R fun utrecht
1 like534 views
This document summarizes a meetup about using R on iOS devices. It explains that jailbreaking is required to install R and other applications not available on the App Store. Once jailbroken, the Cydia app store can be used to install R and utilities like OpenSSH. While iOS devices have powerful hardware, their limitations for development include a small screen, lack of keyboard shortcuts, and Apple restricting third-party software. Alternatives like cloud-based development are suggested to avoid issues with code signing and library installation on jailbroken devices.
1 of 15
Download to read offline







Ad
Recommended
Types of Hardware
Types of HardwareCharles Vincent Familar
╠²
This document defines and describes the physical components of a computer, including storage devices like hard drives that store data and programs, the central processing unit (CPU) that executes instructions, input devices like keyboards and mice that allow user input, and output devices like monitors that display information to the user. It briefly mentions that one of the earliest computers was the abacus invented by the Babylonians to perform basic math operations.Talk data sciencemeetup
Talk data sciencemeetupdatasciencenl
╠²
This document discusses techniques for visualizing high-dimensional data, including t-Distributed Stochastic Neighbor Embedding (t-SNE). t-SNE is used to visualize molecular data with thousands of features and won a Kaggle competition by mapping the data based on activity and time. The document also discusses limitations of single maps and introduces multiple maps t-SNE to better model relationships between different concepts.128-ch3.pptx
128-ch3.pptxDeepakPanchal65
╠²
This document provides a history of iOS and discusses security measures implemented over time. It describes how early versions of iOS had little security but over time Apple added sandboxing, code signing, address space layout randomization, and encryption. The document discusses how jailbreaking allows users to bypass iOS restrictions but makes the device less secure by disabling security features. It also provides examples of attacks like the JailbreakMe 3.0 vulnerability and the iKee worm that targeted jailbroken devices.iOS Basics
iOS BasicsRicha Jain
╠²
iOS is Apple's mobile operating system that runs on iPhones, iPads, iPod touches and Apple TVs. It has gone through several updates and is interacted with through touch gestures like swiping, tapping and pinching. Cydia is an app store for jailbroken iOS devices that provides access to apps not available in the official Apple App Store. It allows users to install, upgrade and remove apps with an interface similar to the App Store. Common troubleshooting steps for jailbroken devices include booting into safe mode which disables all tweaks and extensions to isolate the cause of any crashing.iOS jailbreaking
iOS jailbreakingVarun Luthra
╠²
This document provides an overview of iOS jailbreaking. It explains that jailbreaking removes limitations imposed by Apple to allow root access and installation of unauthorized apps. Reasons for jailbreaking include customization, adding features, and making development easier. The document discusses the jailbreaking process, which involves exploiting checkpoints in the device startup process. It also covers jailbreak tools, repositories for unauthorized apps like Cydia, common jailbreak terms, and legal issues.Introduction to iOS Penetration Testing
Introduction to iOS Penetration TestingOWASP
╠²
The document provides an introduction to iOS penetration testing. It discusses the speaker's background in mobile and web penetration testing with a focus on iOS. The agenda outlines that the talk will cover introduction to iOS, Objective-C runtime basics, setting up a testing environment, and fundamentals of application testing with a focus on black-box testing. It will not cover jailbreak development, Swift, white-box testing, or webapp pentesting. The document then delves into various aspects of iOS including the security model, application sandboxing, Objective-C, and the iOS runtime. It also discusses tools and techniques for static analysis, runtime manipulation, bypassing protections, and investigating local storage.CNIT 128 Ch 3: iOS
CNIT 128 Ch 3: iOSSam Bowne
╠²
This document summarizes the history and security of iOS, including how jailbreaking works and associated risks. It discusses how iOS became more secure over time with features like sandboxing and ASLR. Early jailbreaks exploited vulnerabilities like in MobileSafari, but updating iOS eliminates most risks unless jailbroken. The document outlines some successful attacks like JailbreakMe and iKee worm, but notes iOS defenses make remote exploits difficult.2a Analyzing iOS Apps Part 1
2a Analyzing iOS Apps Part 1Sam Bowne
╠²
This document provides an overview of analyzing iOS apps, including jailbreaking mobile devices. It discusses iOS security features like code signing and sandboxing. It explains how to set up a test environment for analyzing apps by jailbreaking a device and using Unix tools. Key files like property lists and databases that can be explored are also outlined.Hands-On iOS Application Penetraion Testing.pptx
Hands-On iOS Application Penetraion Testing.pptxAkashKatare9
╠²
This presentation provides a comprehensive dive into iOS application security, covering everything from architecture to advanced pentesting techniques. The topics include an overview of iOS architecture, an understanding of jailbreak types (rootful vs. rootless), and methods for jailbreaking iDevices. You'll explore tools for testing iOS applications on both jailbroken and non-jailbroken devices, as well as key analysis techniques like static analysis and extracting decrypted IPA files.
I have also covered common vulnerabilities such as local storage security, binary protection, and keychain data leaks, with practical demonstrations of tools like Filza and Objection. The advanced testing section delves into bypassing jailbreak detection, intercepting traffic, and attacking SSL/TLS certificate pinning in Swift, Flutter, and XAMARIN apps.
Finally, the session explores the exploitation of DeepLinking, testing URL schemes and universal links to perform account compromises and bypass host validation, demonstrating real-world attacks on iOS applications through traffic interception and custom script creation. This session is essential for anyone looking to master iOS application pentesting and vulnerability assessment.[CONFidence 2016] Sławomir Kosowski - Introduction to iOS Application Securit...
