Rotor machine,subsitution technique
Download as pptx, pdf0 likes3,734 views
This document discusses rotor machines, which are electro-mechanical stream cipher devices used to encrypt and decrypt secret messages. Rotor machines were widely used for cryptography from the 1920s to 1970s. The most famous example is the German Enigma machine, whose messages were deciphered by the Allies during World War II to produce intelligence code-named Ultra. The document also briefly mentions that substitution ciphers encrypt by replacing plaintext units like single letters or pairs of letters with ciphertext units.
1 of 4
Downloaded 16 times


More Related Content
What's hot (20)
PPTX
Elgamal & schnorr digital signature scheme copyNorth Cap University (NCU) Formely ITM University?
Elgamal & schnorr digital signature scheme copyNorth Cap University (NCU) Formely ITM University
?
More from kirupasuchi1996 (15)
Ad
Recently uploaded (20)
PDF
Beginning-Laravel-Build-Websites-with-Laravel-5.8-by-Sanjib-Sinha-z-lib.org.pdfTagumLibuganonRiverB?
Beginning-Laravel-Build-Websites-with-Laravel-5.8-by-Sanjib-Sinha-z-lib.org.pdfTagumLibuganonRiverB
?
Ad
Rotor machine,subsitution technique
- 1. M.SUJITHA, II-M.SC(CS&IT), Nadar Saraswathi College Of Arts And Science, Theni
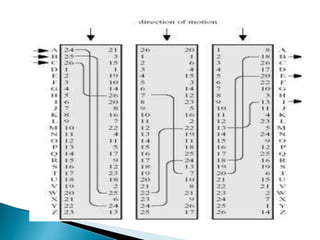
- 2. ? A rotor machine is an electro-mechanical stream cipher device used for encrypting and decrypting secret messages. ? Rotor machines were the cryptographic state-of-the-art for a prominent period of history; they were in widespread use in the 1920s¨C1970s. ? The most famous example is the German Enigma machine, whose messages were deciphered by the Allies during World War II, producing intelligence code-named Ultra.
- 4. ? Asubstitution cipher is a method of encrypting by which units of plaintext are replaced with ciphertext, ? According to a fixed system; the "units" may be single letters pairs of letters, triplets of letters.