Citrix Mobile Work Space
- 1. 14 Citrix. Confidential. мӢңл„Ҳм§Җ 2014 лЎңмҠӨм•Өм Өл ҲмҠӨ
- 4. 14 Citrix. Confidential. лӘЁл°”мқјлӘЁл°”мқјлӘЁл°”мқјлӘЁл°”мқј мӣҢнҒ¬мҠӨнҺҳмқҙмӣҢнҒ¬мҠӨнҺҳмқҙмӣҢнҒ¬мҠӨнҺҳмқҙмӣҢнҒ¬мҠӨнҺҳмқҙмҠӨмҠӨмҠӨмҠӨ м•ұ, лҚ°мқҙн„°, м„ң비мҠӨлҘј лӘЁл“ кё°кё°, лӘЁл“ л„ӨнҠёмӣҢнҒ¬ л°Ҹ нҒҙлқјмҡ°л“ңлҘј нҶөн•ҙ м•Ҳм „н•ҳкІҢ нҶөн•©
- 5. 14 Citrix. Confidential. лӘЁл°”мқјлӘЁл°”мқјлӘЁл°”мқјлӘЁл°”мқј мӣҢнҒ¬мҠӨнҺҳмқҙмҠӨмқҳмӣҢнҒ¬мҠӨнҺҳмқҙмҠӨмқҳмӣҢнҒ¬мҠӨнҺҳмқҙмҠӨмқҳмӣҢнҒ¬мҠӨнҺҳмқҙмҠӨмқҳ лҰ¬лҚ”мһ…лӢҲлӢӨлҰ¬лҚ”мһ…лӢҲлӢӨлҰ¬лҚ”мһ…лӢҲлӢӨлҰ¬лҚ”мһ…лӢҲлӢӨ. мӢңнҠёлҰӯмҠӨлҠ”
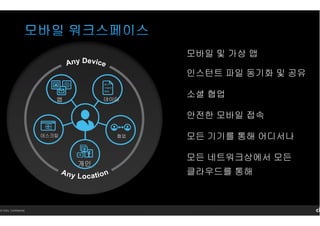
- 6. 14 Citrix. Confidential. лӘЁл°”мқј л°Ҹ к°ҖмғҒ м•ұ мқёмҠӨн„ҙнҠё нҢҢмқј лҸҷкё°нҷ” л°Ҹ кіөмң мҶҢм…ң нҳ‘м—… м•Ҳм „н•ң лӘЁл°”мқј м ‘мҶҚ лӘЁл“ кё°кё°лҘј нҶөн•ҙ м–ҙл””м„ңлӮҳ лӘЁл“ л„ӨнҠёмӣҢнҒ¬мғҒм—җм„ң лӘЁл“ нҒҙлқјмҡ°л“ңлҘј нҶөн•ҙ лҚ°мқҙн„° лҚ°мҠӨнҒ¬нғ‘ нҳ‘м—… м•ұ к°ңмқё
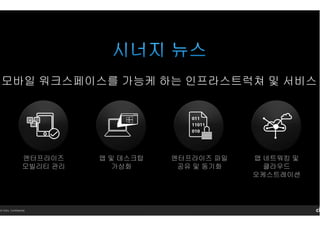
- 7. 14 Citrix. Confidential. м—”н„°н”„лқјмқҙмҰҲ нҢҢмқј кіөмң л°Ҹ лҸҷкё°нҷ” м•ұ л„ӨнҠёмӣҢнӮ№ л°Ҹ нҒҙлқјмҡ°л“ң мҳӨмјҖмҠӨнҠёл Ҳмқҙм…ҳ м—”н„°н”„лқјмқҙмҰҲ лӘЁл№ҢлҰ¬нӢ° кҙҖлҰ¬ м•ұ л°Ҹ лҚ°мҠӨнҒ¬нғ‘ к°ҖмғҒнҷ” лӘЁл°”мқј мӣҢнҒ¬мҠӨнҺҳмқҙмҠӨлҘј к°ҖлҠҘмјҖ н•ҳлҠ” мқён”„лқјмҠӨнҠёлҹӯміҗ л°Ҹ м„ң비мҠӨ
