Riptech Verio Presentation
- 1. The Managed Security Imperative 2099 Gateway Place San Jose, CA 95110 877-INFOSEC www.riptech.com [email_address] October 16, 2001 Copyright 2001 Riptech, Inc. Real-Time Information Protection SM
- 2. Riptech: The Managed Security Leader Founded in 1998 by former Department of Defense and other leading security professionals Received more than $40 million in venture capital investment Other accomplishments include: Channel partnerships with Cisco, Verio, Yipes, Epoch Internet, Equinix, Enspherics Hundreds of clients in over 30 Countries including several of the worldŌĆÖs largest banks, pharmaceuticals, utilities, and government agencies.
- 3. The Information Security Problem: (You May Already Know This) 85% of survey respondents detect computer security breaches within the last twelve months 70% cited Internet Connections as a frequent point of attack - up from 59% from previous year 91% detected employee abuse 40% detected system penetration from the outside Average incidents cost companies more than $2 million *2001 Computer Crime and Security Survey ** 538 Computer Security Practitioners
- 4. ╠²
- 5. Hardware and Software Solutions Are Not Enough: A False Sense Of Security Of the organizations suffering security compromises in the last year ŌĆō 95% had Firewalls and 61% had IDSs ! Need for Real-Time Security Monitoring! 90 92 93 Access Control 98 100 98 Anti-virus software SECURITY TECHNOLOGIES USED ( %) 64 62 61 Encrypted Files 95 78 91 Firewalls 61 50 42 Intrusion Detection Systems 2001 2000 1999
- 6. The Challenge: Security Products Generate Vast Amounts Of Complex And Difficult To Manage Data A single firewall on a busy network may generate 1000 MB of log data per hour, 23.4 GB per day and 164 GB per week. A single IDS on a busy network may generate 1,500 alerts per hour, 36,000 alerts per day and 252,000 alerts per week. What if you have 2? 20? 200??? What if your security devices are from different vendors?
- 7. Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 30.187.10.130 44654 dest 10.0.0.1 5631 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 93.132.178.83 25779 dest 10.0.0.1 32771 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 88.156.231.45 25645 dest 10.0.0.1 21 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 172.203.138.42 6368 dest 10.0.0.1 27665 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 112.8.46.29 38347 dest 10.0.0.1 80 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 17 Connection denied by outbound list 1 src 248.61.8.19 49358 dest 10.0.0.1 45224 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 70.139.144.19 21 dest 10.0.0.1 47681 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106018: ICMP packet type 3 denied by outbound list 1 src 0.0.0.0 dest 10.0.0.1 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 211.73.233.3 50103 dest 10.0.0.1 80 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 208.160.119.20 49038 dest 10.0.0.1 80 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 109.92.79.135 110 dest 10.0.0.1 62919 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 17 Connection denied by outbound list 1 src 95.14.76.85 2140 dest 10.0.0.1 60000 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106018: ICMP packet type 11 denied by outbound list 1 src 0.0.0.0 dest 10.0.0.1
- 8. Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 30.187.10.130 44654 dest 10.0.0.1 5631 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 93.132.178.83 25779 dest 10.0.0.1 32771 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 88.156.231.45 25645 dest 10.0.0.1 21 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 172.203.138.42 6368 dest 10.0.0.1 27665 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 112.8.46.29 38347 dest 10.0.0.1 80 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 17 Connection denied by outbound list 1 src 248.61.8.19 49358 dest 10.0.0.1 45224 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 70.139.144.19 21 dest 10.0.0.1 47681 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106018: ICMP packet type 3 denied by outbound list 1 src 0.0.0.0 dest 10.0.0.1 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 211.73.233.3 50103 dest 10.0.0.1 80 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 208.160.119.20 49038 dest 10.0.0.1 80 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 109.92.79.135 110 dest 10.0.0.1 62919 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 17 Connection denied by outbound list 1 src 95.14.76.85 2140 dest 10.0.0.1 60000 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106018: ICMP packet type 11 denied by outbound list 1 src 0.0.0.0 dest 10.0.0.1
