Quiz 1
âĒDownload as DOCX, PDFâĒ
0 likesâĒ87 views
Data, information, databases, database management systems, repositories, metadata, constraints, user interfaces, database applications, file processing systems, and multi-tier databases are key terms defined in the context of database design and management. A database stores and organizes related data, a database management system includes data definitions and constraints, and metadata provides context and summaries for understanding data.
1 of 1
Download to read offline

Recommended
Mca 303



Mca 303smumbahelp
Ėý
Dear students, get JNU 2021 Solved assignments and case study help by professionals.
Mail us at : help.mbaassignments@gmail.com
Call us at : 08263069601
Q1 (a)



Q1 (a)Dastan Kamaran
Ėý
c- information, a- data placed in context or summarized, b- centralized storehouse for all data definitions, d- organized collection of related data, e- includes data definitions and constraints, i- database management system, j- constraint, k- database application, l- distributed data stores that can be read from a single source, f- text and graphical displays that user interact with, h- supports 25-100 users and the user interface is accessible on the individual computer users, g- file processing systemMcq for final



Mcq for finalsazzadulbarihridoy
Ėý
This document contains questions about databases and networking concepts. It covers topics like database characteristics, roles, models, languages, and components. Regarding networks, it discusses transmission media, protocols, topologies, and applications like EDI and client/server computing. The questions are multiple choice designed to test understanding of fundamental database and networking concepts.Bangladesh Bank Assistant Maintenance Engineer Question Solution.



Bangladesh Bank Assistant Maintenance Engineer Question Solution.Engr. Md. Jamal Uddin Rayhan
Ėý
Maintenance Engineer Question Solution of Bangladesh Bank. assistant programmer job preparation Bangladesh bank1.introduction qb



1.introduction qbMohammed Shoaib
Ėý
1) Database systems provide several key advantages over file-based systems, including controlling redundancy, restricting unauthorized access, and representing complex relationships among data. They allow data to be stored logically in one place while supporting multiple views.
2) A DBMS allows defining data structures, manipulating and sharing databases for applications. It provides facilities for backup/recovery and enforcing integrity constraints.
3) A database administrator is responsible for authorizing access, coordinating use, and acquiring resources for the database and DBMS. Their role is to oversee the primary resource of the database and secondary resources of related software.Test03 solution



Test03 solutionfmbuthia
Ėý
The document is an operating system test from Professor Chu-Sing Yang on March 17, 2008. It contains 9 questions testing knowledge of processes, process state diagrams, context switching, synchronous vs asynchronous communication, automatic vs explicit buffering, fixed vs variable message sizes, the fork() system call, process memory layout, information in a process control block, reasons for process cooperation, sockets, and communication methods in client-server systems.A Reconfigurable Component-Based Problem Solving Environment



A Reconfigurable Component-Based Problem Solving EnvironmentSheila Sinclair
Ėý
This technical report describes a reconfigurable component-based problem solving environment called DISCWorld. The key features discussed are:
1) DISCWorld uses a data flow model represented as directed acyclic graphs (DAGs) of operators to integrate distributed computing components across networks.
2) It supports both long running simulations and parameter search applications by allowing complex processing requests to be composed graphically or through scripting and executed on heterogeneous platforms.
3) Operators can be simple "pure Java" implementations or wrappers to fast platform-specific implementations, and some operators may represent sub-graphs that can be reconfigured to run across multiple servers for faster execution.A ____________ is a disconnected, memory-resident representation o.docx



A ____________ is a disconnected, memory-resident representation o.docxransayo
Ėý
A DBA's responsibilities include managing the database, ensuring data quality and integrity, and supporting users. Key activities involve backup/recovery, performance monitoring, security management, and change management. DBAs require both technical skills with database systems as well as managerial/communication skills to work with various stakeholders.DELL EMC DEA-1TT5 Updated Dumps 2023



DELL EMC DEA-1TT5 Updated Dumps 2023VictoriaMeisel
Ėý
This document contains a practice exam for the DEA-1TT5 Associate - Information Storage and Management exam. It includes 18 multiple choice questions covering topics like capacity management, machine learning, Internet of Things, data protection, storage infrastructure, networking, file systems, software-defined networking, fibre channel, and hypervisors. The questions are accompanied by explanations of the correct answers.Lesson - 02 Network Design and Management



Lesson - 02 Network Design and ManagementAngel G Diaz
Ėý
The document discusses the systems development life cycle (SDLC) process for developing business systems. It describes the typical phases of SDLC - planning, analysis, design, implementation, and maintenance. It notes that a systems analyst is responsible for managing projects and guiding them through each SDLC phase. The document also provides an overview of some network modeling techniques for depicting connectivity within wide area, metropolitan area, and local area networks.Concepts and Applications of Information Technology IFSM.docx



