Networking For Ethical Hacking (Hackers)
- 2. What is Networking? Networking means connecting multiple devices (like computers, phones, routers) so they can communicate and share information with each other. Example: Imagine you have a Wi-Fi router at home. ŌĆóYour phone, laptop, and TV are connected to it. ŌĆóThey can access the internet and even share files with each other.
- 4. 1’ĖÅŌāŻ The Internet (Cloud Icon at the Top) ŌĆóThe Internet is like a huge ocean of data where all websites, services, and online platforms exist. ŌĆóYour network (home or office) connects to this vast Internet through an ISP (Internet Service Provider) like Jio, Airtel, or BSNL. 2’ĖÅŌāŻ Firewall (Black Box with Fire Symbol) ŌĆóBefore data enters your network, it first passes through the firewall. ŌĆóThe firewall checks if the data is safe or harmful. If it detects malware, hacking attempts, or suspicious activity, it blocks the data. 3’ĖÅŌāŻ Router (Middle Device with Wi-Fi Signals) ŌĆóIf the firewall allows the data, it is sent to the router. ŌĆóThe router distributes Internet access to all connected devices (PCs, laptops, mobile phones, etc.). 4’ĖÅŌāŻ Connected Devices (PCs, Laptops, Mobiles, Printer, Tablet, etc.) ŌĆóThese devices can now safely access the Internet for browsing, downloading, gaming, and more.
- 5. Step-by-Step Journey of YouTube Data to Your Mobile 1’ĖÅŌāŻ You Open YouTube and Click a Video ŌĆóYour mobile sends a request to YouTube to play a video. ŌĆóThis request is sent via the Internet to YouTubeŌĆÖs servers. 2’ĖÅŌāŻ Your Request is Processed by YouTubeŌĆÖs Servers ŌĆóYouTubeŌĆÖs servers are located in Google Data Centers across the world. ŌĆóBut YouTube does not always send data directly from the USA or other countries. Instead, it uses CDNs (Content Delivery Networks). 3’ĖÅŌāŻ CDN (Content Delivery Network) Delivers the Video ŌĆóYouTube has CDN servers in India (like in Mumbai, Chennai, Delhi, etc.). ŌĆóThese servers store copies of popular videos to reduce loading time. ŌĆóIf the video you requested is in a nearby CDN server, it sends the data quickly to your mobile. ŌĆóIf not, your request goes to a main YouTube server (Google Data Center), which then sends the data. 4’ĖÅŌāŻ Data Travels Through the Internet (ISP Networks) ŌĆóYouTube data is broken into small packets and sent to your mobile. ŌĆóThese packets travel through undersea fiber optic cables, satellites, and local telecom networks to reach India. ŌĆóYour ISP (Internet Service Provider) like Jio, Airtel, or BSNL routes the data to your mobile network. 5’ĖÅŌāŻ Mobile Network Delivers Data to Your Phone ŌĆóThe ISP sends the data to a cell tower near your location. ŌĆóThe tower transmits the video via 4G/5G signals to your mobile phone. 6’ĖÅŌāŻ Your Mobile Reassembles the Data and Plays the Video ŌĆóYour phone receives the video packets, puts them together, and starts playing the YouTube video.
- 6. Important Networking Protocols What is IPv4? (Old Address System) ŌĆóIPv4 is like the old address system in a city, where there are only 4.3 billion (430 crores) houses (addresses). ŌĆóLooks like this: 192.168.1.1 (Just a way to write an address, donŌĆÖt worry about the numbers). ŌĆóThe problem? Too many people moved in, and we ran out of addresses! Example: Imagine a small town planned for 4.3 billion houses, but suddenly 8 billion people want to live there. Not enough houses for everyone! The Problem: ŌĆóIf every device (phone, laptop, smart TV) needs a unique IPv4 address, we donŌĆÖt have enough. ŌĆóSolution? NAT (Network Address Translation) ŌĆō Sharing Addresses! IP Address (Internet Protocol Address) is a unique identifier assigned to each device on a network.
- 7. What is NAT? (Sharing One Address Among Many Devices) Since IPv4 ran out of addresses, we had to find a way to fit more people into the same houses. Solution: NAT (Network Address Translation) ŌĆō It allows many devices to share a single IP address. Example: Imagine an apartment building with only one main address (public IP). ŌĆóInside the building, each person has their own flat number (private IP). ŌĆóWhen someone outside (the internet) sends a letter, it goes to the buildingŌĆÖs main address, and the receptionist (NAT) sends it to the correct flat. How NAT Works in Networking: ŌĆóYour home WiFi router has one public IP address (the buildingŌĆÖs address). ŌĆóAll your devices (phone, laptop, smart TV) have private IPs (flat numbers). ŌĆóThe router (receptionist) manages who sent/received data and makes sure it reaches the right device. Problem with NAT: ŌĆóIt adds extra steps, making the internet slower. ŌĆóIt hides your real device, which is good for security but bad for some applications.
- 8. What is IPv6? (New Address System ŌĆō No More Sharing!) To fix this shortage, we created IPv6, which has trillions of addresses ŌĆō enough for every device to have its own unique address. ŌĆóLooks like this: 2001:db8::8a2e:0370:7334 (No need to memorize it). ŌĆóNo need for NAT! Every device gets its own home, so no more apartment sharing. Example: IPv6 is like building infinite houses, so everyone gets their own address without sharing.