[CONFidence 2016] Sławomir Kosowski - Introduction to iOS Application Securit...PROIDEA
╠²
This document provides an introduction to iOS penetration testing, focused on setting up testing environments and the fundamentals of app testing, particularly black-box testing. It outlines core iOS security features, the Objective-C runtime, and methods for both static and runtime analysis, as well as common techniques for bypassing jailbreak detections and certificate pinning. The presentation concludes with practical guidance for pentesters on testing strategies and the evolving landscape of iOS security.CNIT 128 2. Analyzing iOS Applications (Part 1)
CNIT 128 2. Analyzing iOS Applications (Part 1)Sam Bowne
╠²
This document provides a comprehensive overview of mobile device hacking, focusing on iOS applications and the security measures in place. Key topics include the iOS security model, app signing and sandboxing, data protection methods, and the implications of jailbreaking. It also explains app distribution methods, vulnerabilities, and tools used for testing and analysis in the context of iOS ecosystem.Android and ios cracking, hackintosh included !
Android and ios cracking, hackintosh included !Veduruparthy Bharat
╠²
This document discusses and compares the Android and iOS mobile operating systems. It provides details on their development platforms, multitasking abilities, software specifications, supported devices, architectures, and key features. It also describes the processes of rooting Android devices and jailbreaking iOS devices to remove restrictions. Rooting allows administrative access on Android while jailbreaking aims to expand limited features on iOS. The document further explains custom ROMs, benefits and risks of rooting, and the Cydia app store available after jailbreaking. Lastly, it briefly outlines how to set up a Hackintosh computer running the macOS operating system on non-Apple hardware.OWASP Melbourne - Introduction to iOS Application Penetration Testing
OWASP Melbourne - Introduction to iOS Application Penetration Testingeightbit
╠²
This document provides an introduction to iOS application penetration testing. It discusses setting up an iOS penetration testing environment, including jailbreaking a test device and installing necessary software tools. It also provides an overview of iOS and Objective-C, covering key security features of iOS like sandboxing, ASLR, code signing, and data encryption. Topics to be covered include assessing data security, binary analysis, runtime manipulation, and evaluating authentication, session management, and transport security.Jailbreaking iOS
Jailbreaking iOSMihir Patel
╠²
The document discusses jailbreaking iPhones and iOS devices. Jailbreaking removes security restrictions to allow installation of unauthorized apps and modifications to the operating system. It describes how to jailbreak a device using evasi0n software. Potential benefits of jailbreaking include customization and access to unauthorized apps and services, while risks include reduced security and stability. The document also covers types of jailbreaks like tethered vs untethered and concludes that jailbreaking gives users fewer restrictions but also less security.Ruxmon April 2014 - Introduction to iOS Penetration Testing
Ruxmon April 2014 - Introduction to iOS Penetration Testingeightbit
╠²
The document provides an introduction to iOS application penetration testing. It discusses setting up a testing environment including jailbreaking a device and installing tools. It covers assessing data security issues like insecurely stored data and background snapshots. Topics to be covered include binary analysis, runtime manipulation, transport security, and other testing like authentication and sessions.EkoParty 2010: iPhone Rootkit? There's an App for that.
EkoParty 2010: iPhone Rootkit? There's an App for that.Eric Monti
╠²
This document discusses a proof of concept iPhone rootkit developed by reverse engineering the JailbreakMe exploit and jailbreak tools. It describes patching the tools to remove security checks and pop-ups, and preparing a custom "wad.bin" filesystem containing backdoored system utilities and apps to enable remote access and control of an infected device without the user's knowledge. A demo is proposed using a Ruby Sinatra server to serve the exploit to a vanilla iOS device and install the rootkit via the existing JailbreakMe vulnerability. The rootkit aims to remain hidden using techniques like disguising process names and removing GUI indicators of running services.NCC Group 44Con Workshop: How to assess and secure ios apps
NCC Group 44Con Workshop: How to assess and secure ios appsNCC Group
╠²
This document provides an overview of assessing and securing iOS apps. It discusses setting up a testing environment by jailbreaking an iOS device to gain root access. Various tools are installed to analyze apps, including intercepting network traffic both passively and by acting as an HTTP proxy gateway. The document also covers monitoring local app data, binaries, and runtime analysis for black-box security testing of iOS apps.Attacking and Defending Apple iOS Devices
Attacking and Defending Apple iOS DevicesTom Eston
╠²
The document discusses the security landscape of Apple iOS devices within enterprise environments, covering topics such as current device states, real-world attacks, and assessment methodologies. It highlights the importance of evaluating iOS deployments due to vulnerabilities, user behavior like jailbreaking, and the need for robust management practices. Additionally, it outlines defensive techniques, hardening practices, and the relevance of mobile device management solutions for ensuring device security.Beyond the 'cript practical i os reverse engineering lascon
Beyond the 'cript practical i os reverse engineering lasconNino Ho
╠²
The document presents a comprehensive overview of practical iOS reverse engineering techniques and tools, including a general toolkit and methods for assessing iOS applications. It covers various topics such as Mach-O binary format, ARM assembly, identifying and bypassing jailbreak detection, and common attack vectors like insecure storage and inter-process communication. The presentation aims to enhance understanding of iOS internals and improve the effectiveness of security assessments and research.Jail breaking
Jail breakingRokkam Reddy
╠²
Jailbreaking allows iPhone, iPad, and iPod Touch users to run unauthorized third-party software and customize their devices beyond Apple's limitations. The jailbreaking process involves unlocking the operating system to grant root access. Once jailbroken, users can download apps from Cydia and modify features like installing WiFi hotspots, using FaceTime over cellular networks, blocking calls and texts, and customizing home screens and lock screens. While jailbreaking is legal in the US, it voids the device warranty and carries small risks like potential lag, viruses, or incompatible apps.iOS-Application-Security-iAmPr3m
iOS-Application-Security-iAmPr3mPrem Kumar (OSCP)
╠²
Prem Kumar is a senior security consultant who specializes in web, mobile, and network penetration testing. He has previously presented at security conferences and found vulnerabilities in applications from companies like Facebook, Apple, and Yahoo. The agenda for his talk covers topics like iOS architecture, application structures, types of iOS applications and distribution methods, iOS penetration testing techniques, jailbreaking, and setting up an iOS testing platform. He will demonstrate runtime analysis and penetration testing on real iOS applications.iOS Application Exploitation
iOS Application ExploitationPositive Hack Days
╠²
An iOS application penetration testing training covers various topics including:
- Setting up an iOS pen testing environment and understanding the iOS filesystem.