Concepts and Applications of Information Technology IFSM.docxmaxinesmith73660
Ėý
Concepts and Applications of Information Technology
IFSM201-C806
Midterm Exam
Name:_________________________
Exam Directions:
The exam is open book and notes are allowed
You will have 2 days to complete the exam
Select the best answer for each question
Place your answers on your answer sheet
The completed answer sheet should be posted in the Assignment Folder by the assigned date and time.
Part 1 - Multiple Choice (25 points total)
Identify the choice that best completes the statement or answers the question.
____ 1. Ultra-mobile PCs are also called ____.
a. mini computers c. range computers
b. handheld computers d. frame computers
____ 2. A ____ is a collection of hardware and other devices that are connected together so that users can share
hardware, software, and data, as well as electronically communicate with each other.
a. computer bank c. data bank
b. database d. computer network
____ 3. Similar to the way an IP address or domain name uniquely identifies a computer on the Internet, a ____
uniquely identifies a Web page.
a. universal resource identifier (URI) c. uniform resource locator (URL)
b. Web ID (WID) d. Web resource identifier (WRI)
____ 4. Each place value in a binary number represents ____ raised to the appropriate power.
a. 0 c. 2
b. 1 d. 10
____ 5. A ____ is an electronic path over which data can travel.
a. bus c. word
b. lane d. cache memory
____ 6. A USB ____ is a device that plugs into your PCâs USB port to convert one port into several USB ports.
a. hub c. bus
b. module d. connector
____ 7. The elements shown in the accompanying figure are ____, which are used to organize related documents.
a. files c. folders
b. drives d. clipboards
Case-Based Critical Thinking Questions
Case 3-1
Dan is a small business owner who depends on his computer to keep track of customer and sales data. He
is investigating storage options because it is critical for him to ensure that his data is safe in the event of a
computer failure.
____ 8. A friend of Dan suggested to him that he can use an external hard drive for his data storage and backup
needs. To use an external hard drive, Dan should make sure that his computer has an available USB or
____ port.
a. ScanDisk c. flash
b. Zip d. FireWire
____ 9. ____ includes all the programs that allow a user to perform specific tasks on a computer, such as writing a
letter.
a. System software c. Application software
b. Utility programs d. Background programs
____ 10. A computerâs ____ is a collection of programs that manage and coordinate the activities taking place
within a computer system.
a. database system c. application system
b. storage system d. operating system
____ 11. ____ refers to the ability of an operating system to work with more than one program at one time.
a. Multidimensional c. Polyprogramming
b. Multiprogramming d. Multitaski.Software Engineering Question Bank all.pdf



Software Engineering Question Bank all.pdfkarthikaparthasarath
Ėý
All Units covered MCQ and Part A,B & C Improve cyber resiliency and protect data from cyber ransomware threats by us...



Improve cyber resiliency and protect data from cyber ransomware threats by us...Principled Technologies
Ėý
With Dell Technologies PowerProtect Cyber Recovery with CyberSense
Conclusion
Organizations must consider many attack vectors when constructing a data protection plan. This includes protecting all data, but most importantly, the critical data imperative to operations. PowerProtect Cyber Recovery isolates the critical data and helps ensure proper recovery of data in the event of a cyberattack. Cyber Recovery uses ML-based analytics, in CyberSense, to determine the integrity of the data in the vault and identify clean backup data for recovery. In our testing, we found that PowerProtect Cyber Recovery detected infection in SQL database pagesâsomething that a competing solution could not do. PowerProtect Cyber Recovery also required fewer backups than a competing solution to determine corruption in the data. In addition to all this and more, the Cyber Recovery solution delivers many recovery options, relying on uncompromised data from the vault for an efficient and smooth return to operations.
Unit 5



Unit 5vamsitricks
Ėý
The document discusses database issues related to mobile computing. It describes how mobile devices cache data from servers to reduce latency when the device is offline. The cached data is stored locally in a process called hoarding. It discusses different database architectures and cache invalidation mechanisms used to maintain consistency between cached and server data. These include stateless asynchronous, stateful asynchronous, and stateful synchronous approaches. Maintaining cache consistency through invalidation reports and periodic updates is important for reliable usage of cached data on mobile devices.Mobile computing unit 5



Mobile computing unit 5Assistant Professor
Ėý
The document discusses database issues related to mobile computing. It describes how mobile devices cache data from servers to reduce latency when the device is offline. The cached data is referred to as being "hoarded" in the device database. It discusses different database architectures including one-tier architectures where the database is specific to a mobile device and two-tier architectures involving client-server models. It also describes different cache invalidation mechanisms used to maintain consistency between cached data on devices and data on servers.1989 Joyce: An Object-Oriented Decision Tree Builder



1989 Joyce: An Object-Oriented Decision Tree BuilderBob Marcus
Ėý
Joyce was a toolkit for building visual programing environments that allowed domain experts to create decision trees.Joyce: An Object-oriented Decision Tree Builder 1989



Joyce: An Object-oriented Decision Tree Builder 1989Bob Marcus
Ėý
Describes a prototype visual decision tree building development environment developed in Lisp on a SymbolicsE.F. Codd (1970). Evolution of Current Generation Database Tech.docx



E.F. Codd (1970). Evolution of Current Generation Database Tech.docxjacksnathalie
Ėý
E.F. Codd (1970). Evolution of Current Generation Database Technologies. Communications of the ACM archive. Vol 13. Issue 6(June 1970
The database technology system can be traced back to a flat file, whose function was to keep data. These flat files surfaced in the 1960s and had many disadvantages. During the period 1968 to 1980, referred to as the Hierarchical error since the Hierarchical Database was developed, the IBM joined NAA to come up with GUAM, the first DBMS called the Information Management System (IMS). The following are the step by step evolution of the three major database systems since then, with regard to the specific model layers:
(a)Hierarchical Model: Here, this IMS was built by IBM in collaboration with Rockwell, and it becomes the major database system in the 1970s and 1980s. This model entailed the relation of files in a child -parent example, whereby at most one parent file hosted each child file.
(b)The Network Model was first developed by Charles Bachmann at Honeywell called the Integrated Data Store (IDS), which was considered fit for international use (standardization) in the year 1971 by the CODASYL body, meaning the Conference on Data Systems Languages. Here, files are perceived as members and owners, whereby each member may harbor many owners. Network Schema, Data Management Language and Sub-Schema are the three components associated to this model. The CODASYL DBTG was the most popular network model during those times.
(c) The Relational Database Model was developed in 1970 by E.F. Codd. He proposed the construction of this model, which saw to the onset of two major projects in the IBM's San Jose Lab. The model developed several branches or other forms of it like the INGRES, a University of California invention, which became widespread and the POSTGRES which was later developed into the Informix. The lab in San Jose had developed a System R, and this gradually shifted into the DB2, a relational model product. This model constitutes the use of instance and schema, with instance comprising of a table with columns and rows and the schema guiding on the structure used. It was wholly developed under the mathematical concept of set theory and the predicate logic. This model became stronger and fully effective in the 1980s, marked with the increase in the development of more relational based DBMS and the introduction of the SQL standard in the ISO and ANSI models.
The other database models were developed similarly in stages. Peter Chen came up with the Entity-Relationship model in the year 1976. This was followed by the 1985 development of the Object-Oriented Database Models. In the 1990s, an important development occurred, which entailed the addition of object-orientation in relational models. This time frame also witnessed the addition of more application areas or units such as OLAP, data warehouse, the web, enterprise resource planning and even the internet. The year 1991 saw the creation of Microsoft Ships Acce ...Mse unit5



