Recommendation For Improving Authentication For Our Online Systems At Pace V2.0
1 like243 views
The document discusses authentication practices for online systems at Pace University. It provides an overview of authentication methods ranging from no authentication to multi-factor authentication. It also summarizes Pace's current complex password rules and recommendations for improving authentication, which include assigning risk categories to users and enforcing more frequent password changes for high-risk users. The document also discusses the use of biometrics and multi-factor authentication at other universities.
1 of 11








![Questions? More information is available from the Division of Information Technology: phone: 914 ŌĆō 773 - 3648 via web: http:// doithelpdesk.pace.edu [email_address] , 914-923-2658](https://image.slidesharecdn.com/recommendation-for-improving-authentication-for-our-online-systems-at-pace-v20-1233004523650810-3/85/Recommendation-For-Improving-Authentication-For-Our-Online-Systems-At-Pace-V2-0-11-320.jpg)
Recommended
Resume - Lyman Holton - 160210 (SA)



Resume - Lyman Holton - 160210 (SA)Lyman L. Holton, MBA, BS
╠²
Lyman L. Holton is seeking a new career opportunity and has over 25 years of experience in security, education, sales, and consulting. He has a Master's in Business Administration and a Bachelor's in Information Technology Management, both completed with honors. Holton has strong communication, analytical, and computer skills and experience managing security operations and personnel in Korea and the United States.Tamu V1 5



Tamu V1 5monacofamily
╠²
Project SPARTA was Pace University's implementation of the Sungard Banner Enterprise Resource Planning (ERP) system to streamline administrative processes and provide real-time access to services. The multi-year project was led by Chief Information Officer Frank Monaco and included replacing older systems with an integrated Oracle database, SCT Banner modules, and third-party applications accessed through a central MyPace portal. Stakeholder engagement and change management were keys to the project's success in transitioning the university to a digital environment.USMA 1970 National Conference on Ethics in America



USMA 1970 National Conference on Ethics in Americamonacofamily
╠²
The document summarizes the 2009 National Conference on Ethics in America to be hosted by the United States Military Academy from October 18-22. The conference will bring together senior leaders, mentors, 180 student delegates and 30 faculty delegates from colleges across the country to discuss ethical issues. Over the course of four days, participants will attend plenary lectures and small group discussions. They will also have the opportunity to engage directly with senior leaders. The document outlines the schedule, speakers, Military Academy staff organizing the event and near term milestones to prepare for the conference.Pace Information Exchange Proposal 12 9 05 Final Version



Pace Information Exchange Proposal 12 9 05 Final Versionmonacofamily
╠²
How a Comprehensive Knowledge base could have been built at Pace University - but this was NOT approved by new administrationStrategic Plans For The Technical And Human Sides Of Convergence



Strategic Plans For The Technical And Human Sides Of Convergencemonacofamily
╠²
Briefing Given to explain a methodology for balancing technical and people issues in a large project implementationNational Cabinet Presentation 2009



National Cabinet Presentation 2009mekogan
╠²
NCC Company was established in 2004 and has over 40 years of experience in cabinet and complimentary product distribution. It aims to provide unique, quality products and optimal service at lowest cost to multi-family developers, property managers, condo developers, and general contractors. NCC partners with 6 cabinet manufacturers and offers products like cabinetry, countertops, and hardware. It provides services like measuring, ordering, delivery management, and turnkey installation to reduce costs and promote optimal return on investment for clients. NCC has a variety of current and past clients across the US.Hudson Samples



Hudson Samplesguestd2728
╠²
The document is an issue of DairyBusiness magazine from October 2008. It provides an alphabetized overview of important issues and events that impacted the dairy industry in 2008, from A (AFACT) to Z (Year in Review). Each letter highlights a topic, such as elections, exports, ethanol, and the economy, with a brief description of how it related to dairy that year. The magazine aims to be a relevant media source for the dairy business.Timely Emergency Notification Systems



Timely Emergency Notification Systemsmonacofamily
╠²
The document discusses the need for timely emergency notification systems at universities to comply with the Clery Act and protect campus communities. It analyzes options for Pace University, from basic email/text messaging to more robust systems integrating voice, text, email and other channels. The recommendation is to initially use an in-house system for email/text, then engage an outside provider offering more capabilities for around $30,000-$35,000 annually as budget allows.8 passwordsecurity



8 passwordsecurityricharddxd
╠²
The document discusses password security, explaining authentication and authorization, how passwords are used to control access, the importance of strong password selection to prevent cracking, and provides guidelines for password policies and creating strong passwords to protect against attacks. It examines common authentication methods, why passwords should be complex and regularly changed, and tools that can crack passwords if they are weak.Two-factor authentication- A sample writing _Zaman



Two-factor authentication- A sample writing _ZamanAsad Zaman
╠²
This document discusses various authentication methods including passwords, biometrics, tokens, two-factor authentication, and multi-factor authentication. It provides details on each method, including their strengths, weaknesses, and how they provide different levels of security. Multiple authentication factors can be combined to achieve stronger authentication through a multi-factor approach. The document also includes examples of how different authentication methods may be suitable for different access levels and use cases.Three Step Multifactor Authentication Systems for Modern Security



Three Step Multifactor Authentication Systems for Modern Securityijtsrd
╠²
Three factor authentication includes all major features in password authentication such as one factor authentication. Using passwords and two factor authentication is not enough to provide the best protection in the digital age significantly. Advances in the field of information technology. Even when one or two feature authentication was used to protect the remote control system, hacking tools, it was a simple computer program to collect private keys, and private generators made it difficult to provide protection. Security threats based on malware, such as key trackers installed, continue to be available to improve security risks. This requires the use of safe and easy to use materials. As a result, Three Level Security is an easy to use software. Soumyashree RK | Goutham S "Three Step Multifactor Authentication Systems for Modern Security" Published in International Journal of Trend in Scientific Research and Development (ijtsrd), ISSN: 2456-6470, Volume-6 | Issue-3 , April 2022, URL: https://www.ijtsrd.com/papers/ijtsrd49785.pdf Paper URL: https://www.ijtsrd.com/computer-science/computer-security/49785/three-step-multifactor-authentication-systems-for-modern-security/soumyashree-rk
Making User Authentication More Usable



