Network Intrusion Detection Systems #1
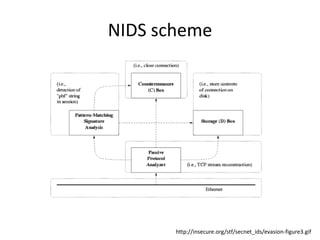
- 2. NIDS (detecton system) ŌĆó realtime attack detection ŌĆó passive (watchers) / active (measurement) systems ŌĆó via analysis ŌĆō protocol analysis ŌĆō graph analysis ŌĆō anomaly detection ŌĆó analysis of direct network traffic ŌĆō complete / light
- 4. Traffic analysis ŌĆó analyzing behaviour, not just packets ŌĆó difficulties ŌĆō NIDS can be run from different part of network ŌĆō bad packets ŌĆō reordering issues ŌĆó sensor placement ŌĆō inline ŌĆō passive ŌĆó spanning port ŌĆó network tap ŌĆó load balancer
- 7. Signature-based analysis ŌĆó pattern matching ŌĆó ŌĆ£patterns of malicious trafficŌĆØ ŌĆó very elementary (basically grepping) + huge community for rule generation + great for low level analysis (rules are very specific) + not taking too much resources - lower performance with big ruleset - slight attack variation can beat the rule
- 8. Rule example # alert tcp $EXTERNAL_NET any -> $HOME_NET 53 ( msg:"OS-SOLARIS EXPLOIT sparc overflow attempt"; flow:to_server,established; content:"|90 1A C0 0F 90 02| |08 92 02| |0F D0 23 BF F8|"; fast_pattern:only; metadata:ruleset community, service dns; classtype:attempted-admin; sid:267; rev:13; )
- 9. Protocol-based analysis ŌĆó reviewing network data ŌĆó strictly based on layer headers ŌĆó knowledge of expected values + better possibility for scalability + generic, able to catch zero-day exploits - protocol headers preprocessor need resources - rules can get extremely difficult to write/understand - provide low information, admin has to investigate
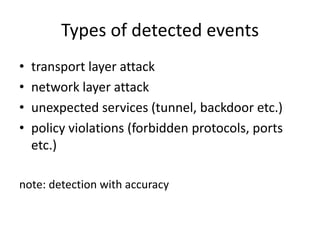
- 10. Types of detected events ŌĆó transport layer attack ŌĆó network layer attack ŌĆó unexpected services (tunnel, backdoor etc.) ŌĆó policy violations (forbidden protocols, ports etc.) note: detection with accuracy
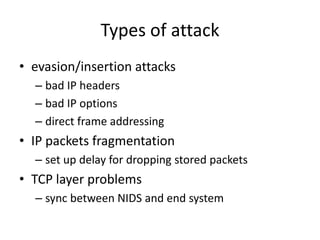
- 11. Types of attack ŌĆó evasion/insertion attacks ŌĆō bad IP headers ŌĆō bad IP options ŌĆō direct frame addressing ŌĆó IP packets fragmentation ŌĆō set up delay for dropping stored packets ŌĆó TCP layer problems ŌĆō sync between NIDS and end system
- 12. Prevention ŌĆó passive ŌĆō ending TCP stream ŌĆó inline ŌĆō inline firewalling ŌĆō throttling bandwith usage ŌĆō altering malicious content ŌĆó passive and inline ŌĆō running third party script ŌĆō reconfiguring other network devices
- 13. Toolset ŌĆó SNORT ŌĆō opensource ŌĆō windows / linux ŌĆō lots of plugins ŌĆó OSSIM (security information and event management) ŌĆó Sguil (network security monitor)
- 14. SNORT ŌĆó started as sniffer in 1998 ŌĆó sniffer, packet logger, and NIDS ŌĆó most used open-source NIDS right now ŌĆó loads of add-ons ŌĆó big and stable community (regular community rule releases)
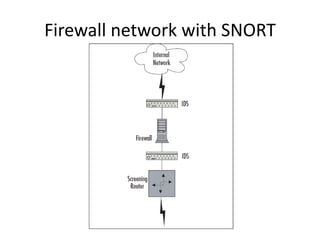
- 15. Firewall network with SNORT
- 16. SNORT add-ons ŌĆó DumbPig ŌĆō bad rule grammar detection ŌĆó OfficeCat ŌĆō search for vurneabilities in Microsoft Office docs ŌĆó SnoGE ŌĆō reporting tool parsing your logs and visualising them as points at Google Maps ŌĆó Oinkmaster ŌĆō tool for creating and managing rules ŌĆó iBlock ŌĆō daemon grepping alert file and blocking offending hosts http://www.snort.org/snort-downloads/additional-downloads
- 17. Q&A