Prezentarea "Securitatea Aplicatiilor Online" de la ODO
Download as ppt, pdf0 likes448 views
The document discusses online application security vulnerabilities, including SQL injection, XSS, CSRF, email injection, and directory traversal. It emphasizes the importance of input validation, data encryption, daily backups, and regular updates to server databases to protect against these threats. Additionally, it highlights that user trust is not guaranteed, suggesting a paranoid approach to security.
1 of 22
Downloaded 15 times


![SQL Injection Atac asupra bazei de date http://www.example.com/view.php?id_cat=4 "SELECT * FROM data WHERE id_category = " + $_GET[ŌĆśidŌĆÖ] + ";" http://www.example.com/view.php?id_cat=4 OR 1=1 "SELECT * FROM data WHERE id = 1 OR 1=1;" OR 1=1](https://image.slidesharecdn.com/securitatea-aplicatiilor-online-1217850356985504-8/85/Prezentarea-Securitatea-Aplicatiilor-Online-de-la-ODO-6-320.jpg)









Ad
Recommended
Owasp and friends
Owasp and friendsMa┼Švydas Skuodas
╠²
This document discusses application security and the OWASP Top 10 list of vulnerabilities. It covers topics like injection flaws, broken authentication, sensitive data exposure, and denial of service attacks. Application security involves adequately defending against easy-to-find vulnerabilities to achieve Level 1 certification. The OWASP Top 10 lists the most critical web app security risks, including injection, XSS, broken access control, and using components with known vulnerabilities. Denial of service attacks work by consuming limited resources like bandwidth or database connections to prevent legitimate use.Joomla Security
Joomla SecurityRuth Cheesley
╠²
The document discusses security best practices for Joomla websites. It defines security as authorized access to data and files while preventing malicious attacks. It recommends always getting installation files from Joomla.org, using reputable hosting providers, keeping software updated, regularly backing up files and databases offline, and changing default usernames and passwords. Specific security tools mentioned include jSecure to hide the administrator page and EasySpamKiller to block known attacker IP addresses.WordPress Security - What to do, What NOT to do
WordPress Security - What to do, What NOT to doWordPress Trivandrum
╠²
The document outlines best practices for securing WordPress sites, emphasizing the importance of security measures such as choosing a reliable hosting provider, updating software regularly, and implementing strong authentication methods. It also lists common security risks identified by OWASP and highlights the role of the WordPress security team in addressing vulnerabilities. Popular security plugins and server maintenance tips are provided to enhance overall site protection.WordPress Security Best Practices
WordPress Security Best PracticesJason Yingling
╠²
The document outlines best practices for WordPress security, highlighting common attacks such as cross-site scripting, brute-force attacks, SQL injections, and DDoS. It emphasizes the importance of using strong passwords, keeping software updated, implementing two-factor authentication, and utilizing security plugins like iThemes Security and Wordfence. The document also advises on the significance of regular backups and choosing trusted plugins to enhance overall site protection.Joomla sp├®cialiste
Joomla sp├®cialisteRomain Caisse
╠²
The document outlines essential steps to enhance Joomla security, emphasizing the importance of regular updates, appropriate hosting, and using .htaccess to block vulnerabilities. It highlights various measures such as managing extensions, using strong passwords, and conducting vulnerability scans to protect against hacking attempts. Additionally, it recommends turning off FTP layers and utilizing SEO-friendly URLs to improve site security.Prezentare Haipa despre bloguri
Prezentare Haipa despre bloguriGabriel Curcudel
╠²
Documentul ofer─ā o list─ā extins─ā de platforme ╚Öi sisteme de gestionare a con╚øinutului pentru crearea de bloguri, inclusiv WordPress, Drupal ╚Öi Joomla. De asemenea, abordeaz─ā ├«ntreb─āri despre utilizarea blogurilor, generarea de venituri ╚Öi flexibilitatea WordPress. Autorul documentului este Gabriel Amarandei, administrator al haipa.ro ╚Öi optzile.ro.KFP New Media & Prevention
KFP New Media & PreventionLaDonna Coy
╠²
The document discusses the concept of new media and its role in social change and community engagement, particularly within the Kansas Family Partnership. It emphasizes the importance of connectivity, participation, and the utilization of various platforms like social media, blogs, and podcasts to convey messages and foster collaboration. The exploration of new media aims to enhance communication among community partners, youth, and policymakers for more effective prevention strategies.Cum generezi asteptari realiste folosind segmentari de piata si personas
Cum generezi asteptari realiste folosind segmentari de piata si personasGabriel Curcudel
╠²
Documentul explic─ā conceptul de 'personas', care sunt arhetipuri fictive de utilizatori create pentru a ghida deciziile legate de produsele digitale, navigare ╚Öi design vizual. Personas sunt bazate pe date reale ╚Öi trebuie s─ā fie corelate cu realitatea pentru a fi utile, cercet─ārile calitative ╚Öi cantitative fiind esen╚øiale ├«n crearea lor. Folosirea acestor arhetipuri ajut─ā la ├«n╚øelegerea mai bun─ā a comportamentului utilizatorilor ╚Öi ├«mbun─āt─ā╚øe╚Öte modul de comunicare ╚Öi strategia de marketing.Web Apps Security
Web Apps SecurityVictor Bucutea
╠²
