1 of 27
Download to read offline


























Recommended
Tempo October 2014



Tempo October 2014Tempoplanet
Ìę
Tempo October 2014
Cover Story: Being Arab
Check out our website: http://tempoplanet.com/
Check us out on our social media pages:
Facebook: https://www.facebook.com/pages/Abu-Dhabi-Tempo/114665148553019
Twitter: https://twitter.com/tempoplanet
Instagram: http://instagram.com/tempoplanetPromart corp ppt feb 2013 changes made



Promart corp ppt feb 2013 changes madePromart Retail India Pvt. Ltd.
Ìę
Promart is a multi-brand retail chain that offers discounts between 25-60% on national brands of clothing, footwear, and accessories. It aims to cater to brand-conscious young Indian consumers across 1000-5000 sq ft stores located in prominent malls and high streets of Tier 1-6 cities. The company sources unsold inventory from brands and plans to expand its network of both company-owned and franchise stores to 100 and 50 respectively by 2013. Promart leverages the large aspirational middle class in India and their demand for discounted premium brands.

10. jesĂșs en jerusalĂ©nA L
Ìę
Santa Biblia
Antiguo Testamento
Nuevo Testamento
Escuela SabĂĄtica
Segundo Trimestre del 2016
GuĂa de Estudio de la Biblia
El libro de Mateo
GRES
GuĂa para el Repaso de Escuela SabĂĄtica
Material de apoyo
Estudio BĂblico inductivo de la Palabra de Dios
Iglesia Adventista del SĂ©ptimo DĂa
Airtherm product range



Airtherm product rangeAirtherm Engineering
Ìę
Airtherm Products brochure »
An introduction to the various products and systems we offer at Airtherm and information outlining the specifics of each system and further information such as design, installation, benefits, application, controls and related products.CT-2085B EUR WIFI 2.4ghz 5ghz 3.5gz wimax cdam gsm 2g 3g 4g 8 antennas 18w br...



CT-2085B EUR WIFI 2.4ghz 5ghz 3.5gz wimax cdam gsm 2g 3g 4g 8 antennas 18w br...Shop-WiFi - Wireless RF Technology R&R Group Jammers4u
Ìę
CT-2085B EUR WIFI 2.4ghz 5ghz 3.5gz wimax cdam gsm 2g 3g 4g 8 antennas 18w briefcase jammer up to 50m www.jammers4u.comSCA Group Brief February 2013 - Access (Scaffold and Rope Access), Containmen...



SCA Group Brief February 2013 - Access (Scaffold and Rope Access), Containmen...Claudine Cross
Ìę
Established in 1998, the SCA Group consists of four operational businesses:
âą SCA Scaffold Projects â supply and erection of scaffolding to a variety of clients, with market-leading design capabilities, providing bespoke solutions
âą SCA Marine â marine-focused, providing tailored access and containment solutions to the UKâs ship repair and refurbishment industry
âą SCA ProTect â specialist, high-quality site/structure protection and weatherproof containment utilising fully recyclable shrink-wrap material
âą SCA Rope Access â specialist access to the most demanding projects; highways, byways and railways, on and offshore, including oil, nuclear and renewable energy industries
Underpinning all of the SCA Groupâs divisions are a team of directly employed, qualified and experienced multi-disciplinary specialists, providing industrial support services such as surface-preparation, blasting, painting, inspection/analysis, non-destructive testing (NDT) and corrosion-control. We cater for projects in the most challenging of locations for a wide variety of market sectors.


8. jesĂșs mostraba simpatĂaA L
Ìę
Santa Biblia
Antiguo Testamento
Nuevo Testamento
Escuela SabĂĄtica
Tercer Trimestre del 2016
GuĂa de Estudio de la Biblia
El Papel de la Iglesia en la Comunidad
GRES
GuĂa para el Repaso de Escuela SabĂĄtica
Material de apoyo
Estudio BĂblico inductivo de la Palabra de Dios
Iglesia Adventista del SĂ©ptimo DĂa


Rachel Fullmer-portfolio



Rachel Fullmer-portfolioskeez0526
Ìę
This document appears to be a design portfolio containing examples of work from various design projects including website design, magazine layout, social media advertising, poster advertisements, event flyers, photo collages, slide design, and typography. The portfolio is presented across 10 pages and concludes by thanking the viewer for their consideration.

