RIPE: Runtime Intrusion Prevention Evaluator
- 1. RIPE: Runtime Intrusion Prevention Evaluator John Wilander, Nick Nikiforakis,Yves Younan, Mariam Kamkar, and Wouter Joosen
- 2. RIPE is ... ... a deliberately vulnerable C program ... that attacks itself, ... to allow evaluation of countermeasures. @johnwilander @nicknikiforakis ACSAC¡¯11
- 3. RIPE contributions: 850 working buffer over?ow attack forms Evaluation of 8 countermeasures 7% to 89% of attack forms prohibited @johnwilander @nicknikiforakis ACSAC¡¯11
- 4. RIPE download (MIT license): https://github.com/johnwilander/RIPE @johnwilander @nicknikiforakis ACSAC¡¯11
- 5. A Quick Look at How RIPE Works @johnwilander @nicknikiforakis ACSAC¡¯11
- 6. RIPE backend Backend Performs (C) one attack per execution Can be run stand-alone, command-line @johnwilander @nicknikiforakis ACSAC¡¯11
- 7. RIPE backend Backend ./ripe_attack_generator Performs (C) -t direct -i simplenop -c one attack ret per execution -l stack -f strcpy Can be run stand-alone, command-line @johnwilander @nicknikiforakis ACSAC¡¯11
- 8. RIPE frontend Frontend Drives Backend (Python) (C) Report @johnwilander @nicknikiforakis ACSAC¡¯11
- 9. RIPE frontend Frontend Drives Backend python ripe_tester.py (Python) (C) {direct|indirect|both} number of times to repeat tests Report @johnwilander @nicknikiforakis ACSAC¡¯11
- 10. RIPE frontend Frontend Drives Backend (Python) (C) python ripe_tester.py both 5 Report @johnwilander @nicknikiforakis ACSAC¡¯11
- 11. Which Attack Forms are Possible? @johnwilander @nicknikiforakis ACSAC¡¯11
- 12. NDSS ¡¯03 Testbed Target 20 attack forms Technique ti on o ca L @johnwilander @nicknikiforakis ACSAC¡¯11
- 13. ACSAC ¡¯11 Testbed Target 850 attack forms Att ac kc od e Technique o n ti oc a Fu L nc tio n @johnwilander @nicknikiforakis ACSAC¡¯11
- 14. ACSAC ¡¯11 Testbed ? RET ? Old base ptr Target ? Func ptr Att ? Longjmp buffer ac kc ? Struct with buffer & func ptr od e Technique o n ti oc a Fu L nc tio n @johnwilander @nicknikiforakis ACSAC¡¯11
- 15. ACSAC ¡¯11 Testbed Target Att ac kc od e Technique ? Direct ti o n ? Indirect oc a Fu L nc tio n @johnwilander @nicknikiforakis ACSAC¡¯11
- 16. ACSAC ¡¯11 Testbed Target Att ac kc od e Technique o n ti ?memcpy oc a Fu ?str(n)cpy L nc tio ?s(n)printf n ?str(n)cat ?{s|f}scanf ? loop equiv of memcpy @johnwilander @nicknikiforakis ACSAC¡¯11
- 17. ACSAC ¡¯11 Testbed Target Att ac kc od e Technique o n ti oc a Fu L nc tio ? Stack (local var & param) n ? Heap ? BSS ? Data @johnwilander @nicknikiforakis ACSAC¡¯11
- 18. ACSAC ¡¯11 Testbed ? Shellcode Target ? Shellcode + NOP ? Shellcode + Polym. NOP ? Create ?le Att ac ? Return-into-libc kc od ? ROP e Technique o n ti oc a Fu L nc tio n @johnwilander @nicknikiforakis ACSAC¡¯11
- 19. Examples of Attack Forms @johnwilander @nicknikiforakis ACSAC¡¯11
- 20. Direct Over?ow with Injected Code Vulnerable Other variables Target code buffer pointer Optional Attack code Padded Address N NOP sled, (shell code bytes back to u simple or or NOP sled or l polymorph create ?le) attack code l ./ripe_attack_generator -t direct -i simplenop -c ret -l stack -f strcpy @johnwilander @nicknikiforakis ACSAC¡¯11
- 21. Indirect Over?ow Vulnerable Other variables General buffer pointer Optional Attack code Padded Address N NOP sled, (shell code bytes back to u simple or or NOP sled or l polymorph create ?le) attack code l Target code pointer ./ripe_attack_generator -t indirect -i nonop -c ret -l stack -f strcpy @johnwilander @nicknikiforakis ACSAC¡¯11
- 22. Over?ow Within Struct Struct Vulnerable Other Function buffer variables pointer Optional Attack code Address NOP sled, (shell code back to simple or or NOP sled or polymorph create ?le) attack code ./ripe_attack_generator -t direct -i nonop -c structfuncptrstack -l stack -f strcpy @johnwilander @nicknikiforakis ACSAC¡¯11