Mse unit5NikithaNag
Ėý
The document discusses several topics related to mobile systems engineering including:
1. Data storage options for Android applications including SharedPreferences, internal storage, external storage, SQLite databases, and network connections.
2. The concept of mobile cloud computing including definitions, architectures, advantages and issues.
3. Context-aware computing including definitions, basic functions, and a layered framework.
4. The Internet of Things including definitions, characteristics, enabling technologies, and applications across various domains.A cloud environment for backup and data storage



A cloud environment for backup and data storageIGEEKS TECHNOLOGIES
Ėý
The document proposes a cloud environment for backup and data storage using remote servers that can be accessed through the Internet. It involves using the disks of cluster nodes as a global storage system with PVFS2 parallel file system for improved performance. The proposed system aims to increase data availability and reduce information loss by storing data on a private cloud using PVFS2 and developing a multiplatform client application for fast data transfer. It allows reuse of existing infrastructure to reduce costs and gives users experience of managing a private cloud.A systematic review of in-memory database over multi-tenancy



A systematic review of in-memory database over multi-tenancyIJECEIAES
Ėý
The significant cost and time are essential to obtain a comprehensive response, the response time to a query across a peer-to-peer database is one of the most challenging issues. This is particularly exact when dealing with large-scale data processing, where the traditional approach of processing data on a single machine may not be sufficient. The need for a scalable, reliable, and secure data processing system is becoming increasingly important. Managing a single in-memory database instance for multiple tenants is often easier than managing separate databases for each tenant. The research work is focused on scalability with multi-tenancy and more efficiency with a faster querying performance using in-memory database approach. We compare the performance of a row-oriented approach and column-oriented approach on our benchmark human resources (HR) schema using Oracle TimesTen in-memory database. Also, we captured some of the key advantages on optimization dimension(s) are the traditional approach, late-materialization, compression and invisible join on column-store (c-store) and row-base. When compression and late materialization are enabled in a query set; it improves the overall performance of query sets. In particular, the paper aims to elucidate the motivations behind multi-tenant application requirements concerning the database engine and highlight major designs over in-memory database for the tenancy approach on cloud.A cloud enviroment for backup and data storage



A cloud enviroment for backup and data storageIGEEKS TECHNOLOGIES
Ėý
IGeekS Technologies (Make Final Year Project)
No: 19, MN Complex, 2nd Cross,
Sampige Main Road, Malleswaram
Bangalore- 560003.
Phone No: 080-32487434 /9590544567 / 9739066172
Mail: nandu@igeekstechnologies.com , nanduigeeks2010@gmail.com
Land mark : Near to Mantri Mall, Malleswaram BangaloreTowards Secure and Dependable Storage Services in Cloud Computing 



Towards Secure and Dependable Storage Services in Cloud Computing IJMER
Ėý
Electrical Engineering,Mechanical Engineering,Computer Science & Engineering,Artificial Intelligence,Material Science,Mathematicse,Applied physics,Applied Chemistry,Electronics Engineering,Instrumentation Engineering,Civil Engineering,Earth quake Engineering,Structural engineering,There are four types of personnel involved in a DBMS- implementers- en.docx



There are four types of personnel involved in a DBMS- implementers- en.docxrochellej1
Ėý
There are four types of personnel involved in a DBMS: implementers, end users, database administrator, and application programmers. Who would usually perform the following for an inventory system in a large company?
(a) Update the number of stocks for specific items
(b) Modify a query optimizer
(c) Change the structure of the database to include more information on each item
(d) Implement a module for user login
Solution
(a) Update the number of stocks for specific items
implementters does the work of insert, update, delete and select from database as required by the application program and also it can modify the database contents as per need via program code or via database gui or via query
(b) Modify a query optimizer
this task is usually performed by end user as they can optimize query as per their need or according to the data and the format they want.
(c) Change the structure of the database to include more information on each item
this permission is only with the dba (Database Administrator)
(d) Implement a module for user login
application programmer does this work of adding and deleting any new module to the application program and implementer connects it to the database via Queries
.Custom Software Development Checklist by Michael Cordova



Custom Software Development Checklist by Michael Cordovahoolikar77
Ėý
The document provides a checklist of questions to facilitate custom software development projects. It includes questions about business considerations like project timeline and costs, the nature of the application including desired technologies and security needs, data volume and types, and importing of existing data. Answering the checklist questions upfront helps guide analysis and requirements gathering for the new software system.Basic computer mcqs



Basic computer mcqsAsadMehboob4
Ėý
The document contains 10 multiple choice questions about database management systems and design.
The questions cover topics such as:
- The order of elements in a data hierarchy (bit, byte, record, etc.)
- Characteristics of network data structures
- Problems with file management systems
- Components of a database management system
- Functions of a database
- Languages used to access database systems
The answers to the 10 questions are provided at the end.DETECTION METHOD FOR CLASSIFYING MALICIOUS FIRMWARE



DETECTION METHOD FOR CLASSIFYING MALICIOUS FIRMWAREIJNSA Journal
Ėý
This document proposes using deep learning to classify firmware as malicious or benign by converting firmware binaries into small grayscale images and training convolutional neural networks (CNNs) on these images. Testing of a MobileNetV2 CNN achieved over 90% accuracy on the image classifications. Decision trees and random forests were also applied and achieved similar or higher accuracy than the CNN. The document concludes that machine learning methods show promise for detecting malicious firmware updates through analyzing the patterns in converted firmware image files.AdistributedinfrastructuresupportingpersonalizedservicesfortheMobileWeb