2. crisis en el edénA L
Ìę
Santa Biblia
Antiguo Testamento
Nuevo Testamento
Escuela SabĂĄtica
Primer Trimestre del 2016
GuĂa de Estudio de la Biblia
RebeliĂłn y RedenciĂłn
GRES
GuĂa para el Repaso de Escuela SabĂĄtica
Material de apoyo
Estudio BĂblico inductivo de la Palabra de Dios
Iglesia Adventista del SĂ©ptimo DĂa
Coal train fact_check



Coal train fact_checkBentonFranklin
Ìę
This document provides a fact check by Bob Vance, P.E. on issues related to proposed coal export shipments from the Powder River Basin in Wyoming to China via rail lines and shipping terminals in Washington state. Bob rates several claims as only 10-25% true, finding that dust mitigation measures have significantly reduced coal dust losses from trains. He also rates claims about the impacts of additional coal trains on traffic and the rail system as 90% true, but notes confirmation is needed from railroads. Bob concludes that dust control at port facilities can be adequately managed with conventional technology.Spyddr



SpyddrSteph Cliche
Ìę
The document summarizes the encryption methods used by the MfS (Stasi) of East Germany to communicate with spies via shortwave radio. It describes how agents were initially given mnemonic phrases to encrypt messages with a Soviet method until 1959, when the MfS switched to a secure one-time pad cipher using random numbers printed on paper strips. Messages were encrypted in headquarters and transmitted in 5-number groups to transmission stations. Agents decrypted with matching paper strips. Later, programmable speech-morse generators digitally announced numbers to agents in various languages. The document details the MfS's transmission stations, equipment, and methods used over time to covertly transmit encrypted radio messages to agents.Cf 8 blocks of success training1



Cf 8 blocks of success training1Muhammed Eid
Ìę
The document outlines the 8 success basics for network marketing: 1) creating a dreams list, 2) building a contact list, 3) making invitation calls, 4) developing presentation skills, 5) follow up, 6) handling objections, 7) closing, and 8) duplication. It then provides more details on each step, explaining how to create a dreams list, build a contact list of friends and family, conduct invitation calls, present to prospects, follow up after presentations, address common objections, close by welcoming new members, and ultimately duplicate the process by learning from uplines. The overall message is that following these 8 success basics can help one achieve their dreams through network marketing. flue dilution solution 



flue dilution solution Airtherm Engineering
Ìę
Airtherm offers flue dilution systems using fan technology to dilute combustion emissions from gas boilers. Their systems allow for flexible boiler siting and eliminate the need for expensive or unsightly flue stacks. They provide customized flue dilution solutions suitable for commercial, industrial, and domestic applications. Their installation teams have extensive experience meeting all necessary standards for projects.

12. los Ășltimos dĂas de jesĂșsA L
Ìę
Santa Biblia
Antiguo Testamento
Nuevo Testamento
Escuela SabĂĄtica
Segundo Trimestre del 2016
GuĂa de Estudio de la Biblia
El libro de Mateo
GRES
GuĂa para el Repaso de Escuela SabĂĄtica
Material de apoyo
Estudio BĂblico inductivo de la Palabra de Dios
Iglesia Adventista del SĂ©ptimo DĂa
WordPress 3.6 New Features



WordPress 3.6 New Featuresmasmanx
Ìę
WordPress 3.6 introduced new post formats, improved audio and video support without needing plugins, enhanced navigation menus, improved auto save functionality, post revision management, post locking notifications, and a new default theme called 2013. Key new features included standard and gallery post formats, direct video embedding from URLs, an accordion-based menu UI, preventing data loss from browser or server issues during editing, tracking post changes over time, and warnings of concurrent editing.

