RFID based access control ppt
- 1. RFID based AccessRFID based Access ControlControl S.PradheepS.Pradheep S.Vivek SwaminathanS.Vivek Swaminathan T.Balaji SrinivasanT.Balaji Srinivasan TCE, Madurai.TCE, Madurai.
- 2. What is RFID?What is RFID? ’ü« Radio Frequency IdentificationRadio Frequency Identification ’ü« Radio Frequency IdentificationRadio Frequency Identification ((RFIDRFID) is an) is an automatic identification method, relying on storing andautomatic identification method, relying on storing and remotely retrieving data using devices called RFID tagsremotely retrieving data using devices called RFID tags or transponders. An RFID tag is an object that can beor transponders. An RFID tag is an object that can be attached to or incorporated into a product, animal, orattached to or incorporated into a product, animal, or person for the purpose of identification using radioperson for the purpose of identification using radio waves. Chip-based RFID tags contain silicon chips andwaves. Chip-based RFID tags contain silicon chips and antennas. Passive tags require no internal power source,antennas. Passive tags require no internal power source, whereas active tags require a power source.whereas active tags require a power source.
- 3. Types of RFID tagsTypes of RFID tags ’ü« RFID cards are also known as "proximity",RFID cards are also known as "proximity", "proxy" or "contactless cards" and come in three"proxy" or "contactless cards" and come in three general varieties:general varieties: ’ü« passivepassive,, semi-passivesemi-passive (also known as(also known as semi-activesemi-active), or), or activeactive
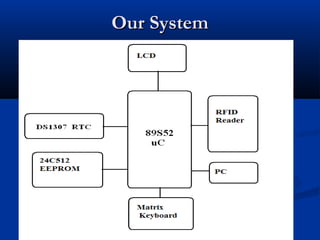
- 4. Our RFID readerOur RFID reader ’ü« RFID Reader Module, are also called as interrogators. They convert radio waves returned from the RFID tag into a form that can be passed on to Controllers, which can make use of it. ’ü« RFID tags and readers have to be tuned to the same frequency in order to communicate. RFID systems use many different frequencies, but the most common and widely used & supported by our Reader is 125 KHz.
- 5. ApplicationsApplications ’ü« Some other areas where passive RFID has been applied in recent past are:Some other areas where passive RFID has been applied in recent past are: ’ü« Person IdentificationPerson Identification ’ü« Food Production ControlFood Production Control ’ü« Vehicle Parking MonitoringVehicle Parking Monitoring ’ü« Toxic Waste MonitoringToxic Waste Monitoring ’ü« Valuable Objects Insurance IdentificationValuable Objects Insurance Identification ’ü« Asset ManagementAsset Management ’ü« Access ControlAccess Control Short range or proximity applications are typically access control applications.Short range or proximity applications are typically access control applications. Some main areas are:Some main areas are: ’ü« Access controlAccess control ’ü« Mass transit ticketingMass transit ticketing
- 7. AdvantagesAdvantages ’ü« Extremely affordableExtremely affordable ’ü« Simple and compact systemSimple and compact system ’ü« PortablePortable ’ü« DoesnŌĆÖt require any additional softwareDoesnŌĆÖt require any additional software ’ü« No need for a dedicated PCNo need for a dedicated PC
- 8. Future WorksFuture Works ’ü« Uploading the RFID accumulated data directlyUploading the RFID accumulated data directly to the internet using an Ethernet moduleto the internet using an Ethernet module (without a PC).(without a PC).
- 9. ’ü« THANK YOUTHANK YOU
- 10. ’ü« THANK YOUTHANK YOU