HubSpot Sales Hub?
If your HubSpot feels like more of an admin burden than a revenue enabler, youˇŻre not alone. Many sales leaders find that their team isn't updating records consistently, pipeline visibility is poor, and reporting doesnˇŻt deliver the insights they need to drive strategy.
The good news? You donˇŻt need to upgrade your HubSpot subscription to sort these issues.
Join us for this webinar to learn 5 mighty tactics that will help you streamline your sales process, improve pipeline visibility, and extract more revenue from your existing pipeline, without spending more on marketing or hiring extra sales reps.
What YouˇŻll Learn
? Customising Records ¨C Increase sales momentum with more useful CRM data for your salespeople
? Pipeline Rules ¨C Improve deal stage consistency and data accuracy for improved prioritisation and forecasting
? Team Permissions & Defaults ¨C Control access and streamline processes. Spend more time selling, less on admin
? Pipeline View Customisation ¨C Get clearer sales insights, faster, to deal with revenue leaks
? Simple Sales Reports ¨C Build actionable dashboards to drive strategy with data
? Bonus: Successful Sales Hub users will share their experiences and the revenue impact it has delivered for them.
Who is this webinar for?
Sales leaders using HubSpot Sales Hub Starter, or those new to HubSpot
Sales managers who need better CRM adoption from their team
Anyone struggling with pipeline visibility, reporting, or forecasting
Teams who want to close more deals without extra sales headcount San Francisco Atlassian ACE - Mar 27 2025.pdf



San Francisco Atlassian ACE - Mar 27 2025.pdfMatt Doar
?
şÝşÝߣs from 7 vendors at. the Atlassian ACE event in SF on March 27th 2025A General introduction to Ad ranking algorithms



A General introduction to Ad ranking algorithmsBuhwan Jeong
?
Details of AD ranking algorithms and beyondDraginoĄ×ĄíĄŔĄŻĄČĄ«ĄżĄíĄ° LoRaWAN NB-IoT LTE cat.M1ÉĚĆ·ĄęĄąĄČ



DraginoĄ×ĄíĄŔĄŻĄČĄ«ĄżĄíĄ° LoRaWAN NB-IoT LTE cat.M1ÉĚĆ·ĄęĄąĄČCRI Japan, Inc.
?
DraginoĄ×ĄíĄŔĄŻĄČĄ«ĄżĄíĄ° LoRaWAN NB-IoT LTE cat.M1ÉĚĆ·ĄęĄąĄČThe metaverse : A Digital Transformation



The metaverse : A Digital Transformationmatlotloatang03
?
Dive into the fascinating world of the metaverse,a digital universe that blends virtual , augmented reality.Sugarlab AI: How Much Does an XXX AI Porn Generator Cost in 2025



Sugarlab AI: How Much Does an XXX AI Porn Generator Cost in 2025Sugarlab AI
?
The cost of an XXX AI porn generator in 2025 varies depending on factors like AI sophistication, subscription plans, and additional expenses. Whether you're looking for a free AI porn video generator or a premium adult AI image generator, pricing ranges from basic tools to enterprise-level solutions. This article breaks down the costs, features, and what to expect from AI-driven adult content platforms.Recruiting Tech: A Look at Why AI is Actually OG



Recruiting Tech: A Look at Why AI is Actually OGMatt Charney
?
A lot of recruiting technology vendors out there are talking about how they're offering the first ever (insert AI use case here), but turns out, everything they're selling as innovative or cutting edge has been around since Yahoo! and MySpace were category killers. Here's the receipts.The Future of Materials: Transitioning from Silicon to Alternative Metals



The Future of Materials: Transitioning from Silicon to Alternative Metalsanupriti
?
This presentation delves into the emerging technologies poised to revolutionize the world of computing. From carbon nanotubes and graphene to quantum computing and DNA-based systems, discover the next-generation materials and innovations that could replace or complement traditional silicon chips. Explore the future of computing and the breakthroughs that are shaping a more efficient, faster, and sustainable technological landscape.Columbia Weather Systems - Product Overview



Columbia Weather Systems - Product OverviewColumbia Weather Systems
?
Columbia Weather Systems offers professional weather stations in basically three configurations for industry and government agencies worldwide: Fixed-Base or Fixed-Mount Weather Stations, Portable Weather Stations, and Vehicle-Mounted Weather Stations.
Models include all-in-one sensor configurations as well as modular environmental monitoring systems. Real-time displays include hardware console, WeatherMaster? Software, and a Weather MicroServer? with industrial protocols, web and app monitoring options.
Innovative Weather Monitoring: Trusted by industry and government agencies worldwide. Professional, easy-to-use monitoring options. Customized sensor configurations. One-year warranty with personal technical support. Proven reliability, innovation, and brand recognition for over 45 years.202408_JAWSPANKRATION_Introduction_of_Minaden.pdf