76216 99253-1-pbRolando Calle
Ìę
El documento analiza la evoluciĂłn del pensamiento de PlatĂłn sobre la distinciĂłn entre episteme y doxa en el contexto Ă©tico. Indica que en los primeros diĂĄlogos platĂłnicos, la doxa se refiere a la opiniĂłn subjetiva, mientras que la episteme se entiende como habilidad tĂ©cnica. Posteriormente, PlatĂłn desarrolla conceptos mĂĄs estrictos de ambos tĂ©rminos y los aplica a cuestiones Ă©ticas, llegando a identificar la Ă©tica con la episteme en La RepĂșblica.Social Media for Business



Social Media for BusinessDeborah Deras, M.S., ALSP
Ìę
Deborah Deras, Corporate Trainer, Keynote Speaker, Author and Faculty at the University of Phoenix was the keynote speaker in Orange County on Social Media for Business Owners.The busy author's guide to popularity and profit on pinterest



The busy author's guide to popularity and profit on pinterestBestsellerSociety
Ìę
The document provides tips and strategies for using Pinterest effectively for authors. It discusses how to set up a Pinterest profile in 10 easy steps, including signing up, creating boards, and pinning content. It also lists 7 free tools that can help supercharge pinning on Pinterest, such as tools for creating pinnable images, tracking website traffic from Pinterest, and scheduling pins in advance. Finally, it lists 11 places authors can find free and legal photos to use on their blogs and websites.Spy pack



Spy packSteph Cliche
Ìę
This document provides instructions for setting up a school spy ring using activities from Tom Palmer's Spy Pack. It includes:
1) Instructions for choosing children to join the spy ring and finding a secret location to brief them.
2) Suggestions for introducing the spy ring concept and testing the children's suitability for the role.
3) A note that establishing rules and identities for the spy ring will help build group identity and secrecy.Sc2014 proceedings



Sc2014 proceedingsSteph Cliche
Ìę
This document provides an overview of the SAT Competition 2014 (SC 2014). SC 2014 consisted of 13 competition tracks to evaluate SAT solvers on various types of benchmarks under different resource constraints. Around 50 solver descriptions and 10 benchmark descriptions were submitted by a total of around 80 contributors. This document compiles all the non-peer-reviewed solver and benchmark descriptions to provide insights into state-of-the-art SAT solving technology in 2014 and serve as a historical reference. Major support for running SC 2014 came from the community and computing resources from the University of Texas at Austin.Satellite hacking



Satellite hackingSteph Cliche
Ìę
The document provides an overview of satellite systems and hacking vulnerabilities. It describes the basic components of satellite systems, including the satellite itself with its payload and bus, as well as tracking, telemetry and control ground stations. It discusses various satellite orbits, frequencies used for transmission, and the structure of very small aperture terminals (VSATs) and other scaled down ground stations. The document notes that while satellite systems have some redundancy to mitigate risks, their design also has elements of simplicity that could enable hacking, such as accessing unencrypted frequencies. However, fully hacking a satellite would require significant technical knowledge and resources.Safes locking device-_mechanical_locks_versus_electronic_locks



Safes locking device-_mechanical_locks_versus_electronic_locksSteph Cliche
Ìę
The document discusses mechanical dial locks versus electronic locks for safes. It recommends either a UL Group II mechanical dial lock or a commercial-grade electronic lock. While electronic locks are more convenient, mechanical dial locks are more durable and reliable long-term. The Sargent & Greenleaf model 6730 dial lock is an industry standard. Cheap imported electronic locks are prone to failures and can be difficult to repair if the lock fails with the door closed. The document advises choosing a UL certified commercial-grade electronic lock from reputable manufacturers if an electronic lock is preferred.Ieee project-2014-2015-context-based-access-control-systems



Ieee project-2014-2015-context-based-access-control-systemsSteph Cliche
Ìę
The document proposes a context-based access control mechanism for Android systems that allows users to set configuration policies controlling applications' access to device resources and services based on context such as location and time. It implements this access control framework on the Android operating system, allowing users to define physical places and link them to logical locations. The access controller then enforces the defined policies by granting or restricting privileges to applications dynamically based on the device's detected context. Experimental results show this mechanism can accurately detect contexts using Wi-Fi signals and effectively enforce access control policies with minimal performance impact.Ieee interference-measurements-802.11n



Ieee interference-measurements-802.11nSteph Cliche
Ìę
The document describes interference measurements taken in an 802.11n wireless mesh network testbed. The testbed uses wireless routers with multiple 802.11n transceivers and directional antennas. Measurements were taken of co-channel interference, signal-to-interference-and-noise ratio (SINR), and TCP/UDP throughput over different channels. Even with very high SINR links of 30-40 dB using MIMO antennas and frame aggregation, the maximum TCP throughput achieved was only 47.85 Mbps, which is significantly lower than the maximum PHY transmission rate of 144 Mbps. The interference measurements from this testbed can help optimize the performance of large-scale 802.11n wirelessMore Related Content
Viewers also liked (15)


8. jesĂșs mostraba simpatĂaA L
Ìę
Santa Biblia
Antiguo Testamento
Nuevo Testamento
Escuela SabĂĄtica
Tercer Trimestre del 2016
GuĂa de Estudio de la Biblia
El Papel de la Iglesia en la Comunidad
GRES
GuĂa para el Repaso de Escuela SabĂĄtica
Material de apoyo
Estudio BĂblico inductivo de la Palabra de Dios
Iglesia Adventista del SĂ©ptimo DĂa


Rachel Fullmer-portfolio



Rachel Fullmer-portfolioskeez0526
Ìę
This document appears to be a design portfolio containing examples of work from various design projects including website design, magazine layout, social media advertising, poster advertisements, event flyers, photo collages, slide design, and typography. The portfolio is presented across 10 pages and concludes by thanking the viewer for their consideration.

2. crisis en el edénA L
Ìę
Santa Biblia
Antiguo Testamento
Nuevo Testamento
Escuela SabĂĄtica
Primer Trimestre del 2016
GuĂa de Estudio de la Biblia
RebeliĂłn y RedenciĂłn
GRES
GuĂa para el Repaso de Escuela SabĂĄtica
Material de apoyo
Estudio BĂblico inductivo de la Palabra de Dios
Iglesia Adventista del SĂ©ptimo DĂa
Coal train fact_check



Coal train fact_checkBentonFranklin
Ìę
This document provides a fact check by Bob Vance, P.E. on issues related to proposed coal export shipments from the Powder River Basin in Wyoming to China via rail lines and shipping terminals in Washington state. Bob rates several claims as only 10-25% true, finding that dust mitigation measures have significantly reduced coal dust losses from trains. He also rates claims about the impacts of additional coal trains on traffic and the rail system as 90% true, but notes confirmation is needed from railroads. Bob concludes that dust control at port facilities can be adequately managed with conventional technology.Spyddr



SpyddrSteph Cliche
Ìę
The document summarizes the encryption methods used by the MfS (Stasi) of East Germany to communicate with spies via shortwave radio. It describes how agents were initially given mnemonic phrases to encrypt messages with a Soviet method until 1959, when the MfS switched to a secure one-time pad cipher using random numbers printed on paper strips. Messages were encrypted in headquarters and transmitted in 5-number groups to transmission stations. Agents decrypted with matching paper strips. Later, programmable speech-morse generators digitally announced numbers to agents in various languages. The document details the MfS's transmission stations, equipment, and methods used over time to covertly transmit encrypted radio messages to agents.Cf 8 blocks of success training1



Cf 8 blocks of success training1Muhammed Eid
Ìę
The document outlines the 8 success basics for network marketing: 1) creating a dreams list, 2) building a contact list, 3) making invitation calls, 4) developing presentation skills, 5) follow up, 6) handling objections, 7) closing, and 8) duplication. It then provides more details on each step, explaining how to create a dreams list, build a contact list of friends and family, conduct invitation calls, present to prospects, follow up after presentations, address common objections, close by welcoming new members, and ultimately duplicate the process by learning from uplines. The overall message is that following these 8 success basics can help one achieve their dreams through network marketing. flue dilution solution 



flue dilution solution Airtherm Engineering
Ìę
Airtherm offers flue dilution systems using fan technology to dilute combustion emissions from gas boilers. Their systems allow for flexible boiler siting and eliminate the need for expensive or unsightly flue stacks. They provide customized flue dilution solutions suitable for commercial, industrial, and domestic applications. Their installation teams have extensive experience meeting all necessary standards for projects.

12. los Ășltimos dĂas de jesĂșsA L
Ìę
Santa Biblia
Antiguo Testamento
Nuevo Testamento
Escuela SabĂĄtica
Segundo Trimestre del 2016
GuĂa de Estudio de la Biblia
El libro de Mateo
GRES
GuĂa para el Repaso de Escuela SabĂĄtica
Material de apoyo
Estudio BĂblico inductivo de la Palabra de Dios
Iglesia Adventista del SĂ©ptimo DĂa
WordPress 3.6 New Features



WordPress 3.6 New Featuresmasmanx
Ìę
WordPress 3.6 introduced new post formats, improved audio and video support without needing plugins, enhanced navigation menus, improved auto save functionality, post revision management, post locking notifications, and a new default theme called 2013. Key new features included standard and gallery post formats, direct video embedding from URLs, an accordion-based menu UI, preventing data loss from browser or server issues during editing, tracking post changes over time, and warnings of concurrent editing.

