Network Security
Download as pptx, pdf1 like254 views
The document discusses various aspects of network security including cryptography, steganography, cyber crimes, ethical hacking, firewalls, and security mechanisms. It defines cryptography as the security rendered towards a network and describes different types of cryptography such as substitution ciphers, transposition ciphers, secret key cryptography, and public key cryptography. The document also covers cyber crimes, security threats, and the importance of security across different computing environments.
1 of 15
Download to read offline











Ad
Recommended
Password policies
Password policiesAri Elias-Bachrach
╠²
This document discusses problems with current methods of measuring password strength and proposes alternatives. It argues that calculating password complexity based only on total possible combinations is flawed, as it doesn't account for human behavior. Password cracking data shows most common passwords account for a large percentage of those in use. The document proposes analyzing actual password leaks and policies to quantify the risk of different policies. This would allow informed decisions on policies and a true measure of their effectiveness.Steganalysis of LSB Embedded Images Using Gray Level Co-Occurrence Matrix
Steganalysis of LSB Embedded Images Using Gray Level Co-Occurrence MatrixCSCJournals
╠²
The paper presents a steganalysis technique for grayscale and color images using the gray level co-occurrence matrix (GLCM) to identify differences between stego and non-stego images. This method utilizes various feature vectors derived from GLCM and employs distance measures for classification, demonstrating improved performance compared to existing techniques against LSB steganographic schemes. Experimental results indicate that the technique effectively detects hidden messages across a range of payload sizes.Honeypot and Steganography
Honeypot and SteganographyPreeti Yadav
╠²
This document contains a presentation on honeypots and steganography. It includes sections on honeypots that define them, discuss their history and classification, and describe their applications and advantages/disadvantages. It also includes sections on steganography that define it, discuss techniques like LSB insertion, and describe applications. The presentation provides an overview of honeypots and steganography for educational purposes.Steganography
Steganographysandeipz
╠²
This document provides an overview of steganography, which is the practice of hiding secret information within other non-secret digital files like images, audio, or video. The document discusses the history of steganography from ancient times using techniques like hidden tattoos or wax tablets, to its modern uses with digital files and tools. Advantages include secrecy between sender and receiver, while disadvantages include potential use by terrorists. The document contrasts steganography with cryptography, noting that steganography hides the existence of secret messages within other files, while cryptography encrypts messages but does not hide their existence.Steganography
SteganographySonam M
╠²
This document provides an overview of steganography, including its definition, history, differences from cryptography, techniques used, and applications. Steganography involves concealing secret messages within ordinary files like images, audio, or video in order to hide the very existence of communication. Common techniques include least significant bit insertion and substitution. While steganography can benefit covert communication, it also enables malicious uses and is vulnerable to steganalysis attacks aimed at detecting hidden messages. The document outlines both advantages and limitations of steganography.Steganography and watermarking
Steganography and watermarkingsudip nandi
╠²
This document provides an overview of steganography and watermarking techniques for hiding information in digital media. It defines steganography as "covered writing" involving hiding secret messages within other digital files like images, audio, or video. Common steganography methods embed data in the least significant bits of pixels or audio samples. Watermarking differs in embedding identifying marks that are robust to modifications and aim to protect copyrights. The document outlines various media and techniques for each, applications, advantages and limitations of both steganography and watermarking.Steganalysis ppt
Steganalysis pptOm Vishnoi
╠²
This document discusses different types of steganalysis algorithms used to detect hidden messages embedded in digital files such as images, audio, and video. It describes specific steganalysis algorithms designed for certain embedding techniques as well as generic algorithms that can be applied broadly. Specific image steganalysis algorithms are discussed for formats like GIF, BMP, and JPEG. Audio steganalysis targets techniques like low-bit encoding, phase coding, spread spectrum coding, and echo hiding. Video steganalysis uses a framework with watermark attack and pattern recognition stages.Image Steganography using LSB
Image Steganography using LSBSreelekshmi Sree
╠²
This document discusses steganography and image steganography techniques. It defines steganography as hiding information within other information to avoid detection. Image steganography is described as hiding data in digital images using techniques like least significant bit encoding. The document outlines the LSB algorithm, which replaces the least significant bits of image pixel values with bits of the hidden message. Examples are given to illustrate how short messages can be concealed in an image using this method.CS6701 CRYPTOGRAPHY AND NETWORK SECURITY
CS6701 CRYPTOGRAPHY AND NETWORK SECURITYKathirvel Ayyaswamy
╠²
The document covers the fundamentals of cryptography and network security, focusing on definitions, security architecture, attacks, and mechanisms. It introduces classical encryption techniques and delves into concepts such as symmetric and asymmetric ciphers, cryptanalysis, and various cryptographic systems. The document also emphasizes the importance of protecting information in transmission and storage, detailing methods like steganography and different encryption techniques.Cryptography and Network Security-ch1-4.pptx
Cryptography and Network Security-ch1-4.pptxSamiDan3
╠²
The document describes various classical encryption techniques. It discusses symmetric encryption where the same key is used for encryption and decryption. Some classical ciphers described include the Caesar cipher which shifts letters by a fixed number, monoalphabetic substitution ciphers which map each plaintext letter to a ciphertext letter, and the Playfair cipher which encrypts pairs of letters based on a 5x5 keyword matrix. It also covers cryptanalysis techniques like frequency analysis to crack classical ciphers.OS ppt Modified.pptx
OS ppt Modified.pptxStudyvAbhi
╠²
1. Cryptography is the broadest security tool available that allows for secure communication over insecure mediums. It provides confidentiality through encryption.
