PCI DSS Compliance for Web Applications
- 1. PCI DSS Compliance for Web Applications Savan Gadhiya
- 2. #whoami ŌĆō Savan Gadhiya ŌĆó Senior Security Consultant at NotSoSecure ŌĆó Hacker, Security Researcher, Developer and Bounty Hunter Ōś║ ŌĆó 7 years of experience in Information Technology ŌĆó Master of Engineering in IT Systems and Network Security /gadhiyasavan @gadhiyasavan
- 3. Agenda ŌĆó What is Compliance? ŌĆó List of Compliances ŌĆó Understand PCI DSS Compliance ŌĆō Basic ŌĆó Applicability ŌĆó Overview ŌĆó Testing Procedure ŌĆó Storage Procedure ŌĆó Lifecycle Phase ŌĆó PCI DSS ŌĆō Web application checklist
- 4. What is Compliance? ŌĆó Compliance means ŌĆó Conforming to a rule, such as a specification, policy, standard or law ŌĆó List of widely used Compliances: ŌĆó PCI DSS - Payment Card Industry Data Security Standard ŌĆó HIPAA - Health Insurance Portability and Accountability Act ŌĆó FISMA - Federal Information Security Management Act ŌĆó SOX - Sarbanes-Oxley Act ŌĆó GDPR - General Data Protection Regulation
- 5. PCI DSS ŌĆó PCI DSS - Payment Card Industry Data Security Standard ŌĆó Requirement for the majority of businesses today, as most handle or interact with credit card data and other sensitive customer information. Version Date May 2018 3.2.1 April 2016 3.2 ŌĆō Retires on 31st December 2018 April 2015 3.1 November 2013 3.0 October 2010 2.0 July 2009 1.2.1 October 2008 1.2
- 6. PCI DSS ŌĆō Applicability ŌĆó PCI DSS applies to: ŌĆó All entities involved in payment and processing ŌĆō including merchants, processors, acquirers, issuers and service provides ŌĆó Store, process or transmit cardholder data and/or sensitive authentication data ŌĆó Examples: Retail sites, Online travel agencies, bill-pay portals for utilities and services, online wallet and bank transfer services etc. ŌĆó CardholderŌĆÖs data: ŌĆó Primary Account Number ŌĆō PAN ŌĆó Cardholder Name ŌĆó Expiration Date ŌĆó Service Code ŌĆó CardholderŌĆÖs sensitive authentication data: ŌĆó Full track data ŌĆō magnetic-stripe data or equivalent on a chip ŌĆó CAV2/CVC2/CVV2/CID ŌĆó PINs/PIN blocks
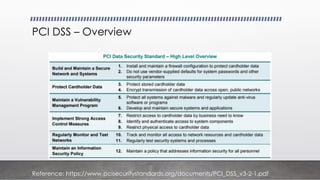
- 7. PCI DSS ŌĆō Overview Reference: https://www.pcisecuritystandards.org/documents/PCI_DSS_v3-2-1.pdf
- 8. PCI DSS ŌĆō Testing Procedure ŌĆó Compliance check on sample systems/devices ŌĆó Selected randomly at the time of audit ŌĆó Examine policies ŌĆó Examine the supporting documentation ŌĆó Interview responsible personnel etc.
- 9. PCI DSS ŌĆō Storage Permission Reference: https://www.pcisecuritystandards.org/documents/PCI_DSS_v3-2-1.pdf
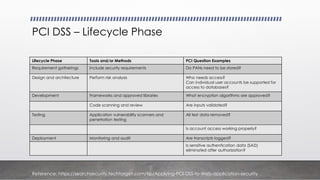
- 10. PCI DSS ŌĆō Lifecycle Phase Lifecycle Phase Tools and/or Methods PCI Question Examples Requirement gatherings Include security requirements Do PANs need to be stored? Design and architecture Perform risk analysis Who needs access? Can individual user accounts be supported for access to databases? Development Frameworks and approved libraries What encryption algorithms are approved? Code scanning and review Are inputs validated? Testing Application vulnerability scanners and penetration testing All test data removed? Is account access working properly? Deployment Monitoring and audit Are transcripts logged? Is sensitive authentication data (SAD) eliminated after authorization? Reference: https://searchsecurity.techtarget.com/tip/Applying-PCI-DSS-to-Web-application-security
- 11. PCI DSS ŌĆō Web Application Checklist ŌĆó Default credentials ŌĆó Firewall bypass ŌĆó Information leakage ŌĆō Card HolderŌĆÖs data ŌĆó Cleartext transmission of card holderŌĆÖs data/credentials/sensitive information ŌĆó Usage of weak cipher suites such as SSL/early TLS ŌĆó Verify that PAN is rendered unreadable or secured with strong cryptography ŌĆó Verify the restrictions on access of Card HolderŌĆÖs data ŌĆó Least amount of data ŌĆó Duration
- 12. PCI DSS ŌĆō Web Application Checklist If support team/administrators are using Card HolderŌĆÖs data for web application: ŌĆó Password Complexity ŌĆó At least 7 characters, Numbers and alphanumeric, Change users password at least once in 90 days, Do not allow to set password from last four passwords ŌĆó Set password for first time use only ŌĆō upon reset to a unique value for each users, change immediately after first usage ŌĆó Remove inactive accounts within 90 days ŌĆó Unique identification of users ŌĆó Account lockout on 6 invalid attempts, set account lockout to a minimum of 30 minutes or until an admin enables the user ID ŌĆó Session Expiration after 15 minutes of inactivity ŌĆó Authenticate users ŌĆó Something you Know, Something you have, Something you are
- 13. PCI DSS ŌĆō Web Application Checklist If support team/administrators are using Card HolderŌĆÖs data for web application: ŌĆó Credentials in unreadable encrypted format while transmission or storage ŌĆó Verify the user identity before modifying any authentication credentials, for e.g. performing password resets, provisioning new tokens, generating new keys etc. ŌĆó Two Factor Authentication for Card Holder Data Environment for Remote accesses ŌĆó Generic or shared user IDs should be disabled Others: ŌĆó Logging management ŌĆó Secure Code Review ŌĆó Application layer firewall in front of Web-facing applications
- 14. References ŌĆó https://www.pcisecuritystandards.org ŌĆó https://www.pcisecuritystandards.org/documents/PCI_DSS_v3-2-1.pdf ŌĆó https://www.pcisecuritystandards.org/pdfs/pci_fs_data_storage.pdf ŌĆó https://www.visa-asia.com/ap/sa/merchants/riskmgmt/includes/uploads/PABP_v14.pdf ŌĆó https://www.pcicomplianceguide.org/web-application-security-how-do-you-know- which-solutions-will-work-best-for-your-business/ ŌĆó https://searchsecurity.techtarget.com/tip/Applying-PCI-DSS-to-Web-application- security