76216 99253-1-pbRolando Calle
Ìę
El documento analiza la evoluciĂłn del pensamiento de PlatĂłn sobre la distinciĂłn entre episteme y doxa en el contexto Ă©tico. Indica que en los primeros diĂĄlogos platĂłnicos, la doxa se refiere a la opiniĂłn subjetiva, mientras que la episteme se entiende como habilidad tĂ©cnica. Posteriormente, PlatĂłn desarrolla conceptos mĂĄs estrictos de ambos tĂ©rminos y los aplica a cuestiones Ă©ticas, llegando a identificar la Ă©tica con la episteme en La RepĂșblica.Social Media for Business



Social Media for BusinessDeborah Deras, M.S., ALSP
Ìę
Deborah Deras, Corporate Trainer, Keynote Speaker, Author and Faculty at the University of Phoenix was the keynote speaker in Orange County on Social Media for Business Owners.The busy author's guide to popularity and profit on pinterest



The busy author's guide to popularity and profit on pinterestBestsellerSociety
Ìę
The document provides tips and strategies for using Pinterest effectively for authors. It discusses how to set up a Pinterest profile in 10 easy steps, including signing up, creating boards, and pinning content. It also lists 7 free tools that can help supercharge pinning on Pinterest, such as tools for creating pinnable images, tracking website traffic from Pinterest, and scheduling pins in advance. Finally, it lists 11 places authors can find free and legal photos to use on their blogs and websites.More from Steph Cliche (20)
Spy pack



Spy packSteph Cliche
Ìę
This document provides instructions for setting up a school spy ring using activities from Tom Palmer's Spy Pack. It includes:
1) Instructions for choosing children to join the spy ring and finding a secret location to brief them.
2) Suggestions for introducing the spy ring concept and testing the children's suitability for the role.
3) A note that establishing rules and identities for the spy ring will help build group identity and secrecy.Sc2014 proceedings



Sc2014 proceedingsSteph Cliche
Ìę
This document provides an overview of the SAT Competition 2014 (SC 2014). SC 2014 consisted of 13 competition tracks to evaluate SAT solvers on various types of benchmarks under different resource constraints. Around 50 solver descriptions and 10 benchmark descriptions were submitted by a total of around 80 contributors. This document compiles all the non-peer-reviewed solver and benchmark descriptions to provide insights into state-of-the-art SAT solving technology in 2014 and serve as a historical reference. Major support for running SC 2014 came from the community and computing resources from the University of Texas at Austin.Satellite hacking



Satellite hackingSteph Cliche
Ìę
The document provides an overview of satellite systems and hacking vulnerabilities. It describes the basic components of satellite systems, including the satellite itself with its payload and bus, as well as tracking, telemetry and control ground stations. It discusses various satellite orbits, frequencies used for transmission, and the structure of very small aperture terminals (VSATs) and other scaled down ground stations. The document notes that while satellite systems have some redundancy to mitigate risks, their design also has elements of simplicity that could enable hacking, such as accessing unencrypted frequencies. However, fully hacking a satellite would require significant technical knowledge and resources.Safes locking device-_mechanical_locks_versus_electronic_locks



Safes locking device-_mechanical_locks_versus_electronic_locksSteph Cliche
Ìę
The document discusses mechanical dial locks versus electronic locks for safes. It recommends either a UL Group II mechanical dial lock or a commercial-grade electronic lock. While electronic locks are more convenient, mechanical dial locks are more durable and reliable long-term. The Sargent & Greenleaf model 6730 dial lock is an industry standard. Cheap imported electronic locks are prone to failures and can be difficult to repair if the lock fails with the door closed. The document advises choosing a UL certified commercial-grade electronic lock from reputable manufacturers if an electronic lock is preferred.Ieee project-2014-2015-context-based-access-control-systems



