Phishing: Swiming with the sharks
- 1. Phishing: Swimming with the Sharks By Nalneesh Gaur InfoSecurity New York Oct 24, 2006
- 2. Outline What Is Phishing? The Attacks, Lifecycle and Players Trends and Implications Solutions For The Enterprise Solutions For The Individual Resources
- 3. What Is Phishing? Phishing uses both social engineering and technical ploy to steal personal information for financial gain The Antiphising Work Group (APWG) defines it as the use of both social engineering and technical ploy to steal consumers' personal identity data and financial account credentials. Email is the most common channel for attacks. However, attacks via search engines, user forums, Instant Messengers (IM), VOIP, Mobile phones and fake advertisement banners are not uncommon. Six commonly seen attacks follow: Fraudulent Link: WYSINWYG – What You See Is Not What You Get Trojan Crimeware Forms in Email Address Bar Forgery Out-of-band Reply Pharming Technical ploys range from simple to sophisticated
- 4. Example Attacks (Fraudulent Link) The link in the phishing attack will take you to a look-alike site source: The Anti-phishing group
- 5. Example Attacks (Fraudulent Link) Criminals capitalize on global events Global events such as a tsunami, crisis in the middle-east or Michael Jackson trial are all exploited to trick the user into submitting personal information. source: The Anti-phishing group
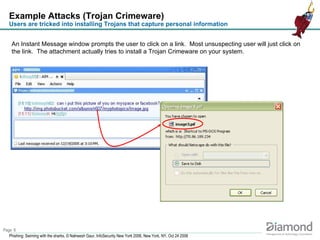
- 6. Example Attacks (Trojan Crimeware) Users are tricked into installing Trojans that capture personal information An Instant Message window prompts the user to click on a link. Most unsuspecting user will just click on the link. The attachment actually tries to install a Trojan Crimeware on your system.
- 7. Example Attacks (Trojan Crimeware) Trojan Crimeware are capable of key stroke and screen capture, redirection, and more This phish is an email purported to be from ebay. When the link in the email is clicked, the website tries to use an Internet Explorer exploit (MHTMLRedir.Exploit) causing Internet Explorer to execute code on your PC without the users permission. In this case, Internet Explorer is used to install a keylogger on your machine. The keylogger is then used to fetch any private information that you may type. This type of attack is detectable by some anti-virus/anti-virus software. source: The Anti-phishing group
- 8. Example Attacks (Forms in Email) HTML enabled emails will deliver the phish within the body of the email The email requests the victim for personal information within the email message itself. source: The Anti-phishing group
- 9. Example Attacks (Address Bar Forgery) Address bar forgery succeeds because it relies on default desktop settings After the initial splash screen the phish proceeds to request personal information. Phished address bar Phished address bar again
- 10. Example Attack (Address Bar Forgery) Address bar forgery will even trick the user who relies on the site address to detect a phish source: The Anti-phishing group The unsuspecting user may not be able to detect that they are dealing with a phish. Address bar forgery again
- 11. An Example Attack (Out-of-band Reply) Even savvy users may be tricked when asked to provide a response over phone The user receives an email requiring them to provide Identity information via phone. The phisher creates a special purpose VoIP phone number along with a PBX system. Dear Customer, We've noticed that you experienced trouble logging into Santa Barbara Bank & Trust Online Banking. After three unsuccessful attempts to access your account, your Santa Barbara Bank & Trust Online Profile has been locked. This has been done to secure your accounts and to protect your private information. Santa Barbara Bank & Trust is committed to make sure that your online transactions are secure. Call this phone number ( 1-805-214-4801 ) to verify your account and your identity. Sincerely, Santa Barbara Bank & Trust Inc. Online Customer Service source: Gary Warner, The Anti-phishing group
- 12. Pharming Pharming attacks are difficult to detect because they target infrastructure elements Attacks the Internet infrastructure elements. Attack involves: Exploiting weakness in the DNS infrastructure (Known since 1998 – InterNic hijacked) Tampering routers (Attacks on the Brazilian ISP, 2003) Replacing/tampering proxy servers Installing Bogus Access points also referred to as evil twins (Wi-phishing) Attacks on end user machines (with malware): Tampering with hosts file Configuring user’s machine to use a rogue proxy server Hooking browser functions (such as, HttpSendRequest on wininet.dll); Unsuspecting user is directed to a fake site because the DNS points to an IP address of a malicious site: DNS: www.somebigbank.com  Actual IP: 192.168.15.2 DNS: www.somebigbank.com  Malicious site IP: 10.15.1.2 Examples of DNS poisoning attacks: 11/04: Google and Amazon users were sent to "Med Network," an online pharmacy. 11/04: The Trojan Banker A/j worm watched for users to visit specific banking sites and then grabbed the personal information. 03/03: Users to Al-Jazeera site was hijacked by a so-called group "Freedom Cyber Force Militia" using DNS poisoning. Al-Jazeera users read a message: "God bless our troops."
