One Shot Eight Bank
1 like331 views
This research analyzed a drop zone hosting stolen credit card data from attacks on eight Italian banks. The drop zone was a custom web application located on a server in Russia that functioned as a command and control center. It contained encrypted credit card and account information in a SQL database. The researchers discovered encryption/decryption keys and functions used by the attackers to decrypt and access the stolen data through the control panel interface. The attacks appeared to be ongoing, targeting new victims each week from the banks.
1 of 6
Download to read offline

![This%research%article%is%a%short%technical%publication%focused%on%technical%approach%used%from%attackers.%
Because'the'attack'campaign'is'¡°ALIVE¡±'I'will'not'revel'the'real'IP'addresses'and'the'real'name'of'the'targeted'bank.'
One$Shot$Eight$Bank$
Page%3%
During%the%static%JavaScript%code%analysis%we%found%the%code%to%encrypt%and%decrypt%¡°key¡±%used%by%hackers.%
This%two%functions%use%two%methods%declared%in%the%same%file%called%¡°encipher¡±%and%¡°decipher¡±%that%realize%
the%encryption/decryption%operation.%
%
%
1. playbovich["prototype"]["encrypt"] = function(collection) {
2.
3.collection = this["escape"](collection);
4. /** @type {number} */
5. var resp = 0;
6. for (;resp < collection["length"] % 16;resp++) {
7. collection += "0";
8. }
9. /** @type {string} */
10. var optsData = "";
11. /** @type {number} */
12. resp = 0;
13. for (;resp < collection["length"];resp += 16) {
14. this["xr_par"] = this["wordunescape"](collection["substr"](resp, 8));
15. this["xl_par"] = this["wordunescape"](collection["substr"](resp + 8, 8));
16. this["encipher"]();
17. optsData += this["wordescape"](this["xr_par"]) +
this["wordescape"](this["xl_par"]);
18. }
19. return optsData;
};! '
Figure'3:'Encryption'Code'
%
1. playbovich["prototype"]["decrypt"] = function(collection) {
2. collection = collection["toUpperCase"]();
3. /** @type {number} */
4. var resp = 0;
5. for (;resp < collection["length"] % 16;resp++) {
6. collection += "0";
7. }
8. /** @type {string} */
9. var later = "";
10. /** @type {number} */
11. resp = 0;
12. for (;resp < collection["length"];resp += 16) {
13. this["xr_par"] = this["wordunescape"](collection["substr"](resp, 8));
14. this["xl_par"] = this["wordunescape"](collection["substr"](resp + 8, 8));
15. this["decipher"]();
16. later += this["wordescape"](this["xr_par"]) +
this["wordescape"](this["xl_par"]);
17. }
18. return this["unescape"](later);
};!
%
Figure'4:'Decryption'Code'
%
%
%](https://image.slidesharecdn.com/oneshoteightbank-140724091725-phpapp02/85/One-Shot-Eight-Bank-3-320.jpg)

Ad
Recommended
IJSRED-V2I4P0
IJSRED-V2I4P0IJSRED
?
This document presents an intelligent system to detect phishing attacks using data mining techniques. It discusses how phishing involves mimicking legitimate websites to steal private information. Various existing solutions have been proposed but cannot fully eliminate phishing. The proposed system uses classifiers like decision trees and random forests trained on features extracted from URLs to classify websites as legitimate or phishing. It aims to construct an accurate intelligent system for phishing detection using data mining techniques.One shot eight banks
One shot eight banksDavide Cioccia
?
This research article discusses an ongoing cyberattack targeting eight Italian banks, utilizing a compromised web application for data theft through phishing. The attackers have implemented a command and control (C&C) center to manage the stolen data, which includes encrypted credit card information. The article emphasizes the importance of cybersecurity measures and suggests updates to antivirus systems as remediation strategies.GraphTalks Italy - Using graphs to fight financial fraud
GraphTalks Italy - Using graphs to fight financial fraudNeo4j
?
1. Traditional fraud detection methods like analyzing individual user accounts and transactions are ineffective at detecting modern fraud carried out by organized rings using synthetic identities and stolen data.
2. Graph databases allow connecting and analyzing related data across systems in real-time to detect complex fraudulent patterns like a ring of accounts linked by shared addresses, phone numbers, and social security numbers.
3. A demo shows how a financial services company can use Neo4j to augment their existing fraud detection by modeling operational data as a graph to identify potential fraud rings and generate alerts for an analyst to investigate in near real-time.GraphTalks Frankfurt - Leveraging Graph-Technology to fight financial fraud
GraphTalks Frankfurt - Leveraging Graph-Technology to fight financial fraudNeo4j
?
1. Traditional fraud detection methods like analyzing individual user accounts and transactions are ineffective at detecting modern fraud carried out by organized rings using synthetic identities and stolen data.
2. Graph databases allow connecting and analyzing related data across systems in real-time to detect complex fraudulent patterns like a ring of accounts linked by shared addresses, phone numbers, and social security numbers.
3. A demo of a fraud detection application built with Neo4j showed how it could generate alerts in real-time by linking operational data on users and transactions to identify potential fraud cases for further human or automated investigation.Do it-yourself-audits
Do it-yourself-auditsJohann-Peter Hartmann
?
The document discusses do-it-yourself security audits for PHP applications. It recommends focusing audits on high risk areas by analyzing data flows for STRIDE risks like spoofing, tampering, and information disclosure. The document outlines tools and techniques for analyzing things like SQL injections, code executions, input validation, and cross-site scripting vulnerabilities. It recommends using input flow analysis or checking critical functions and output escaping to efficiently audit applications. While tools can assist, thorough manual code reviews are still needed to identify security issues.Iy2515891593
Iy2515891593IJERA Editor
?
This document summarizes a research paper that proposes a machine learning approach for detecting phishing websites. It discusses using heuristic features from CANTINA to train machine learning models. A new domain top-page similarity feature is introduced to improve accuracy. Various modules are described, including site training, site capturing, a phishing dictionary, and image correlation to measure similarity. Experimental results show the approach achieves up to 92.5% f-measure and a 7.5% error rate for phishing detection.IRJET- Phishing Website Detection based on Machine Learning
IRJET- Phishing Website Detection based on Machine LearningIRJET Journal
?
This document proposes a machine learning model to detect phishing websites. It discusses how data mining algorithms can be used to classify websites as legitimate or phishing based on their characteristics. The proposed system aims to optimize detection by analyzing URL features, checking blacklists, and using a WHOIS database. It claims this method could decrease the error rate of existing detection systems by 30% and provide a more efficient way to identify phishing websites.State of the Art Analysis Approach for Identification of the Malignant URLs
State of the Art Analysis Approach for Identification of the Malignant URLsIOSRjournaljce
?