Making User Authentication More UsableJim Fenton
╠²
A recent revision to the US GovernmentŌĆÖs authentication guideline, NIST SP 800-63B "Authentication and Lifecycle Management", puts a greater emphasis on the usability of authentication in its recommendations. This talk will discuss the ways in which it attempts to relieve the usersŌĆÖ burden and shift more responsibility to the services themselves, hopefully improving overall security in the process.
Presentation to BayCHI, December 12, 2017Session4-Authentication



Session4-Authenticationzakieh alizadeh
╠²
Table of Content
Common Web Authentication Threats
Common Weak Web Authentication Strategies
Strategies For Strong Authentication
Improving Password Based Security



Improving Password Based SecurityRare Input
╠²
This presentation brings you how you can Improve Password Based Security.
For more visit: http://www.rareinput.com/An Enhanced Security System for Web Authentication 



An Enhanced Security System for Web Authentication IJMER
╠²
Web authentication has low security in these days. Todays, For Authentication purpose,
Textual passwords are commonly used; however, users do not follow their requirements. Users tend to
choose meaningful words from dictionaries, which make textual passwords easy tobreak and vulnerable
to dictionary or brute force attacks. Also, Textual passwords can be identified by 3rd
party softwareŌĆÖs.
Many available graphicalpasswords have a password space that is less than or equal to the textual
passwordspace. Smart cards or tokens can be stolen.There are so many biometric authentications have
been proposed; however, users tend to resistusing biometrics because of their intrusiveness and the effect
on their privacy. Moreover,biometrics cannot be evoked.In this paper, we present and evaluate our
contribution,i.e., the OTP and 3-D password. A one-time password (OTP) is a password that isvalid for
only one login session or transaction. OTPs avoid a number of shortcomingsthat are associated with
traditional (static) passwords. The most important shortcoming that is addressed by OTPs is that, in
contrast to static passwords, they are not vulnerable to replay attacks. It means that a potential intruder
who manages to record an OTPthat was already used to log into a service or to conduct a transaction
will not be able toabuse it, since it will be no longer valid. The 3-D password is a multifactor
authenticationscheme. To be authenticated, we present a 3-D virtual environment where the
usernavigates and interacts with various objects. The sequence of actions and interactionstoward the
objects inside the 3-D environment constructs the userŌĆÖs 3-D password.
IRJET- Graphical user Authentication for an Alphanumeric OTP



IRJET- Graphical user Authentication for an Alphanumeric OTPIRJET Journal
╠²
This document discusses graphical passwords as an alternative to traditional alphanumeric passwords. It summarizes different types of graphical password authentication techniques, including recognition-based systems where users select images during registration and later identify those images to log in. It also discusses recall-based systems where users recreate a password by clicking or drawing on images. The document proposes using a one-time password (OTP) with graphical passwords to enhance security against shoulder surfing attacks, where the OTP provides information about which items to click in an image for authentication. Overall, the document analyzes the security and usability advantages of graphical passwords compared to traditional text-based passwords.Configurable Password Management: Balancing Usability and Compliance



Configurable Password Management: Balancing Usability and CompliancePortalGuard
╠²
This document provides an overview of the configurable password management features of PortalGuard software. It describes how PortalGuard allows organizations to define password policies that can be applied to individual users, groups, or domains to enforce strong passwords. Policies control properties such as password length, complexity, expiration, and history. The document outlines how PortalGuard checks passwords against policies, provides self-service password reset, and balances security and usability.Don't Get Stung - Student Data Security 



Don't Get Stung - Student Data Security cschumley
╠²
Presentation to California Community College Financial Aid Directors 2015 conference about best practices to protect the school from data breachesVoice Biometrics automated password_reset



Voice Biometrics automated password_resetKunal Grover
╠²
The document discusses an automatic password reset solution called Nuance Password Reset Application. It would help address challenges around reducing IT help desk costs, increasing security for password resets, and improving efficiency. The solution uses voice biometrics to securely authenticate users and allow them to reset their own passwords without involving IT support staff. This is estimated to save organizations over $10 per password reset on average by automating the process.Password Strength Policy Query



Password Strength Policy QueryGloria Stoilova
╠²
I. Passwords are an important security measure that require complexity to prevent unauthorized access. Standards recommend passwords be at least 8 characters including 3 of 4 character types and not based on dictionary words.
II. Passwords should be complex, unique, and not related to the user. Common substitutions like 0 for o don't strengthen passwords.
III. Passwords must be kept secret, changed if compromised, and different for different accounts and levels of access. Secure transmission is also important.Email Retention Policy1.0 PurposeThe Email Retention Polic.docx



Email Retention Policy1.0 PurposeThe Email Retention Polic.docxchristinemaritza
╠²
Email Retention Policy
1.0 Purpose
The Email Retention Policy is intended to help employees determine what information sent or received by email should be retained and for how long.
The information covered in these guidelines includes, but is not limited to, information that is either stored or shared via electronic mail or instant messaging technologies.
All employees should familiarize themselves with the email retention topic areas that follow this introduction.
Questions about the proper classification of a specific piece of information should be addressed to your manager. Questions about these guidelines should be addressed to Infosec.
2.0 Scope
This email retention policy is secondary to <Company Name> policy on Freedom of Information and Business Record Keeping. Any email that contains information in the scope of the Business Record Keeping policy should be treated in that manner. All <Company Name> email information is categorized into four main classifications with retention guidelines:
Administrative Correspondence (4 years)
Fiscal Correspondence (4 years)
General Correspondence (1 year)
Ephemeral Correspondence (Retain until read, destroy)
3.0 Policy
3.1 Administrative Correspondence
<Company Name> Administrative Correspondence includes, though is not limited to clarification of established company policy, including holidays, time card information, dress code, work place behavior and any legal issues such as intellectual property violations. All email with the information sensitivity label Management Only shall be treated as Administrative Correspondence. To ensure Administrative Correspondence is retained, a mailbox [email╠²protected]<Company Name> has been created, if you copy (cc) this address when you send email, retention will be administered by the IT Department.
3.2 Fiscal Correspondence
<Company Name> Fiscal Correspondence is all information related to revenue and expense for the company. To ensure Fiscal Correspondence is retained, a mailbox [email╠²protected]<Company Name> has been created, if you copy (cc) this address when you send email, retention will be administered by the IT Department.
3.3 General Correspondence
<Company Name> General Correspondence covers information that relates to customer interaction and the operational decisions of the business. The individual employee is responsible for email retention of General Correspondence.
3.4 Ephemeral Correspondence
<Company Name> Ephemeral Correspondence is by far the largest category and includes personal email, requests for recommendations or review, email related to product development, updates and status reports.
3.5 Instant Messenger Correspondence
<Company Name> Instant Messenger General Correspondence may be saved with logging function of Instant Messenger, or copied into a file and saved. Instant Messenger conversations that are Administrative or Fiscal in nature should be copied into an email message and sent to the appropr.information security and backup system