- 13. Phishing Attack Lifecycle The crime syndicates are highly organized source: The FSTC Counter-phishing solution survey The phishers distribute automated tools and kits over the Internet to speed up each step in the lifecycle.
- 14. Phishing Kits Phishing kits contain the necessary content to launch a phishing attack Phishing kits are easily available on the Internet for as little as $150. The particular phishing kit shown below can be used to target up to 20 institutions.
- 15. Trojan Crimeware Kits Crimeware kits distribute and administer Trojans and collect personal information. Source: Enrique Gonzalez, Panda Software
- 16. Crimeware Tools Crimeware tools are sophisticated and easy to use
- 17. Crimeware is for Real Sophisticated screen scrappers bypass anti-keylogging mechanisms Source: Hispasec Sistemas/virustotal.com
- 18. Crimeware Evades Detection Anti-Virus tools are unable to detect Crimeware Trojans
- 19. After The Phish Phishers use the captured information for money laundering and to commit financial fraud Examples of how criminal’s use stolen information: Contact victim’s credit card issuer and change mailing address. Requesting additional credit/debit cards, and new PIN to facilitate cash advance fraud. Obtain new credit cards, using victim’s name, date of birth and SSN, but some other mailing address. Maximizing credit card limits. Establishing phone or wireless service in victim’s name. Opening a bank account in victim’s name Filing for bankruptcy using victim’s name to avoid paying debts incurred in your name or to avoid eviction. Counterfeiting checks or debit cards to drain victim’s bank account. Purchasing automobiles, boats etc. through loans obtained using victim’s personal information. Giving victim’s name to the police during an arrest. Credit Cards/ Personal Information Carders Phishing Mules e b a y Paypal Financial Gain Money Laundering Carders and Phishing Mules are the means to commit financial fraud.
- 20. The Carders The Carders trade or deal in stolen credit card information Carders are sophisticated and organized and they use automation (using bots) and specialized IRC channels and related web sites to exchange information. A command language is utilized to access the bots database. The bot simply listens on the IRC channel and responds to issued commands. Channel participants often use open proxies/compromised hosts to obfuscate themselves. Bulk of the activity seems to originate from South Asia, former Eastern block and the PacRim. They Recruit other Carders Sample of command sets carders use: !cc Obtains a credit card number from a database !cclimit card_number Determines the available credit !chk card_number Checks a credit card for validity. Example IRC transaction (Source: Project Honeynet) #MasterCcs 10:00:49 newbie: what i have to type to get cc info ? #MasterCcs 10:01:15 helper: type !cc #MasterCcs 10:04:04 newbie: !cc #MasterCcs 10:05:33 Ccs`: newbie!cc Name: Yukio XXXXXXXX |Address: X-X-X-XXX |City: Koduru-shi |State: Tokyo |Zip: XXX-XXXX |Phone: N |Country: Japan |CardType: American Express |Card Number: XXXXXXXXXXXXXXX XXXX
- 21. Forging a magnetic card is easy The equipment and card stock to forge magnetic cards can be obtained for under $1000 Track one is 210 bits per inch (bpi), and holds 79 6-bit plus parity bit read-only characters. Track two is 75 bpi, and holds 40 4-bit plus parity bit characters. Track three is 210 bpi, and holds 107 4-bit plus parity bit characters. Stripe Snoop is an open source suite of tools tools that captures, modifies, validates, generates, analyzes, and shares data from magstripe cards. The perpetrator can then modify Track1 & 2 information to suite their needs. Note: PIN Offset ≠PIN, CVV ≠CVV2 With ATM and PIN debit fraud criminals can immediately get their hands on cash. Often, financial institutions are not validating Track 2 security data while authorizing ATM and PIN debit transactions. PIN Offsets needs to be re-recorded on the magnetic strip each time the PIN is changed, CVV can be brute forced. Track 1: Primary account number Name Expiration date Discretionary data 1 Track 3: (not standardized) Encrypted PIN Amount Authorized 3 Track 2: Primary account number Expiration date PIN Offset and CVV code (ATM/Debit cards) 2
- 22. Phishing Mules Phishers recruits “mules” to launder money using a ploy Thousands of Australians were lured into a training program with Credit Suisse With promise of a career opportunity. Once hooked the mules were asked to transfer money as part of the training exercise. A very convincing URL is used for the site located at: http://credit-suisse-group.de/ en/application_form.html Viagra, Rolex Watches, and Work from home offers are other means that phishers use to lure unsuspecting users. All accounts are useful: Lots of Money – Spend it, No Money – Use it for laundering, Good Credit – New Accounts
- 23. Trends – Rise in Crimeware Financial Institutions are clearly the target and use of crimeware is increasing source: The Anti-phishing group
- 24. Trends and Implications Crimeware will improve in sophistication and increasingly exploit new vulnerabilities. Trends Financial institution will continue to be top targets. Phishing attacks will increasingly victimize the identity of small to medium size institutions and their clients. Phishing attacks and other frauds will continue to exploit global events such as tsunami’s and holidays. According to Louis M. Reigel, assistant director for the FBI, there were roughly 2,300 Katrina-related Web sites identified as of September 1st, only three days after the hurricane hit. Of the 800 Web sites that the FBI investigated, 60% were presumed to be fraudulent. Phishers will use multiple channels to solicit and collect Phishing responses. Crimeware will get more sophisticated and its distribution more aggressive. Implications Medium and Small size institutions will collaborate to address the threat of phishing. Regulations targeting Identity theft will be signed into law. Site takedown services will likely be the only direct response for many organizations in response to a phish. Browsers will detect phishing with increased sophistication. Institutions will increasingly encourage their clients, via various means, to actively protect their own end points (their PC's), via anti-virus, anti-spyware, OS patching, and firewalls.