- 8. 14 Citrix. Confidential. м—”н„°н”„лқјмқҙмҰҲ нҢҢмқј лҸҷкё°нҷ” л°Ҹ кіөмң м•ұ л„ӨнҠёмӣҢнӮ№ л°Ҹ нҒҙлқјмҡ°л“ң мҳӨмјҖмҠӨнҠёл Ҳмқҙм…ҳ м—”н„°н”„лқјмқҙмҰҲм—”н„°н”„лқјмқҙмҰҲм—”н„°н”„лқјмқҙмҰҲм—”н„°н”„лқјмқҙмҰҲ лӘЁл№ҢлҰ¬нӢ°лӘЁл№ҢлҰ¬нӢ°лӘЁл№ҢлҰ¬нӢ°лӘЁл№ҢлҰ¬нӢ° кҙҖкҙҖкҙҖкҙҖлҰ¬лҰ¬лҰ¬лҰ¬ м•ұ л°Ҹ лҚ°мҠӨнҒ¬нғ‘ к°ҖмғҒнҷ” лӘЁл°”мқј мӣҢнҒ¬мҠӨнҺҳмқҙмҠӨлҘј к°ҖлҠҘмјҖ н•ҳлҠ” мқён”„лқјмҠӨнҠёлҹӯміҗ л°Ҹ м„ң비мҠӨ
- 10. 14 Citrix. Confidential. м—”н„°н”„лқјмқҙмҰҲ нҢҢмқј лҸҷкё°нҷ” л°Ҹ кіөмң м•ұ л„ӨнҠёмӣҢнӮ№ л°Ҹ нҒҙлқјмҡ°л“ң мҳӨмјҖмҠӨнҠёл Ҳмқҙм…ҳ м—”н„°н”„лқјмқҙмҰҲ лӘЁл№ҢлҰ¬нӢ° мҡҙмҳҒ м•ұм•ұм•ұм•ұ л°Ҹл°Ҹл°Ҹл°Ҹ лҚ°мҠӨнҒ¬нғ‘лҚ°мҠӨнҒ¬нғ‘лҚ°мҠӨнҒ¬нғ‘лҚ°мҠӨнҒ¬нғ‘ к°ҖмғҒнҷ”к°ҖмғҒнҷ”к°ҖмғҒнҷ”к°ҖмғҒнҷ” лӘЁл°”мқј мӣҢнҒ¬ мҠӨнҺҳмқҙмҠӨлҘј к°ҖлҠҘмјҖ н•ҳлҠ” мқён”„лқјмҠӨнҠёлҹӯміҗ л°Ҹ м„ң비мҠӨ
- 12. 14 Citrix. Confidential. н•ҳмқҙлёҢлҰ¬л“ңн•ҳмқҙлёҢлҰ¬л“ңн•ҳмқҙлёҢлҰ¬л“ңн•ҳмқҙлёҢлҰ¬л“ң нҒҙлқјмҡ°л“ңнҒҙлқјмҡ°л“ңнҒҙлқјмҡ°л“ңнҒҙлқјмҡ°л“ң н”„лЎң비м ҖлӢқн”„лЎң비м ҖлӢқн”„лЎң비м ҖлӢқн”„лЎң비м ҖлӢқ н”ҢлһҳнӢ°л„ҳн”ҢлһҳнӢ°л„ҳн”ҢлһҳнӢ°л„ҳн”ҢлһҳнӢ°л„ҳ лӘЁл№ҢлҰ¬нӢ°лӘЁл№ҢлҰ¬нӢ°лӘЁл№ҢлҰ¬нӢ°лӘЁл№ҢлҰ¬нӢ° н”„лЎңлӘЁм…ҳн”„лЎңлӘЁм…ҳн”„лЎңлӘЁм…ҳн”„лЎңлӘЁм…ҳ AppDNA л§Ҳмқҙк·ёл Ҳмқҙм…ҳл§Ҳмқҙк·ёл Ҳмқҙм…ҳл§Ҳмқҙк·ёл Ҳмқҙм…ҳл§Ҳмқҙк·ёл Ҳмқҙм…ҳ нҲҙнӮ·нҲҙнӮ·нҲҙнӮ·нҲҙнӮ· HDX лӘЁл°”мқјлӘЁл°”мқјлӘЁл°”мқјлӘЁл°”мқј мөңм Ғнҷ”мөңм Ғнҷ”мөңм Ғнҷ”мөңм Ғнҷ” кё°мҲ кё°мҲ кё°мҲ кё°мҲ к°„лӢЁн•ңк°„лӢЁн•ңк°„лӢЁн•ңк°„лӢЁн•ң м„Өм№ҳм„Өм№ҳм„Өм№ҳм„Өм№ҳ л°Ҹл°Ҹл°Ҹл°Ҹ мҡҙмҳҒмҡҙмҳҒмҡҙмҳҒмҡҙмҳҒ