This document discusses various web application security vulnerabilities and methods for mitigating them. It begins by summarizing the OWASP Top 10 list of most critical web application security risks. It then provides examples of different types of injection attacks, cross-site scripting, broken authentication and session management issues. The document also discusses insecure cryptographic storage, insufficient transport layer protection and other vulnerabilities. It emphasizes the importance of input and output validation, as well as proper encoding to prevent attacks. The OWASP ESAPI framework is presented as a tool to help developers address many of these security issues.Roberto Bicchierai - Defending web applications from attacks
Roberto Bicchierai - Defending web applications from attacksPietro Polsinelli
╠²
The document discusses common security mistakes in web application development, emphasizing the importance of strong user identity measures, secure coding practices, and protection against vulnerabilities like SQL injection, XSS, and CSRF. It recommends using techniques such as salted cookies, server-side tokens, and thorough encoding of user inputs to mitigate risks. Additionally, it highlights the necessity of employing SSL for secure data transmission and maintaining robust password policies.Intro to Web Application Security
Intro to Web Application SecurityRob Ragan
╠²
The document discusses web application security, emphasizing that application security involves protecting against vulnerabilities during design, development, and deployment. It highlights the prevalence of attacks on the application layer, the importance of secure coding practices, and common threats like SQL injection and cross-site scripting. The content underscores the necessity of security expertise and best practices in software development to mitigate risks associated with web applications.Web security 101
Web security 101Kristaps Kūlis
╠²
The document provides an overview of common internet security topics such as SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), password storage best practices, and discusses the importance of using encryption and securing web applications, servers, networks and personal devices and data. It emphasizes that security is an ongoing process and outlines some specific vulnerabilities in PHP as well as recommendations for improving security.Websec
WebsecKristaps Kūlis
╠²
The document provides an overview of common internet security topics such as SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), password storage best practices, and session security issues. It also discusses server-side security configurations and risks associated with shared hosting environments. Personal security issues are addressed as well, including password management and securing digital communications.Web Security
Web SecurityGerald Villorente
╠²
Gerald Z. Villorente presents on the topic of web security. He discusses security levels including server, network, application, and user levels. Some common web application threats are also outlined such as cross-site scripting, SQL injection, and denial-of-service attacks. The presentation provides an overview of aspects of data security, principles of secure development, and best practices for web security.2009 Barcamp Nashville Web Security 101
2009 Barcamp Nashville Web Security 101brian_dailey
╠²
The document discusses various web security threats and prevention techniques, focusing on issues like XSS, CSRF, SQL injection, and mass assignment vulnerabilities in web applications. It emphasizes the importance of escaping output, using parameterized statements, and properly managing user permissions to enhance security. Additionally, it recommends resources for further learning and stresses that developers should never assume their frameworks handle all security concerns.How to secure web applications
How to secure web applicationsMohammed A. Imran
╠²
The document discusses the critical need for web application security, highlighting that 90% of companies experienced hacking incidents last year. It debunks common myths about security measures, focuses on secure development principles, and addresses vulnerabilities like SQL injection and cross-site scripting. The document emphasizes the importance of employing strong encryption, minimizing attack surfaces, and following best practices to ensure secure software development.Cum s─ā cre╚Öti v├ónz─ārile online
Cum s─ā cre╚Öti v├ónz─ārile online Gabriel Curcudel
╠²
Prezentarea se concentreaz─ā pe optimizarea ratei de conversie (CRO) ├«n marketingul online, subliniind importan╚øa cre─ārii unei experien╚øe pl─ācute pentru utilizatori pentru a cre╚Öte v├ónz─ārile. Aceasta eviden╚øiaz─ā c─ā, de╚Öi rata de conversie medie este de doar 1% ├«n comer╚øul electronic rom├ónesc, prin ├«n╚øelegerea nevoilor clien╚øilor ╚Öi adaptarea ofertelor se pot maximiza rezultatele. Concluzia este c─ā succesul depinde de aten╚øia la detalii, analiza datelor existente ╚Öi implementarea de solu╚øii corecte pentru a g─āsi ╚Öi rezolva problemele clien╚øilor.Local search 2013 Romania
Local search 2013 RomaniaGabriel Curcudel
╠²
Prezentarea abordeaz─ā importan╚øa promov─ārii afacerilor la nivel local prin intermediul motoarelor de c─āutare, subliniind tendin╚øele de cre╚Ötere a c─āut─ārilor pe mobil ├«n Rom├ónia. Se ofer─ā strategii pentru optimizarea afacerilor locale, inclusiv utilizarea Google Maps ╚Öi recenziilor online pentru a ├«mbun─āt─ā╚øi vizibilitatea. Concluziile sugereaz─ā un poten╚øial semnificativ neexploatat pentru dezvoltarea online ├«n r├óndul afacerilor locale.Competitive link analysis si link management
