Overview on Biometrics by Ch.Ravikumar & Priya N
- 1. Topic: BIOMETRICS Presented By:- Ch Ravikumar T.E.ENTC Priya N T.E.ENTC
- 2. Contents 1.Defination 2.Generic Biometric System 3.Types of biometrics 4.Biometric System Vulnerabilities 5.Security Approaches
- 3. Biometrics ’üĄ ŌĆ£It is a physiological or behavioral characteristic of a human being that can distinguish one person from another and that theoretically can be used for identification or verification of identity.ŌĆØ Who are you? Prove it.
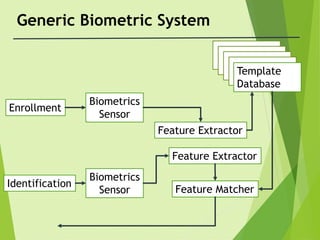
- 4. Generic Biometric System Enrollment Biometrics Sensor Identification Biometrics Sensor Template Database Feature Extractor Feature Extractor Feature Matcher
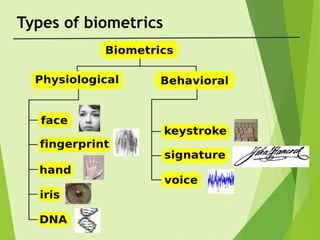
- 6. Face Recognition ŌĆó A face image can be acquired using a normal, off-the-shelf camera ŌĆó Easy to accept by the public ŌĆó Cost is rather low
- 7. Finger Printing ŌĆó Used in forensics more than 100 years ŌĆó Optical, capacitive readers ŌĆó Liveness detection
- 9. Hand Geometry ŌĆóCaptured using a CCD camera, or LED ŌĆóOrthographic Scanning ŌĆóThe system is often bulky
- 10. Eyes:Iris,Retina ŌĆó Extracts features from the colored tissue surrounding the pupil. ŌĆó Monochrome camera with visible and near infra red light ŌĆó Liveness detection
- 11. DNA ŌĆó Deoxyribonucliec Acid ŌĆó Contains Genetic information ŌĆó Differentiated using base pairs
- 12. Keystrokes ŌĆó No special hardware Required ŌĆó Transparent capture
- 13. Voice ŌĆó Speaker recognition uses a microphone to record the voice ŌĆó Your voice can vary with age, illness and emotions ŌĆó Interesting with the increasing use of mobile phones
- 14. Biometric System Vulnerabilities Biometric System Vulnerabilities Adversary Attacks Spoofing Template database leakage Intrinsic Limitations
- 15. Intrinsic Limitations ŌĆó False Non- Match ŌĆó False match ŌĆó Zero effort attack
- 16. Adversary Attacks ŌĆó Caused due to negligence of authorized persons ŌĆó An adversary exploiting the system security using insiders ŌĆó Direct attack on the sensors
- 17. Spoof Attacks
- 18. Template Database leakage ŌĆó Biometric template information becomes available to an adversary ŌĆó Easier to recover by using reverse engineering
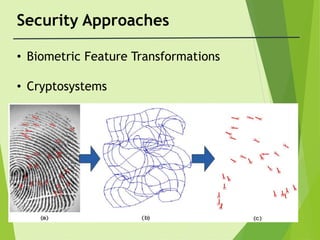
- 19. Security Approaches ŌĆó Biometric Feature Transformations ŌĆó Cryptosystems
- 20. FUTURE METHODS Face recognition through blood vessels
- 21. FUTURE METHODS Brainwave recognition