- 25. Enterprise Preventative Measures Strong Authentication will defeat credential capture Address the inherent problem of reusable passwords Use of two-factor authentication and/or user X509 certificates helps address the problem Use of two-step authentication Use of anti key-logging mechanism Currently used by: AOL HSBC Bank of America – 13.2 Million customers Stanford Federal Credit Union Pros: Replay attacks fail Cons: Large scale deployment is a challenge
- 26. Enterprise Preventative Measures Digitally Signed Email authenticate the sender Uses industry standard such as S/MIME (supported by MS Outlook, Notes, etc). Provides assurance that the “From:” address is not spoofed. Addresses spam issue and provides a trail to phisher. Signing email at the email gateways will allow for faster adoption rather than making every individual user sign outgoing email. Pros: Legitimacy of email is verified Cons: Suffers from SSL pad lock syndrome
- 27. Enterprise Preventative Measures Sender Email Server Authentication ensures that email sender is verified A number of proposed systems have surfaced for validating a sender's email. These include: SPF (Sender Permitted From), Microsoft's SenderID, and Yahoo’s Domain Keys. All of these determine whether email from a particular domain is permitted to originate from a particular IP address. This primarily addresses the spam issue but does not prevent a spammer from registering their own domain. Pros: Largely addresses spam Cons: Not all spam or phishing is addressed
- 28. Enterprise Preventative Measures Improving user awareness is effective when done properly but should not be the only solution Companies can provide their customer/employees with information on how to prevent phishing attacks. For internal communication consider a combination of the following: Internal Security Web Site Internal Blog Mandatory Security Training Annual Security Forum/Days Phishing/Pharming Quiz Computer Security Day Most successful when communication is frequent and uses a variety of different mediums (email, web, post card) Pros: Most effective for those who get it Cons: Time consuming
- 29. Enterprise Preventative Measures Use of personalization features act as a shared secret between the user and the Institution Provides a clue to users by means of colors, sounds, images, and captchas. Use of themes and colors are effective with users who are not well versed with the details of Internet security. Authentication usually involves two steps: 1 st step: Username: Image 2 nd Step: Password: Authenticated Pros: Intuitive to users Cons: User may not use personalization features unless forced upon them
- 30. Enterprise Preventative Measures Improving web application security will minimize the exposures available to phishers Perform content validation to address cross-site scripting issues. Careful handling of session information is critical. e.g. http://www.safebank.com?SESSIONID=SWDESWE234SWED Expire session ID’s No Recycled session ID’s Avoid URL based session ID’s Differentiate between HTTP and HTTPS session ID’s Perform URL validation to prevent phisher from supplying malicious URL’s. e.g. http://www.safebank.com?URL=my.safebank.com Pros: Keeps control on the server side Cons: Requires preiodic review and modification
- 31. Enterprise Preventative Measures Maintaining consistent URL’s will help users who rely on them to detect phish Do not use tiny URL’s. e.g. http://www.informationsecuritymagazine.com/bigurl?name=test becomes http://tinyurl.com/4ebo5 Use one domain for all customer communication. Pros: Simple and good for brand identity Cons: May require application modification
- 32. Enterprise Preventative Measures Improving Infrastructure security will thwart pharming attacks Establish Minimum Security Baseline standards for routers and firewalls (see http://www.cisecurity.org) Although obvious - Patch management, Anti-spam, Anti-Spyware and Anti-virus software must be implemented and updated. Proactively register related Internet Domains. Upgrade DNS Servers to BIND 9. Address DNS Cache poisoning: Configure DNS servers to reject spurious additional records - If query is for www.example.com, only accept records for the example.com domain. Reject additional record for any other domain such as www.somebigbank.com. (see http://www.dnssec.net).