The document discusses a novel approach to identify and classify malicious URLs to enhance web security, as existing detection methods typically fail to address multiple attack types. It describes a system that employs data mining techniques, including an analyzer that uses lexical and host-based features alongside machine learning classifiers to effectively distinguish between benign and malicious URLs. The proposed solution incorporates various processes to gather suspicious URLs, which are then analyzed in real-time, aiming to block malicious content before it can reach users.Online financial fraud infographic
Online financial fraud infographicPrayukth K V
?
Cybercriminals prefer attacking bank customers directly rather than hacking banks. They do this through phishing emails with fake banking forms, spoofing of legitimate banking websites, and intercepting unprotected internet connections to steal users' financial credentials and data. Malware like Trojans also intercept keystrokes and screenshots to steal sensitive banking information from infected computers and mobile devices. Over 1.8 million users encountered financial malware in 2013, losing hundreds of millions of dollars to online financial fraud and theft.Symantec Internet Security Threat Report - 2009
Symantec Internet Security Threat Report - 2009guest6561cc
?
This document is Symantec's annual Global Internet Security Threat Report. It analyzes trends in threats, vulnerabilities, and other security issues from 2009. Some key findings include:
- Countries like the US, China, and India were major sources of malicious activity. Web-based attacks and phishing remained prevalent threats.
- Vulnerabilities in browsers and browser plugins posed risks. Exploits targeting vulnerabilities in Java, Adobe Reader, and other widely used programs were common.
- The number of new malicious code increased significantly in 2009. Trojans and botnets were widely used.
- Phishing targeted many industries, especially financial services. Automated phishing toolkits made phishingGeo-Inference Attacks via the Browser Cache
Geo-Inference Attacks via the Browser CacheThe Hacker News
?
This document describes geo-inference attacks that can infer a user's location by exploiting information leaked through the browser cache, without direct access to GPS or IP address data. The attacks work by measuring the timing differences when loading cached vs. non-cached location-sensitive resources from websites like Google, Craigslist, and Google Maps. The researchers found that all major browsers are vulnerable to these attacks. Over 62% of Alexa Top 100 websites contained location-sensitive resources that could be used to infer a user's country, city, or neighborhood with high accuracy. Existing defenses have limitations and the researchers propose server-aided cache control as a more practical solution.Compromised e commerce_sites_lead_to_web-based_keyloggers
Compromised e commerce_sites_lead_to_web-based_keyloggersAndrey Apuhtin
?
The document discusses a keylogger injection campaign targeting eCommerce sites called "Magecart". It describes how attackers injected JavaScript keylogger code into compromised shopping cart platforms like Magento to steal payment card data. The code captured form fields and sent data to remote attacker sites. The campaign evolved over time from 2016 onward, with attackers refining code and expanding which payment providers were targeted. The document provides examples of keylogger injections on specific compromised sites faber.co.uk and everlast.com.2014 Cybercrime Roundup: The Year of the POS Breach
2014 Cybercrime Roundup: The Year of the POS BreachEMC
?
The monthly fraud report highlights the significant rise in point-of-sale (POS) malware breaches in 2014, attributed mainly to attacks targeting retail chains, with notable malware like Chewbacca and Backoff leading these breaches. Mobile malware also surged alongside the increased use of mobile devices, particularly affecting Android users, and the underground marketplace for fraud has expanded with new payment systems and region-specific fraud schemes emerging, especially in Latin America. The report also notes a decrease in phishing attacks from November to December 2014, with significant financial losses reported from these incidents.The Ransomware Threat: Tracking the Digitial Footprints
The Ransomware Threat: Tracking the Digitial Footprintsk3vb0t
?
This document discusses tracking ransomware through digital footprints. It describes prominent ransomware variants like CryptoLocker, TorrentLocker, Alpha/TeslaCrypt and CryptoWall. It outlines how ransomware infects systems through phishing, compromised domains or malvertising. Ransomware uses geolocation calls and command and control exchanges. Services like Malwr.com and Virustotal.com can be used to identify related domains and track ransomware activity. Training systems to identify previously seen ransomware domains can help block future infections.§·§Ñ§Ü§Ö§â§í §ç§à§ä§ñ§ä §Ó§Ñ§ê §Ò§Ñ§ß§Ü §Ò§à§Ý§î§ê§Ö, §é§Ö§Þ §Ó§Ñ§ê§Ú§ç §Ü§Ý§Ú§Ö§ß§ä§à§Ó
§·§Ñ§Ü§Ö§â§í §ç§à§ä§ñ§ä §Ó§Ñ§ê §Ò§Ñ§ß§Ü §Ò§à§Ý§î§ê§Ö, §é§Ö§Þ §Ó§Ñ§ê§Ú§ç §Ü§Ý§Ú§Ö§ß§ä§à§ÓPositive Hack Days
?
The document discusses targeted attacks on financial institutions. It provides information on:
1) Known targeted attackers like Cobalt, Corkow, and Anunak and their favorite targets like ATMs, card processing, and SWIFT systems.
2) Future targeted attackers that may go after financial networks.
3) The common targets of these attacks, which include corporate internet banking software, payment gateways, ATMs, trade terminals, and SWIFT/ARM CBR systems.
4) The malware delivery methods used by these groups, such as driveby downloads, pay-per-install, web hacks, phishing emails, and spear phishing.Securing the Virtual Branch
Securing the Virtual BranchJay McLaughlin
?
The document discusses the increasing sophistication of cyber threats and the growing prevalence of fraud, such as account takeover and phishing attacks, highlighting that in 2013, there were reported losses of $5 billion due to fraud. It emphasizes the need for enhanced security measures, including biometric authentication and multi-layered protection strategies to combat evolving cyber threats. The overall message stresses the importance of understanding the risks associated with cybersecurity and adapting to the changing threat landscape.Cybercrime: A threat to Financial industry
Cybercrime: A threat to Financial industryAmmar WK
?
The document discusses the threats posed by cybercrime to the financial industry, categorizing different types of cyber crimes targeting individuals, property, organizations, and society. It highlights the significant costs associated with cybercrime in financial services and identifies prevalent threats like credit card fraud, social engineering, and malware. Additionally, it suggests controls and mitigations to protect against these threats, emphasizing the importance of continuous education and security measures in financial institutions.CrossTalk - The Art of Cyber Bank Robbery - Stealing your Money Through Insid...
CrossTalk - The Art of Cyber Bank Robbery - Stealing your Money Through Insid...Aditya K Sood
?
The document discusses the tactics employed by cyber criminals to conduct online banking fraud through advanced attacks, specifically focusing on botnets and malware. It outlines a cyber bank robbery model structured in four phases: malware design, distribution, data exfiltration, and fraud execution, highlighting the economic implications of such crimes and the challenges faced in defending against them. The analysis emphasizes the increasing sophistication of attacks on end-user systems, necessitating robust protective measures from both banks and users.Internet Security Threat Report (ISTR) Government
Internet Security Threat Report (ISTR) GovernmentSSLRenewals
?