AdistributedinfrastructuresupportingpersonalizedservicesfortheMobileWebJim Webb
Ėý
This document proposes an infrastructure and dispatching algorithms to efficiently support personalized services for the mobile web while balancing performance and privacy requirements. The infrastructure consists of a centralized core node integrated with distributed edge nodes located close to clients. Three dispatching algorithms are presented: 1) A Performance and Privacy algorithm that prioritizes privacy while balancing load across nodes; 2) A Performance-oriented algorithm that prioritizes performance by processing most requests at edge nodes; 3) A Privacy-oriented algorithm that prioritizes privacy by processing all sensitive requests at the core node. The document evaluates how well each algorithm balances performance and privacy.Field properties



Field propertiesDastan Kamaran
Ėý
The document discusses various field properties in Microsoft Access including:
- Format - Controls how data is displayed but not stored. Includes predefined and custom formats using symbols.
- Input mask - Controls valid data entry format using mask characters like 0, 9, #, etc. Examples include phone numbers and dates.
- Validation rule - Specifies requirements for data entered using conditions like <, >, Like. accompanied by a validation text message.
- Default value - Automatically populates a value for new records, like a default city name. Only applies to new records, not existing ones.Create table relationships



Create table relationshipsDastan Kamaran
Ėý
Relationships between tables are critical in a relational database because they link separated data back together and impact how queries retrieve answers. There are three main relationship types: one-to-many, which is most common; many-to-many, used in transaction and student databases; and one-to-one, which is rare. A primary key uniquely identifies records in a table and cannot be duplicated or contain null values. Foreign keys in one table reference the primary key of another table to represent relationships between them. Relationships are depicted in entity diagrams by drawing lines between matching keys and labeling the "one" side with 1 and the "many" side with â.More Related Content
Similar to Quiz 1 (20)
DELL EMC DEA-1TT5 Updated Dumps 2023



DELL EMC DEA-1TT5 Updated Dumps 2023VictoriaMeisel
Ėý
This document contains a practice exam for the DEA-1TT5 Associate - Information Storage and Management exam. It includes 18 multiple choice questions covering topics like capacity management, machine learning, Internet of Things, data protection, storage infrastructure, networking, file systems, software-defined networking, fibre channel, and hypervisors. The questions are accompanied by explanations of the correct answers.Lesson - 02 Network Design and Management



Lesson - 02 Network Design and ManagementAngel G Diaz
Ėý
The document discusses the systems development life cycle (SDLC) process for developing business systems. It describes the typical phases of SDLC - planning, analysis, design, implementation, and maintenance. It notes that a systems analyst is responsible for managing projects and guiding them through each SDLC phase. The document also provides an overview of some network modeling techniques for depicting connectivity within wide area, metropolitan area, and local area networks.Concepts and Applications of Information Technology IFSM.docx



Concepts and Applications of Information Technology IFSM.docxmaxinesmith73660
Ėý
Concepts and Applications of Information Technology
IFSM201-C806
Midterm Exam
Name:_________________________
Exam Directions:
The exam is open book and notes are allowed
You will have 2 days to complete the exam
Select the best answer for each question
Place your answers on your answer sheet
The completed answer sheet should be posted in the Assignment Folder by the assigned date and time.
Part 1 - Multiple Choice (25 points total)
Identify the choice that best completes the statement or answers the question.
____ 1. Ultra-mobile PCs are also called ____.
a. mini computers c. range computers
b. handheld computers d. frame computers
____ 2. A ____ is a collection of hardware and other devices that are connected together so that users can share
hardware, software, and data, as well as electronically communicate with each other.
a. computer bank c. data bank
b. database d. computer network
____ 3. Similar to the way an IP address or domain name uniquely identifies a computer on the Internet, a ____
uniquely identifies a Web page.
a. universal resource identifier (URI) c. uniform resource locator (URL)
b. Web ID (WID) d. Web resource identifier (WRI)
____ 4. Each place value in a binary number represents ____ raised to the appropriate power.
a. 0 c. 2
b. 1 d. 10
____ 5. A ____ is an electronic path over which data can travel.
a. bus c. word
b. lane d. cache memory
____ 6. A USB ____ is a device that plugs into your PCâs USB port to convert one port into several USB ports.
a. hub c. bus
b. module d. connector
____ 7. The elements shown in the accompanying figure are ____, which are used to organize related documents.
a. files c. folders
b. drives d. clipboards
Case-Based Critical Thinking Questions
Case 3-1
Dan is a small business owner who depends on his computer to keep track of customer and sales data. He
is investigating storage options because it is critical for him to ensure that his data is safe in the event of a
computer failure.
____ 8. A friend of Dan suggested to him that he can use an external hard drive for his data storage and backup
needs. To use an external hard drive, Dan should make sure that his computer has an available USB or
____ port.
a. ScanDisk c. flash
b. Zip d. FireWire
____ 9. ____ includes all the programs that allow a user to perform specific tasks on a computer, such as writing a
letter.
a. System software c. Application software
b. Utility programs d. Background programs
____ 10. A computerâs ____ is a collection of programs that manage and coordinate the activities taking place
within a computer system.
a. database system c. application system
b. storage system d. operating system
____ 11. ____ refers to the ability of an operating system to work with more than one program at one time.
a. Multidimensional c. Polyprogramming
b. Multiprogramming d. Multitaski.Software Engineering Question Bank all.pdf



Software Engineering Question Bank all.pdfkarthikaparthasarath
Ėý
All Units covered MCQ and Part A,B & C Improve cyber resiliency and protect data from cyber ransomware threats by us...