2. Encryption algorithms use a set of keys to encrypt messages into ciphertexts and decrypt ciphertexts back into messages. The encryption and decryption functions must be efficiently computable.
3. Symmetric encryption uses the same key to encrypt and decrypt, while asymmetric encryption uses a public key to encrypt and a private key to decrypt, allowing for secure communication without having to share private keys.Mastering Network Security: Protecting Networks from Cyber Threats with Firew...
Mastering Network Security: Protecting Networks from Cyber Threats with Firew...Sisodetrupti
╠²
The document discusses network security, outlining its importance in protecting data integrity, confidentiality, and availability amidst rising cyber threats. It details essential security services, including confidentiality, integrity, availability, authentication, authorization, and non-repudiation, with mechanisms such as encryption and access control. Additionally, it covers cryptography principles, communication security measures, and firewall types, emphasizing their roles in safeguarding networks against unauthorized access and threats.Cryptography and Network Security SESSION 1.pptx
Cryptography and Network Security SESSION 1.pptxKehkashHayat1
╠²
This document is a lecture on information security and encryption techniques from the Master of Computer Application program at Graphic Era University in Dehradun, India. It covers topics like computer security, network security, internet security, security attacks and services, security mechanisms, cryptography basics, cryptanalysis, steganography, and symmetric and public key encryption algorithms. The document provides definitions and explanations of these key concepts in information security.IEDA 3302 e-commerce_secure-communications.pptx
IEDA 3302 e-commerce_secure-communications.pptxssuser6d0da2
╠²
The document covers various foundational topics in web security, focusing on secure communications through encryption. It discusses symmetric and asymmetric encryption methods, outlining how both types work and detailing common attacks on web security, such as passive and active attacks. Additionally, it explains the use of public key infrastructure (PKI) and the processes involved in establishing secure communications between clients and servers.chapter 31 security of commun networks
chapter 31 security of commun networksMohammedAbbas653737
╠²
The document outlines Chapter 31 of a cryptography and network security text, covering the fundamental security goals of confidentiality, integrity, and availability, alongside the types of attacks that threaten these goals. It discusses various cryptographic techniques, including symmetric and asymmetric-key ciphers, and highlights the importance of message integrity, authentication, and key management. Additionally, it introduces concepts such as digital signatures and entity authentication as vital components of modern security practices.Network security
Network securityABHISHEK KUMAR
╠²
Network security involves securing computer networks and systems. It is handled by network administrators who implement security policies, software, and hardware to protect networks from unauthorized access, misuse, or denial of resources. Network security aims to authenticate users, control access to resources, and ensure confidentiality, integrity, non-repudiation and availability of networks and resources. Common methods include authentication, access control, encryption, digital signatures, and monitoring systems for security audits.Encryption by fastech
Encryption by fastechAbdulafeez Fasasi
╠²
This document discusses different types of encryption. It describes symmetric encryption which uses a single secret key for encryption and decryption. It also describes asymmetric encryption which uses a public key and private key. The document outlines some encryption algorithms like stream ciphers and block ciphers. It discusses how public key infrastructure works using certificate authorities and digital certificates. Finally, it provides examples of how encryption is used and some best practices for effective encryption.Chapter 1 information assurance and security
Chapter 1 information assurance and securitygaredew32
╠²
The document outlines a course on Information Assurance and Security aimed at final year IT students, featuring key topics such as cryptography, network security, and cybersecurity strategies. It defines Information Assurance as the management and protection of data, combining information assurance and security principles, while addressing crucial security services, mechanisms, and the nature of various cyber threats. Additionally, it emphasizes enterprise security's holistic approach to safeguarding an organization's information assets through compliance and protective measures.Cryptography
CryptographyAbhi Prithi
╠²