The Internet Security Threat Report (ISTR) for June 2017 highlights evolving cyber threats, including targeted attacks related to espionage, ransomware, and vulnerabilities associated with the Internet of Things (IoT). It emphasizes the significant role of government actions and collaborations between private sectors in combating cybercrime, as exemplified by the influence of cyber activities during the 2016 U.S. presidential election and various destructive attacks on critical infrastructure. Overall, the report calls for enhanced security measures across sectors to mitigate emerging threats and protect national security.Fade from Whitehat... to Black
Fade from Whitehat... to BlackBeau Bullock
?
The document discusses the tactics and methodologies used in penetration testing, with a focus on maintaining operational security (opsec) and non-attribution. Key points include understanding vulnerabilities, target acquisition, and turning compromises into profit, while emphasizing the importance of anonymity and ethical considerations in cybersecurity practices. The author, Beau Bullock, highlights the need for defenders to shift from attribution to detection and prevention to enhance cybersecurity measures.The Rise and Rise of Web Fraud
The Rise and Rise of Web FraudDavid Jones
?
The document provides an overview of the evolution and increasing sophistication of web fraud, outlining the history of various fraud methods and the development of solutions by ThreatMetrix since its founding in 2005. It highlights the concept of 'fraud as a service' and the challenges posed by advanced fraud techniques that exploit anonymity and compromised identities. Additionally, it presents case studies demonstrating the effectiveness of ThreatMetrix's real-time fraud detection capabilities in preventing fraudulent activities.A WINDOW INTO RUSSIAN SPEAKING CYBERCRIME by Tim Bobak
A WINDOW INTO RUSSIAN SPEAKING CYBERCRIME by Tim BobakCODE BLUE
?
The document explores the landscape of Russian-speaking cybercrime, highlighting its collaborative nature, various criminal services, and the significant financial losses incurred through targeted attacks on banking systems and digital infrastructures. It discusses the motivations behind these crimes, the evolving tactics used by attackers, and the challenges in policing such activities. The text emphasizes the importance of cooperation and increased investment in anti-fraud measures to combat the growing threat of cybercrime.Website Security Threats - January 2014 Update
Website Security Threats - January 2014 Update Symantec Website Security
?
This document provides a summary of website security threats from January 2014. It discusses cybercrime statistics from the month including money earned by cybercriminals and numbers of stolen payment cards and user credentials. New types of malware like malicious Firefox add-ons and malware disguising as IIS servers are covered. Reasons for growing interest in IT risk like lack of visibility and interconnectedness are summarized. High profile hacks impacting millions of users are briefly outlined.Measurements in Cryptocurrency Networks
Measurements in Cryptocurrency NetworksBernhard Haslhofer
?
Dr. Bernhard Haslhofer presented on measurements and analytics techniques for cryptocurrency networks. He discussed network abstractions like transaction networks and address networks that can be used to cluster addresses and analyze cryptocurrency flows. As an example application, he described a ransomware study using the GraphSense analytics platform that identified the Locky ransomware family as generating the highest revenues, estimated at over $7 million USD, by tracing cryptocurrency transactions from seed ransomware addresses.7 mike-steenberg-carlos-lopera-us-bank
7 mike-steenberg-carlos-lopera-us-bankshreemala1
?
This document provides an overview of cyber security threats facing businesses in the 21st century. It discusses the scale of cyber crime, changing threats from insiders, hacktivists, organized crime and nation-states. It also covers common forms of malware, how malware infects systems and steals credentials, and tips for businesses to prevent account takeover and avoid being victims of cyber attacks.Is Troy Burning: an overview of targeted trojan attacks
Is Troy Burning: an overview of targeted trojan attacksMaarten Van Horenbeeck
?
This document summarizes a presentation on targeted trojan attacks and the related malware infrastructure. It describes how trojans are delivered through social engineering techniques, often using current events or topics of interest. Once installed, the malware establishes command and control channels using domain name parking and multiple control servers to evade detection. The attacks appear focused on intellectual property theft and espionage, especially targeting Japanese, Canadian and US government organizations.Cybercrime In The Deep Web
Cybercrime In The Deep WebTrend Micro
?
The document presents research conducted by Marco Balduzzi and Vincenzo Ciancaglini on cybercrime in the deep web, highlighting the use of Deep Web Analyzer (DEWA) for data collection, enrichment, and indexing. It discusses various features of the deep web, including its vastness and the infrastructure supporting illegal activities, such as marketplaces for cybercrime goods and malware distribution. The findings emphasize the capabilities of modern malware and its operational integration within the deep web ecosystem.Cybercrime in the Deep Web (BHEU 2015)
Cybercrime in the Deep Web (BHEU 2015)Marco Balduzzi
?
The document discusses cybercrime in the deep web, highlighting the vastness and complexity of this hidden part of the internet, which is much larger than the surface web. It introduces the Deep Web Analyzer (DEWA) used for data collection, enrichment, and analysis of illegal activities, including the trade of drugs, weapons, and personal information. The authors, experienced researchers in cybersecurity, emphasize the importance of their findings in identifying and combating cybercriminal activities.Famous C&C servers from inside to outside.
Famous C&C servers from inside to outside.Senad Aruc
?
The document discusses the inner workings of several cybercriminal operations and malware campaigns. It reveals details about the Cryptolocker ransomware command and control server infrastructure, including how it targeted victims and stored encrypted files. It also analyzes unique man-in-the-browser malware used to target online banking and a botnet that compromised QNAP network attached storage devices to potentially launch distributed denial of service attacks.Puzzle Lock
Puzzle LockSenad Aruc
?
Cloud Puzzle Lock is a new secure way to store and share files using cloud drives. It splits files into encrypted puzzle pieces that are distributed across multiple cloud drives. This makes the files much more secure against hacking or surveillance, as an attacker would need to compromise all of the cloud drives to reconstruct the file. The system aims to provide government agencies and companies with an easy yet highly secure method of accessing and sharing files remotely.More Related Content
Similar to One Shot Eight Bank (20)
Online financial fraud infographic
Online financial fraud infographicPrayukth K V
?
Cybercriminals prefer attacking bank customers directly rather than hacking banks. They do this through phishing emails with fake banking forms, spoofing of legitimate banking websites, and intercepting unprotected internet connections to steal users' financial credentials and data. Malware like Trojans also intercept keystrokes and screenshots to steal sensitive banking information from infected computers and mobile devices. Over 1.8 million users encountered financial malware in 2013, losing hundreds of millions of dollars to online financial fraud and theft.Symantec Internet Security Threat Report - 2009
Symantec Internet Security Threat Report - 2009guest6561cc
?
This document is Symantec's annual Global Internet Security Threat Report. It analyzes trends in threats, vulnerabilities, and other security issues from 2009. Some key findings include:
- Countries like the US, China, and India were major sources of malicious activity. Web-based attacks and phishing remained prevalent threats.