- 9. num;date;time;orig;type;action;alert;i/f_name;i/f_dir;proto;src;dst;service;s_port;len;rule;xlatesrc;xlatedst;xlatesport;xlatedport;icmp-type;icmp-code;reason:;sys_msgs 0;26Mar2001;17:50:58;fw_dev1;control;ctl;;daemon;inbound;;;;;;;;;;;;;;;started sending log to localhost 1;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Chris1;soc1_DB1 (Valid Address);ms_sql_445;3120;48;14;D-Chris1;soc1_DB1;3120;ms_sql_445;;;; 2;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Chris1;soc1_DB1 (Valid Address);nbsession;3121;48;14;D-Chris1;soc1_DB1;3121;nbsession;;;; 3;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_backend_DB (Valid Address);ms_sql_445;2106;48;14;D-Daniel1;soc1_backend_DB;2106;ms_sql_445;;;; 4;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_backend_DB (Valid Address);nbsession;2108;48;14;D-Daniel1;soc1_backend_DB;2108;nbsession;;;; 5;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Chris1;soc1_AuxDB (Valid Address);ms_sql_445;3122;48;14;D-Chris1;soc1_AuxDB;3122;ms_sql_445;;;; 6;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Chris1;soc1_AuxDB (Valid Address);nbsession;3123;48;14;D-Chris1;soc1_AuxDB;3123;nbsession;;;; 7;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_AuxDB (Valid Address);ms_sql_445;2109;48;14;D-Daniel1;soc1_AuxDB;2109;ms_sql_445;;;; 8;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_AuxDB (Valid Address);nbsession;2110;48;14;D-Daniel1;soc1_AuxDB;2110;nbsession;;;; 9;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_DB1 (Valid Address);ms_sql_445;2111;48;14;D-Daniel1;soc1_DB1;2111;ms_sql_445;;;; 10;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_DB1 (Valid Address);nbsession;2112;48;14;D-Daniel1;soc1_DB1;2112;nbsession;;;; 11;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_backend_DB (Valid Address);ms_sql_445;2113;48;14;D-Daniel1;soc1_backend_DB;2113;ms_sql_445;;;; 12;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_backend_DB (Valid Address);nbsession;2114;48;14;D-Daniel1;soc1_backend_DB;2114;nbsession;;;; 13;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_AuxDB (Valid Address);ms_sql_445;2115;48;14;D-Daniel1;soc1_AuxDB;2115;ms_sql_445;;;; 14;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_AuxDB (Valid Address);nbsession;2116;48;14;D-Daniel1;soc1_AuxDB;2116;nbsession;;;; 15;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_AuxDB (Valid Address);ms_sql_445;2582;48;14;workstation2;soc1_AuxDB;2582;ms_sql_445;;;; 16;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_AuxDB (Valid Address);nbsession;2583;48;14;workstation2;soc1_AuxDB;2583;nbsession;;;; 17;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_backend_DB (Valid Address);ms_sql_445;2117;48;14;D-Daniel1;soc1_backend_DB;2117;ms_sql_445;;;; 18;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_backend_DB (Valid Address);nbsession;2118;48;14;D-Daniel1;soc1_backend_DB;2118;nbsession;;;; 19;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_backend_DB (Valid Address);ms_sql_445;2584;48;14;workstation2;soc1_backend_DB;2584;ms_sql_445;;;; 20;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_backend_DB (Valid Address);nbsession;2585;48;14;workstation2;soc1_backend_DB;2585;nbsession;;;; 21;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_DB2 (Valid Address);ms_sql_445;2586;48;14;workstation2;soc1_DB2;2586;ms_sql_445;;;; 22;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_DB2 (Valid Address);nbsession;2587;48;14;workstation2;soc1_DB2;2587;nbsession;;;; 23;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_DB1 (Valid Address);ms_sql_445;2588;48;14;workstation2;soc1_DB1;2588;ms_sql_445;;;; 24;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_DB1 (Valid Address);nbsession;2589;48;14;workstation2;soc1_DB1;2589;nbsession;;;;
- 10. num;date;time;orig;type;action;alert;i/f_name;i/f_dir;proto;src;dst;service;s_port;len;rule;xlatesrc;xlatedst;xlatesport;xlatedport;icmp-type;icmp-code;reason:;sys_msgs 0;26Mar2001;17:50:58;fw_dev1;control;ctl;;daemon;inbound;;;;;;;;;;;;;;;started sending log to localhost 1;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Chris1;soc1_DB1 (Valid Address);ms_sql_445;3120;48;14;D-Chris1;soc1_DB1;3120;ms_sql_445;;;; 2;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Chris1;soc1_DB1 (Valid Address);nbsession;3121;48;14;D-Chris1;soc1_DB1;3121;nbsession;;;; 3;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_backend_DB (Valid Address);ms_sql_445;2106;48;14;D-Daniel1;soc1_backend_DB;2106;ms_sql_445;;;; 4;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_backend_DB (Valid Address);nbsession;2108;48;14;D-Daniel1;soc1_backend_DB;2108;nbsession;;;; 5;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Chris1;soc1_AuxDB (Valid Address);ms_sql_445;3122;48;14;D-Chris1;soc1_AuxDB;3122;ms_sql_445;;;; 6;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Chris1;soc1_AuxDB (Valid Address);nbsession;3123;48;14;D-Chris1;soc1_AuxDB;3123;nbsession;;;; 