Cryptography is used to provide security goals like confidentiality, integrity, authentication and non-repudiation. It involves encryption of messages using algorithms and keys. Symmetric key cryptography uses a shared secret key while public key cryptography uses separate public and private keys. Cryptographic protocols specify the steps entities take to achieve security objectives like key exchange and authentication. Cryptanalysis involves techniques to break cryptographic systems and protocols.amer-network-sihubconferances-security.ppt
amer-network-sihubconferances-security.pptnavidkamrava
╠²
This document summarizes key aspects of computer system security discussed in Chapter 9. It discusses threats to system security goals like confidentiality, integrity and availability. It also covers basic cryptography techniques like encryption, hashing, digital signatures and authentication using passwords. Specific algorithms and protocols discussed include DES, AES, RSA, MD5, SHA-1 and PGP. The document stresses the importance of authentication, protecting passwords, and defending against different types of attackers.Computer and Network Security
Computer and Network SecurityMuhammad Yousuf Abdul Qadir
╠²
This document provides an overview of a lecture on computer and network security. It discusses an upcoming JCE tutorial and homework assignment. It also lists assigned readings and asks for comments. The rest of the document summarizes a high-level survey of cryptography, covering goals like confidentiality and integrity. It discusses private-key settings where parties share a secret key, and provides examples of simple encryption schemes like shift ciphers and their limitations. It emphasizes using standardized cryptographic algorithms.Information security
Information securitySina Bagherinezhad
╠²
The document discusses information security, including its history, definitions, basic principles, controls, access control, and cryptography. Key points include the preservation of confidentiality, integrity, and availability of information, as well as various methods of access control and cryptographic techniques such as RSA encryption. It provides foundational knowledge relevant to the protection of information systems against unauthorized access and threats.Crpto ppt
Crpto pptAsmita Pal
╠²
This document provides an overview of cryptography. It discusses security threats and goals, then defines cryptography as using mathematics to encrypt and decrypt data. It describes basic terms like plaintext, encryption, ciphertext, and decryption. The document outlines symmetric and asymmetric key cryptography, and examples of techniques like transposition ciphers, substitution ciphers, stream ciphers, and block ciphers. It concludes that cryptography should be used to implement network security and prevent data leakage through encryption and decryption techniques.Unit - I cyber security fundamentals part -1.pptx
Unit - I cyber security fundamentals part -1.pptxkarthikaparthasarath
╠²
This document provides an overview of cyber security fundamentals and concepts including information assurance, authentication, authorization, non-repudiation, confidentiality, integrity, and availability. It defines these terms and describes how they relate to maintaining the security properties of systems. The document also discusses specific authentication methods like factors of authentication. It explains concepts like authorization, encryption techniques including symmetric and asymmetric cryptography, and the goals of confidentiality, integrity and availability.Analysis of Cryptographic Algorithms for Network Security
Analysis of Cryptographic Algorithms for Network SecurityEditor IJCATR
╠²
This document discusses and analyzes various cryptographic algorithms used for network security. It begins with definitions of key cryptographic terms like plain text, cipher text, encryption, decryption, and keys. It then describes different types of cryptographic schemes, including symmetric, asymmetric, and hash functions. Specific algorithms are analyzed like DES, AES, RSA, and Diffie-Hellman. Factors to consider when selecting a cryptographic algorithm like speed, memory requirements, security needs, and data type are also discussed. Overall the document provides a comprehensive overview and comparison of cryptographic algorithms and their applications for network security.chapter 7.pptx
chapter 7.pptxMelkamtseganewTigabi1
╠²
The document provides an overview of network security, emphasizing the importance of preventing unauthorized access and attacks on computer systems. It outlines essential security measures such as external security, operational security, password management, and the use of firewalls and encryption methods. Additionally, it discusses types of attacks, cryptography basics, and strategies for implementing an effective security policy.A Cluster-Based Trusted Secure Multipath Routing Protocol for Mobile Ad Hoc N...
