Operating Systems - File Space Allocation
- 1. Operating System Handout Unit VI ŌĆō File management 1.Files Concepts: ’éĘ A file is a named collection of related information that is recorded on secondary storage such as magnetic disks, magnetic tapes and optical disks. ’éĘ In general, a file is a sequence of bits, bytes, lines or records whose meaning is defined by the files creator and user. ’éĘ Attributes of a File ’éĘ Following are some of the attributes of a file: ’éĘ Name . It is the only information which is in human-readable form. ’éĘ Identifier. The file is identified by a unique tag(number) within file system. ’éĘ Type. It is needed for systems that support different types of files. ’éĘ Location. Pointer to file location on device. ’éĘ Size. The current size of the file. ’éĘ Protection. This controls and assigns the power of reading, writing, executing. ’éĘ Time, date, and user identification. This is the data for protection, security, and usage monitoring ’éĘ File Operation ’éĘ The operating system must do to perform basic file operations given below. ’éĘ Creating a file: Two steps are necessary to create a file. First, space in the file system must be found for the file. Second, an entry for the new file must be made in the directory. ’éĘ Writing a file: To write a file, we make a system call specifying both the name of the file and the information to be written to the file. Given the name of the file, the system searches the directory to find the file's location. The system must keep a write pointer to the location in the file where the next write is to take place. The write pointer must be updated whenever a write occurs. ’éĘ Reading a file: To read from a file, we use a system call that specifies the name of the file and where (in memory) the next block of the file should be put. Again, the directory is searched for the associated entry, and the system needs to keep a read pointer to the location in the file where the next read is to take place. Once the read has taken place, the read pointer is updated. ’éĘ Repositioning within a file: The directory is searched for the appropriate entry, and the current-file-position pointer is repositioned to a given value. Repositioning within a file need not involve any actual I/O. This file operation is also known as a file seek. ’éĘ Deleting a file. To delete a file, we search the directory for the named file. Having found the associated directory entry, we release all file space, so that it can be reused bv other files, and erase the directory entry. Mr. V.N.Kukre Page 1 of 17
- 2. Operating System Handout ’éĘ Protection: Access-control information determines who can do reading, writing, executing, and so on. ’éĘ Truncating a file: The user may want to erase the contents of a file but keep its attributes. Rather than forcing the user to delete the file and then recreate it, this function allows all attributes to remain unchangedŌĆöexcept for file lengthŌĆöbut lets the tile be reset to length zero and its file space released. In brief File Types Mr. V.N.Kukre Page 2 of 17
- 3. Operating System Handout File System Structure A File Structure should be according to a required format that the operating system can understand. ’éĘA file has a certain defined structure according to its type. ’éĘA text file is a sequence of characters organized into lines. ’éĘA source file is a sequence of procedures and functions. ’éĘAn object file is a sequence of bytes organized into blocks that are understandable by the machine. ’éĘWhen operating system defines different file structures, it also contains the code to support these file structure. Unix, MS-DOS support minimum number of file structure. Files can be structured in several ways in which three common structures are given in this tutorial with their short description one by one. File Structure 1 ’éĘHere, as you can see from the figure 1, the file is an unstructured sequence of bytes. ’éĘTherefore, the OS doesn't care about what is in the file, as all it sees are bytes. File Structure 2 ’éĘNow, as you can see from the figure 2 that shows the second structure of a file, where a file is a sequence of fixed-length records where each with some internal structure. ’éĘCentral to the idea about a file being a sequence of records is the idea that read operation returns a record and write operation just appends a record. File Structure 3 ’éĘNow in the last structure of a file that you can see in the figure 3, a file basically consists of a tree of records, not necessarily all the same length, each containing a key field in a fixed position in the record. The tree is stored on the field, just to allow the rapid searching for a specific key. Fig.1 Fig.2 Fig.3 Mr. V.N.Kukre Page 3 of 17