information security and backup systemEngr. Md. Jamal Uddin Rayhan
╠²
An information system is a set of components that collect, process, store, and distribute information to support decision making in an organization. It includes hardware, software, data, procedures, and human resources. Information security aims to protect these assets by implementing policies, access controls, encryption, firewalls, and monitoring, as well as physical security controls. Regular backups of important data are also crucial, and different backup media like tapes, disks, and cloud storage should be considered based on factors like speed, reliability, capacity, and cost. Proper backup procedures and disaster recovery plans help ensure data is protected and can be restored in case of issues.Password management



Password managementKaren F
╠²
This was a technology class sponsored by the Cochise County Library District.
See https://www.makingandsharing.com/summer-tech-learning/C02



C02newbie2019
╠²
The document discusses authentication, authorization, and accounting (the three As) as a leading model for access control. It describes authentication as identifying users, usually with a username and password. Authorization gives users access to resources based on their identity. Accounting (also called auditing) tracks user activity like time spent and services accessed. The document provides details on different authentication methods like passwords, PINs, smart cards, and digital certificates. It emphasizes the importance of strong passwords and changing them regularly.M-Pass: Web Authentication Protocol



M-Pass: Web Authentication ProtocolIJERD Editor
╠²
This document summarizes a research paper on M-Pass, a proposed user authentication protocol that aims to prevent password stealing and reuse attacks. M-Pass leverages cell phones and SMS to authenticate users on untrusted devices without requiring them to enter passwords. It involves a registration phase where users register with a website and encrypt a password with their phone number. For login, users provide their username and long-term phone password, and the website generates a one-time password using a secret credential. The protocol aims to eliminate the need to remember multiple passwords by using the phone for authentication across websites. Evaluation shows registration and login times average around 4 and 3.5 minutes respectively. The researchers conclude M-Pass can prevent password stealing and reusePasswordless auth



Passwordless authLesha Bhansali
╠²
The history of passwords, its vulnerabilities, why the way we authenticate needs to change, potential solutions A Novel Web-based Approach for Balancing Usability and Security Requirements ...



A Novel Web-based Approach for Balancing Usability and Security Requirements ...IJNSA Journal
╠²
This document describes a novel web-based framework called iPass that aims to balance usability and security requirements for text passwords. The framework educates users on password strength, monitors entered passwords for strength, and provides feedback to help users select stronger passwords that meet usability needs. It was developed to address the conflicting goals of users wanting easy passwords and services requiring strong security. The framework suggests transformed versions of entered passwords or allows user selection from options to improve strength while considering memorability.Ch10 system administration 



Ch10 system administration Raja Waseem Akhtar
╠²
The document discusses user account management tasks for system administrators, including creating login names, assigning home directories and user IDs, setting passwords and password policies, and tools for managing user accounts. It covers challenges around reusable passwords and approaches to improve security such as password aging, lockouts for failed attempts, and one-time password tokens.KISS: Proven Strategies to Stay Connected with Online Students!



KISS: Proven Strategies to Stay Connected with Online Students!monacofamily
╠²
Teaching online without the benefit of face-to-face interaction has many challenges.
However, over the years of teaching in the classroom and online both at the graduate and undergraduate level, the author has found some very simple strategies (often overlooked) that can greatly increase student satisfaction with online delivery almost to the level of good face-to-face instruction.
This session will enumerate (and demonstrate) several of these extremely simple proven strategies, that, when enthusiastically executed, can vastly improve online connectivity and dialogue with students.
If these ŌĆ£KISSŌĆØ strategies are added to an online adjunctŌĆÖs toolbox, higher satisfaction and better teaching and learning could result.
2012-NCEA-Presentation



2012-NCEA-Presentationmonacofamily
╠²
The document summarizes the National Conference on Ethics in America held at West Point Military Academy. It provides details on the conference structure and goals. The conference is sponsored by AT&T and the West Point Class of 1970. It brings together student delegates, faculty members, and senior leaders from business, education, and military fields to discuss ethics. Through plenary sessions, breakout groups, and panels, the conference aims to share best practices in teaching ethics and create practical ideas for applying ethics.More Related Content
Similar to Recommendation For Improving Authentication For Our Online Systems At Pace V2.0 (20)
8 passwordsecurity



8 passwordsecurityricharddxd
╠²
The document discusses password security, explaining authentication and authorization, how passwords are used to control access, the importance of strong password selection to prevent cracking, and provides guidelines for password policies and creating strong passwords to protect against attacks. It examines common authentication methods, why passwords should be complex and regularly changed, and tools that can crack passwords if they are weak.Two-factor authentication- A sample writing _Zaman



Two-factor authentication- A sample writing _ZamanAsad Zaman
╠²
This document discusses various authentication methods including passwords, biometrics, tokens, two-factor authentication, and multi-factor authentication. It provides details on each method, including their strengths, weaknesses, and how they provide different levels of security. Multiple authentication factors can be combined to achieve stronger authentication through a multi-factor approach. The document also includes examples of how different authentication methods may be suitable for different access levels and use cases.Three Step Multifactor Authentication Systems for Modern Security



Three Step Multifactor Authentication Systems for Modern Securityijtsrd
╠²
Three factor authentication includes all major features in password authentication such as one factor authentication. Using passwords and two factor authentication is not enough to provide the best protection in the digital age significantly. Advances in the field of information technology. Even when one or two feature authentication was used to protect the remote control system, hacking tools, it was a simple computer program to collect private keys, and private generators made it difficult to provide protection. Security threats based on malware, such as key trackers installed, continue to be available to improve security risks. This requires the use of safe and easy to use materials. As a result, Three Level Security is an easy to use software. Soumyashree RK | Goutham S "Three Step Multifactor Authentication Systems for Modern Security" Published in International Journal of Trend in Scientific Research and Development (ijtsrd), ISSN: 2456-6470, Volume-6 | Issue-3 , April 2022, URL: https://www.ijtsrd.com/papers/ijtsrd49785.pdf Paper URL: https://www.ijtsrd.com/computer-science/computer-security/49785/three-step-multifactor-authentication-systems-for-modern-security/soumyashree-rk
Making User Authentication More Usable