- Understanding the Objective-C runtime and performing runtime analysis and manipulation.
- Analyzing insecure data storage in plist files, NSUserDefaults, CoreData, and the keychain.
- Identifying side channel data leakage through device logs, application snapshots, and the pasteboard.Wahckon[2] - iOS Runtime Hacking Crash Course
Wahckon[2] - iOS Runtime Hacking Crash Courseeightbit
╠²
This document provides an introduction to runtime hacking on iOS. It discusses setting up the environment, mapping out an application by decrypting and dumping binaries to obtain class information. It then covers techniques for dumping and modifying variables at runtime like retrieving sensitive user data. Methods for manipulating functions are also presented, such as bypassing authentication or jailbreak detection. Persistence techniques like injecting libraries are explained. Finally, it addresses considerations for hacking Swift applications. The overall goal is to quickly get people up to speed on runtime analysis and manipulation of third-party iOS apps.iOS Application Security
iOS Application SecurityEgor Tolstoy
╠²
This document provides an agenda for a training on iOS application penetration testing. It covers topics such as setting up an iOS pen testing environment, understanding the iOS filesystem and Objective-C runtime, runtime analysis and manipulation, insecure data storage, analyzing network traffic, jailbreak detection, secure coding guidelines, and automated testing. Tools discussed include class-dump-z, cycript, clutch, and gdb for analyzing iOS applications.IoS An enomorous thing
IoS An enomorous thingSOUNDARRAJAN V
╠²
The document provides an overview of iOS, Apple's mobile operating system, detailing its history, key features, kernel structure, and security measures. It outlines the evolution of iOS versions since its introduction in 2007, highlighting significant advancements like multitasking and Siri. Additionally, it compares iOS with Android, noting differences in architecture and app management.CrikeyCon 2015 - iOS Runtime Hacking Crash Course
CrikeyCon 2015 - iOS Runtime Hacking Crash Courseeightbit
╠²
This document provides a crash course on runtime hacking of iOS applications. It discusses setting up the necessary environment, mapping out an application by decrypting and dumping binaries to obtain class information. It then demonstrates how to retrieve sensitive variables like credentials by directly accessing them at runtime using Cycript. Finally, it shows how functions can be manipulated to bypass security checks or modify application behavior persistently through injection.Pentesting iOS Applications
Pentesting iOS Applicationsjasonhaddix
╠²
The document discusses penetration testing of iOS applications. It provides an overview of the key aspects of testing including:
- Setting up the testing environment with tools like Xcode, Instruments, Burp Suite, and SQLite Manager.
- Performing whitebox testing through source code analysis, identifying HTTP/WS calls, file system interactions, and manual code review.
- Proxying the iOS simulator to intercept and analyze network traffic.
- Exploring various data storage mechanisms like plists, SQLite databases, and the keychain for sensitive data.iOS Jail break
iOS Jail breakyarden hanan
╠²
Jailbreaking allows users to install unauthorized apps, customize their iOS interface, and remove restrictions. It gives the user root access to the operating system. Yalu is a website that hosts jailbreak versions for different iOS releases. To jailbreak, users must check device compatibility, back up data, disable security features, connect the device to a computer, use Cydia Impactor to sign and install the Yalu app, trust the app, run Yalu to install Cydia, and then Cydia will be available after a restart.Supporting the NextGen 911 Digital Transformation with FME
Supporting the NextGen 911 Digital Transformation with FMESafe Software
╠²
Next Generation 911 involves the transformation of our 911 system from an old analog one to the new digital internet based architecture. The evolution of NG911 opens up a host of new opportunities to improve the system. This includes everything from device based location, to real time text. This can improve location accuracy dramatically as well as provide live updates from the citizen in need along with real time sensor updates. There is also the opportunity to provide multi-media attachments and medical records if the end user approves. This digital transformation and enhancements all require the support of new NENA and CRTC standards, along with integration across a variety of data streams.
This presentation will focus on how FME has supported NG911 transformations to date, and how we are positioning FME to support the enhanced capabilities to come. This session will be of interest to emergency services, municipalities and anyone who may be interested to know more about how emergency services are being improved to provide more accurate, localized information in order to improve the speed and relevance of emergency response and ultimately save more lives and provide better outcomes for those in need.Data Validation and System Interoperability
Data Validation and System InteroperabilitySafe Software
╠²
A non-profit human services agency with specialized health record and billing systems. Challenges solved include access control integrations from employee electronic HR records, multiple regulations compliance, data migrations, benefits enrollments, payroll processing, and automated reporting for business intelligence and analysis.More Related Content
Similar to R fun utrecht (20)
Hands-On iOS Application Penetraion Testing.pptx
Hands-On iOS Application Penetraion Testing.pptxAkashKatare9
╠²
This presentation provides a comprehensive dive into iOS application security, covering everything from architecture to advanced pentesting techniques. The topics include an overview of iOS architecture, an understanding of jailbreak types (rootful vs. rootless), and methods for jailbreaking iDevices. You'll explore tools for testing iOS applications on both jailbroken and non-jailbroken devices, as well as key analysis techniques like static analysis and extracting decrypted IPA files.
I have also covered common vulnerabilities such as local storage security, binary protection, and keychain data leaks, with practical demonstrations of tools like Filza and Objection. The advanced testing section delves into bypassing jailbreak detection, intercepting traffic, and attacking SSL/TLS certificate pinning in Swift, Flutter, and XAMARIN apps.
Finally, the session explores the exploitation of DeepLinking, testing URL schemes and universal links to perform account compromises and bypass host validation, demonstrating real-world attacks on iOS applications through traffic interception and custom script creation. This session is essential for anyone looking to master iOS application pentesting and vulnerability assessment.[CONFidence 2016] Sławomir Kosowski - Introduction to iOS Application Securit...