Ieee project-2014-2015-context-based-access-control-systemsSteph Cliche
Ìę
The document proposes a context-based access control mechanism for Android systems that allows users to set configuration policies controlling applications' access to device resources and services based on context such as location and time. It implements this access control framework on the Android operating system, allowing users to define physical places and link them to logical locations. The access controller then enforces the defined policies by granting or restricting privileges to applications dynamically based on the device's detected context. Experimental results show this mechanism can accurately detect contexts using Wi-Fi signals and effectively enforce access control policies with minimal performance impact.Ieee interference-measurements-802.11n



Ieee interference-measurements-802.11nSteph Cliche
Ìę
The document describes interference measurements taken in an 802.11n wireless mesh network testbed. The testbed uses wireless routers with multiple 802.11n transceivers and directional antennas. Measurements were taken of co-channel interference, signal-to-interference-and-noise ratio (SINR), and TCP/UDP throughput over different channels. Even with very high SINR links of 30-40 dB using MIMO antennas and frame aggregation, the maximum TCP throughput achieved was only 47.85 Mbps, which is significantly lower than the maximum PHY transmission rate of 144 Mbps. The interference measurements from this testbed can help optimize the performance of large-scale 802.11n wirelessGuardi final report



Guardi final reportSteph Cliche
Ìę
This document describes the design and implementation of a Bluetooth communication protocol between an Android mobile device and a microcontroller-powered robotic platform. The author selected the Android operating system and Samsung Galaxy Note II mobile device for development. A Propeller microcontroller, ActivityBot robotic kit, and RN-42 Bluetooth module were used for the robotic platform. The communication protocol and Android/Propeller software were developed to allow control of the robotic platform from the Android application over Bluetooth. Testing demonstrated responsive control of the robot via slider bars in the Android app.718001 000 en



718001 000 enSteph Cliche
Ìę
This document provides instructions for using Televes SAT over IP products, including the SIP-4 and SIP-REC1. It describes:
1. The technical specifications of the SIP-4 and SIP-REC1 units.
2. How to connect the SIP-4 server to a satellite dish and network to stream satellite channels over IP.
3. How to access the SAT-IP stream using a web browser on a PC or apps on tablets to view live TV channels.2010 12-03 a-lawyers_guidetodata



2010 12-03 a-lawyers_guidetodataSteph Cliche
Ìę
The document discusses security risks related to mobile devices used by lawyers and law firms. It notes that hundreds of laptops, storage devices, and handheld devices containing confidential information have been lost or stolen from government agencies in recent years. The document provides guidance on securing documents, passwords, encryption, metadata, and various mobile devices including laptops, USB drives, portable hard drives, phones and PDAs to protect confidential client information that may be stored or transferred using these devices. It emphasizes the importance of training staff, developing computer use policies, and balancing security needs with work demands.Tmplab hostile wrt-5-hacklu



Tmplab hostile wrt-5-hackluSteph Cliche
Ìę
HostileWRT is an OpenWRT-based project that aims to automate wireless network auditing and attacks. It includes scripts to quickly crack WEP networks using aircrack-ng and supports running in access point, client, and monitor modes. Future plans include adding a web UI, improving support for resistant WEP networks, and potentially exploiting WPA networks using the Kalk cryptography tool. The project developers are seeking help from developers, testers, and experts to advance the tool's capabilities and conduct real-world testing.Public wifi



Public wifiSteph Cliche
Ìę
This report summarizes research analyzing vulnerabilities when users connect to unsecured public Wi-Fi networks. The researchers collected data by creating their own rogue access points and monitoring existing public networks. They found over 2500 domains visited by 270 users, with many sites only using HTTPS for login leaving other traffic unencrypted. Successful attacks like traffic monitoring, HTTP request/response modification, and session hijacking were possible. A survey found most users aware of risks but not taking precautions. The researchers conclude that while encryption can help, users also need to be cautious on unsecured networks.