Improve cyber resiliency and protect data from cyber ransomware threats by us...Principled Technologies
Ėý
With Dell Technologies PowerProtect Cyber Recovery with CyberSense
Conclusion
Organizations must consider many attack vectors when constructing a data protection plan. This includes protecting all data, but most importantly, the critical data imperative to operations. PowerProtect Cyber Recovery isolates the critical data and helps ensure proper recovery of data in the event of a cyberattack. Cyber Recovery uses ML-based analytics, in CyberSense, to determine the integrity of the data in the vault and identify clean backup data for recovery. In our testing, we found that PowerProtect Cyber Recovery detected infection in SQL database pagesâsomething that a competing solution could not do. PowerProtect Cyber Recovery also required fewer backups than a competing solution to determine corruption in the data. In addition to all this and more, the Cyber Recovery solution delivers many recovery options, relying on uncompromised data from the vault for an efficient and smooth return to operations.
Unit 5



Unit 5vamsitricks
Ėý
The document discusses database issues related to mobile computing. It describes how mobile devices cache data from servers to reduce latency when the device is offline. The cached data is stored locally in a process called hoarding. It discusses different database architectures and cache invalidation mechanisms used to maintain consistency between cached and server data. These include stateless asynchronous, stateful asynchronous, and stateful synchronous approaches. Maintaining cache consistency through invalidation reports and periodic updates is important for reliable usage of cached data on mobile devices.Mobile computing unit 5



Mobile computing unit 5Assistant Professor
Ėý
The document discusses database issues related to mobile computing. It describes how mobile devices cache data from servers to reduce latency when the device is offline. The cached data is referred to as being "hoarded" in the device database. It discusses different database architectures including one-tier architectures where the database is specific to a mobile device and two-tier architectures involving client-server models. It also describes different cache invalidation mechanisms used to maintain consistency between cached data on devices and data on servers.1989 Joyce: An Object-Oriented Decision Tree Builder



1989 Joyce: An Object-Oriented Decision Tree BuilderBob Marcus
Ėý
Joyce was a toolkit for building visual programing environments that allowed domain experts to create decision trees.Joyce: An Object-oriented Decision Tree Builder 1989



Joyce: An Object-oriented Decision Tree Builder 1989Bob Marcus
Ėý
Describes a prototype visual decision tree building development environment developed in Lisp on a SymbolicsE.F. Codd (1970). Evolution of Current Generation Database Tech.docx



E.F. Codd (1970). Evolution of Current Generation Database Tech.docxjacksnathalie
Ėý
E.F. Codd (1970). Evolution of Current Generation Database Technologies. Communications of the ACM archive. Vol 13. Issue 6(June 1970
The database technology system can be traced back to a flat file, whose function was to keep data. These flat files surfaced in the 1960s and had many disadvantages. During the period 1968 to 1980, referred to as the Hierarchical error since the Hierarchical Database was developed, the IBM joined NAA to come up with GUAM, the first DBMS called the Information Management System (IMS). The following are the step by step evolution of the three major database systems since then, with regard to the specific model layers:
(a)Hierarchical Model: Here, this IMS was built by IBM in collaboration with Rockwell, and it becomes the major database system in the 1970s and 1980s. This model entailed the relation of files in a child -parent example, whereby at most one parent file hosted each child file.
(b)The Network Model was first developed by Charles Bachmann at Honeywell called the Integrated Data Store (IDS), which was considered fit for international use (standardization) in the year 1971 by the CODASYL body, meaning the Conference on Data Systems Languages. Here, files are perceived as members and owners, whereby each member may harbor many owners. Network Schema, Data Management Language and Sub-Schema are the three components associated to this model. The CODASYL DBTG was the most popular network model during those times.
(c) The Relational Database Model was developed in 1970 by E.F. Codd. He proposed the construction of this model, which saw to the onset of two major projects in the IBM's San Jose Lab. The model developed several branches or other forms of it like the INGRES, a University of California invention, which became widespread and the POSTGRES which was later developed into the Informix. The lab in San Jose had developed a System R, and this gradually shifted into the DB2, a relational model product. This model constitutes the use of instance and schema, with instance comprising of a table with columns and rows and the schema guiding on the structure used. It was wholly developed under the mathematical concept of set theory and the predicate logic. This model became stronger and fully effective in the 1980s, marked with the increase in the development of more relational based DBMS and the introduction of the SQL standard in the ISO and ANSI models.
The other database models were developed similarly in stages. Peter Chen came up with the Entity-Relationship model in the year 1976. This was followed by the 1985 development of the Object-Oriented Database Models. In the 1990s, an important development occurred, which entailed the addition of object-orientation in relational models. This time frame also witnessed the addition of more application areas or units such as OLAP, data warehouse, the web, enterprise resource planning and even the internet. The year 1991 saw the creation of Microsoft Ships Acce ...Mse unit5



Mse unit5NikithaNag
Ėý
The document discusses several topics related to mobile systems engineering including:
1. Data storage options for Android applications including SharedPreferences, internal storage, external storage, SQLite databases, and network connections.
2. The concept of mobile cloud computing including definitions, architectures, advantages and issues.
3. Context-aware computing including definitions, basic functions, and a layered framework.
4. The Internet of Things including definitions, characteristics, enabling technologies, and applications across various domains.A cloud environment for backup and data storage



A cloud environment for backup and data storageIGEEKS TECHNOLOGIES
Ėý
The document proposes a cloud environment for backup and data storage using remote servers that can be accessed through the Internet. It involves using the disks of cluster nodes as a global storage system with PVFS2 parallel file system for improved performance. The proposed system aims to increase data availability and reduce information loss by storing data on a private cloud using PVFS2 and developing a multiplatform client application for fast data transfer. It allows reuse of existing infrastructure to reduce costs and gives users experience of managing a private cloud.A systematic review of in-memory database over multi-tenancy