Competitive link analysis si link managementGabriel Curcudel
╠²
Prezentarea oli Krumel despre analiza competitiv─ā a linkurilor ╚Öi managementul acestora subliniaz─ā importan╚øa ├«n╚øelegerii strategiilor concuren╚øilor pentru a ├«mbun─āt─ā╚øi performan╚øa ├«n c─āut─āri. Documentul eviden╚øiaz─ā instrumentele utilizate pentru analizarea concuren╚øei ╚Öi gestionarea linkurilor, precum cognitiveseo.com ╚Öi ahrefs.com, care ofer─ā metrici esen╚øiale. De asemenea, se discut─ā despre cum un management eficient al linkurilor poate influen╚øa rezultatele c─āut─ārilor ╚Öi bugetul asociat acestora.Local search Romania 2012 - Krumel - SEM Days
Local search Romania 2012 - Krumel - SEM DaysGabriel Curcudel
╠²
Documentul analizeaz─ā impactul ├«mbun─āt─ā╚øirii Google Venice asupra c─āut─ārilor locale din Rom├ónia, eviden╚øiind relevan╚øa site-urilor locale ├«n func╚øie de loca╚øie. Analiza a fost realizat─ā pentru 6 ora╚Öe, revel├ónd volumele de c─āutare pentru termeni specifici, precum ╚Öi dominarea site-urilor generale ├«n unele zone. Concluziile arat─ā c─ā Timi╚Öoara are cele mai multe c─āut─āri comerciale, iar Bucure╚Öti are cele mai multe c─āut─āri necomerciale.Link building Tecomm Cluj
Link building Tecomm ClujGabriel Curcudel
╠²
Link building-ul este o strategie SEO esen╚øial─ā care ajut─ā la generarea de trafic organic ╚Öi referrals. ├Än document sunt prezentate diverse metode de link building, precum ├«nscrierea ├«n directoare, social bookmarking ╚Öi guest posting, al─āturi de importan╚øa managementului link-urilor pentru a asigura eficien╚øa acestora. Este crucial─ā diversificarea anchor text-ului ╚Öi a partenerilor de linking pentru a evita penaliz─ārile ╚Öi a ob╚øine rezultate optimale.Analiza SEO ptr site-uri din 2parale
Analiza SEO ptr site-uri din 2paraleGabriel Curcudel
╠²
Analiza examineaz─ā modul ├«n care site-urile afiliate ├«n re╚øeaua 2parale profit─ā de SEO ╚Öi SEM, eviden╚øiind problemele legate de utilizarea ineficient─ā a cuvintelor cheie ╚Öi absen╚øa unor strategii bune de link building. Majoritatea site-urilor analizate nu reu╚Öesc s─ā abordeze cuvinte cheie specifice ╚Öi se concentreaz─ā pe termeni generali cu concuren╚ø─ā mare, ceea ce duce la conversii slabe. Solu╚øiile propuse includ ├«mbun─āt─ā╚øirea ni╚Ö─ārii cuvintelor cheie ╚Öi diversificarea surselor de link-uri.Long tail - Krumel - IMTO Seo & Sem
Long tail - Krumel - IMTO Seo & SemGabriel Curcudel
╠²
Prezentarea de la IMTO 2010, sus╚øinut─ā de Krumel, discut─ā conceptul de 'long tail' ├«n SEO, incluz├ónd defini╚øii, avantaje ╚Öi dezavantaje. Avantajele includ trafic relevant ╚Öi conversii ├«nalte, ├«n timp ce dezavantajele constau ├«n volumul sc─āzut de trafic. Documentul subliniaz─ā importan╚øa cre─ārii de con╚øinut adaptat at├ót pentru utilizatori c├ót ╚Öi pentru motoarele de c─āutare.Lumea Seo Sem Ppc
Lumea Seo Sem PpcGabriel Curcudel
╠²
Documentul abordeaz─ā importan╚øa optimiz─ārii SEO pentru site-uri ├«n Rom├ónia, subliniind c─ā SEO este esen╚øial pentru atragerea vizitatorilor din motoarele de c─āutare, ├«n special Google. De asemenea, sunt prezentate criteriile de selec╚øie a prestatorilor de servicii SEO ╚Öi importan╚øa analiz─ārii competitivit─ā╚øii, precum ╚Öi influen╚øa modific─ārilor on-page ╚Öi off-page asupra pozi╚øiei ├«n rezultatele c─āut─ārilor. ├Än concluzie, SEO trebuie integrat ├«ntr-o strategie de marketing online mai ampl─ā pentru a fi cu adev─ārat eficient.SEO si SEM ŌĆō strategii pentru afaceri oline
SEO si SEM ŌĆō strategii pentru afaceri olineGabriel Curcudel
╠²
Documentul discut─ā importan╚øa SEO ╚Öi SEM pentru afacerile online, explic├ónd cum SEO ajut─ā la optimizarea site-urilor pentru motoarele de c─āutare ╚Öi la atragerea traficului targetat. Se subliniaz─ā necesitatea de a defini strategii clare pentru SEO ╚Öi SEM, incluz├ónd analiza audien╚øei, obiectivelor site-ului, precum ╚Öi strategii de link building ╚Öi anun╚øuri pl─ātite. ├Än final, reu╚Öita acestor strategii se m─āsoar─ā prin cre╚Öterea v├ónz─ārilor ╚Öi a notoriet─ā╚øii brandului.Prezentare IMTO - Krumel
Prezentare IMTO - KrumelGabriel Curcudel
╠²
Documentul abordeaz─ā importan╚øa SEO ├«n Rom├ónia, subliniind c─ā optimizarea site-urilor pentru motoarele de c─āutare este esen╚øial─ā pentru a atrage trafic profitabil. Se discut─ā despre criteriile de alegere a prestatorilor SEO, responsabilitatea modific─ārilor ╚Öi fluctua╚øiile de pozi╚øionare ├«n func╚øie de factori externi ╚Öi interni. De asemenea, se men╚øioneaz─ā c─ā nu exist─ā garan╚øii ├«n SEO ╚Öi c─ā pre╚øurile variaz─ā ├«n func╚øie de cerin╚øele specifice ale fiec─ārui proiect.Working for the client's clients
Working for the client's clientsGabriel Curcudel
╠²
Iulian Avasiloaia discut─ā despre problemele actuale din interac╚øiunea prestator-client, eviden╚øiind c─ā un client mul╚øumit nu garanteaz─ā un proiect de succes. Prezentarea subliniaz─ā importan╚øa introducerii unei ter╚øe p─ār╚øi, clientul clientului, ╚Öi propune metode de ├«mbun─āt─ā╚øire a acestei rela╚øii. Exemplele folosite includ studii de caz cu clientela Apple, subliniind necesitatea de responsabilitate ╚Öi educare ├«n pia╚ø─ā.Seo Vs Copywriting
Seo Vs CopywritingGabriel Curcudel
╠²
Documentul ofer─ā o perspectiv─ā asupra atragerii ╚Öi p─āstr─ārii vizitatorilor pe blog prin SEO ╚Öi web copywriting. Este subliniat─ā importan╚øa tehnicilor corecte de SEO, cum ar fi evitarea keyword stuffing ╚Öi comentariilor spam, precum ╚Öi strategii de copywriting pentru convertirea traficului. De asemenea, se discut─ā despre obiectivele blogului, inclusiv crearea unei comunit─ā╚øi ╚Öi ├«mbun─āt─ā╚øirea clasamentului ├«n motoarele de c─āutare.Google Analytics The Fruits Salad Sibiu 2009