[CONFidence 2016] Sławomir Kosowski - Introduction to iOS Application Securit...PROIDEA
╠²
This document provides an introduction to iOS penetration testing, focused on setting up testing environments and the fundamentals of app testing, particularly black-box testing. It outlines core iOS security features, the Objective-C runtime, and methods for both static and runtime analysis, as well as common techniques for bypassing jailbreak detections and certificate pinning. The presentation concludes with practical guidance for pentesters on testing strategies and the evolving landscape of iOS security.CNIT 128 2. Analyzing iOS Applications (Part 1)
CNIT 128 2. Analyzing iOS Applications (Part 1)Sam Bowne
╠²
This document provides a comprehensive overview of mobile device hacking, focusing on iOS applications and the security measures in place. Key topics include the iOS security model, app signing and sandboxing, data protection methods, and the implications of jailbreaking. It also explains app distribution methods, vulnerabilities, and tools used for testing and analysis in the context of iOS ecosystem.Android and ios cracking, hackintosh included !
Android and ios cracking, hackintosh included !Veduruparthy Bharat
╠²
This document discusses and compares the Android and iOS mobile operating systems. It provides details on their development platforms, multitasking abilities, software specifications, supported devices, architectures, and key features. It also describes the processes of rooting Android devices and jailbreaking iOS devices to remove restrictions. Rooting allows administrative access on Android while jailbreaking aims to expand limited features on iOS. The document further explains custom ROMs, benefits and risks of rooting, and the Cydia app store available after jailbreaking. Lastly, it briefly outlines how to set up a Hackintosh computer running the macOS operating system on non-Apple hardware.OWASP Melbourne - Introduction to iOS Application Penetration Testing
OWASP Melbourne - Introduction to iOS Application Penetration Testingeightbit
╠²
This document provides an introduction to iOS application penetration testing. It discusses setting up an iOS penetration testing environment, including jailbreaking a test device and installing necessary software tools. It also provides an overview of iOS and Objective-C, covering key security features of iOS like sandboxing, ASLR, code signing, and data encryption. Topics to be covered include assessing data security, binary analysis, runtime manipulation, and evaluating authentication, session management, and transport security.Jailbreaking iOS
Jailbreaking iOSMihir Patel
╠²
The document discusses jailbreaking iPhones and iOS devices. Jailbreaking removes security restrictions to allow installation of unauthorized apps and modifications to the operating system. It describes how to jailbreak a device using evasi0n software. Potential benefits of jailbreaking include customization and access to unauthorized apps and services, while risks include reduced security and stability. The document also covers types of jailbreaks like tethered vs untethered and concludes that jailbreaking gives users fewer restrictions but also less security.Ruxmon April 2014 - Introduction to iOS Penetration Testing
Ruxmon April 2014 - Introduction to iOS Penetration Testingeightbit
╠²
The document provides an introduction to iOS application penetration testing. It discusses setting up a testing environment including jailbreaking a device and installing tools. It covers assessing data security issues like insecurely stored data and background snapshots. Topics to be covered include binary analysis, runtime manipulation, transport security, and other testing like authentication and sessions.EkoParty 2010: iPhone Rootkit? There's an App for that.
EkoParty 2010: iPhone Rootkit? There's an App for that.Eric Monti
╠²
This document discusses a proof of concept iPhone rootkit developed by reverse engineering the JailbreakMe exploit and jailbreak tools. It describes patching the tools to remove security checks and pop-ups, and preparing a custom "wad.bin" filesystem containing backdoored system utilities and apps to enable remote access and control of an infected device without the user's knowledge. A demo is proposed using a Ruby Sinatra server to serve the exploit to a vanilla iOS device and install the rootkit via the existing JailbreakMe vulnerability. The rootkit aims to remain hidden using techniques like disguising process names and removing GUI indicators of running services.NCC Group 44Con Workshop: How to assess and secure ios apps
NCC Group 44Con Workshop: How to assess and secure ios appsNCC Group
╠²
This document provides an overview of assessing and securing iOS apps. It discusses setting up a testing environment by jailbreaking an iOS device to gain root access. Various tools are installed to analyze apps, including intercepting network traffic both passively and by acting as an HTTP proxy gateway. The document also covers monitoring local app data, binaries, and runtime analysis for black-box security testing of iOS apps.Attacking and Defending Apple iOS Devices
Attacking and Defending Apple iOS DevicesTom Eston
╠²
The document discusses the security landscape of Apple iOS devices within enterprise environments, covering topics such as current device states, real-world attacks, and assessment methodologies. It highlights the importance of evaluating iOS deployments due to vulnerabilities, user behavior like jailbreaking, and the need for robust management practices. Additionally, it outlines defensive techniques, hardening practices, and the relevance of mobile device management solutions for ensuring device security.Beyond the 'cript practical i os reverse engineering lascon
Beyond the 'cript practical i os reverse engineering lasconNino Ho
╠²
The document presents a comprehensive overview of practical iOS reverse engineering techniques and tools, including a general toolkit and methods for assessing iOS applications. It covers various topics such as Mach-O binary format, ARM assembly, identifying and bypassing jailbreak detection, and common attack vectors like insecure storage and inter-process communication. The presentation aims to enhance understanding of iOS internals and improve the effectiveness of security assessments and research.Jail breaking
Jail breakingRokkam Reddy
╠²
Jailbreaking allows iPhone, iPad, and iPod Touch users to run unauthorized third-party software and customize their devices beyond Apple's limitations. The jailbreaking process involves unlocking the operating system to grant root access. Once jailbroken, users can download apps from Cydia and modify features like installing WiFi hotspots, using FaceTime over cellular networks, blocking calls and texts, and customizing home screens and lock screens. While jailbreaking is legal in the US, it voids the device warranty and carries small risks like potential lag, viruses, or incompatible apps.iOS-Application-Security-iAmPr3m
iOS-Application-Security-iAmPr3mPrem Kumar (OSCP)
╠²
Prem Kumar is a senior security consultant who specializes in web, mobile, and network penetration testing. He has previously presented at security conferences and found vulnerabilities in applications from companies like Facebook, Apple, and Yahoo. The agenda for his talk covers topics like iOS architecture, application structures, types of iOS applications and distribution methods, iOS penetration testing techniques, jailbreaking, and setting up an iOS testing platform. He will demonstrate runtime analysis and penetration testing on real iOS applications.iOS Application Exploitation
iOS Application ExploitationPositive Hack Days
╠²
An iOS application penetration testing training covers various topics including:
- Setting up an iOS pen testing environment and understanding the iOS filesystem.