013 50001-001 spy-elite_operators_manual_rev_e



013 50001-001 spy-elite_operators_manual_rev_eSteph Cliche
Ìę
The SPY Elite System is a fluorescence imaging system that allows surgeons to capture and review real-time images of blood flow and tissue perfusion during surgery. It consists of an imaging device and single-use kits containing indocyanine green dye and sterile drapes. Operators must be trained to use the system safely and it requires adherence to warnings and safety procedures regarding the laser, ICG administration, and device operation.Hack.lu 09 ip-morph



Hack.lu 09 ip-morphSteph Cliche
Ìę
This document discusses IpMorph, an open source software project that aims to defeat OS fingerprinting tools by spoofing the OS fingerprint of systems. It provides an overview of OS fingerprinting techniques, the state of spoofing tools at the time of writing, IpMorph's architecture and components, and how it can spoof fingerprints seen by tools like Nmap.12



12Steph Cliche
Ìę
This document proposes two designs for a location-based authentication system for satellite TV to reduce piracy:
1) A lower-cost one-way system where an added decryption module receives an encrypted decryption key from the satellite signal.
2) A higher-cost two-way system requiring the module to also transmit and interact with a third party. Both aim to frequently change decryption keys embedded in signals in a transparent way to users, reducing disruptions compared to current smart card methods. The one-way system has limitations around key updating if messages are missed.09 09 2014



09 09 2014Steph Cliche
Ìę
Home Depot confirmed that its payment systems in Canada and the US were breached, potentially affecting customers who used credit or debit cards between April-September 2014. Experts say the same malware may have been used in other recent retailer breaches like Target and Sally Beauty. Barclays is introducing finger-vein biometrics for internet banking authentication by 2015. A small number of Australians have microchipped themselves for convenience and to be on the cutting edge of technology.7 1-system plus-evolution_spares_eng_6.0



7 1-system plus-evolution_spares_eng_6.0Steph Cliche
Ìę
This document is a spare parts catalogue for Micromed systems. It includes amplifiers, stimulators, interfaces, headbox cables, monitor cables, network components, supports, trolleys and other spare parts. The catalogue is divided into sections for current standard parts and obsolete parts. Current standard parts include items for the SD PLUS, SD LTM EXPRESS, MORPHEUS, MATRIX, MATRIX LIGHT, BRAIN SPY PLUS, ENERGY and PATTERN 10 systems. Obsolete sections cover older headboxes, stimulators, interfaces and accessories no longer in standard production. Micromed operates under ISO quality standards and parts are intended to be compatible replacements for Micromed EEG, EMG, PSG andGlobal maritime-security



Global maritime-securitySteph Cliche
Ìę
This document summarizes a research paper about strategies for gaining state support for global maritime security integration. It discusses two case studies: the Global Maritime Partnership and the Proliferation Security Initiative. The Global Maritime Partnership has been successful by promoting global maritime security without formal structures that could undermine state sovereignty. It leverages economic benefits of secure trade routes. The Proliferation Security Initiative also facilitates global integration by bypassing traditional state partnership mechanisms. Both examples concentrate on cooperative techniques that extend beyond just states to gain broader support for anti-piracy networks.Future war



Future warSteph Cliche
Ìę
This article discusses how future wars may be fought based on the strategic cultures of different actors. It uses a "2x2 matrix" methodology to categorize actors into four strategic cultures - the Bully, the Underdog, the Shape-Shifter, and the Survivor - based on their size and tendency towards warrior ideology or pragmatism. It provides examples of current actors that exhibit characteristics of each strategic culture, and argues that understanding these strategic cultures can provide insight into how future wars may be approached and fought by different actors through 2025.Penetration document format slides
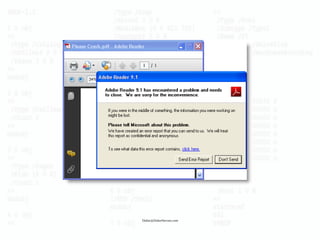
- 6. Didier@DidierStevens.com PDFiD 0.0.9 hello-world.pdf PDF Header: %PDF-1.1 obj 7 endobj 7 stream 1 endstream 1 xref 1 trailer 1 startxref 1 /Page 1 /Encrypt 0 /ObjStm 0 /JS 0 /JavaScript 0 /AA 0 /OpenAction 0 /AcroForm 0 /JBIG2Decode 0 /RichMedia 0 /Colors > 2^24 0 PDFiD
- 20. Didier@DidierStevens.com ⊠Find His Achilles Heel
- 22. Didier@DidierStevens.com Use Restricted Tokens â Windows >= Vista + UAC â DropMyRights â StripMyRights â SAFER SRP
- 23. Didier@DidierStevens.com Restricted Token in Action
- 26. Didier@DidierStevens.com Questions? And hopefully some answers...