Google Analytics The Fruits Salad Sibiu 2009Gabriel Curcudel
╠²
Documentul discut─ā despre utilizarea Google Analytics, eviden╚øiind importan╚øa acestei platforme pentru analiza datelor de marketing. Se men╚øioneaz─ā un num─ār semnificativ de vizitatori unici ╚Öi rata de respingere, subliniind nevoia de segmentare a datelor. Informa╚øiile sunt furnizate ├«ntr-un mod fragmentat, reflect├ónd at├ót beneficii, c├ót ╚Öi ├«ntreb─āri legate de ac╚øiunile ce urmeaz─ā analizei.Traficul Organic Si Relevanta Pentru Vizitatori A Paginilor Web
Traficul Organic Si Relevanta Pentru Vizitatori A Paginilor WebGabriel Curcudel
╠²
Prezentarea lui Gabriel Curcudel discut─ā despre traficul organic ╚Öi relevan╚øa c─āut─ārilor pe motoarele de c─āutare, explic├ónd psihologia utilizatorilor ╚Öi clasificarea informa╚øiilor c─āutate. Rezultatele organice sunt generate de algoritmi, f─ār─ā a fi pl─ātite, ╚Öi genereaz─ā trafic de calitate, care converte╚Öte mai bine. Studiile eviden╚øiaz─ā importan╚øa relevan╚øei c─āut─ārilor ╚Öi cum utilizatorii detaliaz─ā c─āut─ārile pentru a ob╚øine rezultate mai precise.More Related Content
Similar to Prezentarea "Securitatea Aplicatiilor Online" de la ODO (8)
Web Apps Security
Web Apps SecurityVictor Bucutea
╠²
This document discusses various web application security vulnerabilities and methods for mitigating them. It begins by summarizing the OWASP Top 10 list of most critical web application security risks. It then provides examples of different types of injection attacks, cross-site scripting, broken authentication and session management issues. The document also discusses insecure cryptographic storage, insufficient transport layer protection and other vulnerabilities. It emphasizes the importance of input and output validation, as well as proper encoding to prevent attacks. The OWASP ESAPI framework is presented as a tool to help developers address many of these security issues.Roberto Bicchierai - Defending web applications from attacks
Roberto Bicchierai - Defending web applications from attacksPietro Polsinelli
╠²
The document discusses common security mistakes in web application development, emphasizing the importance of strong user identity measures, secure coding practices, and protection against vulnerabilities like SQL injection, XSS, and CSRF. It recommends using techniques such as salted cookies, server-side tokens, and thorough encoding of user inputs to mitigate risks. Additionally, it highlights the necessity of employing SSL for secure data transmission and maintaining robust password policies.Intro to Web Application Security
Intro to Web Application SecurityRob Ragan
╠²
The document discusses web application security, emphasizing that application security involves protecting against vulnerabilities during design, development, and deployment. It highlights the prevalence of attacks on the application layer, the importance of secure coding practices, and common threats like SQL injection and cross-site scripting. The content underscores the necessity of security expertise and best practices in software development to mitigate risks associated with web applications.Web security 101
Web security 101Kristaps Kūlis
╠²
The document provides an overview of common internet security topics such as SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), password storage best practices, and discusses the importance of using encryption and securing web applications, servers, networks and personal devices and data. It emphasizes that security is an ongoing process and outlines some specific vulnerabilities in PHP as well as recommendations for improving security.Websec
WebsecKristaps Kūlis
╠²
The document provides an overview of common internet security topics such as SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), password storage best practices, and session security issues. It also discusses server-side security configurations and risks associated with shared hosting environments. Personal security issues are addressed as well, including password management and securing digital communications.Web Security
Web SecurityGerald Villorente
╠²
Gerald Z. Villorente presents on the topic of web security. He discusses security levels including server, network, application, and user levels. Some common web application threats are also outlined such as cross-site scripting, SQL injection, and denial-of-service attacks. The presentation provides an overview of aspects of data security, principles of secure development, and best practices for web security.2009 Barcamp Nashville Web Security 101
2009 Barcamp Nashville Web Security 101brian_dailey
╠²
The document discusses various web security threats and prevention techniques, focusing on issues like XSS, CSRF, SQL injection, and mass assignment vulnerabilities in web applications. It emphasizes the importance of escaping output, using parameterized statements, and properly managing user permissions to enhance security. Additionally, it recommends resources for further learning and stresses that developers should never assume their frameworks handle all security concerns.How to secure web applications
How to secure web applicationsMohammed A. Imran
╠²
The document discusses the critical need for web application security, highlighting that 90% of companies experienced hacking incidents last year. It debunks common myths about security measures, focuses on secure development principles, and addresses vulnerabilities like SQL injection and cross-site scripting. The document emphasizes the importance of employing strong encryption, minimizing attack surfaces, and following best practices to ensure secure software development.More from Gabriel Curcudel (20)