Making User Authentication More UsableJim Fenton
╠²
A recent revision to the US GovernmentŌĆÖs authentication guideline, NIST SP 800-63B "Authentication and Lifecycle Management", puts a greater emphasis on the usability of authentication in its recommendations. This talk will discuss the ways in which it attempts to relieve the usersŌĆÖ burden and shift more responsibility to the services themselves, hopefully improving overall security in the process.
Presentation to BayCHI, December 12, 2017Session4-Authentication



Session4-Authenticationzakieh alizadeh
╠²
Table of Content
Common Web Authentication Threats
Common Weak Web Authentication Strategies
Strategies For Strong Authentication
Improving Password Based Security



Improving Password Based SecurityRare Input
╠²
This presentation brings you how you can Improve Password Based Security.
For more visit: http://www.rareinput.com/An Enhanced Security System for Web Authentication 



An Enhanced Security System for Web Authentication IJMER
╠²
Web authentication has low security in these days. Todays, For Authentication purpose,
Textual passwords are commonly used; however, users do not follow their requirements. Users tend to
choose meaningful words from dictionaries, which make textual passwords easy tobreak and vulnerable
to dictionary or brute force attacks. Also, Textual passwords can be identified by 3rd
party softwareŌĆÖs.
Many available graphicalpasswords have a password space that is less than or equal to the textual
passwordspace. Smart cards or tokens can be stolen.There are so many biometric authentications have
been proposed; however, users tend to resistusing biometrics because of their intrusiveness and the effect
on their privacy. Moreover,biometrics cannot be evoked.In this paper, we present and evaluate our
contribution,i.e., the OTP and 3-D password. A one-time password (OTP) is a password that isvalid for
only one login session or transaction. OTPs avoid a number of shortcomingsthat are associated with
traditional (static) passwords. The most important shortcoming that is addressed by OTPs is that, in
contrast to static passwords, they are not vulnerable to replay attacks. It means that a potential intruder
who manages to record an OTPthat was already used to log into a service or to conduct a transaction
will not be able toabuse it, since it will be no longer valid. The 3-D password is a multifactor
authenticationscheme. To be authenticated, we present a 3-D virtual environment where the
usernavigates and interacts with various objects. The sequence of actions and interactionstoward the
objects inside the 3-D environment constructs the userŌĆÖs 3-D password.
IRJET- Graphical user Authentication for an Alphanumeric OTP



IRJET- Graphical user Authentication for an Alphanumeric OTPIRJET Journal
╠²
This document discusses graphical passwords as an alternative to traditional alphanumeric passwords. It summarizes different types of graphical password authentication techniques, including recognition-based systems where users select images during registration and later identify those images to log in. It also discusses recall-based systems where users recreate a password by clicking or drawing on images. The document proposes using a one-time password (OTP) with graphical passwords to enhance security against shoulder surfing attacks, where the OTP provides information about which items to click in an image for authentication. Overall, the document analyzes the security and usability advantages of graphical passwords compared to traditional text-based passwords.Configurable Password Management: Balancing Usability and Compliance



Configurable Password Management: Balancing Usability and CompliancePortalGuard
╠²
This document provides an overview of the configurable password management features of PortalGuard software. It describes how PortalGuard allows organizations to define password policies that can be applied to individual users, groups, or domains to enforce strong passwords. Policies control properties such as password length, complexity, expiration, and history. The document outlines how PortalGuard checks passwords against policies, provides self-service password reset, and balances security and usability.Don't Get Stung - Student Data Security 



Don't Get Stung - Student Data Security cschumley
╠²
Presentation to California Community College Financial Aid Directors 2015 conference about best practices to protect the school from data breachesVoice Biometrics automated password_reset



Voice Biometrics automated password_resetKunal Grover
╠²
The document discusses an automatic password reset solution called Nuance Password Reset Application. It would help address challenges around reducing IT help desk costs, increasing security for password resets, and improving efficiency. The solution uses voice biometrics to securely authenticate users and allow them to reset their own passwords without involving IT support staff. This is estimated to save organizations over $10 per password reset on average by automating the process.Password Strength Policy Query



Password Strength Policy QueryGloria Stoilova
╠²
I. Passwords are an important security measure that require complexity to prevent unauthorized access. Standards recommend passwords be at least 8 characters including 3 of 4 character types and not based on dictionary words.
II. Passwords should be complex, unique, and not related to the user. Common substitutions like 0 for o don't strengthen passwords.
III. Passwords must be kept secret, changed if compromised, and different for different accounts and levels of access. Secure transmission is also important.Email Retention Policy1.0 PurposeThe Email Retention Polic.docx



Email Retention Policy1.0 PurposeThe Email Retention Polic.docxchristinemaritza
╠²
Email Retention Policy
1.0 Purpose
The Email Retention Policy is intended to help employees determine what information sent or received by email should be retained and for how long.
The information covered in these guidelines includes, but is not limited to, information that is either stored or shared via electronic mail or instant messaging technologies.
All employees should familiarize themselves with the email retention topic areas that follow this introduction.
Questions about the proper classification of a specific piece of information should be addressed to your manager. Questions about these guidelines should be addressed to Infosec.
2.0 Scope
This email retention policy is secondary to <Company Name> policy on Freedom of Information and Business Record Keeping. Any email that contains information in the scope of the Business Record Keeping policy should be treated in that manner. All <Company Name> email information is categorized into four main classifications with retention guidelines:
Administrative Correspondence (4 years)
Fiscal Correspondence (4 years)
General Correspondence (1 year)
Ephemeral Correspondence (Retain until read, destroy)
3.0 Policy
3.1 Administrative Correspondence
<Company Name> Administrative Correspondence includes, though is not limited to clarification of established company policy, including holidays, time card information, dress code, work place behavior and any legal issues such as intellectual property violations. All email with the information sensitivity label Management Only shall be treated as Administrative Correspondence. To ensure Administrative Correspondence is retained, a mailbox [email╠²protected]<Company Name> has been created, if you copy (cc) this address when you send email, retention will be administered by the IT Department.
3.2 Fiscal Correspondence
<Company Name> Fiscal Correspondence is all information related to revenue and expense for the company. To ensure Fiscal Correspondence is retained, a mailbox [email╠²protected]<Company Name> has been created, if you copy (cc) this address when you send email, retention will be administered by the IT Department.
3.3 General Correspondence
<Company Name> General Correspondence covers information that relates to customer interaction and the operational decisions of the business. The individual employee is responsible for email retention of General Correspondence.
3.4 Ephemeral Correspondence
<Company Name> Ephemeral Correspondence is by far the largest category and includes personal email, requests for recommendations or review, email related to product development, updates and status reports.
3.5 Instant Messenger Correspondence
<Company Name> Instant Messenger General Correspondence may be saved with logging function of Instant Messenger, or copied into a file and saved. Instant Messenger conversations that are Administrative or Fiscal in nature should be copied into an email message and sent to the appropr.information security and backup system