- 13. 14 Citrix. Confidential. XenDesktop 7.5 м—…лҚ°мқҙнҠё *л§Ҙмҡ©л§Ҙмҡ©л§Ҙмҡ©л§Ҙмҡ© лҚ°мҠӨнҒ¬нғ‘лҚ°мҠӨнҒ¬нғ‘лҚ°мҠӨнҒ¬нғ‘лҚ°мҠӨнҒ¬нғ‘ н”Ңл Ҳмқҙм–ҙн”Ңл Ҳмқҙм–ҙн”Ңл Ҳмқҙм–ҙн”Ңл Ҳмқҙм–ҙ н”ҢлһҳнӢ°л„ҳн”ҢлһҳнӢ°л„ҳн”ҢлһҳнӢ°л„ҳн”ҢлһҳнӢ°л„ҳ лӘЁл№ҢлҰ¬нӢ°лӘЁл№ҢлҰ¬нӢ°лӘЁл№ҢлҰ¬нӢ°лӘЁл№ҢлҰ¬нӢ° н”„лЎңлӘЁм…ҳн”„лЎңлӘЁм…ҳн”„лЎңлӘЁм…ҳн”„лЎңлӘЁм…ҳ AppDNA л§Ҳмқҙк·ёл Ҳмқҙм…ҳл§Ҳмқҙк·ёл Ҳмқҙм…ҳл§Ҳмқҙк·ёл Ҳмқҙм…ҳл§Ҳмқҙк·ёл Ҳмқҙм…ҳ нҲҙнӮ·нҲҙнӮ·нҲҙнӮ·нҲҙнӮ· мӣҗкІ©мӣҗкІ©мӣҗкІ©мӣҗкІ© PC Wake-on-LAN н•ҳмқҙлёҢлҰ¬л“ңн•ҳмқҙлёҢлҰ¬л“ңн•ҳмқҙлёҢлҰ¬л“ңн•ҳмқҙлёҢлҰ¬л“ң нҒҙлқјмҡ°л“ңнҒҙлқјмҡ°л“ңнҒҙлқјмҡ°л“ңнҒҙлқјмҡ°л“ң н”„лЎң비м ҖлӢқн”„лЎң비м ҖлӢқн”„лЎң비м ҖлӢқн”„лЎң비м ҖлӢқ
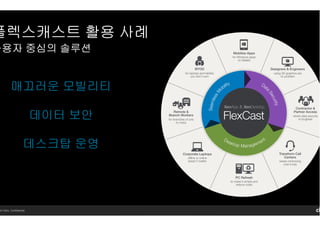
- 14. 14 Citrix. Confidential. н”Ңл үмҠӨмәҗмҠӨнҠён”Ңл үмҠӨмәҗмҠӨнҠён”Ңл үмҠӨмәҗмҠӨнҠён”Ңл үмҠӨмәҗмҠӨнҠё нҷңмҡ©нҷңмҡ©нҷңмҡ©нҷңмҡ© мӮ¬лЎҖмӮ¬лЎҖмӮ¬лЎҖмӮ¬лЎҖ мӮ¬мҡ©мһҗмӮ¬мҡ©мһҗмӮ¬мҡ©мһҗмӮ¬мҡ©мһҗ мӨ‘мӢ¬мқҳмӨ‘мӢ¬мқҳмӨ‘мӢ¬мқҳмӨ‘мӢ¬мқҳ мҶ”лЈЁм…ҳмҶ”лЈЁм…ҳмҶ”лЈЁм…ҳмҶ”лЈЁм…ҳ л§ӨлҒ„лҹ¬мҡҙ лӘЁл№ҢлҰ¬нӢ° лҚ°мқҙн„° ліҙм•Ҳ лҚ°мҠӨнҒ¬нғ‘ мҡҙмҳҒ
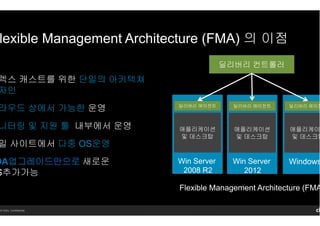
- 15. 14 Citrix. Confidential. lexible Management Architecture (FMA) мқҳ мқҙм җ л”ңлҰ¬лІ„лҰ¬ м»ЁнҠёлЎӨлҹ¬ Win Server 2008 R2 м• н”ҢлҰ¬мјҖмқҙм…ҳ л°Ҹ лҚ°мҠӨнҒ¬нғ‘ л”ңлҰ¬лІ„лҰ¬ м—җмқҙм „нҠё Win Server 2012 м• н”ҢлҰ¬мјҖмқҙм…ҳ л°Ҹ лҚ°мҠӨнҒ¬нғ‘ л”ңлҰ¬лІ„лҰ¬ м—җмқҙм „нҠё Windows м• н”ҢлҰ¬мјҖмқҙ л°Ҹ лҚ°мҠӨнҒ¬нғ‘ л”ңлҰ¬лІ„лҰ¬ м—җмқҙм „ Flexible Management Architecture (FMA л үмҠӨ мәҗмҠӨнҠёлҘј мң„н•ң лӢЁмқјмқҳ м•„нӮӨн…Қміҗ мһҗмқё лқјмҡ°л“ң мғҒм—җм„ң к°ҖлҠҘн•ң мҡҙмҳҒ лӢҲн„°л§Ғ л°Ҹ м§Җмӣҗ нҲҙ лӮҙл¶Җм—җм„ң мҡҙмҳҒ мқј мӮ¬мқҙнҠём—җм„ң лӢӨмӨ‘ OSмҡҙмҳҒ DAм—…к·ёл Ҳмқҙл“ңл§ҢмңјлЎңм—…к·ёл Ҳмқҙл“ңл§ҢмңјлЎңм—…к·ёл Ҳмқҙл“ңл§ҢмңјлЎңм—…к·ёл Ҳмқҙл“ңл§ҢмңјлЎң мғҲлЎңмҡҙ S추к°Җк°ҖлҠҘ
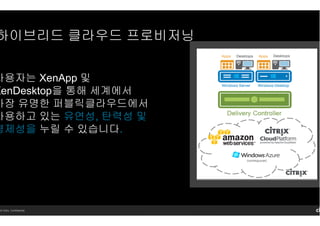
- 16. 14 Citrix. Confidential. мӮ¬мҡ©мһҗлҠ” XenApp л°Ҹ XenDesktopмқ„ нҶөн•ҙ м„ёкі„м—җм„ң к°ҖмһҘ мң лӘ…н•ң нҚјлё”лҰӯнҒҙлқјмҡ°л“ңм—җм„ң мӮ¬мҡ©н•ҳкі мһҲлҠ” мң м—°м„ұ, нғ„л Ҙм„ұ л°Ҹ кІҪм ңм„ұмқ„ лҲ„лҰҙ мҲҳ мһҲмҠөлӢҲлӢӨ. н•ҳмқҙлёҢлҰ¬л“ң нҒҙлқјмҡ°л“ң н”„лЎң비м ҖлӢқ
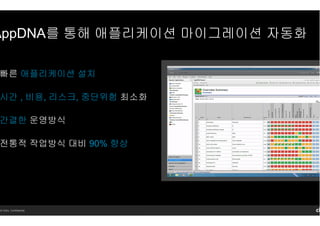
- 17. 14 Citrix. Confidential. AppDNAлҘј нҶөн•ҙ м• н”ҢлҰ¬мјҖмқҙм…ҳ л§Ҳмқҙк·ёл Ҳмқҙм…ҳ мһҗлҸҷнҷ” л№ лҘё м• н”ҢлҰ¬мјҖмқҙм…ҳ м„Өм№ҳ мӢңк°„ , 비мҡ©, лҰ¬мҠӨнҒ¬, мӨ‘лӢЁмң„н—ҳ мөңмҶҢнҷ” к°„кІ°н•ң мҡҙмҳҒл°©мӢқ м „нҶөм Ғ мһ‘м—…л°©мӢқ лҢҖ비 90% н–ҘмғҒ
- 18. 14 Citrix. Confidential. GPU л°Ҹ NVIDIA GRIDлҘј нҷңмҡ©н•ң мӢңмһҘм—җ нҳ„мЎҙн•ҳлҠ” мөңкі мқҳ 3D м–ҙн”ҢлҰ¬мјҖмқҙм…ҳмқ„ мң„н•ң мҶ”лЈЁм…ҳ н•ҳл“ңмӣЁм–ҙ кіөмң vGPU мҶ”лЈЁм…ҳ вҖў нғҖмӮ¬лҘј лҠҘк°Җн•ҳлҠ” GPUмүҗм–ҙл§Ғ мҶ”лЈЁм…ҳ м„ұлҠҘ вҖў м• н”ҢлҰ¬мјҖмқҙм…ҳмқ„ мң„н•ң л„ӨмқҙнӢ°лёҢ GPU лІӨлҚ” л“ңлқјмқҙлІ„ м§Җмӣҗ
- 19. 14 Citrix. Confidential. 30м–ө кё°кё°м—җм„ң мҡҙмҳҒ
- 20. 14 Citrix. Confidential. лһ©нғ‘нғҖлё”л ӣмҠӨл§ҲнҠё нҸ° лҚ°мҠӨнҒ¬нғ‘