Cum s─ā cre╚Öti v├ónz─ārile online
Cum s─ā cre╚Öti v├ónz─ārile online Gabriel Curcudel
╠²
Prezentarea se concentreaz─ā pe optimizarea ratei de conversie (CRO) ├«n marketingul online, subliniind importan╚øa cre─ārii unei experien╚øe pl─ācute pentru utilizatori pentru a cre╚Öte v├ónz─ārile. Aceasta eviden╚øiaz─ā c─ā, de╚Öi rata de conversie medie este de doar 1% ├«n comer╚øul electronic rom├ónesc, prin ├«n╚øelegerea nevoilor clien╚øilor ╚Öi adaptarea ofertelor se pot maximiza rezultatele. Concluzia este c─ā succesul depinde de aten╚øia la detalii, analiza datelor existente ╚Öi implementarea de solu╚øii corecte pentru a g─āsi ╚Öi rezolva problemele clien╚øilor.Local search 2013 Romania
Local search 2013 RomaniaGabriel Curcudel
╠²
Prezentarea abordeaz─ā importan╚øa promov─ārii afacerilor la nivel local prin intermediul motoarelor de c─āutare, subliniind tendin╚øele de cre╚Ötere a c─āut─ārilor pe mobil ├«n Rom├ónia. Se ofer─ā strategii pentru optimizarea afacerilor locale, inclusiv utilizarea Google Maps ╚Öi recenziilor online pentru a ├«mbun─āt─ā╚øi vizibilitatea. Concluziile sugereaz─ā un poten╚øial semnificativ neexploatat pentru dezvoltarea online ├«n r├óndul afacerilor locale.Competitive link analysis si link management
Competitive link analysis si link managementGabriel Curcudel
╠²
Prezentarea oli Krumel despre analiza competitiv─ā a linkurilor ╚Öi managementul acestora subliniaz─ā importan╚øa ├«n╚øelegerii strategiilor concuren╚øilor pentru a ├«mbun─āt─ā╚øi performan╚øa ├«n c─āut─āri. Documentul eviden╚øiaz─ā instrumentele utilizate pentru analizarea concuren╚øei ╚Öi gestionarea linkurilor, precum cognitiveseo.com ╚Öi ahrefs.com, care ofer─ā metrici esen╚øiale. De asemenea, se discut─ā despre cum un management eficient al linkurilor poate influen╚øa rezultatele c─āut─ārilor ╚Öi bugetul asociat acestora.Local search Romania 2012 - Krumel - SEM Days
Local search Romania 2012 - Krumel - SEM DaysGabriel Curcudel
╠²
Documentul analizeaz─ā impactul ├«mbun─āt─ā╚øirii Google Venice asupra c─āut─ārilor locale din Rom├ónia, eviden╚øiind relevan╚øa site-urilor locale ├«n func╚øie de loca╚øie. Analiza a fost realizat─ā pentru 6 ora╚Öe, revel├ónd volumele de c─āutare pentru termeni specifici, precum ╚Öi dominarea site-urilor generale ├«n unele zone. Concluziile arat─ā c─ā Timi╚Öoara are cele mai multe c─āut─āri comerciale, iar Bucure╚Öti are cele mai multe c─āut─āri necomerciale.Link building Tecomm Cluj
Link building Tecomm ClujGabriel Curcudel
╠²
Link building-ul este o strategie SEO esen╚øial─ā care ajut─ā la generarea de trafic organic ╚Öi referrals. ├Än document sunt prezentate diverse metode de link building, precum ├«nscrierea ├«n directoare, social bookmarking ╚Öi guest posting, al─āturi de importan╚øa managementului link-urilor pentru a asigura eficien╚øa acestora. Este crucial─ā diversificarea anchor text-ului ╚Öi a partenerilor de linking pentru a evita penaliz─ārile ╚Öi a ob╚øine rezultate optimale.Analiza SEO ptr site-uri din 2parale
Analiza SEO ptr site-uri din 2paraleGabriel Curcudel
╠²
Analiza examineaz─ā modul ├«n care site-urile afiliate ├«n re╚øeaua 2parale profit─ā de SEO ╚Öi SEM, eviden╚øiind problemele legate de utilizarea ineficient─ā a cuvintelor cheie ╚Öi absen╚øa unor strategii bune de link building. Majoritatea site-urilor analizate nu reu╚Öesc s─ā abordeze cuvinte cheie specifice ╚Öi se concentreaz─ā pe termeni generali cu concuren╚ø─ā mare, ceea ce duce la conversii slabe. Solu╚øiile propuse includ ├«mbun─āt─ā╚øirea ni╚Ö─ārii cuvintelor cheie ╚Öi diversificarea surselor de link-uri.Long tail - Krumel - IMTO Seo & Sem
Long tail - Krumel - IMTO Seo & SemGabriel Curcudel
╠²
Prezentarea de la IMTO 2010, sus╚øinut─ā de Krumel, discut─ā conceptul de 'long tail' ├«n SEO, incluz├ónd defini╚øii, avantaje ╚Öi dezavantaje. Avantajele includ trafic relevant ╚Öi conversii ├«nalte, ├«n timp ce dezavantajele constau ├«n volumul sc─āzut de trafic. Documentul subliniaz─ā importan╚øa cre─ārii de con╚øinut adaptat at├ót pentru utilizatori c├ót ╚Öi pentru motoarele de c─āutare.Lumea Seo Sem Ppc
Lumea Seo Sem PpcGabriel Curcudel
╠²
Documentul abordeaz─ā importan╚øa optimiz─ārii SEO pentru site-uri ├«n Rom├ónia, subliniind c─ā SEO este esen╚øial pentru atragerea vizitatorilor din motoarele de c─āutare, ├«n special Google. De asemenea, sunt prezentate criteriile de selec╚øie a prestatorilor de servicii SEO ╚Öi importan╚øa analiz─ārii competitivit─ā╚øii, precum ╚Öi influen╚øa modific─ārilor on-page ╚Öi off-page asupra pozi╚øiei ├«n rezultatele c─āut─ārilor. ├Än concluzie, SEO trebuie integrat ├«ntr-o strategie de marketing online mai ampl─ā pentru a fi cu adev─ārat eficient.SEO si SEM ŌĆō strategii pentru afaceri oline
SEO si SEM ŌĆō strategii pentru afaceri olineGabriel Curcudel
╠²
Documentul discut─ā importan╚øa SEO ╚Öi SEM pentru afacerile online, explic├ónd cum SEO ajut─ā la optimizarea site-urilor pentru motoarele de c─āutare ╚Öi la atragerea traficului targetat. Se subliniaz─ā necesitatea de a defini strategii clare pentru SEO ╚Öi SEM, incluz├ónd analiza audien╚øei, obiectivelor site-ului, precum ╚Öi strategii de link building ╚Öi anun╚øuri pl─ātite. ├Än final, reu╚Öita acestor strategii se m─āsoar─ā prin cre╚Öterea v├ónz─ārilor ╚Öi a notoriet─ā╚øii brandului.Prezentare IMTO - Krumel
Prezentare IMTO - KrumelGabriel Curcudel
╠²