- 9. What is a MAC Address? A MAC Address is a unique ID given to every network device (WiFi card, Ethernet card, etc.) by the manufacturer. It never changes, even if you switch networks. It looks like this: 00:1A:2B:3C:4D:5E (12-digit hexadecimal format). Every device has a different MAC address, just like every house has a unique name. Example:- ŌĆóYour Wi-Fi router has a MAC address. ŌĆóYour laptopŌĆÖs network card has a MAC address. ŌĆóYour mobile phoneŌĆÖs Wi-Fi has a MAC address. Even if your IP address changes, your MAC address stays the same!
- 10. What is ARP? ŌĆóARP (Address Resolution Protocol) is like a phonebook for networks. ŌĆóIt helps a device find the MAC address of another device using its IP address. Example:- ŌĆóYou want to visit House No. 192 (IP Address), but you donŌĆÖt know its House Name (MAC Address). ŌĆóYou ask the security guard (ARP), who tells you, ŌĆ£House No. 192 is called ŌĆśGreen VillaŌĆÖŌĆØ (MAC Address). Now, you can send a message to the correct house!
- 11. Types of Spoofing in Networking 1’ĖÅŌāŻ MAC Spoofing ŌĆō Changing Device ID (MAC Address) ŌĆóLike changing your homeŌĆÖs name to pretend to be another house. ŌĆóExample: A hacker changes their MAC address to look like your Wi-Fi router and steals your data. 2’ĖÅŌāŻ IP Spoofing ŌĆō Faking Internet Address (IP Address) ŌĆóLike writing a fake return address on a letter so no one knows where it really came from. ŌĆóExample: A hacker sends harmful data but hides their real IP address. 3’ĖÅŌāŻ ARP Spoofing ŌĆō Tricking Devices to Send Data to Hacker ŌĆóLike telling a delivery guy the wrong house address, so a package (data) goes to the wrong place. ŌĆóExample: A hacker pretends to be the Wi-Fi router, and your device unknowingly sends data to them.
- 12. SUMMARY:-
- 13. DNS (Domain Name System) ŌĆō The InternetŌĆÖs Phonebook Imagine you want to call a friend, but instead of remembering their 10-digit phone number, you just save their name in your contacts. When you tap their name, your phone automatically dials the correct number. DNS does the same for the internet! What is DNS? ŌĆóDNS stands for Domain Name System. ŌĆóIt converts website names (like youtube.com) into IP addresses (like 142.250.183.206). ŌĆóComputers donŌĆÖt understand namesŌĆöthey only communicate using IP addresses. Without DNS, we would have to type numbers instead of website names!
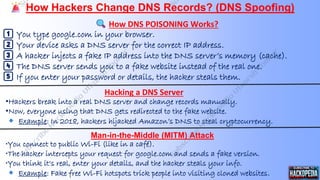
- 14. How DNS POISONING Works? 1’ĖÅŌāŻ You type google.com in your browser. 2’ĖÅŌāŻ Your device asks a DNS server for the correct IP address. 3’ĖÅŌāŻ A hacker injects a fake IP address into the DNS serverŌĆÖs memory (cache). 4’ĖÅŌāŻ The DNS server sends you to a fake website instead of the real one. 5’ĖÅŌāŻ If you enter your password or details, the hacker steals them. Hacking a DNS Server ŌĆóHackers break into a real DNS server and change records manually. ŌĆóNow, everyone using that DNS gets redirected to the fake website. Example: In 2018, hackers hijacked AmazonŌĆÖs DNS to steal cryptocurrency. Man-in-the-Middle (MITM) Attack ŌĆóYou connect to public Wi-Fi (like in a caf├®). ŌĆóThe hacker intercepts your request for google.com and sends a fake version. ŌĆóYou think it's real, enter your details, and the hacker steals your info. Example: Fake free Wi-Fi hotspots trick people into visiting cloned websites. How Hackers Change DNS Records? (DNS Spoofing)
- 15. HTTP vs HTTPS HTTP (Hyper-Text Transfer Protocol) ŌåÆ Not Secure HTTPS (Hyper-Text Transfer Protocol Secure) ŌåÆ Secure WHY HTTP IS NOT SECURE? 1’ĖÅŌāŻ You connect to public Wi-Fi (like in a caf├® or airport). 2’ĖÅŌāŻ You visit an http:// website (NOT encrypted). 3’ĖÅŌāŻ The hacker, also on the same Wi-Fi, runs a packet sniffer tool (like Wireshark). 4’ĖÅŌāŻ This tool listens to and captures all data sent over the network. 5’ĖÅŌāŻ Since HTTP sends data as plain text, the hacker sees everythingŌĆöyour usernames, passwords, credit card details, and messages. How to Stay Safe? Use HTTPS websites (https://, secure). Avoid public Wi-Fi for banking & logins. Use a VPN to encrypt your data.
- 16. What is TCP and UDP? Both TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are rules for sending data over the internet. They decide how information travels from one device to another. TCP (Reliable but Slow) ŌĆō Like a WhatsApp Message ŌĆóWhen you send a WhatsApp message , it checks if the message is delivered. ŌĆóIf the message doesnŌĆÖt reach, it resends it. ŌĆóMakes sure everything arrives in the correct order. ŌĆóUsed for: Websites, emails, file downloads (where accuracy matters). Example: Downloading a file ŌåÆ TCP makes sure every part of the file is received correctly. UDP (Fast but Unreliable) ŌĆō Like a Live Video Call ŌĆóWhen you do a video call , the data must be fast. ŌĆóIf some words or frames are lost, it doesnŌĆÖt resend them. ŌĆóSpeed is more important than accuracy. ŌĆóUsed for: Gaming, live streaming, video calls (where speed matters). Example: Playing PUBG ŌåÆ UDP ensures fast gameplay, even if some data is lost.