A systematic review of in-memory database over multi-tenancyIJECEIAES
Ėý
The significant cost and time are essential to obtain a comprehensive response, the response time to a query across a peer-to-peer database is one of the most challenging issues. This is particularly exact when dealing with large-scale data processing, where the traditional approach of processing data on a single machine may not be sufficient. The need for a scalable, reliable, and secure data processing system is becoming increasingly important. Managing a single in-memory database instance for multiple tenants is often easier than managing separate databases for each tenant. The research work is focused on scalability with multi-tenancy and more efficiency with a faster querying performance using in-memory database approach. We compare the performance of a row-oriented approach and column-oriented approach on our benchmark human resources (HR) schema using Oracle TimesTen in-memory database. Also, we captured some of the key advantages on optimization dimension(s) are the traditional approach, late-materialization, compression and invisible join on column-store (c-store) and row-base. When compression and late materialization are enabled in a query set; it improves the overall performance of query sets. In particular, the paper aims to elucidate the motivations behind multi-tenant application requirements concerning the database engine and highlight major designs over in-memory database for the tenancy approach on cloud.A cloud enviroment for backup and data storage



A cloud enviroment for backup and data storageIGEEKS TECHNOLOGIES
Ėý
IGeekS Technologies (Make Final Year Project)
No: 19, MN Complex, 2nd Cross,
Sampige Main Road, Malleswaram
Bangalore- 560003.
Phone No: 080-32487434 /9590544567 / 9739066172
Mail: nandu@igeekstechnologies.com , nanduigeeks2010@gmail.com
Land mark : Near to Mantri Mall, Malleswaram BangaloreTowards Secure and Dependable Storage Services in Cloud Computing 



Towards Secure and Dependable Storage Services in Cloud Computing IJMER
Ėý
Electrical Engineering,Mechanical Engineering,Computer Science & Engineering,Artificial Intelligence,Material Science,Mathematicse,Applied physics,Applied Chemistry,Electronics Engineering,Instrumentation Engineering,Civil Engineering,Earth quake Engineering,Structural engineering,There are four types of personnel involved in a DBMS- implementers- en.docx



There are four types of personnel involved in a DBMS- implementers- en.docxrochellej1
Ėý
There are four types of personnel involved in a DBMS: implementers, end users, database administrator, and application programmers. Who would usually perform the following for an inventory system in a large company?
(a) Update the number of stocks for specific items
(b) Modify a query optimizer
(c) Change the structure of the database to include more information on each item
(d) Implement a module for user login
Solution
(a) Update the number of stocks for specific items
implementters does the work of insert, update, delete and select from database as required by the application program and also it can modify the database contents as per need via program code or via database gui or via query
(b) Modify a query optimizer
this task is usually performed by end user as they can optimize query as per their need or according to the data and the format they want.
(c) Change the structure of the database to include more information on each item
this permission is only with the dba (Database Administrator)
(d) Implement a module for user login
application programmer does this work of adding and deleting any new module to the application program and implementer connects it to the database via Queries
.Custom Software Development Checklist by Michael Cordova



Custom Software Development Checklist by Michael Cordovahoolikar77
Ėý
The document provides a checklist of questions to facilitate custom software development projects. It includes questions about business considerations like project timeline and costs, the nature of the application including desired technologies and security needs, data volume and types, and importing of existing data. Answering the checklist questions upfront helps guide analysis and requirements gathering for the new software system.Basic computer mcqs



Basic computer mcqsAsadMehboob4
Ėý
The document contains 10 multiple choice questions about database management systems and design.
The questions cover topics such as:
- The order of elements in a data hierarchy (bit, byte, record, etc.)
- Characteristics of network data structures
- Problems with file management systems
- Components of a database management system
- Functions of a database
- Languages used to access database systems
The answers to the 10 questions are provided at the end.DETECTION METHOD FOR CLASSIFYING MALICIOUS FIRMWARE



DETECTION METHOD FOR CLASSIFYING MALICIOUS FIRMWAREIJNSA Journal
Ėý
This document proposes using deep learning to classify firmware as malicious or benign by converting firmware binaries into small grayscale images and training convolutional neural networks (CNNs) on these images. Testing of a MobileNetV2 CNN achieved over 90% accuracy on the image classifications. Decision trees and random forests were also applied and achieved similar or higher accuracy than the CNN. The document concludes that machine learning methods show promise for detecting malicious firmware updates through analyzing the patterns in converted firmware image files.AdistributedinfrastructuresupportingpersonalizedservicesfortheMobileWeb



AdistributedinfrastructuresupportingpersonalizedservicesfortheMobileWebJim Webb
Ėý
This document proposes an infrastructure and dispatching algorithms to efficiently support personalized services for the mobile web while balancing performance and privacy requirements. The infrastructure consists of a centralized core node integrated with distributed edge nodes located close to clients. Three dispatching algorithms are presented: 1) A Performance and Privacy algorithm that prioritizes privacy while balancing load across nodes; 2) A Performance-oriented algorithm that prioritizes performance by processing most requests at edge nodes; 3) A Privacy-oriented algorithm that prioritizes privacy by processing all sensitive requests at the core node. The document evaluates how well each algorithm balances performance and privacy.Improve cyber resiliency and protect data from cyber ransomware threats by us...



Improve cyber resiliency and protect data from cyber ransomware threats by us...Principled Technologies
Ėý
More from Dastan Kamaran (6)
Field properties



Field propertiesDastan Kamaran
Ėý
The document discusses various field properties in Microsoft Access including:
- Format - Controls how data is displayed but not stored. Includes predefined and custom formats using symbols.
- Input mask - Controls valid data entry format using mask characters like 0, 9, #, etc. Examples include phone numbers and dates.
- Validation rule - Specifies requirements for data entered using conditions like <, >, Like. accompanied by a validation text message.
- Default value - Automatically populates a value for new records, like a default city name. Only applies to new records, not existing ones.Create table relationships



Create table relationshipsDastan Kamaran
Ėý
Relationships between tables are critical in a relational database because they link separated data back together and impact how queries retrieve answers. There are three main relationship types: one-to-many, which is most common; many-to-many, used in transaction and student databases; and one-to-one, which is rare. A primary key uniquely identifies records in a table and cannot be duplicated or contain null values. Foreign keys in one table reference the primary key of another table to represent relationships between them. Relationships are depicted in entity diagrams by drawing lines between matching keys and labeling the "one" side with 1 and the "many" side with â.Field properties