Documentul abordeaz─ā importan╚øa SEO ├«n Rom├ónia, subliniind c─ā optimizarea site-urilor pentru motoarele de c─āutare este esen╚øial─ā pentru a atrage trafic profitabil. Se discut─ā despre criteriile de alegere a prestatorilor SEO, responsabilitatea modific─ārilor ╚Öi fluctua╚øiile de pozi╚øionare ├«n func╚øie de factori externi ╚Öi interni. De asemenea, se men╚øioneaz─ā c─ā nu exist─ā garan╚øii ├«n SEO ╚Öi c─ā pre╚øurile variaz─ā ├«n func╚øie de cerin╚øele specifice ale fiec─ārui proiect.Working for the client's clients
Working for the client's clientsGabriel Curcudel
╠²
Iulian Avasiloaia discut─ā despre problemele actuale din interac╚øiunea prestator-client, eviden╚øiind c─ā un client mul╚øumit nu garanteaz─ā un proiect de succes. Prezentarea subliniaz─ā importan╚øa introducerii unei ter╚øe p─ār╚øi, clientul clientului, ╚Öi propune metode de ├«mbun─āt─ā╚øire a acestei rela╚øii. Exemplele folosite includ studii de caz cu clientela Apple, subliniind necesitatea de responsabilitate ╚Öi educare ├«n pia╚ø─ā.Seo Vs Copywriting
Seo Vs CopywritingGabriel Curcudel
╠²
Documentul ofer─ā o perspectiv─ā asupra atragerii ╚Öi p─āstr─ārii vizitatorilor pe blog prin SEO ╚Öi web copywriting. Este subliniat─ā importan╚øa tehnicilor corecte de SEO, cum ar fi evitarea keyword stuffing ╚Öi comentariilor spam, precum ╚Öi strategii de copywriting pentru convertirea traficului. De asemenea, se discut─ā despre obiectivele blogului, inclusiv crearea unei comunit─ā╚øi ╚Öi ├«mbun─āt─ā╚øirea clasamentului ├«n motoarele de c─āutare.Google Analytics The Fruits Salad Sibiu 2009
Google Analytics The Fruits Salad Sibiu 2009Gabriel Curcudel
╠²
Documentul discut─ā despre utilizarea Google Analytics, eviden╚øiind importan╚øa acestei platforme pentru analiza datelor de marketing. Se men╚øioneaz─ā un num─ār semnificativ de vizitatori unici ╚Öi rata de respingere, subliniind nevoia de segmentare a datelor. Informa╚øiile sunt furnizate ├«ntr-un mod fragmentat, reflect├ónd at├ót beneficii, c├ót ╚Öi ├«ntreb─āri legate de ac╚øiunile ce urmeaz─ā analizei.Traficul Organic Si Relevanta Pentru Vizitatori A Paginilor Web
Traficul Organic Si Relevanta Pentru Vizitatori A Paginilor WebGabriel Curcudel
╠²
Prezentarea lui Gabriel Curcudel discut─ā despre traficul organic ╚Öi relevan╚øa c─āut─ārilor pe motoarele de c─āutare, explic├ónd psihologia utilizatorilor ╚Öi clasificarea informa╚øiilor c─āutate. Rezultatele organice sunt generate de algoritmi, f─ār─ā a fi pl─ātite, ╚Öi genereaz─ā trafic de calitate, care converte╚Öte mai bine. Studiile eviden╚øiaz─ā importan╚øa relevan╚øei c─āut─ārilor ╚Öi cum utilizatorii detaliaz─ā c─āut─ārile pentru a ob╚øine rezultate mai precise.Google Ad Planner Pentru Plasamente anunturi Adwords
Google Ad Planner Pentru Plasamente anunturi AdwordsGabriel Curcudel
╠²
Documentul descrie utilizarea Google Ad Planner pentru plasarea anun╚øurilor AdWords ├«n domeniul con╚øinutului rom├ónesc, cu focus pe site-uri destinate copiilor ╚Öi p─ārin╚øilor. Se eviden╚øiaz─ā procesul de cercetare a ni╚Öei, selectarea criteriilor precum ╚øara, loca╚øia ╚Öi cuvintele cheie pentru a ob╚øine rezultate relevante. De asemenea, se ofer─ā detalii despre formatele anun╚øurilor ╚Öi despre estim─ārile de trafic disponibile pentru site-urile selectate.Cum vinde GOOGLE pentru tine?
Cum vinde GOOGLE pentru tine?Gabriel Curcudel
╠²
The document discusses Google advertising products and services including AdWords and AdSense. It asks how AdWords can be used with earnings from AdSense, what content ads can include, and how AdWords is expanding to video ads on YouTube similarly to how ads appear in videos now.Cum Folosesti Motoarele De Cautare
Cum Folosesti Motoarele De CautareGabriel Curcudel
╠²
Prezentarea explic─ā importan╚øa SEO (optimizarea pentru motoarele de c─āutare) ├«n promovarea online a site-urilor, subliniind rolul s─āu ├«n atragerea de trafic relevant ╚Öi cre╚Öterea conversiilor. Se discut─ā despre strategii de optimizare a con╚øinutului, inclusiv utilizarea de cuvinte cheie specifice ╚Öi regionalizarea c─āut─ārii pentru afaceri locale. Concluzia este c─ā un SEO bine implementat poate genera rezultate semnificative ├«n atragerea clien╚øilor, mai ales ├«n contextul c─āut─ārilor regionale.Webdeveloper Ciprian Berescu
Webdeveloper Ciprian BerescuGabriel Curcudel
╠²
Prezentarea lui Ciprian Berescu la Online Career Day la Iasi despre Webdevelopment .Mituri Despre Antreprenoriat
Mituri Despre AntreprenoriatGabriel Curcudel
╠²
Documentul abordeaz─ā miturile comune despre antreprenoriat, subliniind c─ā nu este u╚Öor s─ā devii antreprenor. Exist─ā multe concep╚øii gre╚Öite, cum ar fi ideea c─ā se poate c├ó╚Ötiga rapid bani sau c─ā se poate avea un program flexibil, c├ónd, de fapt, munca necesit─ā mult─ā dedicare ╚Öi sacrificii personale. De asemenea, succesul nu este garantat ╚Öi produsele nu se v├ónd singure f─ār─ā eforturi suplimentare.Online Commercial Intention
Online Commercial IntentionGabriel Curcudel
╠²
The document discusses detecting online commercial intention (OCI) through a machine learning approach that classifies web pages and queries as commercial or non-commercial. It outlines the challenges of identifying OCI due to the lack of explicit commercial indicators in short search queries and presents a framework that improves classification accuracy using keywords and content from search results. The study highlights promising future research avenues, including understanding user intent timing and detecting more specific commercial intents across various domains.Ad
Recently uploaded (20)
FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography.pptx
FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography.pptxFIDO Alliance
╠²
FIDO Seminar: Evolving Landscape of Post-Quantum CryptographyEnhance GitHub Copilot using MCP - Enterprise version.pdf
Enhance GitHub Copilot using MCP - Enterprise version.pdfNilesh Gule
╠²
║▌║▌▀Ż deck related to the GitHub Copilot Bootcamp in Melbourne on 17 June 2025FIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptx
FIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptxFIDO Alliance
╠²
FIDO Seminar: Perspectives on Passkeys & Consumer AdoptionFIDO Seminar: Targeting Trust: The Future of Identity in the Workforce.pptx
FIDO Seminar: Targeting Trust: The Future of Identity in the Workforce.pptxFIDO Alliance
╠²
FIDO Seminar: Targeting Trust: The Future of Identity in the WorkforceWar_And_Cyber_3_Years_Of_Struggle_And_Lessons_For_Global_Security.pdf
War_And_Cyber_3_Years_Of_Struggle_And_Lessons_For_Global_Security.pdfbiswajitbanerjee38
╠²
Russia is one of the most aggressive nations when it comes to state coordinated cyberattacksŌĆŖŌĆöŌĆŖand Ukraine has been at the center of their crosshairs for 3 years. This report, provided the State Service of Special Communications and Information Protection of Ukraine contains an incredible amount of cybersecurity insights, showcasing the coordinated aggressive cyberwarfare campaigns of Russia against Ukraine.
It brings to the forefront that understanding your adversary, especially an aggressive nation state, is important for cyber defense. Knowing their motivations, capabilities, and tactics becomes an advantage when allocating resources for maximum impact.
Intelligence shows Russia is on a cyber rampage, leveraging FSB, SVR, and GRU resources to professionally target UkraineŌĆÖs critical infrastructures, military, and international diplomacy support efforts.
The number of total incidents against Ukraine, originating from Russia, has steadily increased from 1350 in 2021 to 4315 in 2024, but the number of actual critical incidents has been managed down from a high of 1048 in 2022 to a mere 59 in 2024ŌĆŖŌĆöŌĆŖshowcasing how the rapid detection and response to cyberattacks has been impacted by UkraineŌĆÖs improved cyber resilience.
Even against a much larger adversary, Ukraine is showcasing outstanding cybersecurity, enabled by strong strategies and sound tactics. There are lessons to learn for any enterprise that could potentially be targeted by aggressive nation states.
Definitely worth the read!GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdf
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdfPriyanka Aash
╠²
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing NowCrypto Super 500 - 14th Report - June2025.pdf
Crypto Super 500 - 14th Report - June2025.pdfStephen Perrenod
╠²
This OrionX's 14th semi-annual report on the state of the cryptocurrency mining market. The report focuses on Proof-of-Work cryptocurrencies since those use substantial supercomputer power to mint new coins and encode transactions on their blockchains. Only two make the cut this time, Bitcoin with $18 billion of annual economic value produced and Dogecoin with $1 billion. Bitcoin has now reached the Zettascale with typical hash rates of 0.9 Zettahashes per second. Bitcoin is powered by the world's largest decentralized supercomputer in a continuous winner take all lottery incentive network.OpenACC and Open Hackathons Monthly Highlights June 2025
OpenACC and Open Hackathons Monthly Highlights June 2025OpenACC
╠²
The OpenACC organization focuses on enhancing parallel computing skills and advancing interoperability in scientific applications through hackathons and training. The upcoming 2025 Open Accelerated Computing Summit (OACS) aims to explore the convergence of AI and HPC in scientific computing and foster knowledge sharing. This year's OACS welcomes talk submissions from a variety of topics, from Using Standard Language Parallelism to Computer Vision Applications. The document also highlights several open hackathons, a call to apply for NVIDIA Academic Grant Program and resources for optimizing scientific applications using OpenACC directives.Improving Data Integrity: Synchronization between EAM and ArcGIS Utility Netw...
Improving Data Integrity: Synchronization between EAM and ArcGIS Utility Netw...Safe Software
╠²
Utilities and water companies play a key role in the creation of clean drinking water. The creation and maintenance of clean drinking water is becoming a critical problem due to pollution and pressure on the environment. A lot of data is necessary to create clean drinking water. For fieldworkers, two types of data are key: Asset data in an asset management system (EAM for example) and Geographic data in a GIS (ArcGIS Utility Network ). Keeping this type of data up to date and in sync is a challenge for many organizations, leading to duplicating data and creating a bulk of extra attributes and data to keep everything in sync. Using FME, it is possible to synchronize Enterprise Asset Management (EAM) data with the ArcGIS Utility Network in real time. Changes (creation, modification, deletion) in ArcGIS Pro are relayed to EAM via FME, and vice versa. This ensures continuous synchronization of both systems without daily bulk updates, minimizes risks, and seamlessly integrates with ArcGIS Utility Network services. This presentation focuses on the use of FME at a Dutch water company, to create a sync between the asset management and GIS.Information Security Response Team Nepal_npCERT_Vice_President_Sudan_Jha.pdf
Information Security Response Team Nepal_npCERT_Vice_President_Sudan_Jha.pdfICT Frame Magazine Pvt. Ltd.