- Vulnerabilities in browsers and browser plugins posed risks. Exploits targeting vulnerabilities in Java, Adobe Reader, and other widely used programs were common.
- The number of new malicious code increased significantly in 2009. Trojans and botnets were widely used.
- Phishing targeted many industries, especially financial services. Automated phishing toolkits made phishingGeo-Inference Attacks via the Browser Cache
Geo-Inference Attacks via the Browser CacheThe Hacker News
?
This document describes geo-inference attacks that can infer a user's location by exploiting information leaked through the browser cache, without direct access to GPS or IP address data. The attacks work by measuring the timing differences when loading cached vs. non-cached location-sensitive resources from websites like Google, Craigslist, and Google Maps. The researchers found that all major browsers are vulnerable to these attacks. Over 62% of Alexa Top 100 websites contained location-sensitive resources that could be used to infer a user's country, city, or neighborhood with high accuracy. Existing defenses have limitations and the researchers propose server-aided cache control as a more practical solution.Compromised e commerce_sites_lead_to_web-based_keyloggers
Compromised e commerce_sites_lead_to_web-based_keyloggersAndrey Apuhtin
?
The document discusses a keylogger injection campaign targeting eCommerce sites called "Magecart". It describes how attackers injected JavaScript keylogger code into compromised shopping cart platforms like Magento to steal payment card data. The code captured form fields and sent data to remote attacker sites. The campaign evolved over time from 2016 onward, with attackers refining code and expanding which payment providers were targeted. The document provides examples of keylogger injections on specific compromised sites faber.co.uk and everlast.com.2014 Cybercrime Roundup: The Year of the POS Breach
2014 Cybercrime Roundup: The Year of the POS BreachEMC
?
The monthly fraud report highlights the significant rise in point-of-sale (POS) malware breaches in 2014, attributed mainly to attacks targeting retail chains, with notable malware like Chewbacca and Backoff leading these breaches. Mobile malware also surged alongside the increased use of mobile devices, particularly affecting Android users, and the underground marketplace for fraud has expanded with new payment systems and region-specific fraud schemes emerging, especially in Latin America. The report also notes a decrease in phishing attacks from November to December 2014, with significant financial losses reported from these incidents.The Ransomware Threat: Tracking the Digitial Footprints
The Ransomware Threat: Tracking the Digitial Footprintsk3vb0t
?
This document discusses tracking ransomware through digital footprints. It describes prominent ransomware variants like CryptoLocker, TorrentLocker, Alpha/TeslaCrypt and CryptoWall. It outlines how ransomware infects systems through phishing, compromised domains or malvertising. Ransomware uses geolocation calls and command and control exchanges. Services like Malwr.com and Virustotal.com can be used to identify related domains and track ransomware activity. Training systems to identify previously seen ransomware domains can help block future infections.§·§Ñ§Ü§Ö§â§í §ç§à§ä§ñ§ä §Ó§Ñ§ê §Ò§Ñ§ß§Ü §Ò§à§Ý§î§ê§Ö, §é§Ö§Þ §Ó§Ñ§ê§Ú§ç §Ü§Ý§Ú§Ö§ß§ä§à§Ó
§·§Ñ§Ü§Ö§â§í §ç§à§ä§ñ§ä §Ó§Ñ§ê §Ò§Ñ§ß§Ü §Ò§à§Ý§î§ê§Ö, §é§Ö§Þ §Ó§Ñ§ê§Ú§ç §Ü§Ý§Ú§Ö§ß§ä§à§ÓPositive Hack Days
?
The document discusses targeted attacks on financial institutions. It provides information on:
1) Known targeted attackers like Cobalt, Corkow, and Anunak and their favorite targets like ATMs, card processing, and SWIFT systems.
2) Future targeted attackers that may go after financial networks.
3) The common targets of these attacks, which include corporate internet banking software, payment gateways, ATMs, trade terminals, and SWIFT/ARM CBR systems.
4) The malware delivery methods used by these groups, such as driveby downloads, pay-per-install, web hacks, phishing emails, and spear phishing.Securing the Virtual Branch
Securing the Virtual BranchJay McLaughlin
?
The document discusses the increasing sophistication of cyber threats and the growing prevalence of fraud, such as account takeover and phishing attacks, highlighting that in 2013, there were reported losses of $5 billion due to fraud. It emphasizes the need for enhanced security measures, including biometric authentication and multi-layered protection strategies to combat evolving cyber threats. The overall message stresses the importance of understanding the risks associated with cybersecurity and adapting to the changing threat landscape.Cybercrime: A threat to Financial industry
Cybercrime: A threat to Financial industryAmmar WK
?
The document discusses the threats posed by cybercrime to the financial industry, categorizing different types of cyber crimes targeting individuals, property, organizations, and society. It highlights the significant costs associated with cybercrime in financial services and identifies prevalent threats like credit card fraud, social engineering, and malware. Additionally, it suggests controls and mitigations to protect against these threats, emphasizing the importance of continuous education and security measures in financial institutions.CrossTalk - The Art of Cyber Bank Robbery - Stealing your Money Through Insid...
CrossTalk - The Art of Cyber Bank Robbery - Stealing your Money Through Insid...Aditya K Sood
?
The document discusses the tactics employed by cyber criminals to conduct online banking fraud through advanced attacks, specifically focusing on botnets and malware. It outlines a cyber bank robbery model structured in four phases: malware design, distribution, data exfiltration, and fraud execution, highlighting the economic implications of such crimes and the challenges faced in defending against them. The analysis emphasizes the increasing sophistication of attacks on end-user systems, necessitating robust protective measures from both banks and users.Internet Security Threat Report (ISTR) Government
Internet Security Threat Report (ISTR) GovernmentSSLRenewals
?
The Internet Security Threat Report (ISTR) for June 2017 highlights evolving cyber threats, including targeted attacks related to espionage, ransomware, and vulnerabilities associated with the Internet of Things (IoT). It emphasizes the significant role of government actions and collaborations between private sectors in combating cybercrime, as exemplified by the influence of cyber activities during the 2016 U.S. presidential election and various destructive attacks on critical infrastructure. Overall, the report calls for enhanced security measures across sectors to mitigate emerging threats and protect national security.Fade from Whitehat... to Black
Fade from Whitehat... to BlackBeau Bullock
?
The document discusses the tactics and methodologies used in penetration testing, with a focus on maintaining operational security (opsec) and non-attribution. Key points include understanding vulnerabilities, target acquisition, and turning compromises into profit, while emphasizing the importance of anonymity and ethical considerations in cybersecurity practices. The author, Beau Bullock, highlights the need for defenders to shift from attribution to detection and prevention to enhance cybersecurity measures.The Rise and Rise of Web Fraud
The Rise and Rise of Web FraudDavid Jones
?