A Cluster-Based Trusted Secure Multipath Routing Protocol for Mobile Ad Hoc N...IJCNCJournal
╠²
Mobile Ad Hoc Network (MANET) is a self-organizing and flexible system. MANET systems manage sensitive data from many distinct applications in various domains. Its dynamic nature increases its vulnerability to numerous types of security threats. Many of the present approaches using indirect approaches provide false approximations of trust degrees. It is significantly required a good routing system that meets Quality of Service (QoS) standards and enhances network performance. In this paper purposed cluster-based trustworthy safe multipath routing (CTSMP-Routing) for mobile ad hoc networks (MANETs). Load balancing challenge is addressed by using a modified proportional topology optimization (MPTO) approach using geographical data related to network nodes. The Enhanced Seeker Search Optimization (ESSO) approach is used to compute trust degrees after the clustering phase considering numerous network constraints including node mobility, received signal strength, energy consumption, and cooperation rate. Assumed to be the service node, the node showing the highest degree of trust manages inter-cluster routing. We have developed a hybrid soft computing approach termed the multi-layer deep recurrent neural network (ML-DRNN) to enhance the optimal path-finding process. This method selects, among many routes between source and destination nodes, the best one quickly. The outcomes of this paper demonstrate that CTSMP-Routing provides effective protection against several attack paths within the MANET environment and displays better performance in regard to quality of service (QoS) requirements.More Related Content
Similar to Network Security (20)
CS6701 CRYPTOGRAPHY AND NETWORK SECURITY
CS6701 CRYPTOGRAPHY AND NETWORK SECURITYKathirvel Ayyaswamy
╠²
The document covers the fundamentals of cryptography and network security, focusing on definitions, security architecture, attacks, and mechanisms. It introduces classical encryption techniques and delves into concepts such as symmetric and asymmetric ciphers, cryptanalysis, and various cryptographic systems. The document also emphasizes the importance of protecting information in transmission and storage, detailing methods like steganography and different encryption techniques.Cryptography and Network Security-ch1-4.pptx
Cryptography and Network Security-ch1-4.pptxSamiDan3
╠²
The document describes various classical encryption techniques. It discusses symmetric encryption where the same key is used for encryption and decryption. Some classical ciphers described include the Caesar cipher which shifts letters by a fixed number, monoalphabetic substitution ciphers which map each plaintext letter to a ciphertext letter, and the Playfair cipher which encrypts pairs of letters based on a 5x5 keyword matrix. It also covers cryptanalysis techniques like frequency analysis to crack classical ciphers.OS ppt Modified.pptx
OS ppt Modified.pptxStudyvAbhi
╠²
1. Cryptography is the broadest security tool available that allows for secure communication over insecure mediums. It provides confidentiality through encryption.
2. Encryption algorithms use a set of keys to encrypt messages into ciphertexts and decrypt ciphertexts back into messages. The encryption and decryption functions must be efficiently computable.
3. Symmetric encryption uses the same key to encrypt and decrypt, while asymmetric encryption uses a public key to encrypt and a private key to decrypt, allowing for secure communication without having to share private keys.Mastering Network Security: Protecting Networks from Cyber Threats with Firew...