7;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_AuxDB (Valid Address);ms_sql_445;2109;48;14;D-Daniel1;soc1_AuxDB;2109;ms_sql_445;;;; 8;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_AuxDB (Valid Address);nbsession;2110;48;14;D-Daniel1;soc1_AuxDB;2110;nbsession;;;; 9;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_DB1 (Valid Address);ms_sql_445;2111;48;14;D-Daniel1;soc1_DB1;2111;ms_sql_445;;;; 10;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_DB1 (Valid Address);nbsession;2112;48;14;D-Daniel1;soc1_DB1;2112;nbsession;;;; 11;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_backend_DB (Valid Address);ms_sql_445;2113;48;14;D-Daniel1;soc1_backend_DB;2113;ms_sql_445;;;; 12;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_backend_DB (Valid Address);nbsession;2114;48;14;D-Daniel1;soc1_backend_DB;2114;nbsession;;;; 13;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_AuxDB (Valid Address);ms_sql_445;2115;48;14;D-Daniel1;soc1_AuxDB;2115;ms_sql_445;;;; 14;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_AuxDB (Valid Address);nbsession;2116;48;14;D-Daniel1;soc1_AuxDB;2116;nbsession;;;; 15;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_AuxDB (Valid Address);ms_sql_445;2582;48;14;workstation2;soc1_AuxDB;2582;ms_sql_445;;;; 16;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_AuxDB (Valid Address);nbsession;2583;48;14;workstation2;soc1_AuxDB;2583;nbsession;;;; 17;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_backend_DB (Valid Address);ms_sql_445;2117;48;14;D-Daniel1;soc1_backend_DB;2117;ms_sql_445;;;; 18;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_backend_DB (Valid Address);nbsession;2118;48;14;D-Daniel1;soc1_backend_DB;2118;nbsession;;;; 19;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_backend_DB (Valid Address);ms_sql_445;2584;48;14;workstation2;soc1_backend_DB;2584;ms_sql_445;;;; 20;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_backend_DB (Valid Address);nbsession;2585;48;14;workstation2;soc1_backend_DB;2585;nbsession;;;; 21;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_DB2 (Valid Address);ms_sql_445;2586;48;14;workstation2;soc1_DB2;2586;ms_sql_445;;;; 22;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_DB2 (Valid Address);nbsession;2587;48;14;workstation2;soc1_DB2;2587;nbsession;;;; 23;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_DB1 (Valid Address);ms_sql_445;2588;48;14;workstation2;soc1_DB1;2588;ms_sql_445;;;; 24;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_DB1 (Valid Address);nbsession;2589;48;14;workstation2;soc1_DB1;2589;nbsession;;;;
- 11. 26 13:59:50 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 13:03:31" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=45529 dst_port=633 service=TCP port 633 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:01:10 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 13:04:47" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=45532 dst_port=964 service=TCP port 964 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:02:30 192.168.60.65 QA-Netscreen-10: netscreen: User netscreen telnet management session from (192.168.60.232:4383) timed out (2001-3-26 13:12:15) Mar 26 14:43:03 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=792 service=TCP port 792 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:44:23 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=1527 service=TCP port 1527 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:45:43 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=418 service=TCP port 418 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:47:03 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=983 service=TCP port 983 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:48:23 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=28 service=TCP port 28 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:49:43 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=761 service=TCP port 761 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:51:03 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=2033 service=TCP port 2033 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:52:23 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=1475 service=TCP port 1475 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:53:43 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=1530 service=TCP port 1530 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny
- 12. 26 13:59:50 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 13:03:31" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=45529 dst_port=633 service=TCP port 633 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:01:10 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 13:04:47" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=45532 dst_port=964 service=TCP port 964 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:02:30 192.168.60.65 QA-Netscreen-10: netscreen: User netscreen telnet management session from (192.168.60.232:4383) timed out (2001-3-26 13:12:15) Mar 26 14:43:03 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=792 service=TCP port 792 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:44:23 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=1527 service=TCP port 1527 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:45:43 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=418 service=TCP port 418 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:47:03 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=983 service=TCP port 983 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:48:23 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=28 service=TCP port 28 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:49:43 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=761 service=TCP port 761 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:51:03 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=2033 service=TCP port 2033 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:52:23 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=1475 service=TCP port 1475 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:53:43 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=1530 service=TCP port 1530 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny
- 13. 2001-03-13 10:29:43|drag-sensor1|DRAGONRIDER-START|0.0.0.0|0.0.0.0|0|0|?||0|dv=,tz=GMT| 2001-03-13 10:30:32|drag-sensor1|DRAGONRIDER-START|0|0|0|0|?||0|dv=,tz=GMT| 2001-03-13 11:02:05|drag-sensor1|HEARTBEAT|0|0|0|0|I||0|IP=1380,ICMP=0,TCP=1237,UDP=143,EVENTS=1,DROP=0,VER=4.2.2| 2001-03-13 12:02:44|drag-sensor1|HEARTBEAT|0|0|0|0|I||0|IP=201,ICMP=0,TCP=3,UDP=198,EVENTS=1,DROP=0,VER=4.2.2| 2001-03-13 12:23:23|drag-sensor1|TCP-SCAN|727912620|1684213932|0|0|I|------S-|0|total=490,min=2,max=1024,up=241,down=249,flags=------S-,Mar13-12:22,Mar13-12:23| 2001-03-13 12:23:23|drag-sensor1|TCP-SCAN|727912620|1684213932|55564|0|I|------S-|0|total=500,min=1,max=1022,up=242,down=258,sp=55564,flags=------S-,Mar13-12:23,Mar13-12:23| 2001-03-13 12:24:31|drag-sensor1|TCP-SCAN|727912620|1684213932|55564|0|I|------S-|0|total=34,min=42,max=942,up=16,down=18,sp=55564,flags=------S-,Mar13-12:23,Mar13-12:23| 2001-03-13 12:24:31|drag-sensor1|TCP-SCAN|727912620|23269548|0|0|I|------S-|0|total=462,min=1,max=1022,up=235,down=227,flags=------S-,Mar13-12:23,Mar13-12:24| 2001-03-13 12:25:35|drag-sensor1|TCP-SCAN|727912620|23269548|55902|0|I|------S-|0|total=497,min=1,max=1023,up=235,down=262,sp=55902,flags=------S-,Mar13-12:24,Mar13-12:25| 2001-03-13 12:28:16|drag-sensor1|TCP-SCAN|727912620|23269548|34861|0|I|------S-|0|total=235,min=12,max=1023,up=116,down=119,sp=34861,flags=------S-,Mar13-12:25,Mar13-12:26| 2001-03-13 12:28:16|drag-sensor1|TCP-SCAN|727912620|1164120236|0|0|I|------S-|0|total=255,min=8,max=1022,up=129,down=126,flags=------S-,Mar13-12:27,Mar13-12:28| 2001-03-13 12:28:17|drag-sensor1|TCP-SCAN|727912620|1164120236|49693|0|I|------S-|0|total=500,min=1,max=1023,up=241,down=259,sp=49693,flags=------S-,Mar13-12:28,Mar13-12:28| 2001-03-13 12:50:47|drag-sensor1|FTP:NOPASSWORD|23269548|1180897452|1558|21|I||6|tcp,dp=21,sp=1558| 2001-03-13 12:50:47|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1558|I|---A----|6|tcp,sp=21,dp=1558,flags=---A----| 2001-03-13 12:50:47|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1558|I|---AP---|6|tcp,sp=21,dp=1558,flags=---AP---| 2001-03-13 12:50:47|drag-sensor1|DYNAMIC-TCP|23269548|1180897452|1558|21|I|---A----|6|tcp,sp=1558,dp=21,flags=---A----| 2001-03-13 12:50:52|drag-sensor1|DYNAMIC-TCP|23269548|1180897452|1558|21|I|---AP---|6|tcp,sp=1558,dp=21,flags=---AP---| 2001-03-13 12:50:52|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1558|I|---AP---|6|tcp,sp=21,dp=1558,flags=---AP---| 2001-03-13 12:50:52|drag-sensor1|DYNAMIC-TCP|23269548|1180897452|1558|21|I|---A---F|6|tcp,sp=1558,dp=21,flags=---A---F| 2001-03-13 12:50:52|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1558|I|---A----|6|tcp,sp=21,dp=1558,flags=---A----| 2001-03-13 12:50:52|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1558|I|---A---F|6|tcp,sp=21,dp=1558,flags=---A---F| 2001-03-13 12:50:52|drag-sensor1|DYNAMIC-TCP|23269548|1180897452|1558|21|I|---A----|6|tcp,sp=1558,dp=21,flags=---A----| 2001-03-13 12:50:53|drag-sensor1|DYNAMIC-TCP|23269548|1180897452|1559|21|I|------S-|6|tcp,sp=1559,dp=21,flags=------S-| 2001-03-13 12:50:53|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1559|I|---A--S-|6|tcp,sp=21,dp=1559,flags=---A--S-| 2001-03-13 12:50:53|drag-sensor1|DYNAMIC-TCP|23269548|1180897452|1559|21|I|---A----|6|tcp,sp=1559,dp=21,flags=---A----| 2001-03-13 12:50:56|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1559|I|---AP---|6|tcp,sp=21,dp=1559,flags=---AP---|