Field propertiesDastan Kamaran
Ėý
The document discusses various field properties in Microsoft Access including:
1. Format - Controls how data is displayed but not stored, with predefined and custom formats using symbols.
2. Input mask - Allows controlling data entry format using character placeholders.
3. Validation rule - Specifies requirements for data entered using expressions. Validation text displays error messages.
4. Default value - Automatically populates a field value for new records.Create table relationships



Create table relationshipsDastan Kamaran
Ėý
Relationships between tables are critical in a relational database because they link data separated across tables and impact how queries retrieve answers. There are three main relationship types: one-to-many, which is most common; many-to-many, used in transaction and student databases; and one-to-one, which is rare. A primary key uniquely identifies records in a table and cannot be duplicated or contain null values. Foreign keys in one table reference the primary key of another table to represent relationships. Relationships are defined by matching keys between tables which must have the same data type and field size.Oop lecture1-chapter1(review of java)



Oop lecture1-chapter1(review of java)Dastan Kamaran
Ėý
This document outlines the syllabus for an Object Oriented Programming course in Java. The course aims to teach students the principles of OOP using Java, including classes, objects, inheritance, polymorphism, exceptions handling, and more. It covers topics like Java basics, GUI programming, JDBC, collections, and multithreading. The course objectives are to enable students to write Java programs that solve problems and demonstrate good OOP skills. The content includes revising Java principles, learning about classes, interfaces, packages and more.Oop lecture1-chapter1(review of java)



Oop lecture1-chapter1(review of java)Dastan Kamaran
Ėý
This document outlines the syllabus for an Object Oriented Programming course in Java. The course aims to teach students the principles of OOP using Java, including classes, objects, inheritance, polymorphism, interfaces, exceptions handling, and more. It will cover both programming concepts in Java as well as GUI, database connectivity, collections, and multithreading. The course content is presented over several classes and includes lectures, practical sessions, and assessed exercises.Recently uploaded (20)
Cost sheet. with basics and formats of sheet



Cost sheet. with basics and formats of sheetsupreetk82004
Ėý
Cost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetNew Income Tax Bill - Capital Gains .pdf



New Income Tax Bill - Capital Gains .pdfHarshilShah134194
Ėý
The #IncomeTaxBill 2025 simplifies capital gains taxation by removing exemptions, restricting tax benefits to long-term gains, and limiting indexation. Here is our detailed analysis of the proposed changes.
HIRE MUYERN TRUST HACKER FOR AUTHENTIC CYBER SERVICES



HIRE MUYERN TRUST HACKER FOR AUTHENTIC CYBER SERVICESanastasiapenova16
Ėý
Itâs hard to imagine the frustration and helplessness a 65-year-old man with limited computer skills must feel when facing the aftermath of a crypto scam. Recovering a hacked trading wallet can feel like an absolute nightmare, especially when every step seems to lead you into an endless loop of failed solutions. Thatâs exactly what I went through over the past four weeks. After my trading wallet was compromised, the hacker changed my email address, password, and even removed my phone number from the account. For someone with little technical expertise, this was not just overwhelming, it was a disaster. Every suggested solution I came across in online help centers was either too complex or simply ineffective. I tried countless links, tutorials, and forums, only to find myself stuck, not even close to reclaiming my stolen crypto. In a last-ditch effort, I turned to Google and stumbled upon a review about MUYERN TRUST HACKER. At first, I was skeptical, like anyone would be in my position. But the glowing reviews, especially from people with similar experiences, gave me a glimmer of hope. Despite my doubts, I decided to reach out to them for assistance.The team at MUYERN TRUST HACKER immediately put me at ease. They were professional, understanding, and reassuring. Unlike other services that felt impersonal or automated, they took the time to walk me through every step of the recovery process. The fact that they were willing to schedule a 25-minute session to help me properly secure my account after recovery was invaluable. Today, Iâm grateful to say that my stolen crypto has been fully recovered, and my account is secure again. This experience has taught me that sometimes, even when you feel like all hope is lost, thereâs always a way to fight back. If youâre going through something similar, donât give up. Reach out to MUYERN TRUST HACKER. Even if youâve already tried everything, their expertise and persistence might just be the solution you need.I wholeheartedly recommend MUYERN TRUST HACKER to anyone facing the same situation. Whether youâre a novice or experienced in technology, theyâre the right team to trust when it comes to recovering stolen crypto or securing your accounts. Donât hesitate to contact them, it's worth it. Reach out to them on telegram at muyerntrusthackertech or web: ht tps :// muyerntrusthacker . o r g for faster response.Certificado Business Intelligence - Alber Florentin.pdf



Certificado Business Intelligence - Alber Florentin.pdfalberalen
Ėý
Operador de Excel Empresarial - Business Intelligence.ðĨððĄðð__Cubase Pro Crack Full Activativated 2025



ðĨððĄðð__Cubase Pro Crack Full Activativated 2025abrishhayat858
Ėý
ðąðDOWNLOAD LINK ðð https://pcsoftcrack.net/ds/ ðð
Cubase is a professional digital audio workstation (DAW) developed by Steinberg for music production, recording, editing, and mixing. Since its initial release in 1989, Cubase has been widely used by musicians, producers, and sound engineers across various genres. Known for its powerful features, intuitive interface, and high-quality sound engine, Cubase has remained a leading choice for both beginners and professionals in the music industry.
âĄïļ ðCOPY LINK & PASTE INTO GOOGLE ðð https://pcsoftcrack.net/ds/ ðPRGTUG Meeting: Lost in Data? Let's Chart the Way Out!



