Python Programlama Dili
- 2. Genel Bak─▒┼¤ ŌĆó A├¦─▒k kaynakl─▒ ŌĆó Nesne y├Čnelimli ŌĆó Y├╝ksek seviyeli ŌĆó Yorumlamal─▒ ŌĆó Girintilere dayal─▒ basit s├Čz dizimi ŌĆó Ana Felsefesi : Kod Okunabilirli─¤i ŌĆó Kurum : Python Yaz─▒l─▒m Vakf─▒ ŌĆō https://www.python.org/psf/
- 3. Dil Tasar─▒mc─▒s─▒ (Guido van Rossem, 1991) 2005-2012 : Google GoogleŌĆÖdan sonra : Dropbox
- 5. Python Ad─▒ (Monty Python, ─░ngiliz Komedi Grubu) http://www.montypython.com/pythons
- 6. Python Kullanan ┼×irketler ŌĆó Google ŌĆó Amazon ŌĆó Facebook ŌĆó Spotify ŌĆó Wikipedia ŌĆó Instagram ŌĆó CERN ŌĆó NASA ŌĆó Reddit ŌĆó Yahoo! ŌĆó ve daha fazlas─▒ ŌĆ”
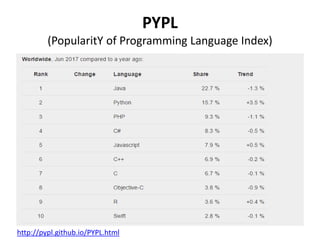
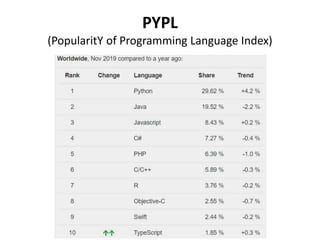
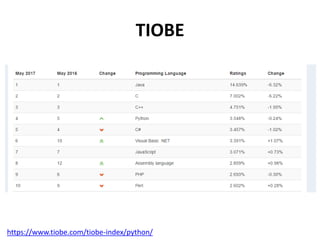
- 7. PYPL (PopularitY of Programming Language Index) http://pypl.github.io/PYPL.html
- 8. PYPL (PopularitY of Programming Language Index)
- 10. Python Neden Pop├╝ler? ŌĆó Kolay ├Č─¤renilebilir ŌĆó Gereksiz kod karma┼¤as─▒ yok ŌĆó Y├╝ksek seviyeli bir dil ŌĆó B├╝y├╝k bir topluluk deste─¤ine sahip ŌĆó ├ćoklu-platform uygulama geli┼¤tirme deste─¤i ŌĆó T├╝m bunlar nedeniyle ├¦ook fazla a├¦─▒k kaynakl─▒ projede tercih ediliyorŌĆ”
- 11. Python ile Neler Yap─▒labilir? ŌĆó Sistem & A─¤ Uygulamalar─▒ ŌĆó G├╝venlik & Hacking Ara├¦lar─▒ ŌĆó Web Uygulamalar─▒ ŌĆó Masa├╝st├╝ Uygulamalar ŌĆó API / RESTful / Microservice Uygulamalar─▒ ŌĆó Mobil Uygulamalar ŌĆó Bot & Crawler Uygulamalar─▒ ŌĆó Otomasyon & Ara├¦ Seti(Tool) Uygulamalar─▒ ŌĆó Oyun Uygulamalar─▒ ŌĆó Yapay Zeka Uygulamalar─▒ ŌĆō ML : Machine Learning ŌĆō DL : Deep Learning ŌĆō CV : Computer Vision ŌĆō NLP : Natural Language Processing ŌĆō Visualization ŌĆó Ve daha bir├¦okŌĆ”
- 12. Python IDEs (Geli┼¤tirme Ortamlar─▒) ŌĆó Visual Studio Code (Tavsiye) ŌĆō https://code.visualstudio.com/ ŌĆō Plugin : https://marketplace.visualstudio.com/items?itemName=ms-python.python ŌĆó PyCharm (Tavsiye) ŌĆō https://www.jetbrains.com/pycharm/download/#section=windows ŌĆó Notepad++ ŌĆō https://notepad-plus-plus.org/downloads/ ŌĆó Brackets ŌĆō http://brackets.io/ ŌĆó Eclipse ŌĆō https://www.eclipse.org/downloads/ ŌĆó PyDev ŌĆō http://www.pydev.org/ ŌĆō https://marketplace.eclipse.org/content/pydev-python-ide-eclipse ŌĆó Atom ŌĆō https://atom.io/
- 13. K├╝t├╝phaneler (The Python Standard Library, https://docs.python.org/3/library/) ŌĆó Markup Processing : docs.python.org/3/library/markup.html ŌĆō html : https://docs.python.org/3/library/html.html ŌĆō xml : https://docs.python.org/3/library/xml.html ŌĆó Internet Data Handling : https://docs.python.org/3/library/json.html ŌĆō email : https://docs.python.org/3/library/email.html ŌĆō json : https://docs.python.org/3/library/json.html ŌĆó Internet Protocols : docs.python.org/3/library/internet.html ŌĆō http : HTTP mod├╝l├╝ ŌĆō ftplib : FTP protokol istemci ŌĆō telnetlib : Telnet istemcisi ŌĆō xmlrpc : XMLRPC sunucu ve istemci mod├╝lleri ŌĆó Python Runtime : docs.python.org/3/library/python.html ŌĆó Networking : docs.python.org/3/library/ipc.html ŌĆó Internet Data Handling : docs.python.org/3/library/netdata.html ŌĆó Cryptographic Services: docs.python.org/3/library/crypto.html ŌĆó Data Compression : httpdocs.python.org/3/library/archiving.html