- Understanding the Objective-C runtime and performing runtime analysis and manipulation.
- Analyzing insecure data storage in plist files, NSUserDefaults, CoreData, and the keychain.
- Identifying side channel data leakage through device logs, application snapshots, and the pasteboard.Wahckon[2] - iOS Runtime Hacking Crash Course
Wahckon[2] - iOS Runtime Hacking Crash Courseeightbit
╠²
This document provides an introduction to runtime hacking on iOS. It discusses setting up the environment, mapping out an application by decrypting and dumping binaries to obtain class information. It then covers techniques for dumping and modifying variables at runtime like retrieving sensitive user data. Methods for manipulating functions are also presented, such as bypassing authentication or jailbreak detection. Persistence techniques like injecting libraries are explained. Finally, it addresses considerations for hacking Swift applications. The overall goal is to quickly get people up to speed on runtime analysis and manipulation of third-party iOS apps.iOS Application Security
iOS Application SecurityEgor Tolstoy
╠²
This document provides an agenda for a training on iOS application penetration testing. It covers topics such as setting up an iOS pen testing environment, understanding the iOS filesystem and Objective-C runtime, runtime analysis and manipulation, insecure data storage, analyzing network traffic, jailbreak detection, secure coding guidelines, and automated testing. Tools discussed include class-dump-z, cycript, clutch, and gdb for analyzing iOS applications.IoS An enomorous thing
IoS An enomorous thingSOUNDARRAJAN V
╠²
The document provides an overview of iOS, Apple's mobile operating system, detailing its history, key features, kernel structure, and security measures. It outlines the evolution of iOS versions since its introduction in 2007, highlighting significant advancements like multitasking and Siri. Additionally, it compares iOS with Android, noting differences in architecture and app management.CrikeyCon 2015 - iOS Runtime Hacking Crash Course
CrikeyCon 2015 - iOS Runtime Hacking Crash Courseeightbit
╠²
This document provides a crash course on runtime hacking of iOS applications. It discusses setting up the necessary environment, mapping out an application by decrypting and dumping binaries to obtain class information. It then demonstrates how to retrieve sensitive variables like credentials by directly accessing them at runtime using Cycript. Finally, it shows how functions can be manipulated to bypass security checks or modify application behavior persistently through injection.Pentesting iOS Applications
Pentesting iOS Applicationsjasonhaddix
╠²
The document discusses penetration testing of iOS applications. It provides an overview of the key aspects of testing including:
- Setting up the testing environment with tools like Xcode, Instruments, Burp Suite, and SQLite Manager.
- Performing whitebox testing through source code analysis, identifying HTTP/WS calls, file system interactions, and manual code review.
- Proxying the iOS simulator to intercept and analyze network traffic.
- Exploring various data storage mechanisms like plists, SQLite databases, and the keychain for sensitive data.iOS Jail break
iOS Jail breakyarden hanan
╠²
Jailbreaking allows users to install unauthorized apps, customize their iOS interface, and remove restrictions. It gives the user root access to the operating system. Yalu is a website that hosts jailbreak versions for different iOS releases. To jailbreak, users must check device compatibility, back up data, disable security features, connect the device to a computer, use Cydia Impactor to sign and install the Yalu app, trust the app, run Yalu to install Cydia, and then Cydia will be available after a restart.Recently uploaded (20)
Supporting the NextGen 911 Digital Transformation with FME
Supporting the NextGen 911 Digital Transformation with FMESafe Software
╠²
Next Generation 911 involves the transformation of our 911 system from an old analog one to the new digital internet based architecture. The evolution of NG911 opens up a host of new opportunities to improve the system. This includes everything from device based location, to real time text. This can improve location accuracy dramatically as well as provide live updates from the citizen in need along with real time sensor updates. There is also the opportunity to provide multi-media attachments and medical records if the end user approves. This digital transformation and enhancements all require the support of new NENA and CRTC standards, along with integration across a variety of data streams.
This presentation will focus on how FME has supported NG911 transformations to date, and how we are positioning FME to support the enhanced capabilities to come. This session will be of interest to emergency services, municipalities and anyone who may be interested to know more about how emergency services are being improved to provide more accurate, localized information in order to improve the speed and relevance of emergency response and ultimately save more lives and provide better outcomes for those in need.Data Validation and System Interoperability
Data Validation and System InteroperabilitySafe Software
╠²
A non-profit human services agency with specialized health record and billing systems. Challenges solved include access control integrations from employee electronic HR records, multiple regulations compliance, data migrations, benefits enrollments, payroll processing, and automated reporting for business intelligence and analysis.MuleSoft for AgentForce : Topic Center and API Catalog
MuleSoft for AgentForce : Topic Center and API Catalogshyamraj55
╠²
This presentation dives into how MuleSoft empowers AgentForce with organized API discovery and streamlined integration using Topic Center and the API Catalog. Learn how these tools help structure APIs around business needs, improve reusability, and simplify collaboration across teams. Ideal for developers, architects, and business stakeholders looking to build a connected and scalable API ecosystem within AgentForce.Integration of Utility Data into 3D BIM Models Using a 3D Solids Modeling Wor...