information security and backup systemEngr. Md. Jamal Uddin Rayhan
╠²
An information system is a set of components that collect, process, store, and distribute information to support decision making in an organization. It includes hardware, software, data, procedures, and human resources. Information security aims to protect these assets by implementing policies, access controls, encryption, firewalls, and monitoring, as well as physical security controls. Regular backups of important data are also crucial, and different backup media like tapes, disks, and cloud storage should be considered based on factors like speed, reliability, capacity, and cost. Proper backup procedures and disaster recovery plans help ensure data is protected and can be restored in case of issues.Password management



Password managementKaren F
╠²
This was a technology class sponsored by the Cochise County Library District.
See https://www.makingandsharing.com/summer-tech-learning/C02



C02newbie2019
╠²
The document discusses authentication, authorization, and accounting (the three As) as a leading model for access control. It describes authentication as identifying users, usually with a username and password. Authorization gives users access to resources based on their identity. Accounting (also called auditing) tracks user activity like time spent and services accessed. The document provides details on different authentication methods like passwords, PINs, smart cards, and digital certificates. It emphasizes the importance of strong passwords and changing them regularly.M-Pass: Web Authentication Protocol



M-Pass: Web Authentication ProtocolIJERD Editor
╠²
This document summarizes a research paper on M-Pass, a proposed user authentication protocol that aims to prevent password stealing and reuse attacks. M-Pass leverages cell phones and SMS to authenticate users on untrusted devices without requiring them to enter passwords. It involves a registration phase where users register with a website and encrypt a password with their phone number. For login, users provide their username and long-term phone password, and the website generates a one-time password using a secret credential. The protocol aims to eliminate the need to remember multiple passwords by using the phone for authentication across websites. Evaluation shows registration and login times average around 4 and 3.5 minutes respectively. The researchers conclude M-Pass can prevent password stealing and reusePasswordless auth



Passwordless authLesha Bhansali
╠²
The history of passwords, its vulnerabilities, why the way we authenticate needs to change, potential solutions A Novel Web-based Approach for Balancing Usability and Security Requirements ...



A Novel Web-based Approach for Balancing Usability and Security Requirements ...IJNSA Journal
╠²
This document describes a novel web-based framework called iPass that aims to balance usability and security requirements for text passwords. The framework educates users on password strength, monitors entered passwords for strength, and provides feedback to help users select stronger passwords that meet usability needs. It was developed to address the conflicting goals of users wanting easy passwords and services requiring strong security. The framework suggests transformed versions of entered passwords or allows user selection from options to improve strength while considering memorability.Ch10 system administration 



Ch10 system administration Raja Waseem Akhtar
╠²
The document discusses user account management tasks for system administrators, including creating login names, assigning home directories and user IDs, setting passwords and password policies, and tools for managing user accounts. It covers challenges around reusable passwords and approaches to improve security such as password aging, lockouts for failed attempts, and one-time password tokens.More from monacofamily (6)
KISS: Proven Strategies to Stay Connected with Online Students!



KISS: Proven Strategies to Stay Connected with Online Students!monacofamily
╠²
Teaching online without the benefit of face-to-face interaction has many challenges.
However, over the years of teaching in the classroom and online both at the graduate and undergraduate level, the author has found some very simple strategies (often overlooked) that can greatly increase student satisfaction with online delivery almost to the level of good face-to-face instruction.
This session will enumerate (and demonstrate) several of these extremely simple proven strategies, that, when enthusiastically executed, can vastly improve online connectivity and dialogue with students.
If these ŌĆ£KISSŌĆØ strategies are added to an online adjunctŌĆÖs toolbox, higher satisfaction and better teaching and learning could result.
2012-NCEA-Presentation



2012-NCEA-Presentationmonacofamily
╠²
The document summarizes the National Conference on Ethics in America held at West Point Military Academy. It provides details on the conference structure and goals. The conference is sponsored by AT&T and the West Point Class of 1970. It brings together student delegates, faculty members, and senior leaders from business, education, and military fields to discuss ethics. Through plenary sessions, breakout groups, and panels, the conference aims to share best practices in teaching ethics and create practical ideas for applying ethics.Ethical hacking



Ethical hackingmonacofamily
╠²
The document provides an overview of ethical hacking, including definitions, legal aspects, and certification programs. It describes the role of an ethical hacker as someone who performs penetration testing and security assessments with a company's permission to help identify vulnerabilities. Key points covered include common tools used in security testing, examples of legal and illegal activities, and various certification programs for security professionals like the Certified Ethical Hacker and CISSP certifications.Final Draft of IT 402 Presentation



Final Draft of IT 402 Presentationmonacofamily
╠²
The document discusses a senior design project from 1970 where the author created a limited assembler for the GE-235 computer. It then provides the author's background and experience working with early computer systems from the 1960s through today. Key lessons discussed include understanding user needs, allowing for growth and change using Moore's Law, managing expectations through the Gartner Hype Cycle, and an iterative design process of testing, fixing, and retesting.I I K D For Public Info Version II



I I K D For Public Info Version IImonacofamily
╠²
The document proposes a recommendation for a continuing education program to provide additional training to state and municipal police officers in Puerto Rico. It recommends several training subjects, including defensive tactics, victims of crime awareness, physical fitness, basic building entry, and classroom firearms instruction. For each subject, it provides a description of the course objectives and teaching methods. The proposal argues that the International Institute of Knowledge and Defense is well-suited to develop and deliver this continuing education program due to its qualified trainers and ability to further enhance police training.Trends In Higher Ed



Trends In Higher Edmonacofamily
╠²
1) Computational devices and networks will continue converging both physically and logically, with voice, data, video and other functions combining in various devices and seamless network transfer enabled.
2) Social interactivity will dominate as new technologies emerge that facilitate many-to-many interaction and users are immersed in virtual spaces.
3) Moore's Law will continue enabling technological evolution as chip capabilities double every two years, though challenges remain in universities keeping pace with the rapid changes.Recently uploaded (20)
Leadership u automatizaciji: RPA pri─Źe iz prakse!