- 14. K├╝t├╝phaneler (Web) ŌĆó Django ŌĆō https://www.djangoproject.com/ ŌĆó Flask ŌĆō https://flask.palletsprojects.com/en/1.1.x/ ŌĆó CubicWeb Semantic Web Framework ŌĆō https://www.cubicweb.org/ ŌĆó CherryPy ŌĆō https://cherrypy.org/ ŌĆó Bottle ŌĆō https://bottlepy.org/docs/dev/
- 15. K├╝t├╝phaneler (├će┼¤itli) ŌĆó Requests : En ├╝nl├╝ http k├╝t├╝phanesidir. Kennetz Reitz geli┼¤tirdi. ŌĆō https://pypi.org/project/requests/ ŌĆó BeautifulSoup : HTML Ayr─▒┼¤t─▒rma K├╝t├╝phanesi ŌĆō https://www.crummy.com/software/BeautifulSoup/ ŌĆó Scrapy : HTML Ayr─▒┼¤t─▒rma K├╝t├╝phanesi ŌĆō https://scrapy.org/ ŌĆó Feedparser : RSS Besleme K├╝t├╝phanesi ŌĆō https://pypi.org/project/feedparser/ ŌĆó Paramiko : SSH2 Protokol Implementasyonu ŌĆō http://www.paramiko.org/ ŌĆó wxPython : The GUI Toolkit for Python ŌĆō https://wxpython.org/ ŌĆó Pillow : Python Imaging LibraryŌĆÖden fork edilmi┼¤tir. ŌĆō https://pypi.org/project/Pillow/ ŌĆó Twisted : A─¤ uygulamalar─▒ geli┼¤tirmek i├¦in haz─▒r k├╝t├╝phane. ŌĆō https://twistedmatrix.com/trac/ ŌĆó SQLAlchemy : Veritaban─▒ k├╝t├╝phanesidir. ŌĆō https://www.sqlalchemy.org/
- 16. K├╝t├╝phaneler (Oyun) ŌĆó Kivy Framework ŌĆō https://kivy.org ŌĆó Pygame ŌĆō https://www.pygame.org ŌĆó Pyglet ŌĆō http://pyglet.org/
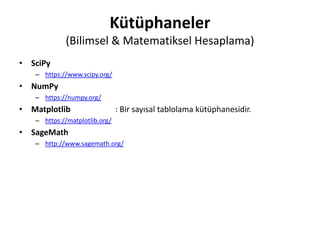
- 17. K├╝t├╝phaneler (Bilimsel & Matematiksel Hesaplama) ŌĆó SciPy ŌĆō https://www.scipy.org/ ŌĆó NumPy ŌĆō https://numpy.org/ ŌĆó Matplotlib : Bir say─▒sal tablolama k├╝t├╝phanesidir. ŌĆō https://matplotlib.org/ ŌĆó SageMath ŌĆō http://www.sagemath.org/
- 18. K├╝t├╝phaneler (Yapay Zeka) ŌĆó TensorFlow ŌĆō https://www.tensorflow.org/ ŌĆó PyTorch ŌĆō https://pytorch.org/ ŌĆó OpenCV ŌĆō https://opencv.org/ - https://pypi.org/project/opencv-python/ ŌĆó Keras ŌĆō http://keras.io/ ŌĆó Scikit-Learn ŌĆō https://scikit-learn.org/ ŌĆó CNTK ŌĆō https://github.com/microsoft/CNTK ŌĆó Theano ŌĆō https://github.com/Theano/Theano ŌĆó NLTK (Natural Language Toolkit) ŌĆō https://www.nltk.org/ ŌĆó NeuroLab ŌĆō https://pythonhosted.org/neurolab/ ŌĆó Deepy ŌĆō https://deepy.readthedocs.io/en/latest/ ŌĆó Ve daha bir├¦okŌĆ” ŌĆō http://www.cihanozhan.com/category/artificial-intelligence/
- 19. Awesome! ŌĆó Python Awesome ŌĆō https://pythonawesome.com/ ŌĆó Awesome Python ŌĆō https://github.com/vinta/awesome-python ŌĆó Awesome Python Applications ŌĆō https://github.com/mahmoud/awesome-python-applications
Editor's Notes
- #15: https://www.mediaclick.com.tr/blog/semantik-web-nedir