Network Security through IP Packet Filtering
- 1. Network (In)Security Through IP Packet Filtering By : Karim Baidar
- 2. Purpose • This paper examines the utility of IP packet filtering as a network security measure. • It describes what packet filters might examine in each packet. • It describes the characteristics of common application protocols as they relate to packet filtering. • This paper identifies and examines problems common to many current packet filtering implementations. • This paper concludes that packet filtering is currently a viable network security mechanism.
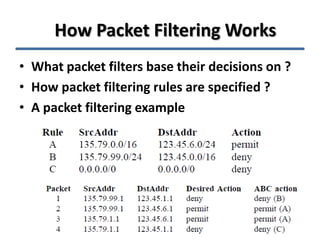
- 3. How Packet Filtering Works • What packet filters base their decisions on ? • How packet filtering rules are specified ? • A packet filtering example
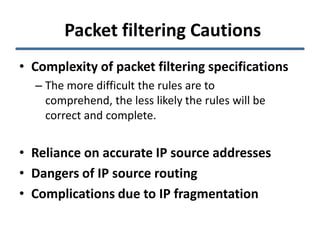
- 4. Packet filtering Cautions • Complexity of packet filtering specifications – The more difficult the rules are to comprehend, the less likely the rules will be correct and complete. • Reliance on accurate IP source addresses • Dangers of IP source routing • Complications due to IP fragmentation
- 5. Problems With Current Packet Filtering Implementations • Filters are difficult to configure. • Tabular filtering rule structures are too cumbersome. • Testing and monitoring filters is difficult.
- 6. Possible Solutions for Current Packet Filtering Problems • Improve filter specification syntax. • Allow inbound filters as well as outbound filters. – This would allow the administrator to position the router either "inside" or "outside" the filtering "fence“ , as appropriate. – The desired functionality may not even be possible with only outbound filters; the case of a fake internal-to-internal packet showing up on the external interface, can’t be detected in an outbound filter set. • Provide tools for developing, testing, and monitoring filters.
- 8. Conclusion • Packet filtering is currently a viable and valuable network security tool, but some simple vendor improvements could have a big impact. • Improvements to filter specification mechanisms could greatly simplify the lives of network administrators trying to use packet filtering capabilities, and increase their confidence that their filters are doing what they think they are.