- 4. Mr. V.N.Kukre Page 4 of 17 Operating System Handout 2. File Access method File access mechanism refers to the manner in which the records of a file may be accessed. There are several ways to access files ŌłÆ ’éĘ Sequential access ’éĘ Direct/Random access ’éĘ Indexed sequential access 1.Sequential Access ’éĘ A sequential access is that in which the records are accessed in some sequence, i.e., the information in the file is processed in order, one record after the other. This access method is the most primitive one. ’éĘ The idea of Sequential access is based on the tape model which is a sequential access device. ’éĘ The Sequential access method is best because most of the records in a file are to be processed. For example, transaction files. ’éĘ Example: Compilers usually access files in this fashion. In Brief: ’éĘData is accessed one record right after another is an order. ’éĘRead command cause a pointer to be moved ahead by one. ’éĘWrite command allocate space for the record and move the pointer to the new End of File. ’éĘSuch a method is reasonable for tape. Advantages of sequential access ’éĘIt is simple to program and easy to design. ’éĘSequential file is best use if storage space. Disadvantages of sequential access ’éĘSequential file is time consuming process. ’éĘIt has high data redundancy. ’éĘRandom searching is not possible. 2.Direct Access ’éĘ Sometimes it is not necessary to process every record in a file. ’éĘ It is not necessary to process all the records in the order in which they are present in the memory. In all such cases, direct access is used. ’éĘ The disk is a direct access device which gives us the reliability to random access of any file block. ’éĘ In the file, there is a collection of physical blocks and the records of that blocks. ’éĘ Example: Databases are often of this type since they allow query processing that involves immediate access to large amounts of information. All reservation systems fall into this category. In brief: ’éĘThis method is useful for disks. ’éĘThe file is viewed as a numbered sequence of blocks or records.
- 5. Mr. V.N.Kukre Page 5 of 17 Operating System Handout ’éĘ There are no restrictions on which blocks are read/written, it can be dobe in any order. ’éĘ User now says "read n" rather than "read next". ’éĘ "n" is a number relative to the beginning of file, not relative to an absolute physical disk location. Advantages: ’éĘ Direct access file helps in online transaction processing system (OLTP) like online railway reservation system. ’éĘ In direct access file, sorting of the records are not required. ’éĘ It accesses the desired records immediately. ’éĘ It updates several files quickly. ’éĘ It has better control over record allocation. Disadvantages: ’éĘ Direct access file does not provide backup facility. ’éĘ It is expensive. ’éĘ It has less storage space as compared to sequential file. 3. Indexed Sequential Access ’éĘ The index sequential access method is a modification of the direct access method. ’éĘ Basically, it is kind of combination of both the sequential access as well as direct access. ’éĘ The main idea of this method is to first access the file directly and then it accesses sequentially. ’éĘ In this access method, it is necessary for maintaining an index. ’éĘ The index is nothing but a pointer to a block. ’éĘ The direct access of the index is made to access a record in a file. ’éĘ The information which is obtained from this access is used to access the file. Sometimes the indexes are very big. ’éĘ So to maintain all these hierarchies of indexes are built in which one direct access of an index leads to information of another index access. ’éĘ It is built on top of Sequential access. ’éĘ It uses an Index to control the pointer while accessing files. Advantages: ’éĘ In indexed sequential access file, sequential file and random file access is possible. ’éĘ It accesses the records very fast if the index table is properly organized. ’éĘ The records can be inserted in the middle of the file. ’éĘ It provides quick access for sequential and direct processing. ’éĘ It reduces the degree of the sequential search. Disadvantages: ’éĘ Indexed sequential access file requires unique keys and periodic reorganization. ’éĘ Indexed sequential access file takes longer time to search the index for the data access or retrieval.