The document provides an overview of the evolution and increasing sophistication of web fraud, outlining the history of various fraud methods and the development of solutions by ThreatMetrix since its founding in 2005. It highlights the concept of 'fraud as a service' and the challenges posed by advanced fraud techniques that exploit anonymity and compromised identities. Additionally, it presents case studies demonstrating the effectiveness of ThreatMetrix's real-time fraud detection capabilities in preventing fraudulent activities.A WINDOW INTO RUSSIAN SPEAKING CYBERCRIME by Tim Bobak
A WINDOW INTO RUSSIAN SPEAKING CYBERCRIME by Tim BobakCODE BLUE
?
The document explores the landscape of Russian-speaking cybercrime, highlighting its collaborative nature, various criminal services, and the significant financial losses incurred through targeted attacks on banking systems and digital infrastructures. It discusses the motivations behind these crimes, the evolving tactics used by attackers, and the challenges in policing such activities. The text emphasizes the importance of cooperation and increased investment in anti-fraud measures to combat the growing threat of cybercrime.Website Security Threats - January 2014 Update
Website Security Threats - January 2014 Update Symantec Website Security
?
This document provides a summary of website security threats from January 2014. It discusses cybercrime statistics from the month including money earned by cybercriminals and numbers of stolen payment cards and user credentials. New types of malware like malicious Firefox add-ons and malware disguising as IIS servers are covered. Reasons for growing interest in IT risk like lack of visibility and interconnectedness are summarized. High profile hacks impacting millions of users are briefly outlined.Measurements in Cryptocurrency Networks
Measurements in Cryptocurrency NetworksBernhard Haslhofer
?
Dr. Bernhard Haslhofer presented on measurements and analytics techniques for cryptocurrency networks. He discussed network abstractions like transaction networks and address networks that can be used to cluster addresses and analyze cryptocurrency flows. As an example application, he described a ransomware study using the GraphSense analytics platform that identified the Locky ransomware family as generating the highest revenues, estimated at over $7 million USD, by tracing cryptocurrency transactions from seed ransomware addresses.7 mike-steenberg-carlos-lopera-us-bank
7 mike-steenberg-carlos-lopera-us-bankshreemala1
?
This document provides an overview of cyber security threats facing businesses in the 21st century. It discusses the scale of cyber crime, changing threats from insiders, hacktivists, organized crime and nation-states. It also covers common forms of malware, how malware infects systems and steals credentials, and tips for businesses to prevent account takeover and avoid being victims of cyber attacks.Is Troy Burning: an overview of targeted trojan attacks
Is Troy Burning: an overview of targeted trojan attacksMaarten Van Horenbeeck
?
This document summarizes a presentation on targeted trojan attacks and the related malware infrastructure. It describes how trojans are delivered through social engineering techniques, often using current events or topics of interest. Once installed, the malware establishes command and control channels using domain name parking and multiple control servers to evade detection. The attacks appear focused on intellectual property theft and espionage, especially targeting Japanese, Canadian and US government organizations.Cybercrime In The Deep Web
Cybercrime In The Deep WebTrend Micro
?
The document presents research conducted by Marco Balduzzi and Vincenzo Ciancaglini on cybercrime in the deep web, highlighting the use of Deep Web Analyzer (DEWA) for data collection, enrichment, and indexing. It discusses various features of the deep web, including its vastness and the infrastructure supporting illegal activities, such as marketplaces for cybercrime goods and malware distribution. The findings emphasize the capabilities of modern malware and its operational integration within the deep web ecosystem.Cybercrime in the Deep Web (BHEU 2015)
Cybercrime in the Deep Web (BHEU 2015)Marco Balduzzi
?
The document discusses cybercrime in the deep web, highlighting the vastness and complexity of this hidden part of the internet, which is much larger than the surface web. It introduces the Deep Web Analyzer (DEWA) used for data collection, enrichment, and analysis of illegal activities, including the trade of drugs, weapons, and personal information. The authors, experienced researchers in cybersecurity, emphasize the importance of their findings in identifying and combating cybercriminal activities.§·§Ñ§Ü§Ö§â§í §ç§à§ä§ñ§ä §Ó§Ñ§ê §Ò§Ñ§ß§Ü §Ò§à§Ý§î§ê§Ö, §é§Ö§Þ §Ó§Ñ§ê§Ú§ç §Ü§Ý§Ú§Ö§ß§ä§à§Ó
§·§Ñ§Ü§Ö§â§í §ç§à§ä§ñ§ä §Ó§Ñ§ê §Ò§Ñ§ß§Ü §Ò§à§Ý§î§ê§Ö, §é§Ö§Þ §Ó§Ñ§ê§Ú§ç §Ü§Ý§Ú§Ö§ß§ä§à§ÓPositive Hack Days
?
More from Senad Aruc (7)
Famous C&C servers from inside to outside.
Famous C&C servers from inside to outside.Senad Aruc
?
The document discusses the inner workings of several cybercriminal operations and malware campaigns. It reveals details about the Cryptolocker ransomware command and control server infrastructure, including how it targeted victims and stored encrypted files. It also analyzes unique man-in-the-browser malware used to target online banking and a botnet that compromised QNAP network attached storage devices to potentially launch distributed denial of service attacks.Puzzle Lock
Puzzle LockSenad Aruc
?
Cloud Puzzle Lock is a new secure way to store and share files using cloud drives. It splits files into encrypted puzzle pieces that are distributed across multiple cloud drives. This makes the files much more secure against hacking or surveillance, as an attacker would need to compromise all of the cloud drives to reconstruct the file. The system aims to provide government agencies and companies with an easy yet highly secure method of accessing and sharing files remotely.Revealing Unique MitB Builder C&C Server
Revealing Unique MitB Builder C&C ServerSenad Aruc
?
The document analyzes a unique 'man-in-the-browser' (MitB) malware known as 'kins' that utilizes a distinctive builder to create targeted attacks against financial institutions. It details the structure and functionalities of the malware, including Command and Control (C&C) server operations, customizable injections, and the ability to bypass two-factor authentication. The findings emphasize the increasing sophistication of such malware, highlighting risks and vulnerabilities in online banking security.Target List of Hesper-BOT Malware
Target List of Hesper-BOT MalwareSenad Aruc
?
This document summarizes technical analysis of the Hesper/BOT malware targeting Russian and other European banks. It identifies common command and control domains and IP addresses the malware communicates with, and lists over 200 bank names that are targeted by the malware in its attempts to steal login credentials. Technical details provided include ASN and geo-location information for IP addresses and domains used in the attacks.State of ART Phishing Attack stealing 50K Credit Cards Revealed
State of ART Phishing Attack stealing 50K Credit Cards RevealedSenad Aruc
?
