Nicholas Dorans - The Evolution of Passwords
- 1. The Evolution of Passwords By Nicholas Dorans
- 2. Brief Overview • Introduction • Brief history of passwords • Best practices for passwords • Current state and future of passwords
- 3. I am Nicholas Dorans • Originally from New Jersey • Software developer for last 5 years • Password user for roughly 25 years • Main passions are biking, traveling and tacos
- 4. A Brief History of Passwords • First used in 1961, at MIT for use with the Compatible Time- Sharing System by Fernando Corbató • In 1962, Ph.D. researcher Allan Scherr “hacked” that system by printing out all of the passwords in plain text • In the 1970’s, Robert Morris developed a one-way encryption function for his UNIX operating system known as “hashing” • Bill Gates declares that the password is dead in 2004
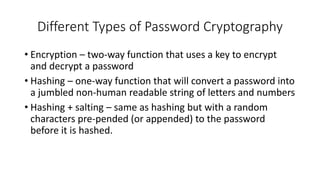
- 5. Different Types of Password Cryptography • Encryption – two-way function that uses a key to encrypt and decrypt a password • Hashing – one-way function that will convert a password into a jumbled non-human readable string of letters and numbers • Hashing + salting – same as hashing but with a random characters pre-pended (or appended) to the password before it is hashed.
- 6. Problems With Passwords • Short ones are easy to remember but easy to hack • Long ones are harder to crack but harder to remember • Average computer user has roughly 90 different online accounts each with their own username/password - this can be overwhelming and lead to poor password hygiene
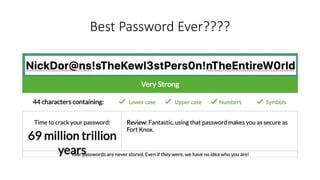
- 7. Best Practices for a User • Never use the same password for 2 or more accounts • Use strong passwords – combination of numbers, uppercase/lowercase letters, special characters with a minimum length of 8 (12 is better) • Use a password manager to help create strong unique passwords for each account
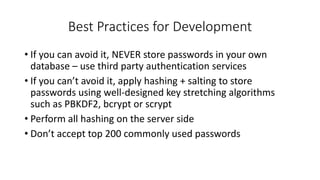
- 9. Best Practices for Development • If you can avoid it, NEVER store passwords in your own database – use third party authentication services • If you can’t avoid it, apply hashing + salting to store passwords using well-designed key stretching algorithms such as PBKDF2, bcrypt or scrypt • Perform all hashing on the server side • Don’t accept top 200 commonly used passwords
- 10. Current and Future State of Passwords • Biometric options are available on most new smart phones – fingerprint, face and iris scanning • Strong standards for password creation on most online services • 2 factor authentication using rsa tokens or a physical device such as Yubikey • Research is currently opening the way for new types of biometrics, such as ear shape or facial thermography.
- 11. FIN