Leadership u automatizaciji: RPA pri─Źe iz prakse!UiPathCommunity
╠²
Dobrodo┼Īli na "AI Powered Automation Leadership Talks", online doga─æaj koji okuplja senior lidere i menad┼Šere iz razli─Źitih industrija kako bi podelili svoja iskustva, izazove i strategije u oblasti RPA (Robotic Process Automation). Ovaj doga─æaj pru┼Ša priliku da zavirite u na─Źin razmi┼Īljanja ljudi koji donose klju─Źne odluke u automatizaciji i liderstvu.
¤ōĢ Kroz panel diskusiju sa tri izuzetna stru─Źnjaka, istra┼Ši─ćemo:
Kako uspe┼Īno zapo─Źeti i skalirati RPA projekte u organizacijama.
Koji su najve─ći izazovi u implementaciji RPA-a i kako ih prevazi─ći.
Na koje na─Źine automatizacija menja radne procese i poma┼Še timovima da ostvare vi┼Īe.
Bez obzira na va┼Īe iskustvo sa UiPath-om ili RPA uop┼Īte, ovaj doga─æaj je osmi┼Īljen kako bi bio koristan svima ŌĆō od menad┼Šera do tehni─Źkih lidera, i svima koji ┼Šele da unaprede svoje razumevanje automatizacije.
Pridru┼Šite nam se i iskoristite ovu jedinstvenu priliku da nau─Źite od onih koji vode automatizaciju u svojim organizacijama. Pripremite svoja pitanja i inspiraciju za slede─će korake u va┼Īoj RPA strategiji!Transcript: AI in publishing: Your questions answered - Tech Forum 2025



Transcript: AI in publishing: Your questions answered - Tech Forum 2025BookNet Canada
╠²
George Walkley, a publishing veteran and leading authority on AI applications, joins us for a follow-up to his presentation "Applying AI to publishing: A balanced and ethical approach". George gives a brief overview of developments since that presentation and answers attendees' pressing questions about AIŌĆÖs impact and potential applications in the book industry.
Link to recording and presentation slides: https://bnctechforum.ca/sessions/ai-in-publishing-your-questions-answered/
Presented by BookNet Canada on February 20, 2025 with support from the Department of Canadian Heritage.UiPath Document Understanding - Generative AI and Active learning capabilities



UiPath Document Understanding - Generative AI and Active learning capabilitiesDianaGray10
╠²
This session focus on Generative AI features and Active learning modern experience with Document understanding.
Topics Covered:
Overview of Document Understanding
How Generative Annotation works?
What is Generative Classification?
How to use Generative Extraction activities?
What is Generative Validation?
How Active learning modern experience accelerate model training?
Q/A
ŌØō If you have any questions or feedback, please refer to the "Women in Automation 2025" dedicated Forum thread. You can find there extra details and updates. Agentic AI: The 2025 Next-Gen Automation Guide



Agentic AI: The 2025 Next-Gen Automation GuideThoughtminds
╠²
Introduction to Agentic AI: Explains how it differs from traditional automation and its ability to make independent decisions.
Comparison with Generative AI: A structured comparison between Generative AI (content creation) and Agentic AI (autonomous action-taking).
Technical Breakdown: Covers core components such as LLMs, reinforcement learning, and cloud infrastructure that power Agentic AI.
Real-World Use Cases (2025 & Beyond): Examines how Agentic AI is transforming industries like insurance, healthcare, retail, finance, and cybersecurity.
Business Impact & ROI: Discusses case studies from Unilever, FedEx, and more, showcasing cost savings and operational efficiency improvements.
Challenges & Risks: Highlights bias, security threats, regulatory compliance, and workforce reskilling as critical challenges in AI adoption.
5-Step Implementation Strategy: A practical roadmap to help organizations integrate Agentic AI seamlessly.
Future Predictions (2025-2030): Forecasts on AI-driven workforce evolution, industry disruptions, and the rise of Quantum AI.Combining Lexical and Semantic Search with Milvus 2.5



Combining Lexical and Semantic Search with Milvus 2.5Zilliz
╠²
In short, lexical search is a way to search your documents based on the keywords they contain, in contrast to semantic search, which compares the similarity of embeddings. WeŌĆÖll be covering:
ŌĆŗWhy, when, and how should you use lexical search
ŌĆŗWhat is the BM25 distance metric
ŌĆŗHow exactly does Milvus 2.5 implement lexical search
ŌĆŗHow to build an improved hybrid lexical + semantic search with Milvus 2.5Caching for Performance Masterclass: Caching Strategies



Caching for Performance Masterclass: Caching StrategiesScyllaDB
╠²
Exploring the tradeoffs of common caching strategies ŌĆō and a look at the architectural differences.
- Which strategies exist
- When to apply different strategies
- ScyllaDB cache designGDG Cloud Southlake #40: Brandon Stokes: How to Build a Great Product



GDG Cloud Southlake #40: Brandon Stokes: How to Build a Great ProductJames Anderson
╠²
How to Build a Great Product
Being a tech entrepreneur is about providing a remarkable product or service that serves the needs of its customers better, faster, and cheaper than anything else. The goal is to "make something people want" which we call, product market fit.
But how do we get there? We'll explore the process of taking an idea to product market fit (PMF), how you know you have true PMF, and how your product strategies differ pre-PMF from post-PMF.
Brandon is a 3x founder, 1x exit, ex-banker & corporate strategist, car dealership owner, and alumnus of Techstars & Y Combinator. He enjoys building products and services that impact people for the better.
Brandon has had 3 different careers (banking, corporate finance & strategy, technology) in 7 different industries; Investment Banking, CPG, Media & Entertainment, Telecommunications, Consumer application, Automotive, & Fintech/Insuretech.
He's an idea to revenue leader and entrepreneur that helps organizations build products and processes, hire talent, test & iterate quickly, collect feedback, and grow in unregulated and heavily regulated industries.Predictive vs. Preventive Maintenance ŌĆö Which One is Right for Your Factory