- 23. Injected Stackframe Vulnerable Other variables Old buffer basepointer Optional Attack code Fake Address N NOP sled, (shell code stack to fake u simple or or frame stack frame l polymorph create ?le) l ./ripe_attack_generator -t indirect -i polynop -c baseptr -l heap -f fscanf @johnwilander @nicknikiforakis ACSAC¡¯11
- 24. Injected Stackframe Vulnerable Other variables Old buffer basepointer Optional Attack code Fake Address N NOP sled, (shell code stack to fake u simple or or frame stack frame l polymorph create ?le) l ./ripe_attack_generator -t indirect -i polynop -c baseptr -l heap -f fscanf @johnwilander @nicknikiforakis ACSAC¡¯11
- 25. All in all, 850 working attack forms @johnwilander @nicknikiforakis ACSAC¡¯11
- 26. Countermeasures Evaluated ? ProPolice (canary-based, variable reorder) ? CRED (boundary checking, referent object) ? StackShield, Libverify (copy & check) ? Libsafe, LibsafePlus, LibsafePlus+TIED (library wrappers) ? PAE & XD (non-executable memory) @johnwilander @nicknikiforakis ACSAC¡¯11
- 27. ProPolice Old Local Local Guard Base RET variables buffers Ptr sorted @johnwilander @nicknikiforakis ACSAC¡¯11
- 28. CRED Base Extent Referent objects Base Extent Base Extent Base Extent Base Extent ptr @johnwilander @nicknikiforakis ACSAC¡¯11
- 29. CRED Base Extent Base Extent Base Extent Base Extent Base Extent Any pointer dereferencing has to stay within bounds ptr @johnwilander @nicknikiforakis ACSAC¡¯11
- 30. CRED Base Extent Base Extent Base Extent Base Extent Base Extent Out-of-bounds object Obj Value Pointers allowed to be out of bounds during ptr artihmetics @johnwilander @nicknikiforakis ACSAC¡¯11
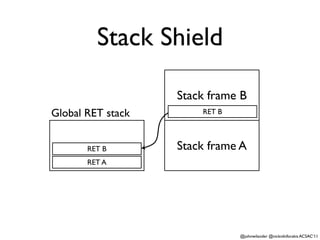
- 31. Stack Shield Global RET stack Stack frame A RET A RET A @johnwilander @nicknikiforakis ACSAC¡¯11
- 32. Stack Shield Stack frame B Global RET stack RET B RET B Stack frame A RET A @johnwilander @nicknikiforakis ACSAC¡¯11
- 33. Stack Shield Stack frame B RET B Global RET stack RET B Stack frame A RET A @johnwilander @nicknikiforakis ACSAC¡¯11
- 34. Stack Shield Stack Heap BSS Data segment Boundary Function pointers Text segment have to point here @johnwilander @nicknikiforakis ACSAC¡¯11
- 35. Libverify Stack Heap BSS Data segment Text segment @johnwilander @nicknikiforakis ACSAC¡¯11
- 36. Libverify Stack Heap BSS Data segment Textfunctions All segment @johnwilander @nicknikiforakis ACSAC¡¯11
- 37. Libverify Stack Heap Copy all BSS functions to the Data segment heap Textfunctions All segment @johnwilander @nicknikiforakis ACSAC¡¯11
- 38. Libverify Stack Instrument all functions to copy RET B their RET to a RET A All functions canary stack and Heap check it before return BSS Data segment Text segment @johnwilander @nicknikiforakis ACSAC¡¯11
- 39. Libsafe Library functions may never overwrite a buffer pass the old base pointer Boundary Old base pointer RET Parameters @johnwilander @nicknikiforakis ACSAC¡¯11
- 40. LibsafePlus & TIED Binary Source Compile code with -g Debug info @johnwilander @nicknikiforakis ACSAC¡¯11
- 41. LibsafePlus & TIED Libsafe- Binary Plus Debug TIED info @johnwilander @nicknikiforakis ACSAC¡¯11
- 42. LibsafePlus & TIED Libsafe- Binary Offset from Plus frame pointer Debug and size for TIED all buffers info @johnwilander @nicknikiforakis ACSAC¡¯11
- 43. LibsafePlus & TIED Instruments all functions to check bounds Libsafe- Binary Offset from Plus frame pointer Debug and size for TIED all buffers info @johnwilander @nicknikiforakis ACSAC¡¯11
- 44. Non-Executable Memory (XD + PAE) Stack W W?X Heap W writable XOR executable BSS W Data segment W Text segment X @johnwilander @nicknikiforakis ACSAC¡¯11
- 45. Empirical Evaluation Results @johnwilander @nicknikiforakis ACSAC¡¯11
- 46. Results Effective Successful Partly Failed attacks successful attacks -ness Ubuntu 6.06 (no protection) 0% 99% 1% 0% Libsafe 7% 91% 2% 7% LibsafePlus 19% 79% 2% 19% StackShield 36% 63% 1% 36% ProPolice 40% 59% 1% 40% LibsafePlus + TIED 77% 20% 3% 77% CRED 79% 20% 0.5% 79% Ubuntu 9.10 (W?X + CRED) 89% 9% 1% 89% @johnwilander @nicknikiforakis ACSAC¡¯11