Integration of Utility Data into 3D BIM Models Using a 3D Solids Modeling Wor...Safe Software
╠²
Jacobs has developed a 3D utility solids modelling workflow to improve the integration of utility data into 3D Building Information Modeling (BIM) environments. This workflow, a collaborative effort between the New Zealand Geospatial Team and the Australian Data Capture Team, employs FME to convert 2D utility data into detailed 3D representations, supporting enhanced spatial analysis and clash detection.
To enable the automation of this process, Jacobs has also developed a survey data standard that standardizes the capture of existing utilities. This standard ensures consistency in data collection, forming the foundation for the subsequent automated validation and modelling steps. The workflow begins with the acquisition of utility survey data, including attributes such as location, depth, diameter, and material of utility assets like pipes and manholes. This data is validated through a custom-built tool that ensures completeness and logical consistency, including checks for proper connectivity between network components. Following validation, the data is processed using an automated modelling tool to generate 3D solids from 2D geometric representations. These solids are then integrated into BIM models to facilitate compatibility with 3D workflows and enable detailed spatial analyses.
The workflow contributes to improved spatial understanding by visualizing the relationships between utilities and other infrastructure elements. The automation of validation and modeling processes ensures consistent and accurate outputs, minimizing errors and increasing workflow efficiency.
This methodology highlights the application of FME in addressing challenges associated with geospatial data transformation and demonstrates its utility in enhancing data integration within BIM frameworks. By enabling accurate 3D representation of utility networks, the workflow supports improved design collaboration and decision-making in complex infrastructure projectsKubernetes Security Act Now Before ItŌĆÖs Too Late
Kubernetes Security Act Now Before ItŌĆÖs Too LateMichael Furman
╠²
In today's cloud-native landscape, Kubernetes has become the de facto standard for orchestrating containerized applications, but its inherent complexity introduces unique security challenges. Are you one YAML away from disaster?
This presentation, "Kubernetes Security: Act Now Before ItŌĆÖs Too Late," is your essential guide to understanding and mitigating the critical security risks within your Kubernetes environments. This presentation dives deep into the OWASP Kubernetes Top Ten, providing actionable insights to harden your clusters.
We will cover:
The fundamental architecture of Kubernetes and why its security is paramount.
In-depth strategies for protecting your Kubernetes Control Plane, including kube-apiserver and etcd.
Crucial best practices for securing your workloads and nodes, covering topics like privileged containers, root filesystem security, and the essential role of Pod Security Admission.
Don't wait for a breach. Learn how to identify, prevent, and respond to Kubernetes security threats effectively.
It's time to act now before it's too late!AudGram Review: Build Visually Appealing, AI-Enhanced Audiograms to Engage Yo...
AudGram Review: Build Visually Appealing, AI-Enhanced Audiograms to Engage Yo...SOFTTECHHUB
╠²
AudGram changes everything by bridging the gap between your audio content and the visual engagement your audience craves. This cloud-based platform transforms your existing audio into scroll-stopping visual content that performs across all social media platforms.
FME for Distribution & Transmission Integrity Management Program (DIMP & TIMP)
FME for Distribution & Transmission Integrity Management Program (DIMP & TIMP)Safe Software
╠²
Peoples Gas in Chicago, IL has changed to a new Distribution & Transmission Integrity Management Program (DIMP & TIMP) software provider in recent years. In order to successfully deploy the new software we have created a series of ETL processes using FME Form to transform our gas facility data to meet the required DIMP & TIMP data specifications. This presentation will provide an overview of how we used FME to transform data from ESRIŌĆÖs Utility Network and several other internal and external sources to meet the strict data specifications for the DIMP and TIMP software solutions.Crypto Super 500 - 14th Report - June2025.pdf
Crypto Super 500 - 14th Report - June2025.pdfStephen Perrenod
╠²
This OrionX's 14th semi-annual report on the state of the cryptocurrency mining market. The report focuses on Proof-of-Work cryptocurrencies since those use substantial supercomputer power to mint new coins and encode transactions on their blockchains. Only two make the cut this time, Bitcoin with $18 billion of annual economic value produced and Dogecoin with $1 billion. Bitcoin has now reached the Zettascale with typical hash rates of 0.9 Zettahashes per second. Bitcoin is powered by the world's largest decentralized supercomputer in a continuous winner take all lottery incentive network.ŌĆ£Addressing Evolving AI Model Challenges Through Memory and Storage,ŌĆØ a Prese...
ŌĆ£Addressing Evolving AI Model Challenges Through Memory and Storage,ŌĆØ a Prese...Edge AI and Vision Alliance
╠²
For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2025/06/addressing-evolving-ai-model-challenges-through-memory-and-storage-a-presentation-from-micron/
Wil Florentino, Senior Segment Marketing Manager at Micron, presents the ŌĆ£Addressing Evolving AI Model Challenges Through Memory and StorageŌĆØ tutorial at the May 2025 Embedded Vision Summit.
In the fast-changing world of artificial intelligence, the industry is deploying more AI compute at the edge. But the growing diversity and data footprint of transformers and models such as large language models and large multimodal models puts a spotlight on memory performance and data storage capacity as key bottlenecks. Enabling the full potential of AI in industries such as manufacturing, automotive, robotics and transportation will require us to find efficient ways to deploy this new generation of complex models.
In this presentation, Florentino explores how memory and storage are responding to this need and solving complex issues in the AI market. He examines the storage capacity and memory bandwidth requirements of edge AI use cases ranging from tiny devices with severe cost and power constraints to edge servers, and he explains how new memory technologies such as LPDDR5, LPCAMM2 and multi-port SSDs are helping system developers to meet these challenges.FIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptx
FIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptxFIDO Alliance
╠²
FIDO Seminar: Perspectives on Passkeys & Consumer AdoptionRaman Bhaumik - Passionate Tech Enthusiast
Raman Bhaumik - Passionate Tech EnthusiastRaman Bhaumik
╠²
A Junior Software Developer with a flair for innovation, Raman Bhaumik excels in delivering scalable web solutions. With three years of experience and a solid foundation in Java, Python, JavaScript, and SQL, she has streamlined task tracking by 20% and improved application stability.Securing Account Lifecycles in the Age of Deepfakes.pptx
Securing Account Lifecycles in the Age of Deepfakes.pptxFIDO Alliance
╠²
Securing Account Lifecycles in the Age of DeepfakesTrustArc Webinar - 2025 Global Privacy Survey
TrustArc Webinar - 2025 Global Privacy SurveyTrustArc
╠²
How does your privacy program compare to your peers? What challenges are privacy teams tackling and prioritizing in 2025?