- 21. 14 Citrix. Confidential. м—”н„°н”„лқјмқҙмҰҲм—”н„°н”„лқјмқҙмҰҲм—”н„°н”„лқјмқҙмҰҲм—”н„°н”„лқјмқҙмҰҲ нҢҢмқјнҢҢмқјнҢҢмқјнҢҢмқј лҸҷкё°нҷ”лҸҷкё°нҷ”лҸҷкё°нҷ”лҸҷкё°нҷ” л°Ҹл°Ҹл°Ҹл°Ҹ кіөмң кіөмң кіөмң кіөмң м•ұ л„ӨнҠёмӣҢнӮ№ л°Ҹ нҒҙлқјмҡ°л“ң мҳӨмјҖмҠӨнҠёл Ҳмқҙм…ҳ м—”н„°н”„лқјмқҙмҰҲ лӘЁл№ҢлҰ¬нӢ° кҙҖлҰ¬ м•ұ л°Ҹ лҚ°мҠӨнҒ¬нғ‘ к°ҖмғҒнҷ” лӘЁл°”мқј мӣҢнҒ¬ мҠӨнҺҳмқҙмҠӨлҘј к°ҖлҠҘмјҖ н•ҳлҠ” мқён”„лқјмҠӨнҠёлҹӯміҗ л°Ҹ м„ң비мҠӨ
- 23. 14 Citrix. Confidential. м—”н„°н”„лқјмқҙмҰҲ нҢҢмқј лҸҷкё°нҷ” л°Ҹ кіөмң м•ұм•ұм•ұм•ұ л„ӨнҠёмӣҢнӮ№л„ӨнҠёмӣҢнӮ№л„ӨнҠёмӣҢнӮ№л„ӨнҠёмӣҢнӮ№ л°Ҹл°Ҹл°Ҹл°Ҹ нҒҙлқјмҡ°л“ңнҒҙлқјмҡ°л“ңнҒҙлқјмҡ°л“ңнҒҙлқјмҡ°л“ң мҳӨмјҖмҠӨнҠёл Ҳмқҙм…ҳмҳӨмјҖмҠӨнҠёл Ҳмқҙм…ҳмҳӨмјҖмҠӨнҠёл Ҳмқҙм…ҳмҳӨмјҖмҠӨнҠёл Ҳмқҙм…ҳ м—”н„°н”„лқјмқҙмҰҲ лӘЁл№ҢлҰ¬нӢ° кҙҖлҰ¬ м•ұ л°Ҹ лҚ°мҠӨнҒ¬нғ‘ к°ҖмғҒнҷ” лӘЁл°”мқј мӣҢнҒ¬ мҠӨнҺҳмқҙмҠӨлҘј к°ҖлҠҘмјҖ н•ҳлҠ” мқён”„лқјмҠӨнҠёлҹӯміҗ л°Ҹ м„ң비мҠӨ
- 24. 14 Citrix. Confidential. м»Ён…җмё л°Ҹ мҠӨнҠёлҰ¬л°Қ мөңм Ғнҷ”лҘј нҶөн•ҙ лӘЁл°”мқј м•ұм—җм„ңмқҳ м„ұлҠҘ 5л°° н–ҘмғҒ лӘЁл°”мқј л„ӨнҠёмӣҢнҒ¬ нҠёлһҳн”Ҫм—җ лҢҖн•ң лҶ’мқҖ к°ҖмӢңм„ұ нҷ•ліҙ мӮ¬мҡ©мһҗ лі„ л°Ҹ м•ұ лі„ лӘЁл°”мқј ліҙм•Ҳкё°лҠҘ нғ‘мһ¬ кё°м—…мқҙ нҷ•мһҘмқ„ н•„мҡ”лЎң н• л•ҢлҘј лҢҖ비н•ң нҒҙлқјмҡ°л“ң мҡ°м„ м•„нӮӨн…Қміҗ нғ‘мһ¬
- 25. 14 Citrix. Confidential. мңҲлҸ„мҡ° м•ұ вҖ“ліҙм•Ҳ л°Ҹ м „лӢ¬ кі м„ұлҠҘ к°ҖмғҒлҚ°мҠӨнҒ¬нғ‘ лӘЁл°”мқј м•ұ л°Ҹ кё°кё° ліҙм•Ҳ лӘЁл°”мқј мғқмӮ°м„ұ м•ұ- л©”мқј л°Ҹ мӣ№ мҳЁн”„л ҲлҜёмҠӨ мғҒмқҳ м•Ҳм „н•ң нҢҢмқј кіөмң л°Ҹ лҸҷкё°нҷ” нҶөн•©лҗң м•ұмҠӨнҶ м–ҙ м•Ҳм „н•ң лӘЁл°”мқј кІҢмқҙнҠё мӣЁмқҙ