Mastering Network Security: Protecting Networks from Cyber Threats with Firew...Sisodetrupti
╠²
The document discusses network security, outlining its importance in protecting data integrity, confidentiality, and availability amidst rising cyber threats. It details essential security services, including confidentiality, integrity, availability, authentication, authorization, and non-repudiation, with mechanisms such as encryption and access control. Additionally, it covers cryptography principles, communication security measures, and firewall types, emphasizing their roles in safeguarding networks against unauthorized access and threats.Cryptography and Network Security SESSION 1.pptx
Cryptography and Network Security SESSION 1.pptxKehkashHayat1
╠²
This document is a lecture on information security and encryption techniques from the Master of Computer Application program at Graphic Era University in Dehradun, India. It covers topics like computer security, network security, internet security, security attacks and services, security mechanisms, cryptography basics, cryptanalysis, steganography, and symmetric and public key encryption algorithms. The document provides definitions and explanations of these key concepts in information security.IEDA 3302 e-commerce_secure-communications.pptx
IEDA 3302 e-commerce_secure-communications.pptxssuser6d0da2
╠²
The document covers various foundational topics in web security, focusing on secure communications through encryption. It discusses symmetric and asymmetric encryption methods, outlining how both types work and detailing common attacks on web security, such as passive and active attacks. Additionally, it explains the use of public key infrastructure (PKI) and the processes involved in establishing secure communications between clients and servers.chapter 31 security of commun networks
chapter 31 security of commun networksMohammedAbbas653737
╠²
The document outlines Chapter 31 of a cryptography and network security text, covering the fundamental security goals of confidentiality, integrity, and availability, alongside the types of attacks that threaten these goals. It discusses various cryptographic techniques, including symmetric and asymmetric-key ciphers, and highlights the importance of message integrity, authentication, and key management. Additionally, it introduces concepts such as digital signatures and entity authentication as vital components of modern security practices.Network security
Network securityABHISHEK KUMAR
╠²
Network security involves securing computer networks and systems. It is handled by network administrators who implement security policies, software, and hardware to protect networks from unauthorized access, misuse, or denial of resources. Network security aims to authenticate users, control access to resources, and ensure confidentiality, integrity, non-repudiation and availability of networks and resources. Common methods include authentication, access control, encryption, digital signatures, and monitoring systems for security audits.Encryption by fastech
Encryption by fastechAbdulafeez Fasasi
╠²
This document discusses different types of encryption. It describes symmetric encryption which uses a single secret key for encryption and decryption. It also describes asymmetric encryption which uses a public key and private key. The document outlines some encryption algorithms like stream ciphers and block ciphers. It discusses how public key infrastructure works using certificate authorities and digital certificates. Finally, it provides examples of how encryption is used and some best practices for effective encryption.Chapter 1 information assurance and security
Chapter 1 information assurance and securitygaredew32
╠²
The document outlines a course on Information Assurance and Security aimed at final year IT students, featuring key topics such as cryptography, network security, and cybersecurity strategies. It defines Information Assurance as the management and protection of data, combining information assurance and security principles, while addressing crucial security services, mechanisms, and the nature of various cyber threats. Additionally, it emphasizes enterprise security's holistic approach to safeguarding an organization's information assets through compliance and protective measures.Cryptography
CryptographyAbhi Prithi
╠²
Cryptography is used to provide security goals like confidentiality, integrity, authentication and non-repudiation. It involves encryption of messages using algorithms and keys. Symmetric key cryptography uses a shared secret key while public key cryptography uses separate public and private keys. Cryptographic protocols specify the steps entities take to achieve security objectives like key exchange and authentication. Cryptanalysis involves techniques to break cryptographic systems and protocols.amer-network-sihubconferances-security.ppt