In the sixth annual Global Privacy Benchmarks Survey, we asked global privacy professionals and business executives to share their perspectives on privacy inside and outside their organizations. The annual report provides a 360-degree view of various industries' priorities, attitudes, and trends. See how organizational priorities and strategic approaches to data security and privacy are evolving around the globe.
This webinar features an expert panel discussion and data-driven insights to help you navigate the shifting privacy landscape. Whether you are a privacy officer, legal professional, compliance specialist, or security expert, this session will provide actionable takeaways to strengthen your privacy strategy.
This webinar will review:
- The emerging trends in data protection, compliance, and risk
- The top challenges for privacy leaders, practitioners, and organizations in 2025
- The impact of evolving regulations and the crossroads with new technology, like AI
Predictions for the future of privacy in 2025 and beyondWar_And_Cyber_3_Years_Of_Struggle_And_Lessons_For_Global_Security.pdf
War_And_Cyber_3_Years_Of_Struggle_And_Lessons_For_Global_Security.pdfbiswajitbanerjee38
╠²
Russia is one of the most aggressive nations when it comes to state coordinated cyberattacksŌĆŖŌĆöŌĆŖand Ukraine has been at the center of their crosshairs for 3 years. This report, provided the State Service of Special Communications and Information Protection of Ukraine contains an incredible amount of cybersecurity insights, showcasing the coordinated aggressive cyberwarfare campaigns of Russia against Ukraine.
It brings to the forefront that understanding your adversary, especially an aggressive nation state, is important for cyber defense. Knowing their motivations, capabilities, and tactics becomes an advantage when allocating resources for maximum impact.
Intelligence shows Russia is on a cyber rampage, leveraging FSB, SVR, and GRU resources to professionally target UkraineŌĆÖs critical infrastructures, military, and international diplomacy support efforts.
The number of total incidents against Ukraine, originating from Russia, has steadily increased from 1350 in 2021 to 4315 in 2024, but the number of actual critical incidents has been managed down from a high of 1048 in 2022 to a mere 59 in 2024ŌĆŖŌĆöŌĆŖshowcasing how the rapid detection and response to cyberattacks has been impacted by UkraineŌĆÖs improved cyber resilience.
Even against a much larger adversary, Ukraine is showcasing outstanding cybersecurity, enabled by strong strategies and sound tactics. There are lessons to learn for any enterprise that could potentially be targeted by aggressive nation states.
Definitely worth the read!ŌĆ£From Enterprise to Makers: Driving Vision AI Innovation at the Extreme Edge,...
ŌĆ£From Enterprise to Makers: Driving Vision AI Innovation at the Extreme Edge,...Edge AI and Vision Alliance
╠²
For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2025/06/from-enterprise-to-makers-driving-vision-ai-innovation-at-the-extreme-edge-a-presentation-from-sony-semiconductor-solutions/
Amir Servi, Edge Deep Learning Product Manager at Sony Semiconductor Solutions, presents the ŌĆ£From Enterprise to Makers: Driving Vision AI Innovation at the Extreme EdgeŌĆØ tutorial at the May 2025 Embedded Vision Summit.
SonyŌĆÖs unique integrated sensor-processor technology is enabling ultra-efficient intelligence directly at the image source, transforming vision AI for enterprises and developers alike. In this presentation, Servi showcases how the AITRIOS platform simplifies vision AI for enterprises with tools for large-scale deployments and model management.
Servi also highlights his companyŌĆÖs collaboration with Ultralytics and Raspberry Pi, which brings YOLO models to the developer community, empowering grassroots innovation. Whether youŌĆÖre scaling vision AI for industry or experimenting with cutting-edge tools, this presentation will demonstrate how Sony is accelerating high-performance, energy-efficient vision AI for all.The State of Web3 Industry- Industry Report
The State of Web3 Industry- Industry ReportLiveplex
╠²
Web3 is poised for mainstream integration by 2030, with decentralized applications potentially reaching billions of users through improved scalability, user-friendly wallets, and regulatory clarity. Many forecasts project trillions of dollars in tokenized assets by 2030 , integration of AI, IoT, and Web3 (e.g. autonomous agents and decentralized physical infrastructure), and the possible emergence of global interoperability standards. Key challenges going forward include ensuring security at scale, preserving decentralization principles under regulatory oversight, and demonstrating tangible consumer value to sustain adoption beyond speculative cycles.AI vs Human Writing: Can You Tell the Difference?
AI vs Human Writing: Can You Tell the Difference?Shashi Sathyanarayana, Ph.D
╠²
This slide illustrates a side-by-side comparison between human-written, AI-written, and ambiguous content. It highlights subtle cues that help readers assess authenticity, raising essential questions about the future of communication, trust, and thought leadership in the age of generative AI.FIDO Seminar: Targeting Trust: The Future of Identity in the Workforce.pptx
FIDO Seminar: Targeting Trust: The Future of Identity in the Workforce.pptxFIDO Alliance
╠²
FIDO Seminar: Targeting Trust: The Future of Identity in the WorkforceCan We Use Rust to Develop Extensions for PostgreSQL? (POSETTE: An Event for ...
Can We Use Rust to Develop Extensions for PostgreSQL? (POSETTE: An Event for ...NTT DATA Technology & Innovation
╠²
Can We Use Rust to Develop Extensions for PostgreSQL?