- 14. 2001-03-13 10:29:43|drag-sensor1|DRAGONRIDER-START|0.0.0.0|0.0.0.0|0|0|?||0|dv=,tz=GMT| 2001-03-13 10:30:32|drag-sensor1|DRAGONRIDER-START|0|0|0|0|?||0|dv=,tz=GMT| 2001-03-13 11:02:05|drag-sensor1|HEARTBEAT|0|0|0|0|I||0|IP=1380,ICMP=0,TCP=1237,UDP=143,EVENTS=1,DROP=0,VER=4.2.2| 2001-03-13 12:02:44|drag-sensor1|HEARTBEAT|0|0|0|0|I||0|IP=201,ICMP=0,TCP=3,UDP=198,EVENTS=1,DROP=0,VER=4.2.2| 2001-03-13 12:23:23|drag-sensor1|TCP-SCAN|727912620|1684213932|0|0|I|------S-|0|total=490,min=2,max=1024,up=241,down=249,flags=------S-,Mar13-12:22,Mar13-12:23| 2001-03-13 12:23:23|drag-sensor1|TCP-SCAN|727912620|1684213932|55564|0|I|------S-|0|total=500,min=1,max=1022,up=242,down=258,sp=55564,flags=------S-,Mar13-12:23,Mar13-12:23| 2001-03-13 12:24:31|drag-sensor1|TCP-SCAN|727912620|1684213932|55564|0|I|------S-|0|total=34,min=42,max=942,up=16,down=18,sp=55564,flags=------S-,Mar13-12:23,Mar13-12:23| 2001-03-13 12:24:31|drag-sensor1|TCP-SCAN|727912620|23269548|0|0|I|------S-|0|total=462,min=1,max=1022,up=235,down=227,flags=------S-,Mar13-12:23,Mar13-12:24| 2001-03-13 12:25:35|drag-sensor1|TCP-SCAN|727912620|23269548|55902|0|I|------S-|0|total=497,min=1,max=1023,up=235,down=262,sp=55902,flags=------S-,Mar13-12:24,Mar13-12:25| 2001-03-13 12:28:16|drag-sensor1|TCP-SCAN|727912620|23269548|34861|0|I|------S-|0|total=235,min=12,max=1023,up=116,down=119,sp=34861,flags=------S-,Mar13-12:25,Mar13-12:26| 2001-03-13 12:28:16|drag-sensor1|TCP-SCAN|727912620|1164120236|0|0|I|------S-|0|total=255,min=8,max=1022,up=129,down=126,flags=------S-,Mar13-12:27,Mar13-12:28| 2001-03-13 12:28:17|drag-sensor1|TCP-SCAN|727912620|1164120236|49693|0|I|------S-|0|total=500,min=1,max=1023,up=241,down=259,sp=49693,flags=------S-,Mar13-12:28,Mar13-12:28| 2001-03-13 12:50:47|drag-sensor1|FTP:NOPASSWORD|23269548|1180897452|1558|21|I||6|tcp,dp=21,sp=1558| 2001-03-13 12:50:47|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1558|I|---A----|6|tcp,sp=21,dp=1558,flags=---A----| 2001-03-13 12:50:47|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1558|I|---AP---|6|tcp,sp=21,dp=1558,flags=---AP---| 2001-03-13 12:50:47|drag-sensor1|DYNAMIC-TCP|23269548|1180897452|1558|21|I|---A----|6|tcp,sp=1558,dp=21,flags=---A----| 2001-03-13 12:50:52|drag-sensor1|DYNAMIC-TCP|23269548|1180897452|1558|21|I|---AP---|6|tcp,sp=1558,dp=21,flags=---AP---| 2001-03-13 12:50:52|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1558|I|---AP---|6|tcp,sp=21,dp=1558,flags=---AP---| 2001-03-13 12:50:52|drag-sensor1|DYNAMIC-TCP|23269548|1180897452|1558|21|I|---A---F|6|tcp,sp=1558,dp=21,flags=---A---F| 2001-03-13 12:50:52|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1558|I|---A----|6|tcp,sp=21,dp=1558,flags=---A----| 2001-03-13 12:50:52|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1558|I|---A---F|6|tcp,sp=21,dp=1558,flags=---A---F| 2001-03-13 12:50:52|drag-sensor1|DYNAMIC-TCP|23269548|1180897452|1558|21|I|---A----|6|tcp,sp=1558,dp=21,flags=---A----| 2001-03-13 12:50:53|drag-sensor1|DYNAMIC-TCP|23269548|1180897452|1559|21|I|------S-|6|tcp,sp=1559,dp=21,flags=------S-| 2001-03-13 12:50:53|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1559|I|---A--S-|6|tcp,sp=21,dp=1559,flags=---A--S-| 2001-03-13 12:50:53|drag-sensor1|DYNAMIC-TCP|23269548|1180897452|1559|21|I|---A----|6|tcp,sp=1559,dp=21,flags=---A----| 2001-03-13 12:50:56|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1559|I|---AP---|6|tcp,sp=21,dp=1559,flags=---AP---|
- 15. num;date;time;orig;type;action;alert;i/f_name;i/f_dir;proto;src;dst;service;s_port;len;rule;xlatesrc;xlatedst;xlatesport;xlatedport;icmp-type;icmp-code;reason:;sys_msgs 0;26Mar2001;17:50:58;fw_dev1;control;ctl;;daemon;inbound;;;;;;;;;;;;;;;started sending log to localhost 1;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Chris1;soc1_DB1 (Valid Address);ms_sql_445;3120;48;14;D-Chris1;soc1_DB1;3120;ms_sql_445;;;; 2;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Chris1;soc1_DB1 (Valid Address);nbsession;3121;48;14;D-Chris1;soc1_DB1;3121;nbsession;;;; 3;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_backend_DB (Valid Address);ms_sql_445;2106;48;14;D-Daniel1;soc1_backend_DB;2106;ms_sql_445;;;; 4;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_backend_DB (Valid Address);nbsession;2108;48;14;D-Daniel1;soc1_backend_DB;2108;nbsession;;;; 5;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Chris1;soc1_AuxDB (Valid Address);ms_sql_445;3122;48;14;D-Chris1;soc1_AuxDB;3122;ms_sql_445;;;; 6;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Chris1;soc1_AuxDB (Valid Address);nbsession;3123;48;14;D-Chris1;soc1_AuxDB;3123;nbsession;;;; 7;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_AuxDB (Valid