This document summarizes a sophisticated phishing attack that stole credit card information from 50,000 victims. The attackers created a fake website mimicking a legitimate site to steal login credentials and payment details. They used multiple compromised servers and domains to host the fake site, send phishing emails, and store the stolen data to evade detection. The security researcher analyzed server logs and source code to map out the full attack infrastructure, including the drop zone where over 50,000 stolen credit cards were ultimately collected and stored by the attackers.Infostealer Botnet Reveal
Infostealer Botnet RevealSenad Aruc
?
This document summarizes the analysis of a botnet command and control server located in the UK that was targeting Italian banks and customers. The botnet contained over 5GB of hacked and encrypted personal data. The malware used keylogging and screenshot capturing to steal login credentials when users accessed banking websites. The command and control server allowed controlling infected machines, uploading new malware files, and searching/viewing the stolen login credentials and personal data of victims.Kins origin malware with unique ATSEngine.
Kins origin malware with unique ATSEngine.Senad Aruc
?
This research article discusses an ongoing attack campaign utilizing Kins origin malware targeting an international bank, which employs a mechanism for dynamic code injection in victims' browsers. The malware's command and control server is located in Russia, controlling the infected machines and facilitating automated money transfers from victims' accounts. The publication reveals technical details of the malware, including its capabilities, statistics on infected users, and insights into the operation of its command and control functionalities.Ad
Recently uploaded (20)
Logging and Automated Alerting Webinar.pdf
Logging and Automated Alerting Webinar.pdfControlCase
?
Join us for an exclusive webinar on Logging and Automated Alerting ¡ª your key to simplifying compliance and strengthening security.
Discover how ControlCase helps organizations move beyond the checklist to achieve real-time monitoring, centralized log management, and faster incident response with minimal internal effort.
? Gain insights into:
? Emerging risks and compliance requirements
? How automated alerting reduces downtime
? The architecture behind our proactive LAAS solution
? Real-world results that boost productivity and performance
? Hosted by our cybersecurity experts Chad Leedy and Elswick Lai.
Secure your spot today and learn how to turn compliance into a competitive advantage.
? [Insert Registration Link]
#Cybersecurity #Compliance #Logging #Alerting #ControlCase #CaaS #ITSecurity #WebinarBitRecover OST to PST Converter Software
BitRecover OST to PST Converter Softwareantoniogosling01
?
BitRecover OST to PST Converter is a powerful tool designed to convert inaccessible or orphaned OST files into Outlook PST format. It ensures complete data recovery including emails, contacts, calendars, and attachments. The software supports both ANSI and Unicode OST files and works with all Outlook versions. With a user-friendly interface and advanced filtering options, it's ideal for professionals needing quick and accurate OST to PST conversion.
https://www.bitrecover.com/ost-to-pst/Transmission Control Protocol (TCP) and Starlink
Transmission Control Protocol (TCP) and StarlinkAPNIC
?
Geoff Huston, APNIC Chief Scientist, delivered a remote presentation on 'TCP and Starlink' at INNOG 8 held in conjunction with the 2nd India ISP Conclave held in Delhi, India from 23 to 28 May 2025.Clive Dickens RedTech Public Copy - Collaborate or Die
Clive Dickens RedTech Public Copy - Collaborate or DieClive Dickens
?
'Collaborate or Die' and 'Simplify Audio Currency Now'.
Clive Dickens Managing Partner from The Meliora Company presentation from RedTech 2025 in Milan 2025 to 50 C-Suites executives from the International Media Industry, highlighting the urgent of deeper collaboration across territories and simplication of measurement and currency of Audio.Make DDoS expensive for the threat actors
Make DDoS expensive for the threat actorsAPNIC
?
Awal Haolader, Network Analyst / Technical Trainer at APNIC, delivered a presentation titled 'Make DDoS expensive for the threat actors' at Phoenix Summit 2025 held in Dhaka, Bangladesh from 19 to 24 May 2025.inside the internet - understanding the TCP/IP protocol
inside the internet - understanding the TCP/IP protocolshainweniton02
?
Key factors on TCP/IP protocolGlobal Networking Trends, presented at the India ISP Conclave 2025
Global Networking Trends, presented at the India ISP Conclave 2025APNIC
?
Jia Rong Low, APNIC Director General, presented on 'Global Networking Trends' at INNOG 8 held jointly with the India ISP Conclave 2025 held in Delhi, India from 23 to 28 May 2025. ºÝºÝߣs: Eco Economic Epochs for The World Game (s) pdf
ºÝºÝߣs: Eco Economic Epochs for The World Game (s) pdfSteven McGee
?
The REAL QFS - DeFi Quantum Financial System structured data AI symbols exchange derived from Net Centric Warfare, Battlefield Digitization for the World Game (s) Great Reset - Redesign: "End state = "in the beginning state" "Start at end state & work backwards" FutureMan
#quantum #financial #system #QFS #patent #Cryptocurrency #Tariff #TradeFi #commodity #wars #patent #law #AI artificial Intelligence Github: https://github.com/Beacon-Heart×îаæÃÀ¹úÌØÀ»ª´óѧ±ÏÒµÖ¤£¨±«¶Ù±ð±ô±ÏÒµÖ¤Ê飩԰涨ÖÆ
×îаæÃÀ¹úÌØÀ»ª´óѧ±ÏÒµÖ¤£¨±«¶Ù±ð±ô±ÏÒµÖ¤Ê飩԰涨ÖÆtaqyea
?