(POSETTE: An Event for Postgres 2025)
June 11, 2025
Shinya Kato
NTT DATA Japan CorporationŌĆ£Addressing Evolving AI Model Challenges Through Memory and Storage,ŌĆØ a Prese...
ŌĆ£Addressing Evolving AI Model Challenges Through Memory and Storage,ŌĆØ a Prese...Edge AI and Vision Alliance
╠²
ŌĆ£From Enterprise to Makers: Driving Vision AI Innovation at the Extreme Edge,...
ŌĆ£From Enterprise to Makers: Driving Vision AI Innovation at the Extreme Edge,...Edge AI and Vision Alliance
╠²
Can We Use Rust to Develop Extensions for PostgreSQL? (POSETTE: An Event for ...
Can We Use Rust to Develop Extensions for PostgreSQL? (POSETTE: An Event for ...NTT DATA Technology & Innovation
╠²
Ad
R fun utrecht
- 1. Data Science NL Meetup Utrecht, 23 January 2014 -fun in Utrecht ichard Gill ! http://www.math.leidenuniv.nl/~gill (R on an iDevice)
- 2. R on iOS ? Sure, thanks to ech0chrome ŌĆó http://leafmoon.users.sourceforge.net/cydia/ ŌĆó http://twitter.com/#!/ech0chrome ŌĆó Taiju Yamada <ech0chrome@104.net>
- 3. R on iOS ŌĆó First jailbreak iDevice ŌĆō gain root privileges and circumvent Apple restrictions (your legal right, AFAIK) ŌĆó Jailbreak restores hidden functionality and installs Cydia (App Store for lots more) ŌĆó Apple doesnŌĆÖt (yet) see difference & device can be restored to original state ŌĆō no loss of warranty
- 4. Why jailbreak an iThing? ŌĆó iPhone, iPad speed, memory, storage, monitor (number of pixels) of typical 10 years old desktop, plus... ŌĆó Internal mobile internet modem (3G cell phone) ŌĆó Bluetooth, Wireless, USB connections... ŌĆó Gorgeous GUI on top of a (BSD) UNIX ŌĆó Apple treats you like a child ŌĆó Why climb Everest? Because itŌĆÖs there
- 5. Jailbreaking ŌĆó At time of writing: works on all iDevices running iOS 7; not dif’¼ücult or risky AFAIK (but make a backup ’¼ürst!) ŌĆó Run evasi0n 7 on Mac or PC connected by USB ŌĆó Uses known CPU architecture & vulnerabilities in AppleŌĆÖs boot process ŌĆó Note: the next generation will have new initially unknown architectures ŌĆó Next upgrade of iOS 7 might well remove currently exploited vulnerability ŌĆó Downgrading a currently installed iOS is essentially impossible ŌĆó Last upgrade of earlier iOS essentially makes earlier exploits impossible
- 6. Jailbreaking iPad2, iOS 7.0.4 ŌĆó Backup; download evasi0n7; connect and run ŌĆó Install OpenSSH and change passwords (alpine) of root and of user (mobile) ŌĆó Install more cool stuff and useful tools ŌĆó You canŌĆÖt upgrade iOS ŌĆó You can re-install iOS, and then restore your personal stuff from iTunes backup (jailbreak lost)
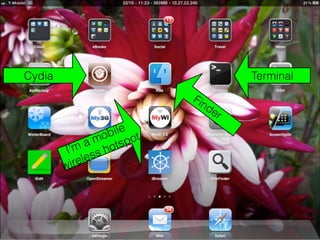
- 7. Cydia Terminal Fin de r bile ot mo tsp a IŌĆÖm ss ho ele wir
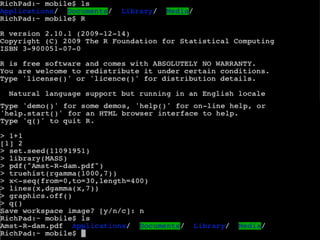
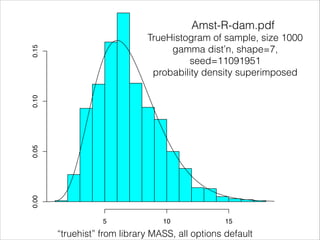
- 11. Amst-R-dam.pdf 0.00 0.05 0.10 0.15 TrueHistogram of sample, size 1000 gamma distŌĆÖn, shape=7, seed=11091951 probability density superimposed 5 10 15 ŌĆ£truehistŌĆØ from library MASS, all options default data
- 12. Have fun! ŌĆó Remember to change the passwords of root and of mobile from alpine to ... ŌĆó Be prepared for annoyance as Apple, hackers, play cat and mouse ŌĆó Beware of scams and rumours, donŌĆÖt pay anyone anything! ŌĆó DonŌĆÖt count on jailbreak still being possible a few models / iOS versions later
- 13. Postscript (1) ŌĆó Why I donŌĆÖt use it much: canŌĆÖt install extra libraries; touchscreen iOS keyboard has no tab, ctrl, arrow keysŌĆ” ŌĆó Apple has made life of a non-standard developer almost impossible (code signing, ŌĆ”) ŌĆó Should you develop on the iDevice or outside? ŌĆó If youŌĆÖve got internet, why not do R in the cloud? ŌĆó RStudio Server ŌĆ” ! (but: a bug presently prevents effective use from iDevice)
- 14. Postscript (2) ŌĆó http://gamma-level.com/iphoneos/ports/texlive (Aaron╠²Grif’¼üth) provides Cydia-based install of LaTeX ŌĆó Just needs Perl from http://coredev.nl/ ŌĆó iOS hard disk has small partition for system, large partition for user. But you can move, symlink /usr/local (system partition) to /private/var/local (user partition), see http://coredev.nl/ ŌĆó Grif’¼üth also explained how he made his own build, could be useful ... ! ŌĆó However these instructions donŌĆÖt work on latest iOS
- 15. R inside The End