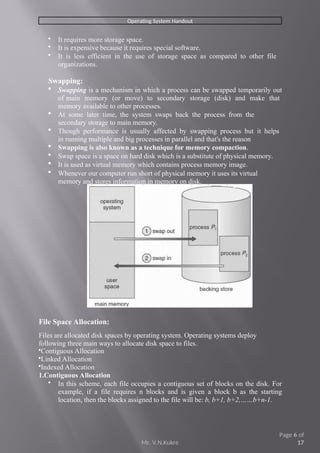
- 6. Operating System Handout ’éĘ It requires more storage space. ’éĘ It is expensive because it requires special software. ’éĘ It is less efficient in the use of storage space as compared to other file organizations. Swapping: ’éĘ Swapping is a mechanism in which a process can be swapped temporarily out of main memory (or move) to secondary storage (disk) and make that memory available to other processes. ’éĘ At some later time, the system swaps back the process from the secondary storage to main memory. ’éĘ Though performance is usually affected by swapping process but it helps in running multiple and big processes in parallel and that's the reason ’éĘ Swapping is also known as a technique for memory compaction. ’éĘ Swap space is a space on hard disk which is a substitute of physical memory. ’éĘ It is used as virtual memory which contains process memory image. ’éĘ Whenever our computer run short of physical memory it uses its virtual memory and stores information in memory on disk. File Space Allocation: Files are allocated disk spaces by operating system. Operating systems deploy following three main ways to allocate disk space to files. ’éĘContiguous Allocation ’éĘLinked Allocation ’éĘIndexed Allocation 1.Contiguous Allocation ’éĘ In this scheme, each file occupies a contiguous set of blocks on the disk. For example, if a file requires n blocks and is given a block b as the starting location, then the blocks assigned to the file will be: b, b+1, b+2,ŌĆ”ŌĆ”b+n-1. Mr. V.N.Kukre Page 6 of 17
- 7. Operating System Handout ’éĘ This means that given the starting block address and the length of the file (in terms of blocks required), we can determine the blocks occupied by the file. ’éĘ The directory entry for a file with contiguous allocation contains 1. Address of starting block 2. Length of the allocated portion. ’éĘ The file ŌĆśmailŌĆÖ in the following figure starts from the block 19 with length = 6 blocks. Therefore, it occupies 19, 20, 21, 22, 23, 24 blocks. ’éĘ Each file occupies a contiguous address space on disk. ’éĘ Assigned disk address is in linear order. ’éĘ Easy to implement. ’éĘ External fragmentation is a major issue with this type of allocation technique. Advantages: ’éĘ Both the Sequential and Direct Accesses are supported by this. For direct access, the address of the kth block of the file which starts at block b can easily be obtained as (b+k). ’éĘ This is extremely fast since the number of seeks are minimal because of contiguous allocation of file blocks. Disadvantages: ’éĘ This method suffers from both internal and external fragmentation. This makes it inefficient in terms of memory utilization. ’éĘ Increasing file size is difficult because it depends on the availability of contiguous memory at a particular instance. 2. Linked Allocation ’éĘ In this scheme, each file is a linked list of disk blocks which need not be contiguous. ’éĘ The disk blocks can be scattered anywhere on the disk. ’éĘ The directory entry contains a pointer to the starting and the ending file block. ’éĘ Each block contains a pointer to the next block occupied by the file. ’éĘ The file ŌĆśjeepŌĆÖ in following image shows how the blocks are randomly distributed. The last block (25) contains -1 indicating a null pointer and does not point to any other block. Mr. V.N.Kukre Page 7 of 17
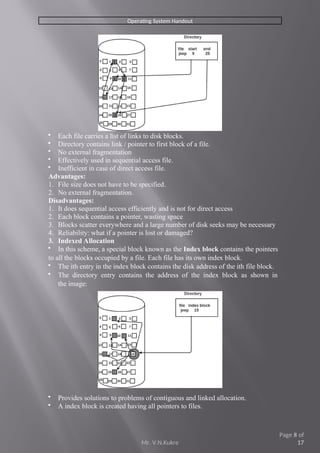
- 8. Operating System Handout ’éĘ Each file carries a list of links to disk blocks. ’éĘ Directory contains link / pointer to first block of a file. ’éĘ No external fragmentation ’éĘ Effectively used in sequential access file. ’éĘ Inefficient in case of direct access file. Advantages: 1. File size does not have to be specified. 2. No external fragmentation. Disadvantages: 1. It does sequential access efficiently and is not for direct access 2. Each block contains a pointer, wasting space 3. Blocks scatter everywhere and a large number of disk seeks may be necessary 4. Reliability: what if a pointer is lost or damaged? 3. Indexed Allocation ’éĘ In this scheme, a special block known as the Index block contains the pointers to all the blocks occupied by a file. Each file has its own index block. ’éĘ The ith entry in the index block contains the disk address of the ith file block. ’éĘ The directory entry contains the address of the index block as shown in the image: ’éĘ Provides solutions to problems of contiguous and linked allocation. ’éĘ A index block is created having all pointers to files. Mr. V.N.Kukre Page 8 of 17