Predictive vs. Preventive Maintenance ŌĆö Which One is Right for Your FactoryDiagsense ltd
╠²
Efficient maintenance is the backbone of any manufacturing operation. It ensures that machinery runs smoothly, minimizes downtime and optimizes overall productivity. Earlier, factories have relied on preventive maintenance but with advancements in technology, Manufacturing PdM Solutions is gaining traction. The question isŌĆöwhich one is the right fit for your factory? LetŌĆÖs break it down.AI Trends and Fun Demos ŌĆō SothebyŌĆÖs Rehoboth Presentation



AI Trends and Fun Demos ŌĆō SothebyŌĆÖs Rehoboth PresentationEthan Holland
╠²
Ethan B. Holland explores the impact of artificial intelligence on real estate and digital transformation. Covering key AI trends such as multimodal AI, agency, co-pilots, and AI-powered computer usage, the document highlights how emerging technologies are reshaping industries. It includes real-world demonstrations of AI in action, from automated real estate insights to AI-generated voice and video applications. With expertise in digital transformation, Ethan shares insights from his work optimizing workflows with AI tools, automation, and large language models. This presentation is essential for professionals seeking to understand AIŌĆÖs role in business, automation, and real estate.
THE BIG TEN BIOPHARMACEUTICAL MNCs: GLOBAL CAPABILITY CENTERS IN INDIA



THE BIG TEN BIOPHARMACEUTICAL MNCs: GLOBAL CAPABILITY CENTERS IN INDIASrivaanchi Nathan
╠²
This business intelligence report, "The Big Ten Biopharmaceutical MNCs: Global Capability Centers in India", provides an in-depth analysis of the operations and contributions of the Global Capability Centers (GCCs) of ten leading biopharmaceutical multinational corporations in India. The report covers AstraZeneca, Bayer, Bristol Myers Squibb, GlaxoSmithKline (GSK), Novartis, Sanofi, Roche, Pfizer, Novo Nordisk, and Eli Lilly. In this report each company's GCC is profiled with details on location, workforce size, investment, and the strategic roles these centers play in global business operations, research and development, and information technology and digital innovation.William Maclyn Murphy McRae - A Seasoned Professional Renowned



William Maclyn Murphy McRae - A Seasoned Professional RenownedWilliam Maclyn Murphy McRae
╠²
William Maclyn Murphy McRae, a logistics expert with 9+ years of experience, is known for optimizing supply chain operations and consistently exceeding industry standards. His strategic approach, combined with hands-on execution, has streamlined distribution processes, reduced lead times, and consistently delivered exceptional results.Webinar: LF Energy GEISA: Addressing edge interoperability at the meter



Webinar: LF Energy GEISA: Addressing edge interoperability at the meterDanBrown980551
╠²
This webinar will introduce the Grid Edge Security and Interoperability Alliance, or GEISA, an effort within LF Energy to address application interoperability at the very edge of the utility network: meters and other distribution automation devices. Over the last decade platform manufacturers have introduced the ability to run applications on electricity meters and other edge devices. Unfortunately, while many of these efforts have been built on Linux, they havenŌĆÖt been interoperable. APIs and execution environment have varied from one manufacturer to the next making it impossible for utilities to obtain applications that they can run across a fleet of different devices. For utilities that want to minimize their supply chain risk by obtaining equipment from multiple suppliers, they are forced to run and maintain multiple separate management systems. Applications available for one device may need to be ported to run on another, or they may not be available at all.
GEISA addresses this by creating a vendor neutral specification for utility edge computing environments. This webinar will discuss why GEISA is important to utilities, the specific issues GEISA will solve and the new opportunities it creates for utilities, platform vendors, and application vendors. Dev Dives: Unlock the future of automation with UiPath Agent Builder



Dev Dives: Unlock the future of automation with UiPath Agent BuilderUiPathCommunity
╠²
This webinar will offer you a first look at the powerful capabilities of UiPath Agent Builder, designed to streamline your automation processes and enhance your workflow efficiency.
¤ōĢ During the session, you will:
- Discover how to build agents with low-code experience, making it accessible for both developers and business users.
- Learn how to leverage automations and activities as tools within your agents, enabling them to handle complex and dynamic workflows.
- Gain insights into the AI Trust Layer, which provides robust management and monitoring capabilities, ensuring trust and transparency in your automation processes.
- See how agents can be deployed and integrated with your existing UiPath cloud and Studio environments.
¤æ©ŌĆŹ¤Å½ Speaker:
Zach Eslami, Sr. Manager, Product Management Director, UiPath
ŌÅ® Register for our upcoming Dev Dives March session:
Unleash the power of macOS Automation with UiPath
¤æē AMER: https://bit.ly/Dev_Dives_AMER_March
¤æē EMEA & APJ:https://bit.ly/Dev_Dives_EMEA_APJ_March
This session was streamed live on February 27, 2025, 15:00 GMT.
Check out future Dev Dives 2025 sessions at:
¤Ü® https://bit.ly/Dev_Dives_2025
5 Must-Use AI Tools to Supercharge Your Productivity



5 Must-Use AI Tools to Supercharge Your Productivitycryptouniversityoffi
╠²
5 Must-Use AI Tools to Supercharge Your Productivity!
AI is changing the game! ¤ÜĆ From research to creativity and coding, here are 5 powerful AI tools you should try.
NotebookLM
¤ōÜ NotebookLM ŌĆō Your AI Research Assistant
Ō£ģ Organizes & summarizes notes
Ō£ģ Generates insights from multiple sources
Ō£ģ Ideal for students, researchers & writers
¤ōØ Boost your productivity with smarter note-taking!
Napkin.ai
¤Ä© Napkin.ai ŌĆō The Creativity Booster
Ō£ģ Connects and organizes ideas
Ō£ģ Perfect for writers, designers & entrepreneurs
Ō£ģ Acts as your AI-powered brainstorming partner
¤ÆĪ Unleash your creativity effortlessly!
DeepSeek
¤öŹ DeepSeek ŌĆō Smarter AI Search
Ō£ģ Delivers deeper & more precise search results
Ō£ģ Analyzes large datasets for better insights
Ō£ģ Ideal for professionals & researchers
¤öÄ Find what you needŌĆöfaster & smarter!
ChatGPT
¤Æ¼ ChatGPT ŌĆō Your AI Chat Assistant
Ō£ģ Answers questions, writes content & assists in coding
Ō£ģ Helps businesses with customer support
Ō£ģ Boosts learning & productivity
¤ż¢ From content to codingŌĆöChatGPT does it all!
Devin AI
¤Æ╗ Devin AI ŌĆō AI for Coders
Ō£ģ Writes, debugs & optimizes code
Ō£ģ Assists developers at all skill levels
Ō£ģ Makes coding faster & more efficient
¤æ©ŌĆŹ¤Æ╗ Let AI be your coding partner!
¤ÜĆ AI is transforming the way we work!MIND Revenue Release Quarter 4 2024 - Finacial Presentation