- 26. 14 Citrix. Confidential. м–ём ң м–ҙл””м„ңлӮҳ, лӘЁл“ мӮ¬лһҢм—җкІҢ нҒҙлқјмҡ°л“ң мў…лҘҳм—җ мғҒкҙҖм—Ҷмқҙ лҶҖлқјмҡҙ лӘЁл°”мқј кІҪн—ҳмқ„ л””мһҗмқё, кө¬м¶• л°Ҹ м „лӢ¬
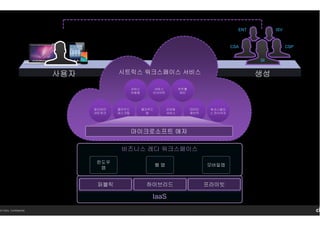
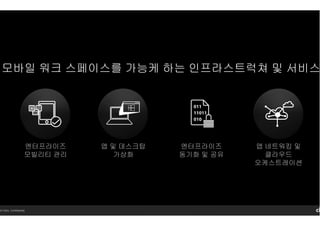
- 27. 14 Citrix. Confidential. нҢҢнҠёл„Ҳ л°Ҹ кі к°қмқ„ мң„н•ң лӘЁл°”мқј мӣҢнҒ¬мҠӨнҺҳмқҙмҠӨлҘј м„Өкі„, кө¬м¶• л°Ҹ мӮ¬мҡ© к°ҖлҠҘн•ҳлҸ„лЎқ м ңкіөн•ҳлҠ” нҒҙлқјмҡ°л“ң кё°л°ҳмқҳ н”Ңлһ«нҸј м»ЁнҠёлЎӨ м„јн„° нҒҙлқјмҡ°л“ң лҚ°мҠӨнҒ¬нғ‘ нҒҙлқјмҡ°л“ң м•ұ лӘЁл°”мқј м„ң비мҠӨ лҚ°мқҙн„° нҢЁлёҢлҰӯ л”ңлҰ¬лІ„лҰ¬ л„ӨнҠёмӣҢнҒ¬ м„ң비мҠӨ мқёмӮ¬мқҙнҠё мӣҢнҒ¬мҠӨнҺҳмқҙмҠӨ м»ЁмӢңм–ҙм§Җ м„ң비мҠӨ мһҗлҸҷнҷ”
- 28. 14 Citrix. Confidential. IaaS нҚјлё”лҰӯ н•ҳмқҙлёҢлҰ¬л“ң н”„лқјмқҙл№— мңҲлҸ„мҡ° м•ұ мӣ№ м•ұ лӘЁл°”мқјм•ұ 비мҰҲлӢҲмҠӨ л Ҳл”” мӣҢнҒ¬мҠӨнҺҳмқҙмҠӨ нҒҙлқјмҡ°л“ң лҚ°мҠӨнҒ¬нғ‘ нҒҙлқјмҡ°л“ң м•ұ лӘЁл°”мқј м„ң비мҠӨ лҚ°мқҙн„° нҢЁлёҢлҰӯ л”ңлҰ¬лІ„лҰ¬ л„ӨнҠёмӣҢнҒ¬ м„ң비мҠӨ мқёмӮ¬мқҙнҠё мӣҢнҒ¬мҠӨнҺҳмқҙ мҠӨ м»ЁмӢңм–ҙм§Җ м„ң비мҠӨ мһҗлҸҷнҷ” мӢңнҠёлҰӯмҠӨ мӣҢнҒ¬мҠӨнҺҳмқҙмҠӨ м„ң비мҠӨмӮ¬мҡ©мһҗ ISV CSPCSA SI мғқм„ұ м»ЁнҠёлЎӨ м„јн„° ENT л§ҲмқҙнҒ¬лЎңмҶҢн”„нҠё м• м Җ
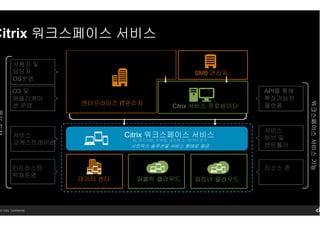
- 29. 