iOS (Vulner)ability
- 1. iOS (Vulner)ability Subho Halder Co Founder AppKnox
- 3. ./WhoAmI Co Founder of AppKnox ( XYSec Labs ) Python Lover Sole Creator and Developer of Android Framework for Exploitation (AFE) Found Security Bugs in Apple, Google, Skype, Webkit, Facebook, Microsoft, âĶ..
- 5. NSLog [@âAgendaâ]; Quick overview of iPhone iOS Platform. iOS Security Structure What is a Jailbreak? iOS App (IN)Securities
- 6. Peek into a state-of-art Prison
- 7. iOS Hardware Architecture Application Processor Baseband iOS User interaction Applications ... NucleusOS Radio communication
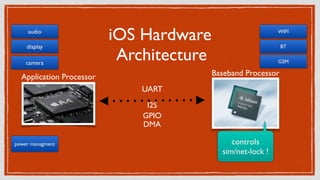
- 8. iOS Hardware Architecture Application Processor Baseband Processor audio display power managment camera WIFI BT GSM UART I2SâĻ GPIOâĻ DMAâĻ controls sim/net-lock !
- 10. ***[Sandboxing]*** NAND Flash FTL: converts logical partition to NAND ïŽash architecture looks like BLOCK device System Partition / (Read Only) User Partition /private/var NAND FTL Block Device / (RO)âĻ (System Partition) /private/var (RW)âĻ (User Partition)
- 11. ***[Sandboxing]*** 3rd Party lives only on User Partition Apps run as mobile user Kernel Signature checks executables âĻ in system-call execve() %{ How did you Jailbreak it? }% NAND FTL Block Device / (RO)âĻ (System Partition) /private/var (RW)âĻ (User Partition)
- 12. **Memory Protection W^X Policy Non Executable Stack or Heap ASLR (Address Space Layout Randomisation) %{ Did you forget about Return-Oriented-Program }%
- 13. Code Signing Implemented inside Kernel Kernel signature checks executables in systemcall execve() Kernel stored on System Partition (kernelcache) Kernel is signature checked before being loaded. %{ Can still be by-passed :/ }%
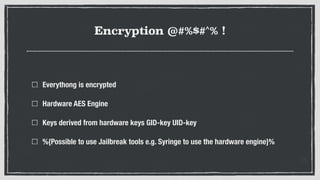
- 14. Encryption @#%$#^% ! Everythong is encrypted Hardware AES Engine Keys derived from hardware keys GID-key UID-key %{Possible to use Jailbreak tools e.g. Syringe to use the hardware engine}%
- 15. What is J@!lbr3@k ?
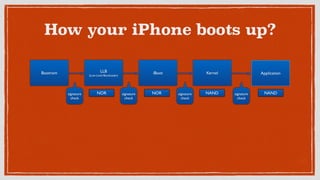
- 16. How your iPhone boots up? signature check signature check signature check signature check Bootrom LLB (Low Level Bootloader) iBoot Kernel Application NOR NOR NAND NAND
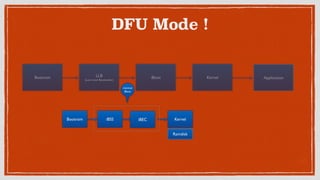
- 18. DFU Mode ! Bootrom iBSS iBEC Kernel Ramdisk Bootrom LLB (Low Level Bootloader) iBoot Kernel Application minimalâĻ iBoot
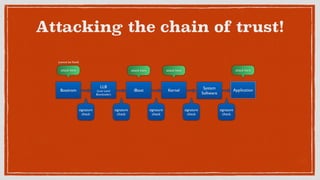
- 19. Attacking the chain of trust! signature check Bootrom LLB (Low Level Bootloader) iBoot Kernel Application signature check signature check signature check signature check attack here (cannot be ïŽxed) attack here attack here attack here System Software
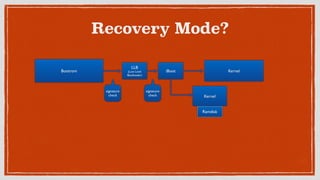
- 20. Where do we go wrong?