amer-network-sihubconferances-security.pptnavidkamrava
╠²
This document summarizes key aspects of computer system security discussed in Chapter 9. It discusses threats to system security goals like confidentiality, integrity and availability. It also covers basic cryptography techniques like encryption, hashing, digital signatures and authentication using passwords. Specific algorithms and protocols discussed include DES, AES, RSA, MD5, SHA-1 and PGP. The document stresses the importance of authentication, protecting passwords, and defending against different types of attackers.Computer and Network Security
Computer and Network SecurityMuhammad Yousuf Abdul Qadir
╠²
This document provides an overview of a lecture on computer and network security. It discusses an upcoming JCE tutorial and homework assignment. It also lists assigned readings and asks for comments. The rest of the document summarizes a high-level survey of cryptography, covering goals like confidentiality and integrity. It discusses private-key settings where parties share a secret key, and provides examples of simple encryption schemes like shift ciphers and their limitations. It emphasizes using standardized cryptographic algorithms.Information security
Information securitySina Bagherinezhad
╠²
The document discusses information security, including its history, definitions, basic principles, controls, access control, and cryptography. Key points include the preservation of confidentiality, integrity, and availability of information, as well as various methods of access control and cryptographic techniques such as RSA encryption. It provides foundational knowledge relevant to the protection of information systems against unauthorized access and threats.Crpto ppt
Crpto pptAsmita Pal
╠²
This document provides an overview of cryptography. It discusses security threats and goals, then defines cryptography as using mathematics to encrypt and decrypt data. It describes basic terms like plaintext, encryption, ciphertext, and decryption. The document outlines symmetric and asymmetric key cryptography, and examples of techniques like transposition ciphers, substitution ciphers, stream ciphers, and block ciphers. It concludes that cryptography should be used to implement network security and prevent data leakage through encryption and decryption techniques.Unit - I cyber security fundamentals part -1.pptx
Unit - I cyber security fundamentals part -1.pptxkarthikaparthasarath
╠²
This document provides an overview of cyber security fundamentals and concepts including information assurance, authentication, authorization, non-repudiation, confidentiality, integrity, and availability. It defines these terms and describes how they relate to maintaining the security properties of systems. The document also discusses specific authentication methods like factors of authentication. It explains concepts like authorization, encryption techniques including symmetric and asymmetric cryptography, and the goals of confidentiality, integrity and availability.Analysis of Cryptographic Algorithms for Network Security
Analysis of Cryptographic Algorithms for Network SecurityEditor IJCATR
╠²
This document discusses and analyzes various cryptographic algorithms used for network security. It begins with definitions of key cryptographic terms like plain text, cipher text, encryption, decryption, and keys. It then describes different types of cryptographic schemes, including symmetric, asymmetric, and hash functions. Specific algorithms are analyzed like DES, AES, RSA, and Diffie-Hellman. Factors to consider when selecting a cryptographic algorithm like speed, memory requirements, security needs, and data type are also discussed. Overall the document provides a comprehensive overview and comparison of cryptographic algorithms and their applications for network security.chapter 7.pptx
chapter 7.pptxMelkamtseganewTigabi1
╠²
The document provides an overview of network security, emphasizing the importance of preventing unauthorized access and attacks on computer systems. It outlines essential security measures such as external security, operational security, password management, and the use of firewalls and encryption methods. Additionally, it discusses types of attacks, cryptography basics, and strategies for implementing an effective security policy.Recently uploaded (20)
A Cluster-Based Trusted Secure Multipath Routing Protocol for Mobile Ad Hoc N...
A Cluster-Based Trusted Secure Multipath Routing Protocol for Mobile Ad Hoc N...IJCNCJournal
╠²