Address);ms_sql_445;2109;48;14;D-Daniel1;soc1_AuxDB;2109;ms_sql_445;;;; 8;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_AuxDB (Valid Address);nbsession;2110;48;14;D-Daniel1;soc1_AuxDB;2110;nbsession;;;; 9;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_DB1 (Valid Address);ms_sql_445;2111;48;14;D-Daniel1;soc1_DB1;2111;ms_sql_445;;;; 10;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_DB1 (Valid Address);nbsession;2112;48;14;D-Daniel1;soc1_DB1;2112;nbsession;;;; 11;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_backend_DB (Valid Address);ms_sql_445;2113;48;14;D-Daniel1;soc1_backend_DB;2113;ms_sql_445;;;; 12;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_backend_DB (Valid Address);nbsession;2114;48;14;D-Daniel1;soc1_backend_DB;2114;nbsession;;;; 13;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_AuxDB (Valid Address);ms_sql_445;2115;48;14;D-Daniel1;soc1_AuxDB;2115;ms_sql_445;;;; 14;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_AuxDB (Valid Address);nbsession;2116;48;14;D-Daniel1;soc1_AuxDB;2116;nbsession;;;; 15;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_AuxDB (Valid Address);ms_sql_445;2582;48;14;workstation2;soc1_AuxDB;2582;ms_sql_445;;;; 16;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_AuxDB (Valid Address);nbsession;2583;48;14;workstation2;soc1_AuxDB;2583;nbsession;;;; 17;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_backend_DB (Valid Address);ms_sql_445;2117;48;14;D-Daniel1;soc1_backend_DB;2117;ms_sql_445;;;; 18;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;D-Daniel1;soc1_backend_DB (Valid Address);nbsession;2118;48;14;D-Daniel1;soc1_backend_DB;2118;nbsession;;;; 19;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_backend_DB (Valid Address);ms_sql_445;2584;48;14;workstation2;soc1_backend_DB;2584;ms_sql_445;;;; 20;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_backend_DB (Valid Address);nbsession;2585;48;14;workstation2;soc1_backend_DB;2585;nbsession;;;; 21;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_DB2 (Valid Address);ms_sql_445;2586;48;14;workstation2;soc1_DB2;2586;ms_sql_445;;;; 22;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_DB2 (Valid Address);nbsession;2587;48;14;workstation2;soc1_DB2;2587;nbsession;;;; 23;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_DB1 (Valid Address);ms_sql_445;2588;48;14;workstation2;soc1_DB1;2588;ms_sql_445;;;; 24;26Mar2001;17:50:58;fw_dev1;log;accept;;DC21X41;inbound;tcp;workstation2;soc1_DB1 (Valid Address);nbsession;2589;48;14;workstation2;soc1_DB1;2589;nbsession;;;; 26 13:59:50 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 13:03:31" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=45529 dst_port=633 service=TCP port 633 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:01:10 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 13:04:47" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=45532 dst_port=964 service=TCP port 964 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:02:30 192.168.60.65 QA-Netscreen-10: netscreen: User netscreen telnet management session from (192.168.60.232:4383) timed out (2001-3-26 13:12:15) Mar 26 14:43:03 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=792 service=TCP port 792 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:44:23 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=1527 service=TCP port 1527 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:45:43 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=418 service=TCP port 418 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:47:03 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=983 service=TCP port 983 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:48:23 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=28 service=TCP port 28 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:49:43 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=761 service=TCP port 761 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:51:03 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=2033 service=TCP port 2033 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:52:23 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=1475 service=TCP port 1475 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny Mar 26 14:53:43 192.168.60.65 QA-Netscreen-10: NetScreen Traffic Log: device_id=QA-Netscreen-10 start_time="2001-3-26 14:41:22" src=/slideshow/riptech-verio-presentation/2772334/192.168.60.208 dst=192.168.60.65 src_port=39629 dst_port=1530 service=TCP port 1530 policy_id=32767 duration=0 sent=0 rcvd=40 action=Deny 2001-03-13 10:29:43|drag-sensor1|DRAGONRIDER-START|0.0.0.0|0.0.0.0|0|0|?||0|dv=,tz=GMT| 2001-03-13 10:30:32|drag-sensor1|DRAGONRIDER-START|0|0|0|0|?