- 21. Plists Used by iPhone to store saved properties and data XML Binary (compressed XML) (depreciated) The binary plists need converting, you can use: plutil to convert to XML Property List Editor (in XCode) plists contain all kinds of juicy information. Check for: Cookies, emails, usernames, passwords, sensitive application data, client side role identiïŽers, protocol handlers, etc.
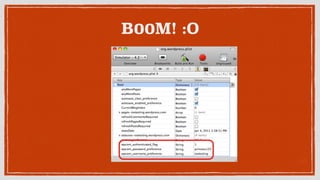
- 22. B00M! :O
- 23. INSERT into `SQLite` A lot of iOS applications sensitive data in SQLite3 databases on the device. Sqlite3 does not have built-in support for encryption. There are extensions (CEROD is one, sqlcipher is another) that support encryption, but the code is not publicly available, you need to license it. Apple has not, so the included version of sqlite3 does not support encrypted databases. Still dangerous to store stuff client side. To bypass: Cerod is as simple as looking for âcerod:passwdâ or break pointing and pulling out of memory: sqlite3_open(":cerod:passwd:ïŽlename.db", &db);
- 24. )()()( Keychains )()()( Keychain = Encrypted container for storing sensitive information Smarter devs store passwords and sensitive data using the keychain. Unfortunately with access to a phone and jailbreaking we can decrypt the keychain and dump the contents.
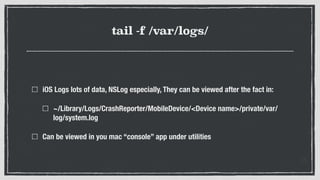
- 25. tail -f /var/logs/ iOS Logs lots of data, NSLog especially, They can be viewed after the fact in: ~/Library/Logs/CrashReporter/MobileDevice/<Device name>/private/var/ log/system.log Can be viewed in you mac âconsoleâ app under utilities
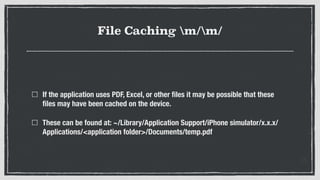
- 26. File Caching m/m/ If the application uses PDF, Excel, or other ïŽles it may be possible that these ïŽles may have been cached on the device. These can be found at: ~/Library/Application Support/iPhone simulator/x.x.x/ Applications/<application folder>/Documents/temp.pdf
- 27. $(`Keyboard Caching`) Keystrokes for predictive spellcheck are stored in: ~/Library/Application Support/iPhone Simulator/x.x.x/Library/Keyboard/ dynamic-text.dat This issue is similar to autocomplete for web browsers. Already disabled for password ïŽelds Should be disabled for any potentially sensitive ïŽelds (account numbers, SSN, etc, etcâĶ) Set UITextField property autocorrectionType = UITextAutocorrectionNo for mitigation.
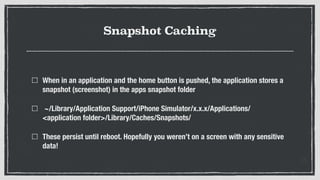
- 28. Snapshot Caching When in an application and the home button is pushed, the application stores a snapshot (screenshot) in the apps snapshot folder ~/Library/Application Support/iPhone Simulator/x.x.x/Applications/ <application folder>/Library/Caches/Snapshots/ These persist until reboot. Hopefully you werenât on a screen with any sensitive data!