2025Ô°æÌØÀ»ª´óѧ±ÏÒµÖ¤Êépdfµç×Ӱ桾qÞ±1954292140¡¿ÃÀ¹ú±ÏÒµÖ¤°ìÀíUDelÌØÀ»ª´óѧ±ÏÒµÖ¤Êé¶àÉÙÇ®£¿¡¾qÞ±1954292140¡¿º£Íâ¸÷´óѧDiploma°æ±¾£¬ÒòΪÒßÇéѧУÍƳٷ¢·ÅÖ¤Êé¡¢Ö¤ÊéÔ¼þ¶ªÊ§²¹°ì¡¢Ã»ÓÐÕý³£±ÏҵδÄÜÈÏ֤ѧÀúÃæÁÙ¾ÍÒµÌṩ½â¾ö°ì·¨¡£µ±ÔâÓö¹Ò¿Æ¡¢¿õ¿Îµ¼ÖÂÎÞ·¨ÐÞÂúѧ·Ö£¬»òÕßÖ±½Ó±»Ñ§Ð£ÍËѧ£¬×îºóÎÞ·¨±ÏÒµÄò»µ½±ÏÒµÖ¤¡£´ËʱµÄÄãÒ»¶¨ÊÖ×ãÎ޴룬ÒòΪÁôѧһ³¡£¬Ã»ÓлñµÃ±ÏÒµÖ¤ÒÔ¼°Ñ§ÀúÖ¤Ã÷¿Ï¶¨ÊÇÎÞ·¨¸ø×Ô¼ººÍ¸¸Ä¸Ò»¸ö½»´úµÄ¡£
¡¾¸´¿ÌÌØÀ»ª´óѧ³É¼¨µ¥ÐÅ·â,Buy University of Delaware Transcripts¡¿
¹ºÂòÈÕº«³É¼¨µ¥¡¢Ó¢¹ú´óѧ³É¼¨µ¥¡¢ÃÀ¹ú´óѧ³É¼¨µ¥¡¢°ÄÖÞ´óѧ³É¼¨µ¥¡¢¼ÓÄôó´óѧ³É¼¨µ¥£¨q΢1954292140£©Ð¼ÓÆ´óѧ³É¼¨µ¥¡¢ÐÂÎ÷À¼´óѧ³É¼¨µ¥¡¢°®¶ûÀ¼³É¼¨µ¥¡¢Î÷°àÑÀ³É¼¨µ¥¡¢µÂ¹ú³É¼¨µ¥¡£³É¼¨µ¥µÄÒâÒåÖ÷ÒªÌåÏÖÔÚÖ¤Ã÷ѧϰÄÜÁ¦¡¢ÆÀ¹ÀѧÊõ±³¾°¡¢Õ¹Ê¾×ÛºÏËØÖÊ¡¢Ìá¸ß¼ȡÂÊ£¬ÒÔ¼°ÊÇ×÷ΪÁôÐÅÈÏÖ¤ÉêÇë²ÄÁϵÄÒ»²¿·Ö¡£
ÌØÀ»ª´óѧ³É¼¨µ¥Äܹ»ÌåÏÖÄúµÄµÄѧϰÄÜÁ¦£¬°üÀ¨ÌØÀ»ª´óѧ¿Î³Ì³É¼¨¡¢×¨ÒµÄÜÁ¦¡¢Ñо¿ÄÜÁ¦¡££¨q΢1954292140£©¾ßÌåÀ´Ëµ£¬³É¼¨±¨¸æµ¥Í¨³£°üº¬Ñ§ÉúµÄѧϰ¼¼ÄÜÓëÏ°¹ß¡¢¸÷¿Æ³É¼¨ÒÔ¼°ÀÏʦÆÀÓïµÈ²¿·Ö£¬Òò´Ë£¬³É¼¨µ¥²»½öÊÇѧÉúѧÊõÄÜÁ¦µÄÖ¤Ã÷£¬Ò²ÊÇÆÀ¹ÀѧÉúÊÇ·ñÊʺÏij¸ö½ÌÓýÏîÄ¿µÄÖØÒªÒÀ¾Ý£¡
ÎÒÃdzÐŵ²ÉÓõÄÊÇѧУ԰æÖ½ÕÅ£¨Ô°æÖ½ÖÊ¡¢µ×É«¡¢ÎÆ·£©ÎÒÃǹ¤³§ÓµÓÐÈ«Ì×½ø¿ÚÔ×°É豸£¬ÌØÊ⹤ÒÕ¶¼ÊDzÉÓò»Í¬»úÆ÷ÖÆ×÷£¬·ÂÕæ¶È»ù±¾¿ÉÒÔ´ïµ½100%£¬ËùÓгÉÆ·ÒÔ¼°¹¤ÒÕЧ¹û¶¼¿ÉÌáÇ°¸ø¿Í»§Õ¹Ê¾£¬²»ÂúÒâ¿ÉÒÔ¸ù¾Ý¿Í»§ÒªÇó½øÐе÷Õû£¬Ö±µ½ÂúÒâΪֹ£¡
¡¾Ö÷ÓªÏîÄ¿¡¿
Ò»¡¢¹¤×÷δȷ¶¨£¬»Ø¹úÐèÏȸø¸¸Ä¸¡¢Ç×ÆÝÅóÓÑ¿´ÏÂÎÄƾµÄÇé¿ö£¬°ìÀí±ÏÒµÖ¤|°ìÀíÎÄƾ: Âò´óѧ±ÏÒµÖ¤|Âò´óѧÎÄƾ¡¾qÞ±1954292140¡¿ÌØÀ»ª´óѧѧλ֤Ã÷ÊéÈçºÎ°ìÀíÉêÇ룿
¶þ¡¢»Ø¹ú½ø˽Æó¡¢ÍâÆó¡¢×Ô¼º×öÉúÒâµÄÇé¿ö£¬ÕâЩµ¥Î»ÊDz»²éѯ±ÏÒµÖ¤ÕæαµÄ£¬¶øÇÒ¹úÄÚûÓÐÇþµÀÈ¥²éѯ¹úÍâÎÄƾµÄÕæ¼Ù£¬Ò²²»ÐèÒªÌṩÕæʵ½ÌÓý²¿ÈÏÖ¤¡£¼øÓÚ´Ë£¬°ìÀíÃÀ¹ú³É¼¨µ¥ÌØÀ»ª´óѧ±ÏÒµÖ¤¡¾qÞ±1954292140¡¿¹úÍâ´óѧ±ÏÒµÖ¤, ÎÄƾ°ìÀí, ¹úÍâÎÄƾ°ìÀí, ÁôÐÅÍøÈÏÖ¤Paper: The World Game (s) Great Redesign.pdf
Paper: The World Game (s) Great Redesign.pdfSteven McGee
?