||0|dv=,tz=GMT| 2001-03-13 11:02:05|drag-sensor1|HEARTBEAT|0|0|0|0|I||0|IP=1380,ICMP=0,TCP=1237,UDP=143,EVENTS=1,DROP=0,VER=4.2.2| 2001-03-13 12:02:44|drag-sensor1|HEARTBEAT|0|0|0|0|I||0|IP=201,ICMP=0,TCP=3,UDP=198,EVENTS=1,DROP=0,VER=4.2.2| 2001-03-13 12:23:23|drag-sensor1|TCP-SCAN|727912620|1684213932|0|0|I|------S-|0|total=490,min=2,max=1024,up=241,down=249,flags=------S-,Mar13-12:22,Mar13-12:23| 2001-03-13 12:23:23|drag-sensor1|TCP-SCAN|727912620|1684213932|55564|0|I|------S-|0|total=500,min=1,max=1022,up=242,down=258,sp=55564,flags=------S-,Mar13-12:23,Mar13-12:23| 2001-03-13 12:24:31|drag-sensor1|TCP-SCAN|727912620|1684213932|55564|0|I|------S-|0|total=34,min=42,max=942,up=16,down=18,sp=55564,flags=------S-,Mar13-12:23,Mar13-12:23| 2001-03-13 12:24:31|drag-sensor1|TCP-SCAN|727912620|23269548|0|0|I|------S-|0|total=462,min=1,max=1022,up=235,down=227,flags=------S-,Mar13-12:23,Mar13-12:24| 2001-03-13 12:25:35|drag-sensor1|TCP-SCAN|727912620|23269548|55902|0|I|------S-|0|total=497,min=1,max=1023,up=235,down=262,sp=55902,flags=------S-,Mar13-12:24,Mar13-12:25| 2001-03-13 12:28:16|drag-sensor1|TCP-SCAN|727912620|23269548|34861|0|I|------S-|0|total=235,min=12,max=1023,up=116,down=119,sp=34861,flags=------S-,Mar13-12:25,Mar13-12:26| 2001-03-13 12:28:16|drag-sensor1|TCP-SCAN|727912620|1164120236|0|0|I|------S-|0|total=255,min=8,max=1022,up=129,down=126,flags=------S-,Mar13-12:27,Mar13-12:28| 2001-03-13 12:28:17|drag-sensor1|TCP-SCAN|727912620|1164120236|49693|0|I|------S-|0|total=500,min=1,max=1023,up=241,down=259,sp=49693,flags=------S-,Mar13-12:28,Mar13-12:28| 2001-03-13 12:50:47|drag-sensor1|FTP:NOPASSWORD|23269548|1180897452|1558|21|I||6|tcp,dp=21,sp=1558| 2001-03-13 12:50:47|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1558|I|---A----|6|tcp,sp=21,dp=1558,flags=---A----| 2001-03-13 12:50:47|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1558|I|---AP---|6|tcp,sp=21,dp=1558,flags=---AP---| 2001-03-13 12:50:47|drag-sensor1|DYNAMIC-TCP|23269548|1180897452|1558|21|I|---A----|6|tcp,sp=1558,dp=21,flags=---A----| 2001-03-13 12:50:52|drag-sensor1|DYNAMIC-TCP|23269548|1180897452|1558|21|I|---AP---|6|tcp,sp=1558,dp=21,flags=---AP---| 2001-03-13 12:50:52|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1558|I|---AP---|6|tcp,sp=21,dp=1558,flags=---AP---| 2001-03-13 12:50:52|drag-sensor1|DYNAMIC-TCP|23269548|1180897452|1558|21|I|---A---F|6|tcp,sp=1558,dp=21,flags=---A---F| 2001-03-13 12:50:52|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1558|I|---A----|6|tcp,sp=21,dp=1558,flags=---A----| 2001-03-13 12:50:52|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1558|I|---A---F|6|tcp,sp=21,dp=1558,flags=---A---F| 2001-03-13 12:50:52|drag-sensor1|DYNAMIC-TCP|23269548|1180897452|1558|21|I|---A----|6|tcp,sp=1558,dp=21,flags=---A----| 2001-03-13 12:50:53|drag-sensor1|DYNAMIC-TCP|23269548|1180897452|1559|21|I|------S-|6|tcp,sp=1559,dp=21,flags=------S-| 2001-03-13 12:50:53|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1559|I|---A--S-|6|tcp,sp=21,dp=1559,flags=---A--S-| 2001-03-13 12:50:53|drag-sensor1|DYNAMIC-TCP|23269548|1180897452|1559|21|I|---A----|6|tcp,sp=1559,dp=21,flags=---A----| 2001-03-13 12:50:56|drag-sensor1|DYNAMIC-TCP|1180897452|23269548|21|1559|I|---AP---|6|tcp,sp=21,dp=1559,flags=---AP---| Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 30.187.10.130 44654 dest 10.0.0.1 5631 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 93.132.178.83 25779 dest 10.0.0.1 32771 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 88.156.231.45 25645 dest 10.0.0.1 21 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 172.203.138.42 6368 dest 10.0.0.1 27665 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 112.8.46.29 38347 dest 10.0.0.1 80 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 17 Connection denied by outbound list 1 src 248.61.8.19 49358 dest 10.0.0.1 45224 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 70.139.144.19 21 dest 10.0.0.1 47681 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106018: ICMP packet type 3 denied by outbound list 1 src 0.0.0.0 dest 10.0.0.1 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 211.73.233.3 50103 dest 10.0.0.1 80 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 208.160.119.20 49038 dest 10.0.0.1 80 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 6 Connection denied by outbound list 1 src 109.92.79.135 110 dest 10.0.0.1 62919 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106002: 17 Connection denied by outbound list 1 src 95.14.76.85 2140 dest 10.0.0.1 60000 Mar 28 19:24:50 192.168.60.62 Mar 28 2001 23:06:34: %PIX-2-106018: ICMP packet type 11 denied by outbound list 1 src 0.0.0.0 dest 10.0.0.1