- 29. Snapshot Caching
- 30. SQL Injection Client-Side SQL injection is a problem on the client side too! BAD: NSString *sql = [NSString stringWithFormat:@"SELECT name FROM products WHERE id = '%@'", id]; const char *query = [sql UTF8String]; GOOD: const char *sql = "SELECT name FROM products WHERE id = ?"; sqlite3_prepare_v2(database, sql, -1, &sql_statement, NULL); sqlite3_bind_text(&sql_statement, 1, id, -1, SQLITE_TRANSIENT);
- 31. XSS Client-Side Can occur whenever user controlled Objective C variables populated in to WebView stringByEvaluatingJavaScriptFromString âĻ âĻ NSString *javascript = [[NSString alloc] initWithFormat:@"var myvar="%@";", username]; âĻ [mywebView stringByEvaluatingJavaScriptFromString:javascript];
- 32. Vulnerable Obj-C Methods NSLog() [NSString stringWithFormat:] [NSString initWithFormat:] [NSMutableString appendFormat:] [NSAlert informativeTextWithFormat:] [NSPredicate predicateWithFormat:] [NSException format:] NSRunAlertPanel
- 33. How can you get started? https://www.owasp.org/index.php/OWASP_iGoat_Project
- 34. AppKnox - Cloud Based Security Automation Tool
- 35. Available for Android Coming soon for iOS
- 36. âCicero âThere is no castle so strong that it cannot be overthrownâ





![NSLog [@âAgendaâ];
Quick overview of iPhone iOS Platform.
iOS Security Structure
What is a Jailbreak?
iOS App (IN)Securities](https://image.slidesharecdn.com/pluggedin71-140612041433-phpapp02/85/iOS-Vulner-ability-5-320.jpg)



![***[Sandboxing]***
NAND Flash
FTL: converts logical partition to NAND ïŽash architecture
looks like BLOCK device
System Partition / (Read Only)
User Partition /private/var
NAND
FTL
Block Device
/ (RO)âĻ
(System Partition)
/private/var (RW)âĻ
(User Partition)](https://image.slidesharecdn.com/pluggedin71-140612041433-phpapp02/85/iOS-Vulner-ability-10-320.jpg)
![***[Sandboxing]***
3rd Party lives only on User Partition
Apps run as mobile user
Kernel Signature checks executables âĻ
in system-call execve()
%{ How did you Jailbreak it? }%
NAND
FTL
Block Device
/ (RO)âĻ
(System Partition)
/private/var (RW)âĻ
(User Partition)](https://image.slidesharecdn.com/pluggedin71-140612041433-phpapp02/85/iOS-Vulner-ability-11-320.jpg)









![SQL Injection Client-Side
SQL injection is a problem on the client side too!
BAD:
NSString *sql = [NSString stringWithFormat:@"SELECT name FROM products
WHERE id = '%@'", id]; const char *query = [sql UTF8String];
GOOD:
const char *sql = "SELECT name FROM products WHERE id = ?";
sqlite3_prepare_v2(database, sql, -1, &sql_statement, NULL);
sqlite3_bind_text(&sql_statement, 1, id, -1, SQLITE_TRANSIENT);](https://image.slidesharecdn.com/pluggedin71-140612041433-phpapp02/85/iOS-Vulner-ability-30-320.jpg)
![XSS Client-Side
Can occur whenever user controlled Objective C variables populated in to
WebView
stringByEvaluatingJavaScriptFromString âĻ
âĻ
NSString *javascript = [[NSString alloc] initWithFormat:@"var myvar="%@";",
username]; âĻ
[mywebView stringByEvaluatingJavaScriptFromString:javascript];](https://image.slidesharecdn.com/pluggedin71-140612041433-phpapp02/85/iOS-Vulner-ability-31-320.jpg)
![Vulnerable Obj-C Methods
NSLog()
[NSString stringWithFormat:]
[NSString initWithFormat:]
[NSMutableString appendFormat:]
[NSAlert informativeTextWithFormat:]
[NSPredicate predicateWithFormat:]
[NSException format:]
NSRunAlertPanel](https://image.slidesharecdn.com/pluggedin71-140612041433-phpapp02/85/iOS-Vulner-ability-32-320.jpg)