202408_JAWSPANKRATION_Introduction_of_Minaden.pdfNTTDOCOMO-ServiceInnovation
?
202408łĺ´ł´ˇ°Âł§±Ę´ˇ±·°¸é´ˇ°Ő±ő°ż±·łĺ×îÖŐ°ć.±č»ĺ´ÚWhy Outsource Accounting to India A Smart Business Move!.pdf



Why Outsource Accounting to India A Smart Business Move!.pdfanjelinajones6811
?
Outsource Accounting to India to reduce costs, access skilled professionals, and streamline financial operations. Indian accounting firms offer expert services, advanced technology, and round-the-clock support, making it a smart choice for businesses looking to improve efficiency and focus on growth.
MQTT + DASH7 Integration
- 1. DASH7 with MQTT? [Application Note]
- 2. DASH7istheOppositeofTCP DASH7ˇŻs networking technology is different than TCP/IP.? DASH7 is designed to handle small data, but lots of devices at the same time. ? TCP/IP handles large data, but only between two devices. 2
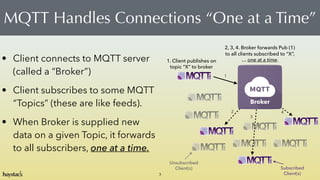
- 3. MQTT Handles Connections ˇ°One at a Timeˇ± 3 ? Client connects to MQTT server (called a ˇ°Brokerˇ±) ? Client subscribes to some MQTT ˇ°Topicsˇ± (these are like feeds). ? When Broker is supplied new data on a given Topic, it forwards to all subscribers, one at a time. Broker Unsubscribed? Client(s) Subscribed? Client(s) 1. Client publishes on? topic ˇ°Xˇ± to broker 1 2 3 4 2, 3, 4. Broker forwards Pub (1)? to all clients subscribed to ˇ°Xˇ±, ˇ one at a time.
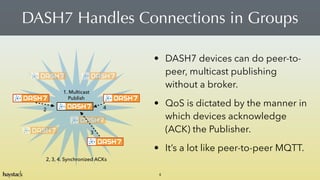
- 4. DASH7 Handles Connections in Groups 4 ? DASH7 devices can do peer-to- peer, multicast publishing without a broker. ? QoS is dictated by the manner in which devices acknowledge (ACK) the Publisher. ? ItˇŻs a lot like peer-to-peer MQTT. 1. Multicast ? Publish 2, 3, 4. Synchronized ACKs 2 3 4
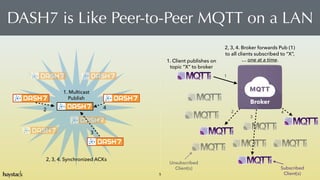
- 5. DASH7 is Like Peer-to-Peer MQTT on a LAN 5 Broker Unsubscribed? Client(s) Subscribed? Client(s) 1. Client publishes on? topic ˇ°Xˇ± to broker 1 2 3 4 2, 3, 4. Broker forwards Pub (1)? to all clients subscribed to ˇ°Xˇ±, ˇ one at a time. 1. Multicast ? Publish 2, 3, 4. Synchronized ACKs 2 3 4
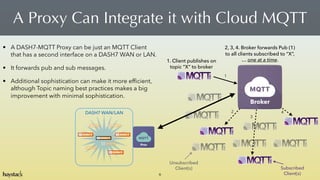
- 6. A Proxy Can Integrate it with Cloud MQTT 6 Broker Unsubscribed? Client(s) Subscribed? Client(s) 1. Client publishes on? topic ˇ°Xˇ± to broker 1 2 3 4 2, 3, 4. Broker forwards Pub (1)? to all clients subscribed to ˇ°Xˇ±, ˇ one at a time. DASH7 WAN/LAN Prox ? A DASH7-MQTT Proxy can be just an MQTT Client that has a second interface on a DASH7 WAN or LAN. ? It forwards pub and sub messages. ? Additional sophistication can make it more ef?cient, although Topic naming best practices makes a big improvement with minimal sophistication.
- 7. Topic Naming Best Practices 7 Keep topic names below 16 chars. ? e.g. topic/this_is_too_long ? e.g. topic/titl ˇŞ (ok) DASH7 devices have limited communication bandwidth and memory. Queries work fastest on strings 16 characters or less. Use Path separators to de?ne hierarchies based on data latency requirements. ? e.g. rt/temp ? e.g. noncrit/temp Here, we have real-time and ˇ°non-criticalˇ± groups of temperature sensors. This structure allows the proxy to be more intelligent. Wildcards are cool. ? e.g. rt/# ? e.g. #/temp ˇŞ (not advisable for std MQTT) DASH7 querying supports wildcards and other search features. The second topic will bog down a normal MQTT network, but a DASH7-MQTT proxy can actually handle it without much drama. The ˇ°ID/ˇ° topic can be used for addressing ? e.g. ID/# ˇŞ (broadcast) ? e.g. ID/0790 ˇŞ (16bit LAN address) ? e.g. ID/DA5701A976B31F54 ˇŞ (MAC) This is a way to tunnel direct device addressing through an MQTT proxy. (And yes, wildcards can be used with partial addressing)