╠²
Artificial Intelligence (AI) is rapidly changing the face of cybersecurity across the globe. In Nepal, the shift is already underway. Vice President of the Information Security Response Team Nepal (npCERT) and Information Security Consultant at One Cover Pvt. Ltd., Sudan Jha, recently presented an in-depth workshop on how AI can strengthen national security and digital defenses.You are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
╠²
We live in an ever evolving landscape for cyber threats creating security risk for your production systems. Mitigating these risks requires participation throughout all stages from development through production delivery - and by every role including architects, developers QA and DevOps engineers, product owners and leadership. No one is excused! This session will cover examples of common mistakes or missed opportunities that can lead to vulnerabilities in production - and ways to do better throughout the development lifecycle.The Future of Data, AI, and AR: Innovation Inspired by You.pdf
The Future of Data, AI, and AR: Innovation Inspired by You.pdfSafe Software
╠²
The future of FME is inspired by you. We can't wait to show you what's ahead for FME and Safe Software. 10 Key Challenges for AI within the EU Data Protection Framework.pdf
10 Key Challenges for AI within the EU Data Protection Framework.pdfPriyanka Aash
╠²
10 Key Challenges for AI within the EU Data Protection FrameworkFIDO Seminar: New Data: Passkey Adoption in the Workforce.pptx
FIDO Seminar: New Data: Passkey Adoption in the Workforce.pptxFIDO Alliance
╠²
FIDO Seminar: New Data: Passkey Adoption in the WorkforceTechniques for Automatic Device Identification and Network Assignment.pdf
Techniques for Automatic Device Identification and Network Assignment.pdfPriyanka Aash
╠²
Techniques for Automatic Device Identification and Network AssignmentThe Future of Technology: 2025-2125 by Saikat Basu.pdf
The Future of Technology: 2025-2125 by Saikat Basu.pdfSaikat Basu
╠²
A peek into the next 100 years of technology. From Generative AI to Global AI networks to Martian Colonisation to Interstellar exploration to Industrial Nanotechnology to Artificial Consciousness, this is a journey you don't want to miss. Which ones excite you the most? Which ones are you apprehensive about? Feel free to comment! Let the conversation begin!"Database isolation: how we deal with hundreds of direct connections to the d...
"Database isolation: how we deal with hundreds of direct connections to the d...Fwdays
╠²
What can go wrong if you allow each service to access the database directly? In a startup, this seems like a quick and easy solution, but as the system scales, problems appear that no one could have guessed.
In my talk, I'll share Solidgate's experience in transforming its architecture: from the chaos of direct connections to a service-based data access model. I will talk about the transition stages, bottlenecks, and how isolation affected infrastructure support. I will honestly show what worked and what didn't. In short, we will analyze the controversy of this talk.Information Security Response Team Nepal_npCERT_Vice_President_Sudan_Jha.pdf
Information Security Response Team Nepal_npCERT_Vice_President_Sudan_Jha.pdfICT Frame Magazine Pvt. Ltd.
╠²
You are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
╠²
Ad
Prezentarea "Securitatea Aplicatiilor Online" de la ODO
- 3. Solutii folosite Servere WEB (IIS, Apache) Database (MySql,Oracle, MSSQL) Interpretoare (Php, PERL, ASP)
- 4. Codul scris SQL injection XSS CSRF/XSRF Email Injection Directory traversal
- 6. SQL Injection Atac asupra bazei de date http://www.example.com/view.php?id_cat=4 "SELECT * FROM data WHERE id_category = " + $_GET[ŌĆśidŌĆÖ] + ";" http://www.example.com/view.php?id_cat=4 OR 1=1 "SELECT * FROM data WHERE id = 1 OR 1=1;" OR 1=1
- 7. why ? Furtul de informatii Alterarea datelor Just for the fun of it Se intampla si la case mai mari 2007 Microsoft UK 2007 UN web site 2008 Kaspersky website
- 8. Protectie Tot input-ul trebuie verificat Criptarea datelor importante Backup zilnic Update la database server
- 9. Demonstratie
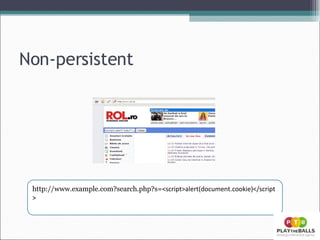
- 10. XSS Input-ul nu este verificat Este acceptat input-ul de HTML Tipuri : Non-persistent Persistent
- 12. Rezultatul :
- 13. persistent
- 14. CSRF/XSRF Impotriva site-urilor care folosesc autentificarile din coockie/session ŌĆ£ Hacker-ulŌĆØ ŌĆō are informatii despre site-ul pe care victima are access <img src=/slideshow/prezentarea-securitatea-aplicatiilor-online-de-la-odo/540898/ŌĆ£http:/www.other-example.com?deleteuser.php?u=vasileŌĆØ />
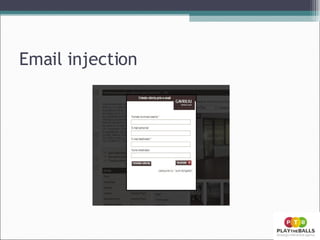
- 15. Email injection
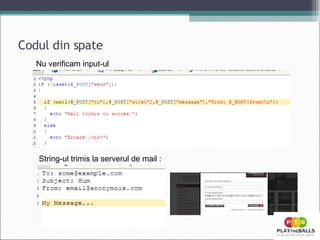
- 16. Codul din spate Nu verificam input-ul String-ul trimis la serverul de mail :
- 17. Directory traversal HTTP requests
- 18. ╠²
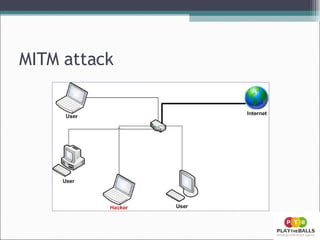
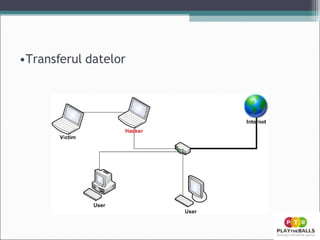
- 19. MITM attack
- 21. Demonstratie
- 22. Concluzii Verifica tot input-ul Informatii criptate Back-up Users canŌĆÖt be trusted Fii paranoic