- 16. The Caltarian Technology Platform Firewalls IDS Raw logs Real-Time Alerts Health and Status Reporting Control and Configuration Customer Premise VPN AV/Content Authentication Server Future Services Relational DB Infrastructure Expert System & Anomaly Query Engine Progressive Threat Model Security Operations Center (SOC) Analyst Response Console Continuous Data Mining Process Import Facilities Authenticate Encrypt Verify Normalize Security Analysts Analysis Client Internet
- 17. The Caltarian Platform Enables Real-Time Monitoring True Security Data Mining: Extensive intelligence layer of on top of supported products Security Correlation: Across the enterprise and over time reveal undetectable attack patterns Algorithmic Costing of Security Events: Allows the most severe events to be processed within seconds Trend Analysis: Independent client and global trend analysis Global IP Tracking Identify coordinated attacks from different IP addresses Identifies new, not-yet-public vulnerabilities by evaluating new scanning and attack trends Progressive Threat Model: Models threat to target environments over time as attacks progress Engineered for Scalability: Automated data-mining technology reduces the unmanageable volumes of network security data to meaningful number of events for thousands of clients
- 18. Real-Time Managed Security Services Case Study: A Global Financial Institution Based on one months of actual customer data. Logs and alerts generated by firewalls and IDSs 9,481,668 620 Security Events The Caltarian processing engine identifies data patterns indicative of security threats Events Provided for Client Review 55 Riptech engineers weed out false positives and report valid events 2 Events Requiring Immediate Customer Contact Riptech proactively contacts clients to warn of a serious security threat
- 19. A Customer-Friendly Interface Enhances Client Interaction Powerful query and analysis tools Concise security event summary information Security events are prioritized according to severity
- 20. Detailed Information is Always Available: Empower the User Detailed analysts reports and recommendations Easy accessible log information Comprehensive event information from across the enterprise
- 21. Access to Log Data And Query Tools: Empower the User Searchable Log File Information Display Filters and Customizable View Options
- 22. The Caltarian Platform Enables Total Security Management Fault Management: Fault Management of interfaces, processes and devices Configuration Management: Firewall Policy Changes Configuration Client-to-Site VPN Adds, Moves, Changes and Deletes Site-to-Site VPN Adds, Moves, Changes and Deletes Operating System configuration Backups of Configurations Addition of new signatures on IDSs Performance Management: Collection of various performance statistics. System Management: Software patches, upgrades, system enhancements
- 23. Security Operations Centers (SOCs) Multi-million dollar facilities Distributed architecture and multiple SOCs provide fail-over capability Redundant power and connectivity Three-factor biometric personnel screening Easily branded for partners
- 24. The Market for Managed Security Rapidly growing market ŌĆō MSS expected to grow from $165M in 2000 to over $2B by 2007* Services range from simple configuration and implementation of security devices to comprehensive, 24x7x365, management and monitoring Value added service great complement to bandwidth and hosting *Frost & Sullivan Report on U.S. Managed Security Services
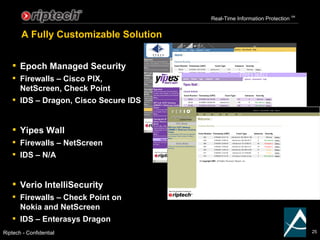
- 25. A Fully Customizable Solution Epoch Managed Security Firewalls ŌĆō Cisco PIX, NetScreen, Check Point IDS ŌĆō Dragon, Cisco Secure IDS Verio IntelliSecurity Firewalls ŌĆō Check Point on Nokia and NetScreen IDS ŌĆō Enterasys Dragon Yipes Wall Firewalls ŌĆō NetScreen IDS ŌĆō N/A
- 26. Partnering for Success Dedicated to providing managed security services through the channel Branded offering preserves your corporate identity Best of breed solution built on proprietary technology platform Complete support of industry leading firewalls and IDSs Flexible program designed to meet your specific business needs Significantly reduces costs and risks of developing your own managed security offering Zero time to market ŌĆō service can be implemented immediately GUARANTEED PROFIT MARGINS!
Editor's Notes
- #24: SOC is fully redundant, Strong physical security Stress Hot backup power, UPS 3 BGP peered T1 lines with 3 separate ISPs, and a 4 th cut-over T1 masquerading as another company. ensures against DDoS New Alexandria SOC by End of December 2000 New San Jose SOC in Q1, Europe Q2 Each soc will fail-over to each other

![The Managed Security Imperative 2099 Gateway Place San Jose, CA 95110 877-INFOSEC www.riptech.com [email_address] October 16, 2001 Copyright 2001 Riptech, Inc. Real-Time Information Protection SM](https://image.slidesharecdn.com/riptechveriopresentation-12616147003702-phpapp02/85/Riptech-Verio-Presentation-1-320.jpg)