- 47. Results, top 4 Effective Successful Partly Failed attacks successful attacks -ness ProPolice 40% 59% 1% 40% LibsafePlus + TIED 77% 20% 3% 77% CRED 79% 20% 0.5% 79% Ubuntu 9.10 (W?X + CRED) 89% 9% 1% 89% @johnwilander @nicknikiforakis ACSAC¡¯11
- 48. Results, top 4 Effective Successful Partly Failed attacks successful attacks -ness ProPolice 40% 59% 1% 40% LibsafePlus + TIED 77% 20% 3% 77% Totally focused on protecting the stack. CRED Indirect, heap/BSS/data-based79% attacks 20% 0.5% 79% against longjmp Ubuntu 9.10stack variables or function 9% buffers as (W?X + CRED) 89% parameters not 1% 89% fully stable and thus categorized as partly successful. @johnwilander @nicknikiforakis ACSAC¡¯11
- 49. Results, top 4 Effective Successful Partly Failed attacks successful attacks -ness ProPolice 40% 59% 1% 40% LibsafePlus + TIED 77% 20% 3% 77% CREDDoen¡¯t wrap memcpy or loop equivalent of 0.5% 79% 79% 20% memcpy. Ubuntu 9.10 (W?X + attacks abusing wrapped1% Spurious successful CRED) 89% 9% functions 89% explains the fairly high ¡±Partly successful¡± ?gure. @johnwilander @nicknikiforakis ACSAC¡¯11
- 50. Results, top 4 Fails to protect against direct and indirect, stack/BSS/ data-based over?ows toward function pointers, longjmp buffers, and structs for sprintf(), snprintf(), Effective Successful Partly Failed sscanf(), and fscanf(). attacks successful attacks -ness Attacks against structs also successful for memcpy() ProPolice equivalent and are the only 59% 1% and loop 40% attacks successful 40% LibsafePlus + TIED the heap. 77% from buffers on 20% 3% 77% CRED 79% 20% 0.5% 79% Ubuntu 9.10 (W?X + CRED) 89% 9% 1% 89% @johnwilander @nicknikiforakis ACSAC¡¯11
- 51. Results, top 4 All code injection countermeasured. Apart from that: All struct attack forms were successful. All direct attacks against function pointers on the heap Effective Successful Partly Failed and the data segment were successful. -ness attacks successful attacks Indirect attacks against the old base pointer work in ProPolice on the heap, BSS, and data segment for general 40% 59% 1% 40% LibsafePlus + TIED strncpy(), sprintf(), snprintf(), 77% memcpy(), strcpy(), 77% 20% 3% strcat(), strncat(), sscanf(), fscanf(), and loop 0.5% 79% CRED 79% 20% equivalent. Ubuntu 9.10 (W?X + CRED) 89% 9% 1% 89% @johnwilander @nicknikiforakis ACSAC¡¯11
- 52. Related Work @johnwilander @nicknikiforakis ACSAC¡¯11
- 53. Dynamic Over?ow Detecion by Zhivich, Leek, and Lippmann @johnwilander @nicknikiforakis ACSAC¡¯11
- 54. Two Testbeds 1. ¡±Variable-over?ow¡± various small over?ows synthesized not attacks 2. ¡±Real exploits¡± modeled from real world detection performace @johnwilander @nicknikiforakis ACSAC¡¯11
- 55. Seven Countermeasures Evaluated 1. Chaperon commercial, works with binaries, monitors execution 2. Valgrind free sw, simulated execution, up to 500% performance hit 3. CCured free sw, static analysis of pointers, may require annotations SAFE = no arithmentic, no cast SEQ = arithmetic WILD = arithmetic and cast @johnwilander @nicknikiforakis ACSAC¡¯11
- 56. Seven Countermeasures Evaluated 4. CRED free sw, bounds checking with referent object 5. Insure++ commercial, instruments source code, up to 2500% performace hit 6. ProPolice free sw, canary-based, reorders stack variables 7. TinyCC free sw, basic referent object bounds checking @johnwilander @nicknikiforakis ACSAC¡¯11
- 57. Results (Zhivich, Leek, and Lippmann) @johnwilander @nicknikiforakis ACSAC¡¯11
- 58. Results (Zhivich, Leek, and Lippmann) @johnwilander @nicknikiforakis ACSAC¡¯11
- 59. Future Work ? Save/load offsets to allow testing of ASLR, probabilistic memory safety ? Other attack forms; Memory mgmt data (free & double free) Heap spraying Non-control data attacks ? Con?gurable memory layout model @johnwilander @nicknikiforakis ACSAC¡¯11
- 60. ºİºİߣs http://www.slideshare.net/johnwilander/ ripe-runtime-intrusion-prevention-evaluator @johnwilander john.wilander@gmail.com
Editor's Notes
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n
- \n