RMF KPIs and KRIs
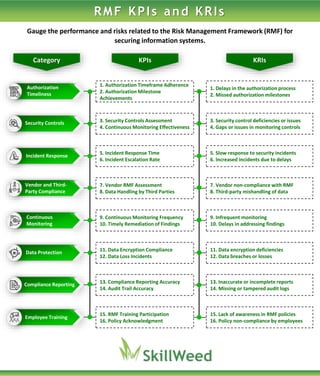
- 1. Authorization Timeliness 1. Authorization Timeframe Adherence 2. Authorization Milestone Achievements 1. Delays in the authorization process 2. Missed authorization milestones Security Controls 3. Security Controls Assessment 4. Continuous Monitoring Effectiveness 3. Security control deficiencies or issues 4. Gaps or issues in monitoring controls Incident Response 5. Incident Response Time 6. Incident Escalation Rate 5. Slow response to security incidents 6. Increased incidents due to delays Vendor and Third- Party Compliance 7. Vendor RMF Assessment 8. Data Handling by Third Parties 7. Vendor non-compliance with RMF 8. Third-party mishandling of data Continuous Monitoring 9. Continuous Monitoring Frequency 10. Timely Remediation of Findings 9. Infrequent monitoring 10. Delays in addressing findings Data Protection 11. Data Encryption Compliance 12. Data Loss Incidents 11. Data encryption deficiencies 12. Data breaches or losses Compliance Reporting 13. Compliance Reporting Accuracy 14. Audit Trail Accuracy 13. Inaccurate or incomplete reports 14. Missing or tampered audit logs Employee Training 15. RMF Training Participation 16. Policy Acknowledgment 15. Lack of awareness in RMF policies 16. Policy non-compliance by employees Category KPIs KRIs RMF KPIs and KRIs Gauge the performance and risks related to the Risk Management Framework (RMF) for securing information systems.