Paper: The REAL QFS - DeFi Quantum Financial System structured data AI symbols exchange derived from Net Centric Warfare, Battlefield Digitization for the World Game (s) Great Reset - Redesign: "End state = "in the beginning state" "Start at end state & work backwards" FutureManAd
One Shot Eight Bank
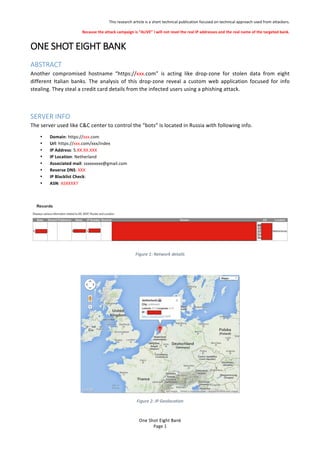
- 1. This%research%article%is%a%short%technical%publication%focused%on%technical%approach%used%from%attackers.% Because'the'attack'campaign'is'¡°ALIVE¡±'I'will'not'revel'the'real'IP'addresses'and'the'real'name'of'the'targeted'bank.' One$Shot$Eight$Bank$ Page%1% ONE$SHOT$EIGHT$BANK!$ ABSTRACT$ Another% compromised% hostname% ¡°https://xxx.com¡±% is% acting% like% drop?zone% for% stolen% data% from% eight% different% Italian% banks.% The% analysis% of% this% drop?zone% reveal% a% custom% web% application% focused% for% info% stealing.%They%steal%a%credit%card%details%from%the%infected%users%using%a%phishing%attack.%% % SERVER$INFO$ The%server%used%like%C&C%center%to%control%the%¡°bots¡±%is%located%in%Russia%with%following%info.% ? Domain:%https://xxx.com% ? Url:%https://xxx.com/xxx/index% ? IP%Address:%5.XX.XX.XXX% ? IP'Location:%Netherland% ? Associated'mail:%sxxxxxxxx@gmail.com% ? Reverse'DNS:%XXX% ? IP'Blacklist'Check:%% ? ASN:%ASXXXX7% % % Figure'1:'Network'details' % % Figure'2:'IP'Geolocation'
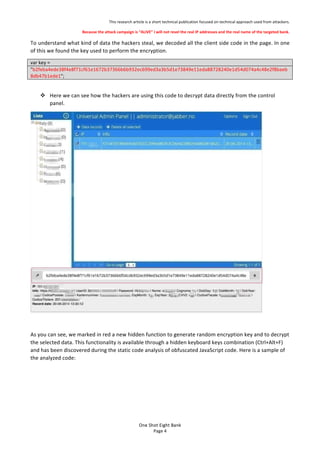
- 3. This%research%article%is%a%short%technical%publication%focused%on%technical%approach%used%from%attackers.% Because'the'attack'campaign'is'¡°ALIVE¡±'I'will'not'revel'the'real'IP'addresses'and'the'real'name'of'the'targeted'bank.' One$Shot$Eight$Bank$ Page%3% During%the%static%JavaScript%code%analysis%we%found%the%code%to%encrypt%and%decrypt%¡°key¡±%used%by%hackers.% This%two%functions%use%two%methods%declared%in%the%same%file%called%¡°encipher¡±%and%¡°decipher¡±%that%realize% the%encryption/decryption%operation.% % % 1. playbovich["prototype"]["encrypt"] = function(collection) { 2. 3.collection = this["escape"](collection); 4. /** @type {number} */ 5. var resp = 0; 6. for (;resp < collection["length"] % 16;resp++) { 7. collection += "0"; 8. } 9. /** @type {string} */ 10. var optsData = ""; 11. /** @type {number} */ 12. resp = 0; 13. for (;resp < collection["length"];resp += 16) { 14. this["xr_par"] = this["wordunescape"](collection["substr"](resp, 8)); 15. this["xl_par"] = this["wordunescape"](collection["substr"](resp + 8, 8)); 16. this["encipher"](); 17. optsData += this["wordescape"](this["xr_par"]) + this["wordescape"](this["xl_par"]); 18. } 19. return optsData; };! ' Figure'3:'Encryption'Code' % 1. playbovich["prototype"]["decrypt"] = function(collection) { 2. collection = collection["toUpperCase"](); 3. /** @type {number} */ 4. var resp = 0; 5. for (;resp < collection["length"] % 16;resp++) { 6. collection += "0"; 7. } 8. /** @type {string} */ 9. var later = ""; 10. /** @type {number} */ 11. resp = 0; 12. for (;resp < collection["length"];resp += 16) { 13. this["xr_par"] = this["wordunescape"](collection["substr"](resp, 8)); 14. this["xl_par"] = this["wordunescape"](collection["substr"](resp + 8, 8)); 15. this["decipher"](); 16. later += this["wordescape"](this["xr_par"]) + this["wordescape"](this["xl_par"]); 17. } 18. return this["unescape"](later); };! % Figure'4:'Decryption'Code' % % %
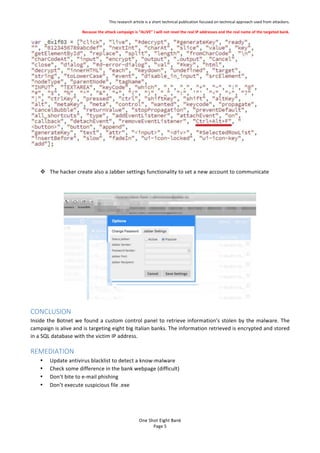
- 5. This%research%article%is%a%short%technical%publication%focused%on%technical%approach%used%from%attackers.% Because'the'attack'campaign'is'¡°ALIVE¡±'I'will'not'revel'the'real'IP'addresses'and'the'real'name'of'the'targeted'bank.' One$Shot$Eight$Bank$ Page%5% % % ! The%hacker%create%also%a%Jabber%settings%functionality%to%set%a%new%account%to%communicate%% % % CONCLUSION$ Inside%the%Botnet%we%found%a%custom%control%panel%to%retrieve%information¡¯s%stolen%by%the%malware.%The% campaign%is%alive%and%is%targeting%eight%big%Italian%banks.%The%information%retrieved%is%encrypted%and%stored% in%a%SQL%database%with%the%victim%IP%address.% REMEDIATION$ ? Update%antivirus%blacklist%to%detect%a%know?malware% ? Check%some%difference%in%the%bank%webpage%(difficult)% ? Don¡¯t%bite%to%e?mail%phishing% ? Don¡¯t%execute%suspicious%file%.exe%
- 6. This%research%article%is%a%short%technical%publication%focused%on%technical%approach%used%from%attackers.% Because'the'attack'campaign'is'¡°ALIVE¡±'I'will'not'revel'the'real'IP'addresses'and'the'real'name'of'the'targeted'bank.' One$Shot$Eight$Bank$ Page%6% STATISTICS$ The%attack%is%alive%and%the%amount%of%the%hacked%users%is%increasing%every%week,%the%amount%of%the%hacked% users%is%3?5%per%week%especially%on%some%banks.%Sometimes%attackers%are%removing%the%data%to%hide%the% impact.% % ABOUT$the$RESEARCHERS$ % Senad%Aruch.% Multiple% Certified% ISMS% Professional% with% 10?year% background% in:% IT% Security,% IDS% and% IPS,% SIEM,% SOC,% Network% Forensics,% Malware% Analyses,% ISMS% and% RISK,% Ethical% Hacking,% Vulnerability% Management,% Anti% Fraud% and% Cyber% Security.% Currently% holding% a% Senior% Security% Specialist% position% at% Reply% s.p.a% ?% Communication% Valley% ?% Security% Operations%Center.%Responsible%for%advanced%security%operations.%%% E?Mail:%senad.aruc@gmail.com% Blog:%www.senadaruc.com% Twitter:%https://twitter.com/senadaruch% LinkedIn:%https://www.linkedin.com/in/senadaruc Davide%Cioccia% MSc%Computer%Engineering%Degree.%Security%Developer%focused%on%Cyber%Security%Intelligence,%Malware%analysis,%Anti? fraud%systems.%Microsoft%certified.%Currently%holding%a%Security%Consultant%position%at%Reply%s.p.a%?%Communication% Valley%?%Security%Operations%Center.% E?Mail:%davide.cioccia@live.it% % Twitter:%https://twitter.com/david107% LinkedIn:%https://www.linkedin.com/in/davidecioccia %