14 Citrix. Confidential. Citrix мӣҢнҒ¬мҠӨнҺҳмқҙмҠӨмӣҢнҒ¬мҠӨнҺҳмқҙмҠӨмӣҢнҒ¬мҠӨнҺҳмқҙмҠӨмӣҢнҒ¬мҠӨнҺҳмқҙмҠӨ м„ң비мҠӨм„ң비мҠӨм„ң비мҠӨм„ң비мҠӨ нҢҢнҠёл„Ҳ нҒҙлқјмҡ°л“ңлҚ°мқҙн„° м„јн„° м—”н„°н”„лқјмқҙмҰҲ ITкҙҖлҰ¬мһҗ Citrix м„ң비мҠӨ н”„лЎңл°”мқҙлҚ” SMB кҙҖлҰ¬мһҗ мқён”„лқјмҠӨнҠё лҹӯміҗмҡҙмҳҒ м„ң비мҠӨ мҳӨмјҖмҠӨнҠёл Ҳмқҙм…ҳ OS л°Ҹ м• н”ҢлҰ¬мјҖмқҙ м…ҳ мҡҙмҳҒ мӮ¬мҡ©мһҗ л°Ҹ лӢҙлӢ№мһҗ OSмҡҙмҳҒ Citrix мӣҢнҒ¬мҠӨнҺҳмқҙмҠӨ м„ң비мҠӨ APIлҘј нҶөн•ҙ нҷ•мһҘк°ҖлҠҘн•ң н”Ңлһ«нҸј м„ң비мҠӨ н—ҲлёҢ л°Ҹ м»ЁнҠёлЎӨлҹ¬ лҰ¬мҶҢмҠӨ мЎҙ нҚјлё”лҰӯ нҒҙлқјмҡ°л“ң ITмқҳкё°лҠҘ мӣҢнҒ¬мҠӨнҺҳмқҙмҠӨм„ң비мҠӨкё°лҠҘ мӢңнҠёлҰӯмҠӨ мҶ”лЈЁм…ҳмқ„ м„ң비мҠӨ нҳ•нғңлЎң м ңкіө м•ұ, лҚ°мҠӨнҒ¬нғ‘, лӘЁл°”мқј, л„ӨнҠёмӣҢк·ё , лҚ°мқҙн„° 분м„қ
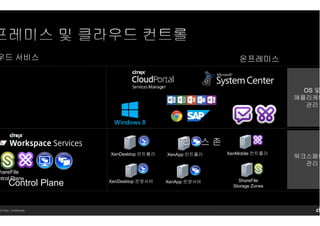
- 30. 14 Citrix. Confidential. OS л°Ҹ м• н”ҢлҰ¬мјҖмқҙ кҙҖлҰ¬ мӣҢнҒ¬мҠӨнҺҳмқҙ кҙҖлҰ¬ мҡ°л“ң м„ң비мҠӨ мҳЁн”„л ҲлҜёмҠӨ Control Plane hareFile ntrol Plane XenDesktop м»ЁнҠёлЎӨлҹ¬ XenMobile м»ЁнҠёлЎӨлҹ¬XenApp м»ЁнҠёлЎӨлҹ¬ XenDesktop мҡҙмҳҒм„ңлІ„ ShareFile Storage Zones XenApp мҡҙмҳҒм„ңлІ„ лҰ¬мҶҢмҠӨ мЎҙ
- 31. 14 Citrix. Confidential. м—”н„°н”„лқјмқҙмҰҲ лҸҷкё°нҷ” л°Ҹ кіөмң м•ұ л„ӨнҠёмӣҢнӮ№ л°Ҹ нҒҙлқјмҡ°л“ң мҳӨмјҖмҠӨнҠёл Ҳмқҙм…ҳ м—”н„°н”„лқјмқҙмҰҲ лӘЁл№ҢлҰ¬нӢ° кҙҖлҰ¬ м•ұ л°Ҹ лҚ°мҠӨнҒ¬нғ‘ к°ҖмғҒнҷ” лӘЁл°”мқј мӣҢнҒ¬ мҠӨнҺҳмқҙмҠӨлҘј к°ҖлҠҘмјҖ н•ҳлҠ” мқён”„лқјмҠӨнҠёлҹӯміҗ л°Ҹ м„ң비мҠӨ
- 32. 14 Citrix. Confidential. к°ҖмһҘк°ҖмһҘк°ҖмһҘк°ҖмһҘ кҙ‘лІ”мң„н•ңкҙ‘лІ”мң„н•ңкҙ‘лІ”мң„н•ңкҙ‘лІ”мң„н•ң лӘЁл°”мқјлӘЁл°”мқјлӘЁл°”мқјлӘЁл°”мқј л°Ҹл°Ҹл°Ҹл°Ҹ лҚ°мҠӨнҒ¬нғ‘лҚ°мҠӨнҒ¬нғ‘лҚ°мҠӨнҒ¬нғ‘лҚ°мҠӨнҒ¬нғ‘ кё°кё°кё°кё°кё°кё°кё°кё° м„ нғқм„ нғқм„ нғқм„ нғқ кё°м—…мқ„кё°м—…мқ„кё°м—…мқ„кё°м—…мқ„ мң„н•ңмң„н•ңмң„н•ңмң„н•ң нҷ•мһҘлҗңнҷ•мһҘлҗңнҷ•мһҘлҗңнҷ•мһҘлҗң лӘЁл°”мқјлӘЁл°”мқјлӘЁл°”мқјлӘЁл°”мқј м•ұм•ұм•ұм•ұ лӘЁл°”мқјлӘЁл°”мқјлӘЁл°”мқјлӘЁл°”мқј м ‘мҶҚмқ„м ‘мҶҚмқ„м ‘мҶҚмқ„м ‘мҶҚмқ„ мң„н•ңмң„н•ңмң„н•ңмң„н•ң мөңмғҒмқҳмөңмғҒмқҳмөңмғҒмқҳмөңмғҒмқҳ м„ұлҠҘм„ұлҠҘм„ұлҠҘм„ұлҠҘ нҒҙлқјмҡ°л“ңнҒҙлқјмҡ°л“ңнҒҙлқјмҡ°л“ңнҒҙлқјмҡ°л“ң л”ңлҰ¬лІ„лҰ¬л”ңлҰ¬лІ„лҰ¬л”ңлҰ¬лІ„лҰ¬л”ңлҰ¬лІ„лҰ¬ л„ӨнҠёмӣҢнҒ¬л„ӨнҠёмӣҢнҒ¬л„ӨнҠёмӣҢнҒ¬л„ӨнҠёмӣҢнҒ¬ нҶөн•©нҶөн•©нҶөн•©нҶөн•© н”„лқјмқҙл№—н”„лқјмқҙл№—н”„лқјмқҙл№—н”„лқјмқҙл№—, нҚјлё”лҰӯнҚјлё”лҰӯнҚјлё”лҰӯнҚјлё”лҰӯ нҒҙлқјмҡ°л“ңнҒҙлқјмҡ°л“ңнҒҙлқјмҡ°л“ңнҒҙлқјмҡ°л“ң л°Ҹл°Ҹл°Ҹл°Ҹ н•ҳмқҙлёҢлҰ¬л“ңн•ҳмқҙлёҢлҰ¬л“ңн•ҳмқҙлёҢлҰ¬л“ңн•ҳмқҙлёҢлҰ¬л“ң н”„лЎң비м ҖлӢқн”„лЎң비м ҖлӢқн”„лЎң비м ҖлӢқн”„лЎң비м ҖлӢқ м„ң비мҠӨм„ң비мҠӨм„ң비мҠӨм„ң비мҠӨ л°Ҹл°Ҹл°Ҹл°Ҹ н”Ңлһ«нҸјн”Ңлһ«нҸјн”Ңлһ«нҸјн”Ңлһ«нҸј н”„лЎңл°”мқҙлҚ”л“Өмқ„н”„лЎңл°”мқҙлҚ”л“Өмқ„н”„лЎңл°”мқҙлҚ”л“Өмқ„н”„лЎңл°”мқҙлҚ”л“Өмқ„ мң„н•ңмң„н•ңмң„н•ңмң„н•ң м—җмҪ”мӢңмҠӨн…ңм—җмҪ”мӢңмҠӨн…ңм—җмҪ”мӢңмҠӨн…ңм—җмҪ”мӢңмҠӨн…ң лӘЁл°”мқј мӣҢнҒ¬мҠӨнҺҳмқҙмҠӨ лҰ¬лҚ”мӢӯ
- 33. 14 Citrix. Confidential. WORK BETTER. LIVE BETTER.










































![[OpenInfra Days Korea 2018] (Track 2) Microservice Architecture, DevOps к·ёлҰ¬кі 5...](https://cdn.slidesharecdn.com/ss_thumbnails/22openinfradayskorea2018-sptek-180704054402-thumbnail.jpg?width=560&fit=bounds)