MIND Revenue Release Quarter 4 2024 - Finacial PresentationMIND CTI
╠²
MIND Revenue Release Quarter 4 2024 - Finacial PresentationTeaching Prompting and Prompt Sharing to End Users.pptx



Teaching Prompting and Prompt Sharing to End Users.pptxMichael Blumenthal (Microsoft MVP)
╠²
How to teach M365 Copilot and M365 Copilot Chat prompting to your colleagues. Presented at the Advanced Learning Institute's "Internal Communications Strategies with M365" event on February 27, 2025. Intended audience: Internal Communicators, User Adoption Specialists, IT.Understanding Traditional AI with Custom Vision & MuleSoft.pptx



Understanding Traditional AI with Custom Vision & MuleSoft.pptxshyamraj55
╠²
Understanding Traditional AI with Custom Vision & MuleSoft.pptx | ### ║▌║▌▀Ż Deck Description:
This presentation features Atul, a Senior Solution Architect at NTT DATA, sharing his journey into traditional AI using Azure's Custom Vision tool. He discusses how AI mimics human thinking and reasoning, differentiates between predictive and generative AI, and demonstrates a real-world use case. The session covers the step-by-step process of creating and training an AI model for image classification and object detectionŌĆöspecifically, an ad display that adapts based on the viewer's gender. Atulavan highlights the ease of implementation without deep software or programming expertise. The presentation concludes with a Q&A session addressing technical and privacy concerns.Recommendation For Improving Authentication For Our Online Systems At Pace V2.0
- 1. Recommendations for improving authentication for our online systems at Pace
- 2. Authentication practices in Higher Education - from bad to good No authentication Weak Passwords Complex Passwords Complex Passwords with frequent mandatory changes, depending on risk Biometrics Multi-Factor bad good
- 3. Current Pace Complex Password Rules must not contain more than 3 consecutive characters of your first name, last name, or username must be 8 or more characters long. must contain at least one character from three of these four categories: UPPERcase characters (A, B, C, ...) lowercase character (a, b, c, ...) numbers (1, 2, 3, ...) special characters (! * + - / : ? _ # $) (i.e. must have at least one uppercase letter, one lowercase letter, and one number) must not be one that you have recently used (you cannot use one of your last 3 passwords) cannot be changed more than once every 24 hours
- 4. Some useful hints for selecting a password Use the first letters of each word from a song, phrase, or quote and replace some letters with numbers. For example, "Mary had a little lamb who's fleece was white as snow!" would become Mha11wfwwa5! (substituting 1 for l and 5 for s). Include punctuation for a more secure password (only use the allowed special characters, which are ! % * + - / : ? _). Try to make the password as long as possible. The longer the password, the harder it is to crack or guess it. Do not write the password down and place on your desk!
- 5. What some other universities are doing about authenticationŌĆ” Enforced password resets occur routinely at: New York UniversityŌĆöall users every 365 days Hofstra UniversityŌĆöall users every 180 days New Jersey Institute of TechnologyŌĆöall users every 120 days Cornell UniversityŌĆöall users every 180 days Seton Hall UniversityŌĆöevery 90 days for administrative systems University of MarylandŌĆöall users every 180 days Penn StateŌĆöall users every 365 days Columbia UniversityŌĆöfaculty/staff every 90 days for ERP SUNY PurchaseŌĆöfaculty/staff every 90 days Note: Rutgers ŌĆō uses Multi-Factor for some ERP Applications
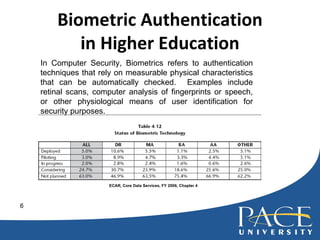
- 6. Biometric Authentication in Higher Education ECAR, Core Data Services, FY 2006, Chapter 4 In Computer Security, Biometrics refers to authentication techniques that rely on measurable physical characteristics that can be automatically checked. Examples include retinal scans, computer analysis of fingerprints or speech, or other physiological means of user identification for security purposes.
- 7. Multi-Factor (two Factor) Authentication Refers to any authentication protocol that requires more than one form of authentication to access a system. This contrasts with tradition password authentication, which requires only one factor (knowledge of the password) in order to gain access to a system. Three standard kinds of authentication factors are recognized: something you know (like a password or PIN), something you have (like a credit card or Cell Phone), or something you are (like a fingerprint, a retinal pattern, or other biometrics).
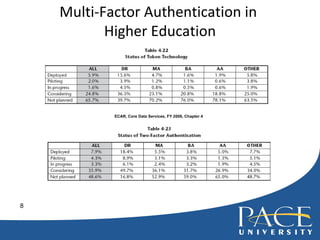
- 8. Multi-Factor Authentication in Higher Education ECAR, Core Data Services, FY 2006, Chapter 4
- 9. How to change your password go to PaceŌĆÖs Password Reset Utility (PRU) located at http://pru.pace.edu select Click here at the top of the page for guidelines and help when choosing a complex password review these guidelines and then select Click here to return to the PRU homepage change your password by selecting Change your password and following the prompts
- 10. Recommendation We should have the technical ability to assign risk categories to various classes of users in February, 2008. Once we have this capability, we should publish and enforce guidelines that ask those with the highest access rights to change their passwords more often than those with less access rights. We should continue to investigate Biometrics and Multi-factor for specific user groups
- 11. Questions? More information is available from the Division of Information Technology: phone: 914 ŌĆō 773 - 3648 via web: http:// doithelpdesk.pace.edu [email_address] , 914-923-2658