Mobile Ad Hoc Network (MANET) is a self-organizing and flexible system. MANET systems manage sensitive data from many distinct applications in various domains. Its dynamic nature increases its vulnerability to numerous types of security threats. Many of the present approaches using indirect approaches provide false approximations of trust degrees. It is significantly required a good routing system that meets Quality of Service (QoS) standards and enhances network performance. In this paper purposed cluster-based trustworthy safe multipath routing (CTSMP-Routing) for mobile ad hoc networks (MANETs). Load balancing challenge is addressed by using a modified proportional topology optimization (MPTO) approach using geographical data related to network nodes. The Enhanced Seeker Search Optimization (ESSO) approach is used to compute trust degrees after the clustering phase considering numerous network constraints including node mobility, received signal strength, energy consumption, and cooperation rate. Assumed to be the service node, the node showing the highest degree of trust manages inter-cluster routing. We have developed a hybrid soft computing approach termed the multi-layer deep recurrent neural network (ML-DRNN) to enhance the optimal path-finding process. This method selects, among many routes between source and destination nodes, the best one quickly. The outcomes of this paper demonstrate that CTSMP-Routing provides effective protection against several attack paths within the MANET environment and displays better performance in regard to quality of service (QoS) requirements.Cadastral Maps
Cadastral MapsGoogle
╠²
Preparation of cadastral maps based by Engineer Dungo Tizazu from Dire Dawa University David Boutry - Mentors Junior Developers
David Boutry - Mentors Junior DevelopersDavid Boutry
╠²
David Boutry is a Senior Software Engineer in New York with expertise in high-performance data processing and cloud technologies like AWS and Kubernetes. With over eight years in the field, he has led projects that improved system scalability and reduced processing times by 40%. He actively mentors aspiring developers and holds certifications in AWS, Scrum, and Azure.Abraham Silberschatz-Operating System Concepts (9th,2012.12).pdf
Abraham Silberschatz-Operating System Concepts (9th,2012.12).pdfShabista Imam
╠²
Complete book of operating system edition 9Fundamentals of Digital Design_Class_12th April.pptx
Fundamentals of Digital Design_Class_12th April.pptxdrdebarshi1993
╠²
Boolean Algebra and Combinational Logic CircuitInternational Journal of Advanced Information Technology (IJAIT)
International Journal of Advanced Information Technology (IJAIT)ijait
╠²
International journal of advanced Information technology (IJAIT) is a bi monthly open access peer-
reviewed journal, will act as a major forum for the presentation of innovative ideas, approaches,
developments, and research projects in the area advanced information technology applications and
services. It will also serve to facilitate the exchange of information between researchers and industry
professionals to discuss the latest issues and advancement in the area of advanced IT. Core areas of
advanced IT and multi-disciplinary and its applications will be covered during the conferences.Tally.ERP 9 at a Glance.book - Tally Solutions .pdf
Tally.ERP 9 at a Glance.book - Tally Solutions .pdfShabista Imam
╠²
Tally.ERP 9 at a Glance.book, a fully completed guidance to learn tally erp 9.0Fundamentals of Digital Design_Class_21st May - Copy.pptx
Fundamentals of Digital Design_Class_21st May - Copy.pptxdrdebarshi1993
╠²
Basics of Number Systems and Logic GatesVARICELLA VACCINATION: A POTENTIAL STRATEGY FOR PREVENTING MULTIPLE SCLEROSIS
VARICELLA VACCINATION: A POTENTIAL STRATEGY FOR PREVENTING MULTIPLE SCLEROSISijab2
╠²
Multiple sclerosis (MS) is a debilitating neurological condition affecting approximately 2.9 million people worldwide. Its cause remains unclear but environmental factors, such as post-childhood Epstein-Barr virus (EBV) infection, are thought to contribute to MS incidence. ElysiumPro Company Profile 2025-2026.pdf
ElysiumPro Company Profile 2025-2026.pdfinfo751436
╠²
Description
ElysiumPro | IEEE Final Year Projects | Best Internship Training | Inplant Training in Madurai
Best Final Year project training center
Address:
First Floor, A Block, 'Elysium Campus, 229, Church Rd, Vaigai Colony, Madurai, Tamil Nadu 625020
Plus Code:
W4CX+56 Madurai, Tamil Nadu
+91 9944793398
info@elysiumpro.in
Elysium Group of Companies established ElysiumPro in 2001. Since its inception, it has been the most sought-after destination for final year project development and research papers among the students. Our commitment to providing quality project training & documentation to students has always been exceptional. We deliver the final year engineering projects and technical documents that provide extra edge and industry exposure to land prestigious jobs and reputed institutions for higher studies. Students from all over the country avail of our services for their final year projects. On average, we develop 5000+ projects and research papers per year on varied advanced domains. Python, JAVA, PHP, Android, Matlab, LabView, VLSI, SIMULINK, Power electronics, Power System, Antenna, Machine Learning, Deep Learning, Data Science, Artificial Intelligence, data Mining, Big Data, Cloud Computing, IoT,