PRGTUG Meeting: Lost in Data? Let's Chart the Way Out!Stanislava Tropcheva
Ėý
Tableau User Group (PRGTUG) Meeting:
Lost in Data?
Let's Chart the Way Out!
27th February 2025
Key Benefits of Implementing Contify's M&CI Platform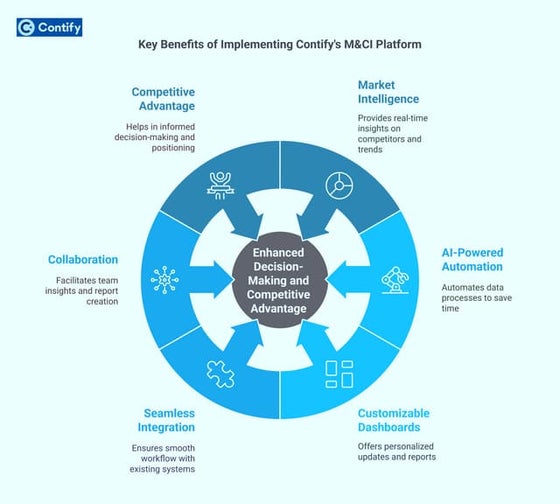



Key Benefits of Implementing Contify's M&CI PlatformContify
Ėý
Contify's Market & Competitive Intelligence platform empowers businesses with real-time insights, automated intelligence gathering, and AI-driven analytics. It enhances decision-making, streamlines competitor tracking, and delivers personalized intelligence reports. With Contify, organizations gain a strategic edge by identifying trends, mitigating risks, and seizing growth opportunities in dynamic market landscapes.
For more information please visit here https://www.contify.com/platform/2025-03-03-Philly-AAAI-GoodData-Build Secure RAG Apps With Open LLM



2025-03-03-Philly-AAAI-GoodData-Build Secure RAG Apps With Open LLMTimothy Spann
Ėý
2025-03-03-Philly-AAAI-GoodData-Build Secure RAG Apps With Open LLM
https://aaai.org/conference/aaai/aaai-25/workshop-list/#ws14Analyzing Consumer Spending Trends and Purchasing Behavior



Analyzing Consumer Spending Trends and Purchasing Behavioromololaokeowo1
Ėý
This project explores consumer spending patterns using Kaggle-sourced data to uncover key trends in purchasing behavior. The analysis involved cleaning and preparing the data, performing exploratory data analysis (EDA), and visualizing insights using ExcelI. Key focus areas included customer demographics, product performance, seasonal trends, and pricing strategies. The project provided actionable insights into consumer preferences, helping businesses optimize sales strategies and improve decision-making.Kaggle & Datathons: A Practical Guide to AI Competitions



Kaggle & Datathons: A Practical Guide to AI Competitionsrasheedsrq
Ėý
Kaggle & Datathons: A Practical Guide to AI Competitions2025 Trends: What Really Works in SEO and Content Marketing



2025 Trends: What Really Works in SEO and Content MarketingDr. Sasidharan Murugan
Ėý
The digital landscape is constantly evolving. Understanding what works in SEO and content marketing today will be critical for success in 2025 and beyond. Let's delve into the key trends shaping the future of online content.How the Best News APIs Work: A Visual Guide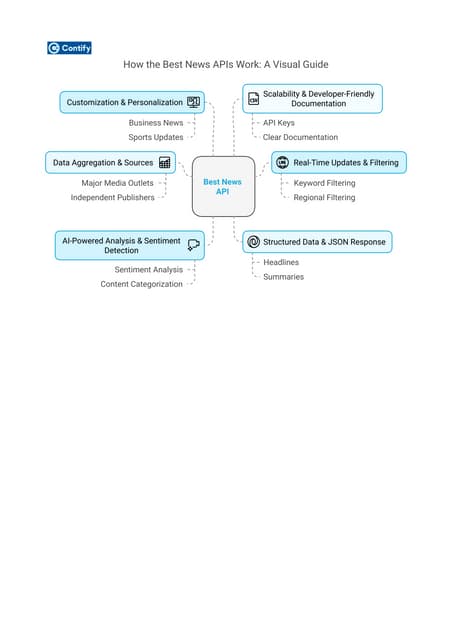



How the Best News APIs Work: A Visual GuideContify
Ėý
Discover how the best news APIs function with this visual guide. Learn how they fetch real-time news, filter content, and integrate seamlessly with apps. Understand key features like authentication, endpoints, and data formats, making it easier to choose the right API for your needs. Perfect for developers and businesses!
For more information please visit here https://www.contify.com/news-api/International Journal on Cloud Computing: Services and Architecture (IJCCSA)



International Journal on Cloud Computing: Services and Architecture (IJCCSA)ijccsa
Ėý
Cloud computing helps enterprises transform business and technology. Companies have begun to
look for solutions that would help reduce their infrastructure costs and improve profitability. Cloud
computing is becoming a foundation for benefits well beyond IT cost savings. Yet, many business
leaders are concerned about cloud security, privacy, availability, and data protection. To discuss
and address these issues, we invite researches who focus on cloud computing to shed more light
on this emerging field. This peer-reviewed open access Journal aims to bring together researchers
and practitioners in all security aspects of cloud-centric and outsourced computing, including (but
not limited to):Quiz 1
- 1. (Q) Match the followingtermsand definitions (10min): _____data a. data placedincontextor summarized _____database managementsystem b. centralizedstorehouse forall datadefinitions _____information c. facts,text,graphics,images,etc. _____repository d. organizedcollection of relateddata _____metadata e.includesdatadefinitionsandconstraints _____two-tierdatabases f.textand graphical displaysthatuserinteractwith _____constraint g. distributeddatastoresthatcan be readfrom a single source _____database application h. support25-100 usersand the userinterface isaccessible on the individualcomputerusers _____database i.a software applicationusedtocreate,maintainand provide controlledaccesstouserdatabases _____user interface j. a rule that cannotbe violatedbydatabase users _____file processingsystem k.applicationprogram(s) _____multi-tierdatabases l. eachmemberof the workgrouphas a computerandthe computersare linked by meansof a network