- 33. Enterprise Detective/Corrective Measures A holistic solution should incorporate detective and corrective features Detective Follow domain registrations closely Active web monitoring Honeypots and Anti-Spam solutions can be used to detect phishing attempts Corrective Phish take down services Victim rehabilitation Forensics Lessons learned/Review
- 34. Solution Categories Approximately 200 vendors seek to provide solution to phishing Vendors Matrix for each category available at the Antiphishing members only site - https://antiphishing.kavi.com/members, Solution Evaluation/Trial group
- 35. Solutions For The Individual The individual user needs to be vigilant and exercise caution Use security best practices for workstations and application E.g. Patch frequently, Use strong passwords Individuals need to modify their behavior Use a different web browser Assess user rights Where available, use site personalization features Deploy browser based plug in solution to detect phishing attacks Understand how your on-line account information is updated Create unique passwords for each site Add a fraud alert to your credit history Report Phishing Attack attempts to spam@uce.gov Report Phishing Attacks that succeeded. Call 1-877-ID-THEFT
- 36. The Statistics Verisign’s iDefense found that the number of keyloggers unleashed by hackers increased this year by 65 percent in 2005. A recent study by Forrestor found that some 600,000 of the UK’s 15 million internet banking customers have turned away from online financial transactions because of concerns about keystroke logging software and phishing emails A recent study by IDG of 1500 respondents found that 49%, couldn't identify "phishing" scam e-mail messages Phishing is one of the Top 10 list of Internet frauds, ranking as much of a problem for the vulnerable as Nigerian bank frauds, according to the National Consumers League. A recent study by TowerGroup claimed that the value of potential fraud losses from phishing will total just $137.1 million globally in 2004. A Gartner study estimated that 30 million Americans have received a phishing attack, and about 3% (1.78 million) submitted personal and/or financial information. In another study, Gartner believes that phishing will inhibit ecommerce growth rates by 1-3%. An APWG study released in 07/06 noted 23,670 phishing email messages reported. Decrease in traditional phishing sites but increase in crimeware. A few other highlights: Number of brands hijacked by phishing campaign in July: 154 Average lifespan of a phishing site in July: 4.8 days Longest time online for site: 31 days US leads with number of hosted phish sites (27.9%), followed by China (12%), Korea (10%), France, Australia, and Germany Financial Services (93.5%), followed by ISP’s, and retailers tend to be the most targeted Industry sectors A study conducted by the Ponemon Institute revealed that Phishing could cost consumers $500 million this year. The same study also found that 70% of the its surveyed users have unintentionally visited a spoofed Web site, and more than 15% admit to revealing sensitive personal information in the process. (November 2004)
- 37. Resources http://www.antiphishing.org: This is the Anti-Phishing Workgroup site - A professional working group dedicated to understanding and eradicating online identity theft http://www.ic3.gov: This is the Internet Crime Complaint Center site. http://www.fraudwatchinternational.com/internetfraud/phishing/email.htm: This is an Australian Web site to combat not just phishing but in general Internet Fraud. http://www.ifccfbi.gov: FBI - Internet Fraud Complaint Centre http://survey.mailfrontier.com/survey/quiztest.html: This site contains a phishing quiz that tests awareness. http://www.bbbonline.org/idtheft/safetyQuiz: ID Theft Quiz from Better Busines Bureau http://www.pc-help.org/obscure.htm: Site shows how to obscure a URL. http://www.ftc.gov/bcp/conline/pubs/alerts/phishingalrt.htm: This is the site that provides consumer advise on “How to Not get hooked by a phishing scam” http://www.consumer.gov/idtheft: The FTC Web site on consumer ID theft. http://fstc.org/projects/FSTC_Phishing_Prospectus_Final.pdf: The Financial Services Technology Consortium effort to address the problem off phishing. http://www.microsoft.com/senderid: The sender ID framework. http://www.ietf.org/internet-drafts/draft-danisch-dns-rr-smtp-03.txt: The Reverse Mail Exchanger (RMX) specification. http://spf.pobox.com: The Sender Permitted From (SPF) specification.
- 38. Resources Cont. http://onguardonline.gov: Federal Government site for phishing awareness. http://secunia.com/multiple_browsers_frame_injection_vulnerability_test: This site contains a demonstration of the Frame Injection vulnerability. http://www.occ.treas.gov/consumer/PhishBrochFINAL-SCREEN.pdf: Phishing prevention tips brochure http://www.identity-theft.org.uk: UK Government website on Identity theft. http://www.phishreport.net: Microsoft/eBay/VISA Antiphishing aggregation service http://www.phishinginfo.org: The National Consumer League’s informational site on phishing. http://www.netcraft.com: Anti-phishing tool bar for Internet Explorer and Firefox http://www.trustedsource.org: Spam data mining portal. http://www.digitalphishnet.org: joint enforcement initiative between industry and law enforcement http://crypto.stanford.edu/PwdHash: The Stanford University unique passwords via password hashing solution. http://www.contentverification.com/attacks.html: Phisihing attack demonstrations.