Hours of Operation: -
Sunday 10am-1pm
Monday 7.30am-8pm
Tuesday 7.30am-8pm
Wednesday 7.30am-8pm
Thursday 7.30am-8pm
Friday 7.30am-8pm
Saturday 7.30am-8pm
Web Site:
https://elysiumpro.in/
*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*
Youtube Geotagged Video:
https://youtu.be/QULY6XfuMyo
*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*
║▌║▌▀Żshow Images (Google Photos):
https://photos.app.goo.gl/hVwQJtkeptA1JZKd9
*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*
GBP Listing:
https://goo.gl/maps/6d6hko6TsDYyeDrz9
*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*
Serving Areas:
https://www.google.com/maps/d/edit?mid=1-fsZogBiEAcjGP_aDyI0UKKIcwVUWfo&usp=sharing
*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*
Google Site:
https://elysiumpro-project-center.business.site
*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*
Google Sheet: https://docs.google.com/spreadsheets/d/1uXA07zxrUx2FCnBZWH80PpBZQrrX-2q1UBBe_0k3Yeo
*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*
Google Document: https://docs.google.com/document/d/1BU4ZHW_41XJm2lvTq9pWYUpZILAEmF9dWEw7-DBbWoE
*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*
Google ║▌║▌▀Żs: https://docs.google.com/presentation/d/1uF8q6ueJWcAnhKTQsZxLE0Bo9PwgRNwCeuGV_ZgbSyU
*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*-*Complete University of Calculus :: 2nd edition
Complete University of Calculus :: 2nd editionShabista Imam
╠²
Master the language of change with the Complete Guidance Book of CalculusŌĆöyour comprehensive resource for understanding the core concepts and applications of differential and integral calculus. Designed for high school, college, and self-study learners, this book takes a clear, intuitive approach to a subject often considered challenging.FUNDAMENTALS OF COMPUTER ORGANIZATION AND ARCHITECTURE
FUNDAMENTALS OF COMPUTER ORGANIZATION AND ARCHITECTUREShabista Imam
╠²
FUNDAMENTALS OF COMPUTER ORGANIZATION AND ARCHITECTURE
By : Mostafa Abd-El-Barr & Hesham El-Rewini:: wiley
A complete guidance bookAd
Network Security
- 1. The Security that we render towards a NETWORK is called Bh Durga Adithya Varma , CSE-A , 12N31A0532
- 2. 1. Cryptography 2. Types of Cryptography 3. Steganography 4. Cyber Crime/Attack 5. Ethical Hacking 6. Fire Walling 7. Security Mechanisms 8. Security Services 9. Security Threats Bh Durga Adithya Varma , CSE-A , 12N31A0532
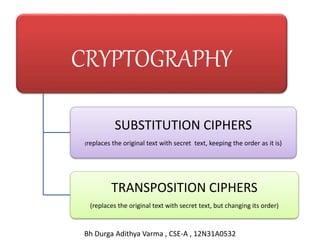
- 3. CRYPTOGRAPHY SUBSTITUTION CIPHERS (replaces the original text with secret text, keeping the order as it is) TRANSPOSITION CIPHERS (replaces the original text with secret text, but changing its order) Bh Durga Adithya Varma , CSE-A , 12N31A0532
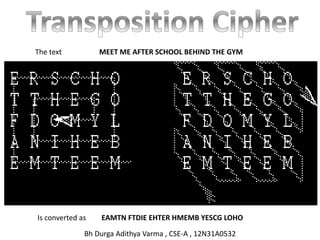
- 4. Plain Text Letters: A B C D E F G H I J K L M N O P Q R S T U V W X Y Z Cipher Text Letters: Q W R T Y U I O P A S D F G H J K L Z X C V B N M The text MEET ME AFTER SCHOOL BEHIND THE GYM Is converted as DTTZD TQYZT KLEIG GSWTI OFRZI TUNDM Bh Durga Adithya Varma , CSE-A , 12N31A0532
- 5. The text MEET ME AFTER SCHOOL BEHIND THE GYM Is converted as EAMTN FTDIE EHTER HMEMB YESCG LOHO Bh Durga Adithya Varma , CSE-A , 12N31A0532
- 6. 1.SECRET KEY CRYPTOGRAPHY 2.PUBLIC KEY CRYPTOGRAPHY Bh Durga Adithya Varma , CSE-A , 12N31A0532
- 7. Plain Text Cipher Text Cipher text Plain Text Key Encryption Decryption Bh Durga Adithya Varma , CSE-A , 12N31A0532
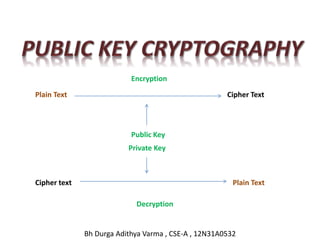
- 8. Encryption Plain Text Cipher Text Cipher text Plain Text Decryption Public Key Private Key Bh Durga Adithya Varma , CSE-A , 12N31A0532
- 9. (Crime is an illegal act if it is done in NETWORKING it is CYBER CRIME)
- 10. Security System that protect your PCŌĆÖs or NETWORK from HACKERS,INTRUDERS &MALICIOUS CODE Bh Durga Adithya Varma , CSE-A , 12N31A0532
- 11. A mechanism that is designed to detect, prevent, or recover from a security attack Bh Durga Adithya Varma , CSE-A , 12N31A0532
- 12. 1. Normal Flow 2. Interruption 3. Interception 4. Modification 5. Fabrication Bh Durga Adithya Varma , CSE-A , 12N31A0532
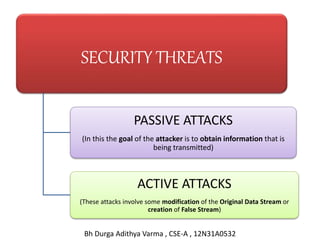
- 13. SECURITY THREATS PASSIVE ATTACKS (In this the goal of the attacker is to obtain information that is being transmitted) ACTIVE ATTACKS (These attacks involve some modification of the Original Data Stream or creation of False Stream) Bh Durga Adithya Varma , CSE-A , 12N31A0532
- 14. CONCLUSION Security is to be given to each and every Environments whether it is our Personal Computing Environment (or) Time Sharing Environment (or) Client-Server Environment (or) Distributed Computing Environment. Bh Durga Adithya Varma , CSE-A , 12N31A0532
- 15. Bh Durga Adithya Varma , CSE-A , 12N31A0532
